| File name: | 782462857fa6aa85c7f7378b82974a0ebdf4a13ffdd219ba0a416e5af92e2e23.msi |
| Full analysis: | https://app.any.run/tasks/d5894c1f-c75c-4a53-8fa7-10a7633b9f30 |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2024, 17:30:17 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
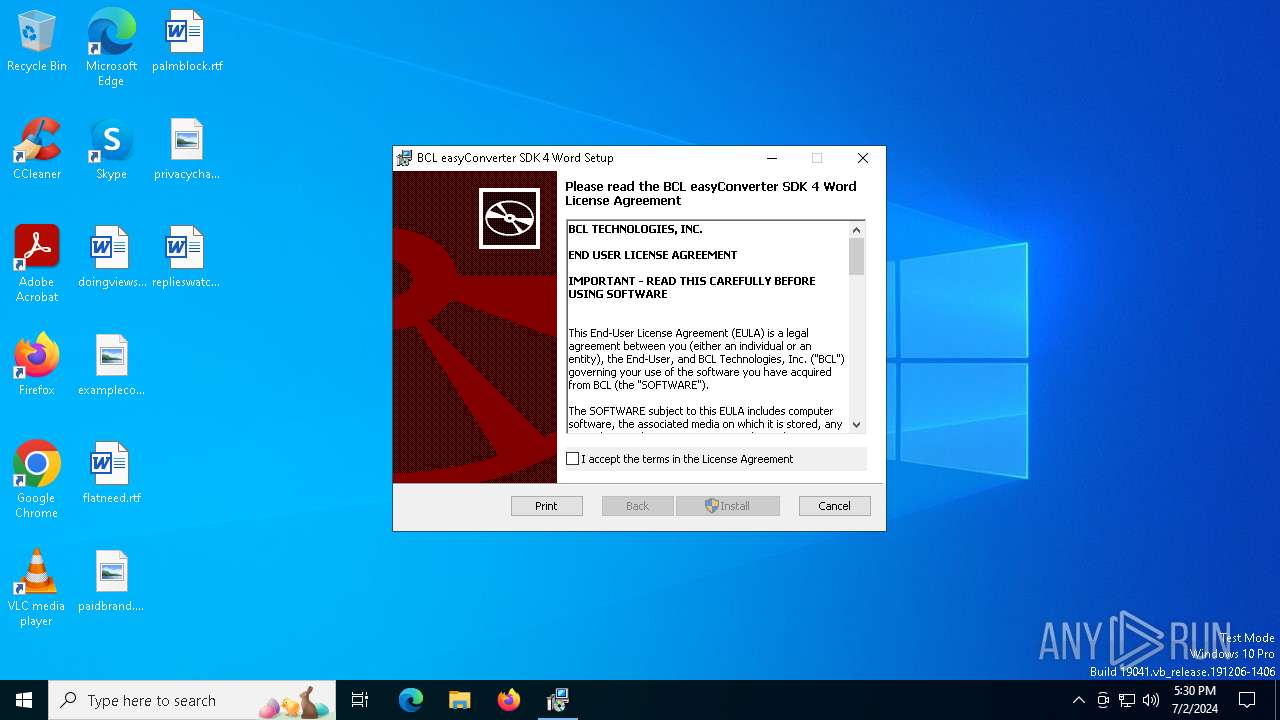
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: easyConverter SDK 4 Word, Author: BCL Technologies, Keywords: BCL easyConverter SDK Word, Comments: (C) 2016 BCL Technologies, Template: Intel;1033, Revision Number: {31248407-0343-46D6-B37F-B147C0BDE56B}, Create Time/Date: Thu Jul 28 20:42:16 2016, Last Saved Time/Date: Thu Jul 28 20:42:16 2016, Number of Pages: 100, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.9.1208.0), Security: 2 |
| MD5: | BA5DE7BD59011DE17B4F636180D38825 |
| SHA1: | 2B2303CD14B40EB03D63D0759701567EAE3CDDB0 |
| SHA256: | 782462857FA6AA85C7F7378B82974A0EBDF4A13FFDD219BA0A416E5AF92E2E23 |
| SSDEEP: | 98304:iylneOCpTxLxhwYjD+AIptwfC15g9mlk67x5koPU6M2maIo8Zp01nkCZTEu8wkV3:chbc4dQWImv4Nn7TtujyuXVQfRe |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 3392)
Registers / Runs the DLL via REGSVR32.EXE
- msiexec.exe (PID: 3392)
SUSPICIOUS
The process checks if it is being run in the virtual environment
- msiexec.exe (PID: 3556)
- msiexec.exe (PID: 3392)
Executes as Windows Service
- VSSVC.exe (PID: 3180)
Checks Windows Trust Settings
- msiexec.exe (PID: 3392)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 3392)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 3392)
- regsvr32.exe (PID: 6316)
INFO
Checks proxy server information
- msiexec.exe (PID: 3556)
An automatically generated document
- msiexec.exe (PID: 3556)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 3556)
Creates files or folders in the user directory
- msiexec.exe (PID: 3556)
Reads the software policy settings
- msiexec.exe (PID: 3556)
- msiexec.exe (PID: 3392)
Checks supported languages
- msiexec.exe (PID: 3392)
- msiexec.exe (PID: 1648)
- becldr.exe (PID: 6376)
Drops the executable file immediately after the start
- msiexec.exe (PID: 3556)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3556)
- msiexec.exe (PID: 3392)
Reads the computer name
- msiexec.exe (PID: 3392)
- msiexec.exe (PID: 1648)
- becldr.exe (PID: 6376)
Reads the machine GUID from the registry
- msiexec.exe (PID: 3392)
Creates a software uninstall entry
- msiexec.exe (PID: 3392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | easyConverter SDK 4 Word |
| Author: | BCL Technologies |
| Keywords: | BCL easyConverter SDK Word |
| Comments: | (C) 2016 BCL Technologies |
| Template: | Intel;1033 |
| RevisionNumber: | {31248407-0343-46D6-B37F-B147C0BDE56B} |
| CreateDate: | 2016:07:28 20:42:16 |
| ModifyDate: | 2016:07:28 20:42:16 |
| Pages: | 100 |
| Words: | 2 |
| Software: | Windows Installer XML Toolset (3.9.1208.0) |
| Security: | Read-only recommended |
Total processes
138
Monitored processes
8
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1648 | C:\Windows\syswow64\MsiExec.exe -Embedding 463D246A85747EE9A38E47F86BC593BB C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3180 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3392 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3556 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\782462857fa6aa85c7f7378b82974a0ebdf4a13ffdd219ba0a416e5af92e2e23.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4276 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6316 | "C:\WINDOWS\SysWOW64\regsvr32.exe" /s "C:\Program Files (x86)\BCL Technologies\easyConverter SDK 4\Rtf\beconv.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6376 | "C:\Program Files (x86)\BCL Technologies\easyConverter SDK 4\Common\becldr.exe" "C:\Program Files (x86)\BCL Technologies\easyConverter SDK 4\Common\becldr.exe" /RegServer | C:\Program Files (x86)\BCL Technologies\easyConverter SDK 4\Common\becldr.exe | — | msiexec.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: BCL EasyConverter Loader Exit code: 0 Version: 4, 0, 0, 1 Modules
| |||||||||||||||
Total events
14 925
Read events
14 289
Write events
607
Delete events
29
Modification events
| (PID) Process: | (3392) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000CFDD4D8CA5CCDA01400D0000F8040000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3392) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000005942508CA5CCDA01400D0000F8040000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3392) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000008978898CA5CCDA01400D0000F8040000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3392) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000008978898CA5CCDA01400D0000F8040000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3392) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000EA2F8E8CA5CCDA01400D0000F8040000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3392) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 48000000000000001795908CA5CCDA01400D0000F8040000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3392) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (3392) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000D1EFEF8CA5CCDA01400D0000F8040000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3392) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000FF53F28CA5CCDA01400D000040130000E8030000010000000000000000000000CACAEB44F0C26047BA654E6AC871CA3C00000000000000000000000000000000 | |||
| (PID) Process: | (3180) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000064B7F48CA5CCDA016C0C00009C0C0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
29
Suspicious files
110
Text files
80
Unknown types
47
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3392 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3392 | msiexec.exe | C:\WINDOWS\Installer\1b2576.msi | — | |
MD5:— | SHA256:— | |||
| 3556 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C46E7B0F942663A1EDC8D9D6D7869173_6043FC604A395E1485AF7AC16D16B7CE | binary | |
MD5:5BFA51F3A417B98E7443ECA90FC94703 | SHA256:BEBE2853A3485D1C2E5C5BE4249183E0DDAFF9F87DE71652371700A89D937128 | |||
| 3556 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\40C68D5626484A90937F0752C8B950AB | binary | |
MD5:C83250D443BD3ED5A71B7E9FF10DDC47 | SHA256:5EE73D2BF4CB684EBACEDD18BB9063BDBA0ED613EA4E98626CB2607D575AF9A0 | |||
| 3392 | msiexec.exe | C:\Program Files (x86)\BCL Technologies\easyConverter SDK 4\Common\Resource\90pv-RKSJ-H | binary | |
MD5:1B54AF63F9977FE92C7E828008669580 | SHA256:2C97A645E63D652FDE1F22012383180955894750C4BC6EE40160097B2D268D64 | |||
| 3556 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\40C68D5626484A90937F0752C8B950AB | der | |
MD5:A0AF4D81B2B19A99A3D01BE89D5F99D9 | SHA256:DE9F05CEB1610CF9964F0DEF09D525005569602993C82A647743F192E9414D4A | |||
| 3556 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EA618097E393409AFA316F0F87E2C202_FF5EB26160850ADC74D22788914C1202 | binary | |
MD5:F693A9A37DEC8650D608BF52BB338216 | SHA256:D7FA5474148F99204B4B7AF9AD3377A4A4086885E97F2303F663977DB840D00D | |||
| 3556 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C46E7B0F942663A1EDC8D9D6D7869173_6043FC604A395E1485AF7AC16D16B7CE | binary | |
MD5:8EE3AB3276A275057E9DD40FF5FA8BD5 | SHA256:F11F1DE92B61558E608199638ECC9CFE37017056C8D7841E805DAD57A7B03674 | |||
| 3392 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:4EFC878081903682E101088084F69B03 | SHA256:EE20D1BE21CCA5DE94300BDA543AF0954C1D76175815FA20817AC12E8F38E703 | |||
| 3556 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EA618097E393409AFA316F0F87E2C202_FF5EB26160850ADC74D22788914C1202 | der | |
MD5:5B79AA149A22607775D15C7E0255BACA | SHA256:9ABF4786A396CDAEE2F7E512C162DECBFB6BC90DD2F411EE1CA39E978FE1D5A1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
63
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3556 | msiexec.exe | GET | 200 | 152.199.19.74:80 | http://sv.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQe6LNDJdqx%2BJOp7hVgTeaGFJ%2FCQgQUljtT8Hkzl699g%2B8uK8zKt4YecmYCEAY32wra%2BgI8deasQ1ULEtU%3D | unknown | — | — | unknown |
3556 | msiexec.exe | GET | 200 | 152.199.19.74:80 | http://s2.symcb.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCED141%2Fl2SWCyYX308B7Khio%3D | unknown | — | — | unknown |
3556 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://s1.symcb.com/pca3-g5.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
3800 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
6828 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
2364 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
3800 | svchost.exe | GET | 200 | 2.21.20.133:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2624 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5636 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3800 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3556 | msiexec.exe | 152.199.19.74:80 | s2.symcb.com | EDGECAST | US | unknown |
3556 | msiexec.exe | 192.229.221.95:80 | s1.symcb.com | EDGECAST | US | whitelisted |
3040 | OfficeClickToRun.exe | 13.89.179.10:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3040 | OfficeClickToRun.exe | 192.229.221.95:80 | s1.symcb.com | EDGECAST | US | whitelisted |
3800 | svchost.exe | 2.21.20.133:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
s2.symcb.com |
| whitelisted |
s1.symcb.com |
| whitelisted |
sv.symcd.com |
| shared |
settings-win.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
www.bing.com |
| whitelisted |