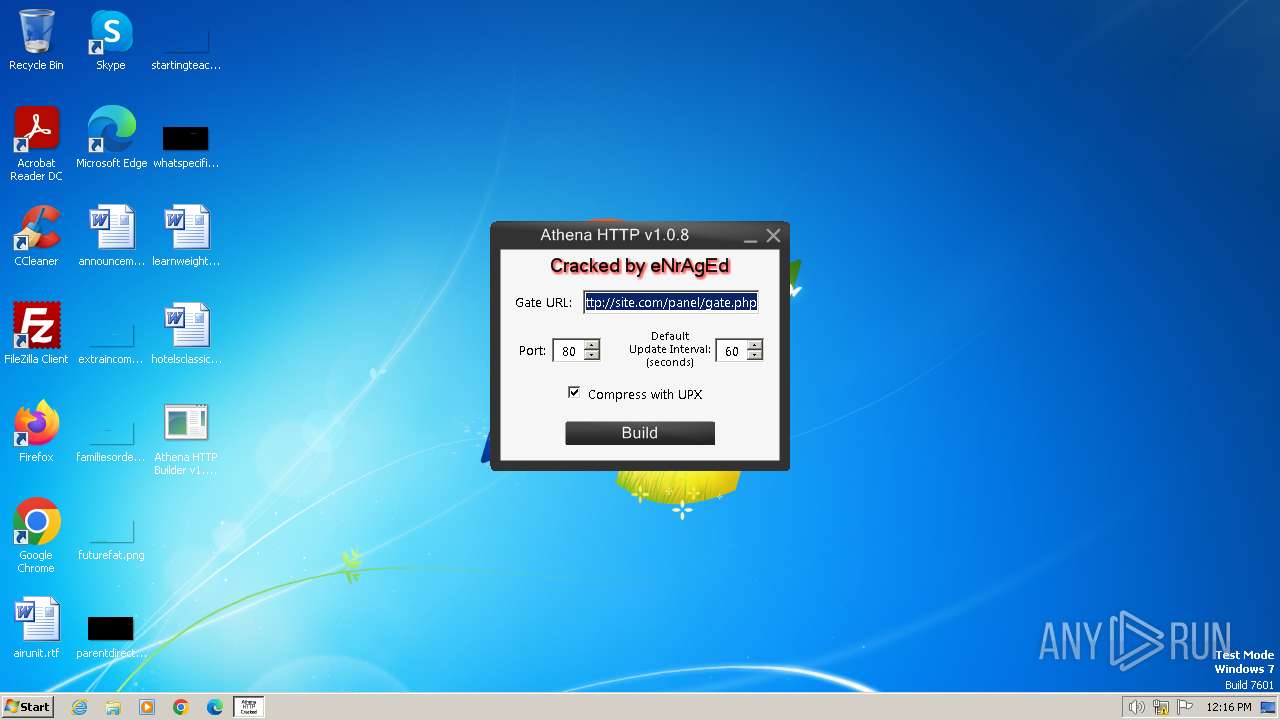
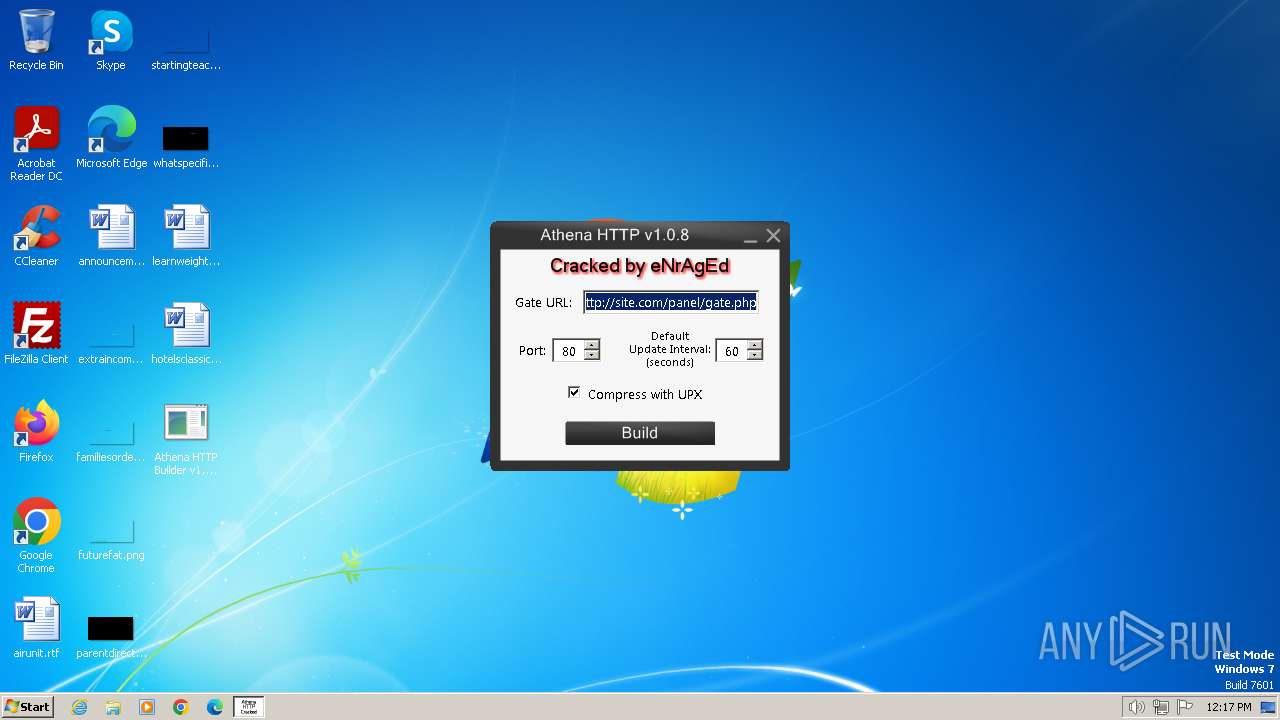
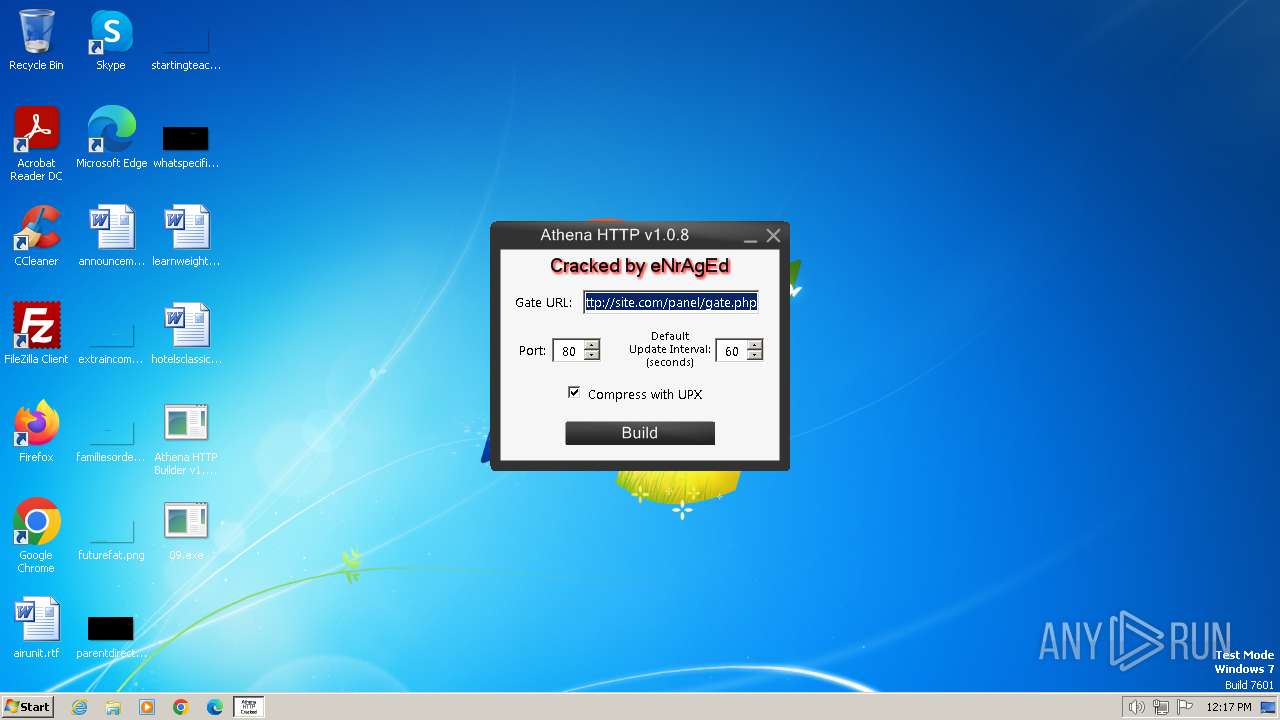
| File name: | Athena HTTP Builder v1.0.8.exe |
| Full analysis: | https://app.any.run/tasks/fd9ffdf6-682a-42bb-9478-8dcdb21255a3 |
| Verdict: | Malicious activity |
| Analysis date: | August 15, 2024, 11:16:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | DA3355DFF41717D157CC64F23746C26D |
| SHA1: | 78A8436413E20A09DD5490F15A3651B94B2EE28F |
| SHA256: | 78135C322E3841C2CF20B01D69F42AFE36BFE44254A0236EEC2A2773252926F2 |
| SSDEEP: | 49152:WXX+C0F5z+uR2FfCf5KBCovDr2CfYVNDuSDgbEpb8U5uWicSSdhQ+YrWbOT23S7Y:zFp+uR2FqsBzDHkZuS0bEpQyCJN+R9 |
MALICIOUS
Changes the autorun value in the registry
- tmp2.exe (PID: 3604)
Changes the login/logoff helper path in the registry
- tmp2.exe (PID: 3604)
Create files in the Startup directory
- tmp2.exe (PID: 3604)
SUSPICIOUS
Reads security settings of Internet Explorer
- Athena HTTP Builder v1.0.8.exe (PID: 1036)
Drops the executable file immediately after the start
- Athena HTTP Builder v1.0.8.exe (PID: 1036)
- tmp2.exe (PID: 3604)
- tmp1.exe (PID: 3660)
- upx.l2vptdvn.q3p.exe (PID: 648)
Executable content was dropped or overwritten
- Athena HTTP Builder v1.0.8.exe (PID: 1036)
- tmp2.exe (PID: 3604)
- wuauclt.exe (PID: 3460)
- tmp1.exe (PID: 3660)
- upx.l2vptdvn.q3p.exe (PID: 648)
Reads the Internet Settings
- Athena HTTP Builder v1.0.8.exe (PID: 1036)
- tmp1.exe (PID: 3660)
Application launched itself
- tmp2.exe (PID: 3604)
Suspicious files were dropped or overwritten
- wuauclt.exe (PID: 3460)
INFO
Checks supported languages
- Athena HTTP Builder v1.0.8.exe (PID: 1036)
- tmp1.exe (PID: 3660)
- tmp2.exe (PID: 3604)
- tmp2.exe (PID: 3452)
- wmpnscfg.exe (PID: 2516)
- upx.l2vptdvn.q3p.exe (PID: 648)
Reads the computer name
- tmp2.exe (PID: 3604)
- Athena HTTP Builder v1.0.8.exe (PID: 1036)
- wmpnscfg.exe (PID: 2516)
- tmp1.exe (PID: 3660)
Create files in a temporary directory
- Athena HTTP Builder v1.0.8.exe (PID: 1036)
- wuauclt.exe (PID: 3460)
- tmp1.exe (PID: 3660)
Reads mouse settings
- tmp2.exe (PID: 3604)
Creates files or folders in the user directory
- tmp2.exe (PID: 3604)
Manual execution by a user
- wmpnscfg.exe (PID: 2516)
Reads the machine GUID from the registry
- tmp1.exe (PID: 3660)
UPX packer has been detected
- tmp1.exe (PID: 3660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Microsoft Visual Basic 6 (33.3) |
|---|---|---|
| .exe | | | InstallShield setup (17.4) |
| .exe | | | Win32 Executable MS Visual C++ (generic) (12.6) |
| .exe | | | Win64 Executable (generic) (11.2) |
| .exe | | | UPX compressed Win32 Executable (10.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:10:30 15:44:41+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 8192 |
| InitializedDataSize: | 8192 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1280 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | eNrAgEd |
| FileDescription: | AthenaHttpBuilder-1.0.8 |
| FileVersion: | 1.0.0.0 |
| InternalName: | AthenaHttpBuilder-1.0.8.exe |
| LegalCopyright: | Copyright © eNrAgEd 2013 |
| OriginalFileName: | AthenaHttpBuilder-1.0.8.exe |
| ProductName: | AthenaHttpBuilder-1.0.8 |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
45
Monitored processes
7
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 648 | "C:\Users\admin\AppData\Local\Temp\upx.l2vptdvn.q3p.exe" -9 "C:\Users\admin\Desktop\09.exe" | C:\Users\admin\AppData\Local\Temp\upx.l2vptdvn.q3p.exe | tmp1.exe | ||||||||||||
User: admin Company: The UPX Team http://upx.sf.net Integrity Level: MEDIUM Description: UPX executable packer Exit code: 0 Version: 3.09 (2013-02-18) Modules
| |||||||||||||||
| 1036 | "C:\Users\admin\Desktop\Athena HTTP Builder v1.0.8.exe" | C:\Users\admin\Desktop\Athena HTTP Builder v1.0.8.exe | explorer.exe | ||||||||||||
User: admin Company: eNrAgEd Integrity Level: MEDIUM Description: AthenaHttpBuilder-1.0.8 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2516 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3452 | "C:\Users\admin\AppData\Local\Temp\tmp2.exe" | C:\Users\admin\AppData\Local\Temp\tmp2.exe | — | tmp2.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java Control Panel Exit code: 0 Version: 10.45.2.18 Modules
| |||||||||||||||
| 3460 | C:\Windows\system32\wuauclt.exe | C:\Windows\System32\wuauclt.exe | tmp2.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Update Version: 7.6.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 3604 | "C:\Users\admin\AppData\Local\Temp\tmp2.exe" | C:\Users\admin\AppData\Local\Temp\tmp2.exe | Athena HTTP Builder v1.0.8.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java Control Panel Exit code: 0 Version: 10.45.2.18 Modules
| |||||||||||||||
| 3660 | "C:\Users\admin\AppData\Local\Temp\tmp1.exe" | C:\Users\admin\AppData\Local\Temp\tmp1.exe | Athena HTTP Builder v1.0.8.exe | ||||||||||||
User: admin Company: eNrAgEd Integrity Level: MEDIUM Description: AthenaHttpBuilder-1.0.8 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
8 034
Read events
7 979
Write events
50
Delete events
5
Modification events
| (PID) Process: | (1036) Athena HTTP Builder v1.0.8.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1036) Athena HTTP Builder v1.0.8.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1036) Athena HTTP Builder v1.0.8.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1036) Athena HTTP Builder v1.0.8.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3604) tmp2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Facebook Update |
Value: %APPDATA%\Microsoft\update.exe | |||
| (PID) Process: | (3604) tmp2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | shell |
Value: %APPDATA%\Microsoft\update.exe,explorer.exe | |||
| (PID) Process: | (3460) wuauclt.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows |
| Operation: | write | Name: | Load |
Value: C:\Users\admin\LOCALS~1\Temp\msvfucr.bat | |||
| (PID) Process: | (3660) tmp1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | write | Name: | 5 |
Value: 74006D00700031002E00650078006500000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000000000000 | |||
| (PID) Process: | (3660) tmp1.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3660) tmp1.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 01000000020000000700000000000000060000000B0000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
Executable files
8
Suspicious files
0
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3604 | tmp2.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Facebook.lnk | lnk | |
MD5:D4706050B67094DCCA58AF1B3C977302 | SHA256:78F1607A2508695E9803EEA57E57C29F2EA7CF9731A273BFDDDC7BB4B14BC6BE | |||
| 1036 | Athena HTTP Builder v1.0.8.exe | C:\Users\admin\AppData\Local\Temp\tmp2.exe | executable | |
MD5:0C107D21DDFFCEFF02B4E1BAF9468FA9 | SHA256:09BFEDC9E0613F5F859853C338EE9845C4307728CA370036F31AC1D596B98C2C | |||
| 648 | upx.l2vptdvn.q3p.exe | C:\Users\admin\Desktop\09.exe | executable | |
MD5:5E9BF52AE614088127E2D57961629AFB | SHA256:CFA4F556075B1B843A329B8B3A1F5449E3AB0E26BC9C2352025D0443A3291994 | |||
| 3660 | tmp1.exe | C:\Users\admin\AppData\Local\Temp\upx.l2vptdvn.q3p.exe | executable | |
MD5:2EC42EEA603C34B79287A4C84C83D851 | SHA256:247F1B56B4600708746A8BF0CD66F11CC047D5F9D531ACC69AF41EFC5C5884E5 | |||
| 3604 | tmp2.exe | C:\Users\admin\AppData\Roaming\Microsoft\update.exe | executable | |
MD5:0C107D21DDFFCEFF02B4E1BAF9468FA9 | SHA256:09BFEDC9E0613F5F859853C338EE9845C4307728CA370036F31AC1D596B98C2C | |||
| 3460 | wuauclt.exe | C:\Users\admin\AppData\Local\Temp\msvfucr.bat | executable | |
MD5:0C107D21DDFFCEFF02B4E1BAF9468FA9 | SHA256:09BFEDC9E0613F5F859853C338EE9845C4307728CA370036F31AC1D596B98C2C | |||
| 3660 | tmp1.exe | C:\Users\admin\Desktop\09.exe | executable | |
MD5:932D251C4CF32BE6F751F0F35CA3C054 | SHA256:9574BF0275858FD5FAA11E99E9AD7C5D2DAA468DCE74F3F7B6BBD8A394769A0E | |||
| 648 | upx.l2vptdvn.q3p.exe | C:\Users\admin\Desktop\09.upx | executable | |
MD5:5E9BF52AE614088127E2D57961629AFB | SHA256:CFA4F556075B1B843A329B8B3A1F5449E3AB0E26BC9C2352025D0443A3291994 | |||
| 1036 | Athena HTTP Builder v1.0.8.exe | C:\Users\admin\AppData\Local\Temp\tmp1.exe | executable | |
MD5:60E8E0F8289D807837F2E2FF5D641559 | SHA256:1F35D00FEEA7EE13ABF919D0F2BEE7D27403CD1900C356056A842C7FCA3B67A6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
10
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 23.50.131.216:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 20.44.239.154:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | SG | unknown |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
3460 | wuauclt.exe | 20.109.209.108:80 | www.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1372 | svchost.exe | 23.50.131.216:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.update.microsoft.com |
| whitelisted |
posticum.lambahost.com |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |