| File name: | sgv7qi.xlsm |
| Full analysis: | https://app.any.run/tasks/a86d04ee-faed-4583-8b95-83b0e6eea570 |
| Verdict: | Malicious activity |
| Analysis date: | February 11, 2019, 01:39:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.spreadsheetml.sheet |
| File info: | Microsoft Excel 2007+ |
| MD5: | 4EDD901B77B576506E9396EA3EDF59CE |
| SHA1: | 04A8AE60FAE237B7A8EE1C244653E66A928F3AF8 |
| SHA256: | 78132071D580D02F75A98B83A0C7412286F51E1C34584D6CE61D324C2FACC94F |
| SSDEEP: | 384:HBhUJqQPczqQKrHehHSNvNYixcYcABPJ2cQuiB:hhU7tpe1SCiGtABPqJ |
MALICIOUS
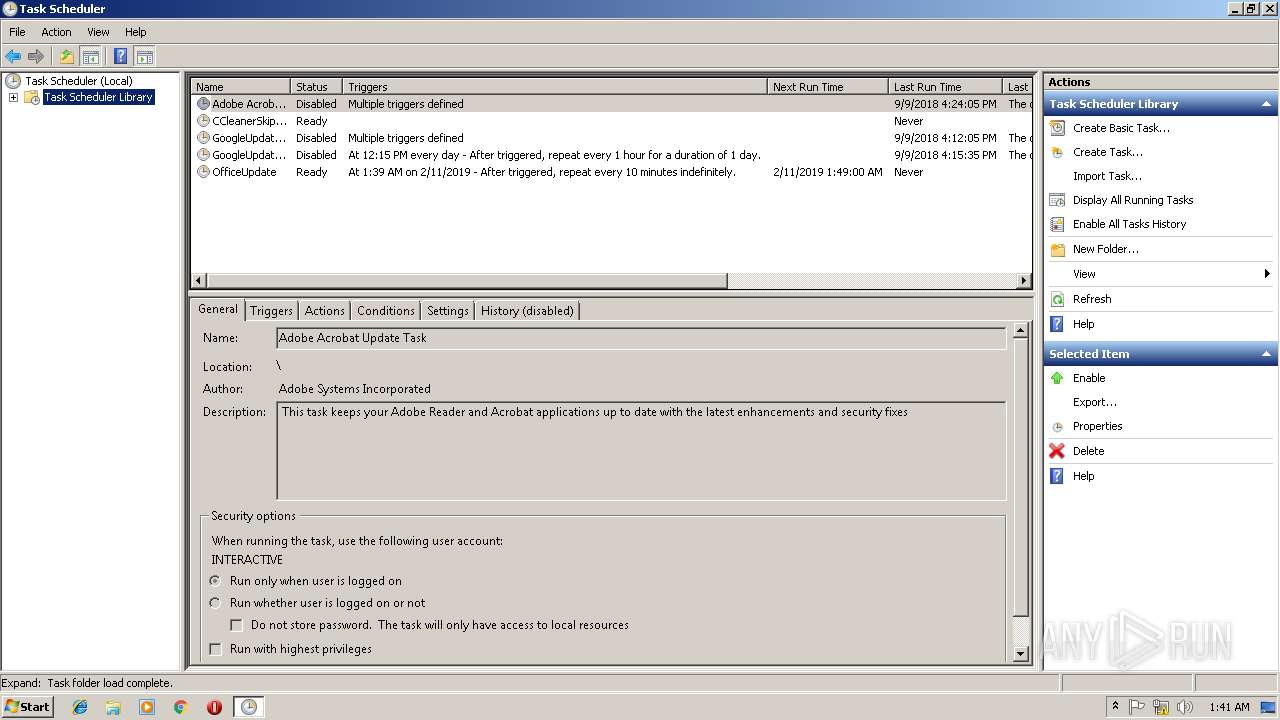
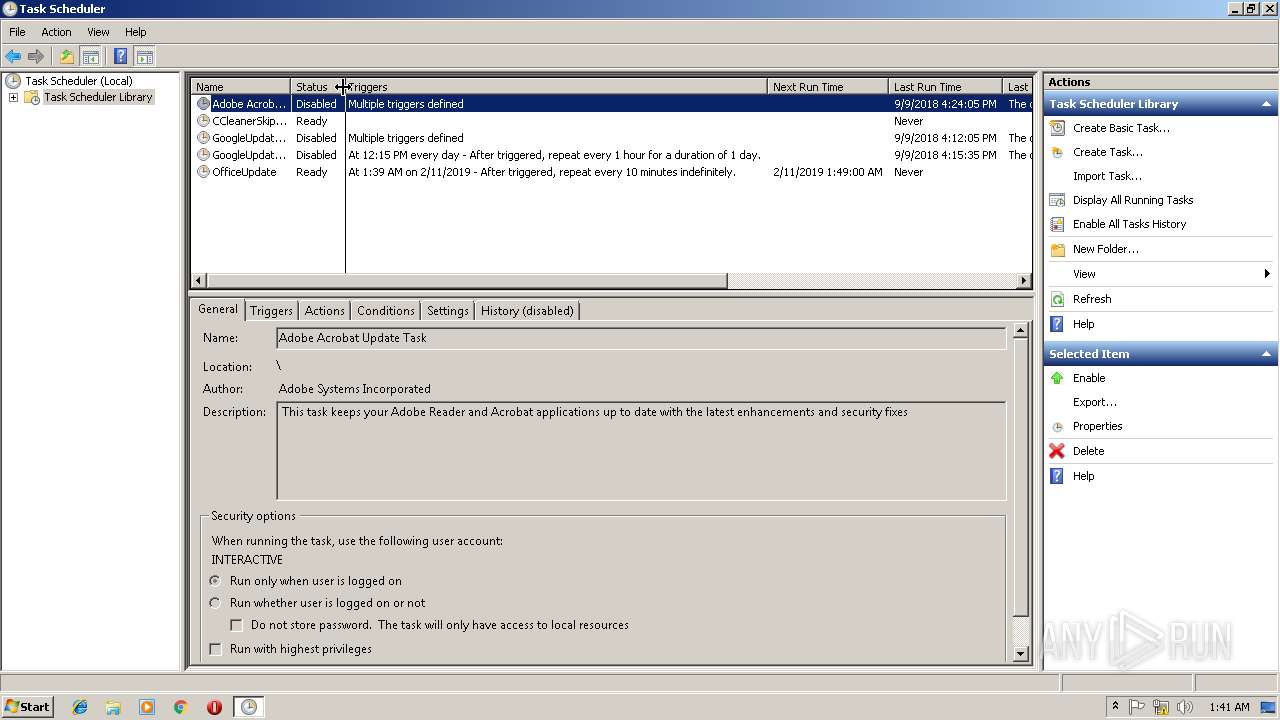
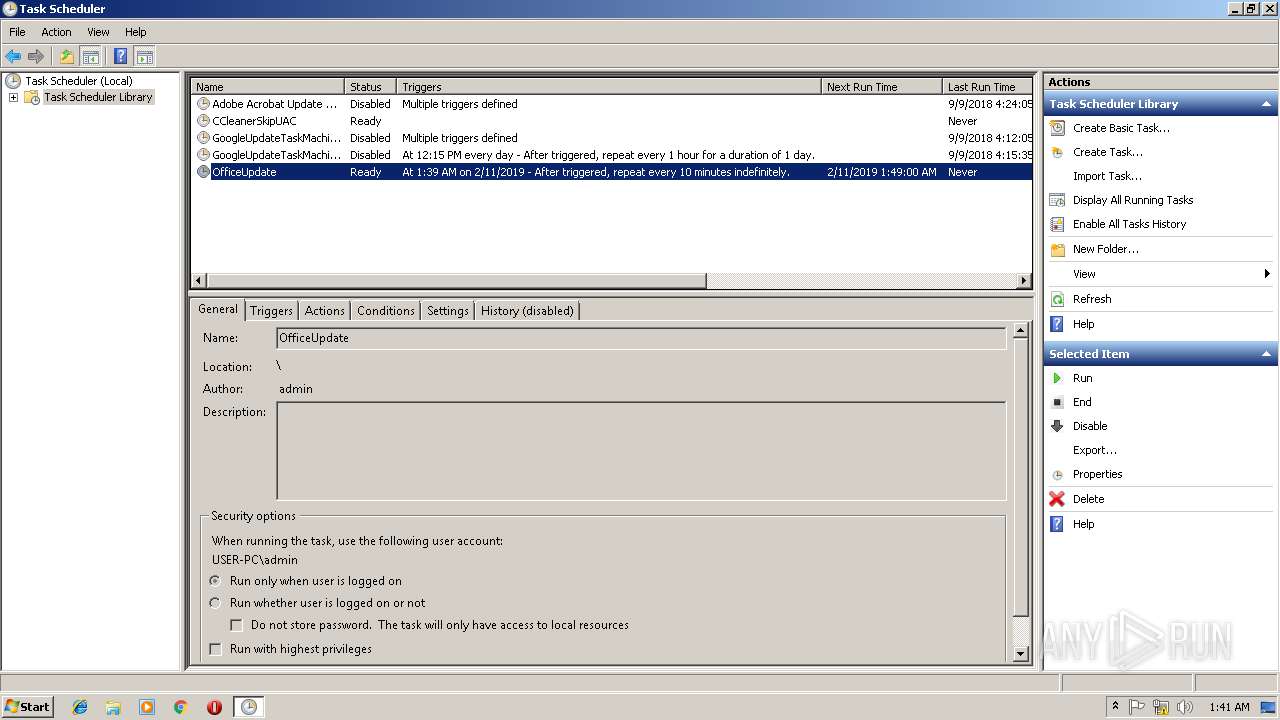
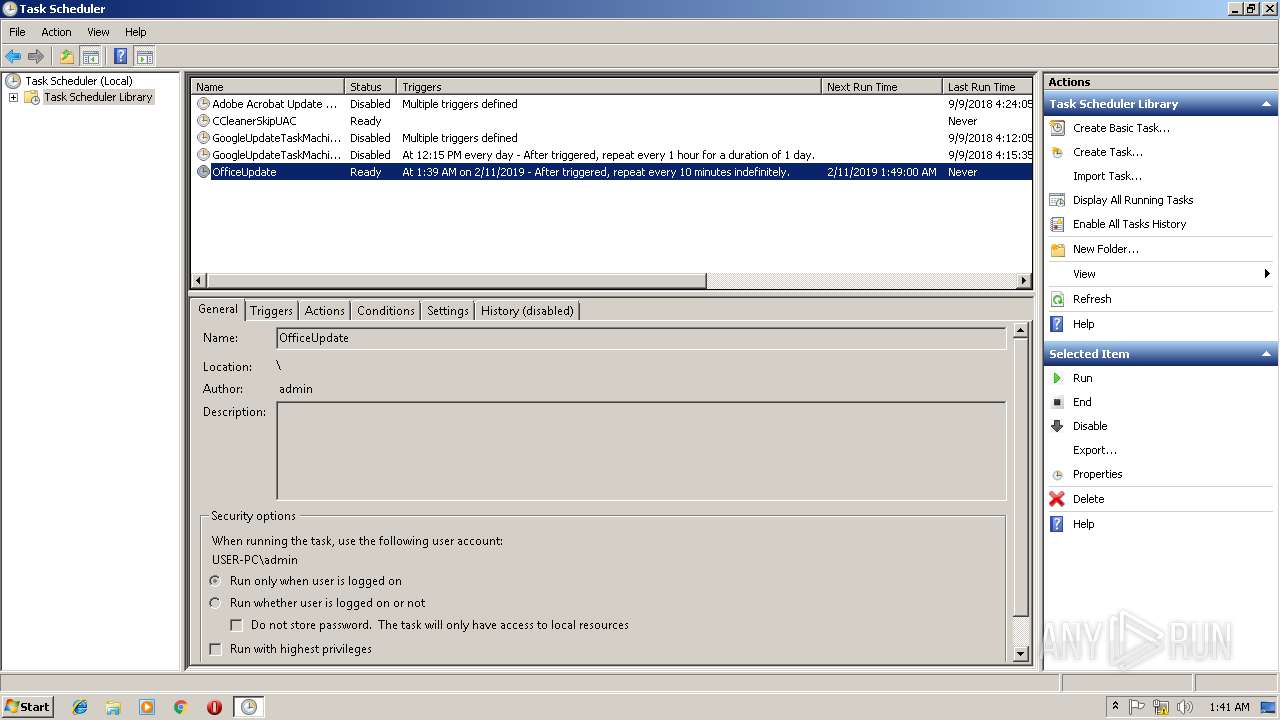
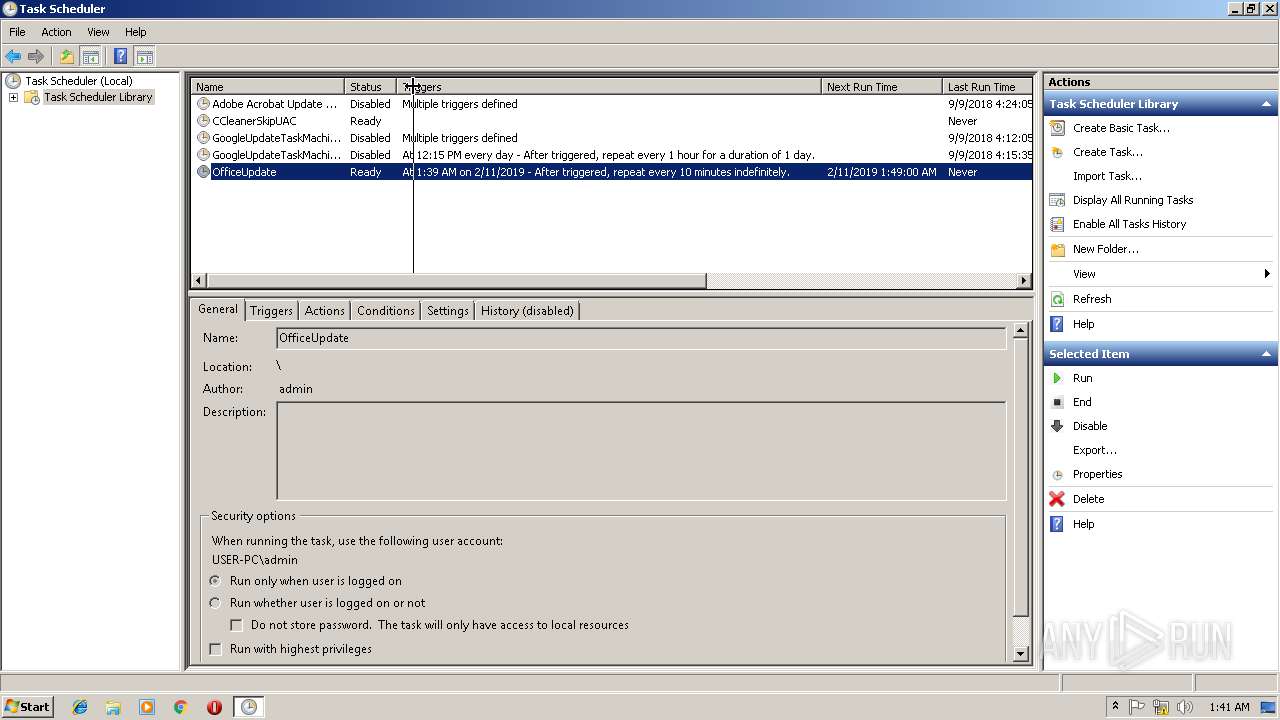
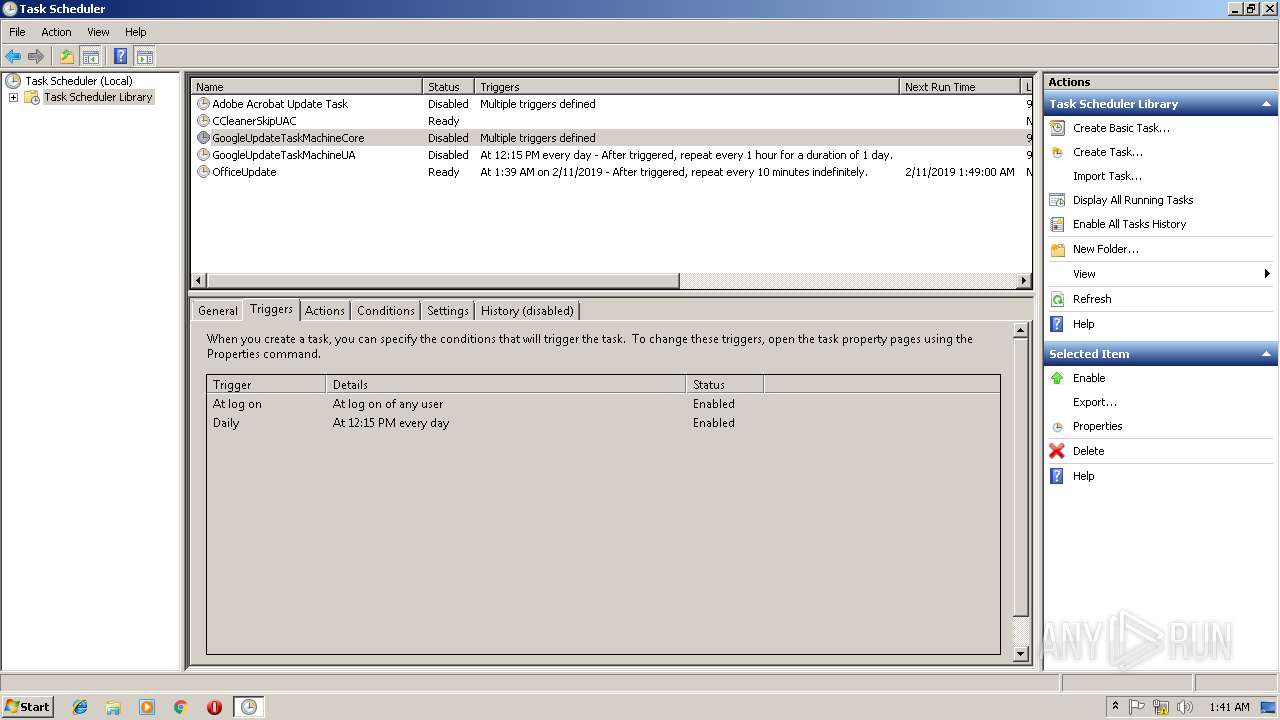
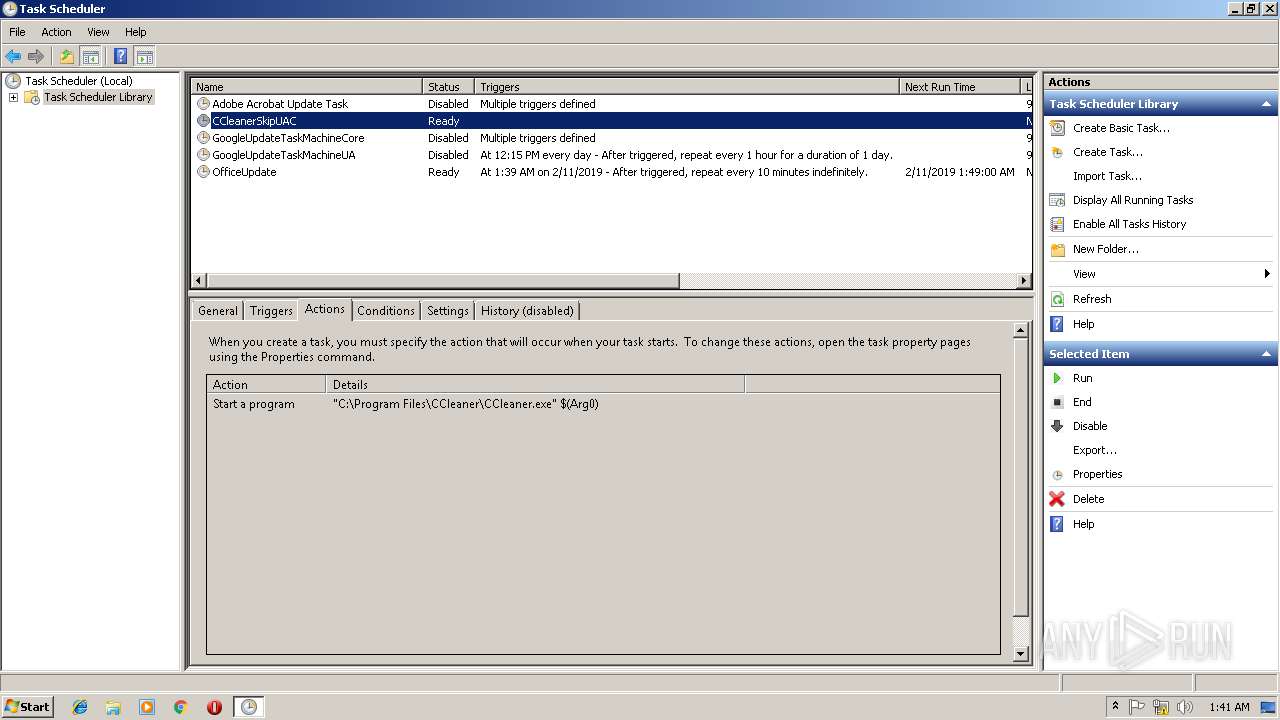
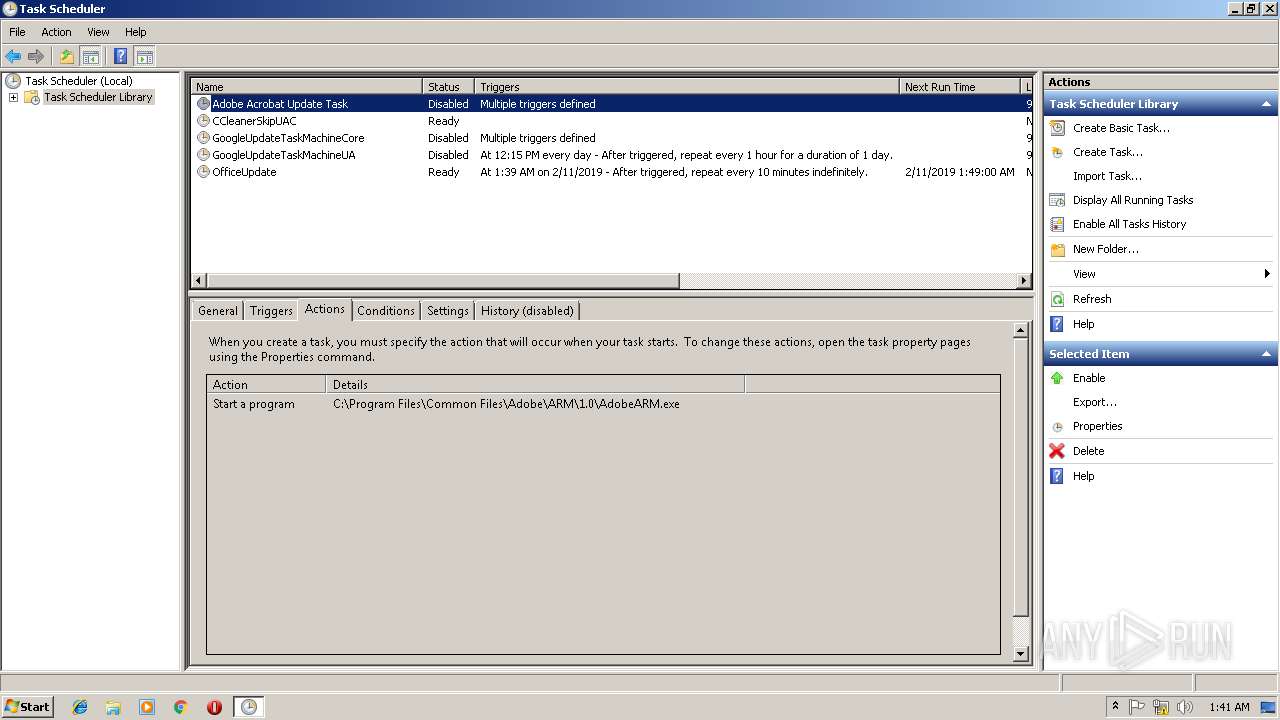
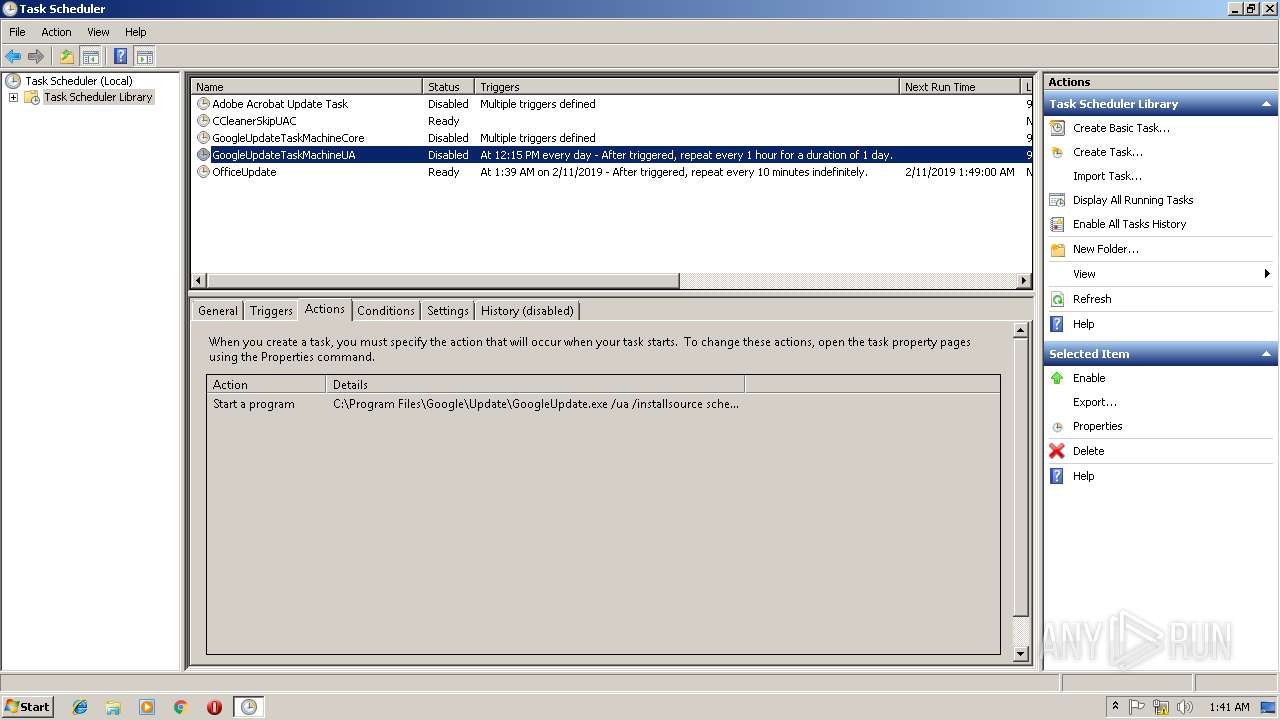
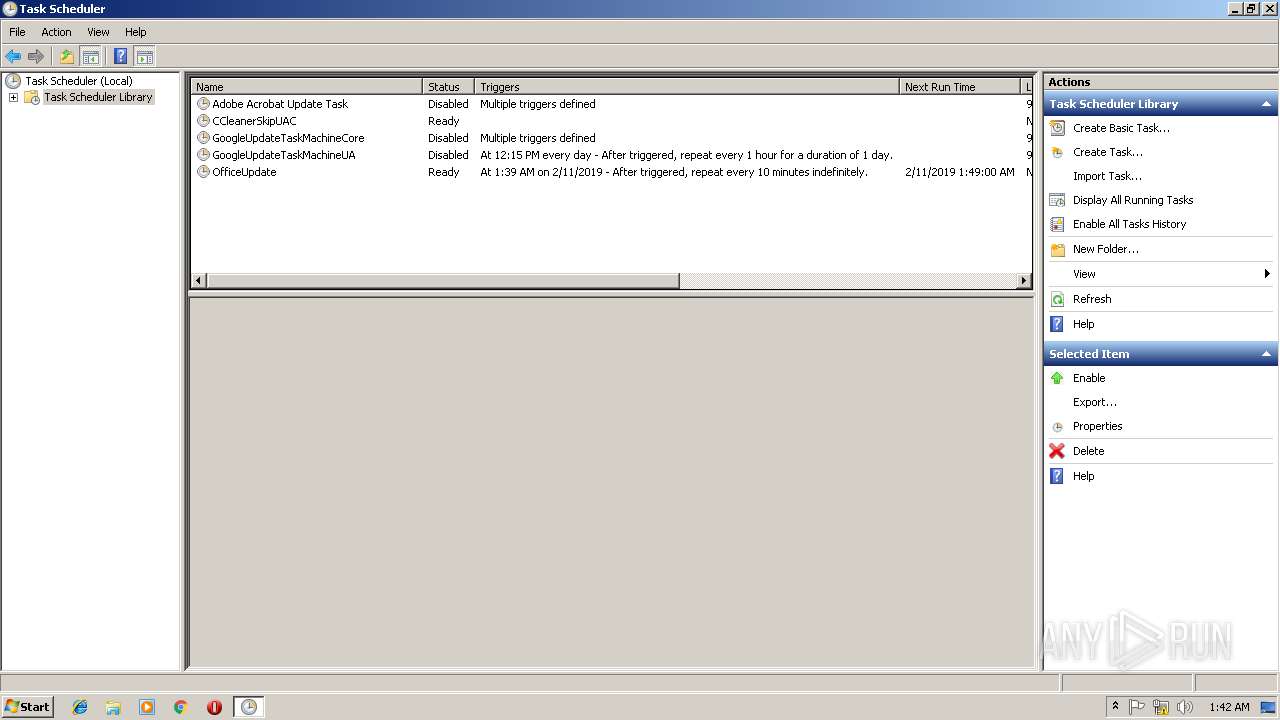
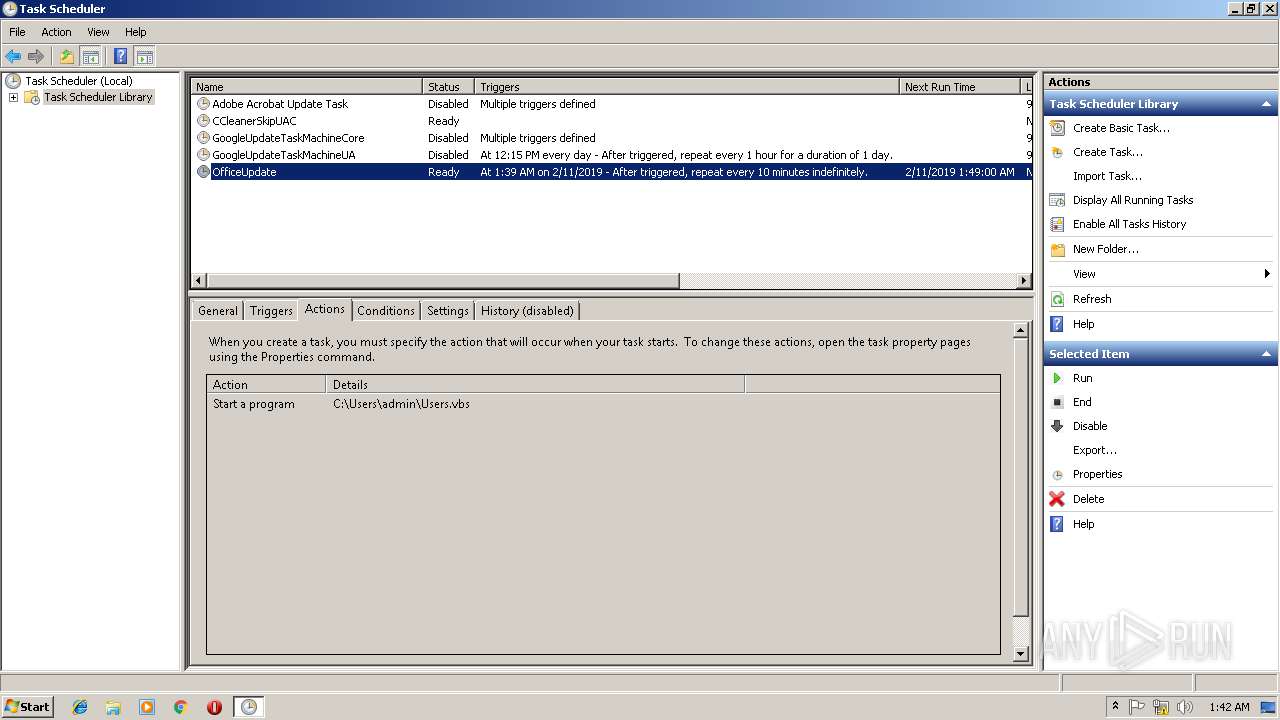
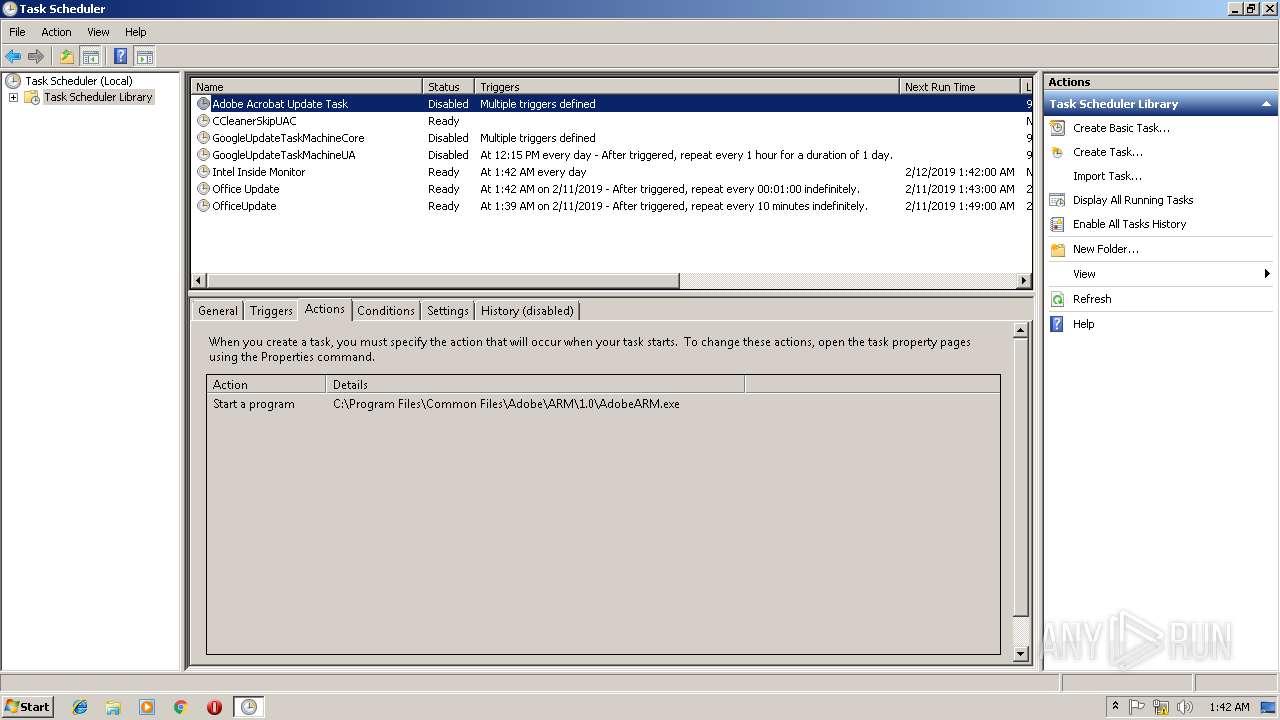
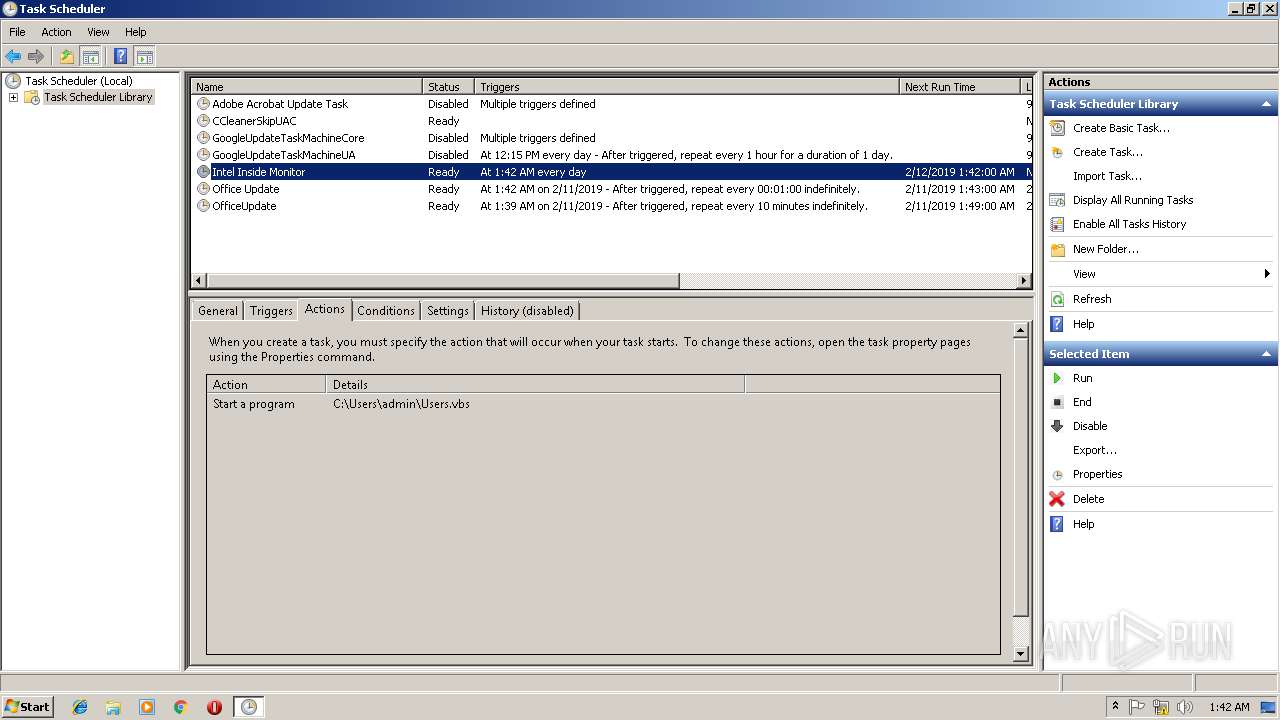
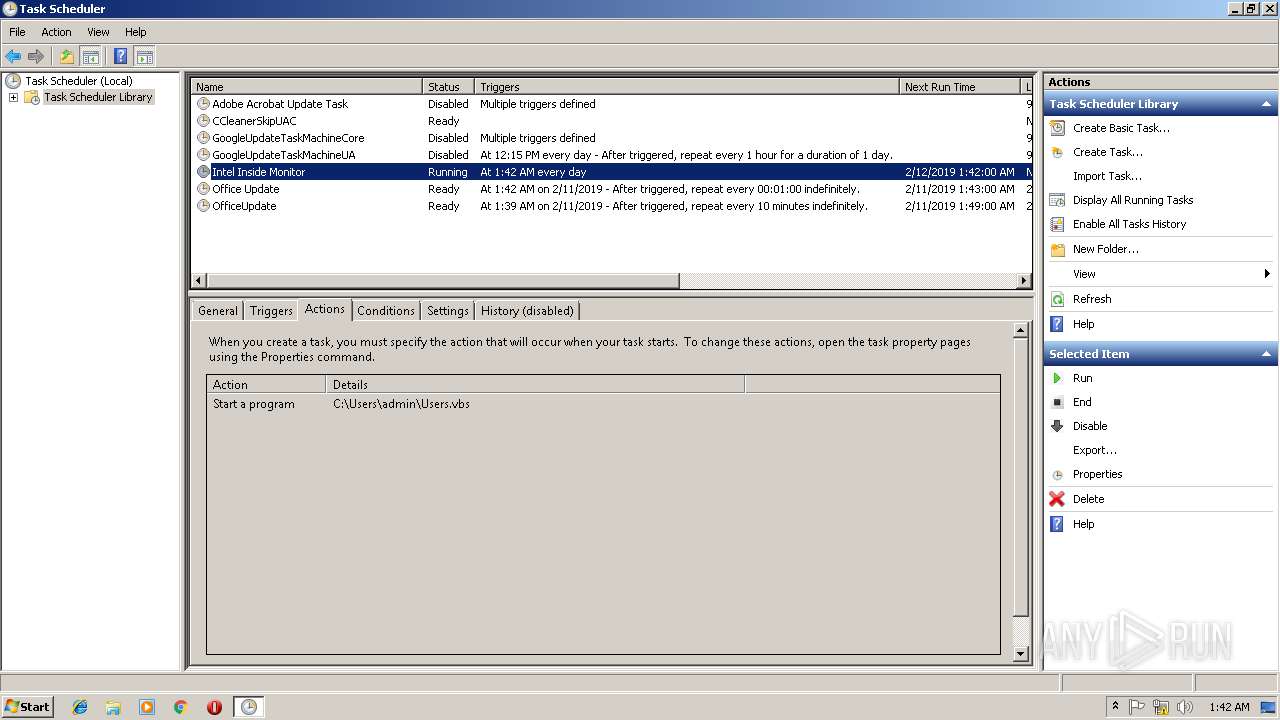
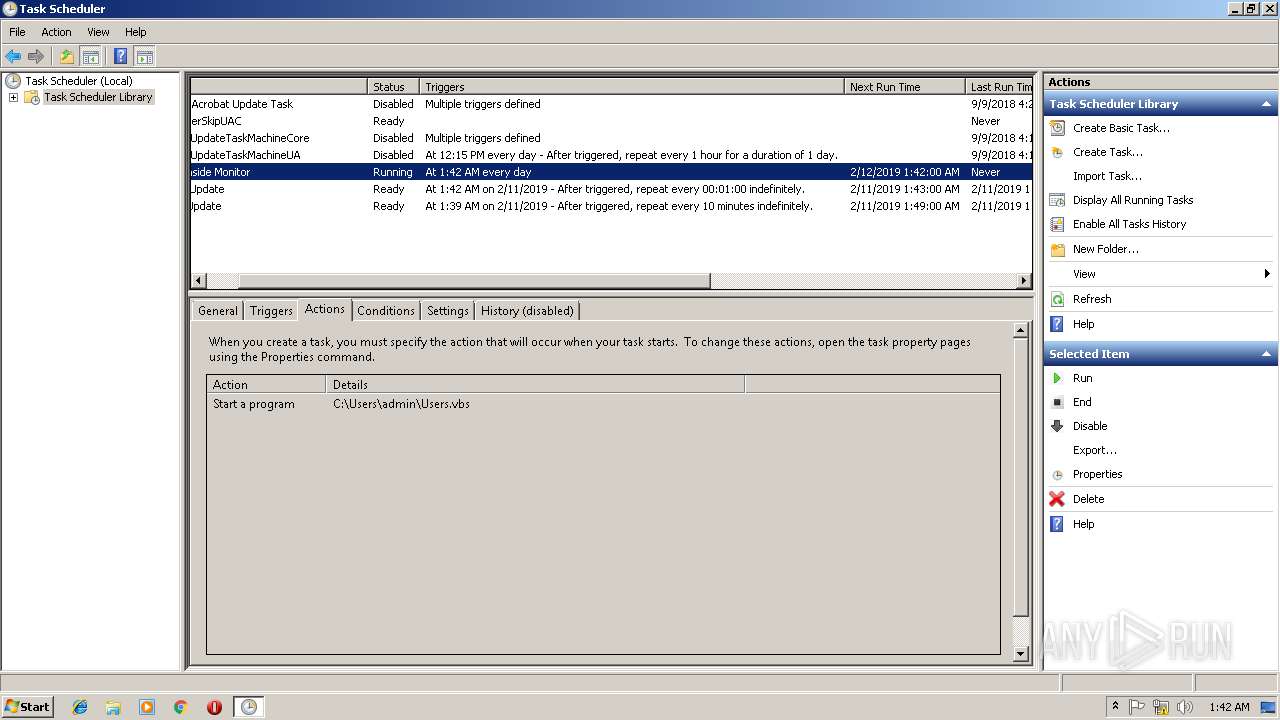
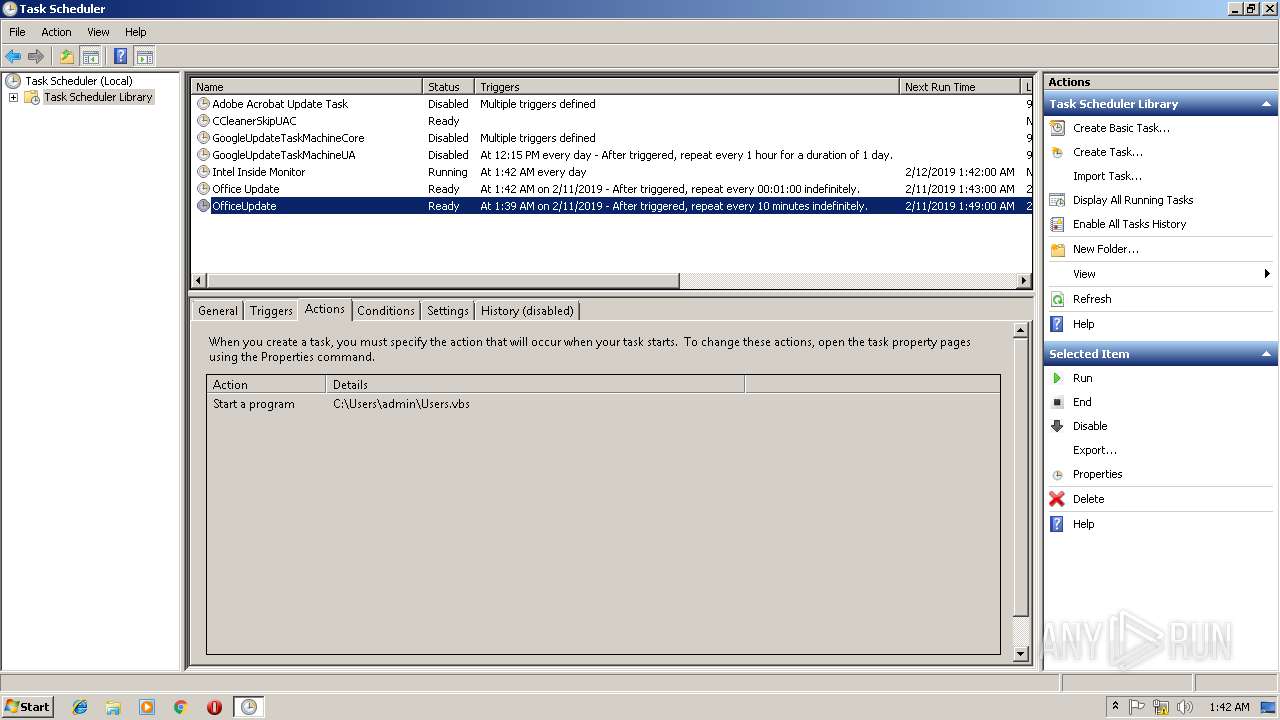
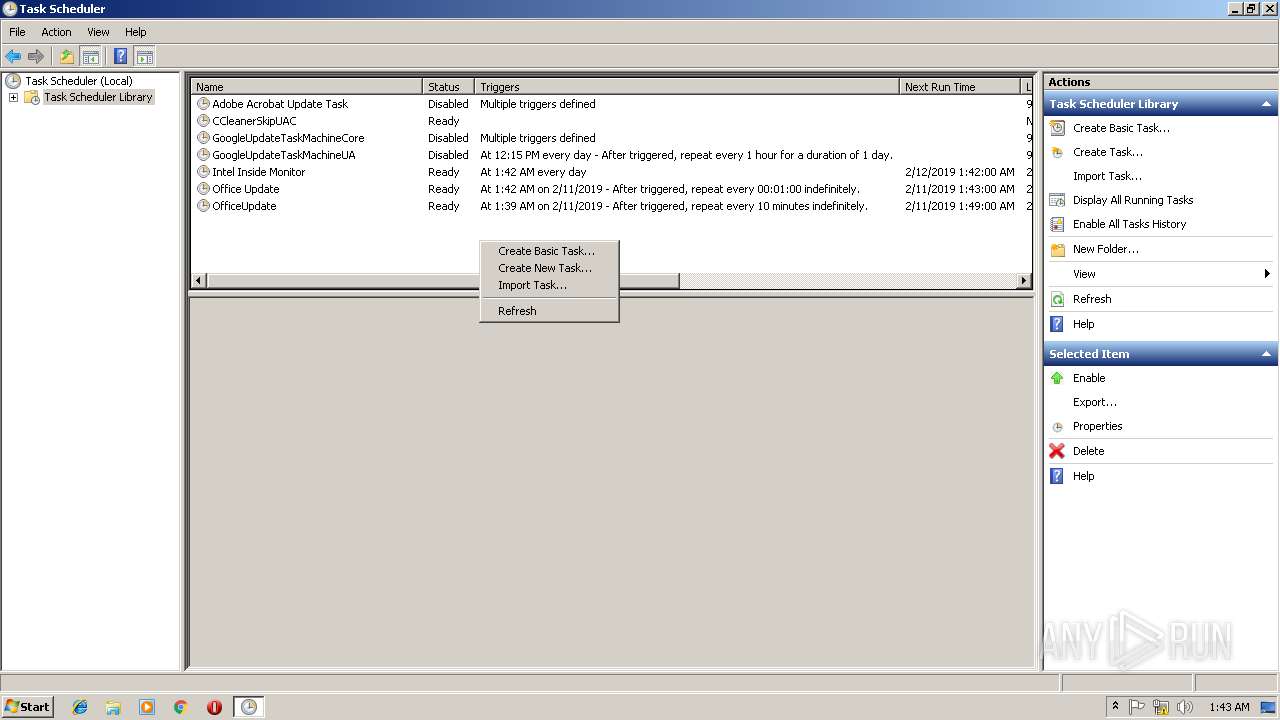
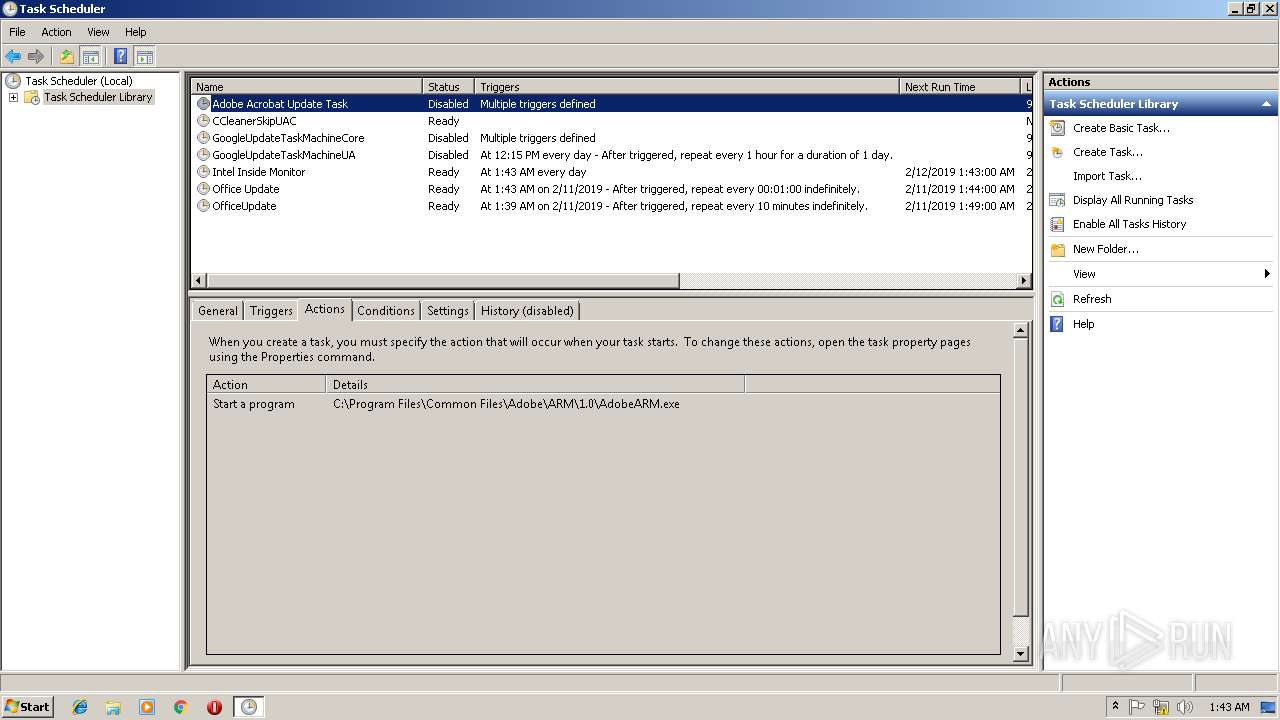
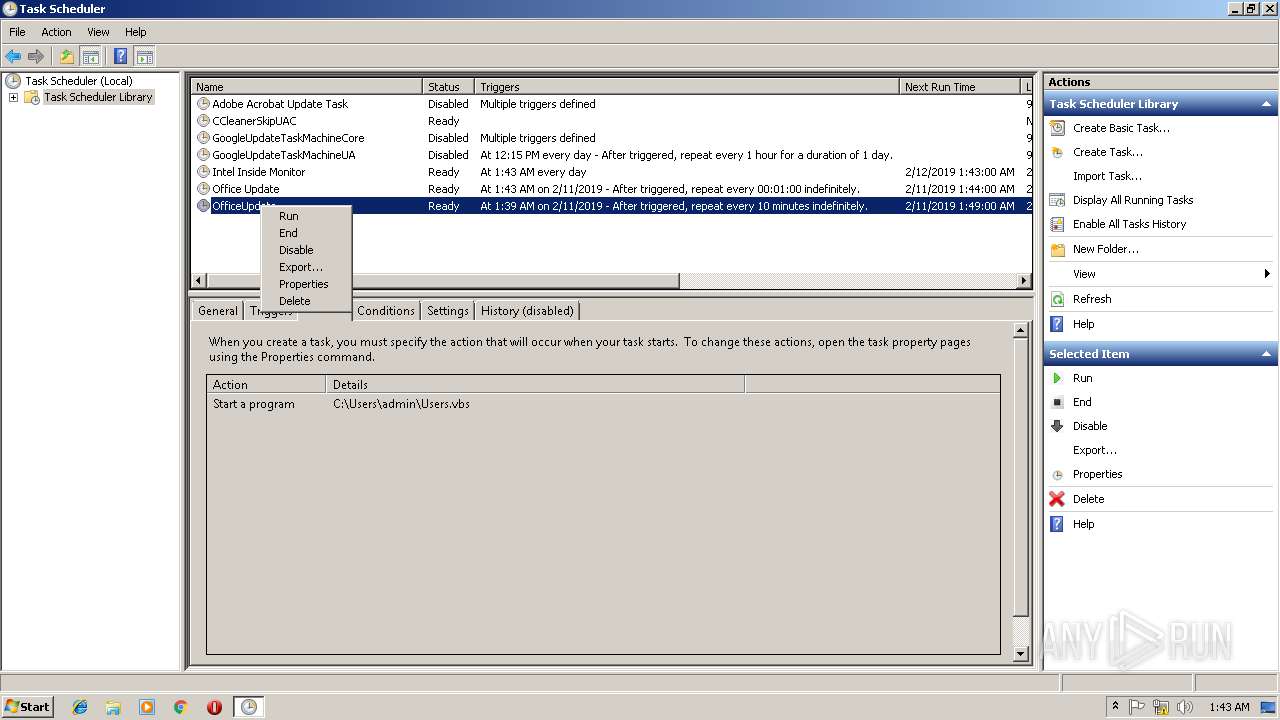
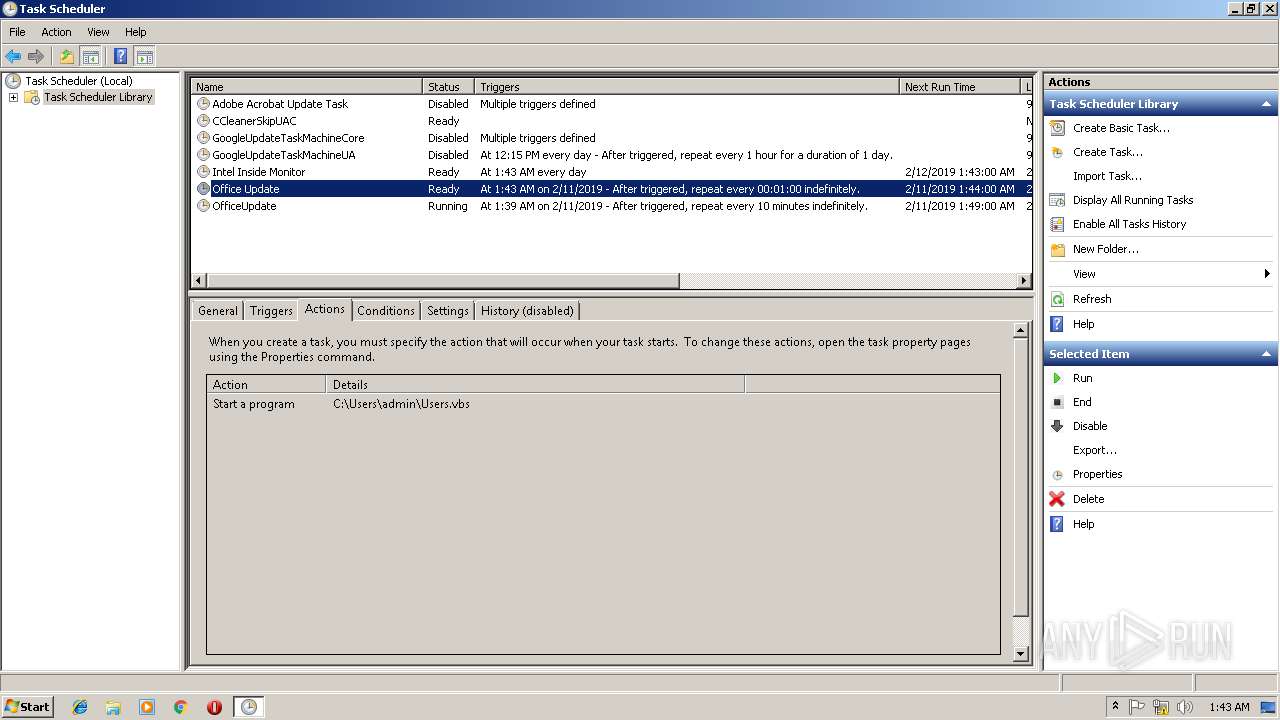
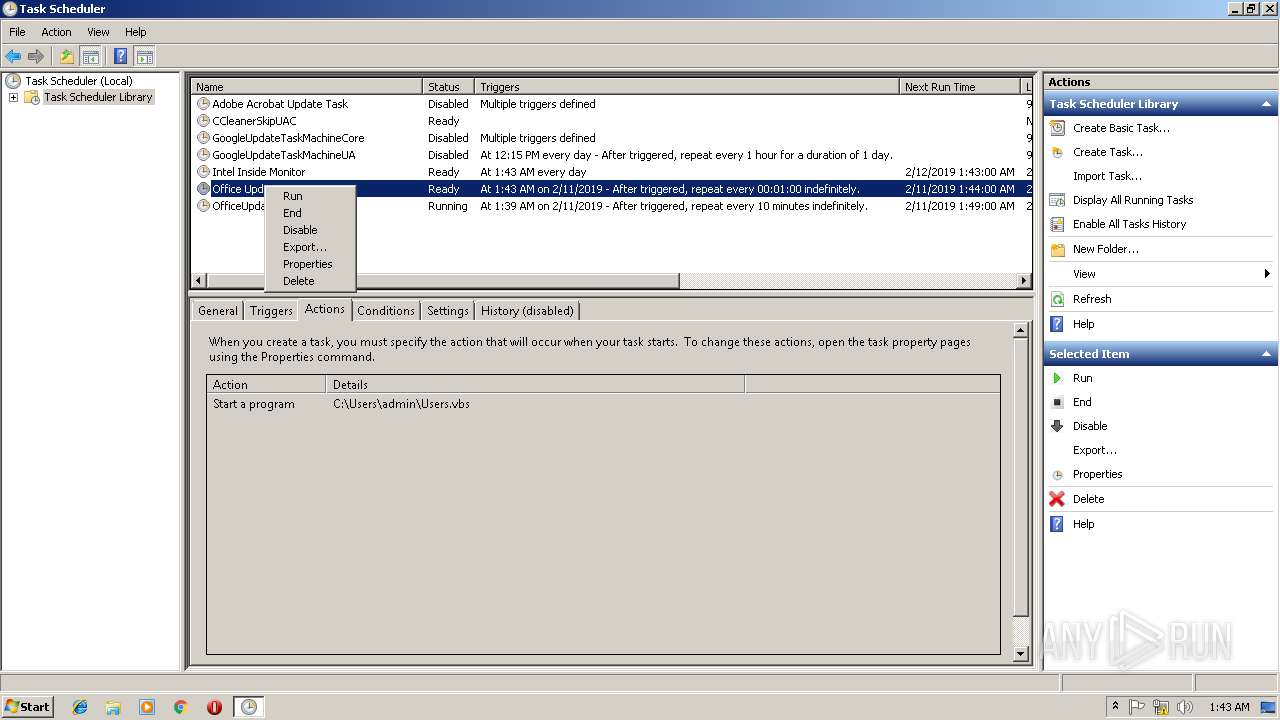
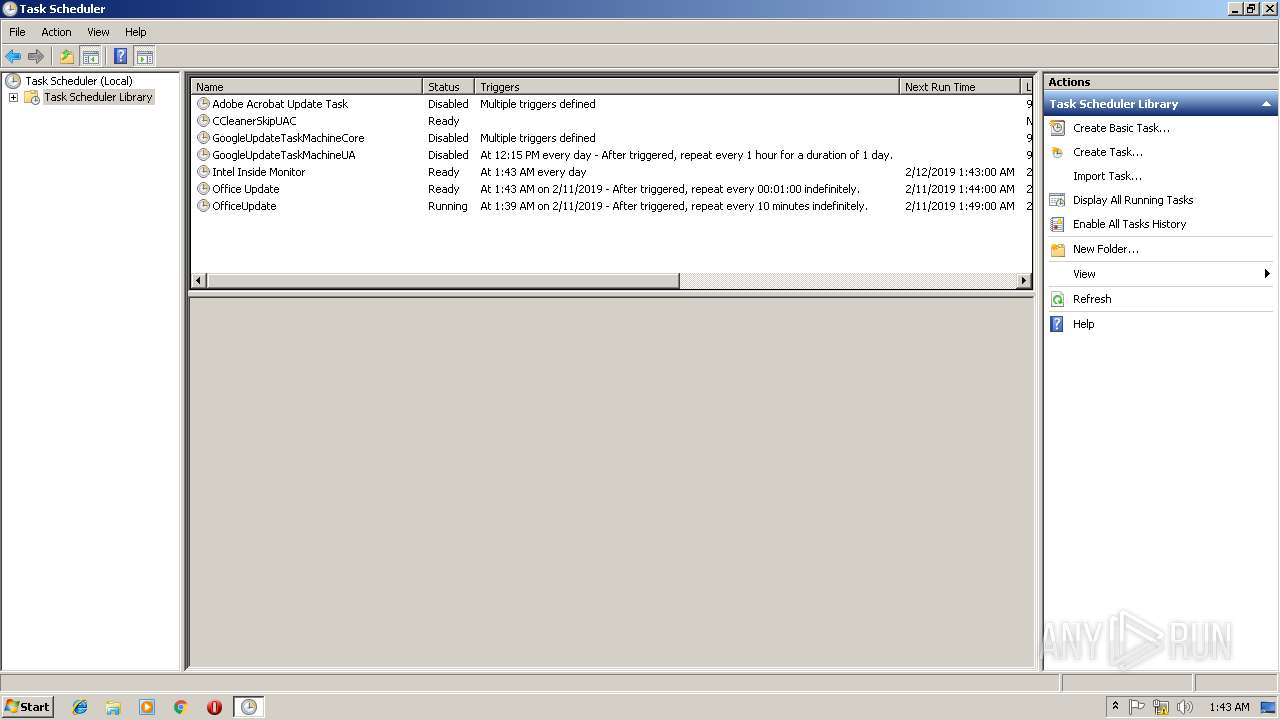
Uses Task Scheduler to run other applications
- EXCEL.EXE (PID: 2764)
- WScript.exe (PID: 3836)
- WScript.exe (PID: 2812)
- WScript.exe (PID: 3976)
- WScript.exe (PID: 3072)
- WScript.exe (PID: 2408)
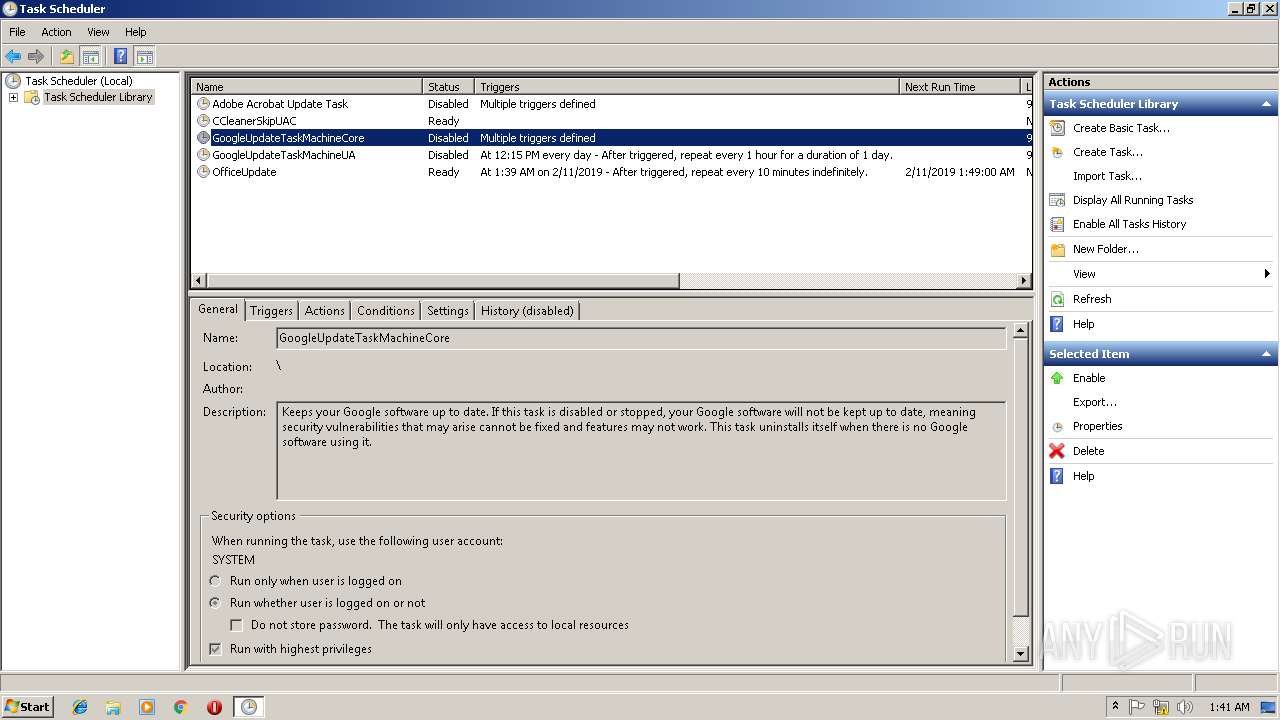
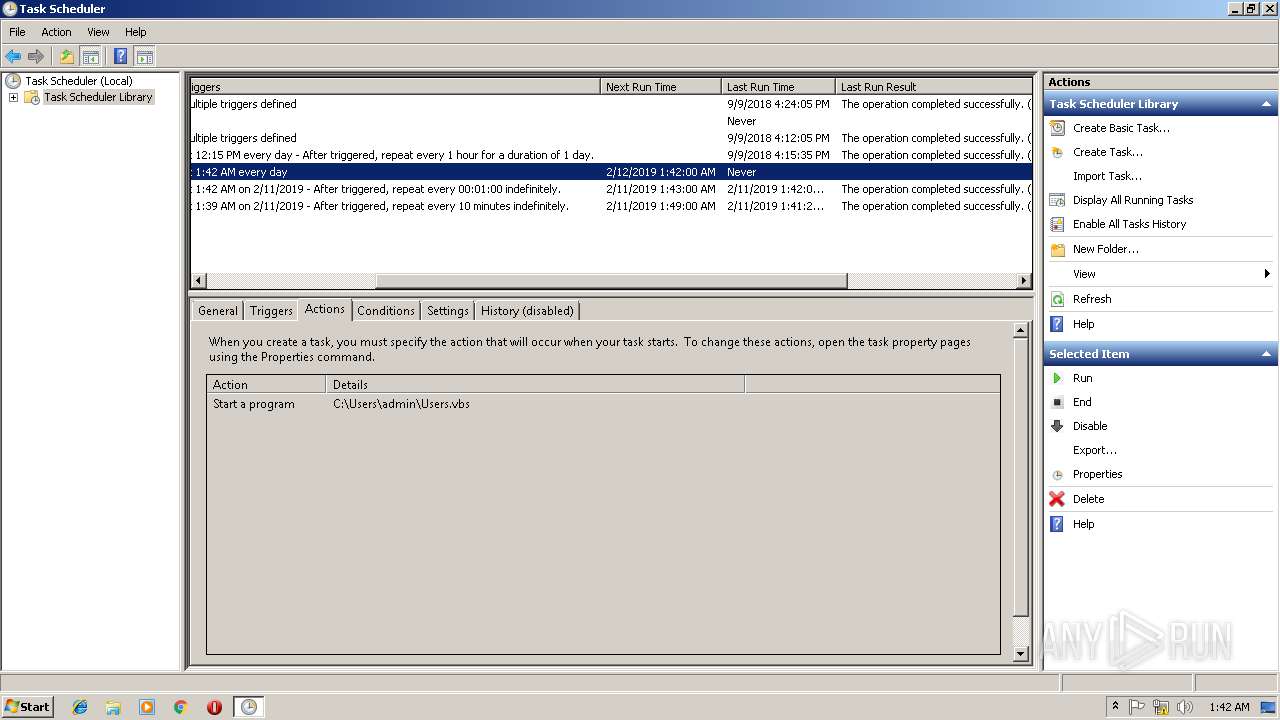
Loads the Task Scheduler COM API
- mmc.exe (PID: 3536)
- Schtasks.exe (PID: 2868)
- schtasks.exe (PID: 2656)
- schtasks.exe (PID: 2328)
- schtasks.exe (PID: 2860)
- schtasks.exe (PID: 2344)
- schtasks.exe (PID: 1360)
- schtasks.exe (PID: 2396)
- schtasks.exe (PID: 1244)
- schtasks.exe (PID: 3468)
- schtasks.exe (PID: 3280)
- schtasks.exe (PID: 3092)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 2764)
Changes settings of System certificates
- WScript.exe (PID: 3836)
- WScript.exe (PID: 2812)
- WScript.exe (PID: 3976)
- WScript.exe (PID: 3072)
- WScript.exe (PID: 2408)
SUSPICIOUS
Unusual connect from Microsoft Office
- EXCEL.EXE (PID: 2764)
Adds / modifies Windows certificates
- WScript.exe (PID: 3836)
- WScript.exe (PID: 2812)
- WScript.exe (PID: 3976)
- WScript.exe (PID: 3072)
- WScript.exe (PID: 2408)
Application launched itself
- WScript.exe (PID: 3836)
- WScript.exe (PID: 2812)
- WScript.exe (PID: 3976)
- WScript.exe (PID: 3072)
- WScript.exe (PID: 2408)
Executes scripts
- WScript.exe (PID: 3836)
- WScript.exe (PID: 2812)
- WScript.exe (PID: 3976)
- WScript.exe (PID: 3072)
- WScript.exe (PID: 2408)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2764)
Creates files in the user directory
- EXCEL.EXE (PID: 2764)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xlsm | | | Excel Microsoft Office Open XML Format document (with Macro) (50.8) |
|---|---|---|
| .xlsx | | | Excel Microsoft Office Open XML Format document (30) |
| .zip | | | Open Packaging Conventions container (15.4) |
| .zip | | | ZIP compressed archive (3.5) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0xbc04c63e |
| ZipCompressedSize: | 371 |
| ZipUncompressedSize: | 1087 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | ://tiny |
|---|---|
| Creator: | http |
XML
| LastModifiedBy: | http |
|---|---|
| CreateDate: | 2018:01:04 06:59:16Z |
| ModifyDate: | 2018:10:23 08:11:36Z |
| Application: | Microsoft Excel |
| DocSecurity: | None |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | Sheet1 |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 12 |
Total processes
74
Monitored processes
25
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1228 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\qThbhtQ.vbs" | C:\Windows\System32\WScript.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
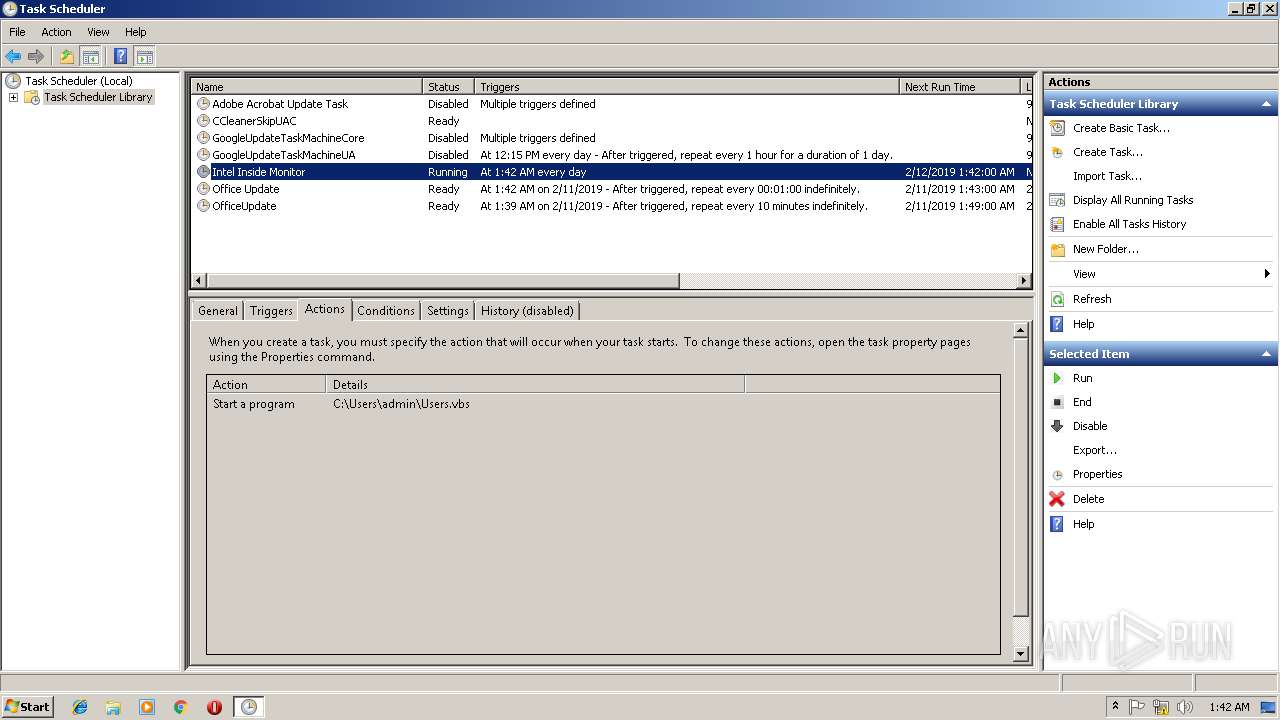
| 1244 | "C:\Windows\System32\schtasks.exe" /Create /SC daily /TN "Intel Inside Monitor" /TR C:\Users\admin\Users.vbs /F | C:\Windows\System32\schtasks.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1360 | "C:\Windows\System32\schtasks.exe" /Create /SC daily /TN "Intel Inside Monitor" /TR C:\Users\admin\Users.vbs /F | C:\Windows\System32\schtasks.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1920 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\B0@WdNF.vbs" | C:\Windows\System32\WScript.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1972 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\xJ&Fyca.vbs" | C:\Windows\System32\WScript.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
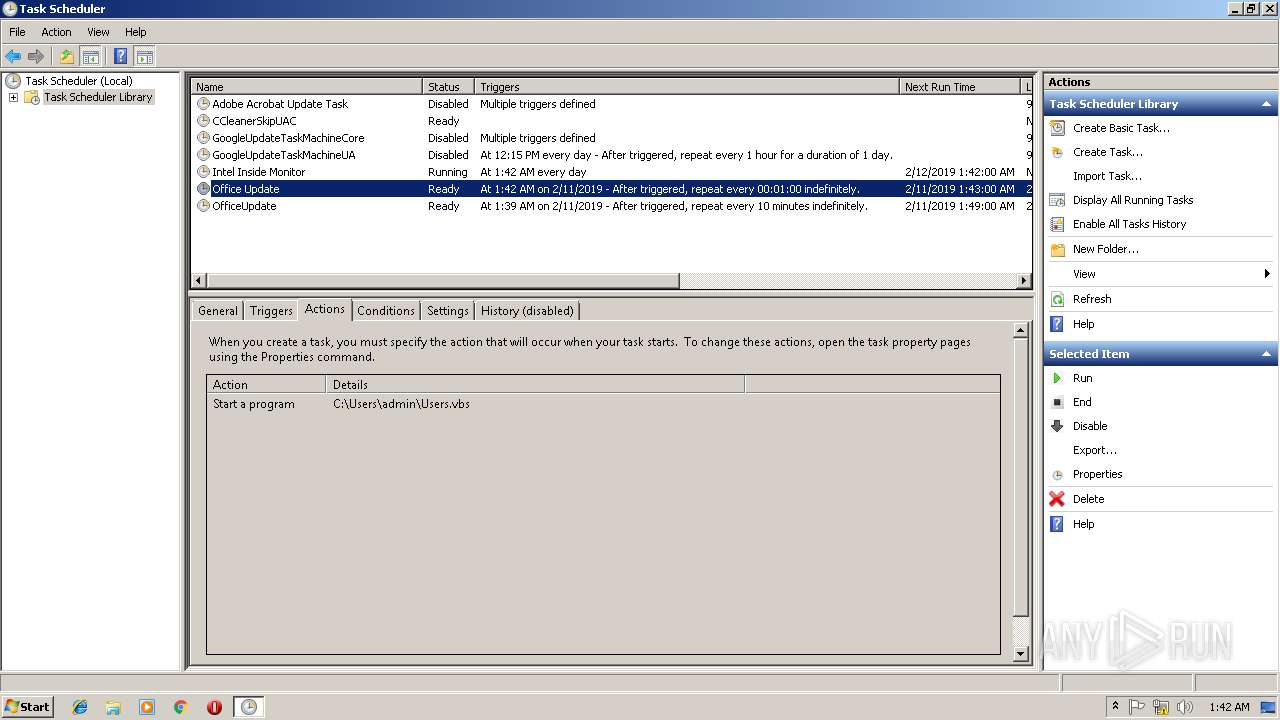
| 2328 | "C:\Windows\System32\schtasks.exe" /Create /SC minute /mo 1 /TN "Office Update" /TR C:\Users\admin\Users.vbs /F | C:\Windows\System32\schtasks.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2344 | "C:\Windows\System32\schtasks.exe" /Create /SC daily /TN "Intel Inside Monitor" /TR C:\Users\admin\Users.vbs /F | C:\Windows\System32\schtasks.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2396 | "C:\Windows\System32\schtasks.exe" /Create /SC minute /mo 1 /TN "Office Update" /TR C:\Users\admin\Users.vbs /F | C:\Windows\System32\schtasks.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2408 | C:\Windows\System32\WScript.exe "C:\Users\admin\Users.vbs" | C:\Windows\System32\WScript.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2656 | "C:\Windows\System32\schtasks.exe" /Create /SC minute /mo 1 /TN "Office Update" /TR C:\Users\admin\Users.vbs /F | C:\Windows\System32\schtasks.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 951
Read events
2 791
Write events
143
Delete events
17
Modification events
| (PID) Process: | (2764) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | n{$ |
Value: 6E7B2400CC0A0000010000000000000000000000 | |||
| (PID) Process: | (2764) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2764) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2764) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: CC0A0000184C89A2AAC1D40100000000 | |||
| (PID) Process: | (2764) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | n{$ |
Value: 6E7B2400CC0A0000010000000000000000000000 | |||
| (PID) Process: | (2764) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2764) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2764) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2764) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2764) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\DocumentRecovery\1993BB |
| Operation: | write | Name: | 1993BB |
Value: 04000000CC0A00002200000043003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070005C007300670076003700710069002E0078006C0073006D00000000001700000043003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070005C0001000000000000000041BEA4AAC1D401BB931900BB93190000000000AC020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
0
Text files
9
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2764 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR8B00.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2764 | EXCEL.EXE | C:\Users\admin\Desktop\~$sgv7qi.xlsm | — | |
MD5:— | SHA256:— | |||
| 2764 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF6F32628CDB46434B.TMP | — | |
MD5:— | SHA256:— | |||
| 3836 | WScript.exe | C:\Users\admin\qThbhtQ.vbs | text | |
MD5:— | SHA256:— | |||
| 2812 | WScript.exe | C:\Users\admin\P7Nut57.vbs | text | |
MD5:— | SHA256:— | |||
| 2764 | EXCEL.EXE | C:\Users\admin\Users.vbs | text | |
MD5:— | SHA256:— | |||
| 2764 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\sgv7qi.xlsm.LNK | lnk | |
MD5:— | SHA256:— | |||
| 3976 | WScript.exe | C:\Users\admin\B0@WdNF.vbs | text | |
MD5:— | SHA256:— | |||
| 2408 | WScript.exe | C:\Users\admin\xJ&Fyca.vbs | text | |
MD5:— | SHA256:— | |||
| 3072 | WScript.exe | C:\Users\admin\pVaxlje.vbs | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
18
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2764 | EXCEL.EXE | GET | 301 | 192.241.240.89:80 | http://tiny.cc/ccddc | US | html | 184 b | malicious |
3836 | WScript.exe | GET | 301 | 192.241.240.89:80 | http://tiny.cc/gogoo | US | html | 184 b | malicious |
2764 | EXCEL.EXE | GET | 301 | 192.241.240.89:80 | http://tiny.cc/zzttzz | US | html | 184 b | malicious |
2812 | WScript.exe | GET | 301 | 192.241.240.89:80 | http://tiny.cc/gogoo | US | html | 184 b | malicious |
3976 | WScript.exe | GET | 301 | 192.241.240.89:80 | http://tiny.cc/gogoo | US | html | 184 b | malicious |
3072 | WScript.exe | GET | 301 | 192.241.240.89:80 | http://tiny.cc/gogoo | US | html | 184 b | malicious |
2408 | WScript.exe | GET | 301 | 192.241.240.89:80 | http://tiny.cc/gogoo | US | html | 184 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2764 | EXCEL.EXE | 192.241.240.89:80 | tiny.cc | Digital Ocean, Inc. | US | malicious |
2764 | EXCEL.EXE | 192.241.240.89:443 | tiny.cc | Digital Ocean, Inc. | US | malicious |
2764 | EXCEL.EXE | 104.20.209.21:443 | pastebin.com | Cloudflare Inc | US | shared |
3836 | WScript.exe | 192.241.240.89:80 | tiny.cc | Digital Ocean, Inc. | US | malicious |
3836 | WScript.exe | 192.241.240.89:443 | tiny.cc | Digital Ocean, Inc. | US | malicious |
3836 | WScript.exe | 104.20.209.21:443 | pastebin.com | Cloudflare Inc | US | shared |
2812 | WScript.exe | 192.241.240.89:80 | tiny.cc | Digital Ocean, Inc. | US | malicious |
2812 | WScript.exe | 192.241.240.89:443 | tiny.cc | Digital Ocean, Inc. | US | malicious |
2812 | WScript.exe | 104.20.209.21:443 | pastebin.com | Cloudflare Inc | US | shared |
3976 | WScript.exe | 192.241.240.89:80 | tiny.cc | Digital Ocean, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
tiny.cc |
| malicious |
pastebin.com |
| malicious |
Threats
Process | Message |
|---|---|
mmc.exe | Constructor: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | OnInitialize: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | ProcessCommandLineArguments: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|