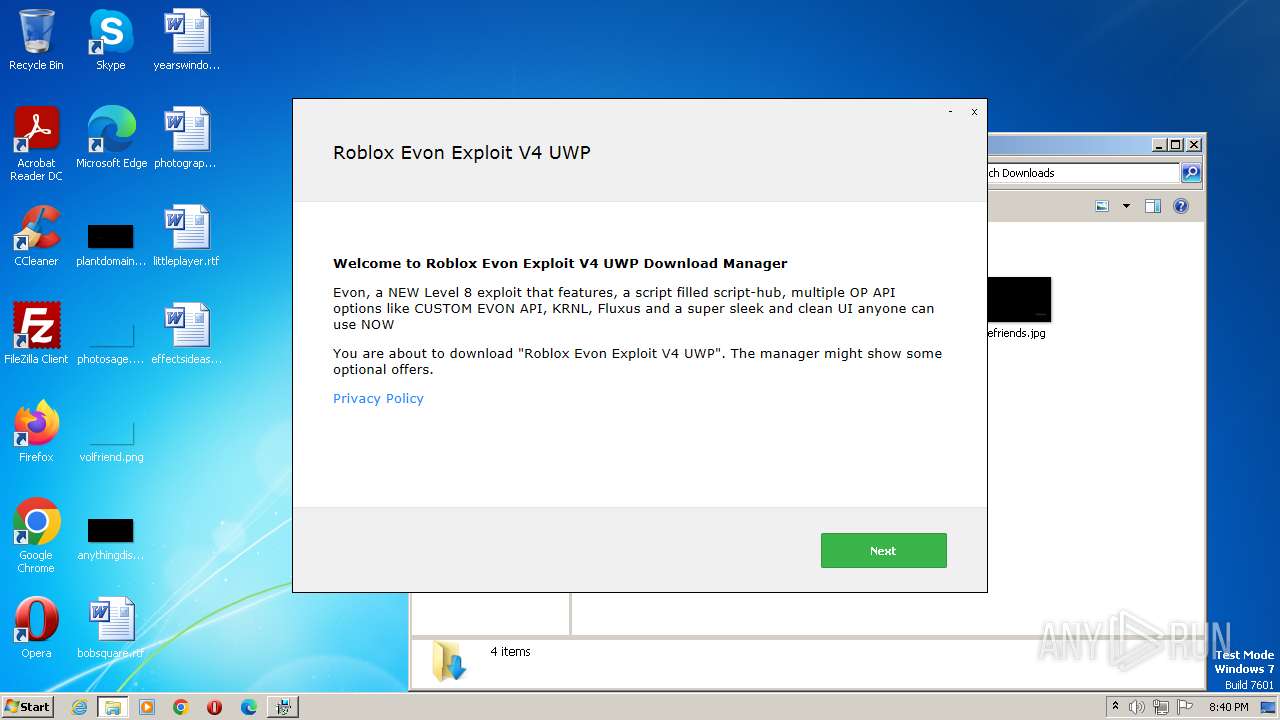
| File name: | Roblox Evon Exploit V4 UWP_23165.exe |
| Full analysis: | https://app.any.run/tasks/b86a9eb4-2853-44b4-b9d3-1256157087a4 |
| Verdict: | Malicious activity |
| Analysis date: | August 10, 2023, 19:39:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C17F0EABABF0977481F7067199485572 |
| SHA1: | 8D4D518C4E3975B8F0862C45CD5BD7B6C049DC3D |
| SHA256: | 7809CC3FEE64EC6F087F6DAB5AC09F8830F79166DA639844FA439E1B6925E2F3 |
| SSDEEP: | 196608:FKQcLwTubhjhPrqNgWomQ3bKfIiaNPFHNRsiKWx1:FF+EuRdrqNloL3bIIiEHMnm1 |
MALICIOUS
Actions looks like stealing of personal data
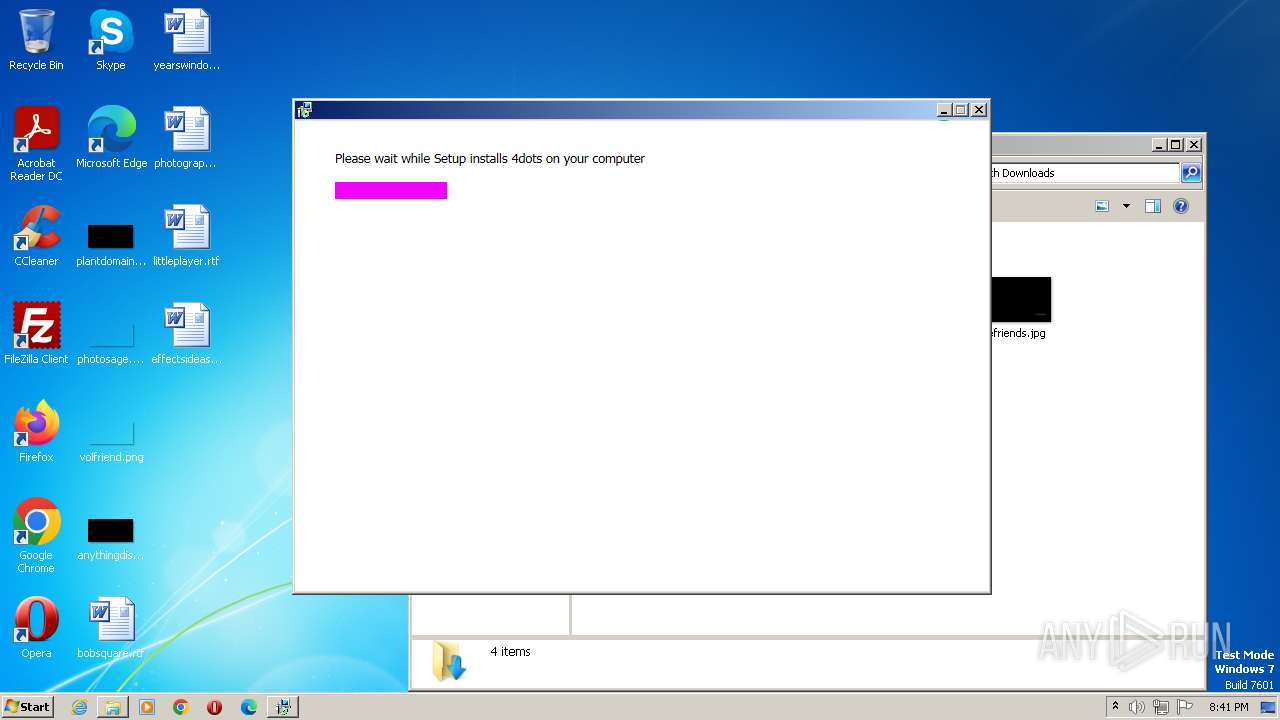
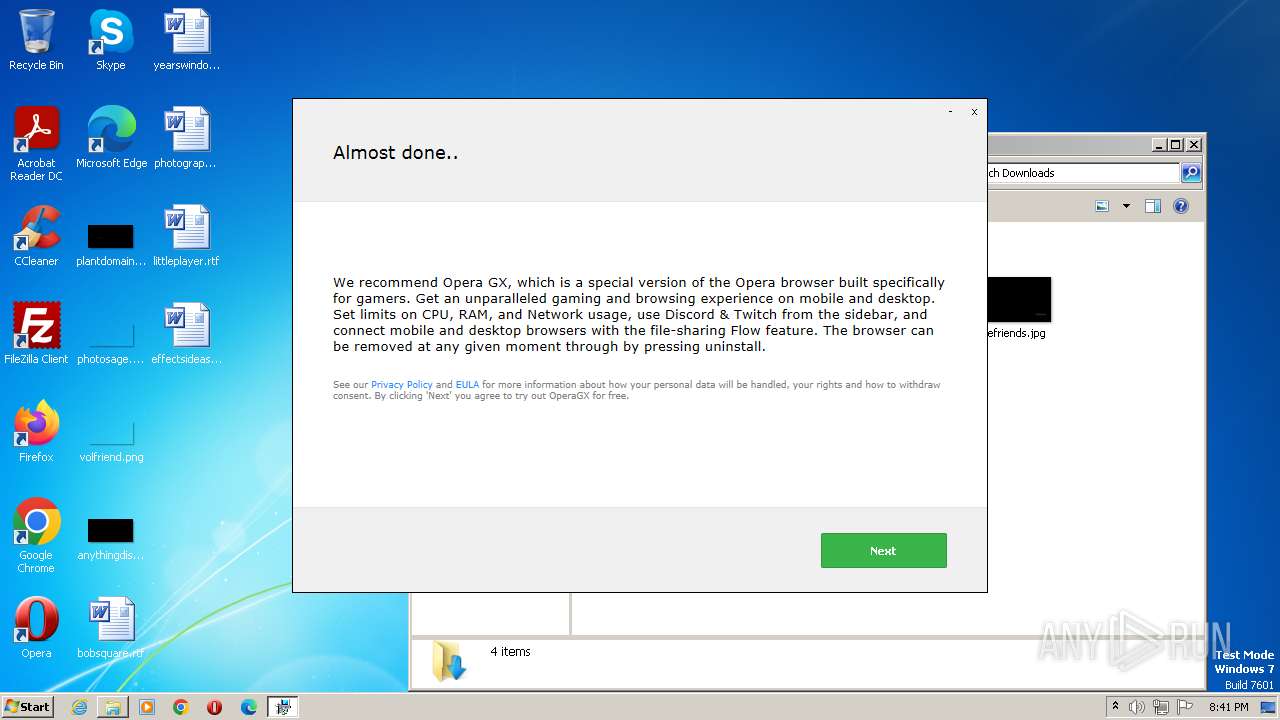
- setup23165.exe (PID: 3572)
- OfferInstaller.exe (PID: 3900)
Application was dropped or rewritten from another process
- setup23165.exe (PID: 3572)
- setup23165.exe (PID: 3212)
- OfferInstaller.exe (PID: 3900)
Loads dropped or rewritten executable
- setup23165.exe (PID: 3572)
- setup23165.exe (PID: 3212)
- OfferInstaller.exe (PID: 3900)
SUSPICIOUS
Reads the Internet Settings
- Roblox Evon Exploit V4 UWP_23165.exe (PID: 2696)
- setup23165.exe (PID: 3572)
- setup23165.exe (PID: 3212)
- OfferInstaller.exe (PID: 3900)
Reads the Windows owner or organization settings
- setup23165.exe (PID: 3572)
- OfferInstaller.exe (PID: 3900)
Reads security settings of Internet Explorer
- setup23165.exe (PID: 3572)
- Roblox Evon Exploit V4 UWP_23165.exe (PID: 2696)
Executable content was dropped or overwritten
- Roblox Evon Exploit V4 UWP_23165.exe (PID: 2696)
- setup23165.exe (PID: 3572)
Checks Windows Trust Settings
- setup23165.exe (PID: 3572)
- Roblox Evon Exploit V4 UWP_23165.exe (PID: 2696)
Reads settings of System Certificates
- setup23165.exe (PID: 3572)
- Roblox Evon Exploit V4 UWP_23165.exe (PID: 2696)
- OfferInstaller.exe (PID: 3900)
Adds/modifies Windows certificates
- Roblox Evon Exploit V4 UWP_23165.exe (PID: 2696)
Searches for installed software
- setup23165.exe (PID: 3572)
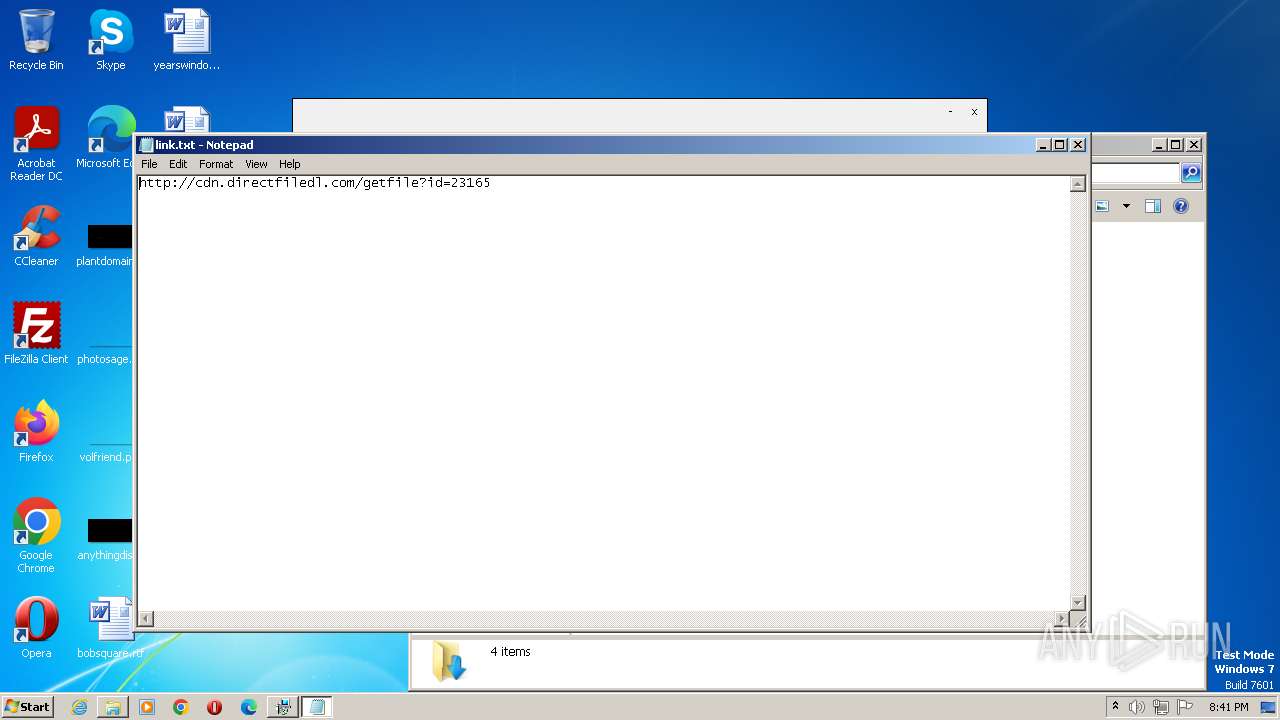
Start notepad (likely ransomware note)
- Roblox Evon Exploit V4 UWP_23165.exe (PID: 2696)
Executing commands from a ".bat" file
- OfferInstaller.exe (PID: 3900)
- setup23165.exe (PID: 3572)
Starts CMD.EXE for commands execution
- OfferInstaller.exe (PID: 3900)
- setup23165.exe (PID: 3572)
Get information on the list of running processes
- cmd.exe (PID: 1604)
- cmd.exe (PID: 2288)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 1604)
- cmd.exe (PID: 2288)
INFO
Reads the computer name
- Roblox Evon Exploit V4 UWP_23165.exe (PID: 2696)
- setup23165.exe (PID: 3572)
- setup23165.exe (PID: 3212)
- OfferInstaller.exe (PID: 3900)
- wmpnscfg.exe (PID: 1208)
Checks proxy server information
- Roblox Evon Exploit V4 UWP_23165.exe (PID: 2696)
Creates files or folders in the user directory
- Roblox Evon Exploit V4 UWP_23165.exe (PID: 2696)
- setup23165.exe (PID: 3572)
- OfferInstaller.exe (PID: 3900)
Checks supported languages
- Roblox Evon Exploit V4 UWP_23165.exe (PID: 2696)
- setup23165.exe (PID: 3572)
- setup23165.exe (PID: 3212)
- OfferInstaller.exe (PID: 3900)
- wmpnscfg.exe (PID: 1208)
The process checks LSA protection
- Roblox Evon Exploit V4 UWP_23165.exe (PID: 2696)
- setup23165.exe (PID: 3572)
- explorer.exe (PID: 2580)
- setup23165.exe (PID: 3212)
- OfferInstaller.exe (PID: 3900)
- tasklist.exe (PID: 3228)
- tasklist.exe (PID: 476)
- tasklist.exe (PID: 2448)
- tasklist.exe (PID: 2160)
- wmpnscfg.exe (PID: 1208)
Reads Environment values
- setup23165.exe (PID: 3572)
- OfferInstaller.exe (PID: 3900)
Reads the machine GUID from the registry
- Roblox Evon Exploit V4 UWP_23165.exe (PID: 2696)
- setup23165.exe (PID: 3572)
- setup23165.exe (PID: 3212)
- OfferInstaller.exe (PID: 3900)
- wmpnscfg.exe (PID: 1208)
Manual execution by a user
- explorer.exe (PID: 2580)
- wmpnscfg.exe (PID: 1208)
- iexplore.exe (PID: 3912)
Reads product name
- setup23165.exe (PID: 3572)
- OfferInstaller.exe (PID: 3900)
Create files in a temporary directory
- setup23165.exe (PID: 3212)
- Roblox Evon Exploit V4 UWP_23165.exe (PID: 2696)
- setup23165.exe (PID: 3572)
- OfferInstaller.exe (PID: 3900)
Application launched itself
- iexplore.exe (PID: 3912)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 6 |
| ImageVersion: | - |
| OSVersion: | 6 |
| EntryPoint: | 0x3814b7 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 5623296 |
| CodeSize: | 4243968 |
| LinkerVersion: | 14.22 |
| PEType: | PE32 |
| ImageFileCharacteristics: | Executable, 32-bit |
| TimeStamp: | 2023:08:08 07:37:13+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 08-Aug-2023 07:37:13 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000128 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 08-Aug-2023 07:37:13 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0040C09B | 0x0040C200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.64613 |
.rdata | 0x0040E000 | 0x000F9C20 | 0x000F9E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.51436 |
.data | 0x00508000 | 0x0002A0E8 | 0x00023E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.82581 |
.rsrc | 0x00533000 | 0x003EE488 | 0x003EE600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.97976 |
.reloc | 0x00922000 | 0x0004A738 | 0x0004A800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.59023 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.04264 | 562 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 2.73071 | 67624 | UNKNOWN | Dutch - Netherlands | RT_ICON |
3 | 2.77417 | 16936 | UNKNOWN | Dutch - Netherlands | RT_ICON |
4 | 3.65334 | 9640 | UNKNOWN | Dutch - Netherlands | RT_ICON |
5 | 2.82974 | 4264 | UNKNOWN | Dutch - Netherlands | RT_ICON |
6 | 4.49114 | 1128 | UNKNOWN | Dutch - Netherlands | RT_ICON |
101 | 7.99934 | 4018880 | UNKNOWN | Dutch - Netherlands | RT_RCDATA |
103 | 2.75463 | 90 | UNKNOWN | Dutch - Netherlands | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
COMDLG32.dll |
GDI32.dll |
IMM32.dll |
KERNEL32.dll |
OLEACC.dll |
OLEAUT32.dll |
SHELL32.dll |
USER32.dll |
Total processes
68
Monitored processes
24
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 476 | tasklist /FI "PID eq 3900" /fo csv | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1036 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\link.txt | C:\Windows\System32\notepad.exe | — | Roblox Evon Exploit V4 UWP_23165.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1208 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1556 | timeout 1 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1604 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\H2OCleanup.bat"" | C:\Windows\System32\cmd.exe | — | setup23165.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2096 | find /I "3900" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2160 | tasklist /FI "PID eq 3572" /fo csv | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2288 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\H2OCleanup.bat"" | C:\Windows\System32\cmd.exe | — | OfferInstaller.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2368 | find /I "3572" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2448 | tasklist /FI "PID eq 3900" /fo csv | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
21 063
Read events
20 858
Write events
202
Delete events
3
Modification events
| (PID) Process: | (2696) Roblox Evon Exploit V4 UWP_23165.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2696) Roblox Evon Exploit V4 UWP_23165.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000004F010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2696) Roblox Evon Exploit V4 UWP_23165.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2696) Roblox Evon Exploit V4 UWP_23165.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2696) Roblox Evon Exploit V4 UWP_23165.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2696) Roblox Evon Exploit V4 UWP_23165.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2696) Roblox Evon Exploit V4 UWP_23165.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2696) Roblox Evon Exploit V4 UWP_23165.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3572) setup23165.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Session Manager |
| Operation: | write | Name: | PendingFileRenameOperations |
Value: \??\C:\Users\admin\AppData\Local\Temp\ec05d89197b949eb6957b79472e8723d\ServiceHide.dll | |||
| (PID) Process: | (3572) setup23165.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
23
Suspicious files
12
Text files
33
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3572 | setup23165.exe | C:\Users\admin\AppData\Local\Temp\ec05d89197b949eb6957b79472e8723d\ServiceHide.dll | executable | |
MD5:72990C7E32EE6C811EA3D2EA64523234 | SHA256:E77E0B4F2762F76A3EAAADF5A3138A35EC06ECE80EDC4B3396DE7A601F8DA1B3 | |||
| 3572 | setup23165.exe | C:\Users\admin\AppData\Local\Temp\ec05d89197b949eb6957b79472e8723d\GenericSetup.LastScreen.dll | executable | |
MD5:6E001F8D0EE4F09A6673A9E8168836B6 | SHA256:6A30F9C604C4012D1D2E1BA075213C378AFB1BFCB94276DE7995ED7BBF492859 | |||
| 3572 | setup23165.exe | C:\Users\admin\AppData\Local\Temp\ec05d89197b949eb6957b79472e8723d\GenericSetup.dll | executable | |
MD5:08112F27DCD8F1D779231A7A3E944CB1 | SHA256:11C6A8470A3F2B2BE9B8CAFE5F9A0AFCE7303BFD02AB783A0F0EE09A184649FA | |||
| 3572 | setup23165.exe | C:\Users\admin\AppData\Local\Temp\ec05d89197b949eb6957b79472e8723d\H2OServices.dll | executable | |
MD5:6DF226BDA27D26CE4523B80DBF57A9EA | SHA256:17D737175D50EEE97AC1C77DB415FE25CC3C7A3871B65B93CC3FAD63808A9ABC | |||
| 3572 | setup23165.exe | C:\Users\admin\AppData\Local\Temp\ec05d89197b949eb6957b79472e8723d\HtmlAgilityPack.dll | executable | |
MD5:17220F65BD242B6A491423D5BB7940C1 | SHA256:23056F14EDB6E0AFC70224D65DE272A710B5D26E6C3B9FE2DFD022073050C59F | |||
| 3572 | setup23165.exe | C:\Users\admin\AppData\Local\Temp\ec05d89197b949eb6957b79472e8723d\SciterWrapper.dll | executable | |
MD5:105A9E404F7AC841C46380063CC27F50 | SHA256:69FE749457218EC9A765F9AAC74CAF6D4F73084CF5175D3FD1E4F345AF8B3B8B | |||
| 3572 | setup23165.exe | C:\Users\admin\AppData\Local\Temp\ec05d89197b949eb6957b79472e8723d\OfferSDK.dll | executable | |
MD5:B199DCD6824A02522A4D29A69AB65058 | SHA256:9310A58F26BE8BD453CDE5CA6AA05042942832711FBDEB5430A2840232BFA5E4 | |||
| 2696 | Roblox Evon Exploit V4 UWP_23165.exe | C:\Users\admin\AppData\Local\setup23165.exe | executable | |
MD5:29D3A70CEC060614E1691E64162A6C1E | SHA256:CC70B093A19610E9752794D757AEC9EF07CA862EA9267EC6F9CC92B2AA882C72 | |||
| 3572 | setup23165.exe | C:\Users\admin\AppData\Local\Temp\ec05d89197b949eb6957b79472e8723d\vcruntime140.dll | executable | |
MD5:1A84957B6E681FCA057160CD04E26B27 | SHA256:9FAEAA45E8CC986AF56F28350B38238B03C01C355E9564B849604B8D690919C5 | |||
| 3572 | setup23165.exe | C:\Users\admin\AppData\Local\Temp\ec05d89197b949eb6957b79472e8723d\H2OUtilities.dll | executable | |
MD5:9D2C520BFA294A6AA0C5CBC6D87CAEEC | SHA256:669C812CB8F09799083014A199B0DEEE10237C95FB49EE107376B952FEE5BD89 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
57
DNS requests
27
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2696 | Roblox Evon Exploit V4 UWP_23165.exe | GET | 200 | 35.190.60.70:80 | http://dlsft.com/callback/info.php?id=23165 | US | text | 234 b | malicious |
2696 | Roblox Evon Exploit V4 UWP_23165.exe | POST | 200 | 35.190.60.70:80 | http://dlsft.com/callback/?channel=lLt76&id=23165&action=started | US | text | 17 b | malicious |
3912 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | US | der | 471 b | whitelisted |
2696 | Roblox Evon Exploit V4 UWP_23165.exe | GET | 200 | 23.37.41.57:80 | http://x1.c.lencr.org/ | NL | binary | 717 b | whitelisted |
3912 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | binary | 1.47 Kb | whitelisted |
2696 | Roblox Evon Exploit V4 UWP_23165.exe | GET | 200 | 35.190.60.70:80 | http://dlsft.com/callback/offers.php | US | text | 17 b | malicious |
2696 | Roblox Evon Exploit V4 UWP_23165.exe | POST | 200 | 35.190.60.70:80 | http://dlsft.com/callback/?channel=lLt76&id=23165&action=operagx-Shown | US | text | 17 b | malicious |
2696 | Roblox Evon Exploit V4 UWP_23165.exe | GET | 200 | 67.27.159.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?99f8e90799ad9ea9 | US | compressed | 4.70 Kb | whitelisted |
2696 | Roblox Evon Exploit V4 UWP_23165.exe | GET | 200 | 67.27.159.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?8d57730f56edc8c6 | US | compressed | 62.3 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2696 | Roblox Evon Exploit V4 UWP_23165.exe | 35.190.60.70:443 | www.dlsft.com | GOOGLE | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3572 | setup23165.exe | 104.17.8.52:443 | flow.lavasoft.com | CLOUDFLARENET | — | shared |
3900 | OfferInstaller.exe | 104.17.8.52:443 | flow.lavasoft.com | CLOUDFLARENET | — | shared |
3572 | setup23165.exe | 104.18.67.73:443 | sos.adaware.com | CLOUDFLARENET | — | whitelisted |
2696 | Roblox Evon Exploit V4 UWP_23165.exe | 35.190.60.70:80 | www.dlsft.com | GOOGLE | US | whitelisted |
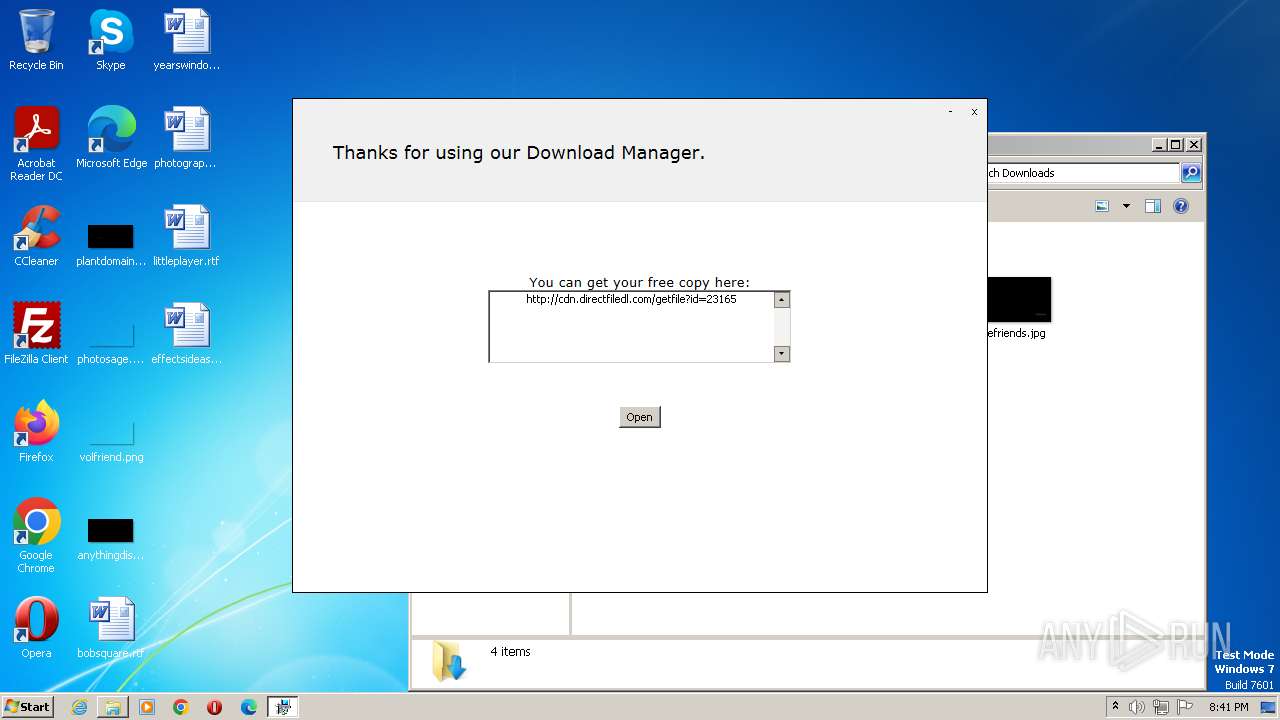
2696 | Roblox Evon Exploit V4 UWP_23165.exe | 188.114.97.3:443 | filedm.com | CLOUDFLARENET | NL | malicious |
3572 | setup23165.exe | 104.18.68.73:443 | sos.adaware.com | CLOUDFLARENET | — | whitelisted |
2696 | Roblox Evon Exploit V4 UWP_23165.exe | 104.21.12.132:443 | www.biphic.com | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.dlsft.com |
| malicious |
dns.msftncsi.com |
| shared |
www.google.com |
| malicious |
flow.lavasoft.com |
| whitelisted |
sos.adaware.com |
| whitelisted |
dlsft.com |
| malicious |
filedm.com |
| malicious |
sdl.adaware.com |
| whitelisted |
www.biphic.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
Threats
6 ETPRO signatures available at the full report
Process | Message |
|---|---|
setup23165.exe | |
setup23165.exe | Error: File not found - sciterwrapper:console.tis
|
setup23165.exe | at sciter:init-script.tis
|
setup23165.exe | |
setup23165.exe | file:resources/tis/TranslateOfferTemplate.tis(82) : warning :'async' does not contain any 'await'
|
setup23165.exe | |
setup23165.exe | Error: File not found - sciterwrapper:console.tis
|
setup23165.exe | at sciter:init-script.tis
|
setup23165.exe | |
setup23165.exe | file:resources/tis/TranslateOfferTemplate.tis(82) : warning :'async' does not contain any 'await'
|