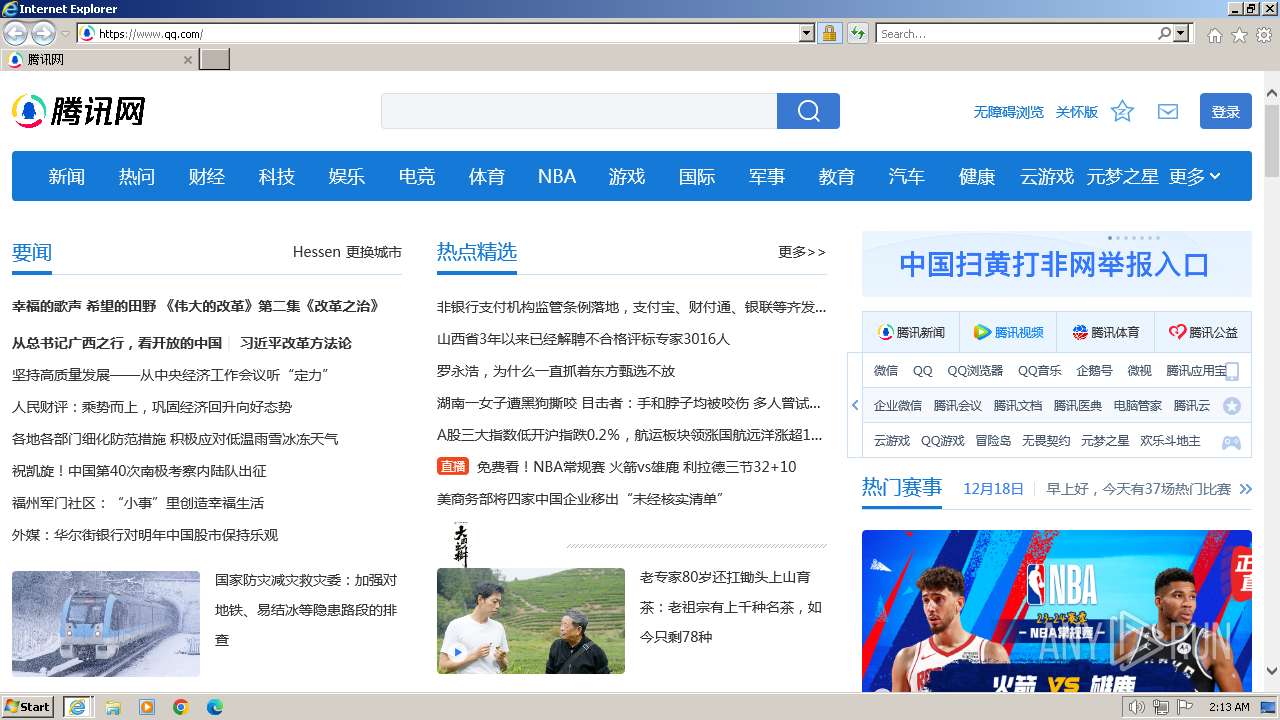
| URL: | qq.com |
| Full analysis: | https://app.any.run/tasks/f7887821-7ed3-4bdd-886c-5fc72877313a |
| Verdict: | Malicious activity |
| Analysis date: | December 18, 2023, 02:12:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | AB735A258A90E8E1F3E3DCF231BF53A9 |
| SHA1: | EA96376E64DC86683C64E7284EF032D3CF654FFC |
| SHA256: | 77F3E4BCA5E8A0BE07CF5AD6C4D2F4BFF369C458965E6767F59D4A5AA7EDFE7C |
| SSDEEP: | 3:NLGT:ZK |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 2040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1056 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2040 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2040 | "C:\Program Files\Internet Explorer\iexplore.exe" "qq.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2332 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2040 CREDAT:2037003 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
25 063
Read events
24 974
Write events
87
Delete events
2
Modification events
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
67
Text files
191
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1056 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 1056 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:A4DCE45335A6B252FA35FF184730BB46 | SHA256:6BDF3F14DFD57B35195568F0947976FC4993B09B36A0A41D65230C85D24F1DFA | |||
| 1056 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:04239C03B37772CD7FA638236626FF49 | SHA256:859DFB0C86ED5048F95506DB0DC0028660CF7D16CEFECDE035589CDE25F83B16 | |||
| 1056 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CF14D1855652602540DFCFECD21854DB_4CBB9675BC1B0A9532841D0EFEA0E99C | binary | |
MD5:6291FE063CE69BCAE777B00CC6DF1E08 | SHA256:85D4568B3DE9D13EE9438F97DE3C605813F7574629B2DAFFC7549E4583203BC9 | |||
| 1056 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\0[1].png | image | |
MD5:F3EDD999B89CCF1595D0B3015CF7981E | SHA256:D5772765312FBFCA46740F16B04F73ADB893F3C32B89A6D626B9F61B9C00EBD9 | |||
| 1056 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:D29B8600016E5B155F44DEC08954FE0B | SHA256:42B3FF524F4E07D585745E8025D7053E57A5BD911AE93A3E364C66DF2EDE8BCC | |||
| 1056 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\0[2].png | image | |
MD5:EA0B1233737234D09096050F3D1D8D63 | SHA256:93E206E275FC147CFD003FD8E27F1B33E59FFDF33758B67D854079724EAA7EB4 | |||
| 1056 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\0[2].png | image | |
MD5:8F8960F2697F92D31FE1CD2208263258 | SHA256:EA00E3EBD79E5452693C383E232A271DA2FFA286C06A2F819B897F8C77608C24 | |||
| 1056 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\0[2].png | image | |
MD5:66D1AC0674AB82D0088588EA83607F9B | SHA256:E7FD3003680756897D554A6A051D0EC5CAA0B20E8A32DD7643FE521A12C8B6E0 | |||
| 1056 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CF14D1855652602540DFCFECD21854DB_4CBB9675BC1B0A9532841D0EFEA0E99C | binary | |
MD5:9FD7F177A642A583EA06A09F8638C1EE | SHA256:6F53D5562E5AEEB43BC3D7A3A504890986B7D7433C2E4F7E0C6C9D80F78AF0BE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
124
DNS requests
47
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1056 | iexplore.exe | GET | 302 | 123.150.76.218:80 | http://qq.com/ | unknown | html | 137 b | unknown |
1056 | iexplore.exe | GET | 200 | 95.101.54.105:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f6bf34dbb61e71d7 | unknown | compressed | 4.66 Kb | unknown |
1056 | iexplore.exe | GET | 200 | 95.101.54.105:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?608cb4ab6d3f68d3 | unknown | compressed | 4.66 Kb | unknown |
1056 | iexplore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/rootr1/ME8wTTBLMEkwRzAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDkcHsQGaDFetObPhfan5 | unknown | binary | 1.41 Kb | unknown |
1056 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
1056 | iexplore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp2.globalsign.com/gsorganizationvalsha2g3/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBSVLM6m9XSaK2pXyc357yFJVjgNwQQUaIa4fXrZbUlrhy8YixU0bNe0eg4CDFhZC0TmFhpZ3rvPJw%3D%3D | unknown | binary | 1.43 Kb | unknown |
1056 | iexplore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp2.globalsign.com/gsorganizationvalsha2g3/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBSVLM6m9XSaK2pXyc357yFJVjgNwQQUaIa4fXrZbUlrhy8YixU0bNe0eg4CDE6TRZ%2BnMqw1TZ6syg%3D%3D | unknown | binary | 1.43 Kb | unknown |
1056 | iexplore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp2.globalsign.com/gsorganizationvalsha2g3/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBSVLM6m9XSaK2pXyc357yFJVjgNwQQUaIa4fXrZbUlrhy8YixU0bNe0eg4CDHPbrB3tdu4CSPJD%2Bw%3D%3D | unknown | binary | 1.43 Kb | unknown |
1056 | iexplore.exe | GET | 200 | 163.181.56.215:80 | http://ocsp.digicert.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbJNRrm8KxusAb7DCqnMkE%3D | unknown | binary | 471 b | unknown |
1056 | iexplore.exe | GET | 200 | 163.181.56.215:80 | http://ocsp.digicert.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQhnxEBNL9LgIhfSsTcHsrTt204QgQURNnISjOO01KNp5KUYR%2BayKW37MsCEAfhftOntfrm58qtJ6JauOY%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1056 | iexplore.exe | 123.150.76.218:80 | qq.com | Tianjij,300000 | CN | unknown |
1056 | iexplore.exe | 23.196.244.121:443 | www.qq.com | AKAMAI-AS | DE | unknown |
1056 | iexplore.exe | 95.101.54.105:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1056 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1056 | iexplore.exe | 101.33.10.108:443 | mat1.gtimg.com | Tencent Building, Kejizhongyi Avenue | DE | unknown |
1056 | iexplore.exe | 104.18.21.226:80 | ocsp.globalsign.com | CLOUDFLARENET | — | shared |
1056 | iexplore.exe | 2.16.184.177:443 | inews.gtimg.com | AKAMAI-AS | DE | unknown |
1056 | iexplore.exe | 43.135.106.184:443 | pacaio.match.qq.com | Tencent Building, Kejizhongyi Avenue | HK | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
qq.com |
| malicious |
www.qq.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
pacaio.match.qq.com |
| whitelisted |
mat1.gtimg.com |
| whitelisted |
inews.gtimg.com |
| unknown |
vm.gtimg.cn |
| whitelisted |
imgcache.qq.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |