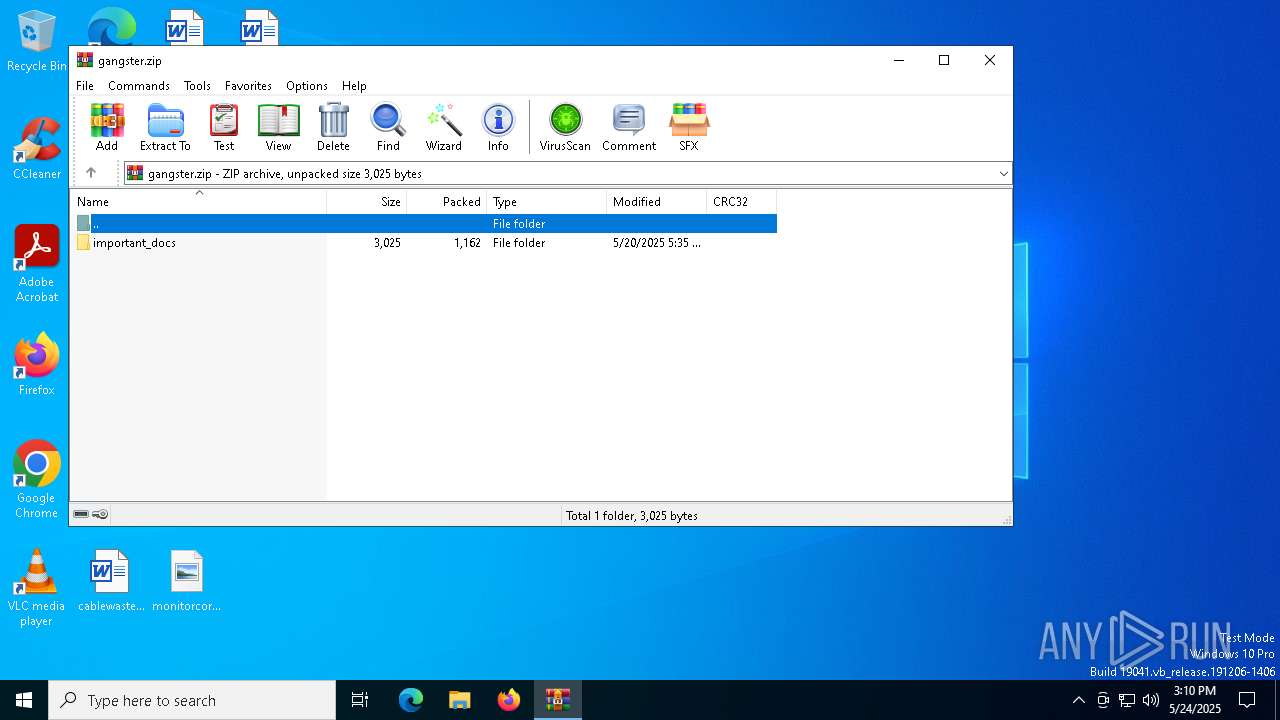
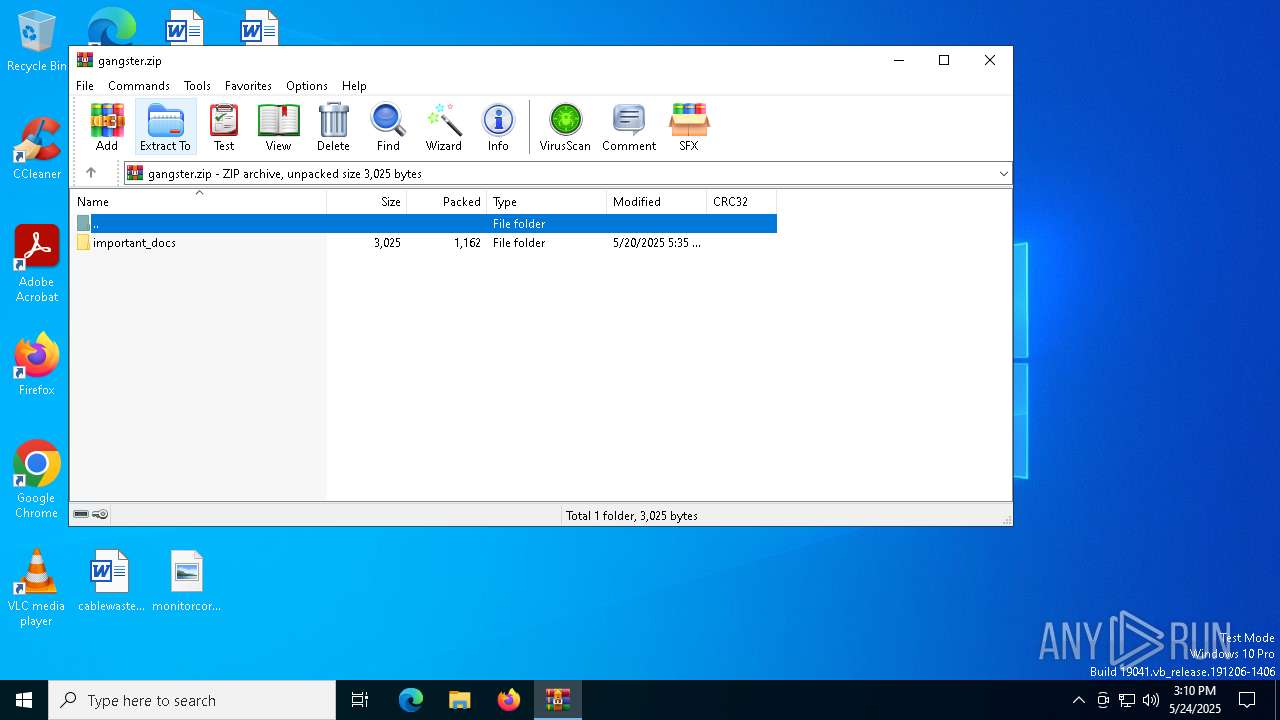
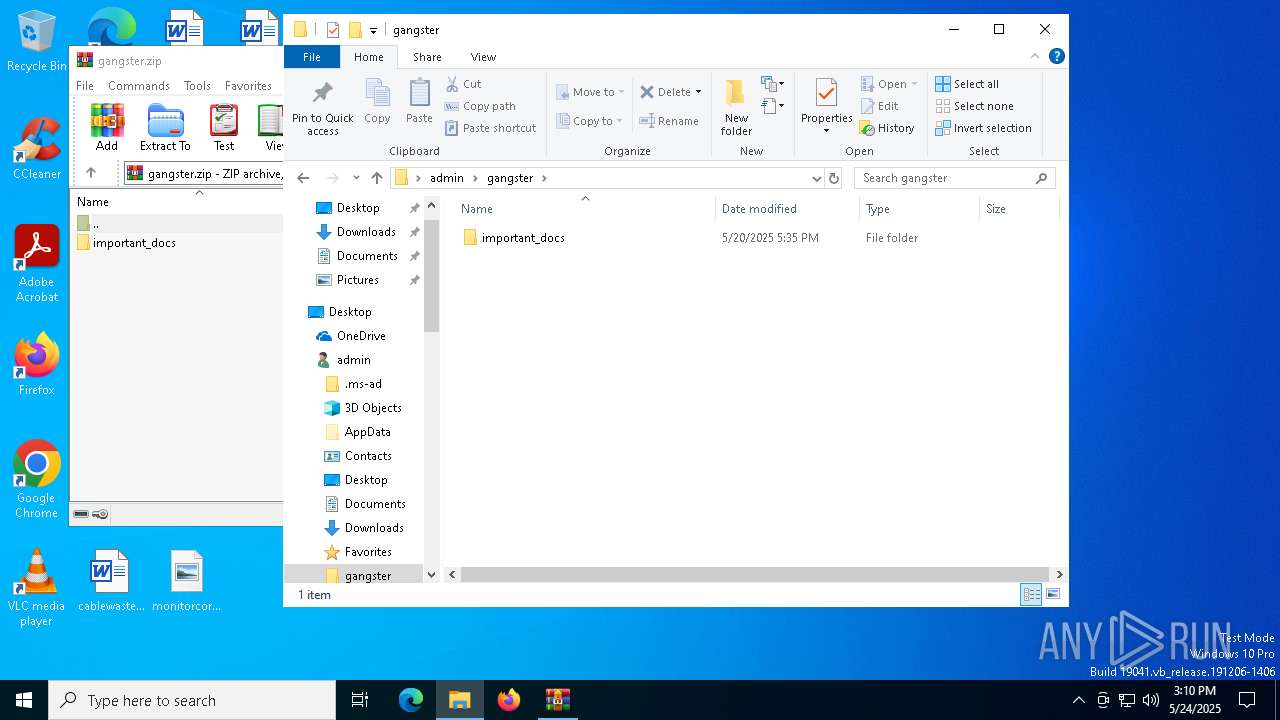
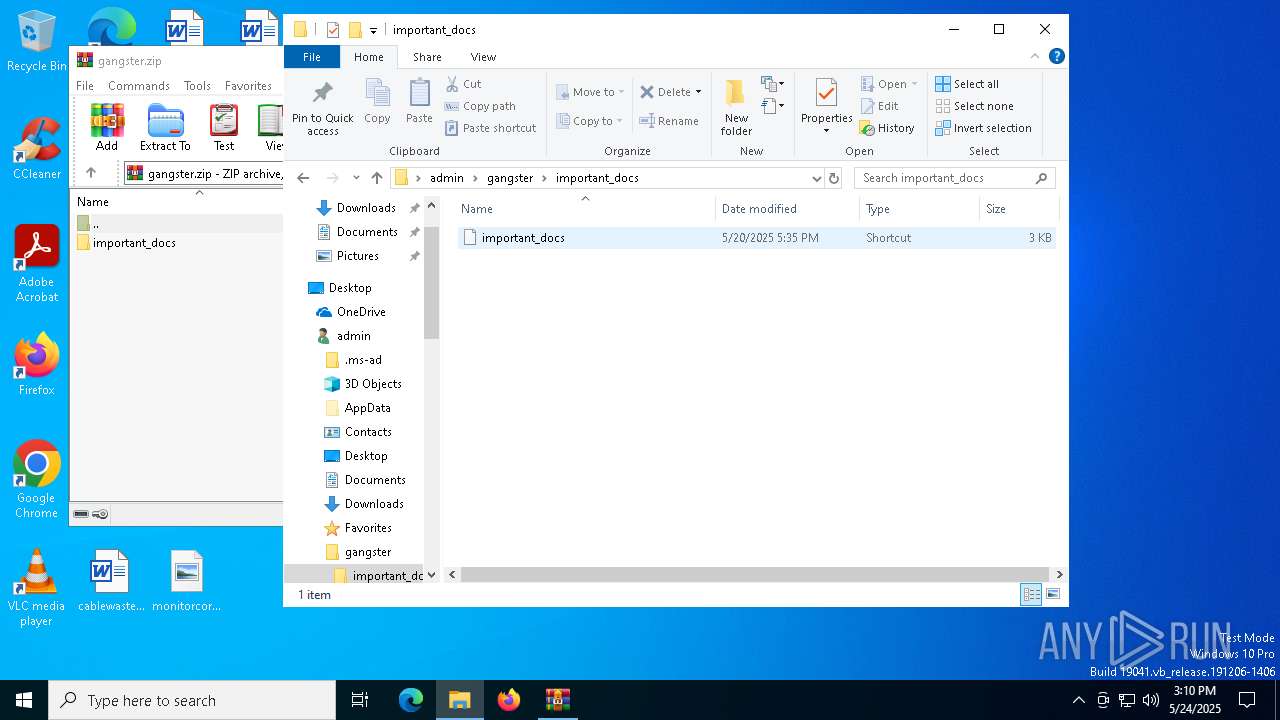
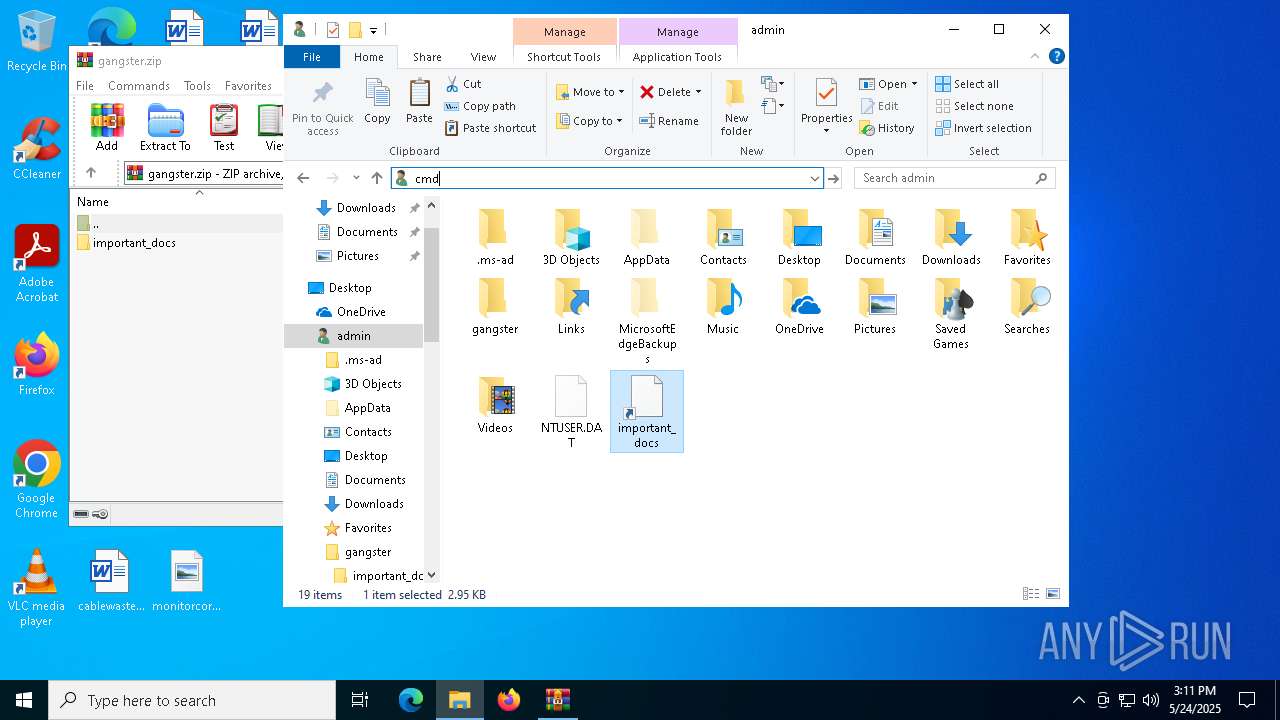
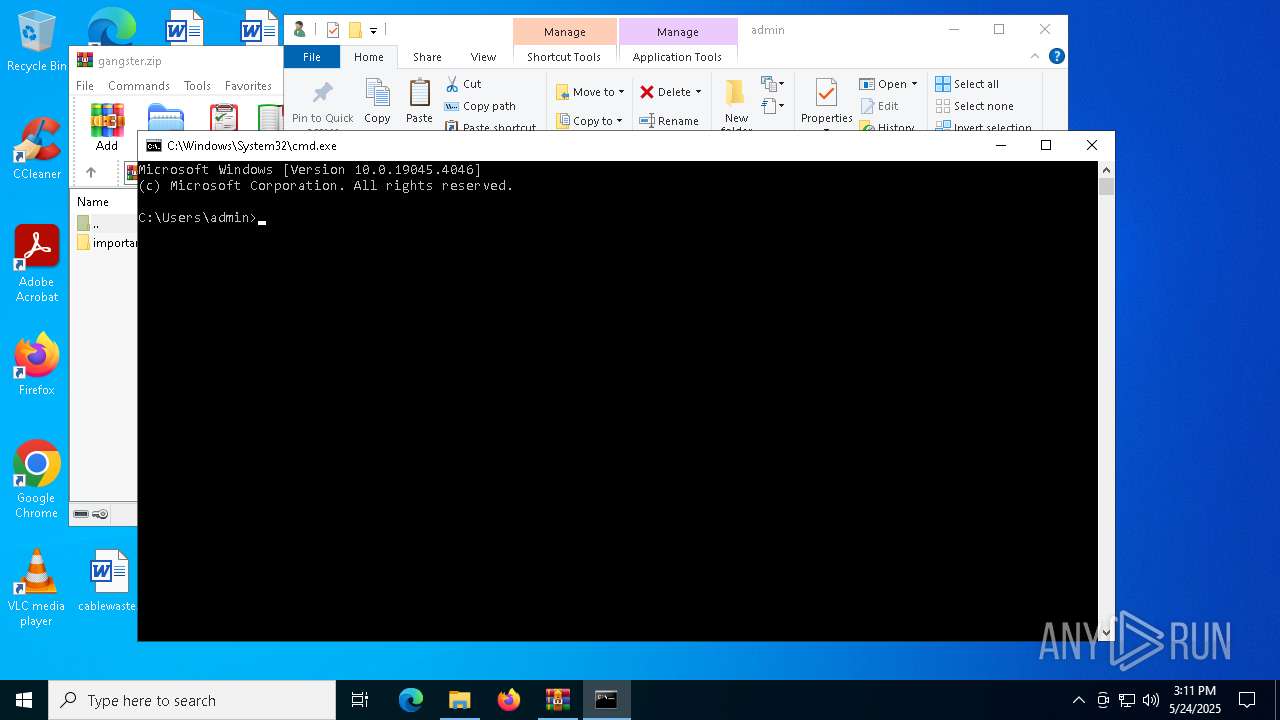
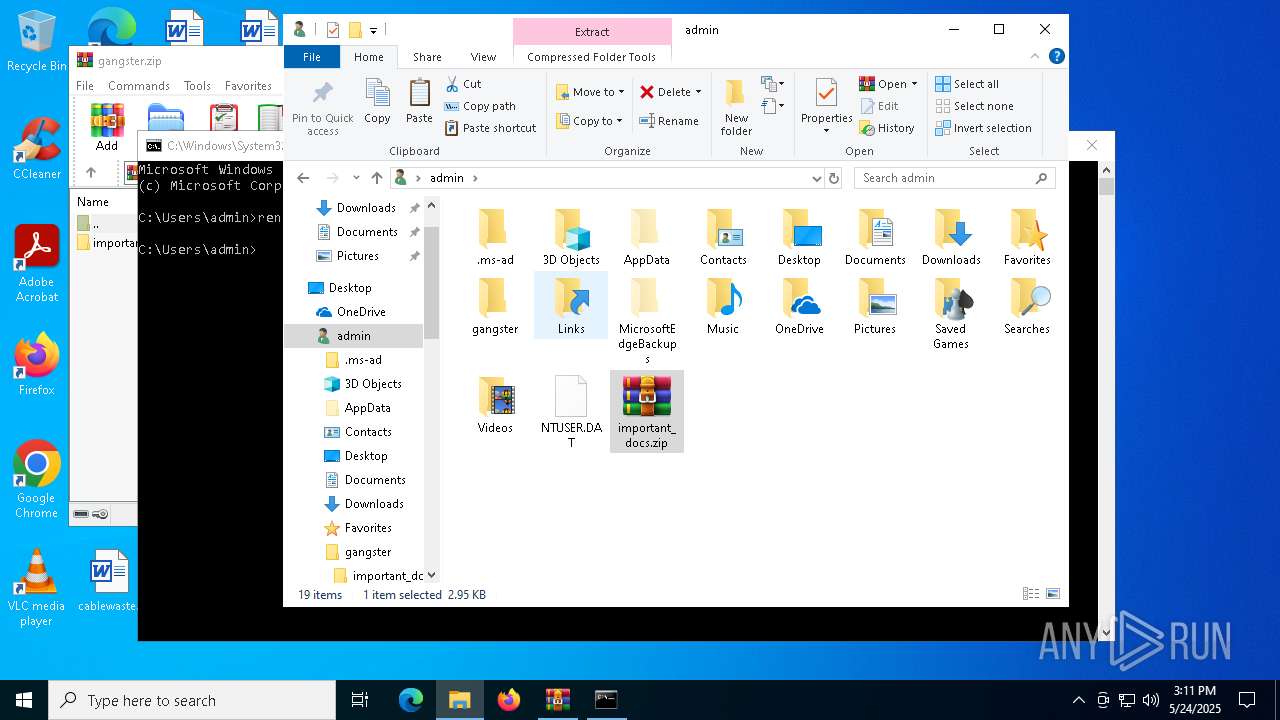
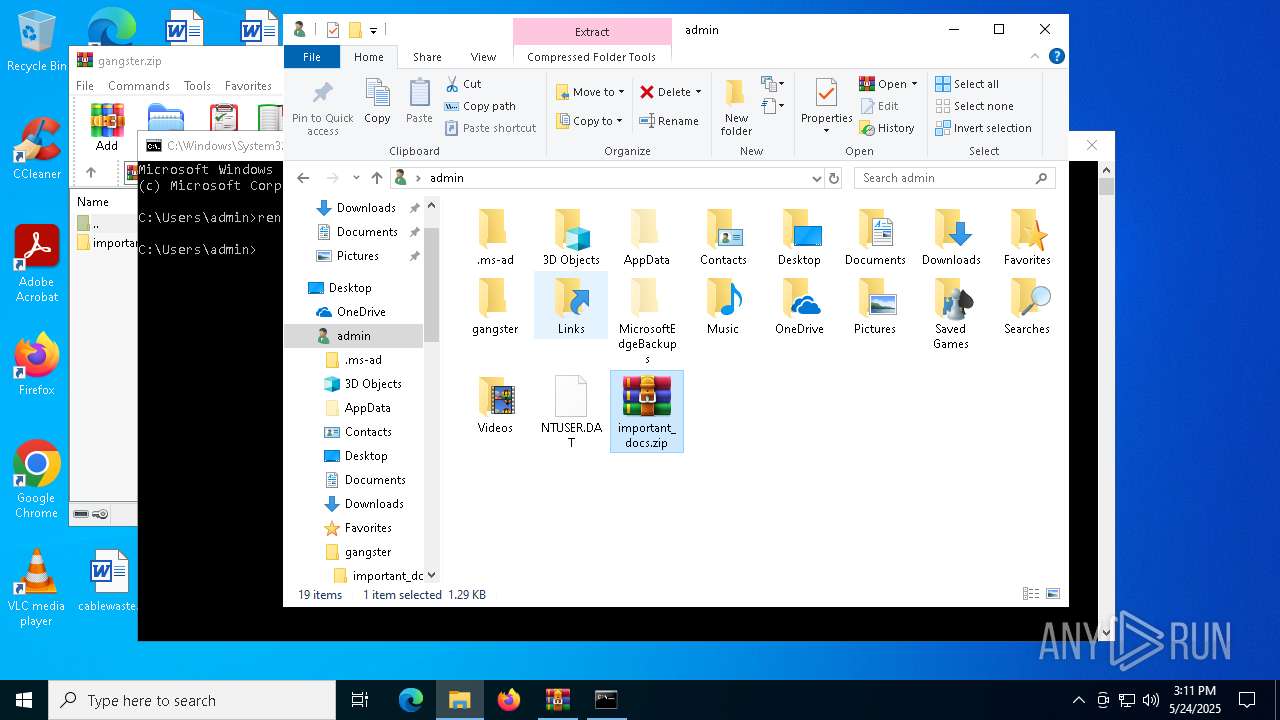
| File name: | gangster.zip |
| Full analysis: | https://app.any.run/tasks/043a13b9-9650-4390-94e4-3935e80399fe |
| Verdict: | Malicious activity |
| Analysis date: | May 24, 2025, 15:10:12 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | AFDC3A6283319F295A1933B0A4A35A22 |
| SHA1: | 00A591AF409C866D2E0DAE6FB41F8A8DF498DE98 |
| SHA256: | 77CAA9E68DDFE5C53E40191DF56752EF5E659F6A73626E0C9CD50AF5E647A4E5 |
| SSDEEP: | 48:9N1KZ9u37zHwCdAYHiHX3RQ6u8FDVezW7/A6frp4gqTuBiKQj/:XUruL5vHCX3buK0zo/A6fGLZKm/ |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 7888)
- powershell.exe (PID: 732)
- powershell.exe (PID: 6768)
Generic archive extractor
- WinRAR.exe (PID: 7012)
SUSPICIOUS
Manipulates environment variables
- powershell.exe (PID: 7888)
- powershell.exe (PID: 732)
- powershell.exe (PID: 6768)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7012)
Starts process via Powershell
- powershell.exe (PID: 7888)
- powershell.exe (PID: 732)
- powershell.exe (PID: 6768)
Returns all items found within a container (POWERSHELL)
- powershell.exe (PID: 7888)
- powershell.exe (PID: 6768)
- powershell.exe (PID: 732)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 7888)
INFO
Manual execution by a user
- powershell.exe (PID: 7888)
- cmd.exe (PID: 4988)
- powershell.exe (PID: 6768)
- powershell.exe (PID: 732)
Returns hidden items found within a container (POWERSHELL)
- conhost.exe (PID: 7896)
- conhost.exe (PID: 2108)
- conhost.exe (PID: 5864)
- conhost.exe (PID: 7512)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7888)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7888)
Reads security settings of Internet Explorer
- notepad.exe (PID: 8052)
Reads the software policy settings
- slui.exe (PID: 7232)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:05:20 17:35:52 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
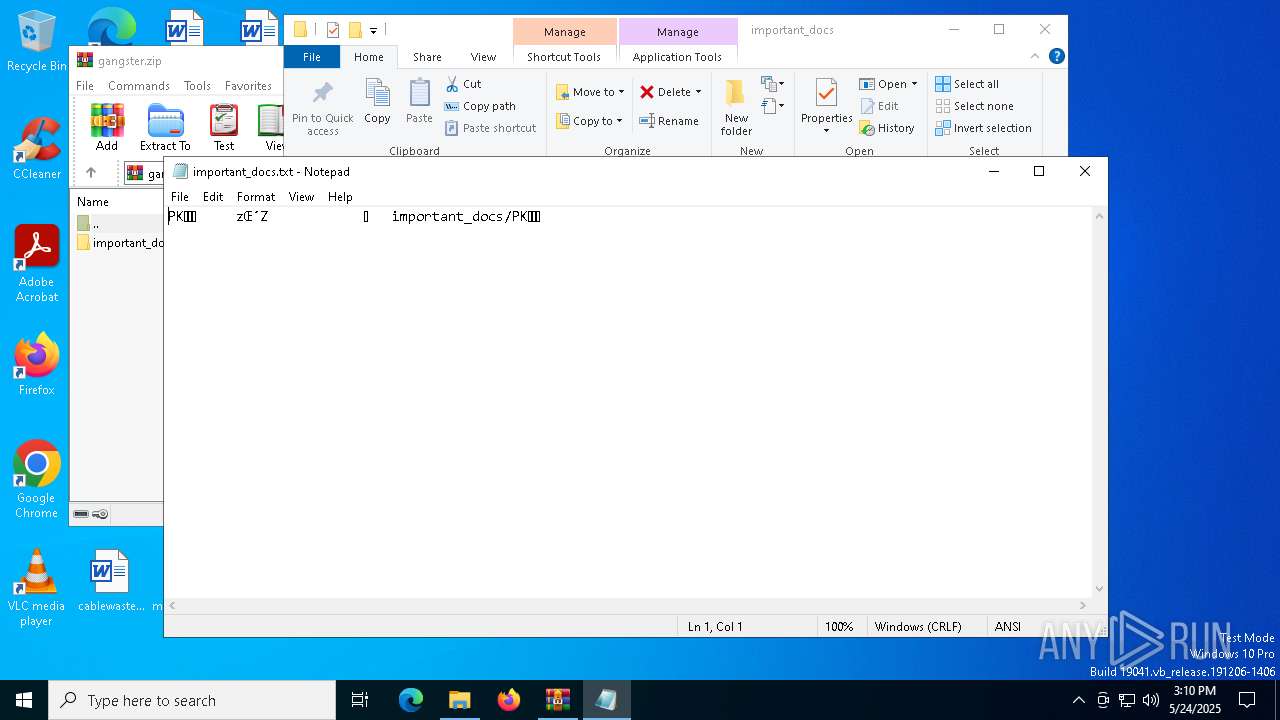
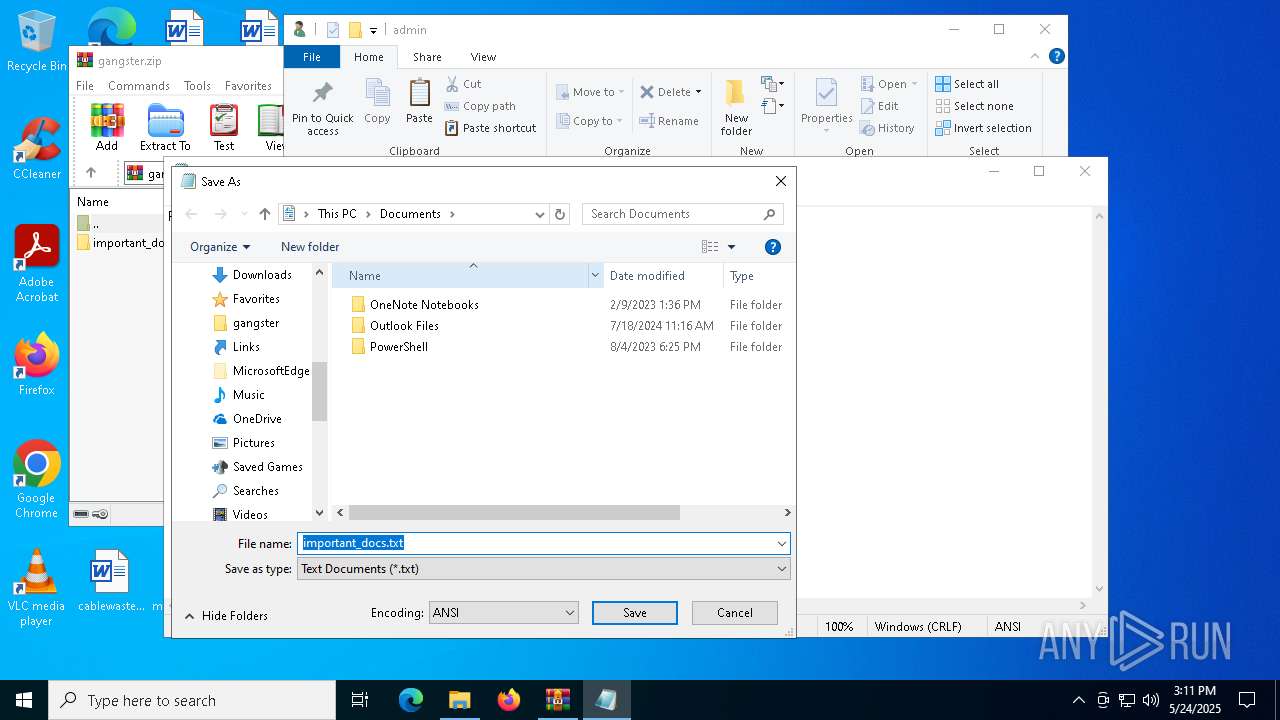
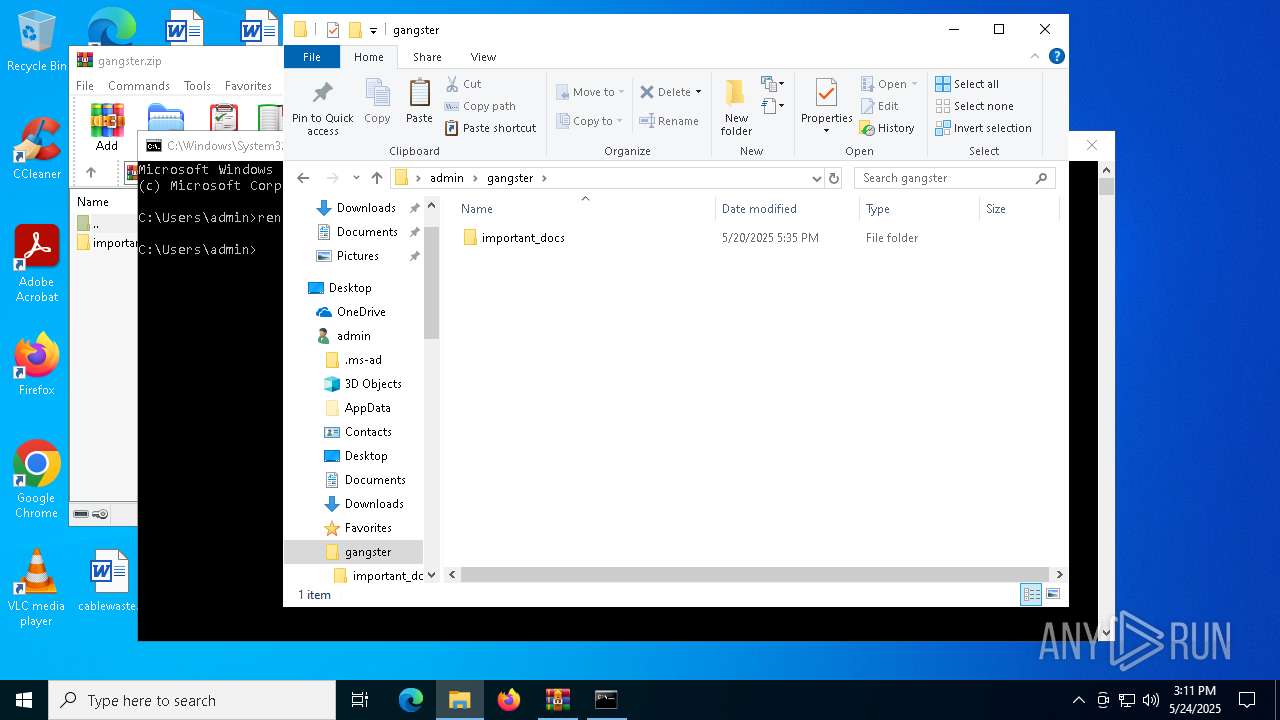
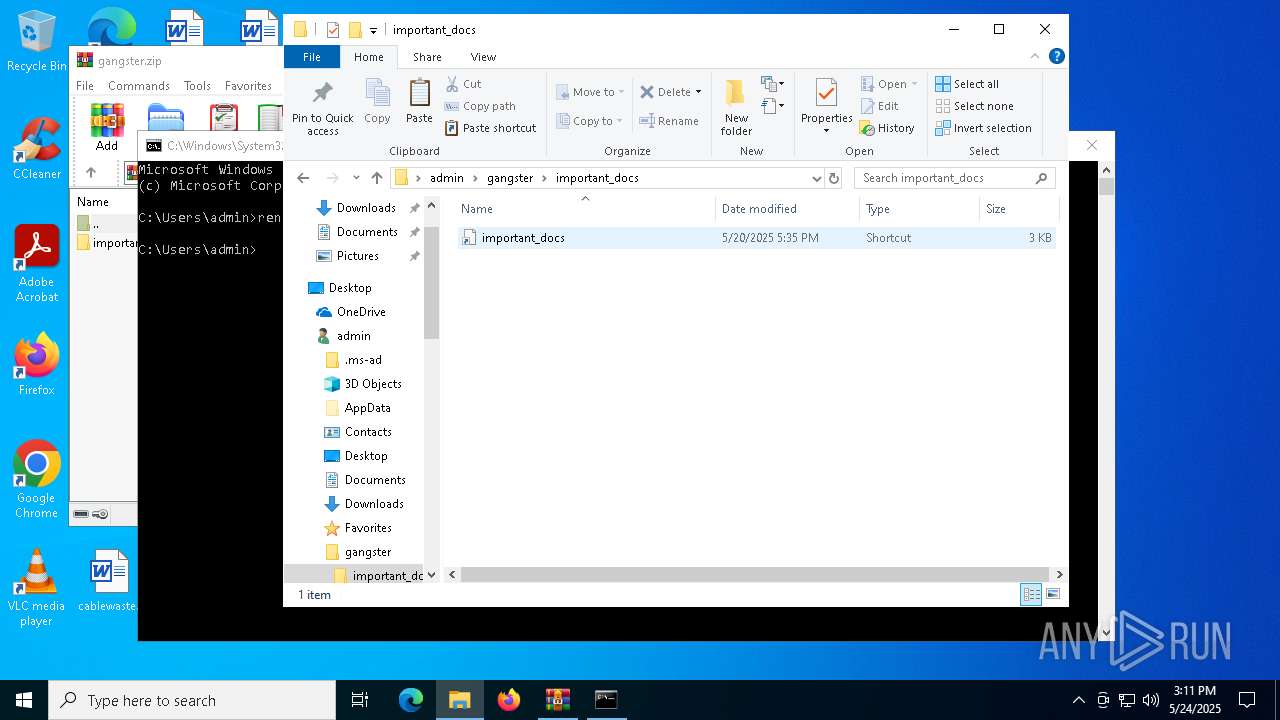
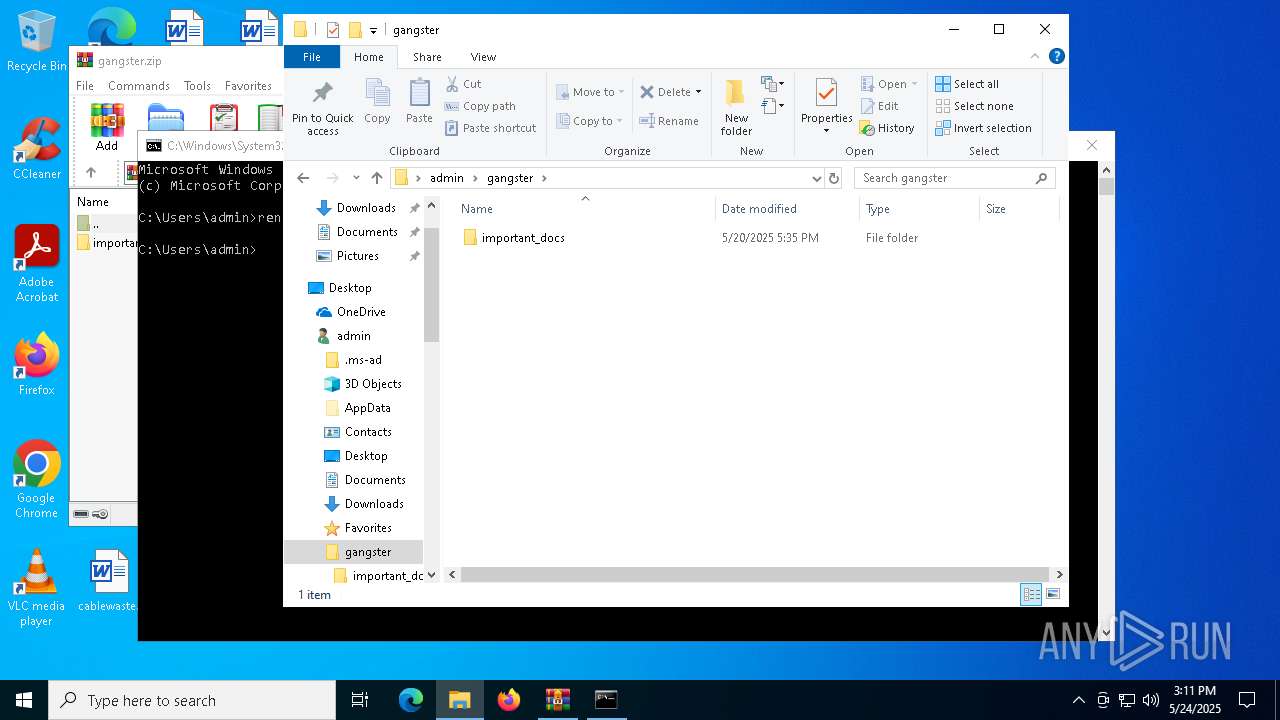
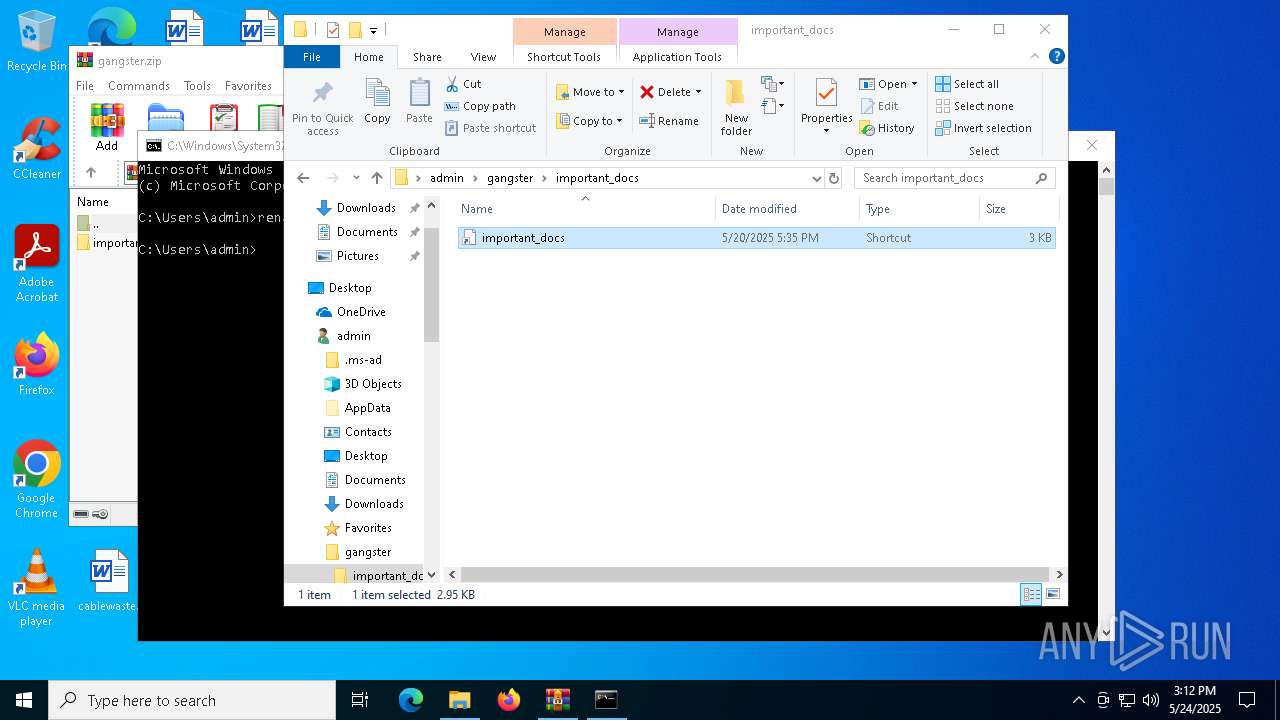
| ZipFileName: | important_docs/ |
Total processes
146
Monitored processes
16
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
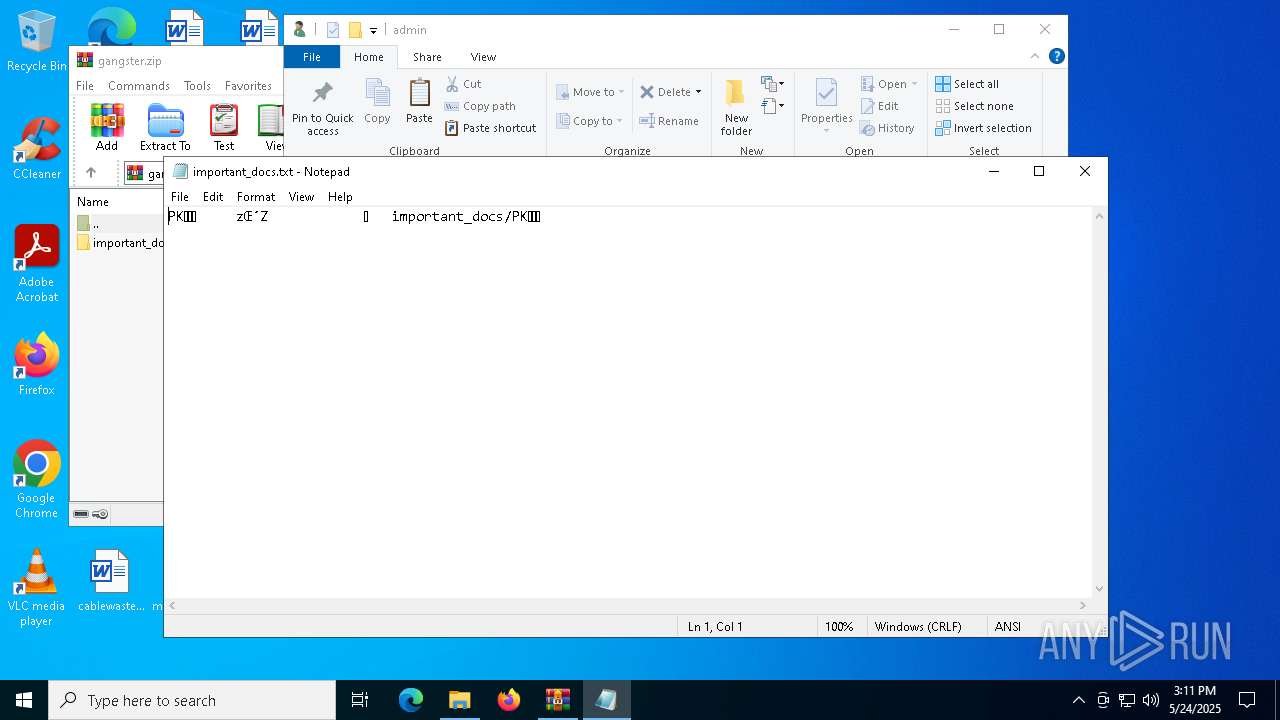
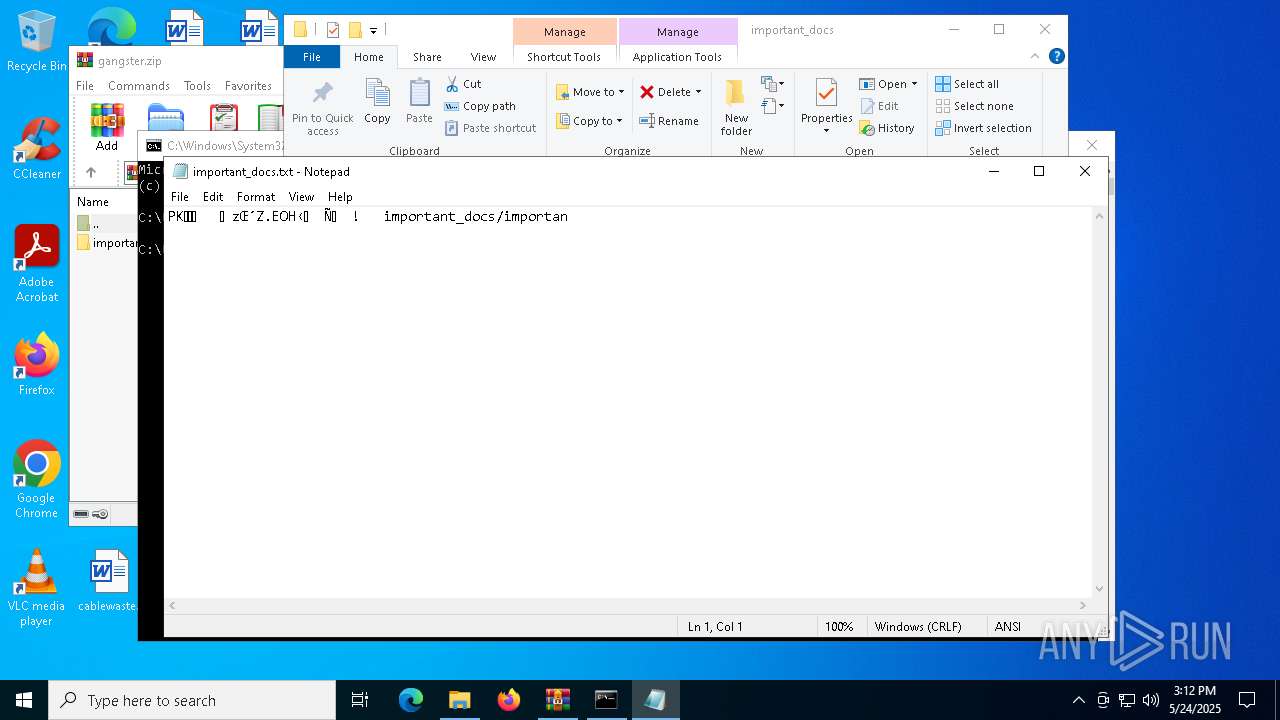
| 732 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w 1 -c "$name = \"important_docs\";$file = (get-childitem -Pa $Env:USERPROFILE -Re -Inc *$name.zip).fullname;$bytes=[System.IO.File]::ReadAllBytes($file);$size = (0..($bytes.Length - 4) | Where-Object {$bytes[$_] -eq 0x55 -and $bytes[$_+1] -eq 0x55 -and $bytes[$_+2] -eq 0x55 -and $bytes[$_+3] -eq 0x55 })[0] + 4;$length=53;$chunk=$bytes[$size..($size+$length-1)];$out = \"$Env:TEMP\$name.txt\";[System.IO.File]::WriteAllBytes($out,$chunk);Invoke-Item $out" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2108 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2320 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4988 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5864 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6768 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w 1 -c "$name = \"important_docs\";$file = (get-childitem -Pa $Env:USERPROFILE -Re -Inc *$name.zip).fullname;$bytes=[System.IO.File]::ReadAllBytes($file);$size = (0..($bytes.Length - 4) | Where-Object {$bytes[$_] -eq 0x55 -and $bytes[$_+1] -eq 0x55 -and $bytes[$_+2] -eq 0x55 -and $bytes[$_+3] -eq 0x55 })[0] + 4;$length=53;$chunk=$bytes[$size..($size+$length-1)];$out = \"$Env:TEMP\$name.txt\";[System.IO.File]::WriteAllBytes($out,$chunk);Invoke-Item $out" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7012 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\gangster.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7196 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7232 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
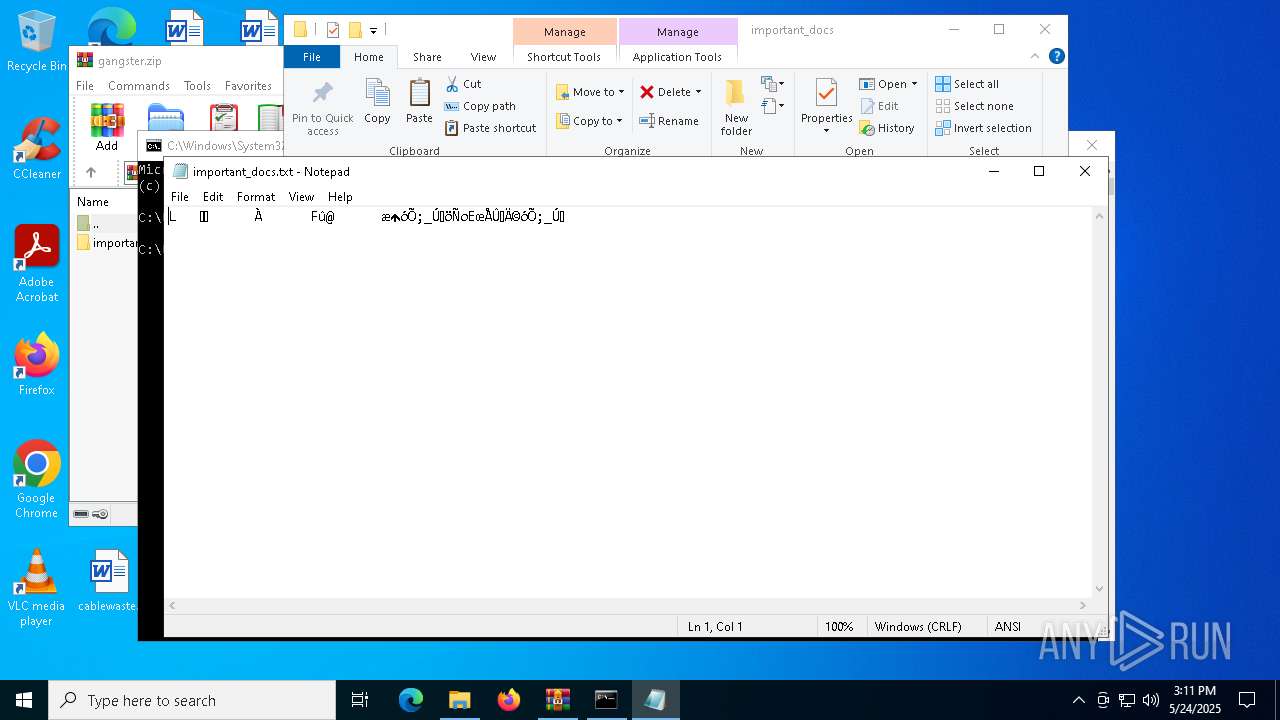
| 7464 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\important_docs.txt | C:\Windows\System32\notepad.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
21 898
Read events
21 809
Write events
74
Delete events
15
Modification events
| (PID) Process: | (7012) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7012) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7012) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7012) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\gangster.zip | |||
| (PID) Process: | (7012) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7012) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7012) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7012) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7012) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Extraction\Profile |
| Operation: | write | Name: | Overwrite |
Value: 0 | |||
| (PID) Process: | (7012) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Extraction\Profile |
| Operation: | write | Name: | Update |
Value: 0 | |||
Executable files
0
Suspicious files
13
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
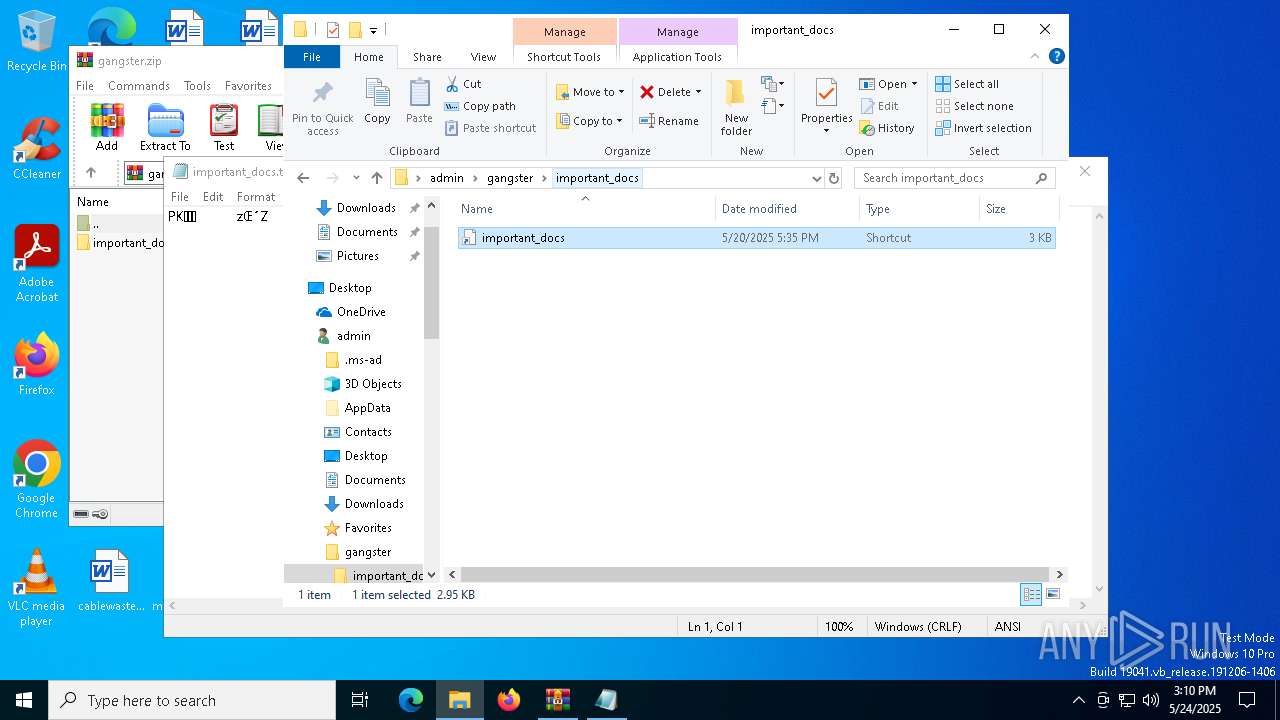
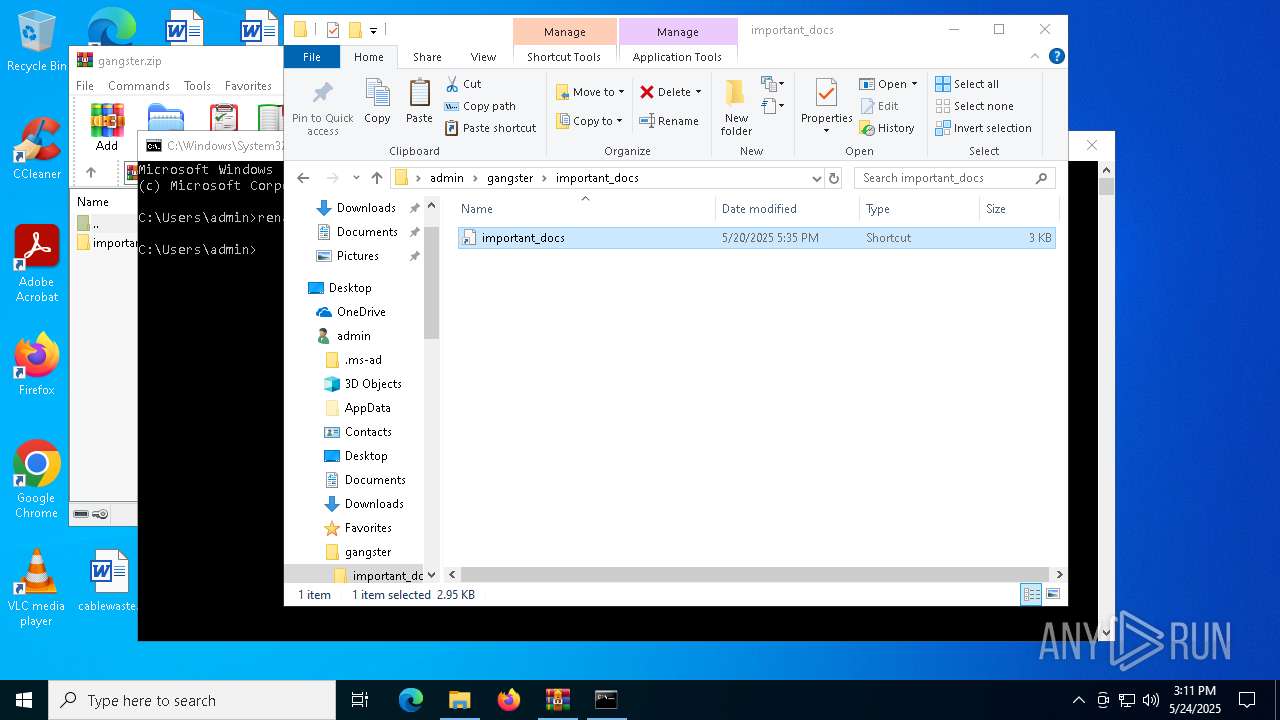
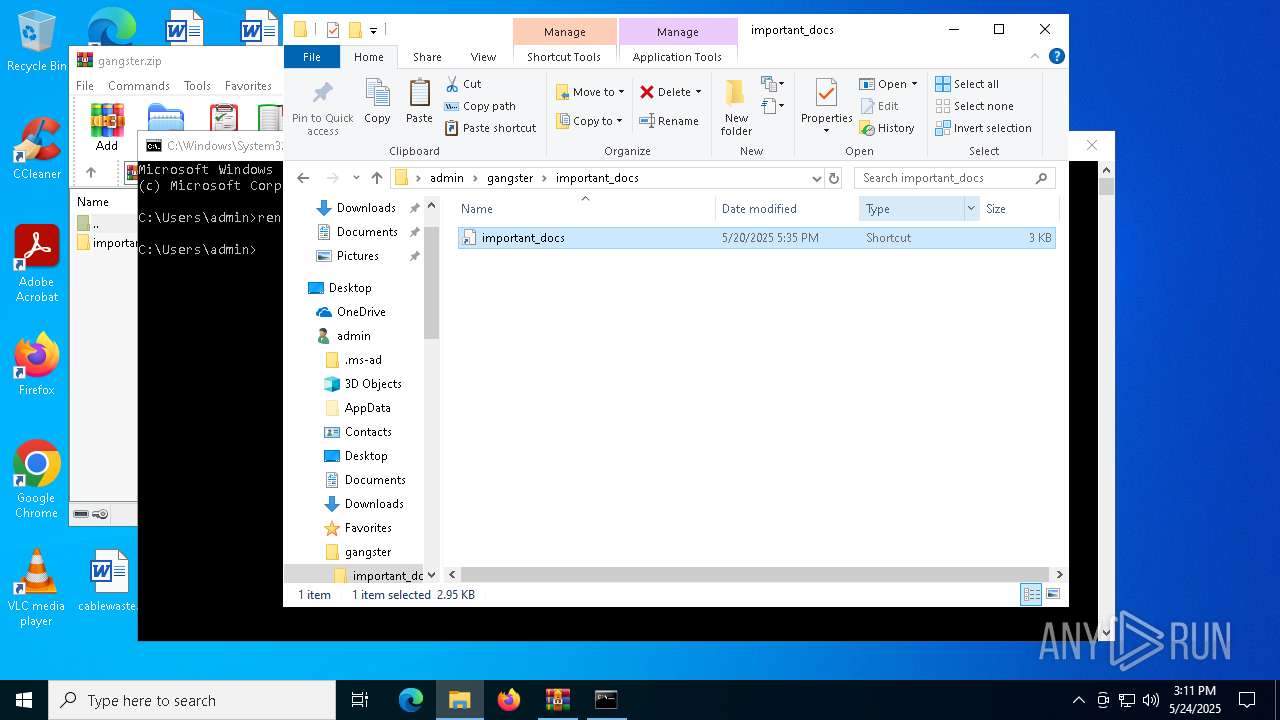
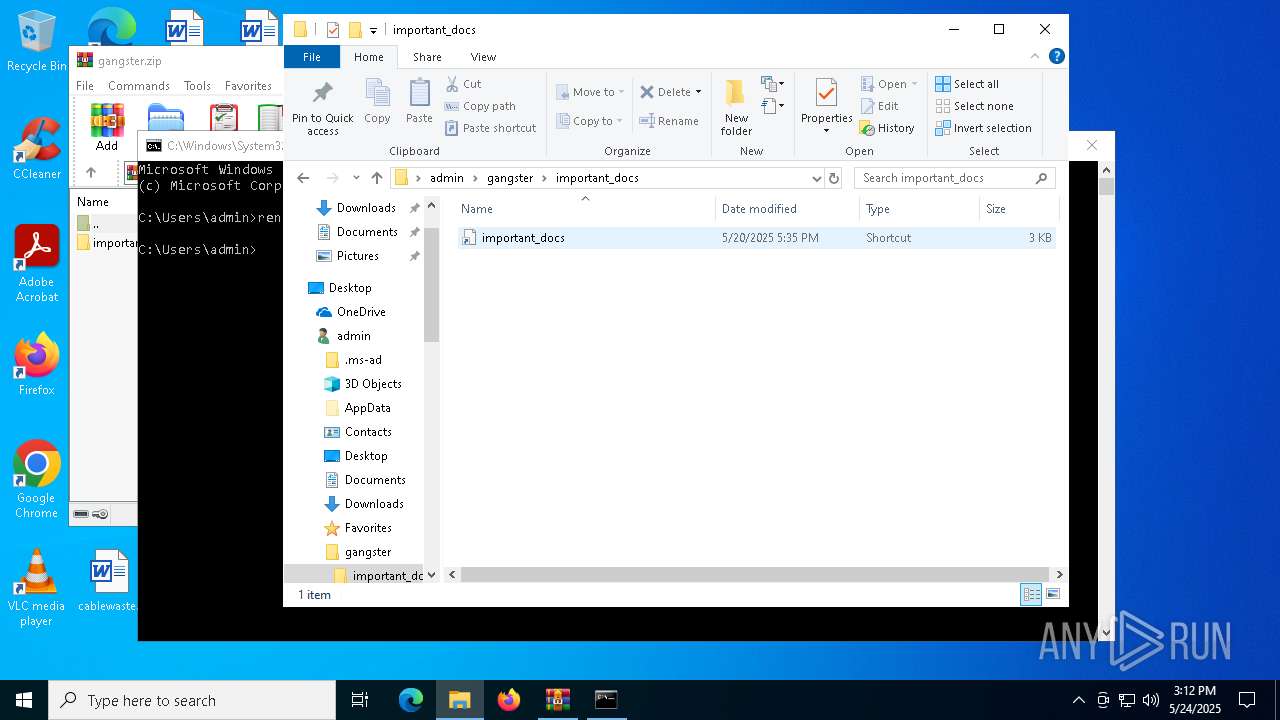
| 7012 | WinRAR.exe | C:\Users\admin\gangster\important_docs\important_docs.lnk | binary | |
MD5:19BF7F328F273642F1FDD88B400E191D | SHA256:48EE84C075FA18E6389027BCCEB6B9108B00716E4D21A8038D24A52B6905A4A1 | |||
| 7888 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_sqemvldi.qbn.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7888 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ywmb4mv3.lrr.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7888 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ABW3J9W90V53I7FRG6UR.temp | binary | |
MD5:498406F05ABD6365E093E586297A6182 | SHA256:F3616A23CA95C73C9D7D87A79FC13637EDFEDA35FB70F484F9C50572B8584978 | |||
| 7888 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ab37bafd3b74970.customDestinations-ms | binary | |
MD5:498406F05ABD6365E093E586297A6182 | SHA256:F3616A23CA95C73C9D7D87A79FC13637EDFEDA35FB70F484F9C50572B8584978 | |||
| 4988 | cmd.exe | C:\Users\admin\important_docs.zip | binary | |
MD5:19BF7F328F273642F1FDD88B400E191D | SHA256:48EE84C075FA18E6389027BCCEB6B9108B00716E4D21A8038D24A52B6905A4A1 | |||
| 6768 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ab37bafd3b74970.customDestinations-ms | binary | |
MD5:9E2F8AE1BAFB927272BF3526F9DA01A4 | SHA256:E796EF63102649E646596C0588CD93B0BC6FFA3F2BBFE3B6CDFF7079ACD767FE | |||
| 8052 | notepad.exe | C:\Users\admin\Documents\important_docs.txt | compressed | |
MD5:2C8572EB0B2ED1EE77D44935F79478DC | SHA256:4E6DF6EB17A8424F4988E4C75B246B7BD3AD5EE090CA1AE95929A372E20CBC95 | |||
| 732 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\9CZDXT26BI01XBR0EORJ.temp | binary | |
MD5:3073E5D698730AECB6F5DB4327BA0FA4 | SHA256:70DEA01ED869AEA8282E421BFF9DCD5912E3310DC579014D0B54CE2339CBE788 | |||
| 7888 | powershell.exe | C:\Users\admin\AppData\Local\Temp\important_docs.txt | compressed | |
MD5:378D59A058D4FEB1128FCDC020AE710A | SHA256:589B8A1D16A745CFFCA58BD686CD7CF10E222E6F8CADA4571D5C640D645C9265 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
24
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8060 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8060 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.31.1:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |