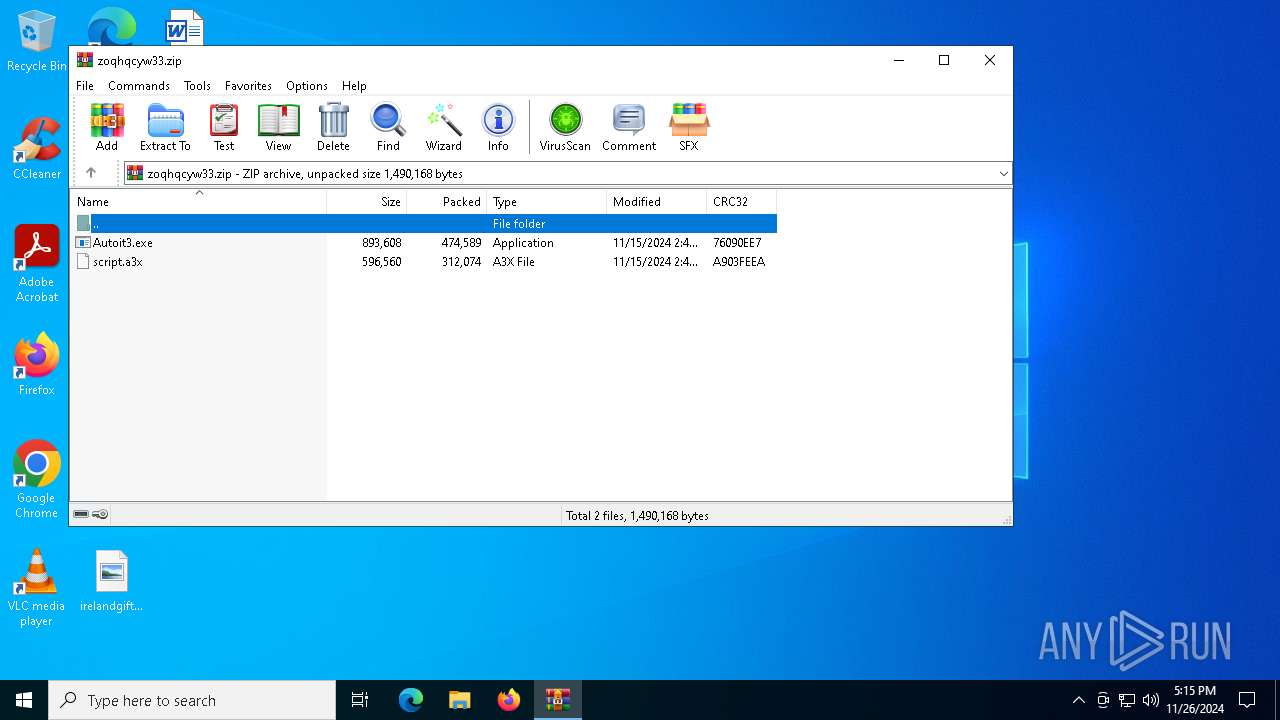
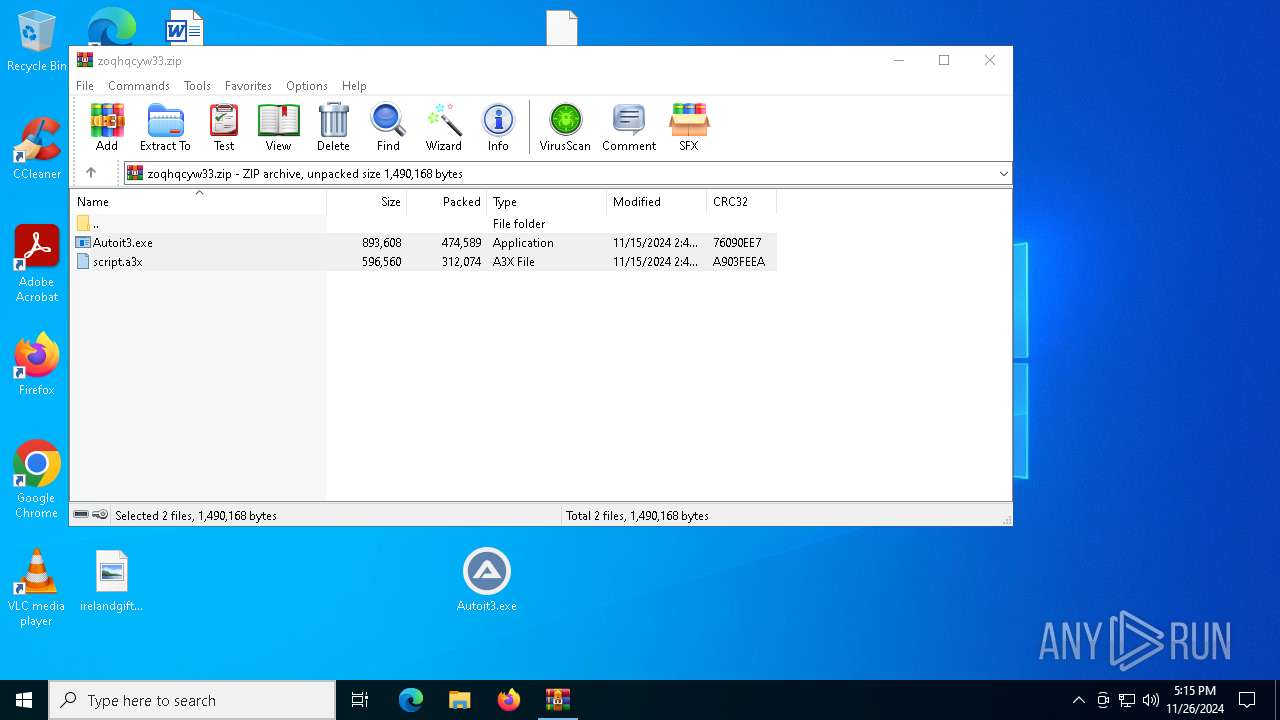
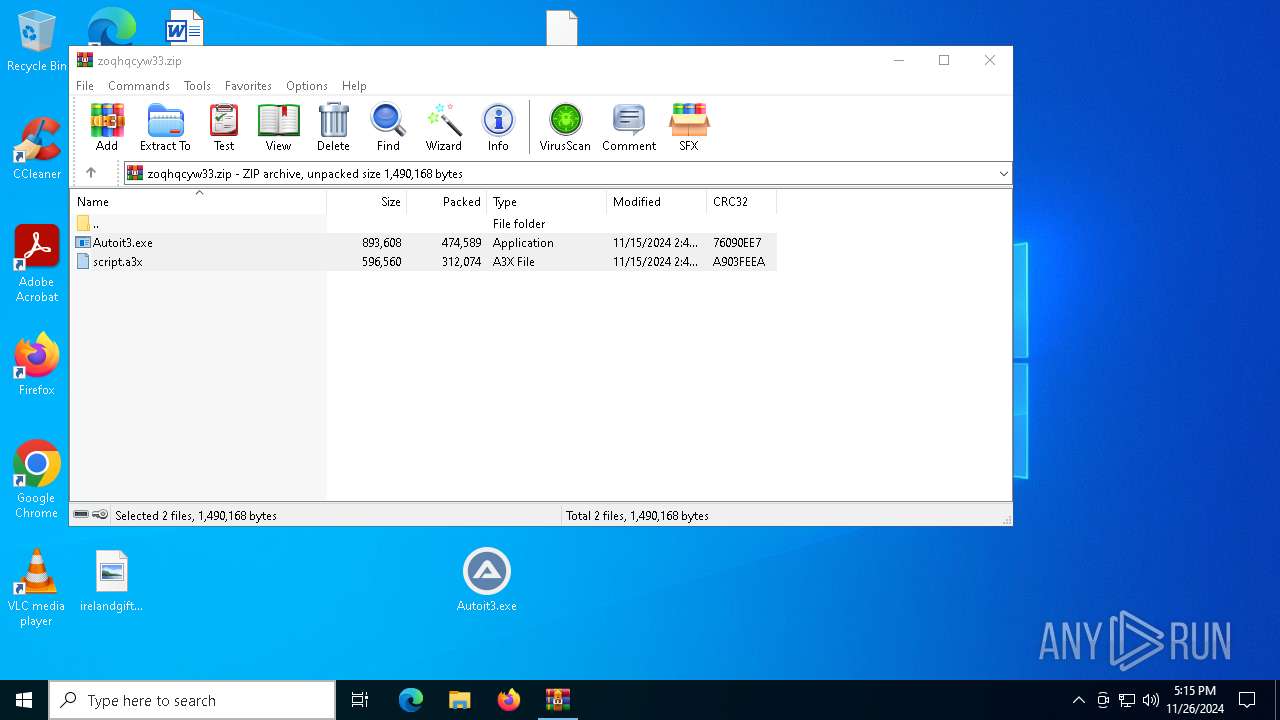
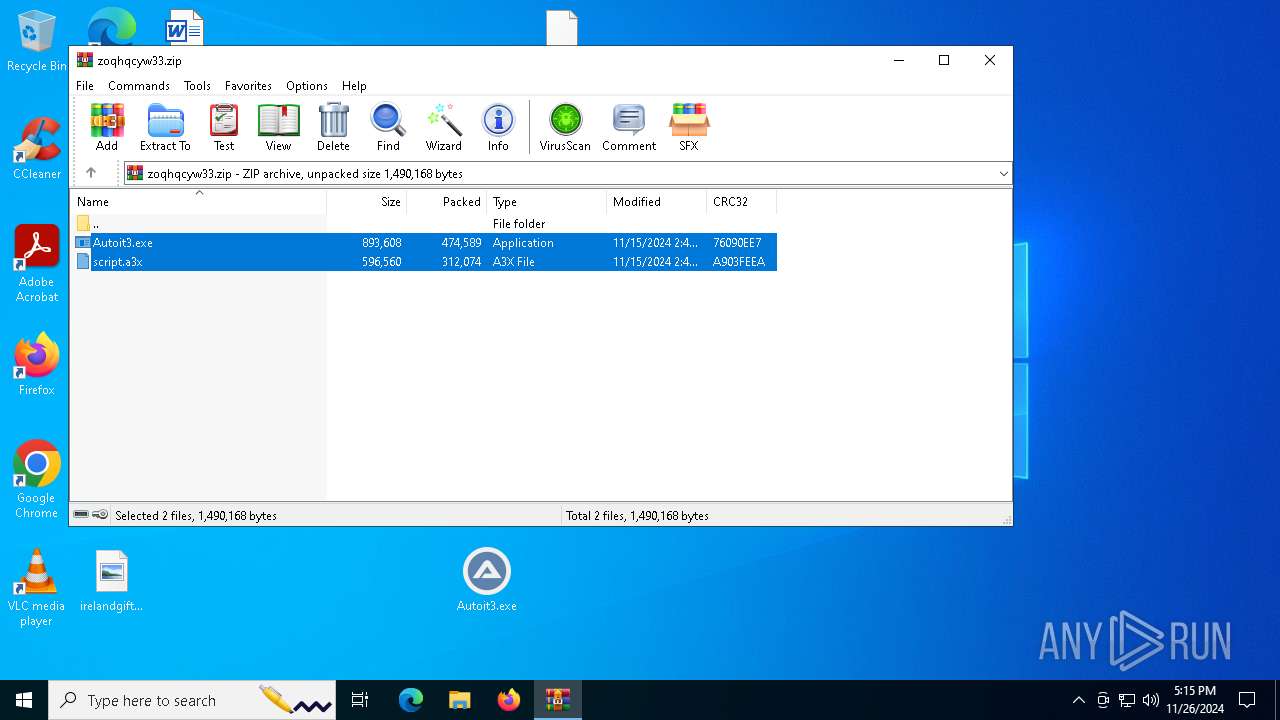
| File name: | zoqhqcyw33.zip |
| Full analysis: | https://app.any.run/tasks/f8cae5ae-70c2-4116-ab4d-4aa7faa67d01 |
| Verdict: | Malicious activity |
| Analysis date: | November 26, 2024, 17:15:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 42FD217377F89BB9765DF2329665014A |
| SHA1: | 213A424C39F903CADB05B40FC4587BF9588A725E |
| SHA256: | 77989454F18EB4906CC606351ADF43B372082F0371DF92A2A55C9C19D145A3DB |
| SSDEEP: | 24576:o3yHC2sBdHl6AO85iYLLo6UAtuzkqkyKiOPwMFvhzXCZIqbBI7sxj+eV:o3yHC2sBpl6jeiyLo6UAtqkqkyKiOPwP |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2512)
SUSPICIOUS
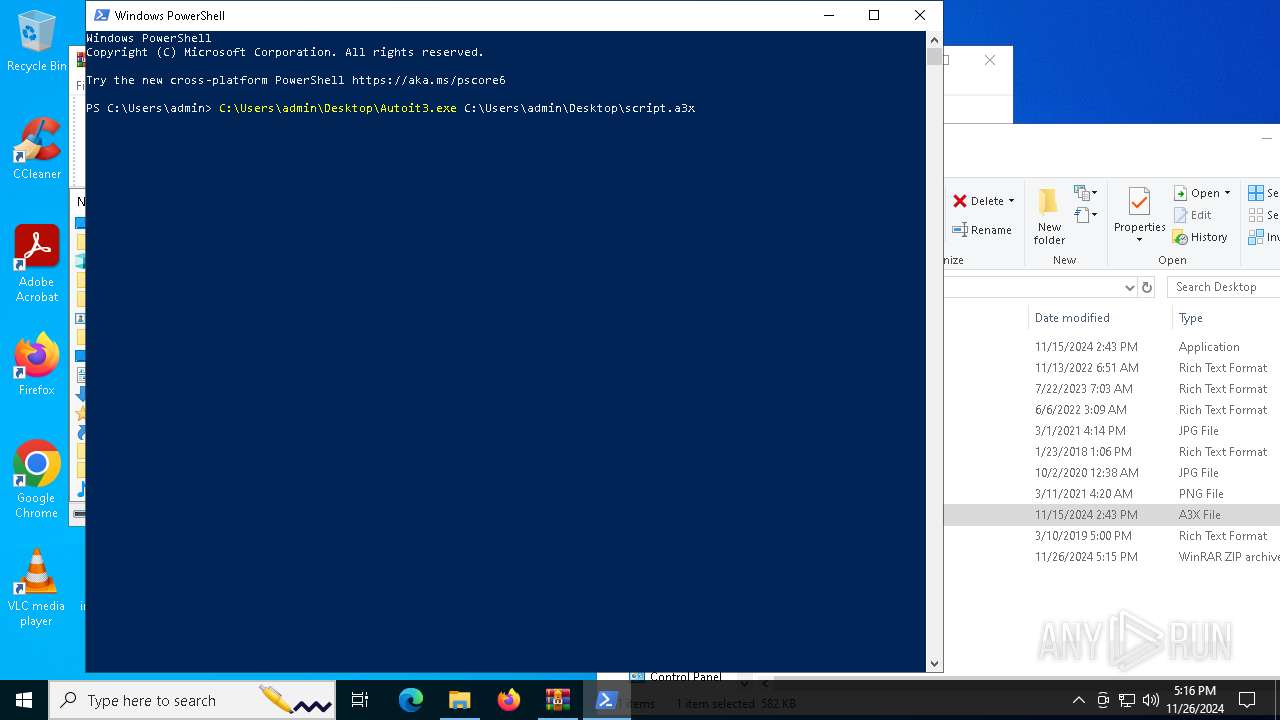
Starts the AutoIt3 executable file
- powershell.exe (PID: 4320)
Executable content was dropped or overwritten
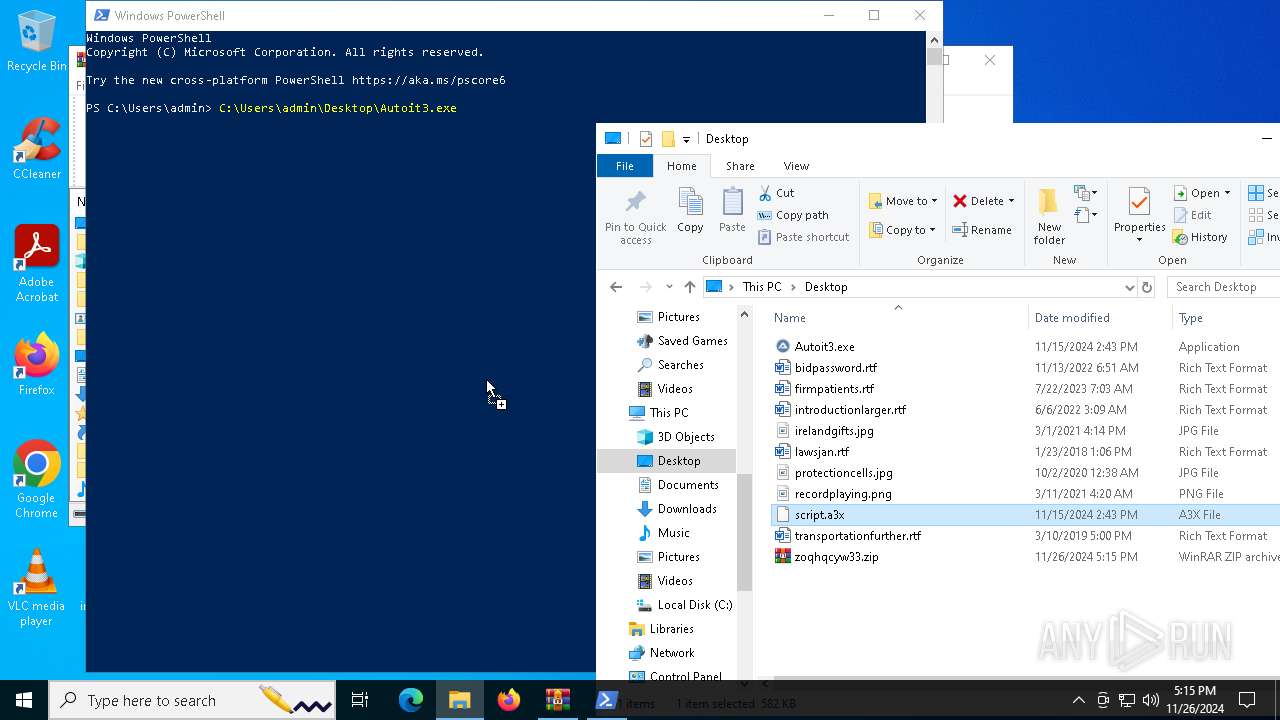
- Autoit3.exe (PID: 716)
Starts CMD.EXE for commands execution
- Autoit3.exe (PID: 716)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 7100)
INFO
Manual execution by a user
- pwsh.exe (PID: 7040)
- powershell.exe (PID: 4320)
The process uses the downloaded file
- WinRAR.exe (PID: 2512)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2512)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:11:15 14:43:56 |
| ZipCRC: | 0xa903feea |
| ZipCompressedSize: | 312074 |
| ZipUncompressedSize: | 596560 |
| ZipFileName: | script.a3x |
Total processes
139
Monitored processes
10
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 716 | "C:\Users\admin\Desktop\Autoit3.exe" C:\Users\admin\Desktop\script.a3x | C:\Users\admin\Desktop\Autoit3.exe | powershell.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 14, 5 Modules
| |||||||||||||||
| 2512 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\zoqhqcyw33.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3540 | wmic ComputerSystem get domain | C:\Windows\SysWOW64\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4076 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4320 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6912 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7040 | "C:\Program Files\PowerShell\7\pwsh.exe" -WorkingDirectory ~ | C:\Program Files\PowerShell\7\pwsh.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: pwsh Exit code: 3221225786 Version: 7.3.5.500 Modules
| |||||||||||||||
| 7048 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | pwsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7100 | "c:\windows\system32\cmd.exe" /c wmic ComputerSystem get domain > C:\ProgramData\cfhkcfk\ahchcfh | C:\Windows\SysWOW64\cmd.exe | — | Autoit3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7136 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 063
Read events
9 049
Write events
14
Delete events
0
Modification events
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\zoqhqcyw33.zip | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
2
Suspicious files
9
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7040 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\3c3871276e149215.customDestinations-ms~RF1378fc.TMP | binary | |
MD5:46E1C931FBFF22C77310388EB2BC9B98 | SHA256:704B8AE61BD9951DEA597ED475FD91BAD6ECDEC71726941BDAC64686A59263DB | |||
| 7040 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\3c3871276e149215.customDestinations-ms | binary | |
MD5:C42F072EBEEB5B0290BB66F29472DAF6 | SHA256:6A7E9AECFE1D398BA3A8EE7559D0425C3A0B05336677037A7BC2357F1CC0EDD3 | |||
| 7040 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\U2J02G7PKRT044QPUDL9.temp | binary | |
MD5:C42F072EBEEB5B0290BB66F29472DAF6 | SHA256:6A7E9AECFE1D398BA3A8EE7559D0425C3A0B05336677037A7BC2357F1CC0EDD3 | |||
| 7040 | pwsh.exe | C:\Users\admin\AppData\Local\Microsoft\PowerShell\StartupProfileData-Interactive | binary | |
MD5:8C840AA62536D84C771D5C41F64B9A11 | SHA256:A2A2C65F004DA1782F1D27B9FC56A7BAE4BFDB917F78F576D919E5AB82E963A5 | |||
| 7040 | pwsh.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tf0fcjly.awp.psm1 | text | |
MD5:FA2C2C4CEFDD40313C84197AFE48FB95 | SHA256:32B77FE8CDC0D14174DCCFE05BC55413D35C1BC90ED716E06CDB9BC61DE13A91 | |||
| 7040 | pwsh.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tqxayknm.bv0.ps1 | text | |
MD5:FA2C2C4CEFDD40313C84197AFE48FB95 | SHA256:32B77FE8CDC0D14174DCCFE05BC55413D35C1BC90ED716E06CDB9BC61DE13A91 | |||
| 2512 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2512.13886\script.a3x | binary | |
MD5:28A5B7B44A0D1F67D125D5B768BC6398 | SHA256:BB56354CDB241DE0051B7BCC7E68099E19CC2F26256AF66FAD69E3D2BC8A8922 | |||
| 716 | Autoit3.exe | C:\Users\admin\AppData\Roaming\AHdAGhh | text | |
MD5:38B20837CB1A1F8A67877281ECACDACD | SHA256:890CBF766E21A84F4BB552688DB43501DC7D3B849E8210B406F224A932414224 | |||
| 716 | Autoit3.exe | C:\temp\aahakeh | text | |
MD5:921573C51E78FE6037E6B996687A32BC | SHA256:F251B822CBE6CC77AFF0F3E4BE981BFC1CE8E6F9F4BDE8A6D7567AE4085D680F | |||
| 716 | Autoit3.exe | C:\ProgramData\cfhkcfk\Autoit3.exe | executable | |
MD5:C56B5F0201A3B3DE53E561FE76912BFD | SHA256:237D1BCA6E056DF5BB16A1216A434634109478F882D3B1D58344C801D184F95D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
41
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6188 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7000 | SIHClient.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7000 | SIHClient.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3508 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.209.148:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
1176 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
5064 | SearchApp.exe | 204.79.197.222:443 | fp.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
r.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
th.bing.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
mcr-ring.msedge.net |
| unknown |