| File name: | error422(1).exe |
| Full analysis: | https://app.any.run/tasks/26ab58f6-0fa0-4643-8ff4-9f4200cb7f95 |
| Verdict: | Malicious activity |
| Analysis date: | December 27, 2021, 13:16:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 7B01E76578486D44BBAFB0D51381820E |
| SHA1: | 0DAA6B605200BF6FABD7A08F7DE4C1EAC4FD12D9 |
| SHA256: | 7765F79269EBAD7F33A0DC8D18360F5ADF9464660F2259F9961CAD0AA2F94BBD |
| SSDEEP: | 196608:GiF+hNQl6gsLxL8QpNpKyro8thPVNadBB:oC0bx5pTKs1JadBB |
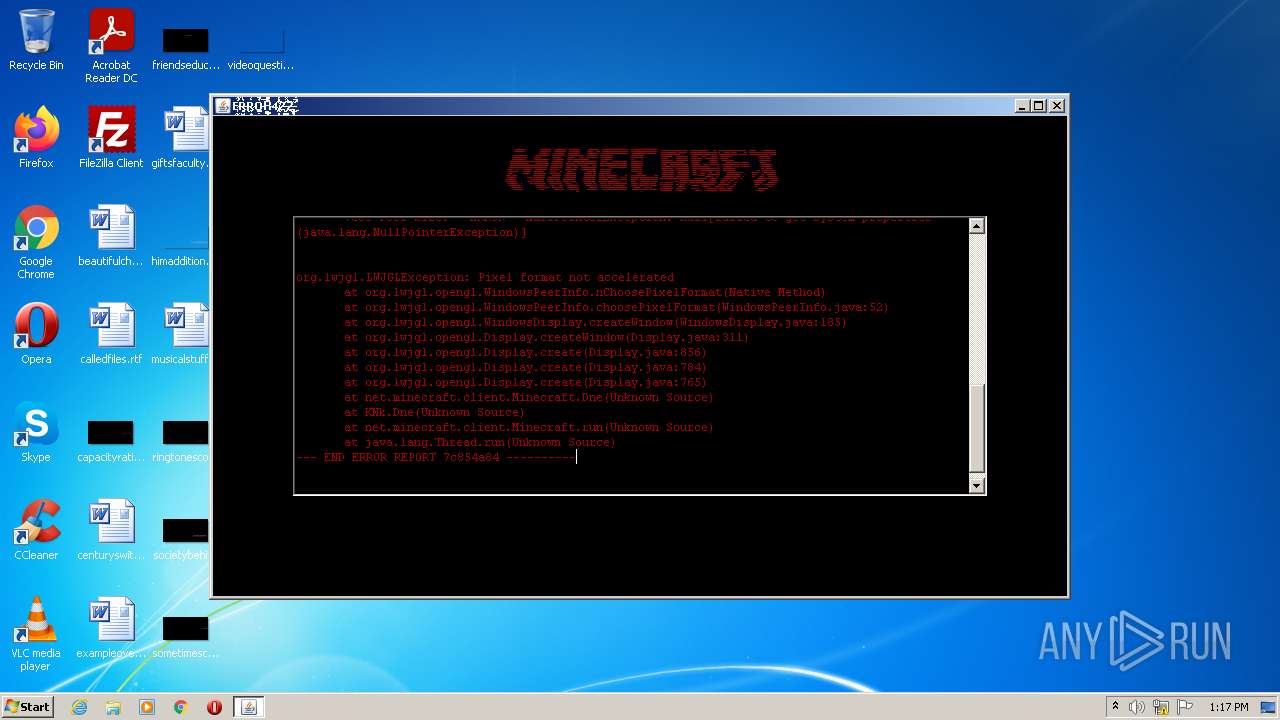
MALICIOUS
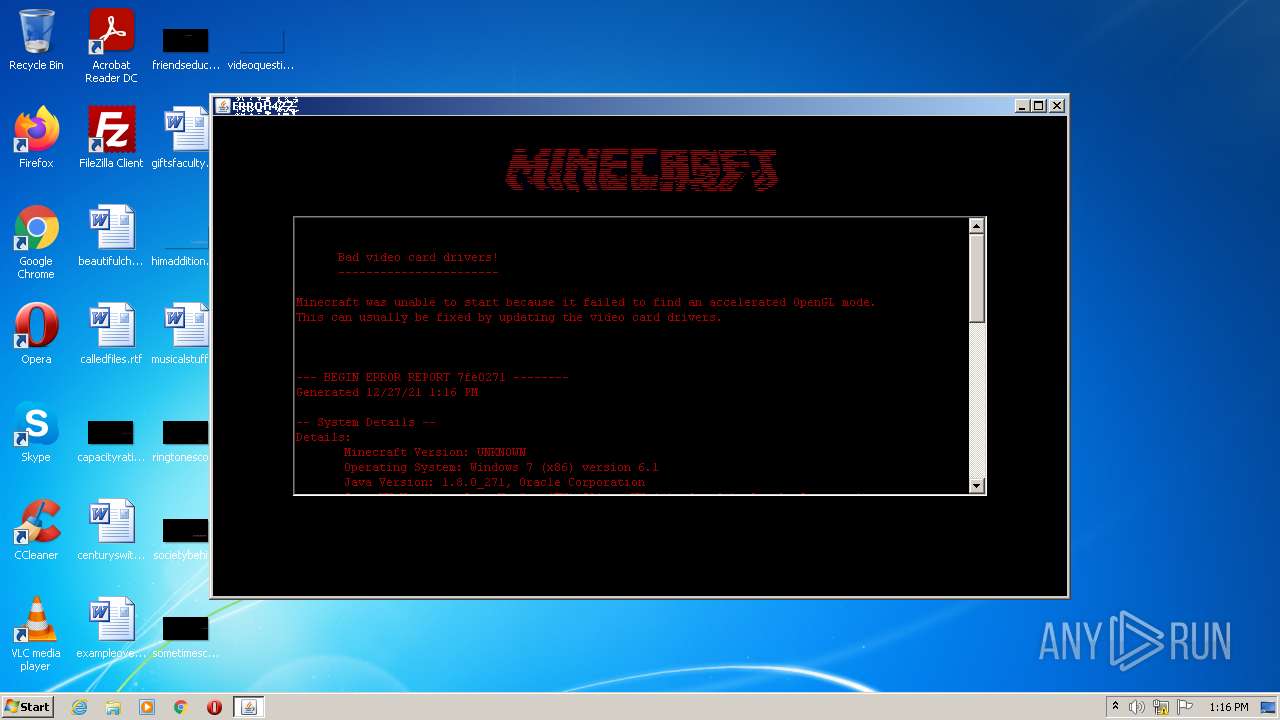
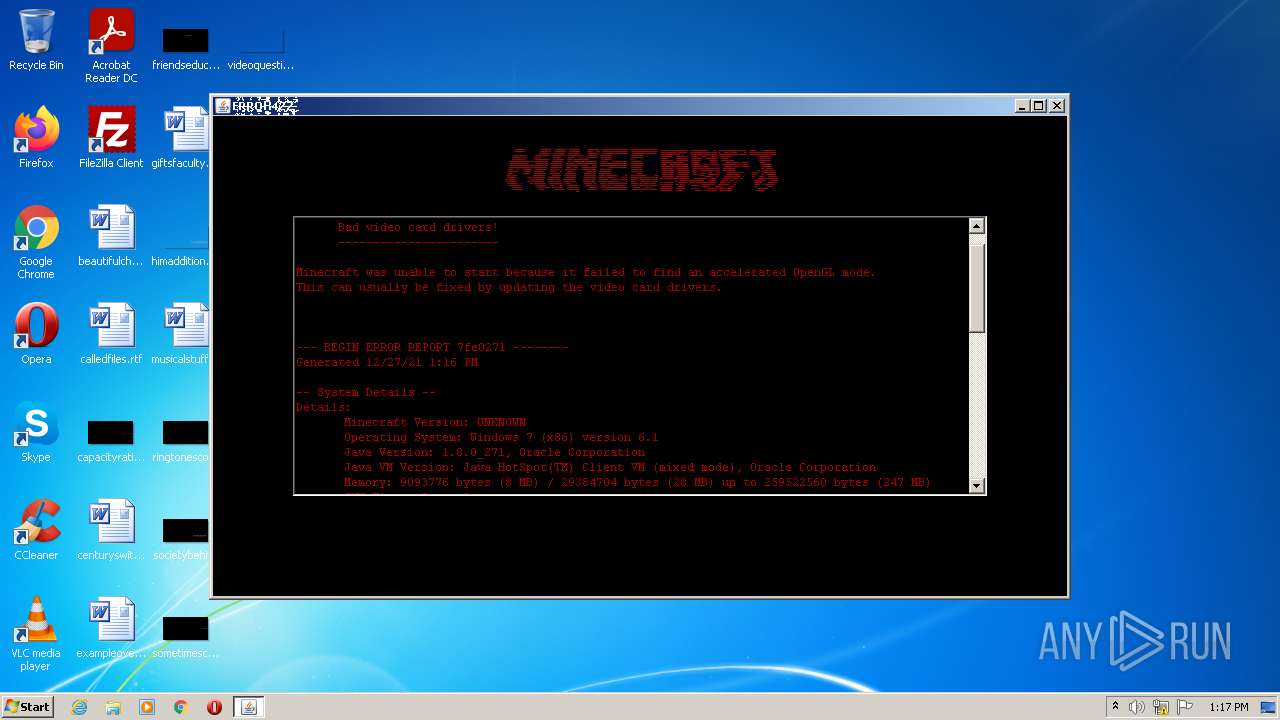
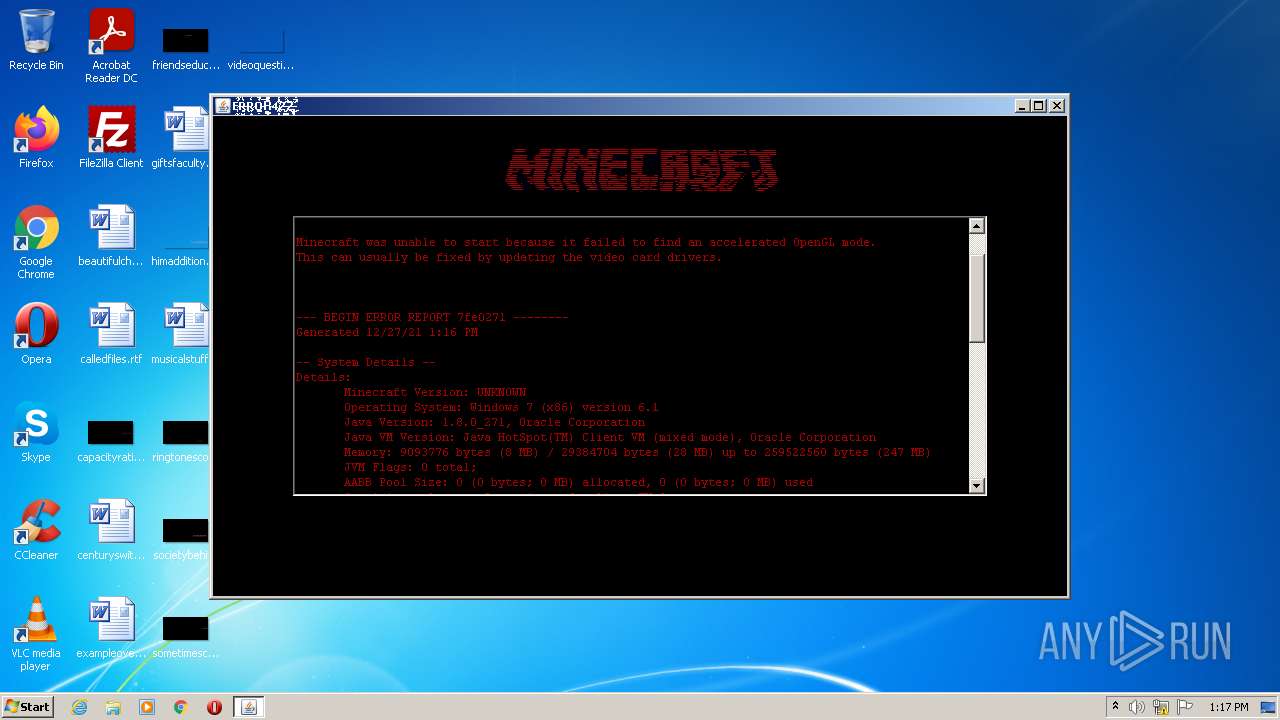
Drops executable file immediately after starts
- error422(1).exe (PID: 4020)
Application was dropped or rewritten from another process
- i4jdel0.exe (PID: 3404)
SUSPICIOUS
Checks supported languages
- error422(1).exe (PID: 4020)
- java.exe (PID: 2128)
- i4jdel0.exe (PID: 3404)
Check for Java to be installed
- error422(1).exe (PID: 4020)
Uses ICACLS.EXE to modify access control list
- java.exe (PID: 2128)
Creates files in the program directory
- java.exe (PID: 2128)
Executable content was dropped or overwritten
- error422(1).exe (PID: 4020)
Creates files in the user directory
- error422(1).exe (PID: 4020)
Reads the computer name
- error422(1).exe (PID: 4020)
INFO
Checks supported languages
- icacls.exe (PID: 1172)
Reads the computer name
- icacls.exe (PID: 1172)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| InternalName: | █████████████ |
|---|---|
| OriginalFileName: | ERROR422.exe |
| ProductVersion: | 54 45 53 54 20 66 69 78 2e 70 61 74 63 68 5f 32 |
| ProductName: | ERROR422 |
| LegalCopyright: | █████████████ |
| FileVersion: | █████████████ |
| FileDescription: | █████████████ |
| CompanyName: | █████████████ |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Unknown |
| FileOS: | Win32 |
| FileFlags: | Debug |
| FileFlagsMask: | 0x0017 |
| ProductVersionNumber: | 54.0.0.0 |
| FileVersionNumber: | 0.0.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 5 |
| ImageVersion: | - |
| OSVersion: | 5 |
| EntryPoint: | 0x15c07 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 130560 |
| CodeSize: | 169472 |
| LinkerVersion: | 9 |
| PEType: | PE32 |
| TimeStamp: | 2020:01:02 18:29:49+01:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 02-Jan-2020 17:29:49 |
| Detected languages: |
|
| CompanyName: | █████████████ |
| FileDescription: | █████████████ |
| FileVersion: | █████████████ |
| LegalCopyright: | █████████████ |
| ProductName: | ERROR422 |
| ProductVersion: | 54 45 53 54 20 66 69 78 2e 70 61 74 63 68 5f 32 |
| OriginalFilename: | ERROR422.exe |
| InternalName: | █████████████ |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 02-Jan-2020 17:29:49 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000294B8 | 0x00029600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.64209 |
.rdata | 0x0002B000 | 0x000090E4 | 0x00009200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.87187 |
.data | 0x00035000 | 0x00010D24 | 0x00001E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.93505 |
.rsrc | 0x00046000 | 0x00003200 | 0x00003200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.8941 |
.reloc | 0x0004A000 | 0x00002BCE | 0x00002C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 5.34541 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.17909 | 1244 | UNKNOWN | UNKNOWN | RT_MANIFEST |
101 | 3.19761 | 302 | UNKNOWN | English - United States | RT_DIALOG |
1001 | 1.91924 | 20 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
KERNEL32.dll |
USER32.dll |
ole32.dll |
Total processes
40
Monitored processes
4
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1172 | C:\Windows\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\system32\icacls.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2128 | c:\PROGRA~1\java\JRE18~1.0_2\bin\java.exe -version | c:\PROGRA~1\java\JRE18~1.0_2\bin\java.exe | — | error422(1).exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 3404 | C:\Users\admin\AppData\Local\Temp\i4jdel0.exe i4j4798473533565837167.tmp | C:\Users\admin\AppData\Local\Temp\i4jdel0.exe | — | error422(1).exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
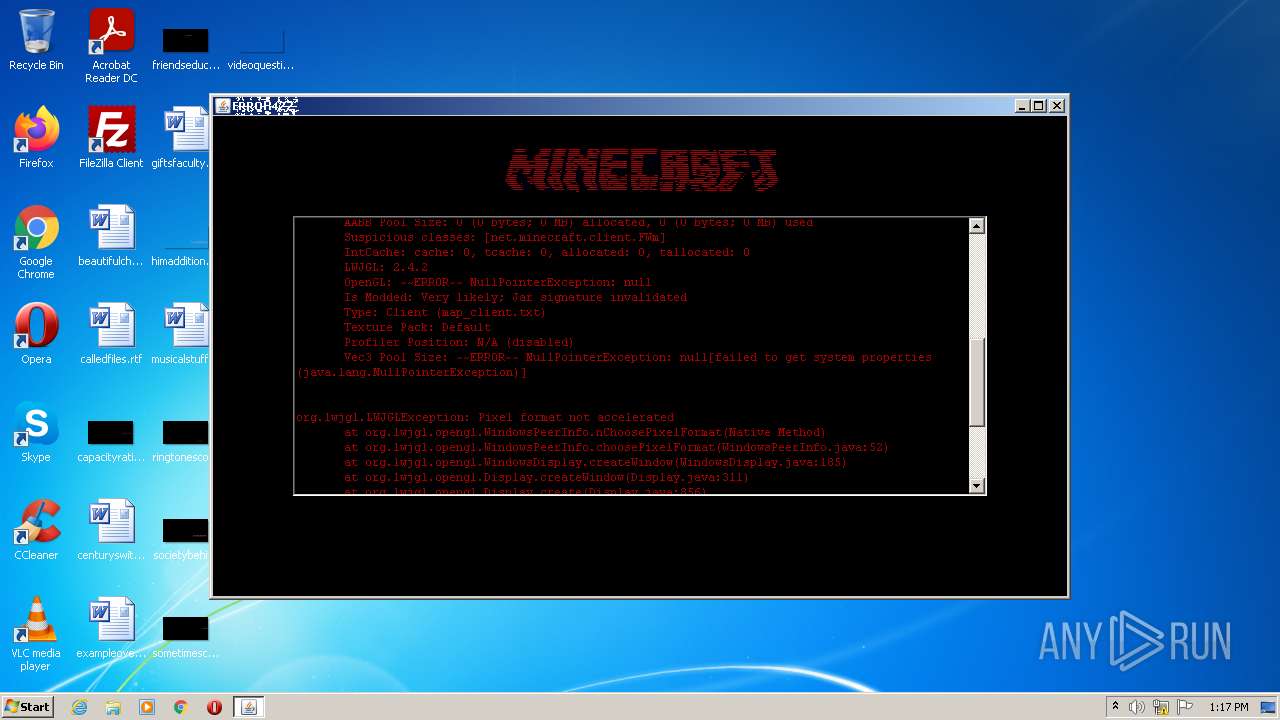
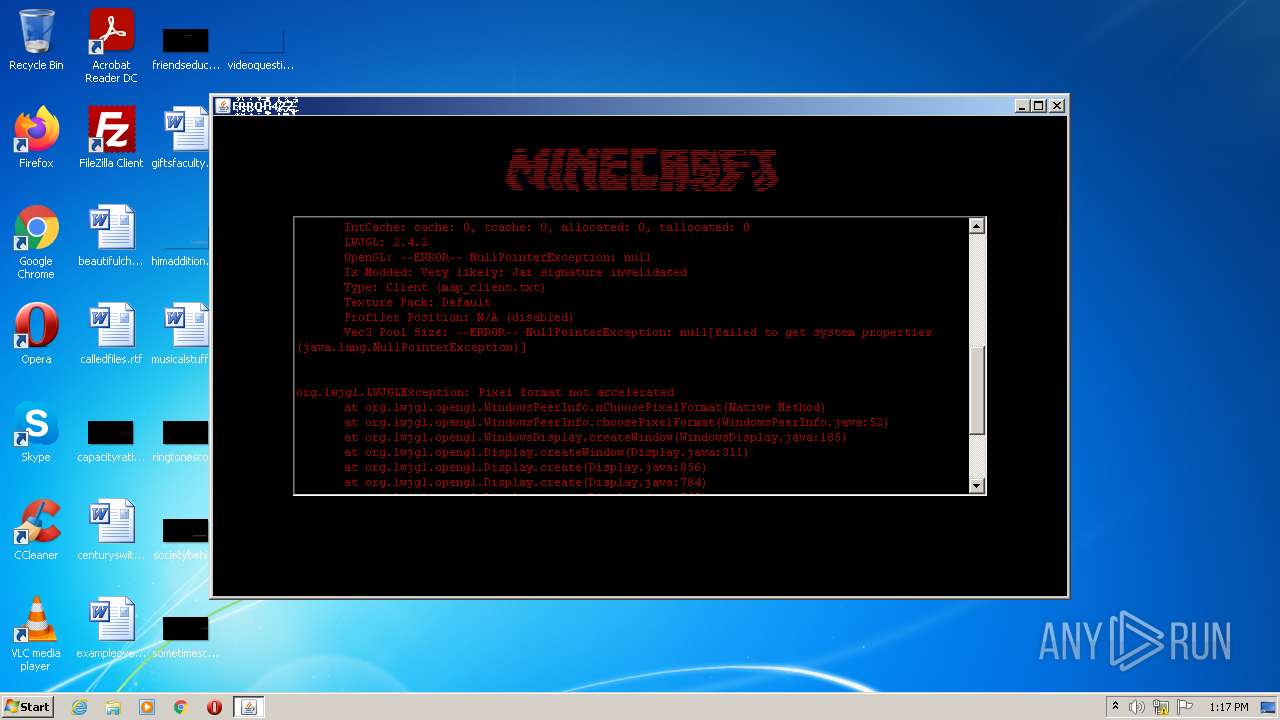
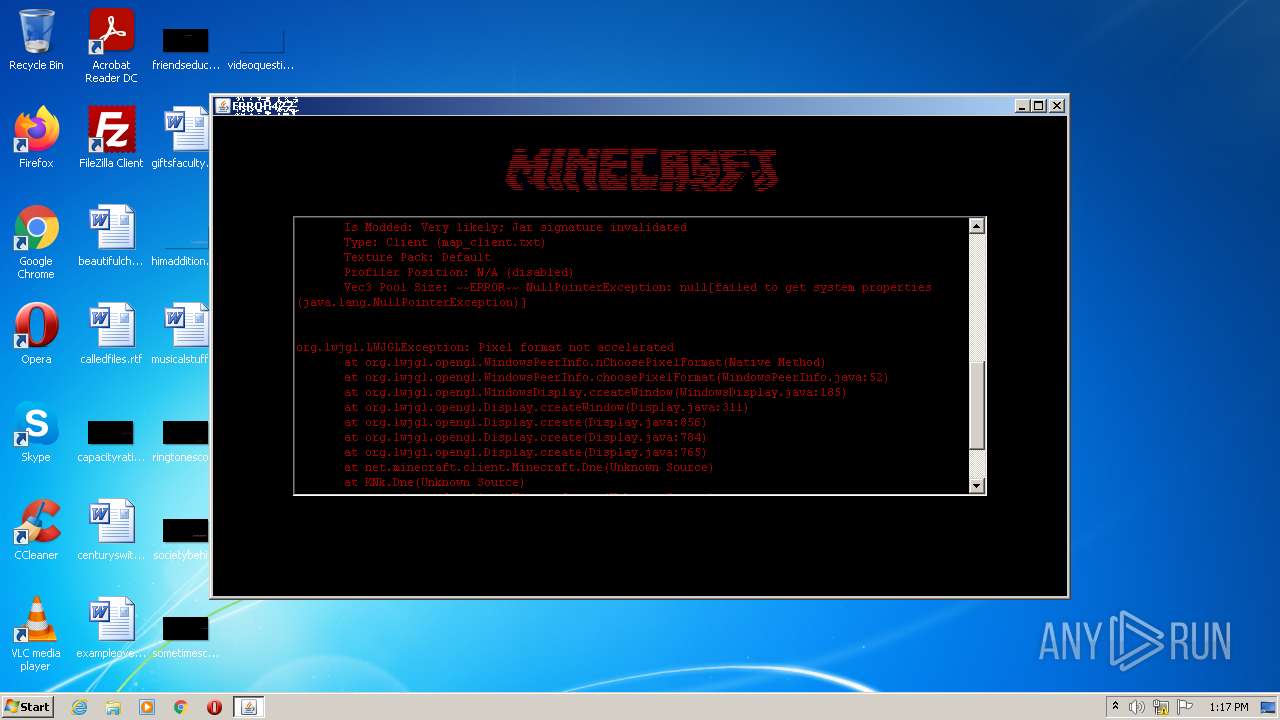
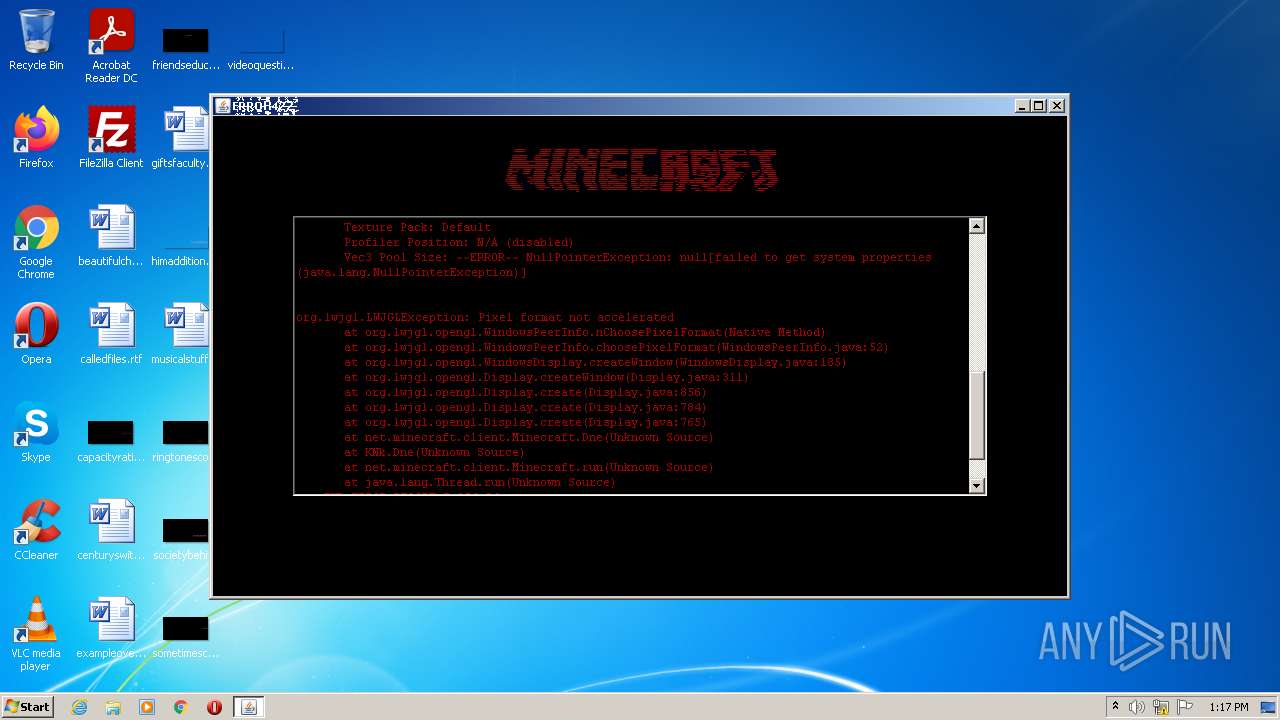
| 4020 | "C:\Users\admin\AppData\Local\Temp\error422(1).exe" | C:\Users\admin\AppData\Local\Temp\error422(1).exe | Explorer.EXE | ||||||||||||
User: admin Company: ������������� Integrity Level: MEDIUM Description: ������������� Exit code: 1 Version: ������������� Modules
| |||||||||||||||
Total events
606
Read events
603
Write events
3
Delete events
0
Modification events
| (PID) Process: | (4020) error422(1).exe | Key: | HKEY_CURRENT_USER\Software\ej-technologies\exe4j\jvms\c:/program files/java/jre1.8.0_271/bin/java.exe |
| Operation: | write | Name: | LastWriteTime |
Value: 7D3ADFE380B1D601 | |||
| (PID) Process: | (4020) error422(1).exe | Key: | HKEY_CURRENT_USER\Software\ej-technologies\exe4j\jvms\c:/program files/java/jre1.8.0_271/bin/java.exe |
| Operation: | write | Name: | Version |
Value: 1.8.0_271 | |||
| (PID) Process: | (4020) error422(1).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: error422(1).exe | |||
Executable files
4
Suspicious files
2
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4020 | error422(1).exe | C:\Users\admin\AppData\Roaming\.minecraft\output-client.log | text | |
MD5:— | SHA256:— | |||
| 2128 | java.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:— | SHA256:— | |||
| 4020 | error422(1).exe | C:\Users\admin\AppData\Local\Temp\imageio457550253217417281.tmp | image | |
MD5:E56ED7F45EAC4C06C03EF9A97FA7062C | SHA256:19984A674BA9543C13DBE21E9863979C27C2BF89C00124761D13C9D10140675A | |||
| 4020 | error422(1).exe | C:\Users\admin\AppData\Local\Temp\e4j60AB.tmp_dir1640611004\exe4jlib.jar | java | |
MD5:D407EF2DD7A82C3733195879498D8E60 | SHA256:8ACCA75F6564DE61A996523C6A4E35273DCC88EE2136811A37299FF86B757539 | |||
| 4020 | error422(1).exe | C:\Users\admin\.JarClassLoader | text | |
MD5:— | SHA256:— | |||
| 4020 | error422(1).exe | C:\Users\admin\AppData\Local\Temp\i4j4798473533565837167.tmp | binary | |
MD5:— | SHA256:— | |||
| 4020 | error422(1).exe | C:\Users\admin\AppData\Local\Temp\e4j6139.tmp | text | |
MD5:04C435364568AB98120F802C798CFD68 | SHA256:7A7FE5291BA42E11E8FA94839E219AB65E3B1411244ECDEFA4222CC60A63ED61 | |||
| 4020 | error422(1).exe | C:\Users\admin\AppData\Local\Temp\JarClassLoader\natives_lwjgl.dll.7080674797825272039.tmp | executable | |
MD5:517D0F050EBBF8A7D2C6A4DEF78218DD | SHA256:A81E22E91C831BF3D60569B6A1D9B0E9BAB283E20BE819DA8117DCBB731E07A2 | |||
| 4020 | error422(1).exe | C:\Users\admin\AppData\Local\Temp\e4j60AB.tmp_dir1640611004\ERROR422.jar | compressed | |
MD5:D16C74868F44ED001FC408F96BD973D0 | SHA256:6B8974F050CE043F81671728916999ABE7C2B724616BB925069BA60C9D8FA646 | |||
| 4020 | error422(1).exe | C:\Users\admin\AppData\Local\Temp\e4j60AB.tmp_dir1640611004\i4jdel.exe | executable | |
MD5:2BDF444EC496C783D7996C4FF76B52D5 | SHA256:0EC8E67837FAAF62653B1A28CEA98008A27FA29A70C28A58FD123C3BCE4C3238 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report