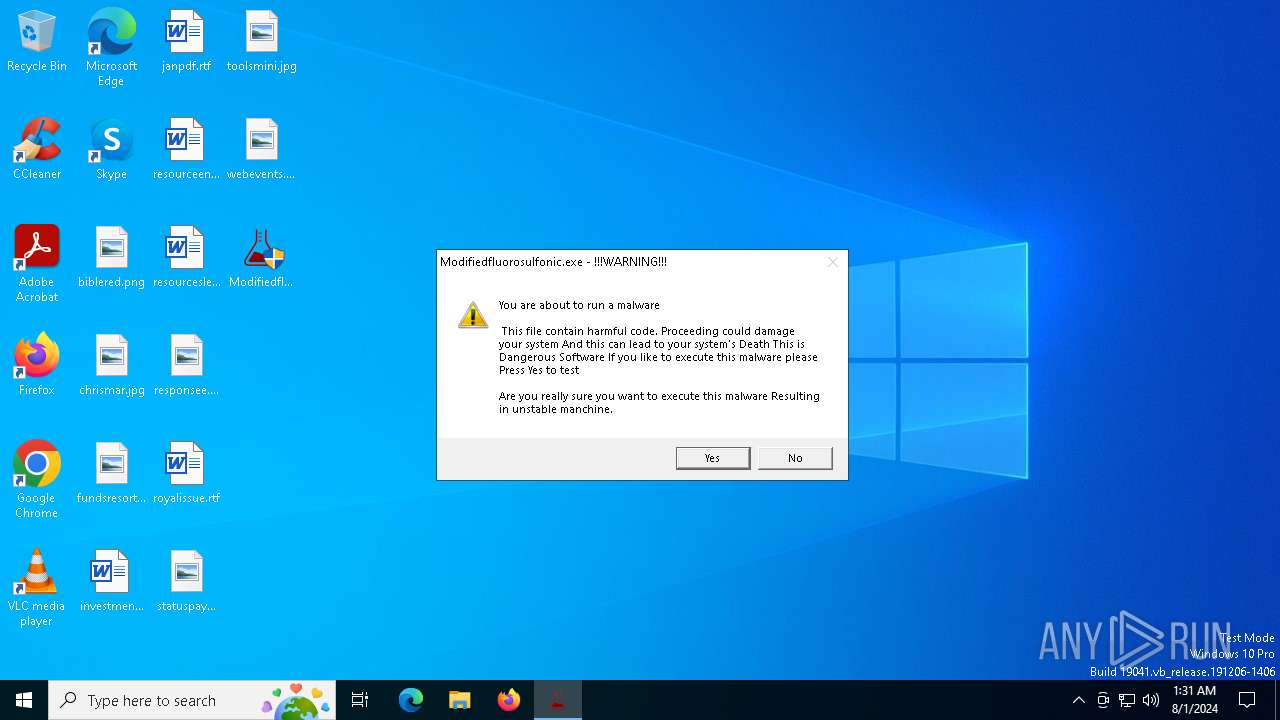
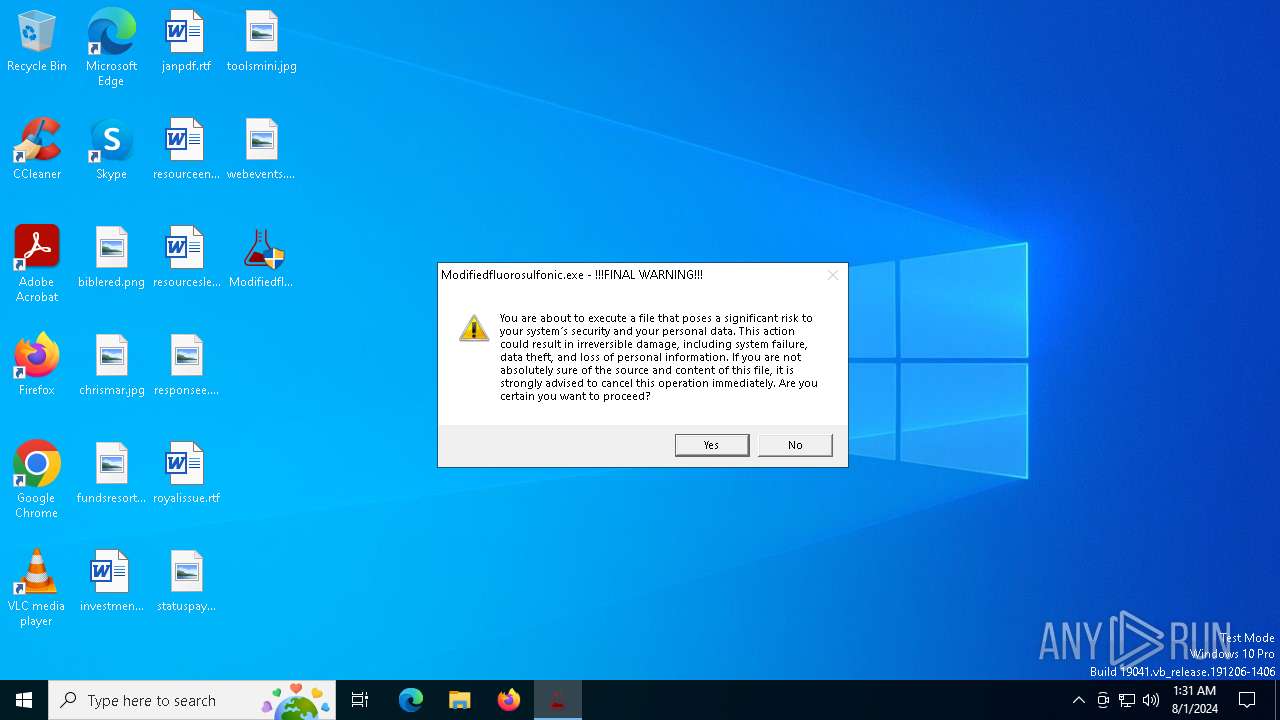
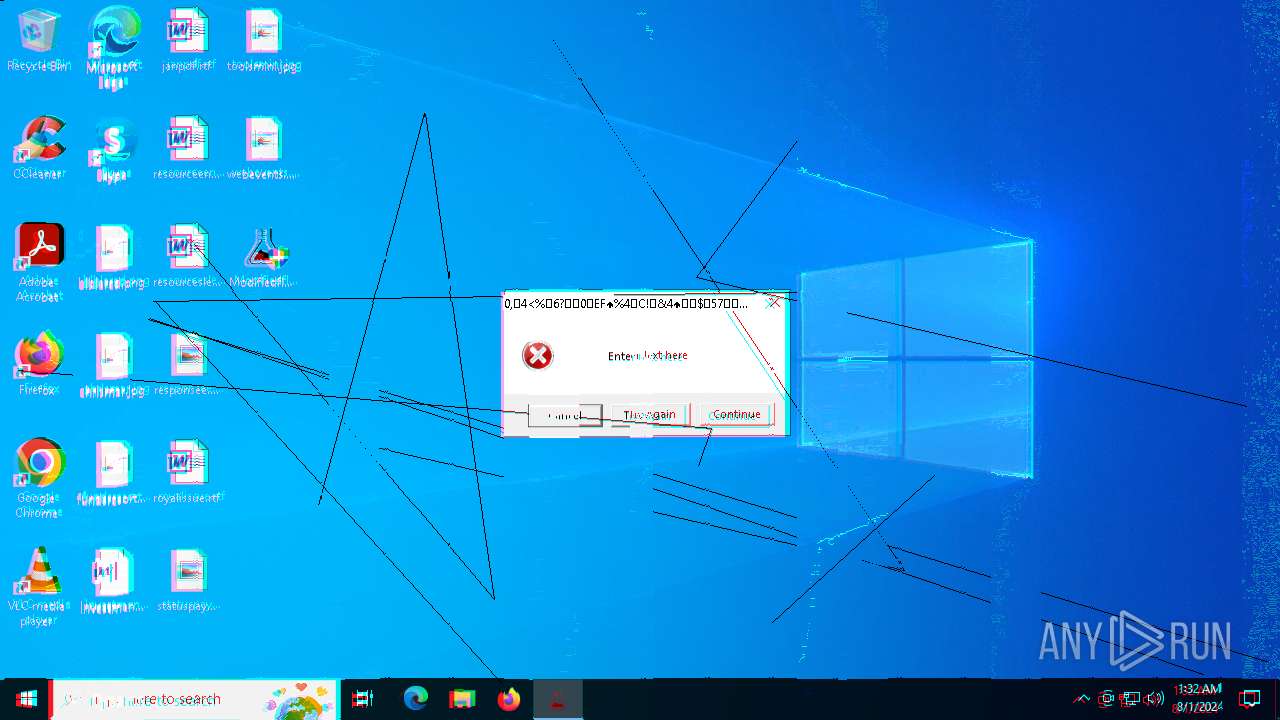
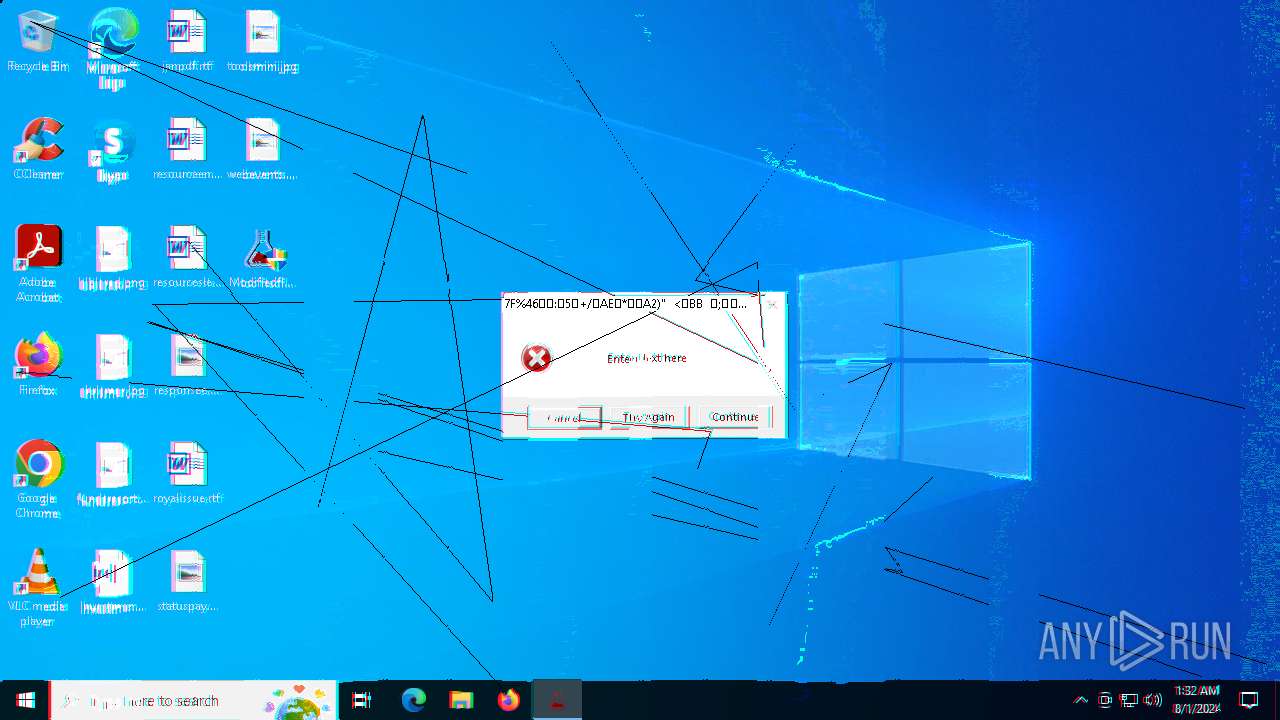
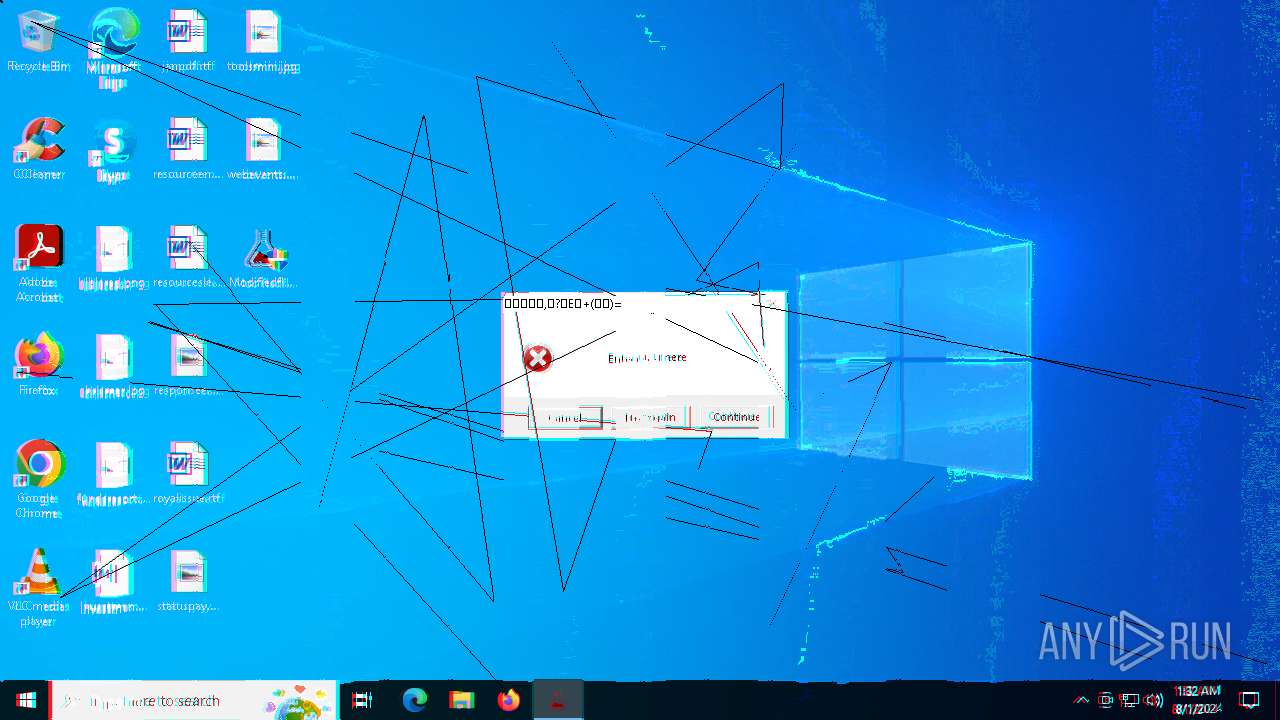
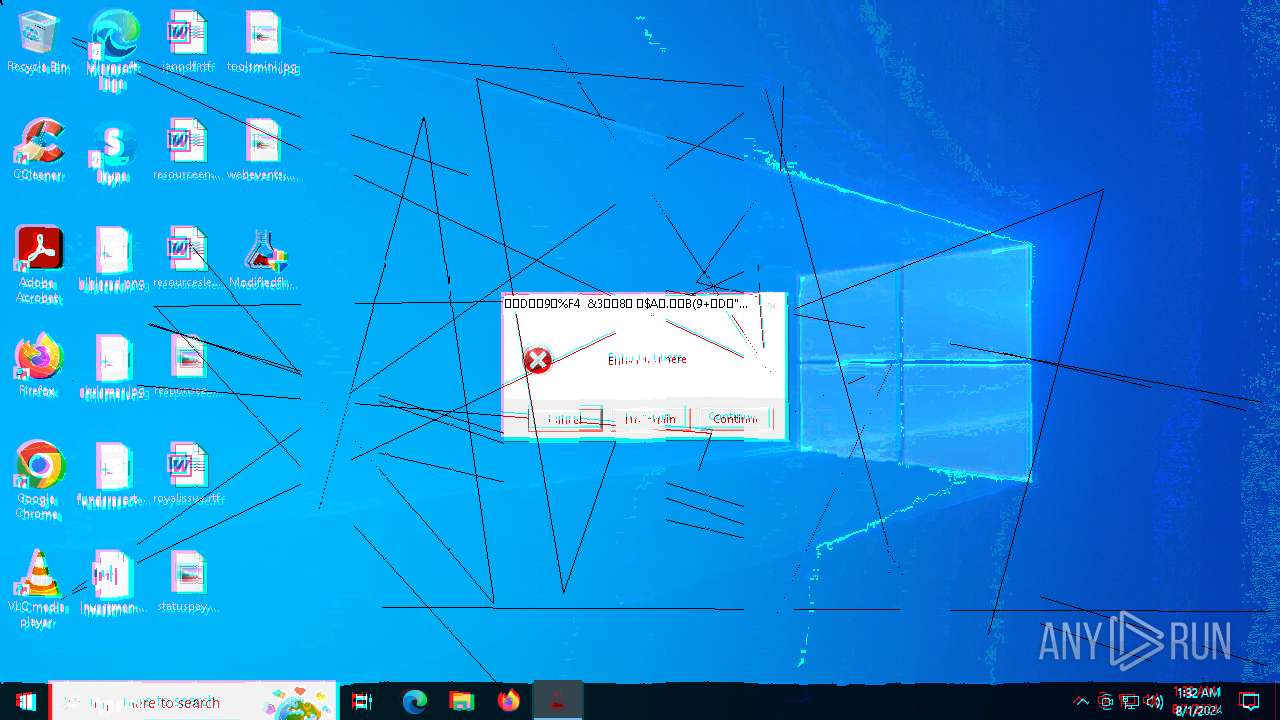
| File name: | Modifiedfluorosulfonic.exe |
| Full analysis: | https://app.any.run/tasks/623486f1-27f7-4e5c-b3dd-74d5efd3d864 |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2024, 01:31:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C6E20E61971DBCC0698BD2EDBD2CCAC1 |
| SHA1: | 71E0FEA5452B2899E2AA48E125CE3E556A36396C |
| SHA256: | 770F96B6B603F11CD3271E05B01393B9952CF80D6EDEA1E9ACB63E96EB848F0A |
| SSDEEP: | 6144:t4ZIanUzmIALbkcJOrmcZVwc6Qyss72XJiWIzdzsE/ZrTrX:tiUEdJEmcoc64tZqzdZrTrX |
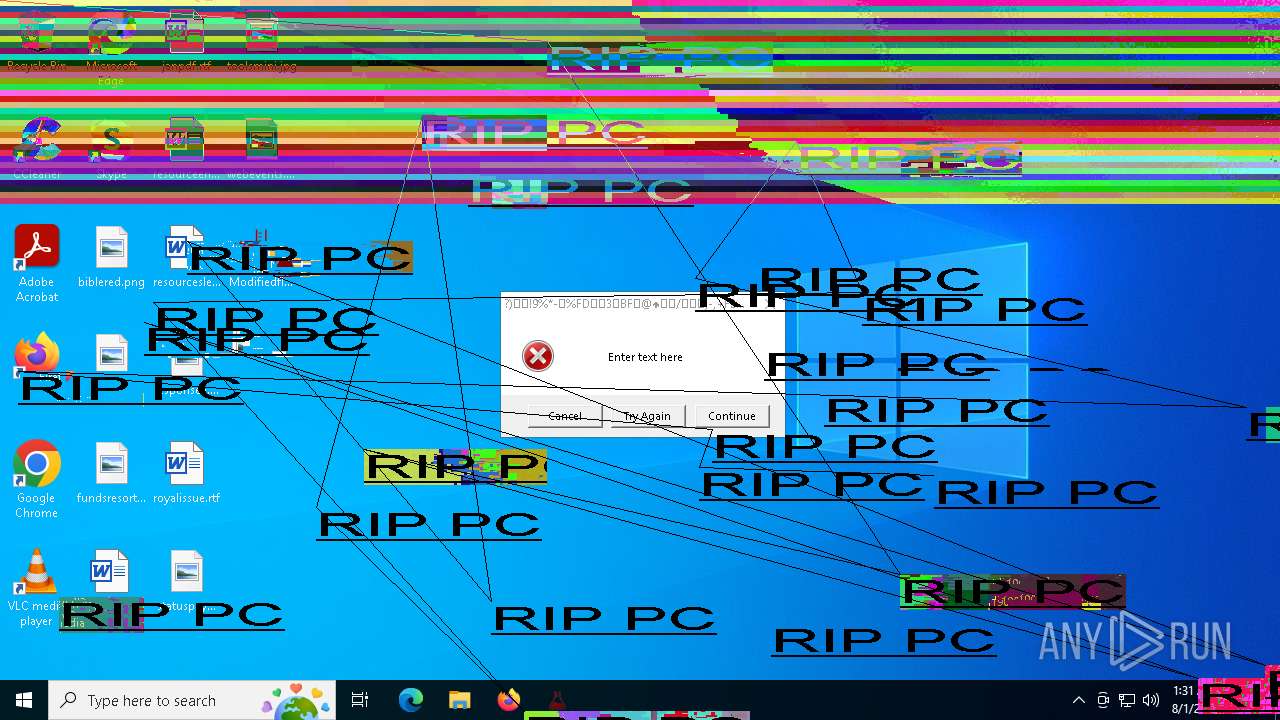
MALICIOUS
Drops the executable file immediately after the start
- Modifiedfluorosulfonic.exe (PID: 6584)
Disables the Run the Start menu
- reg.exe (PID: 2268)
Disables the LogOff the Start menu
- reg.exe (PID: 6204)
SUSPICIOUS
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6292)
- cmd.exe (PID: 3076)
- cmd.exe (PID: 5888)
- cmd.exe (PID: 6244)
- cmd.exe (PID: 2584)
- cmd.exe (PID: 6392)
Uses ATTRIB.EXE to modify file attributes
- Modifiedfluorosulfonic.exe (PID: 6584)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7124)
Starts CMD.EXE for commands execution
- Modifiedfluorosulfonic.exe (PID: 6584)
- forfiles.exe (PID: 8868)
Reads security settings of Internet Explorer
- Modifiedfluorosulfonic.exe (PID: 6584)
- wmplayer.exe (PID: 8540)
- FlashPlayerApp.exe (PID: 9204)
Creates file in the systems drive root
- bootcfg.exe (PID: 4784)
Uses ICACLS.EXE to modify access control lists
- Modifiedfluorosulfonic.exe (PID: 6584)
Executes as Windows Service
- VSSVC.exe (PID: 2960)
- vds.exe (PID: 7576)
- dllhost.exe (PID: 1172)
- msdtc.exe (PID: 8096)
Uses DRIVERQUERY.EXE to obtain a list of installed device drivers
- Modifiedfluorosulfonic.exe (PID: 6584)
Reads the date of Windows installation
- wmplayer.exe (PID: 8540)
- Modifiedfluorosulfonic.exe (PID: 6584)
Using 'findstr.exe' to search for text patterns in files and output
- Modifiedfluorosulfonic.exe (PID: 6584)
Searches and executes a command on selected files
- forfiles.exe (PID: 8868)
Process uses IPCONFIG to get network configuration information
- Modifiedfluorosulfonic.exe (PID: 6584)
Uses RUNDLL32.EXE to load library
- iscsicpl.exe (PID: 6248)
Uses NSLOOKUP.EXE to check DNS info
- Modifiedfluorosulfonic.exe (PID: 6584)
Suspicious use of NETSH.EXE
- Modifiedfluorosulfonic.exe (PID: 6584)
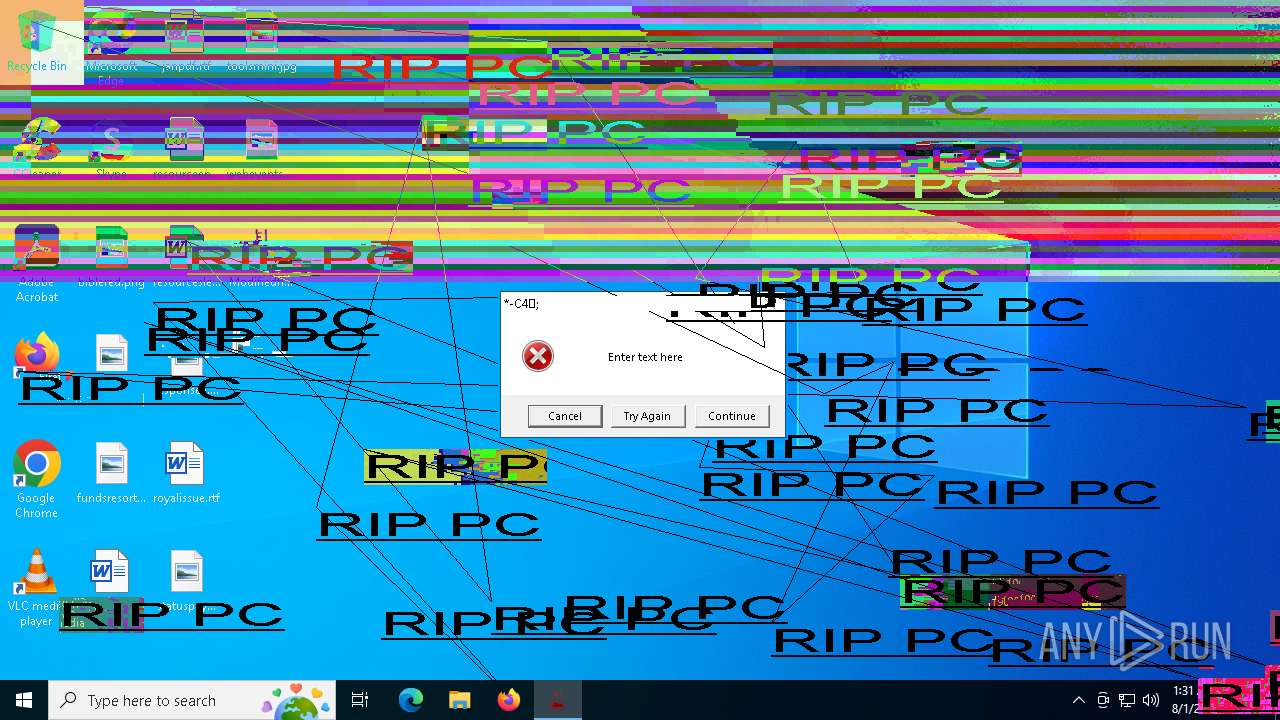
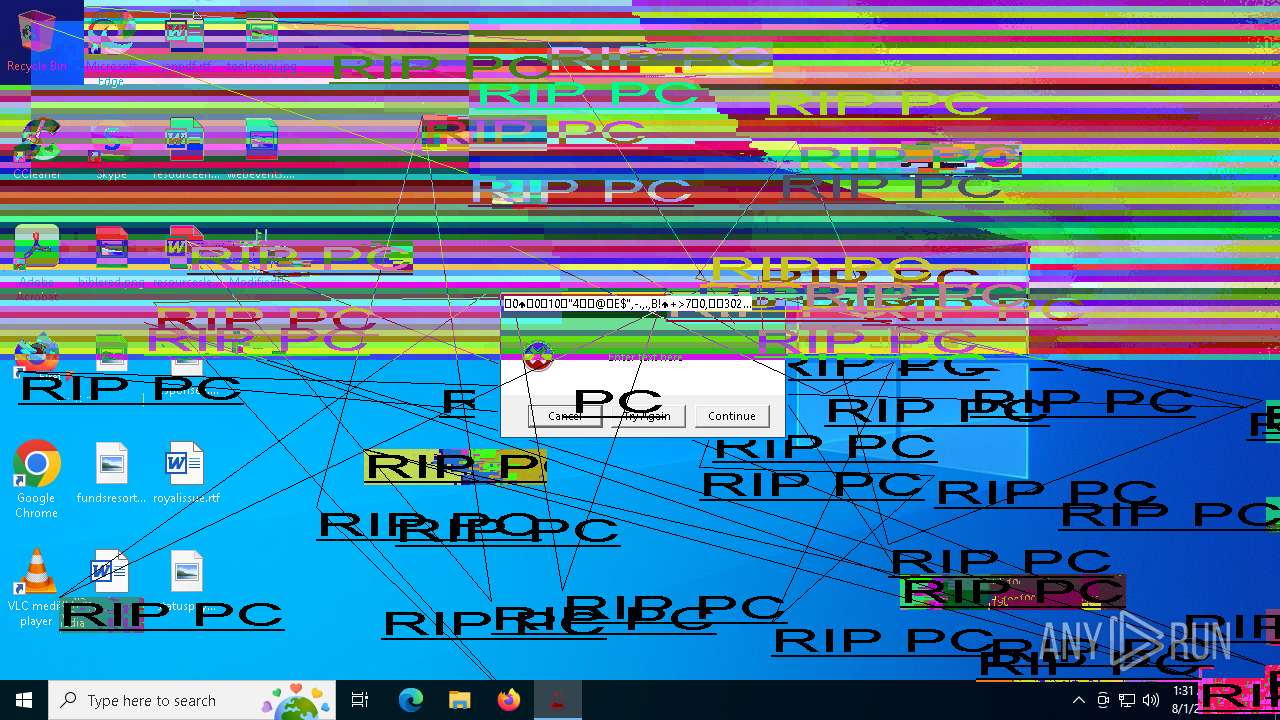
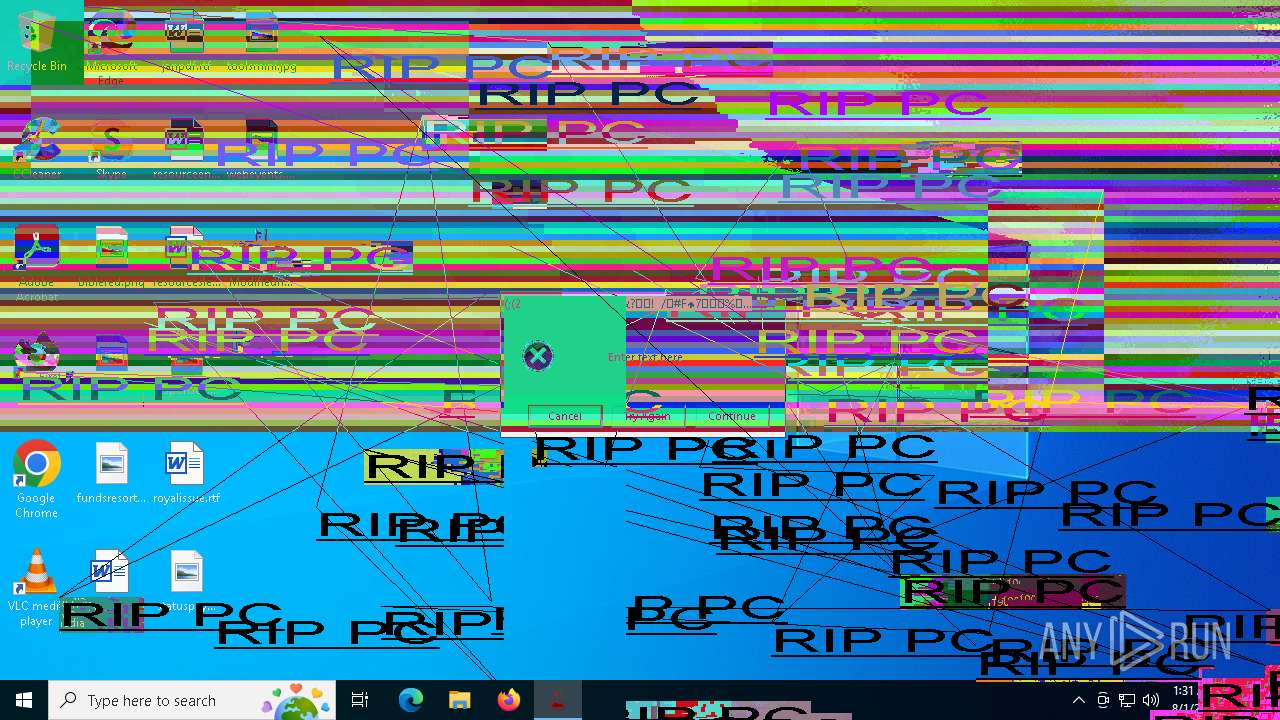
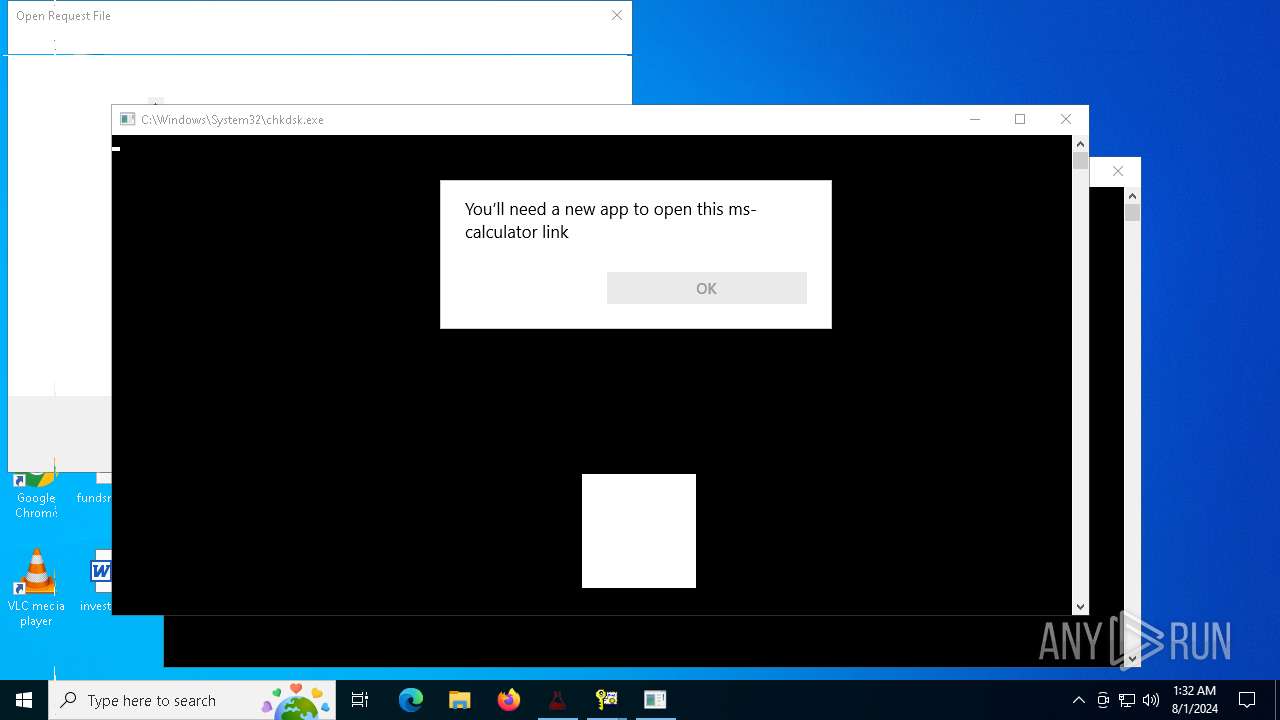
Start notepad (likely ransomware note)
- Modifiedfluorosulfonic.exe (PID: 6584)
Application launched itself
- OneDriveSetup.exe (PID: 8016)
Executable content was dropped or overwritten
- OneDriveSetup.exe (PID: 10844)
Process drops legitimate windows executable
- OneDriveSetup.exe (PID: 10844)
Uses powercfg.exe to modify the power settings
- Modifiedfluorosulfonic.exe (PID: 6584)
INFO
Reads the computer name
- Modifiedfluorosulfonic.exe (PID: 6584)
- wmplayer.exe (PID: 8540)
- setup_wm.exe (PID: 8596)
- extrac32.exe (PID: 8876)
- FlashPlayerApp.exe (PID: 9204)
- agentactivationruntimestarter.exe (PID: 7084)
Checks supported languages
- Modifiedfluorosulfonic.exe (PID: 6584)
- curl.exe (PID: 5468)
- wmplayer.exe (PID: 8540)
- setup_wm.exe (PID: 8596)
- expand.exe (PID: 5400)
- extrac32.exe (PID: 8876)
- FlashPlayerApp.exe (PID: 9204)
- agentactivationruntimestarter.exe (PID: 7084)
- appidtel.exe (PID: 6336)
Uses BITSADMIN.EXE
- Modifiedfluorosulfonic.exe (PID: 6584)
Reads security settings of Internet Explorer
- calc.exe (PID: 2796)
- OpenWith.exe (PID: 5056)
- certreq.exe (PID: 6916)
- cleanmgr.exe (PID: 6376)
- ComputerDefaults.exe (PID: 3844)
- mmc.exe (PID: 6340)
- DpiScaling.exe (PID: 7780)
- explorer.exe (PID: 8064)
- explorer.exe (PID: 7184)
- unregmp2.exe (PID: 8620)
- mmc.exe (PID: 8432)
- mmc.exe (PID: 8492)
- LaunchTM.exe (PID: 6860)
- Magnify.exe (PID: 9508)
Disables trace logs
- cmdl32.exe (PID: 6868)
- cmstp.exe (PID: 4692)
- cmmon32.exe (PID: 6232)
- dialer.exe (PID: 7308)
Reads Microsoft Office registry keys
- ComputerDefaults.exe (PID: 3844)
- explorer.exe (PID: 8064)
- explorer.exe (PID: 7184)
Create files in a temporary directory
- ddodiag.exe (PID: 3684)
- setup_wm.exe (PID: 8596)
Creates files in the program directory
- mmc.exe (PID: 6340)
- mmc.exe (PID: 8492)
- unregmp2.exe (PID: 8700)
Checks transactions between databases Windows and Oracle
- dllhost.exe (PID: 1172)
- msdtc.exe (PID: 8096)
- mmc.exe (PID: 6340)
Process checks computer location settings
- wmplayer.exe (PID: 8540)
- setup_wm.exe (PID: 8596)
- Modifiedfluorosulfonic.exe (PID: 6584)
Reads Environment values
- setup_wm.exe (PID: 8596)
Creates files or folders in the user directory
- FlashPlayerApp.exe (PID: 9204)
- unregmp2.exe (PID: 8700)
Drops the executable file immediately after the start
- OneDriveSetup.exe (PID: 10844)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:07:31 11:37:56+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 152064 |
| InitializedDataSize: | 432128 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa38d |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.6.6.6 |
| ProductVersionNumber: | 6.6.6.6 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Process default |
| CharacterSet: | Unicode |
| CompanyName: | "NILL |
| FileDescription: | NULL |
| FileVersion: | NULL |
| InternalName: | NULL |
| LegalCopyright: | NULL |
| OriginalFileName: | NULL |
| ProductName: | NULL |
| ProductVersion: | NULL |
Total processes
488
Monitored processes
335
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | chkdsk.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | "C:\Windows\System32\CredentialUIBroker.exe" | C:\Windows\SysWOW64\CredentialUIBroker.exe | — | Modifiedfluorosulfonic.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Credential Manager UI Host Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 840 | "C:\Windows\System32\cscript.exe" | C:\Windows\SysWOW64\cscript.exe | — | Modifiedfluorosulfonic.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 872 | "C:\WINDOWS\SysWOW64\ctfmon.exe" | C:\Windows\SysWOW64\ctfmon.exe | — | Modifiedfluorosulfonic.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CTF Loader Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 944 | "C:\Windows\System32\PresentationHost.exe" | C:\Windows\SysWOW64\PresentationHost.exe | — | Modifiedfluorosulfonic.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Presentation Foundation Host Exit code: 1 Version: 4.0.41210.0 built by: Main | |||||||||||||||
| 1076 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1136 | "C:\Windows\System32\powercfg.exe" | C:\Windows\SysWOW64\powercfg.exe | — | Modifiedfluorosulfonic.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Power Settings Command-Line Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1136 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rasautou.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1152 | "C:\Windows\System32\ctfmon.exe" | C:\Windows\SysWOW64\ctfmon.exe | — | Modifiedfluorosulfonic.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CTF Loader Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1172 | C:\WINDOWS\system32\dllhost.exe /Processid:{02D4B3F1-FD88-11D1-960D-00805FC79235} | C:\Windows\System32\dllhost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: COM Surrogate Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
59 973
Read events
59 663
Write events
303
Delete events
7
Modification events
| (PID) Process: | (5740) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\system |
| Operation: | write | Name: | DisableTaskMgr |
Value: 1 | |||
| (PID) Process: | (2268) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoRun |
Value: 1 | |||
| (PID) Process: | (5540) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | HideFastUserSwitching |
Value: 1 | |||
| (PID) Process: | (6204) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoLogoff |
Value: 1 | |||
| (PID) Process: | (6380) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\system |
| Operation: | write | Name: | DisableLockWorkstation |
Value: 1 | |||
| (PID) Process: | (6584) Modifiedfluorosulfonic.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\system |
| Operation: | write | Name: | DisableRegistryTools |
Value: 1 | |||
| (PID) Process: | (6584) Modifiedfluorosulfonic.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Windows\System |
| Operation: | write | Name: | DisableCMD |
Value: 2 | |||
| (PID) Process: | (6584) Modifiedfluorosulfonic.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6584) Modifiedfluorosulfonic.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6584) Modifiedfluorosulfonic.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
68
Suspicious files
20
Text files
48
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6376 | cleanmgr.exe | C:\Windows\System32\LogFiles\setupcln\setupact.log | — | |
MD5:— | SHA256:— | |||
| 7576 | vds.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 6376 | cleanmgr.exe | C:\Windows\System32\LogFiles\setupcln\diagwrn.xml | text | |
MD5:E3BE7F81065AEA7BB1083575E20E4EB2 | SHA256:3D37E117FB659278A3750C38CC6FFC48331B3034C0C1142C11AAEDA880AA7F17 | |||
| 6376 | cleanmgr.exe | C:\Windows\System32\LogFiles\setupcln\setuperr.log | text | |
MD5:72B0157C370C90DD955C7A980B69F890 | SHA256:5CF4FE52B8E16E3507AB4C9C6FD5F3650044D0765EBFA71963853964912E6EF3 | |||
| 6376 | cleanmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\d3fe7cdcb51a5ef5\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 6376 | cleanmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 6376 | cleanmgr.exe | C:\Windows\System32\LogFiles\setupcln\diagerr.xml | text | |
MD5:A0C22C9F1D7FADAAADABF0C83A1F4145 | SHA256:B39BD2E8B9D0CAE257127FE86F4CDAD8A730B923E11CF7C480C441D51E49D3B8 | |||
| 6376 | cleanmgr.exe | C:\Users\admin\AppData\Local\Packages\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\AC\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 6376 | cleanmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\ecbf0d5a3a180bb\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 3684 | ddodiag.exe | C:\Windows\INF\machine.PNF | binary | |
MD5:3CE954C590511BD132F10B4BD35993C1 | SHA256:95B85E032039779021F2A13E6A58137174BDA4E79D40940CED33EEF6E4BBB44C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
20
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 404 | 95.100.146.34:443 | https://www.bing.com/RelatedSearch?addfeaturesnoexpansion=relatedsearch&mkt=en-US | unknown | — | — | unknown |
— | — | GET | 404 | 184.30.129.84:443 | https://cxcs.microsoft.net/api/settings/en-US/xml/settings-tipset?release=20h1&sku=Professional&platform=desktop | unknown | html | 26 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1664 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3520 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1028 | SystemSettings.exe | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | unknown |
1028 | SystemSettings.exe | 184.30.129.84:443 | cxcs.microsoft.net | AKAMAI-AS | US | unknown |
7412 | dasHost.exe | 192.168.100.255:3289 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
cxcs.microsoft.net |
| whitelisted |
win1910.ipv6.microsoft.com |
| whitelisted |
5.6.5.f.e.b.3.d.f.9.3.e.d.f.e.0.0.0.0.0.0.0.0.0.0.0.0.0.0.8.e.f.ip6.arpa |
| unknown |
2.100.168.192.in-addr.arpa |
| whitelisted |
4.b.7.8.3.9.8.0.6.f.6.5.7.d.8.8.0.0.0.0.0.0.0.0.0.0.0.0.0.8.e.f.ip6.arpa |
| unknown |
watson.events.data.microsoft.com |
| whitelisted |
pnrpv2.ipv6.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
mmc.exe | ViewerConfigPath = 'C:\ProgramData\Microsoft\Event Viewer': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerViewsFolderPath = 'C:\ProgramData\Microsoft\Event Viewer\Views': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerAdminViewsPath = 'C:\ProgramData\Microsoft\Event Viewer\Views\ApplicationViewsRootNode': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerExternalLogsPath = 'C:\ProgramData\Microsoft\Event Viewer\ExternalLogs': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
Dism.exe | PID=7752 TID=7756 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=7752 TID=7756 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=7752 TID=7756 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=7752 TID=7756 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=7752 TID=7756 Loading Provider from location C:\Windows\System32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=7752 TID=7756 Connecting to the provider located at C:\Windows\System32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |