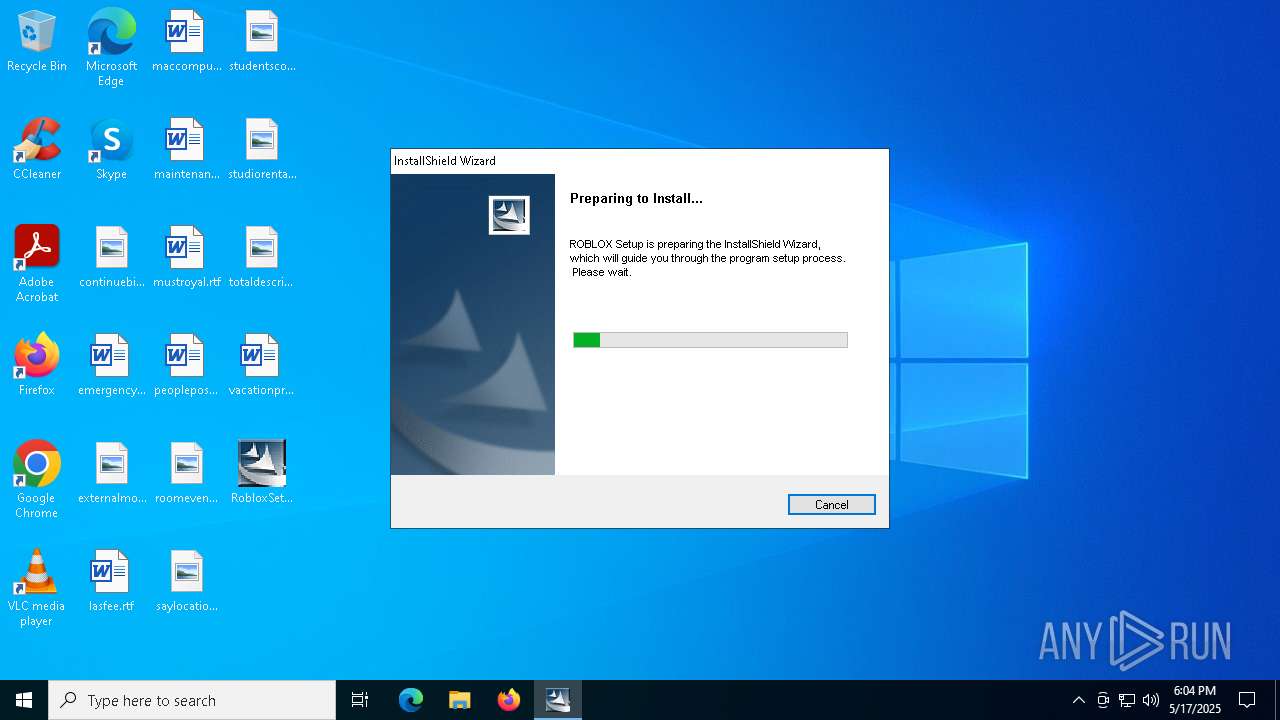
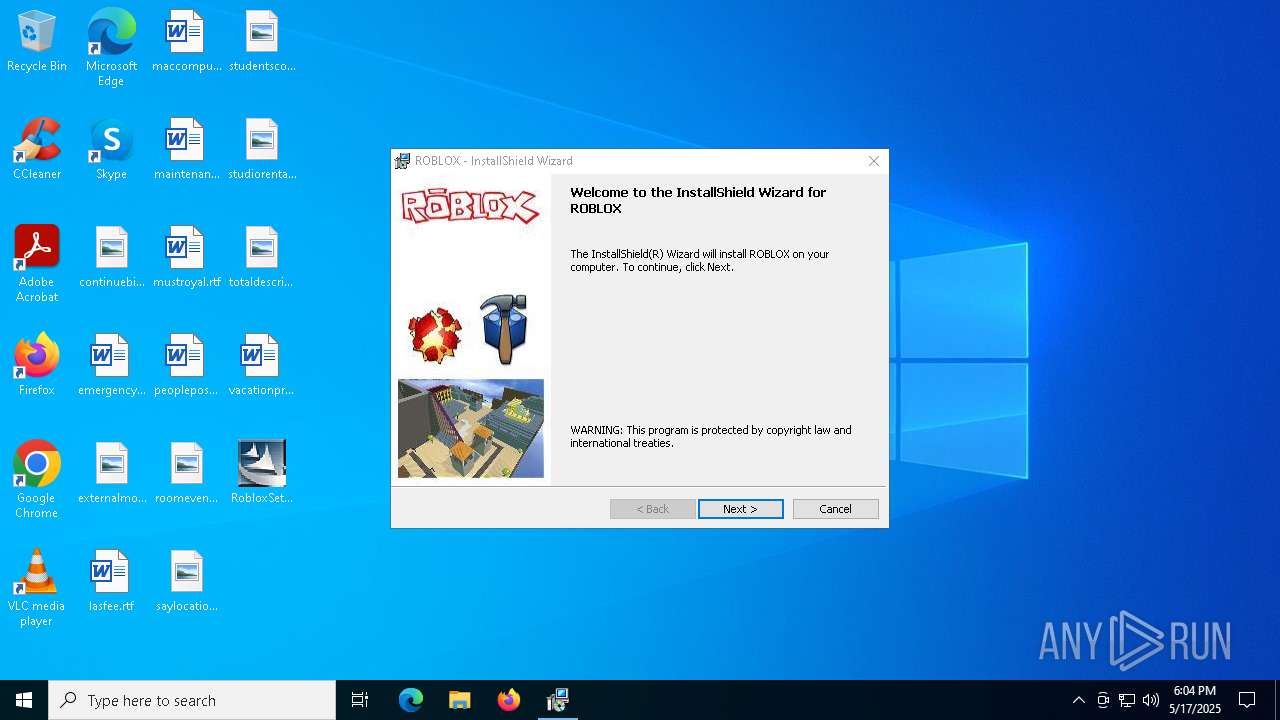
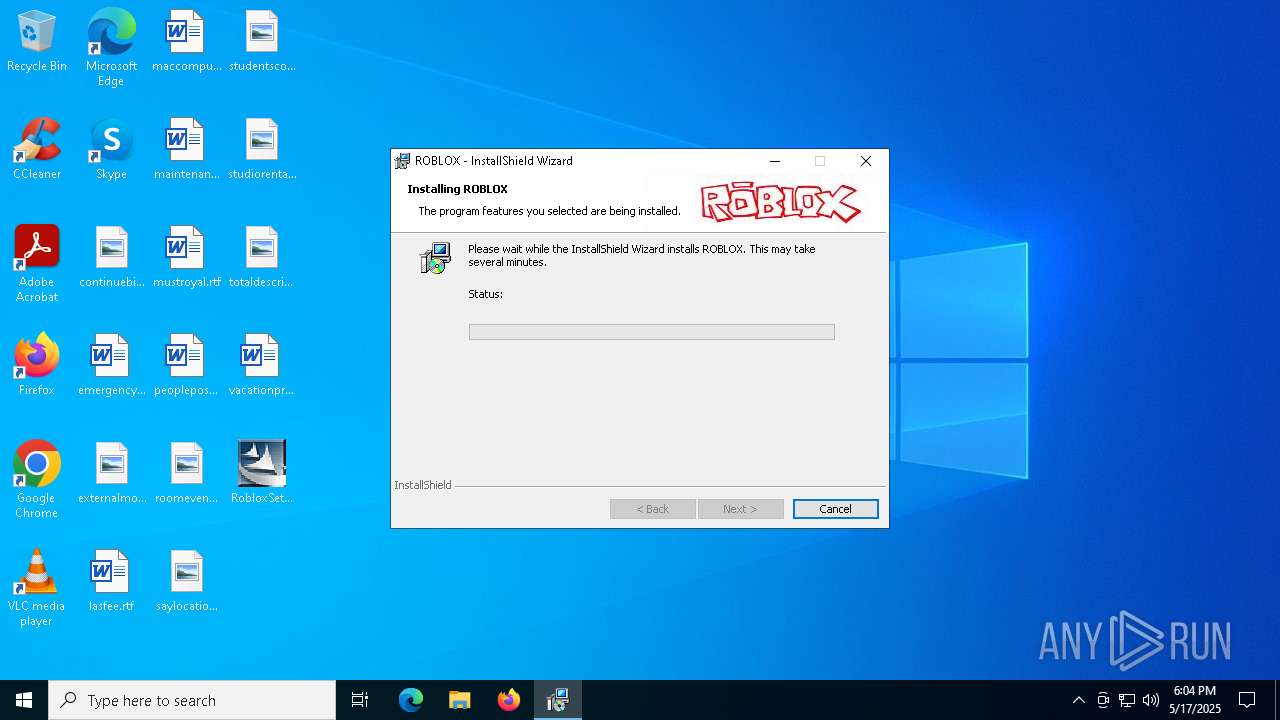
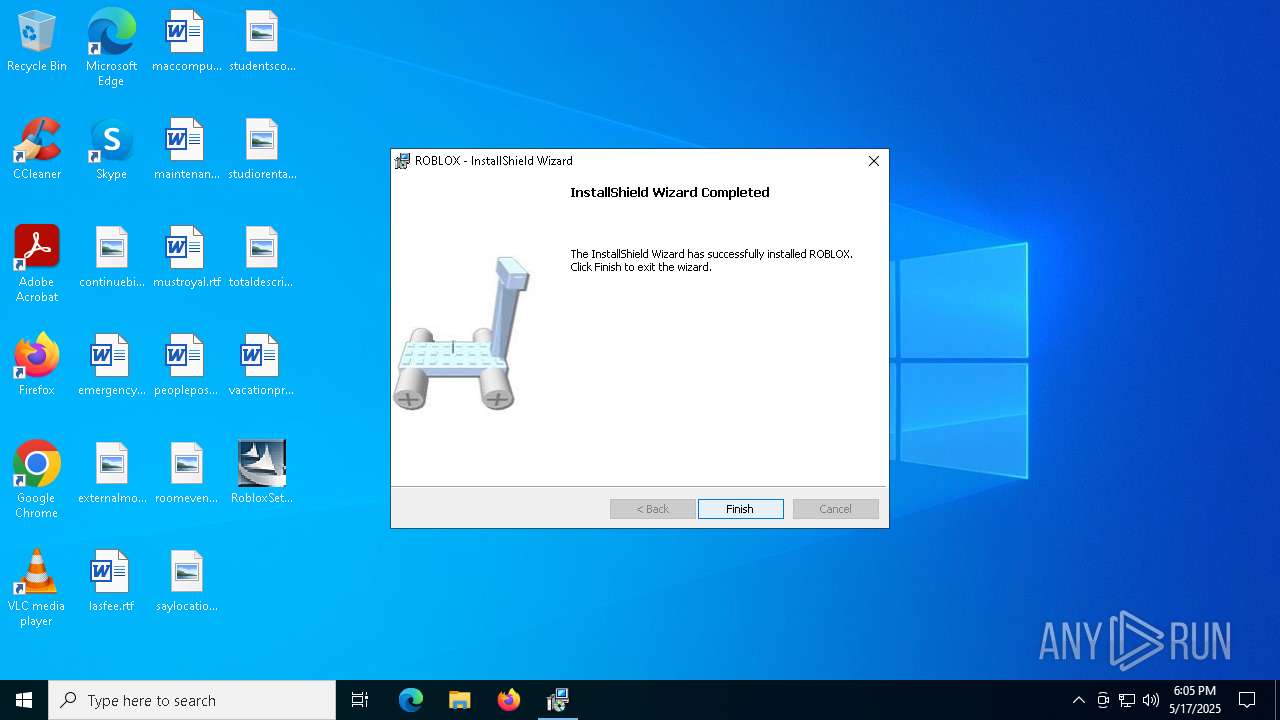
| File name: | RobloxSetup_0.3.696.0January162008.exe |
| Full analysis: | https://app.any.run/tasks/90690863-60c0-4685-a720-688dd7ba74af |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 18:04:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 69E59CE8D92276E7A8A8BEF55217D584 |
| SHA1: | D4F1E4016B2B769402ACF72BE3EB893567361990 |
| SHA256: | 7703501FDF0BB46288EBBFC5EAC6A25A2E0B788EBD2EB9246D3FCE8AA4DFA9B1 |
| SSDEEP: | 196608:d7Rv7vJFZppcPNrJqAMBr08B6ceN1TBcaDBBMygBU4NwuLNvnMBSI:rTxjppArIv08UckTPXMyMRF0II |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 7624)
There is functionality for taking screenshot (YARA)
- RobloxSetup_0.3.696.0January162008.exe (PID: 7388)
The process drops C-runtime libraries
- msiexec.exe (PID: 7448)
- TiWorker.exe (PID: 7152)
Process drops legitimate windows executable
- msiexec.exe (PID: 7448)
- TiWorker.exe (PID: 7152)
Executable content was dropped or overwritten
- TiWorker.exe (PID: 7152)
INFO
Checks supported languages
- RobloxSetup_0.3.696.0January162008.exe (PID: 7388)
- msiexec.exe (PID: 7448)
- msiexec.exe (PID: 7564)
The sample compiled with english language support
- RobloxSetup_0.3.696.0January162008.exe (PID: 7388)
- msiexec.exe (PID: 7412)
- msiexec.exe (PID: 7448)
- TiWorker.exe (PID: 7152)
Reads the computer name
- msiexec.exe (PID: 7564)
- RobloxSetup_0.3.696.0January162008.exe (PID: 7388)
- msiexec.exe (PID: 7448)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7412)
- msiexec.exe (PID: 7448)
Create files in a temporary directory
- RobloxSetup_0.3.696.0January162008.exe (PID: 7388)
Manages system restore points
- SrTasks.exe (PID: 4436)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (36.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (26.6) |
| .exe | | | Win64 Executable (generic) (23.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2007:02:28 22:02:54+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 208896 |
| InitializedDataSize: | 98304 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x28171 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 12.0.0.58851 |
| ProductVersionNumber: | 12.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Roblox Corporation |
| FileDescription: | This installer database contains the logic and data required to install ROBLOX. |
| FileVersion: | 0.3.696.0 |
| InternalName: | Setup |
| LegalCopyright: | Copyright 2005, ROBLOX Corporation |
| OriginalFileName: | Setup.exe |
| ProductName: | ROBLOX |
| ProductVersion: | 0.3.696.0 |
| OLESelfRegister: | - |
Total processes
142
Monitored processes
11
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
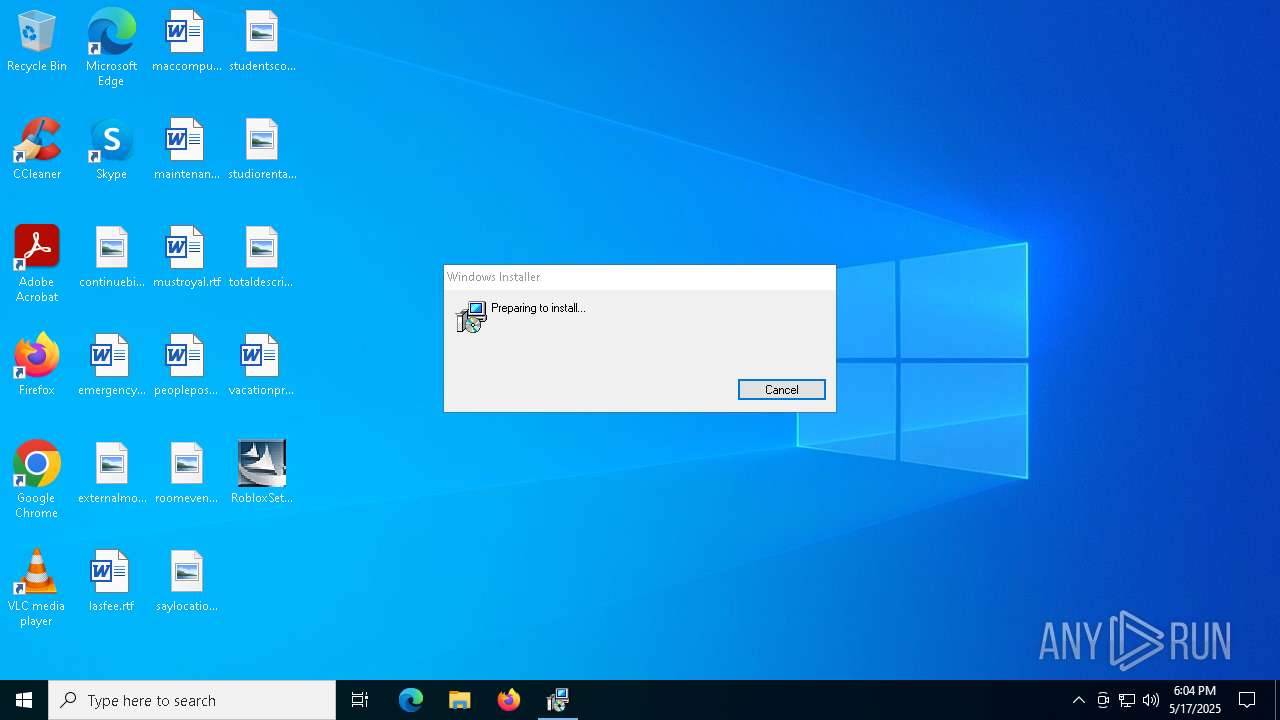
| 2236 | C:\Windows\syswow64\MsiExec.exe -Embedding B28CCBC869C136397844A45BA111230D | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4400 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4436 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5376 | C:\Windows\syswow64\MsiExec.exe -Embedding 2FCA4ABC3E7D7CFC56FDD74E1984434F M Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7152 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7388 | "C:\Users\admin\Desktop\RobloxSetup_0.3.696.0January162008.exe" | C:\Users\admin\Desktop\RobloxSetup_0.3.696.0January162008.exe | — | explorer.exe | |||||||||||
User: admin Company: Roblox Corporation Integrity Level: MEDIUM Description: This installer database contains the logic and data required to install ROBLOX. Exit code: 0 Version: 0.3.696.0 Modules
| |||||||||||||||
| 7412 | MSIEXEC.EXE /i "C:\Users\admin\AppData\Local\Temp\{234AB76F-5408-46DA-A4D1-011882654B14}\ROBLOX.msi" SETUPEXEDIR="C:\Users\admin\Desktop" | C:\Windows\SysWOW64\msiexec.exe | RobloxSetup_0.3.696.0January162008.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7448 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7536 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7564 | C:\Windows\syswow64\MsiExec.exe -Embedding 32FBF96036171B4D874399709021DD31 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 647
Read events
7 062
Write events
538
Delete events
47
Modification events
| (PID) Process: | (7448) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000007876682B56C7DB01181D0000B81D0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7448) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000007876682B56C7DB01181D0000B81D0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7448) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 480000000000000082AC252B56C7DB01181D0000B81D0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7448) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 480000000000000082AC252B56C7DB01181D0000B81D0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7448) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000005BDA6A2B56C7DB01181D0000B81D0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7448) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000288E6F2B56C7DB01181D0000B81D0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7448) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 480000000000000060C2E62B56C7DB01181D0000B81D0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7448) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000AA25E92B56C7DB01181D0000241E0000E80300000100000000000000000000007124192AEF938B44961139AFB21A48F900000000000000000000000000000000 | |||
| (PID) Process: | (7624) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000001AB3F22B56C7DB01C81D0000481E0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7624) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000001AB3F22B56C7DB01C81D0000401E0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
41
Suspicious files
72
Text files
286
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7388 | RobloxSetup_0.3.696.0January162008.exe | C:\Users\admin\AppData\Local\Temp\{234AB76F-5408-46DA-A4D1-011882654B14}\ROBLOX.msi | — | |
MD5:— | SHA256:— | |||
| 7448 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 7448 | msiexec.exe | C:\Windows\Installer\1126fd.msi | — | |
MD5:— | SHA256:— | |||
| 7388 | RobloxSetup_0.3.696.0January162008.exe | C:\Users\admin\AppData\Local\Temp\~C8EF.tmp | text | |
MD5:E88D1138516C695B4BB197D6D56C14E3 | SHA256:A54A4BF24D08B172224C4FBD0DA733AB7362B1E006FBF7CC7DABCCE82E07F568 | |||
| 7448 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:74FC36589C18A8D1747882AED40D0E4F | SHA256:62E45D02E60CA2E90A7DB1F152877D9FC928BA8AC6CB8B77E754FA62AE9C4187 | |||
| 7448 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{2a192471-93ef-448b-9611-39afb21a48f9}_OnDiskSnapshotProp | binary | |
MD5:74FC36589C18A8D1747882AED40D0E4F | SHA256:62E45D02E60CA2E90A7DB1F152877D9FC928BA8AC6CB8B77E754FA62AE9C4187 | |||
| 7388 | RobloxSetup_0.3.696.0January162008.exe | C:\Users\admin\AppData\Local\Temp\{234AB76F-5408-46DA-A4D1-011882654B14}\0x0409.ini | binary | |
MD5:52D179AD79966752EC40A678FD8B0062 | SHA256:57E020C41AD0566FB55415A40167A0C3DA89584BC4E5F961D8E8C646F80C5590 | |||
| 7412 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIE0AD.tmp | executable | |
MD5:FADFFEF98D0F28368B843C6E9AFD9782 | SHA256:73F7E51214B775421F6679ACABC51AC1D34B4271116F5F3DD3426DF50D214886 | |||
| 7448 | msiexec.exe | C:\Windows\Installer\MSI2EC0.tmp | executable | |
MD5:5D2C8E69D2D3CD58FE067CC96544F553 | SHA256:4316B375865B9A0838BD982B06B70153870F42E09C4A9D3C10F09652984E4FD1 | |||
| 7448 | msiexec.exe | C:\Windows\Temp\~DF762F896494EB1602.TMP | binary | |
MD5:541B602E3DFACEAED5F5D11C9E7B30A3 | SHA256:B7736690CDE0A3E5B19667F32A9FCFEB5C3F40BFDE547B1F19C24168FE83B60E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
57
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8016 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
8016 | SIHClient.exe | GET | 200 | 23.216.77.33:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
8016 | SIHClient.exe | GET | 200 | 23.216.77.33:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
8016 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8016 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
8016 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
8016 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2104 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
6544 | svchost.exe | 20.190.160.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
8072 | svchost.exe | 95.100.186.9:443 | go.microsoft.com | AKAMAI-AS | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |