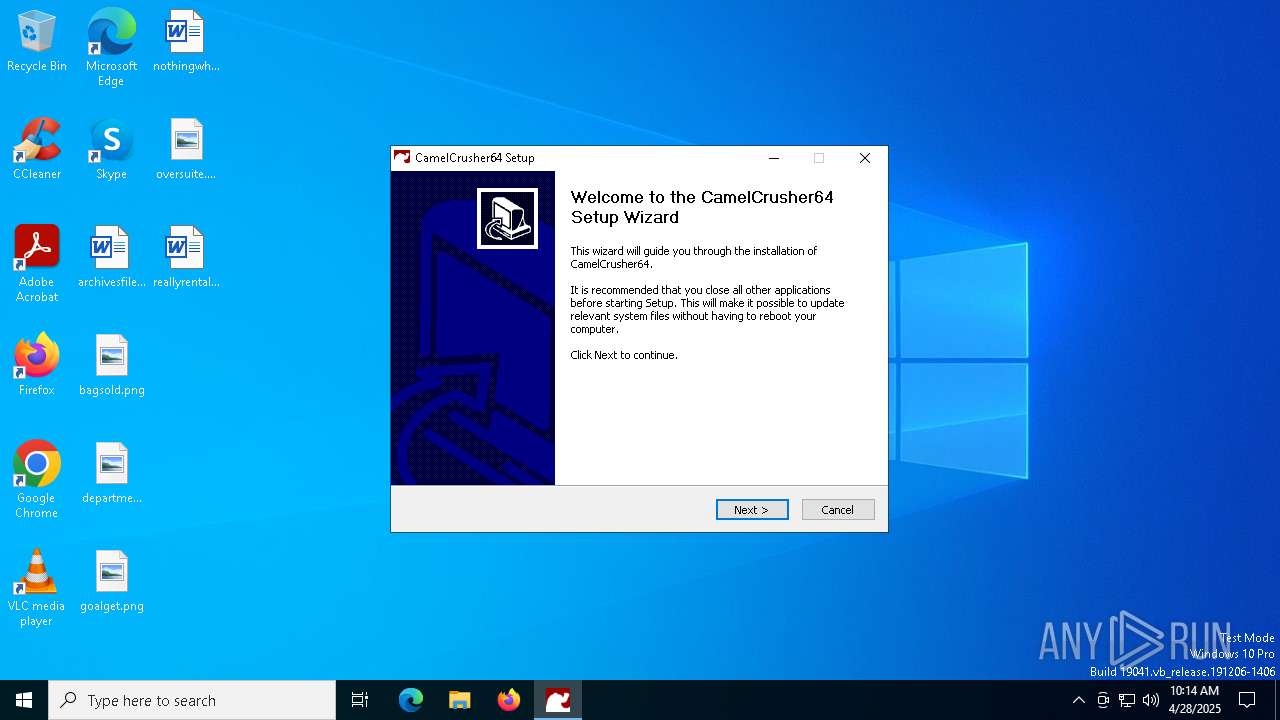
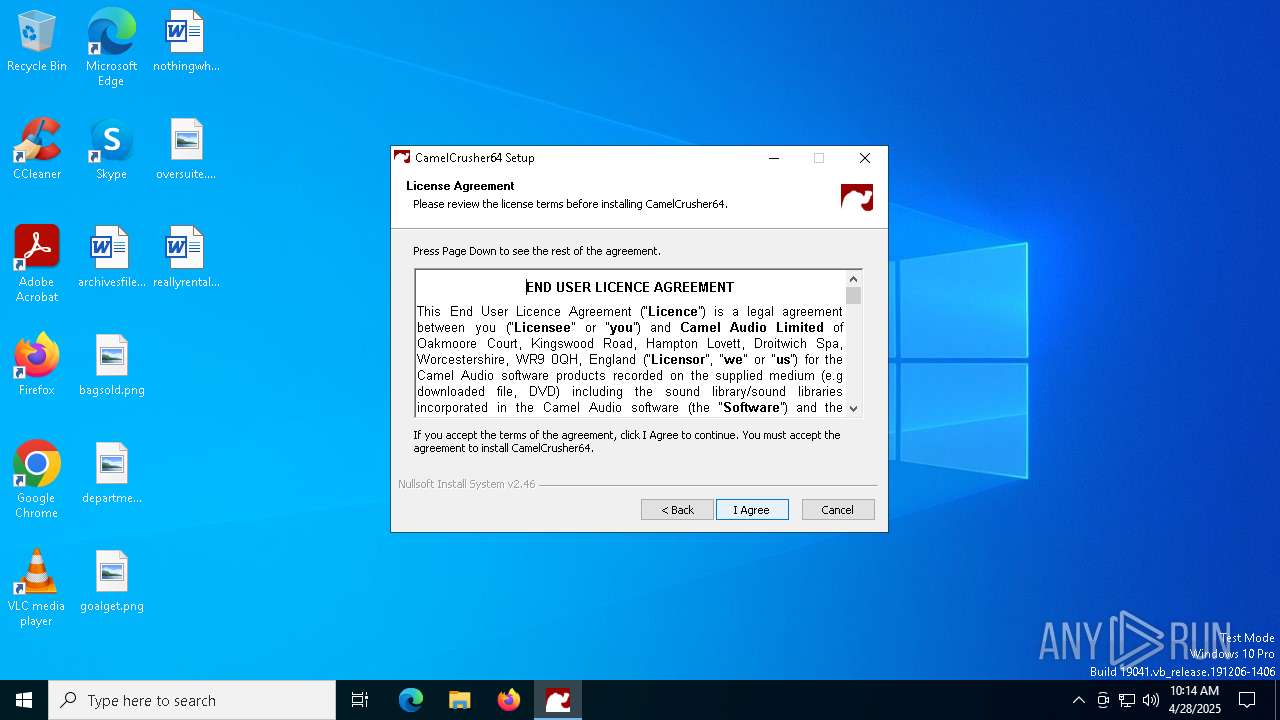
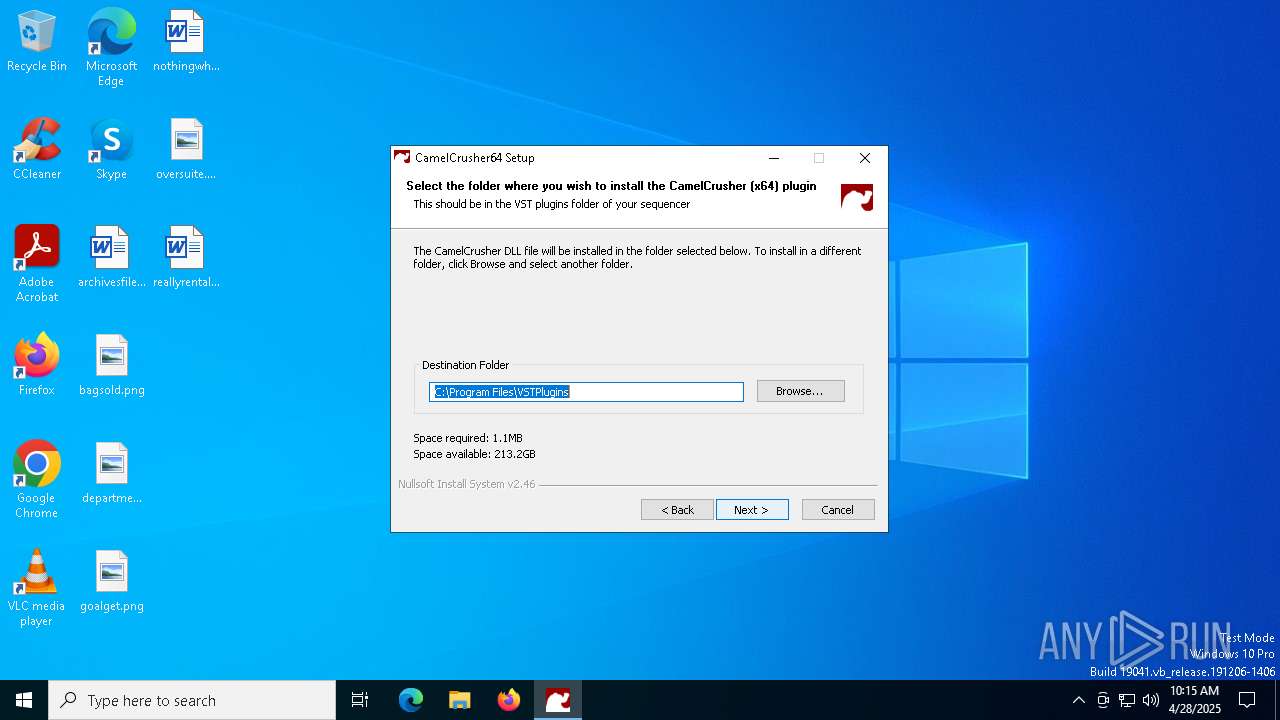
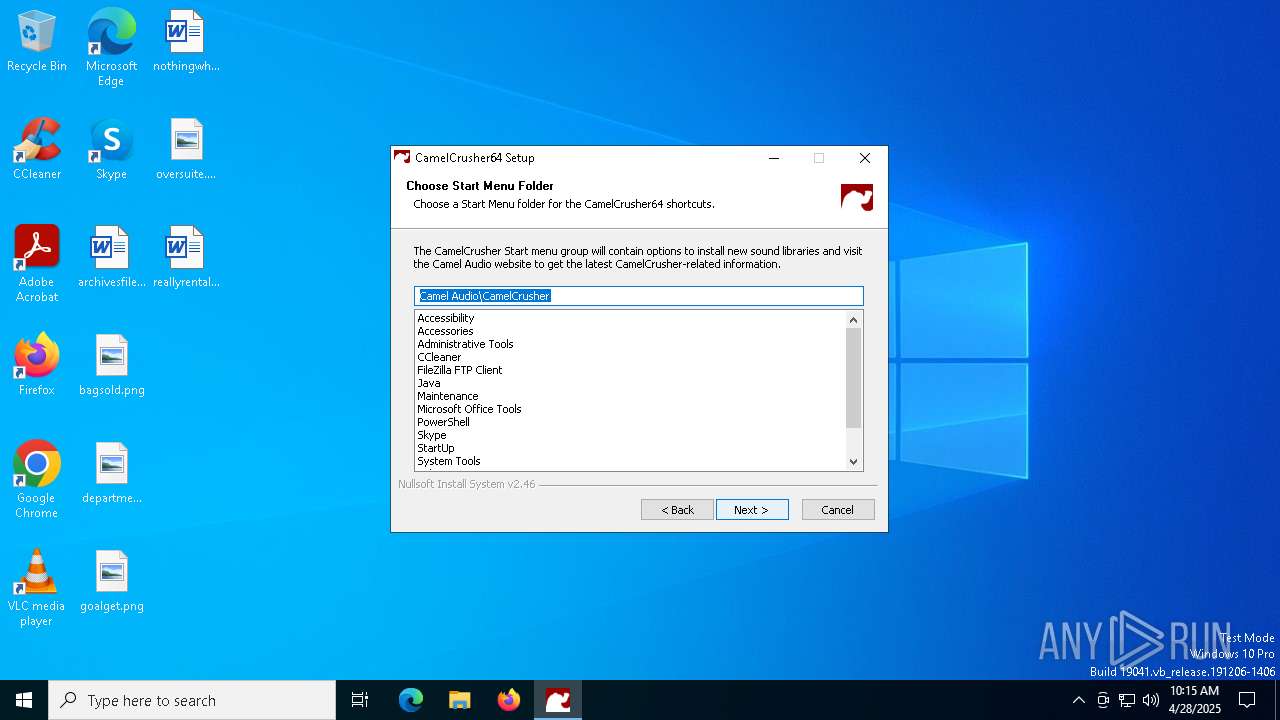
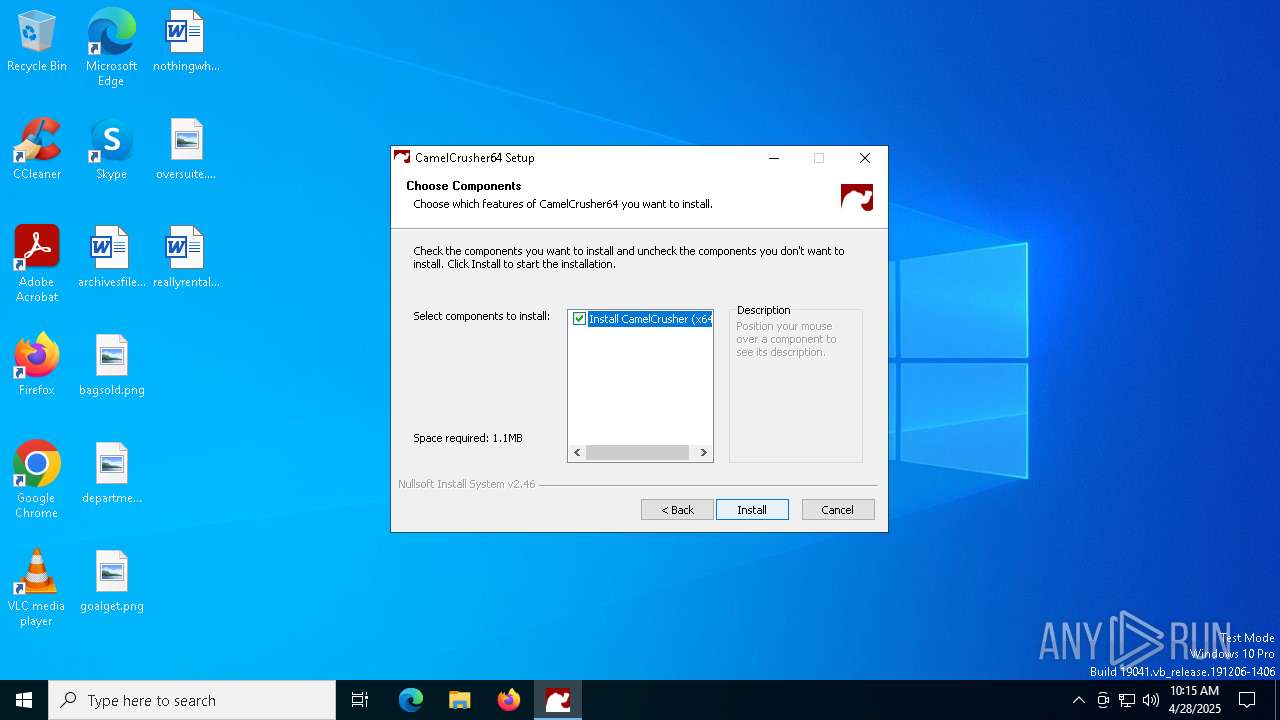
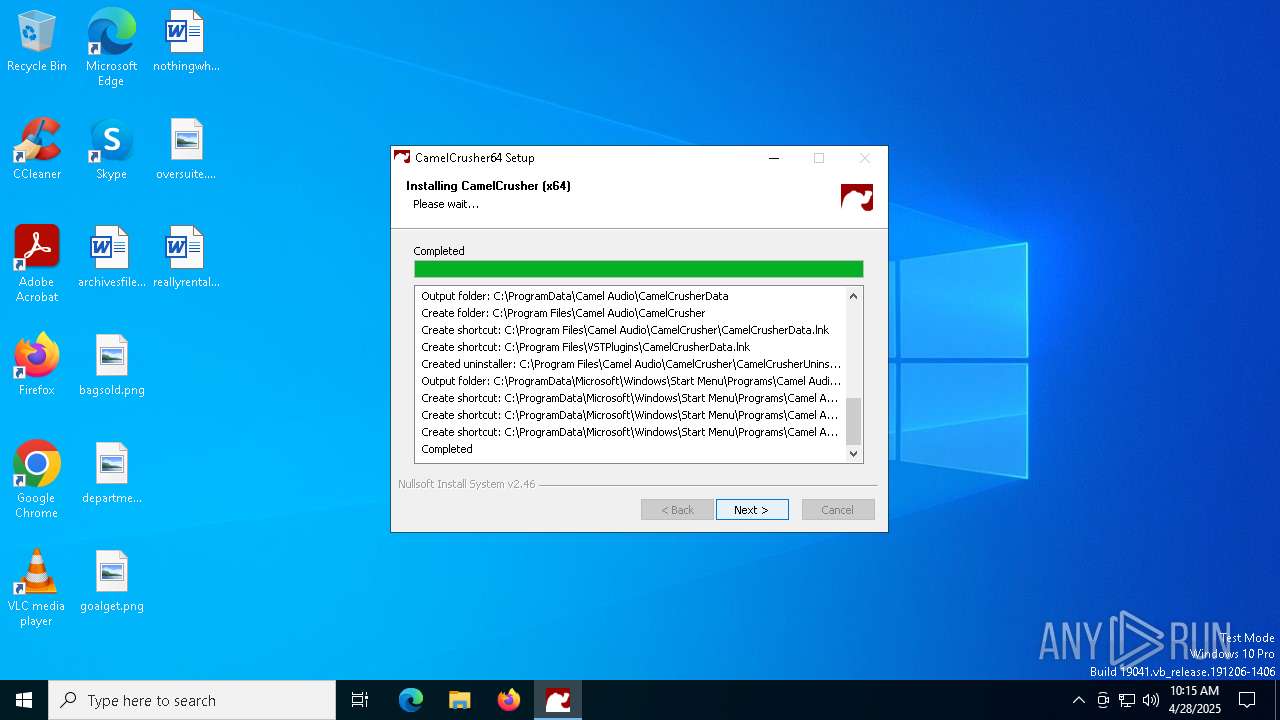
| File name: | CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe |
| Full analysis: | https://app.any.run/tasks/3ead1cb6-92f8-4b16-9973-ce86e0817e7a |
| Verdict: | Malicious activity |
| Analysis date: | April 28, 2025, 10:14:42 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 6F4547B4F8133768A0AB25A68C813E77 |
| SHA1: | D877A5E5A5535272AFD3C2F6CFFBE17640429609 |
| SHA256: | 76EB202284796D258BED9057921F5B72CB5A1B30FB0671F4B5AF402E9D713053 |
| SSDEEP: | 24576:qfyq93DySYvloLdZD6wzGfXey9jKNW/J1a9oE5BVFTUoHPvDpzxGVCsvCaY+AA/5:6LdZOwzGXJq5B3TmVVo+AA/mmLdr |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe (PID: 4628)
Malware-specific behavior (creating "System.dll" in Temp)
- CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe (PID: 4628)
The process creates files with name similar to system file names
- CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe (PID: 4628)
There is functionality for taking screenshot (YARA)
- CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe (PID: 4628)
Reads security settings of Internet Explorer
- CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe (PID: 4628)
Creates a software uninstall entry
- CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe (PID: 4628)
INFO
Checks supported languages
- CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe (PID: 4628)
Create files in a temporary directory
- CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe (PID: 4628)
Creates files in the program directory
- CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe (PID: 4628)
Reads the computer name
- CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe (PID: 4628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (93.4) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .scr | | | Windows screen saver (1.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:12:05 22:50:52+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24064 |
| InitializedDataSize: | 164864 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x30fa |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
131
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 904 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4628 | "C:\Users\admin\AppData\Local\Temp\CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe" | C:\Users\admin\AppData\Local\Temp\CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 5720 | "C:\Users\admin\AppData\Local\Temp\CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe" | C:\Users\admin\AppData\Local\Temp\CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
414
Read events
403
Write events
11
Delete events
0
Modification events
| (PID) Process: | (4628) CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Camel Audio\CamelCrusher64 |
| Operation: | write | Name: | PluginInstallDir |
Value: C:\Program Files\VSTPlugins | |||
| (PID) Process: | (4628) CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Camel Audio\CamelCrusher64 |
| Operation: | write | Name: | Version |
Value: 1.01.0 | |||
| (PID) Process: | (4628) CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Camel Audio\CamelCrusher64 |
| Operation: | write | Name: | StartMenuGroup |
Value: Camel Audio\CamelCrusher | |||
| (PID) Process: | (4628) CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Camel Audio CamelCrusher64 |
| Operation: | write | Name: | DisplayName |
Value: Camel Audio CamelCrusher64 | |||
| (PID) Process: | (4628) CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Camel Audio CamelCrusher64 |
| Operation: | write | Name: | DisplayVersion |
Value: 1.01.0 | |||
| (PID) Process: | (4628) CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Camel Audio CamelCrusher64 |
| Operation: | write | Name: | Publisher |
Value: Camel Audio | |||
| (PID) Process: | (4628) CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Camel Audio CamelCrusher64 |
| Operation: | write | Name: | URLInfoAbout |
Value: http://www.camelaudio.com | |||
| (PID) Process: | (4628) CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Camel Audio CamelCrusher64 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\Camel Audio\CamelCrusher\CamelCrusherUninstall64.exe | |||
| (PID) Process: | (4628) CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Camel Audio CamelCrusher64 |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files\Camel Audio\CamelCrusher\CamelCrusherUninstall64.exe | |||
| (PID) Process: | (4628) CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Camel Audio CamelCrusher64 |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
Executable files
7
Suspicious files
8
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4628 | CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | C:\Users\admin\AppData\Local\Temp\nsaD0A1.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 4628 | CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | C:\ProgramData\Camel Audio\CamelCrusherData\Skins\default\FontDisplay-Old.png | image | |
MD5:B72185607613379425FA95EB6ECFAB63 | SHA256:FF4B2C640D5BE3571A5984BF80D962B4A3E90738302C27C0755A7A153452460A | |||
| 4628 | CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | C:\ProgramData\Camel Audio\CamelCrusherData\CamelCrusherManual.pdf | ||
MD5:1EDA63DC9F8E88AA4FFEEE3DF6195F86 | SHA256:1819103E3A2A24C3C481C4300CB3E287D421D4CACA3A7708CFD5D149A63EBCE0 | |||
| 4628 | CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | C:\Users\admin\AppData\Local\Temp\nsaD0A1.tmp\StartMenu.dll | executable | |
MD5:A4173B381625F9F12AADB4E1CDAEFDB8 | SHA256:7755FF2707CA19344D489A5ACEC02D9E310425FA6E100D2F13025761676B875B | |||
| 4628 | CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | C:\ProgramData\Camel Audio\CamelCrusherData\Skins\default\FontDisplay.png | image | |
MD5:48D3FF17C45A01F92D74B579B965C061 | SHA256:40F14CA49303632227825015F4D239B1BA44B153552C72907163FACFF50D0140 | |||
| 4628 | CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | C:\ProgramData\Camel Audio\CamelCrusherData\CamelCrusherPresetsA.fxb | binary | |
MD5:210CA751B15C10C00700F1D6D4992BBA | SHA256:83736969756DA08E84F0683999AA0484427DDF4AE7AC6A22FE2830869144EE2E | |||
| 4628 | CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | C:\ProgramData\Camel Audio\CamelCrusherData\MidiConfig.txt | text | |
MD5:28FABECD09C264DEC37F58EACD2A03FB | SHA256:ADDEABB82EE40C90C484F2DC6CB3DEF51157E926F3288DE379EC5D8A5E289441 | |||
| 4628 | CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | C:\ProgramData\Camel Audio\CamelCrusherData\Skins\default\ButtonRandom.png | image | |
MD5:265B353A51F327A073A702A30910E993 | SHA256:50B5BA9CE8866207C13AA9902B78EA895A6460A7EFE06E44B852A1114ECA1083 | |||
| 4628 | CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | C:\Users\admin\AppData\Local\Temp\nsaD0A1.tmp\nsDialogs.dll | executable | |
MD5:C10E04DD4AD4277D5ADC951BB331C777 | SHA256:E31AD6C6E82E603378CB6B80E67D0E0DCD9CF384E1199AC5A65CB4935680021A | |||
| 4628 | CamelCrusher-Win-x64-CamelCrusher.Com-1-0-1.exe | C:\Users\admin\AppData\Local\Temp\nsaD0A1.tmp\NSISpcre.dll | executable | |
MD5:BFE060C22B44914E05D3F5367DE6C9FE | SHA256:43041F8540DCCBC33268BFBEF53037D17170B037F6393E77C21429F303AE828F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
39
DNS requests
11
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
171.39.242.20.in-addr.arpa |
| unknown |
6.0.1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.7.0.0.0.0.3.0.1.3.0.6.2.ip6.arpa |
| unknown |