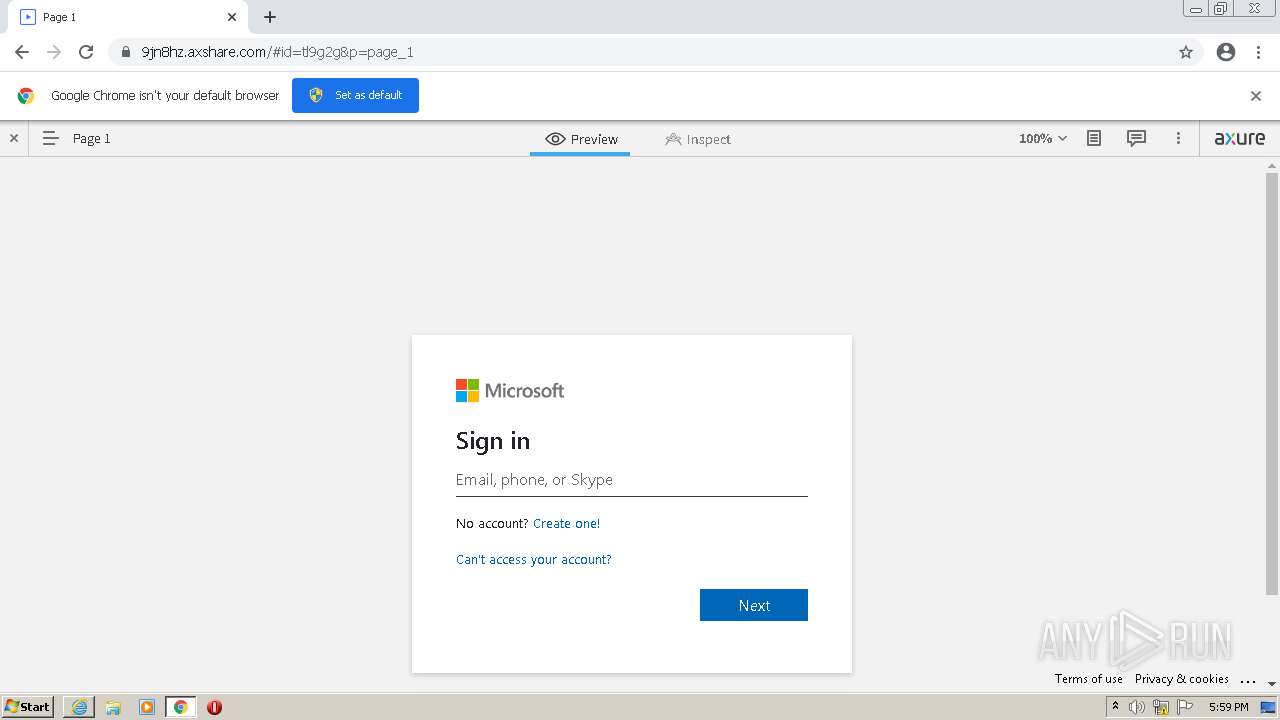
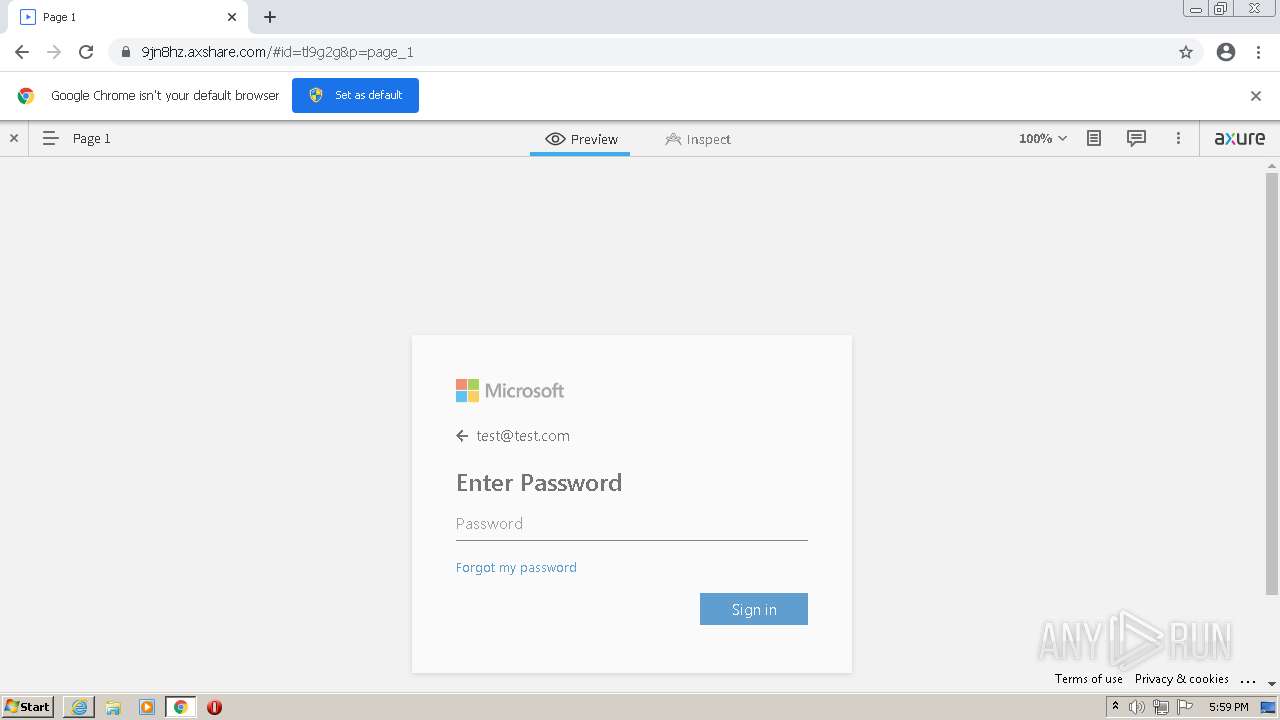
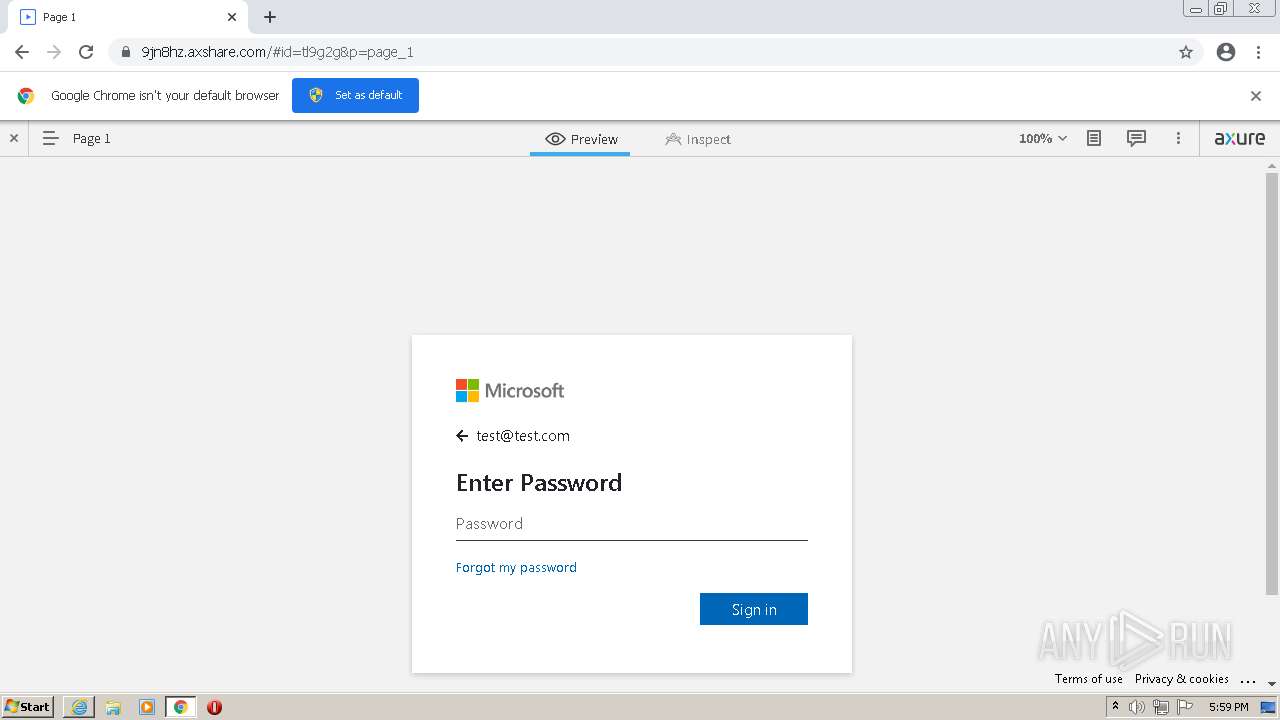
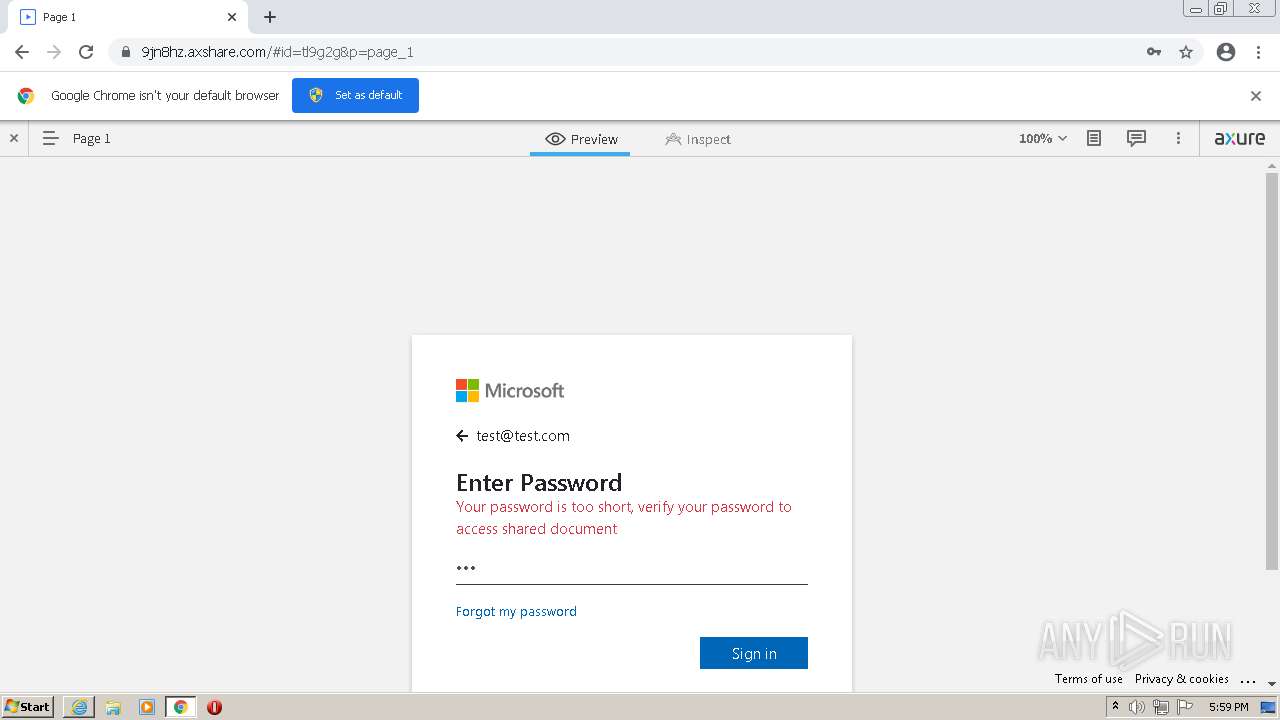
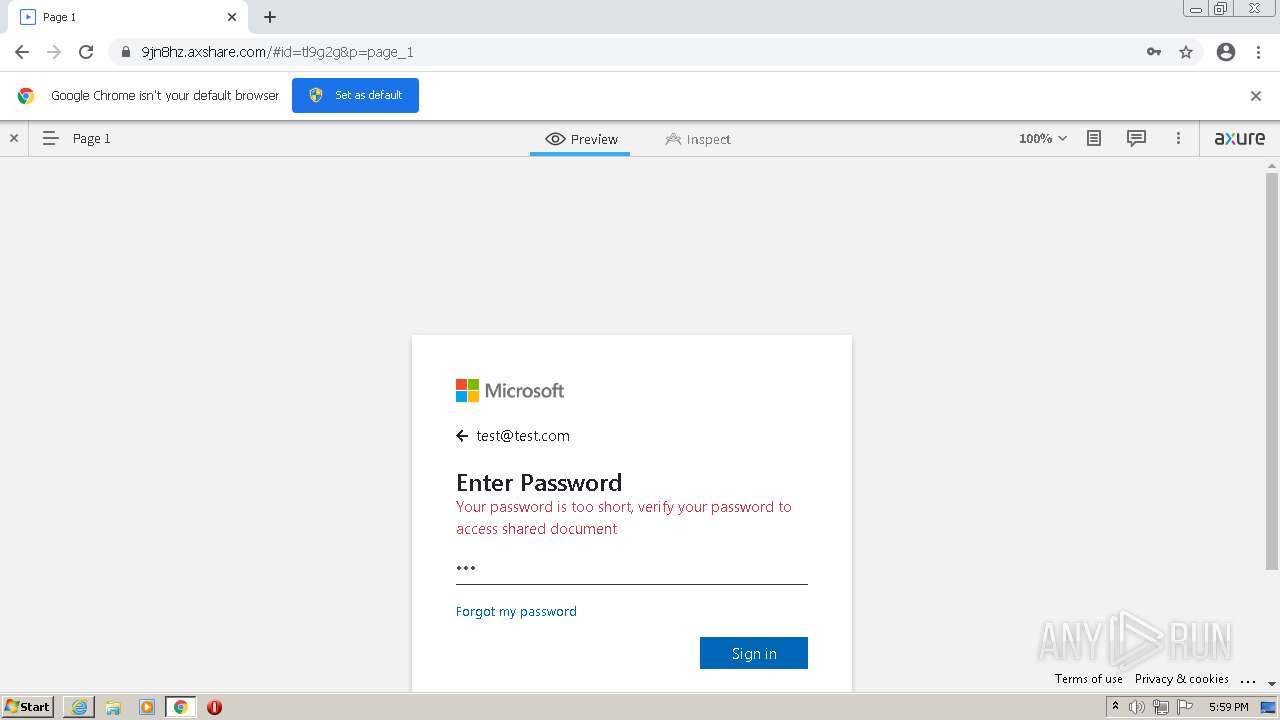
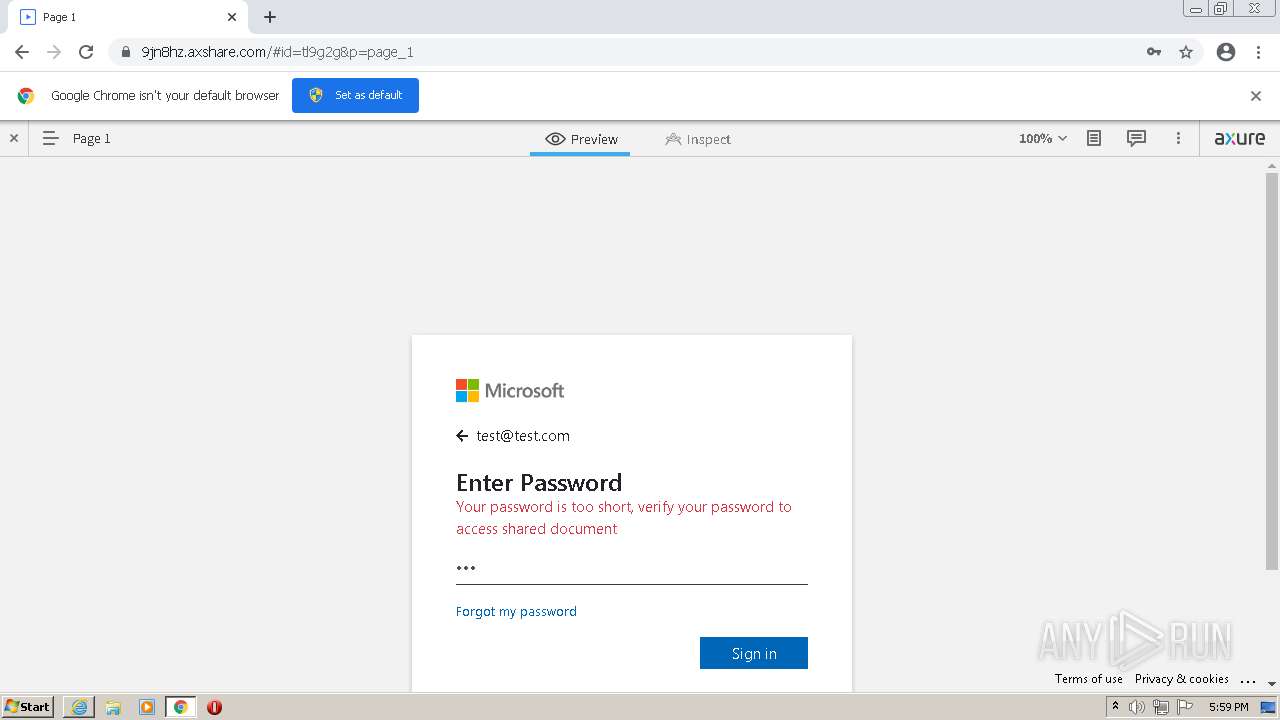
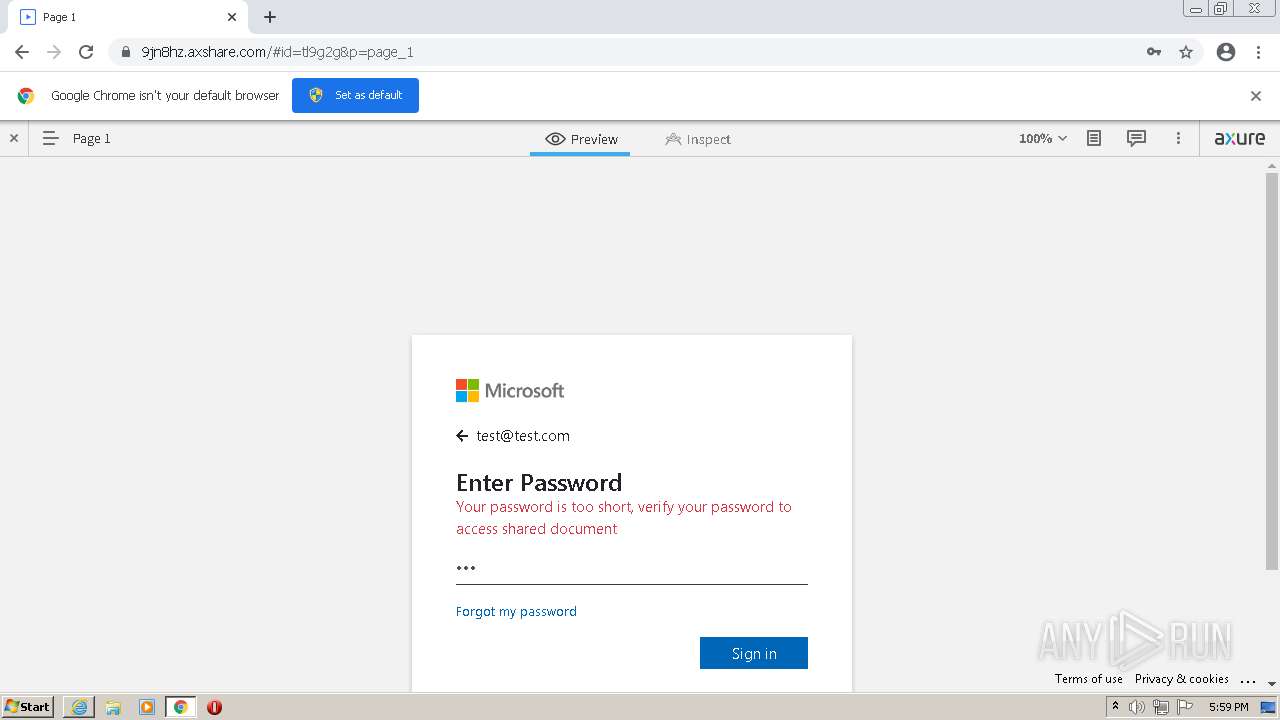
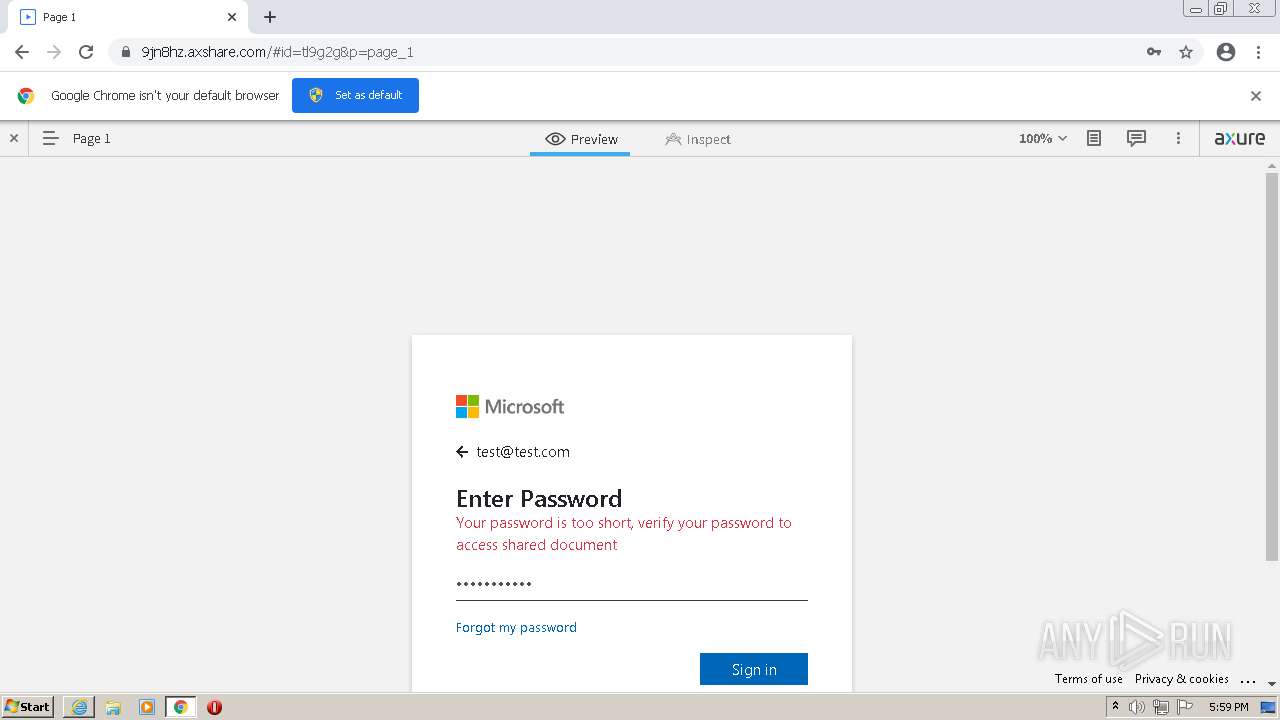
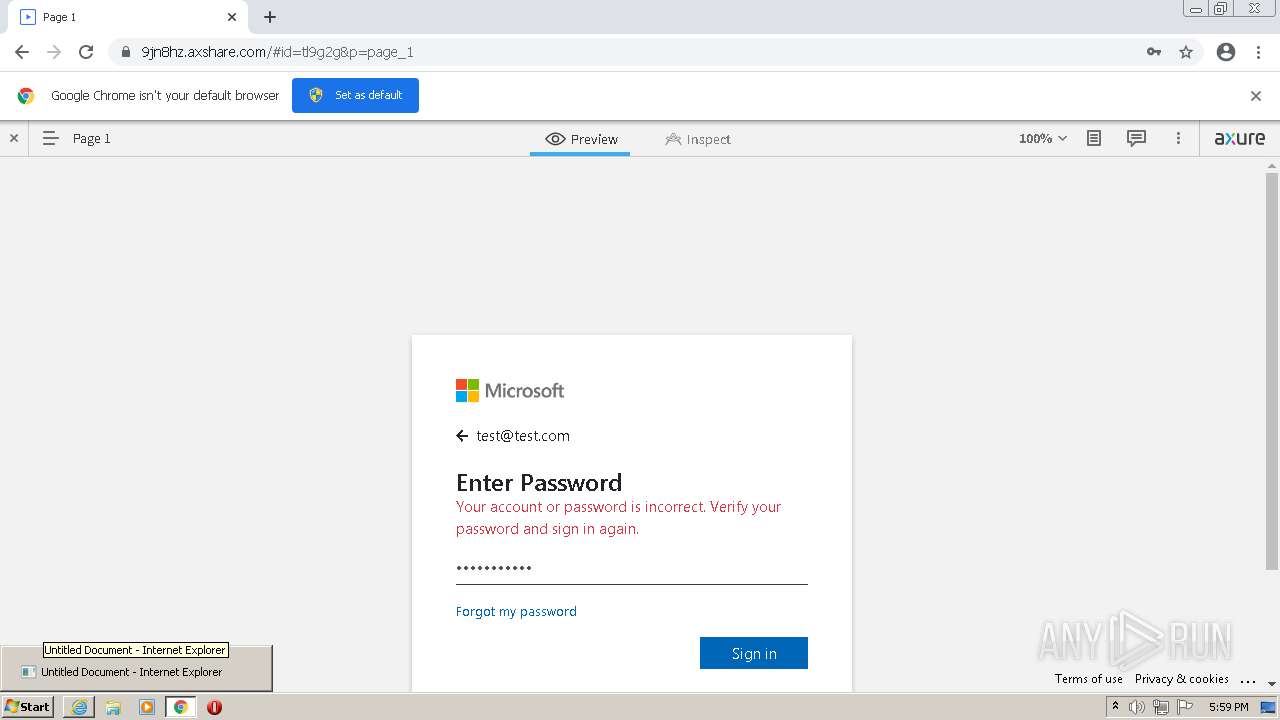
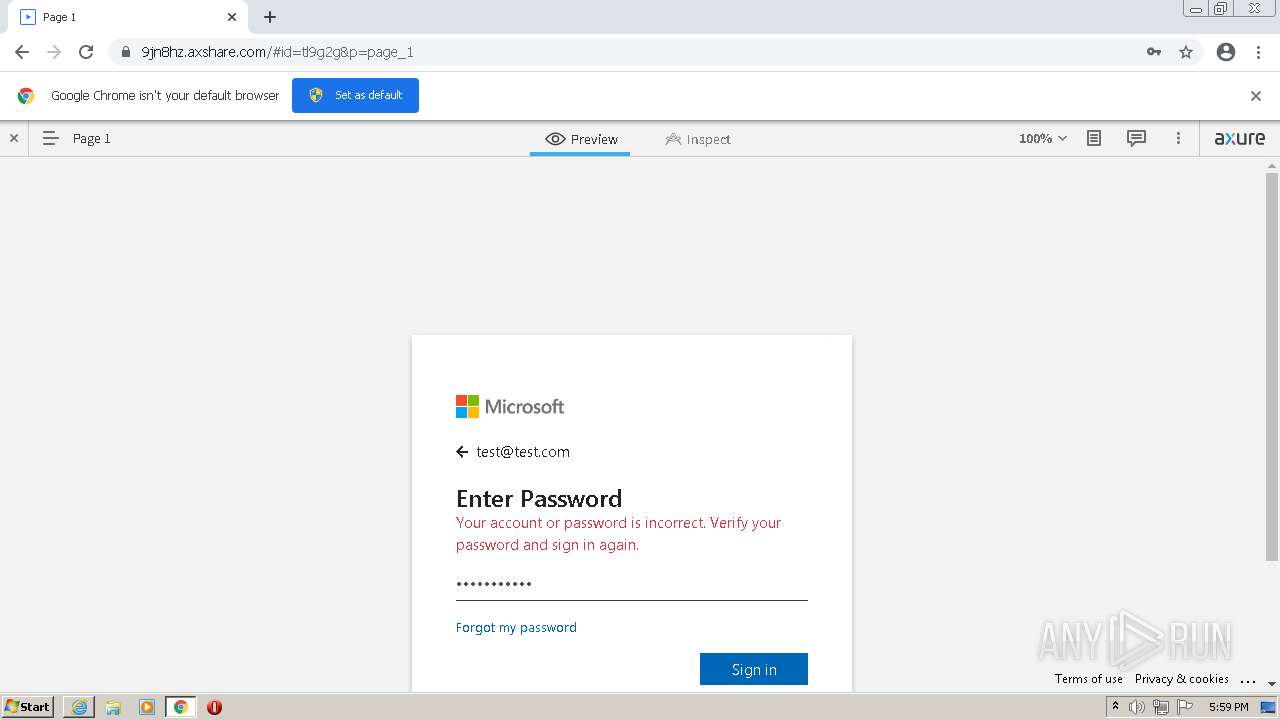
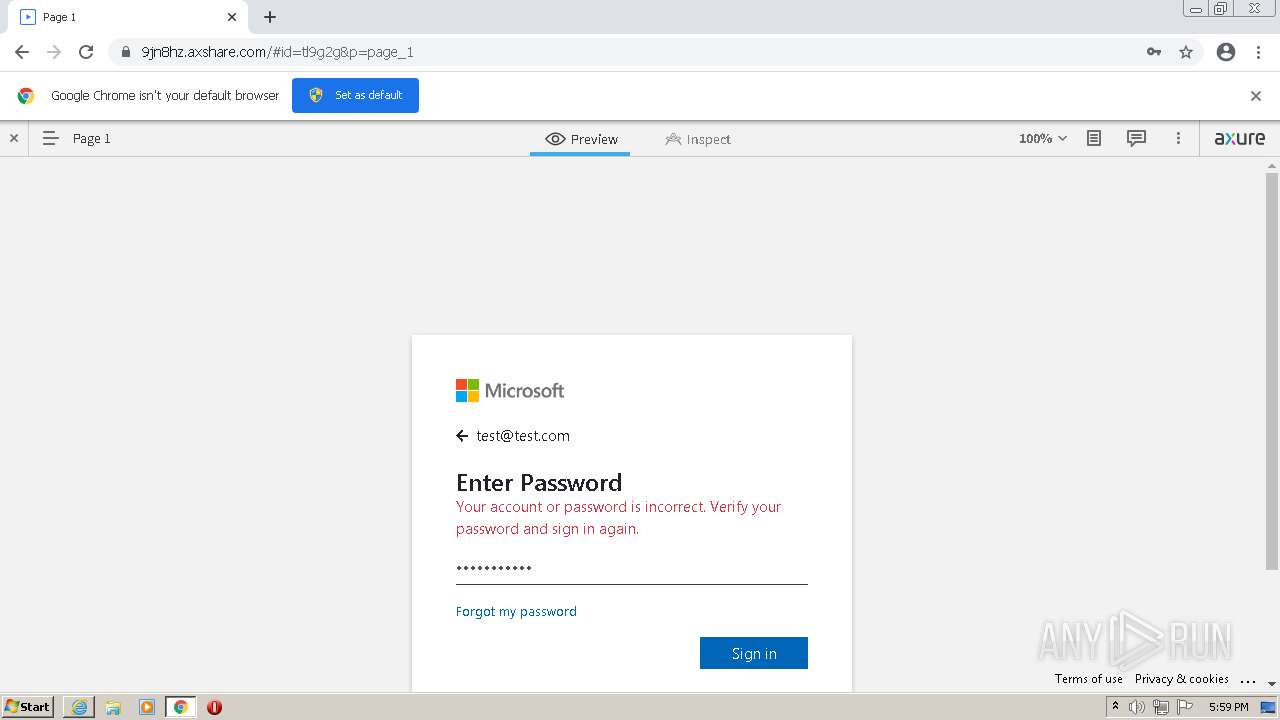
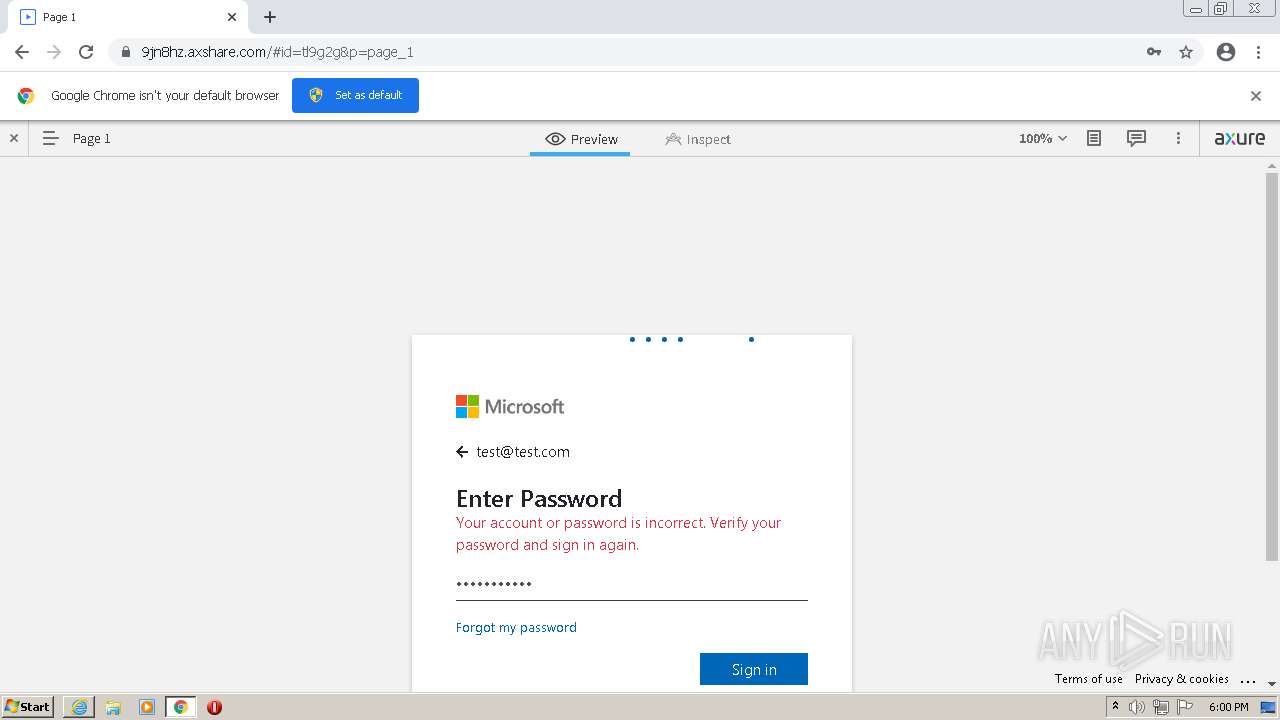
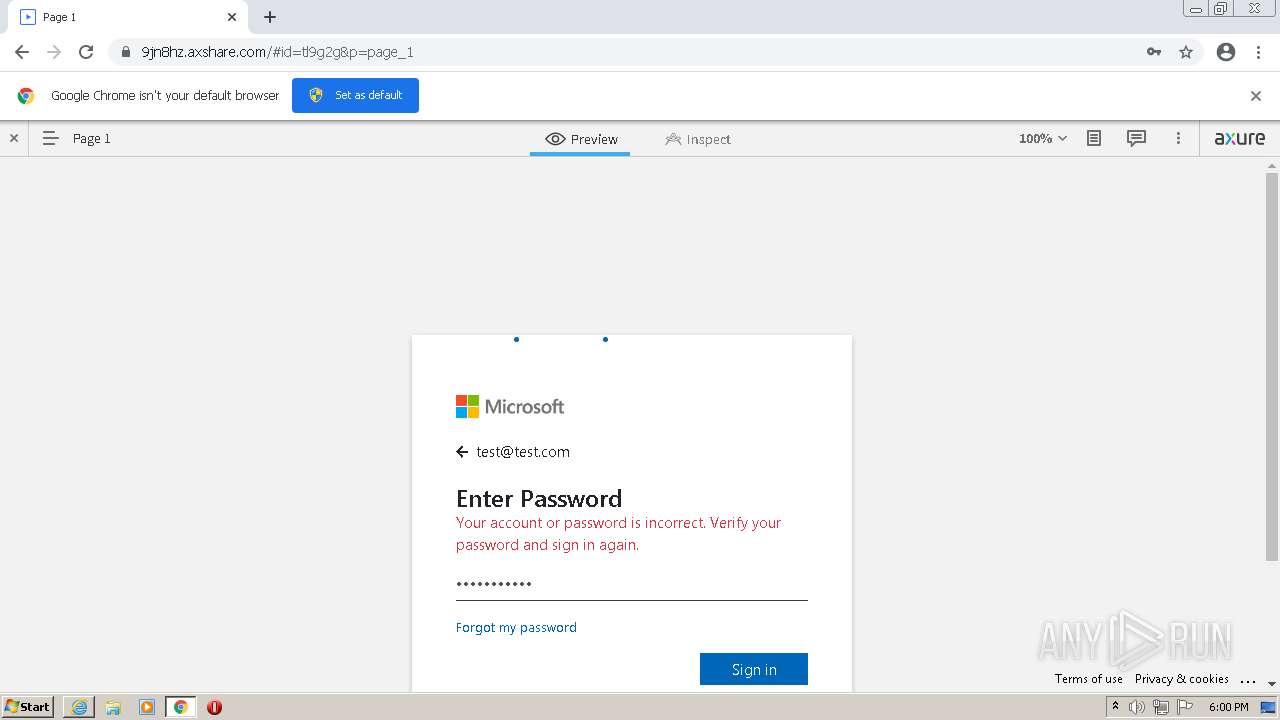
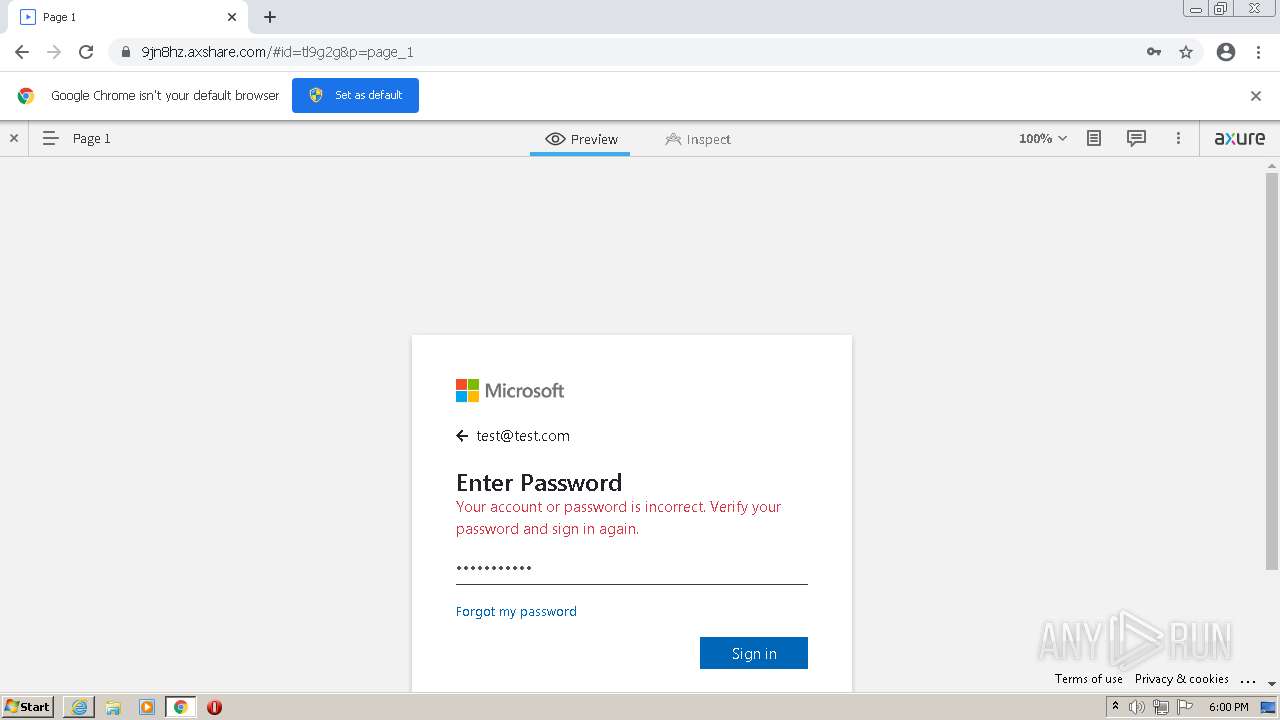
| URL: | https://9jn8hz.axshare.com/ |
| Full analysis: | https://app.any.run/tasks/a8e8ab84-bd37-4c35-b35e-9477b2befe8e |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 17:58:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | D2E324B9C1C7E6D31976890FF2863CBC |
| SHA1: | 8AECC3AEB4FDE04A7193B0B8637D6B0C0A7F5D53 |
| SHA256: | 76A68DEA5D76510F5F2BD39CCA42A35AD70F58E42D7FEED1D1613001F410403E |
| SSDEEP: | 3:N8cpjyK3:2c9yG |
MALICIOUS
Drops executable file immediately after starts
- chrome.exe (PID: 3764)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2236)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3208)
Executable content was dropped or overwritten
- chrome.exe (PID: 3764)
Drops a file that was compiled in debug mode
- chrome.exe (PID: 3764)
INFO
Reads the computer name
- iexplore.exe (PID: 3856)
- chrome.exe (PID: 3208)
- iexplore.exe (PID: 2236)
- chrome.exe (PID: 2284)
- chrome.exe (PID: 1424)
- chrome.exe (PID: 3372)
- chrome.exe (PID: 1972)
- chrome.exe (PID: 300)
- chrome.exe (PID: 2532)
- chrome.exe (PID: 1028)
Checks supported languages
- iexplore.exe (PID: 3856)
- chrome.exe (PID: 2284)
- chrome.exe (PID: 3208)
- chrome.exe (PID: 3432)
- chrome.exe (PID: 1424)
- iexplore.exe (PID: 2236)
- chrome.exe (PID: 888)
- chrome.exe (PID: 2064)
- chrome.exe (PID: 776)
- chrome.exe (PID: 2952)
- chrome.exe (PID: 2636)
- chrome.exe (PID: 3372)
- chrome.exe (PID: 1972)
- chrome.exe (PID: 824)
- chrome.exe (PID: 2676)
- chrome.exe (PID: 3052)
- chrome.exe (PID: 2200)
- chrome.exe (PID: 3236)
- chrome.exe (PID: 3696)
- chrome.exe (PID: 2532)
- chrome.exe (PID: 300)
- chrome.exe (PID: 2372)
- chrome.exe (PID: 3688)
- chrome.exe (PID: 3764)
- chrome.exe (PID: 1028)
- chrome.exe (PID: 2280)
- chrome.exe (PID: 2960)
- chrome.exe (PID: 2764)
- chrome.exe (PID: 1856)
Application launched itself
- chrome.exe (PID: 3208)
- iexplore.exe (PID: 3856)
Reads the hosts file
- chrome.exe (PID: 3208)
- chrome.exe (PID: 1424)
Manual execution by user
- chrome.exe (PID: 3208)
Changes internet zones settings
- iexplore.exe (PID: 3856)
Reads settings of System Certificates
- iexplore.exe (PID: 2236)
- iexplore.exe (PID: 3856)
- chrome.exe (PID: 1424)
Checks Windows Trust Settings
- iexplore.exe (PID: 2236)
- iexplore.exe (PID: 3856)
Reads internet explorer settings
- iexplore.exe (PID: 2236)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 3208)
Creates files in the user directory
- iexplore.exe (PID: 3856)
Changes settings of System certificates
- iexplore.exe (PID: 3856)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3856)
Reads the date of Windows installation
- chrome.exe (PID: 300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
65
Monitored processes
29
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1048,15523029046921091775,5181753879053621715,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1848 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 776 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,15523029046921091775,5181753879053621715,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1840 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 824 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,15523029046921091775,5181753879053621715,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=14 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3156 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 888 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,15523029046921091775,5181753879053621715,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2340 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1048,15523029046921091775,5181753879053621715,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2372 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1424 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1048,15523029046921091775,5181753879053621715,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1320 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1856 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1048,15523029046921091775,5181753879053621715,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2188 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1972 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1048,15523029046921091775,5181753879053621715,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3212 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2064 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,15523029046921091775,5181753879053621715,131072 --enable-features=PasswordImport --lang=en-US --instant-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1904 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2200 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,15523029046921091775,5181753879053621715,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3500 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
24 634
Read events
24 380
Write events
244
Delete events
10
Modification events
| (PID) Process: | (3856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30937419 | |||
| (PID) Process: | (3856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 32673680 | |||
| (PID) Process: | (3856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30937420 | |||
| (PID) Process: | (3856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
213
Text files
171
Unknown types
22
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2236 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2236 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7D6243C18F0F8F9AEC6638DD210F1984_9D57C9D469E8DCA3C61B927F3F448E70 | binary | |
MD5:— | SHA256:— | |||
| 2236 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_93E4B2BA79A897B3100CCB27F2D3BF4F | binary | |
MD5:— | SHA256:— | |||
| 2236 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:— | SHA256:— | |||
| 2236 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7D6243C18F0F8F9AEC6638DD210F1984_9D57C9D469E8DCA3C61B927F3F448E70 | der | |
MD5:— | SHA256:— | |||
| 2236 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\RZ10YWF3.htm | html | |
MD5:— | SHA256:— | |||
| 2236 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:— | SHA256:— | |||
| 2236 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\default[1].css | text | |
MD5:— | SHA256:— | |||
| 2236 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\reset[1].css | text | |
MD5:— | SHA256:— | |||
| 2236 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
76
DNS requests
48
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
872 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | — | — | whitelisted |
2236 | iexplore.exe | GET | 200 | 13.225.84.145:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
3856 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | US | der | 471 b | whitelisted |
3856 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2236 | iexplore.exe | GET | 200 | 13.225.84.97:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
872 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 5.63 Kb | whitelisted |
872 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 43.4 Kb | whitelisted |
872 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 20.9 Kb | whitelisted |
872 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 9.68 Kb | whitelisted |
872 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 9.69 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2236 | iexplore.exe | 13.225.84.145:80 | ocsp.rootg2.amazontrust.com | — | US | whitelisted |
2236 | iexplore.exe | 13.225.84.49:80 | ocsp.rootg2.amazontrust.com | — | US | whitelisted |
2236 | iexplore.exe | 216.58.212.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3856 | iexplore.exe | 131.253.33.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2236 | iexplore.exe | 142.250.186.131:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3856 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2236 | iexplore.exe | 142.250.185.67:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
1424 | chrome.exe | 142.250.186.174:443 | clients2.google.com | Google Inc. | US | whitelisted |
3856 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1424 | chrome.exe | 142.250.184.195:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
9jn8hz.axshare.com |
| suspicious |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.sca1b.amazontrust.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
— | — | Misc activity | ET INFO Suspicious Glitch Hosted DNS Request - Possible Phishing Landing |
1424 | chrome.exe | Misc activity | ET INFO Suspicious Glitch Hosted TLS SNI Request - Possible Phishing Landing |