| File name: | MegaDownloader_v1.8.exe |
| Full analysis: | https://app.any.run/tasks/13ca31d3-5db0-4617-ada6-f14e17766927 |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2025, 14:21:12 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 10 sections |
| MD5: | E88A876515DDCA653C424791D614E58E |
| SHA1: | 4DD7B4BDDAC0AAC4439E0E1582A943628B670E63 |
| SHA256: | 76A56AA46B0102A96A4AF355F5E03AFF2B6AE6076F040FF4FF4E0D943A75D411 |
| SSDEEP: | 49152:2qeNVTiHG5hswaJJoUxpyfKV5SiheRiiZQCu9f0BTHgXhfSUQP:nE5iHUPajqCVlwfgJ0ZgXxxQP |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- MegaDownloader_v1.8.exe (PID: 2708)
- MegaDownloader_v1.8.exe (PID: 1208)
- MegaDownloader_v1.8.tmp (PID: 6896)
Reads security settings of Internet Explorer
- MegaDownloader_v1.8.tmp (PID: 1044)
Reads the Windows owner or organization settings
- MegaDownloader_v1.8.tmp (PID: 6896)
The process checks if it is being run in the virtual environment
- MegaDownloader.exe (PID: 6472)
- MegaDownloader.exe (PID: 6220)
The process executes via Task Scheduler
- updater.exe (PID: 2976)
Application launched itself
- updater.exe (PID: 2976)
Reads Internet Explorer settings
- MegaDownloader.exe (PID: 6220)
INFO
Create files in a temporary directory
- MegaDownloader_v1.8.exe (PID: 2708)
- MegaDownloader_v1.8.exe (PID: 1208)
- MegaDownloader_v1.8.tmp (PID: 6896)
Checks supported languages
- MegaDownloader_v1.8.exe (PID: 2708)
- MegaDownloader_v1.8.tmp (PID: 1044)
- MegaDownloader_v1.8.exe (PID: 1208)
- MegaDownloader_v1.8.tmp (PID: 6896)
- MegaDownloader.exe (PID: 6472)
- MegaDownloader.exe (PID: 6220)
- updater.exe (PID: 2976)
- updater.exe (PID: 4768)
Reads the computer name
- MegaDownloader_v1.8.tmp (PID: 1044)
- MegaDownloader_v1.8.tmp (PID: 6896)
- MegaDownloader.exe (PID: 6472)
- MegaDownloader.exe (PID: 6220)
- updater.exe (PID: 2976)
Process checks computer location settings
- MegaDownloader_v1.8.tmp (PID: 1044)
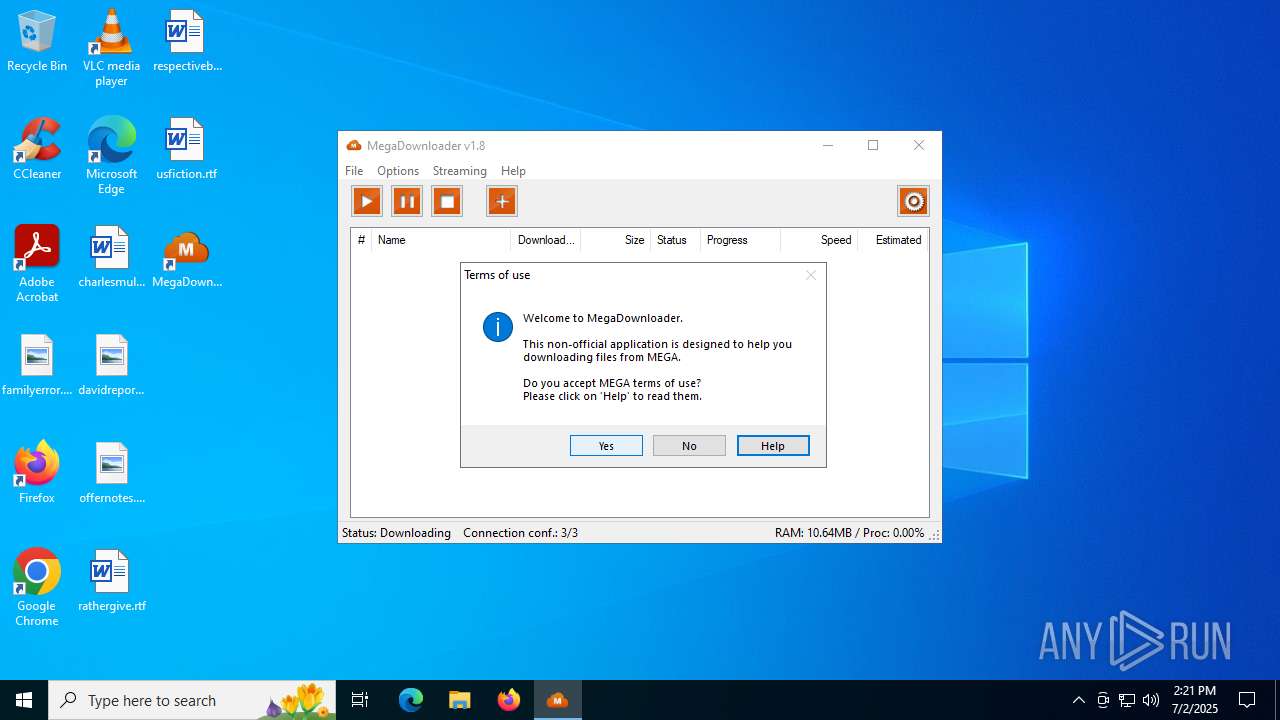
Detects InnoSetup installer (YARA)
- MegaDownloader_v1.8.exe (PID: 2708)
- MegaDownloader_v1.8.tmp (PID: 1044)
Compiled with Borland Delphi (YARA)
- MegaDownloader_v1.8.exe (PID: 2708)
- MegaDownloader_v1.8.tmp (PID: 1044)
Creates files in the program directory
- MegaDownloader_v1.8.tmp (PID: 6896)
Creates a software uninstall entry
- MegaDownloader_v1.8.tmp (PID: 6896)
Checks proxy server information
- MegaDownloader.exe (PID: 6472)
- MegaDownloader.exe (PID: 6220)
- slui.exe (PID: 3624)
Creates files or folders in the user directory
- MegaDownloader.exe (PID: 6472)
- MegaDownloader.exe (PID: 6220)
Reads the machine GUID from the registry
- MegaDownloader.exe (PID: 6472)
- MegaDownloader.exe (PID: 6220)
Reads Environment values
- MegaDownloader.exe (PID: 6472)
- MegaDownloader.exe (PID: 6220)
Disables trace logs
- MegaDownloader.exe (PID: 6472)
- MegaDownloader.exe (PID: 6220)
Reads the software policy settings
- MegaDownloader.exe (PID: 6472)
- slui.exe (PID: 3624)
- MegaDownloader.exe (PID: 6220)
Manual execution by a user
- MegaDownloader.exe (PID: 6220)
Process checks whether UAC notifications are on
- updater.exe (PID: 2976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (51.8) |
|---|---|---|
| .exe | | | InstallShield setup (20.3) |
| .exe | | | Win32 EXE PECompact compressed (generic) (19.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.1) |
| .exe | | | Win32 Executable (generic) (2.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:03:14 17:59:41+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741376 |
| InitializedDataSize: | 37888 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.8.0.0 |
| ProductVersionNumber: | 1.8.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | megadownloaderapp.blogspot.com |
| FileDescription: | MegaDownloader Setup |
| FileVersion: | 1.8 |
| LegalCopyright: | Copyright © 2015-2020 |
| OriginalFileName: | |
| ProductName: | MegaDownloader |
| ProductVersion: | 1.8 |
Total processes
158
Monitored processes
9
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
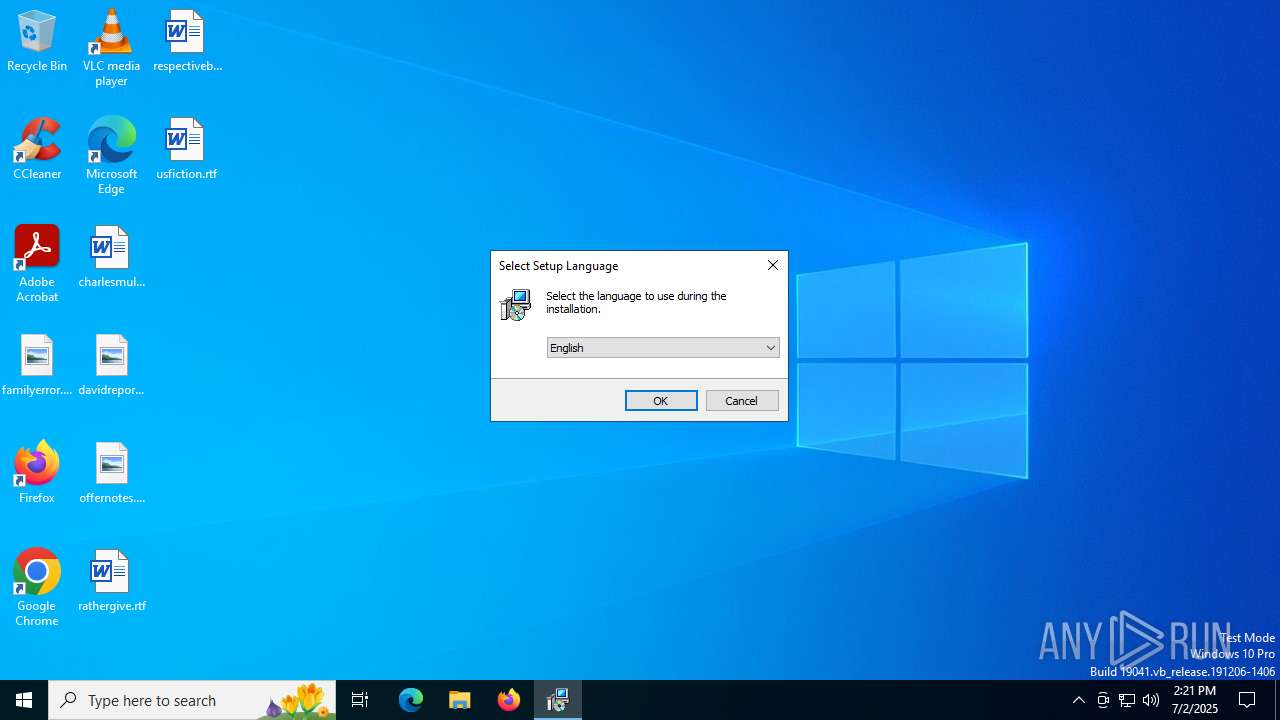
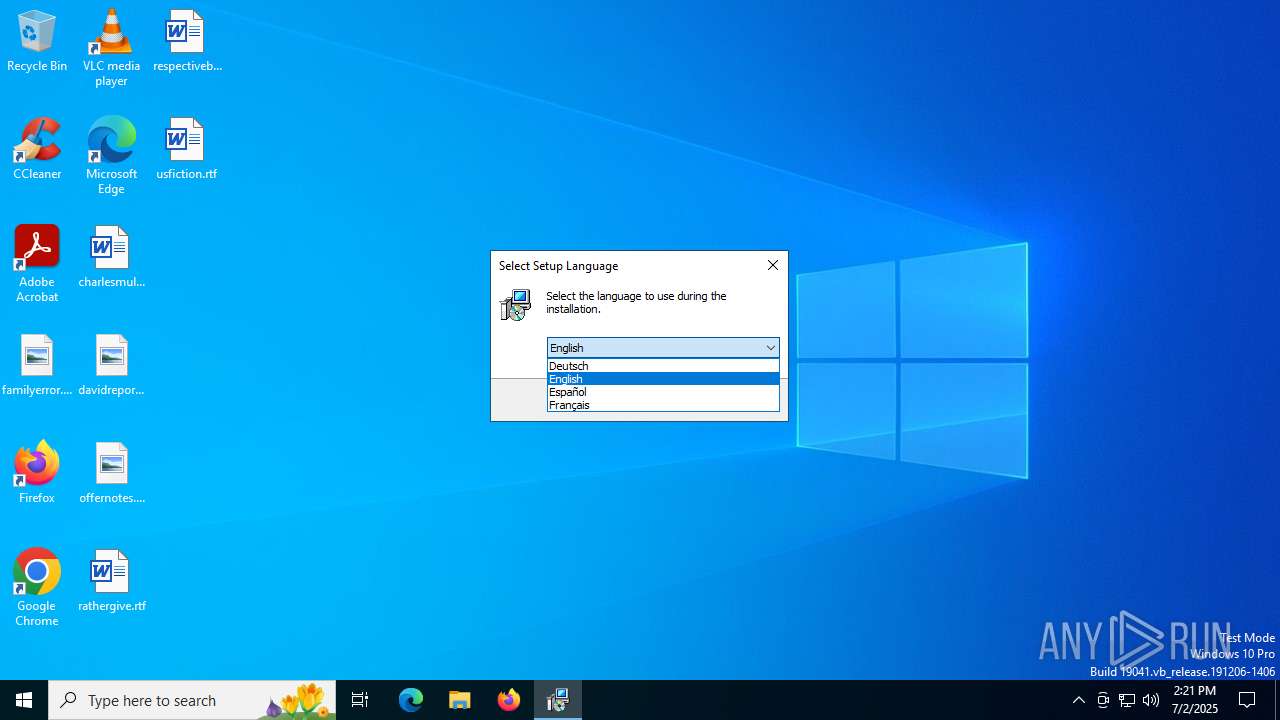
| 1044 | "C:\Users\admin\AppData\Local\Temp\is-5S56A.tmp\MegaDownloader_v1.8.tmp" /SL5="$60282,2536378,780288,C:\Users\admin\AppData\Local\Temp\MegaDownloader_v1.8.exe" | C:\Users\admin\AppData\Local\Temp\is-5S56A.tmp\MegaDownloader_v1.8.tmp | — | MegaDownloader_v1.8.exe | |||||||||||
User: admin Company: megadownloaderapp.blogspot.com Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1208 | "C:\Users\admin\AppData\Local\Temp\MegaDownloader_v1.8.exe" /SPAWNWND=$60374 /NOTIFYWND=$60282 | C:\Users\admin\AppData\Local\Temp\MegaDownloader_v1.8.exe | MegaDownloader_v1.8.tmp | ||||||||||||
User: admin Company: megadownloaderapp.blogspot.com Integrity Level: HIGH Description: MegaDownloader Setup Exit code: 0 Version: 1.8 Modules
| |||||||||||||||
| 2708 | "C:\Users\admin\AppData\Local\Temp\MegaDownloader_v1.8.exe" | C:\Users\admin\AppData\Local\Temp\MegaDownloader_v1.8.exe | explorer.exe | ||||||||||||
User: admin Company: megadownloaderapp.blogspot.com Integrity Level: MEDIUM Description: MegaDownloader Setup Exit code: 0 Version: 1.8 Modules
| |||||||||||||||
| 2976 | "C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe" --wake --system | C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater Exit code: 0 Version: 134.0.6985.0 Modules
| |||||||||||||||
| 3624 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4768 | "C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe" --crash-handler --system "--database=C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\Crashpad" --url=https://clients2.google.com/cr/report --annotation=prod=Update4 --annotation=ver=134.0.6985.0 "--attachment=C:\Program Files (x86)\Google\GoogleUpdater\updater.log" --initial-client-data=0x298,0x29c,0x2a0,0x274,0x2a4,0x111c460,0x111c46c,0x111c478 | C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe | — | updater.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater Exit code: 0 Version: 134.0.6985.0 Modules
| |||||||||||||||
| 6220 | "C:\Program Files\MegaDownloader\MegaDownloader.exe" | C:\Program Files\MegaDownloader\MegaDownloader.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: MegaDownloader Version: 1.0.0.0 Modules
| |||||||||||||||
| 6472 | "C:\Program Files\MegaDownloader\MegaDownloader.exe" | C:\Program Files\MegaDownloader\MegaDownloader.exe | MegaDownloader_v1.8.tmp | ||||||||||||
User: admin Integrity Level: MEDIUM Description: MegaDownloader Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6896 | "C:\Users\admin\AppData\Local\Temp\is-MIBND.tmp\MegaDownloader_v1.8.tmp" /SL5="$1202BA,2536378,780288,C:\Users\admin\AppData\Local\Temp\MegaDownloader_v1.8.exe" /SPAWNWND=$60374 /NOTIFYWND=$60282 | C:\Users\admin\AppData\Local\Temp\is-MIBND.tmp\MegaDownloader_v1.8.tmp | MegaDownloader_v1.8.exe | ||||||||||||
User: admin Company: megadownloaderapp.blogspot.com Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
5 885
Read events
5 844
Write events
40
Delete events
1
Modification events
| (PID) Process: | (6896) MegaDownloader_v1.8.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\mega |
| Operation: | write | Name: | URL protocol |
Value: | |||
| (PID) Process: | (6896) MegaDownloader_v1.8.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\MegaDownloader |
| Operation: | write | Name: | Installer |
Value: 1 | |||
| (PID) Process: | (6896) MegaDownloader_v1.8.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{C12C2297-65A4-4E64-9AE1-29F0D947FDA0}}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.0.4 (u) | |||
| (PID) Process: | (6896) MegaDownloader_v1.8.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{C12C2297-65A4-4E64-9AE1-29F0D947FDA0}}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\MegaDownloader | |||
| (PID) Process: | (6896) MegaDownloader_v1.8.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{C12C2297-65A4-4E64-9AE1-29F0D947FDA0}}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\MegaDownloader\ | |||
| (PID) Process: | (6896) MegaDownloader_v1.8.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{C12C2297-65A4-4E64-9AE1-29F0D947FDA0}}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: MegaDownloader | |||
| (PID) Process: | (6896) MegaDownloader_v1.8.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{C12C2297-65A4-4E64-9AE1-29F0D947FDA0}}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (6896) MegaDownloader_v1.8.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{C12C2297-65A4-4E64-9AE1-29F0D947FDA0}}_is1 |
| Operation: | write | Name: | Inno Setup: Selected Tasks |
Value: desktopicon | |||
| (PID) Process: | (6896) MegaDownloader_v1.8.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{C12C2297-65A4-4E64-9AE1-29F0D947FDA0}}_is1 |
| Operation: | write | Name: | Inno Setup: Deselected Tasks |
Value: quicklaunchicon | |||
| (PID) Process: | (6896) MegaDownloader_v1.8.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{C12C2297-65A4-4E64-9AE1-29F0D947FDA0}}_is1 |
| Operation: | write | Name: | Inno Setup: Language |
Value: en | |||
Executable files
8
Suspicious files
0
Text files
24
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6896 | MegaDownloader_v1.8.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\MegaDownloader\MegaDownloader.lnk | lnk | |
MD5:0E62C6E35BA1298E74B25B290FCC862F | SHA256:AAC6F2DAC33543A9C5FCDDADD1C1A6BD14B79BD09B5D1D0E03BDEA5F8CDBE204 | |||
| 6896 | MegaDownloader_v1.8.tmp | C:\Users\Public\Desktop\MegaDownloader.lnk | lnk | |
MD5:514FD7CC7BE609C42D5CFC82C984DEA1 | SHA256:51CF7A3F2C0DDA7781B21B846ADA3D733FB8459AA50DCF36BE4103F91BBBAECF | |||
| 6896 | MegaDownloader_v1.8.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\MegaDownloader\Uninstall MegaDownloader.lnk | lnk | |
MD5:97644E50FFF1695AF215CA67CDBECEC8 | SHA256:9663E5BC9654FF90EE93CAE669E7A1C508BA9C1490A49C0B4591D8C72621850F | |||
| 6472 | MegaDownloader.exe | C:\Users\admin\AppData\Local\MegaDownloader\Language\en-US.xml | xml | |
MD5:BF2E92AE7C472B30934B61F25E4F4F26 | SHA256:0327DEB81A52BAE540FC30873765D7C636F296DE64E093F1E3D34235AB68240C | |||
| 6472 | MegaDownloader.exe | C:\Users\admin\AppData\Local\MegaDownloader\Language\es-ES.xml | xml | |
MD5:5B112FE88E97A5ABEA97D130E034FCE5 | SHA256:37C3090D3E0E96B5798352180529301FC4140A2DCE6CF164AB7BEE8830D286F5 | |||
| 6896 | MegaDownloader_v1.8.tmp | C:\Program Files\MegaDownloader\unins000.dat | dat | |
MD5:91791BAAA804D8CC5AC9C7D9AAF55686 | SHA256:8CE3BB8DB3EB8A776E63FA978BB7A22D8E89F377BC3F6C63457EB7752DD5E82F | |||
| 6472 | MegaDownloader.exe | C:\Users\admin\AppData\Local\MegaDownloader\Language\fr-FR.xml | xml | |
MD5:F6A68C9F9AA1138EF0E3E2DBB7EA3EB6 | SHA256:81D8348D26A2A7E68797757C48632A0633B979CD473FC6349BF789CD7C9FE350 | |||
| 6896 | MegaDownloader_v1.8.tmp | C:\Program Files\MegaDownloader\is-G9F3U.tmp | executable | |
MD5:F3B0A05D8683D57861E9A42F451F7349 | SHA256:388AF83E7AB90E23BEB0F662C3E08211F63230A7F985E92D4B4D559D8D62B556 | |||
| 2708 | MegaDownloader_v1.8.exe | C:\Users\admin\AppData\Local\Temp\is-5S56A.tmp\MegaDownloader_v1.8.tmp | executable | |
MD5:96EB39B5D1650DAAB0A9FDE463532DBA | SHA256:CEE4083982FEB0E7B78423295621A98EC63DF522CF4475E3CC103AB3A95C0896 | |||
| 6896 | MegaDownloader_v1.8.tmp | C:\Users\admin\AppData\Local\Temp\is-J67F5.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
47
DNS requests
31
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7020 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.192.153.142:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
6492 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1388 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6492 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4808 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7020 | svchost.exe | 40.126.31.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7020 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4140 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
www.mega.nz |
| whitelisted |
www.checkforupdates.ovh |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
6472 | MegaDownloader.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
6220 | MegaDownloader.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
2200 | svchost.exe | Misc activity | INFO [ANY.RUN] Possible short link service (bit .ly) |