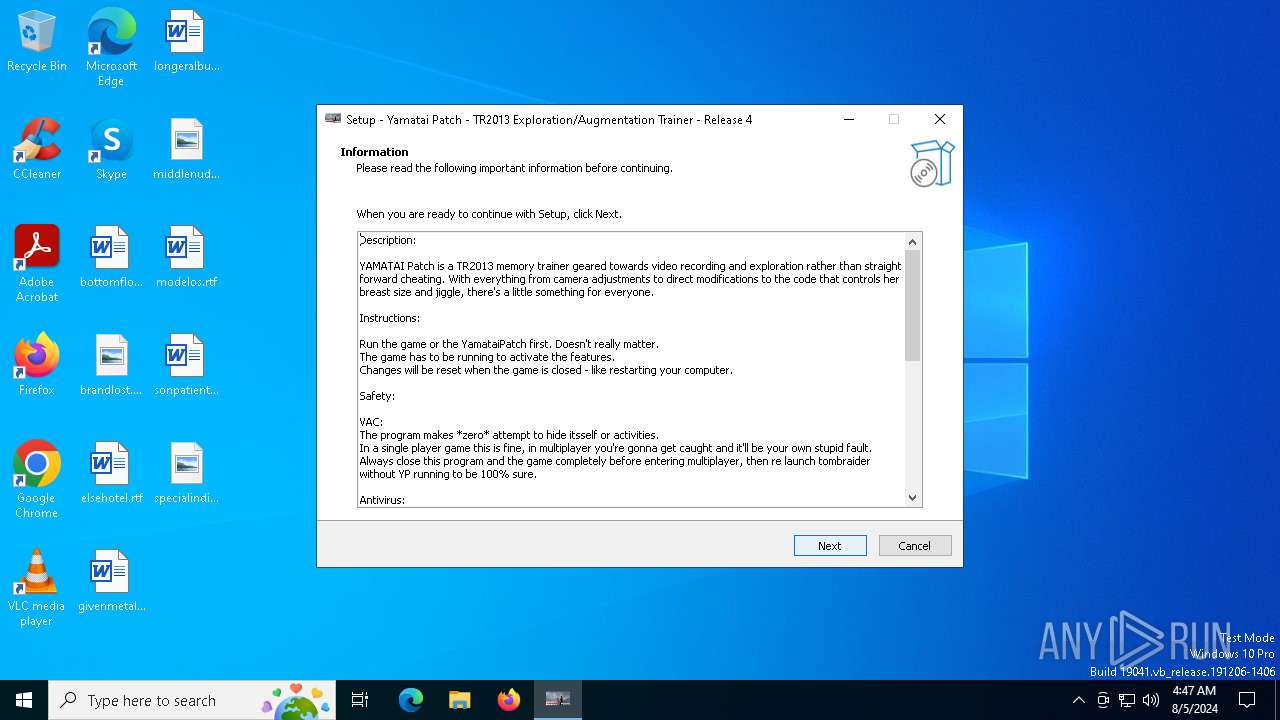
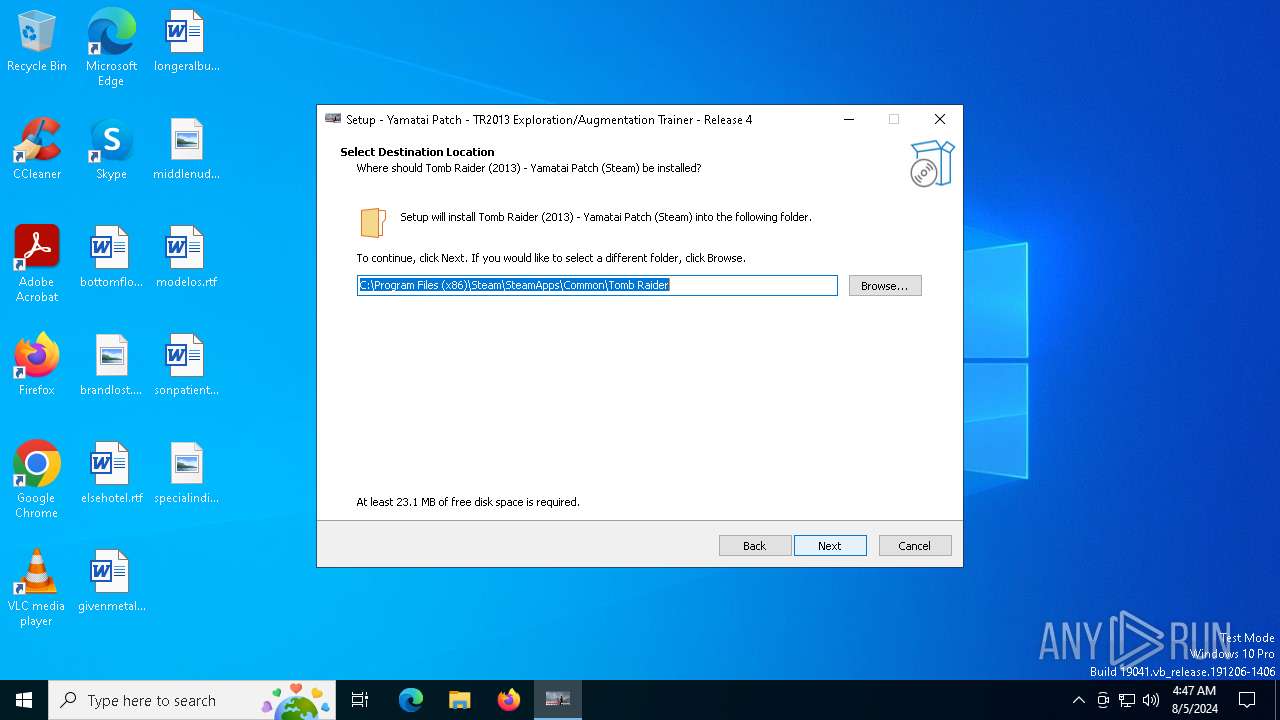
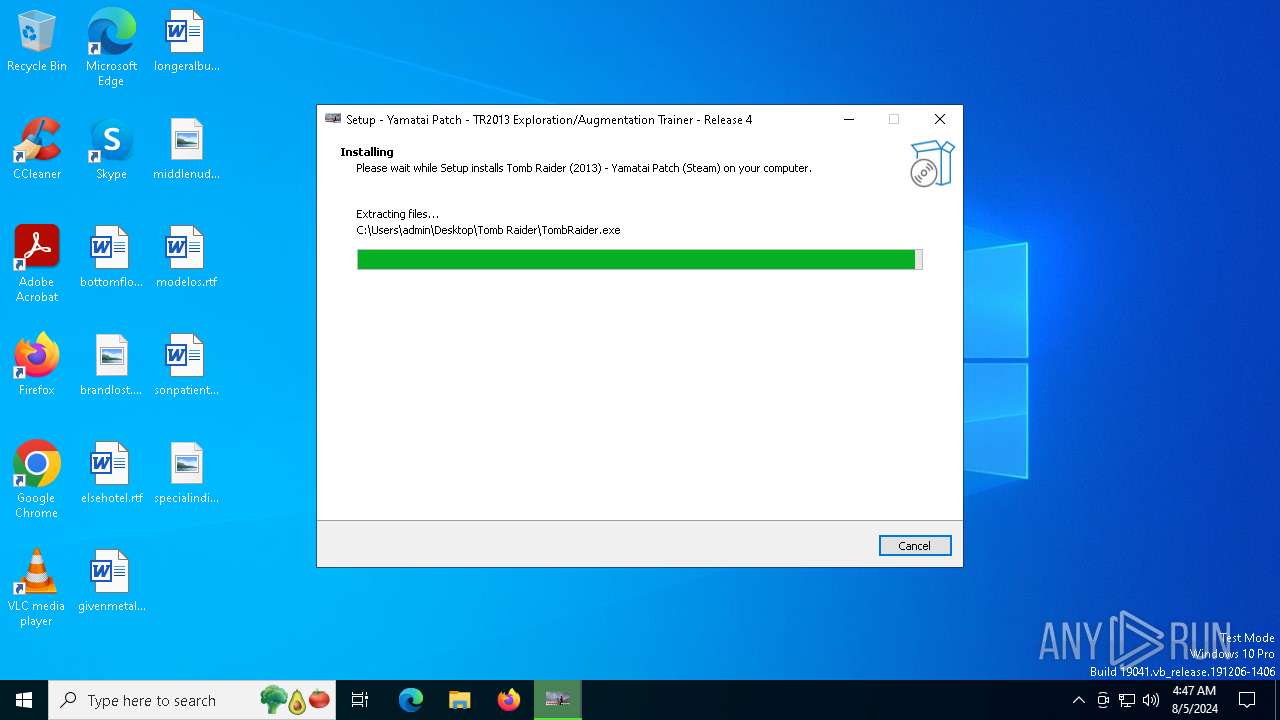
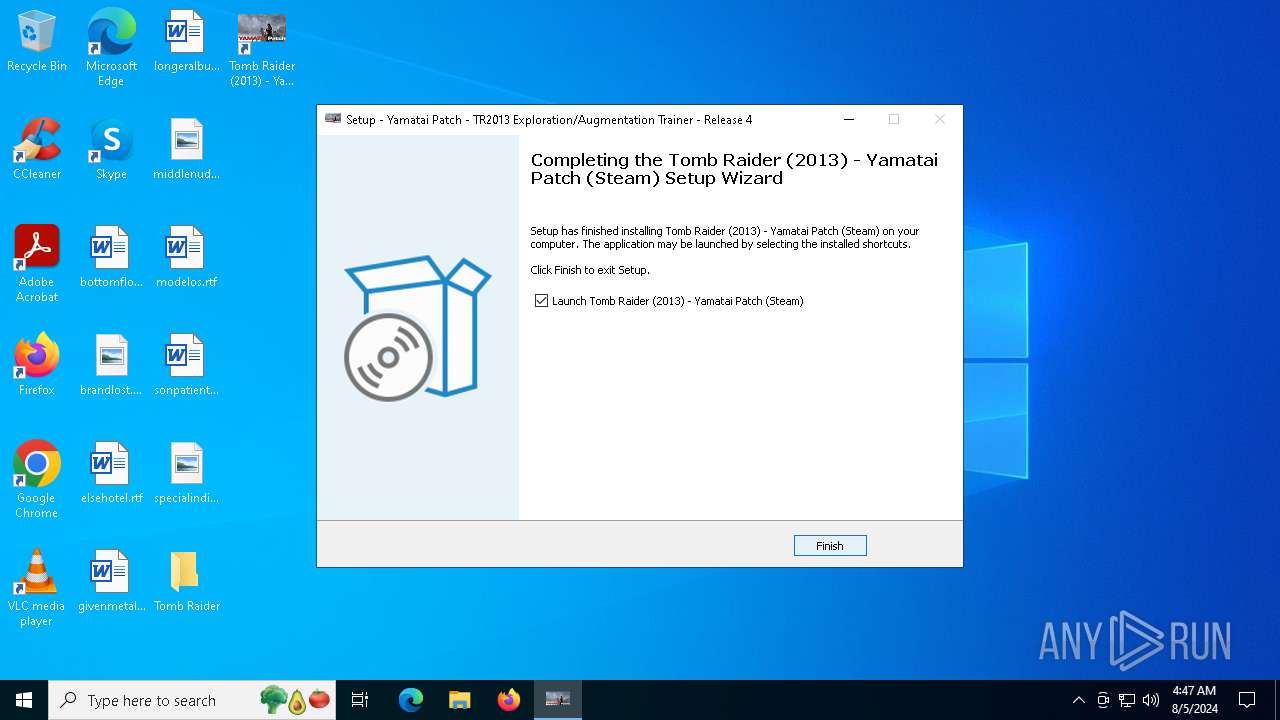
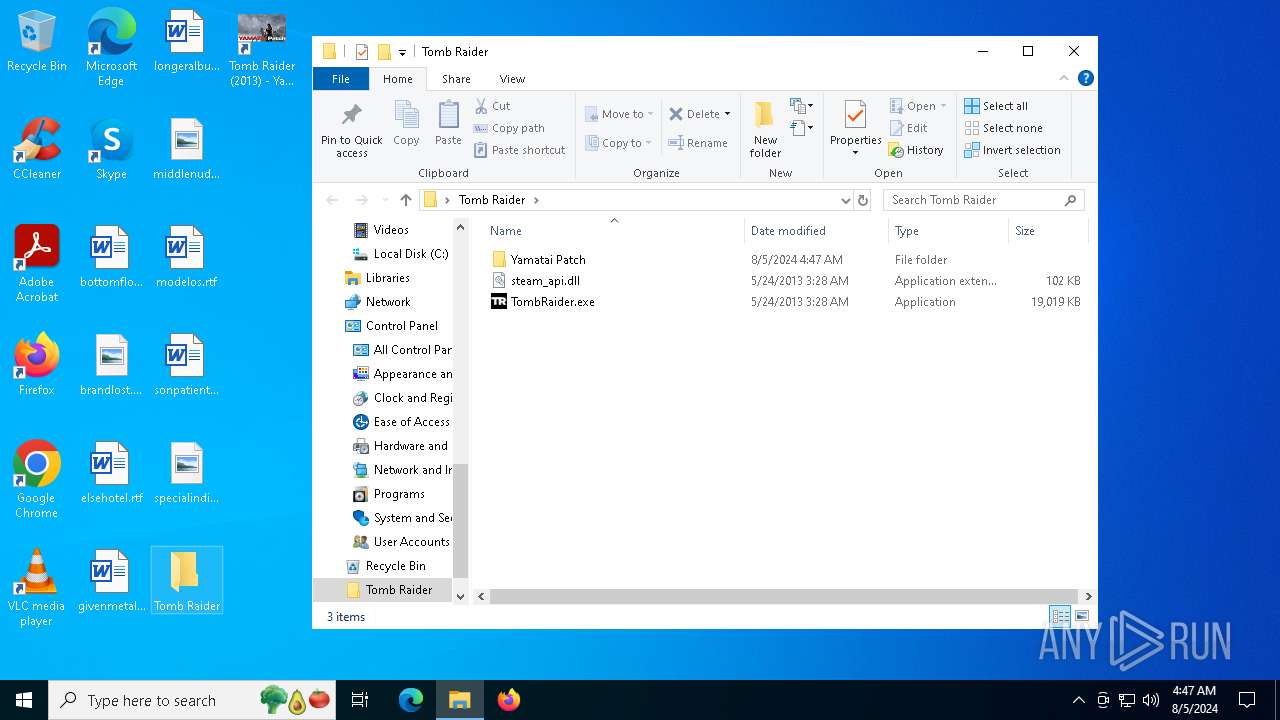
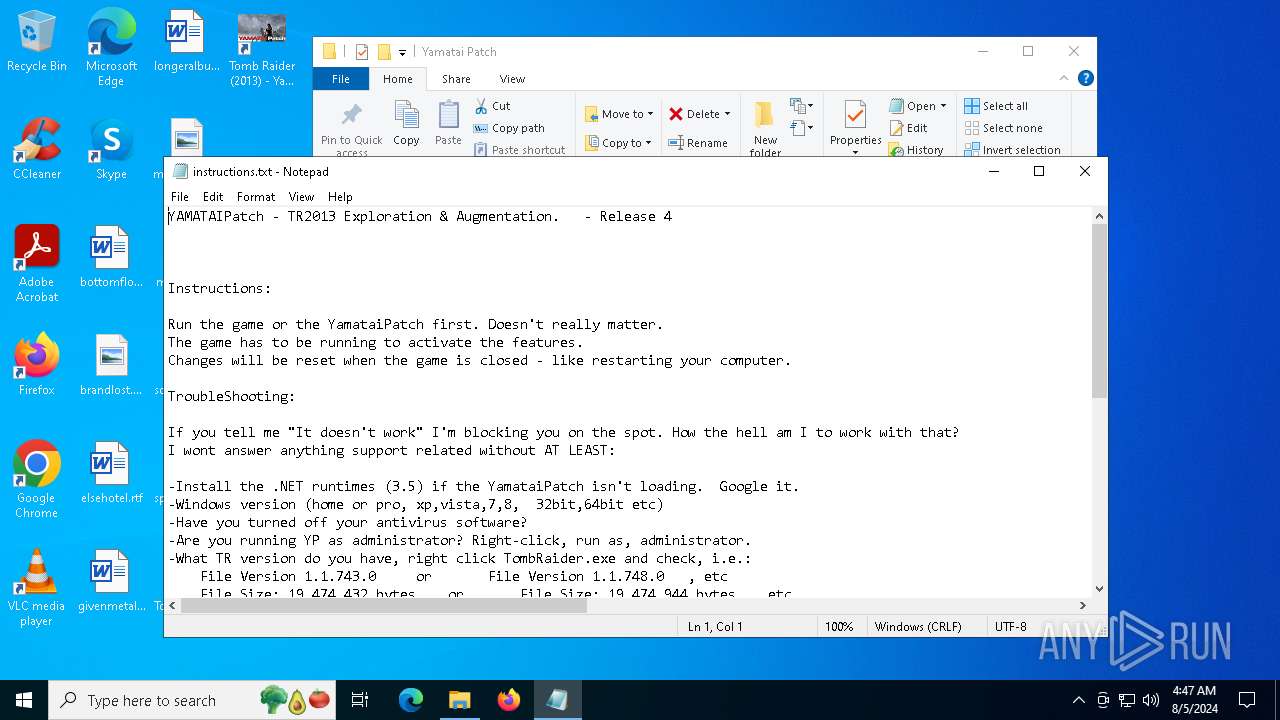
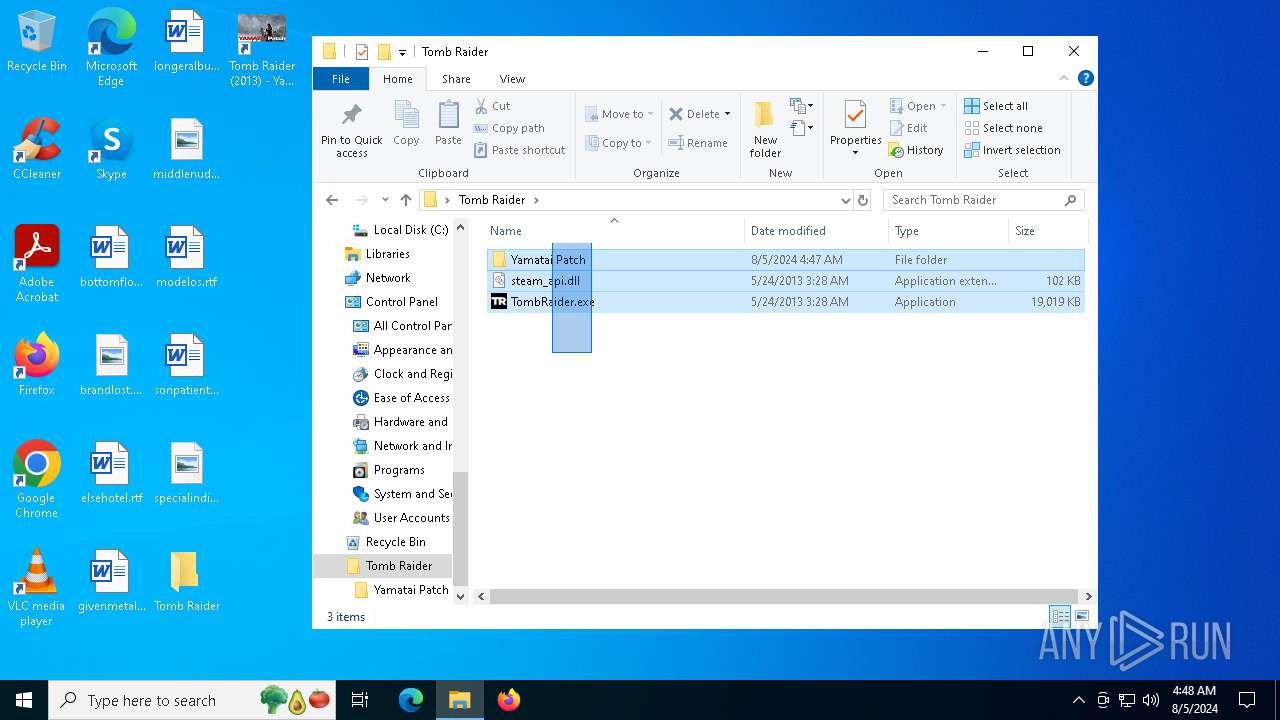
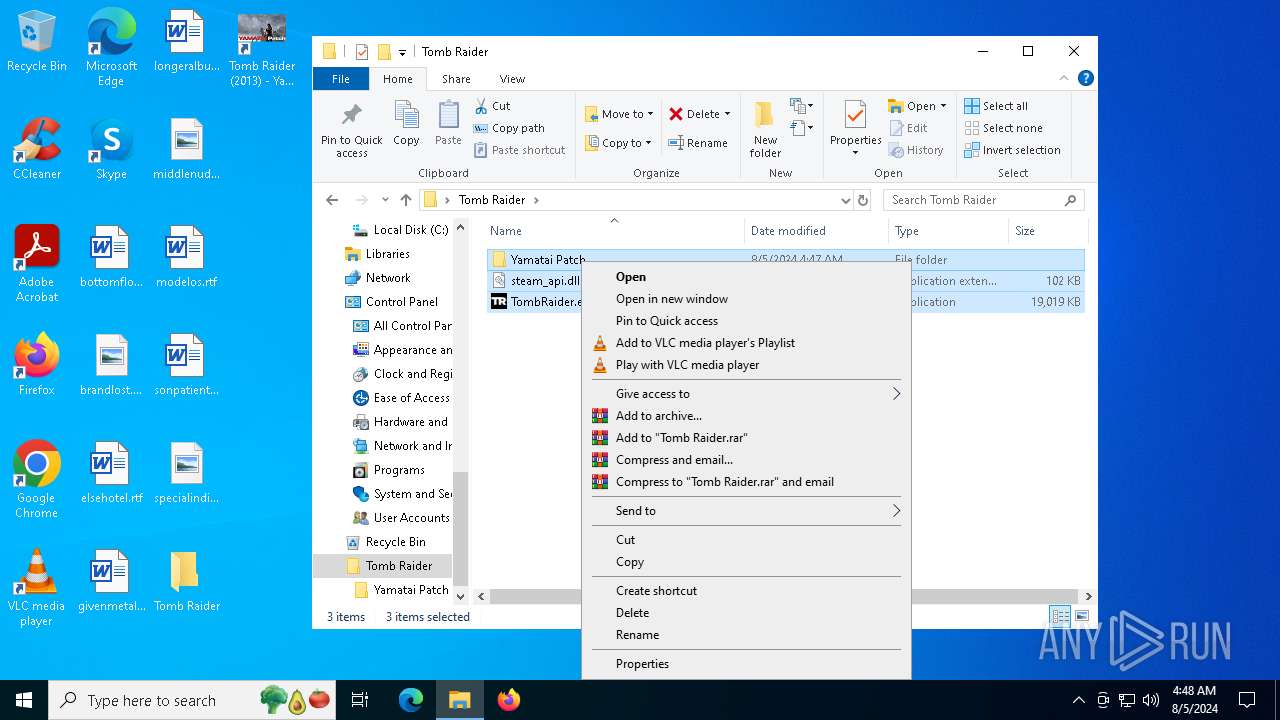
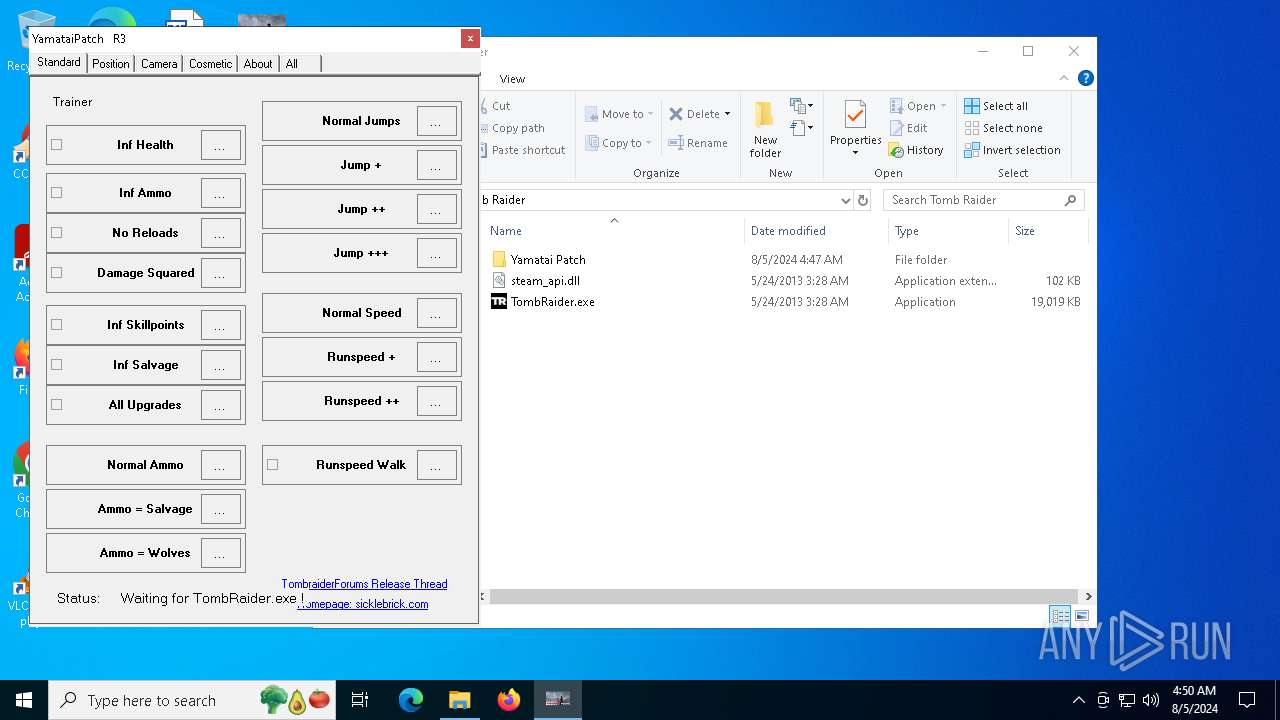
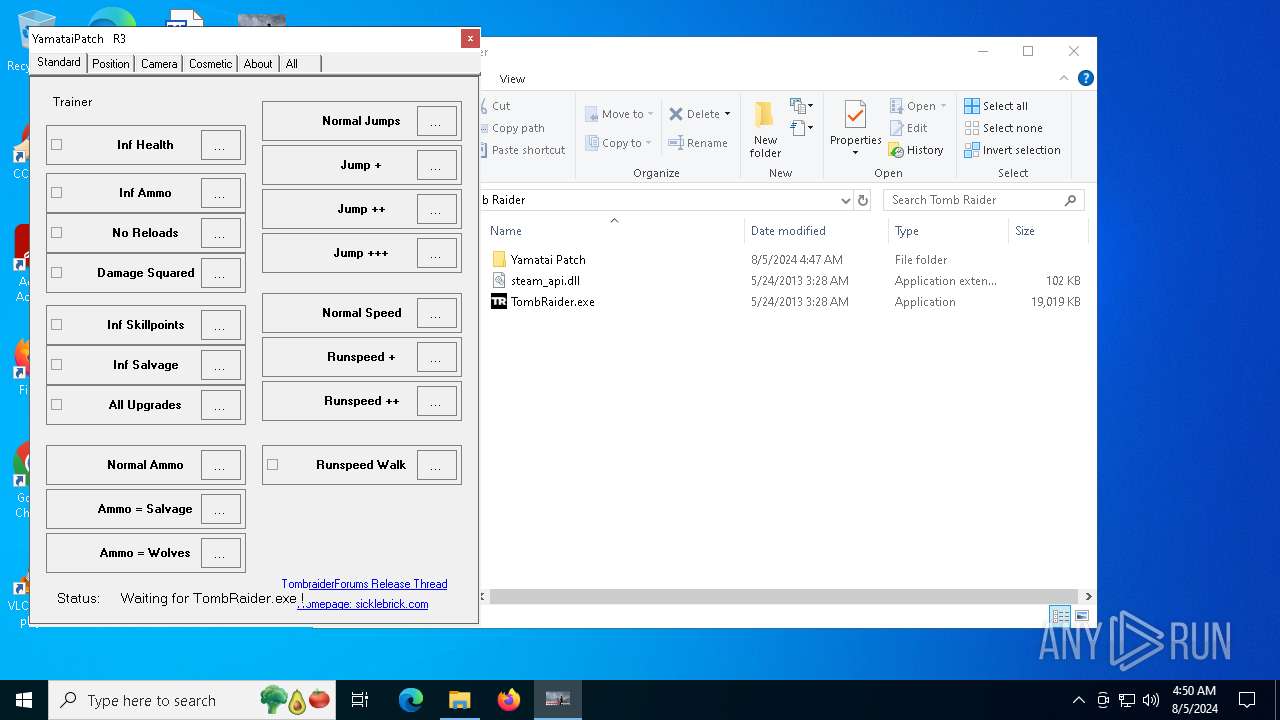
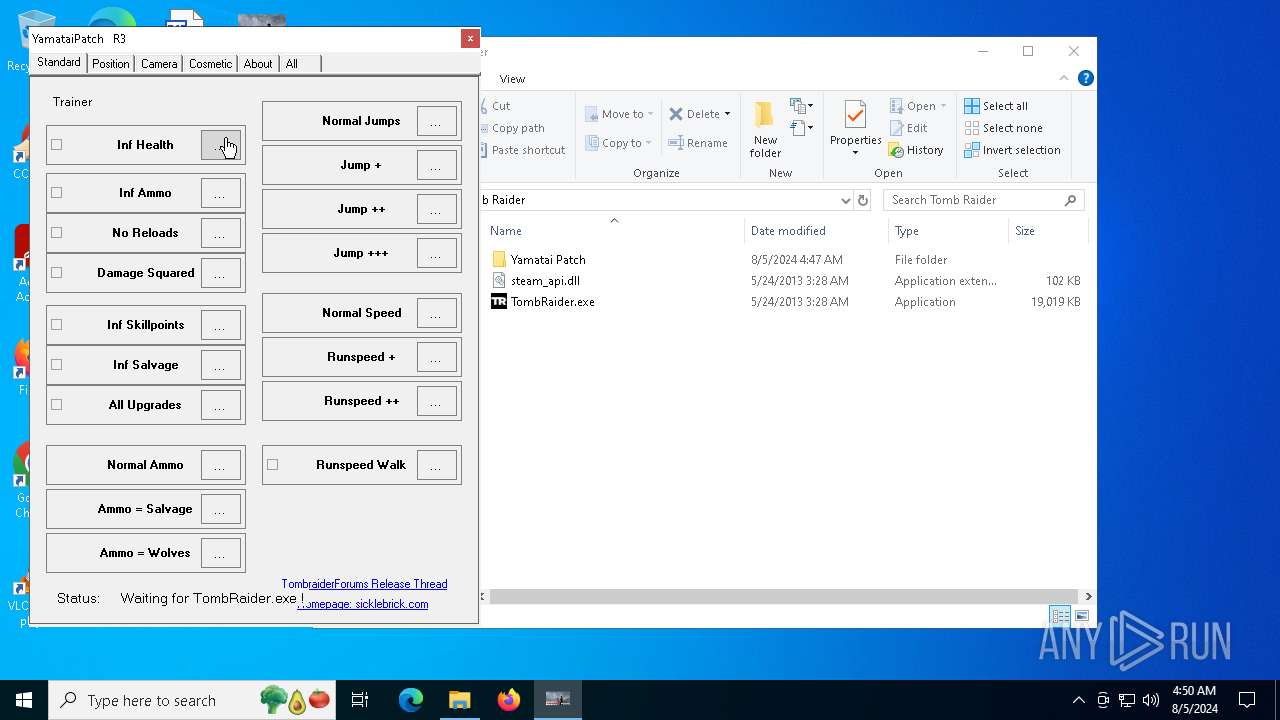
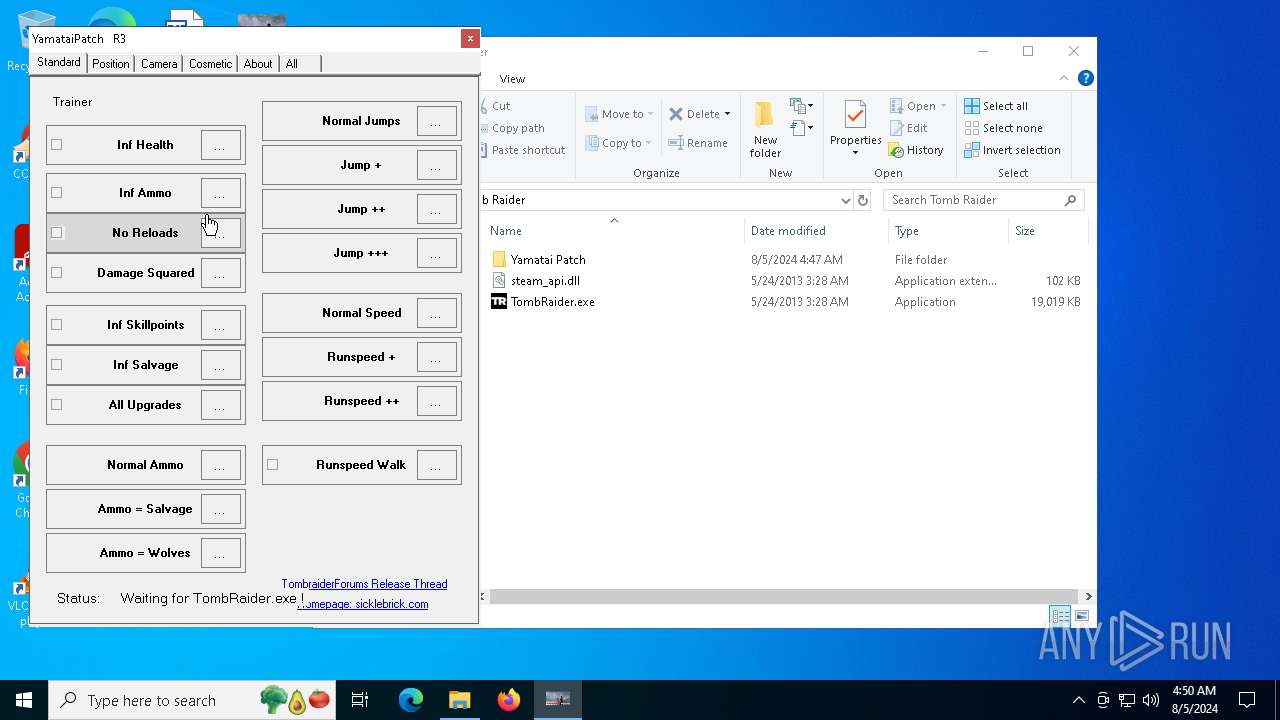
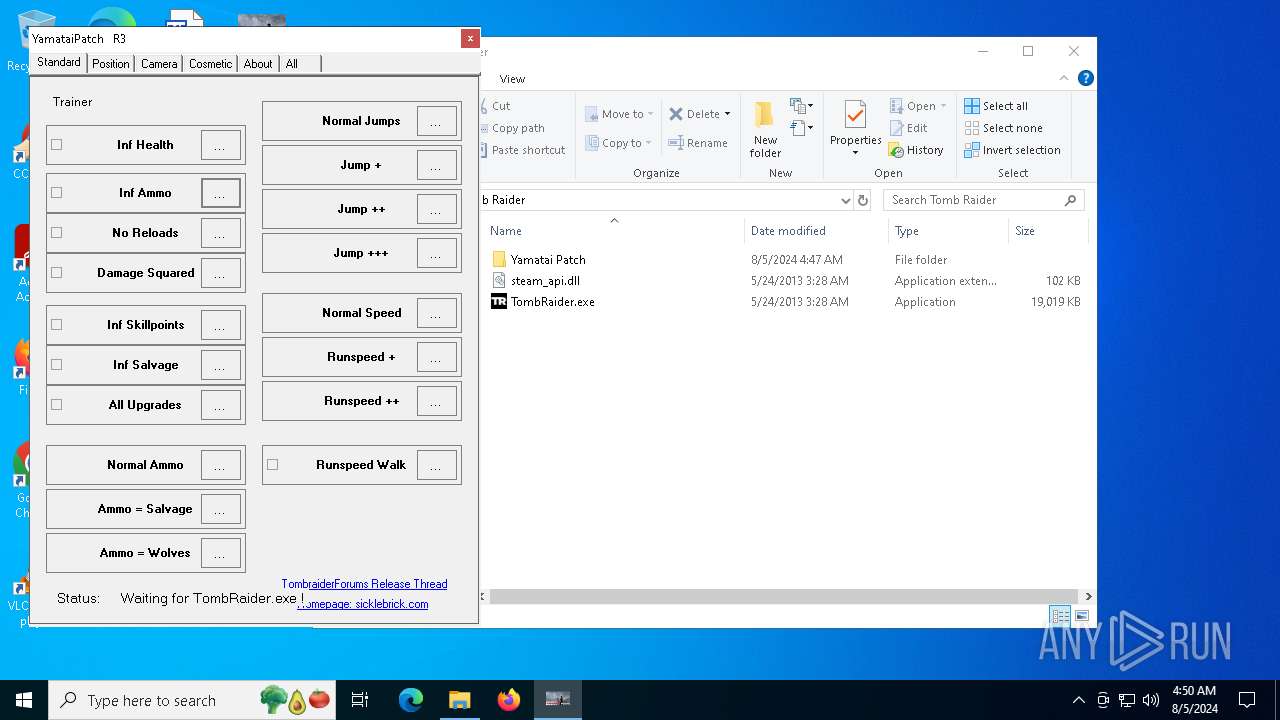
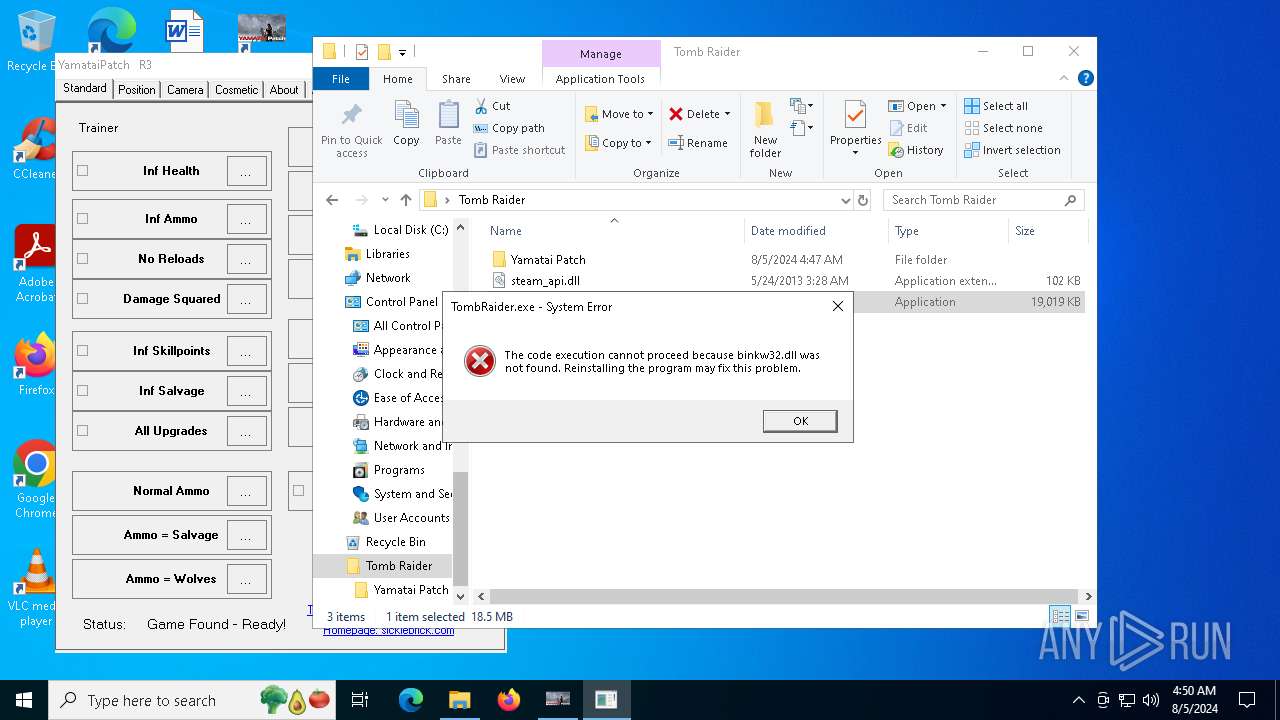
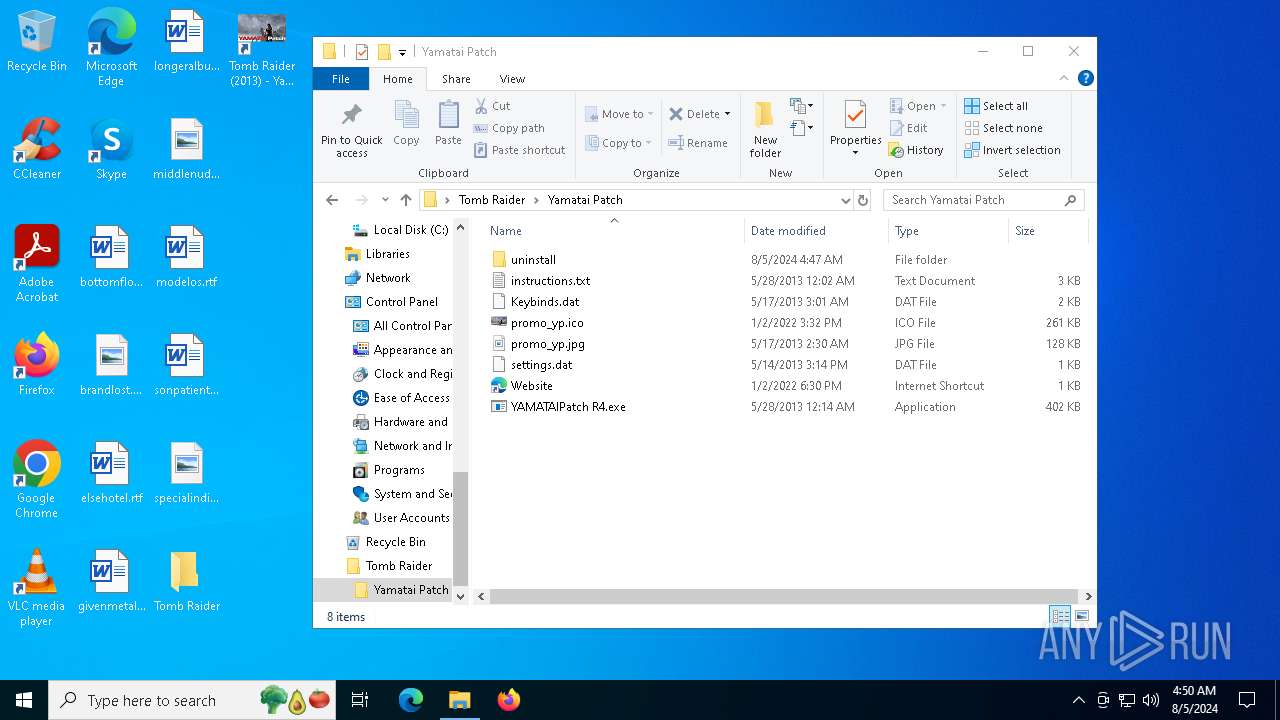
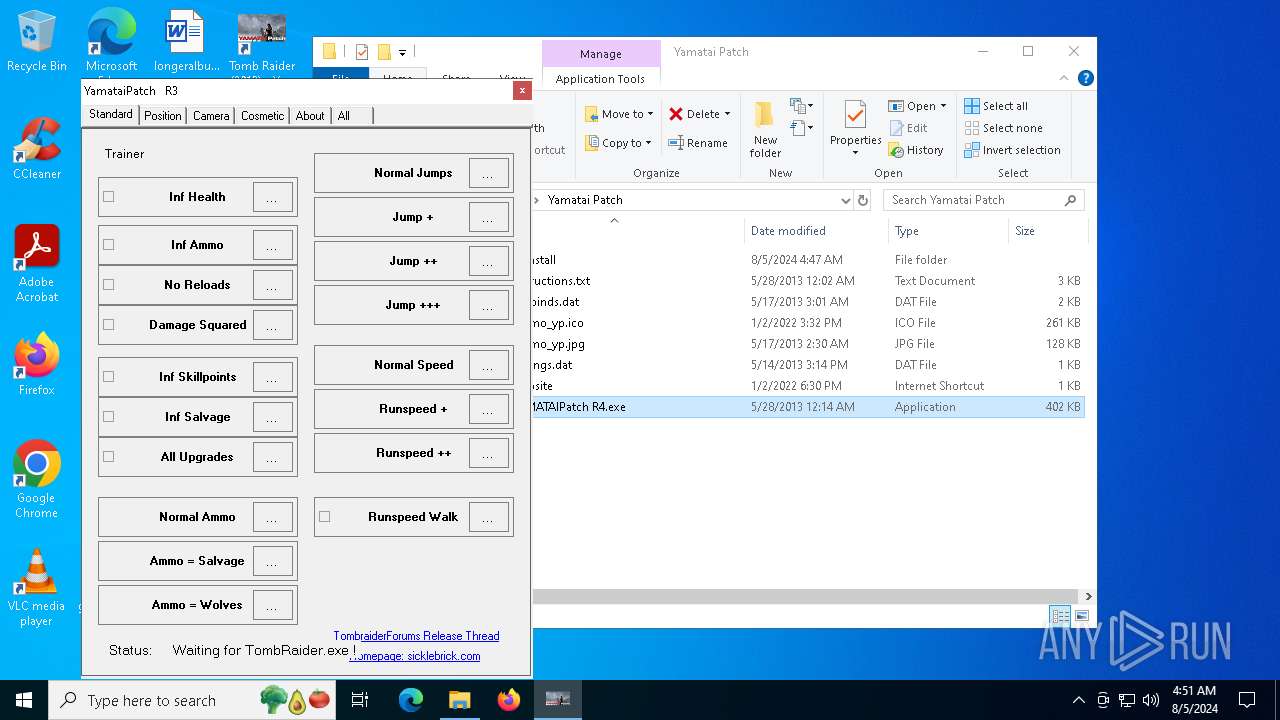
| File name: | TR 2013 Yamatai Patch R4 Setup.exe |
| Full analysis: | https://app.any.run/tasks/6fc2d89f-ea1c-4676-bcbe-f92248d07693 |
| Verdict: | Malicious activity |
| Analysis date: | August 05, 2024, 04:46:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 7B50E3BE317C63A9C0083171C38D6A98 |
| SHA1: | DBA2E65DBF9010705F4F73E03322CCB76C023B3B |
| SHA256: | 7656EFA621D58E3B0FE26DF0D55E781F7B80723B32C7B48EBDCD99A5F7074A22 |
| SSDEEP: | 98304:t+QqZ8fwlTyme4zgrHfRVet2fc2R5oBykSTiFW94gu3jnHVC99eXv5cCxVe2YQgN:cLBTy9UkEhskPG |
MALICIOUS
Drops the executable file immediately after the start
- TR 2013 Yamatai Patch R4 Setup.exe (PID: 6416)
- TR 2013 Yamatai Patch R4 Setup.tmp (PID: 6440)
SUSPICIOUS
Executable content was dropped or overwritten
- TR 2013 Yamatai Patch R4 Setup.tmp (PID: 6440)
- TR 2013 Yamatai Patch R4 Setup.exe (PID: 6416)
Reads security settings of Internet Explorer
- TR 2013 Yamatai Patch R4 Setup.tmp (PID: 6440)
- YAMATAIPatch R4.exe (PID: 3900)
Reads Internet Explorer settings
- YAMATAIPatch R4.exe (PID: 6668)
- YAMATAIPatch R4.exe (PID: 6408)
- YAMATAIPatch R4.exe (PID: 3900)
Reads the Windows owner or organization settings
- TR 2013 Yamatai Patch R4 Setup.tmp (PID: 6440)
INFO
Checks supported languages
- TR 2013 Yamatai Patch R4 Setup.tmp (PID: 6440)
- YAMATAIPatch R4.exe (PID: 6668)
- TR 2013 Yamatai Patch R4 Setup.exe (PID: 6416)
- YAMATAIPatch R4.exe (PID: 3900)
- YAMATAIPatch R4.exe (PID: 6408)
- TextInputHost.exe (PID: 2248)
- TombRaider.exe (PID: 3032)
- identity_helper.exe (PID: 964)
- identity_helper.exe (PID: 6712)
- identity_helper.exe (PID: 5704)
Manual execution by a user
- notepad.exe (PID: 1044)
- YAMATAIPatch R4.exe (PID: 6668)
- YAMATAIPatch R4.exe (PID: 6408)
- TombRaider.exe (PID: 3032)
- YAMATAIPatch R4.exe (PID: 3900)
Reads the computer name
- YAMATAIPatch R4.exe (PID: 6668)
- YAMATAIPatch R4.exe (PID: 3900)
- YAMATAIPatch R4.exe (PID: 6408)
- TextInputHost.exe (PID: 2248)
- identity_helper.exe (PID: 964)
- identity_helper.exe (PID: 5704)
- identity_helper.exe (PID: 6712)
- TR 2013 Yamatai Patch R4 Setup.tmp (PID: 6440)
Creates files or folders in the user directory
- TR 2013 Yamatai Patch R4 Setup.tmp (PID: 6440)
Reads security settings of Internet Explorer
- notepad.exe (PID: 1044)
Reads Microsoft Office registry keys
- YAMATAIPatch R4.exe (PID: 3900)
- msedge.exe (PID: 5240)
- msedge.exe (PID: 6912)
- msedge.exe (PID: 4192)
Application launched itself
- msedge.exe (PID: 5240)
- msedge.exe (PID: 4192)
- msedge.exe (PID: 6912)
Reads Environment values
- identity_helper.exe (PID: 964)
- identity_helper.exe (PID: 5704)
- identity_helper.exe (PID: 6712)
Drops the executable file immediately after the start
- msedge.exe (PID: 5240)
Create files in a temporary directory
- TR 2013 Yamatai Patch R4 Setup.tmp (PID: 6440)
- TR 2013 Yamatai Patch R4 Setup.exe (PID: 6416)
Creates a software uninstall entry
- TR 2013 Yamatai Patch R4 Setup.tmp (PID: 6440)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:06:03 08:09:11+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741376 |
| InitializedDataSize: | 301056 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Application by sicklebrick, installer by Dekaya |
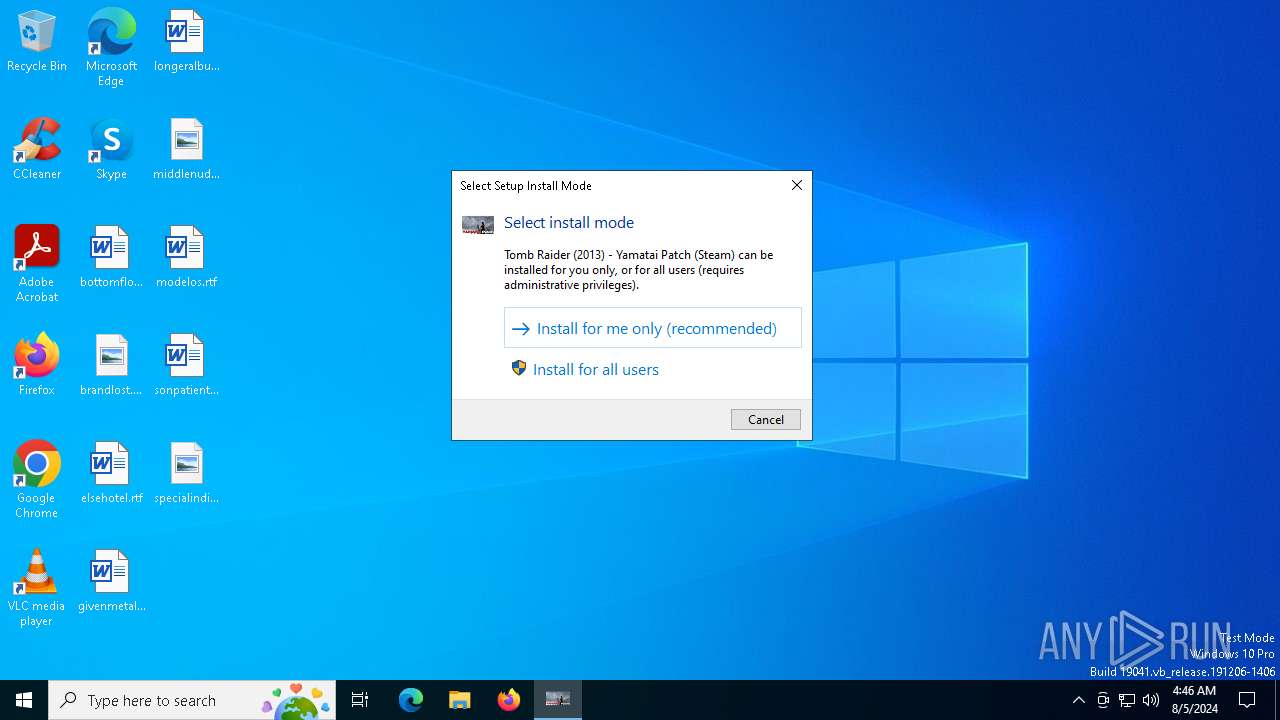
| FileDescription: | Tomb Raider (2013) - Yamatai Patch (Steam) Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | Tomb Raider (2013) - Yamatai Patch (Steam) |
| ProductVersion: | Release 4 |
Total processes
215
Monitored processes
76
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --no-appcompat-clear --mojo-platform-channel-handle=5628 --field-trial-handle=2376,i,6414690920882608803,16719115195034738060,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 752 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument http://sicklebrick.com/?p=513 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | YAMATAIPatch R4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 964 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6280 --field-trial-handle=2336,i,304402009833614458,15156757174613865654,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
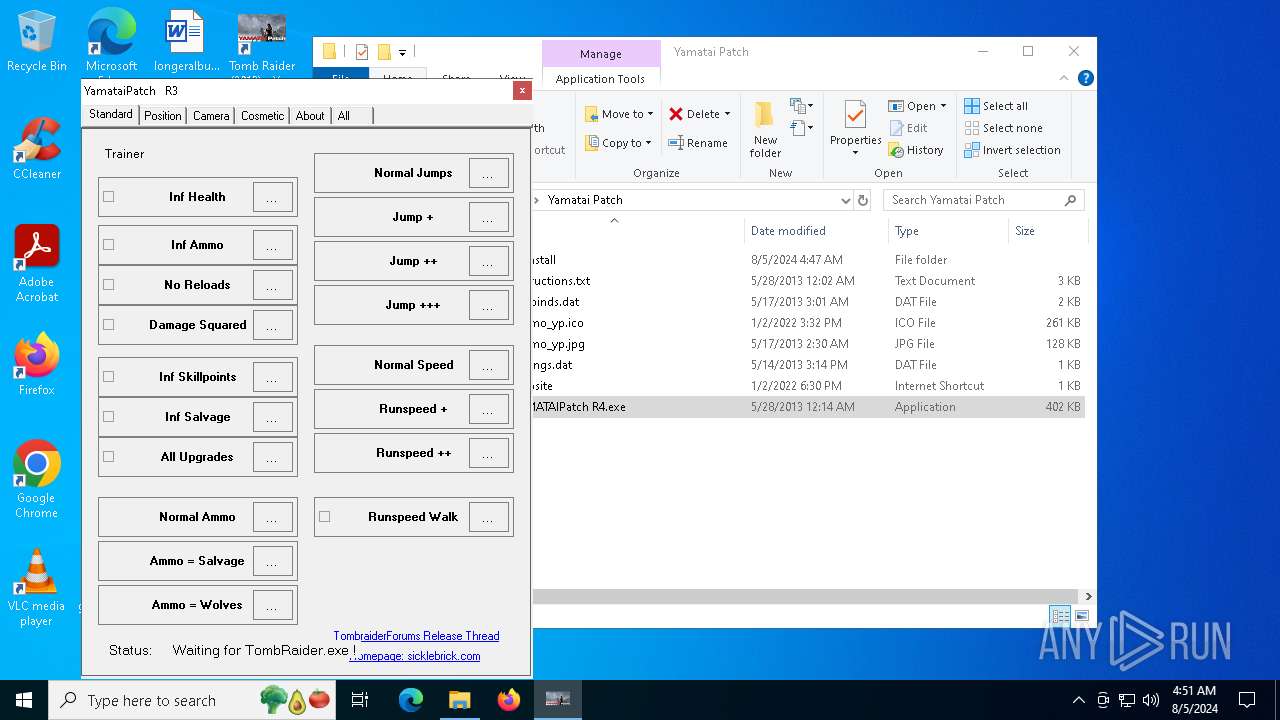
| 1044 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Tomb Raider\Yamatai Patch\instructions.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1140 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4168 --field-trial-handle=2376,i,6414690920882608803,16719115195034738060,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1168 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2580 --field-trial-handle=2376,i,6414690920882608803,16719115195034738060,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1216 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5192 --field-trial-handle=2312,i,9809709195638224968,1041148713302238680,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1564 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1812 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5896 --field-trial-handle=2336,i,304402009833614458,15156757174613865654,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2136 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4048 --field-trial-handle=2336,i,304402009833614458,15156757174613865654,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
26 684
Read events
26 486
Write events
187
Delete events
11
Modification events
| (PID) Process: | (6440) TR 2013 Yamatai Patch R4 Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 281900008C37CE7EF2E6DA01 | |||
| (PID) Process: | (6440) TR 2013 Yamatai Patch R4 Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 52DF9C94176CF23E2A89CE3A2473F956EE4710ED912C3E4AB5EEC271F22CACE5 | |||
| (PID) Process: | (6440) TR 2013 Yamatai Patch R4 Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6440) TR 2013 Yamatai Patch R4 Setup.tmp | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\Program Files (x86)\Common Files\system\wab32res.dll,-10100 |
Value: Contacts | |||
| (PID) Process: | (6440) TR 2013 Yamatai Patch R4 Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6440) TR 2013 Yamatai Patch R4 Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6440) TR 2013 Yamatai Patch R4 Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6440) TR 2013 Yamatai Patch R4 Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6440) TR 2013 Yamatai Patch R4 Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
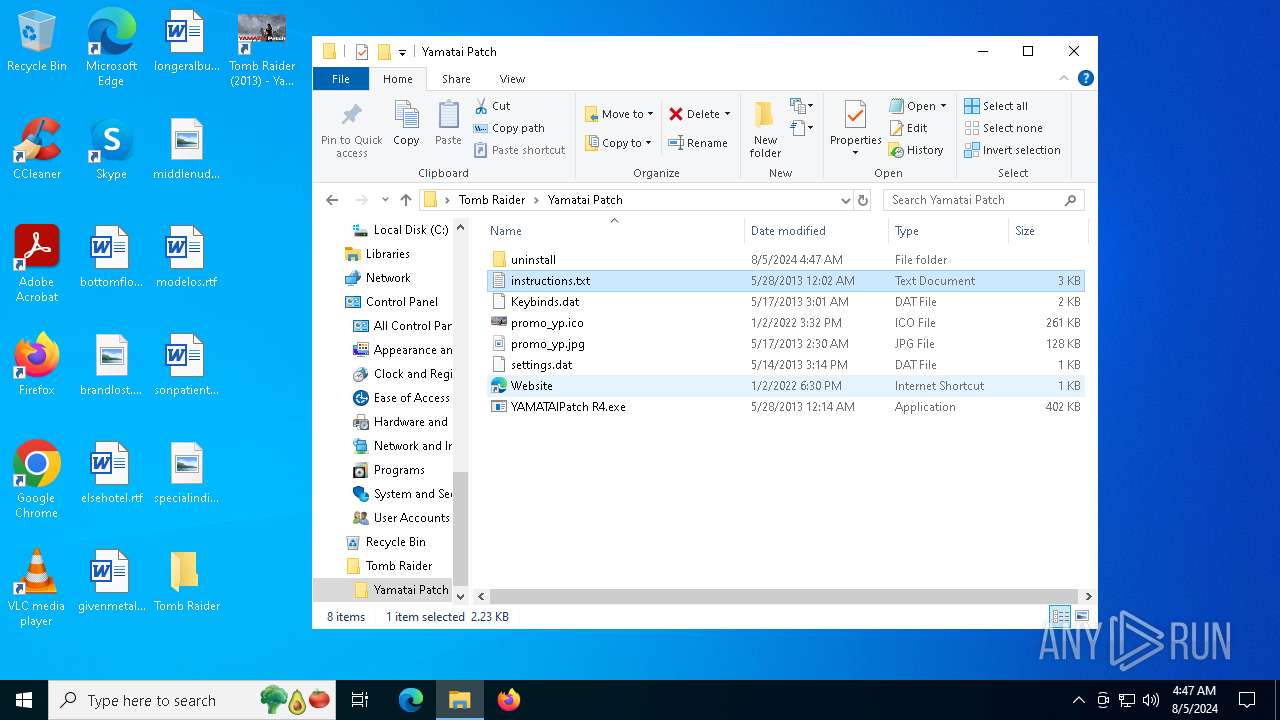
Value: C:\Users\admin\Desktop\Tomb Raider\Yamatai Patch\YAMATAIPatch R4.exe | |||
| (PID) Process: | (6440) TR 2013 Yamatai Patch R4 Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 9627316C5D77319461FC268B708C1885FFC7AD676B203874374B1A8E1F221A0A | |||
Executable files
12
Suspicious files
148
Text files
131
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6440 | TR 2013 Yamatai Patch R4 Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-J3JL2.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 6440 | TR 2013 Yamatai Patch R4 Setup.tmp | C:\Users\admin\Desktop\Tomb Raider\Yamatai Patch\uninstall\is-46AS2.tmp | executable | |
MD5:FFF146003CFAE7961C4C3FDA415B2ADC | SHA256:49966D0F8E2BB1EBA933BABC49D5E4D0924D7DD87D2E6A7A80E44199169F85D1 | |||
| 6440 | TR 2013 Yamatai Patch R4 Setup.tmp | C:\Users\admin\Desktop\Tomb Raider\Yamatai Patch\is-KFTI6.tmp | executable | |
MD5:377AD37FF123FE131364AF8135607E5C | SHA256:592E8D198684ABD15342BE1566780CAD25771752A43FF81B3A3F0757A1A66E0F | |||
| 6440 | TR 2013 Yamatai Patch R4 Setup.tmp | C:\Users\admin\Desktop\Tomb Raider\Yamatai Patch\is-951DD.tmp | text | |
MD5:1960F0670D35E3F986932F546F470741 | SHA256:156B13A43BAA71A6BEE9AFD1F404F5A062970C36A40C6001D20052AD6D38D092 | |||
| 6440 | TR 2013 Yamatai Patch R4 Setup.tmp | C:\Users\admin\Desktop\Tomb Raider\Yamatai Patch\is-6HQCI.tmp | binary | |
MD5:85A3E4C0335310E30CA0AF250A458F52 | SHA256:BFC75155F5A7503989E63B50E6A7772E4A5A1292E93B8804F3E0B1602A109166 | |||
| 6440 | TR 2013 Yamatai Patch R4 Setup.tmp | C:\Users\admin\Desktop\Tomb Raider\Yamatai Patch\uninstall\unins000.exe | executable | |
MD5:FFF146003CFAE7961C4C3FDA415B2ADC | SHA256:49966D0F8E2BB1EBA933BABC49D5E4D0924D7DD87D2E6A7A80E44199169F85D1 | |||
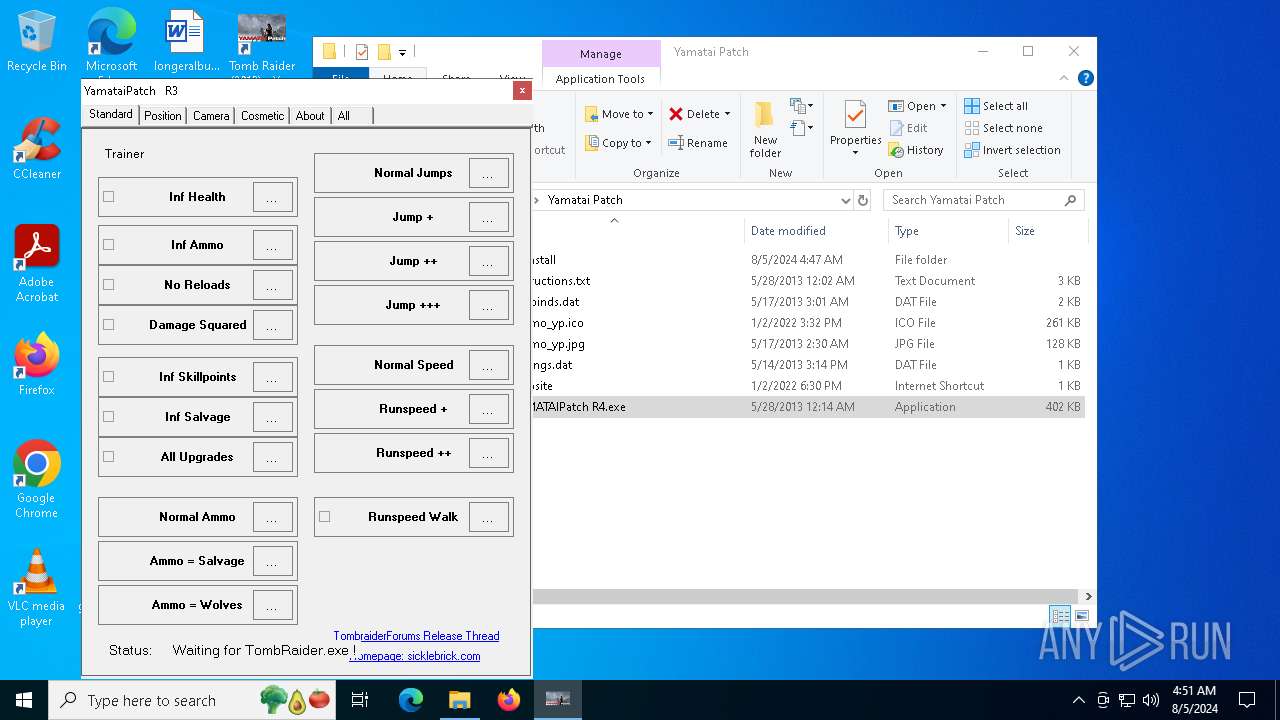
| 6440 | TR 2013 Yamatai Patch R4 Setup.tmp | C:\Users\admin\Desktop\Tomb Raider\Yamatai Patch\instructions.txt | text | |
MD5:DA2A1ACC549AB380664586ADE9753714 | SHA256:8B7E0F95ABC47C70AC2E6042B142ED6853C339CBA3DF452308A42F16A55298DE | |||
| 6416 | TR 2013 Yamatai Patch R4 Setup.exe | C:\Users\admin\AppData\Local\Temp\is-6M48J.tmp\TR 2013 Yamatai Patch R4 Setup.tmp | executable | |
MD5:4B85CC82F28DCA219FA8E2026F0DA698 | SHA256:E0337618CA8854FC759EE272E463FF9A81F74CDD6B71D06E0F96244E7D892166 | |||
| 6440 | TR 2013 Yamatai Patch R4 Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-J3JL2.tmp\_isetup\_iscrypt.dll | executable | |
MD5:A69559718AB506675E907FE49DEB71E9 | SHA256:2F6294F9AA09F59A574B5DCD33BE54E16B39377984F3D5658CDA44950FA0F8FC | |||
| 6440 | TR 2013 Yamatai Patch R4 Setup.tmp | C:\Users\admin\Desktop\Tomb Raider\Yamatai Patch\promo_yp.jpg | image | |
MD5:EAA12CAE36EBFCD4CC2E9727D494B875 | SHA256:ED01D3EE7F8BE3A5383101A3F1ACE993766D56E1D978C86CB2A84061D54B0D75 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
97
DNS requests
87
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6744 | msedge.exe | GET | 200 | 18.245.33.69:80 | http://d1a6zytsvzb7ig.cloudfront.net/newpanel/fonts/proxima-nova/proximanova-bold-webfont.woff2 | unknown | — | — | whitelisted |
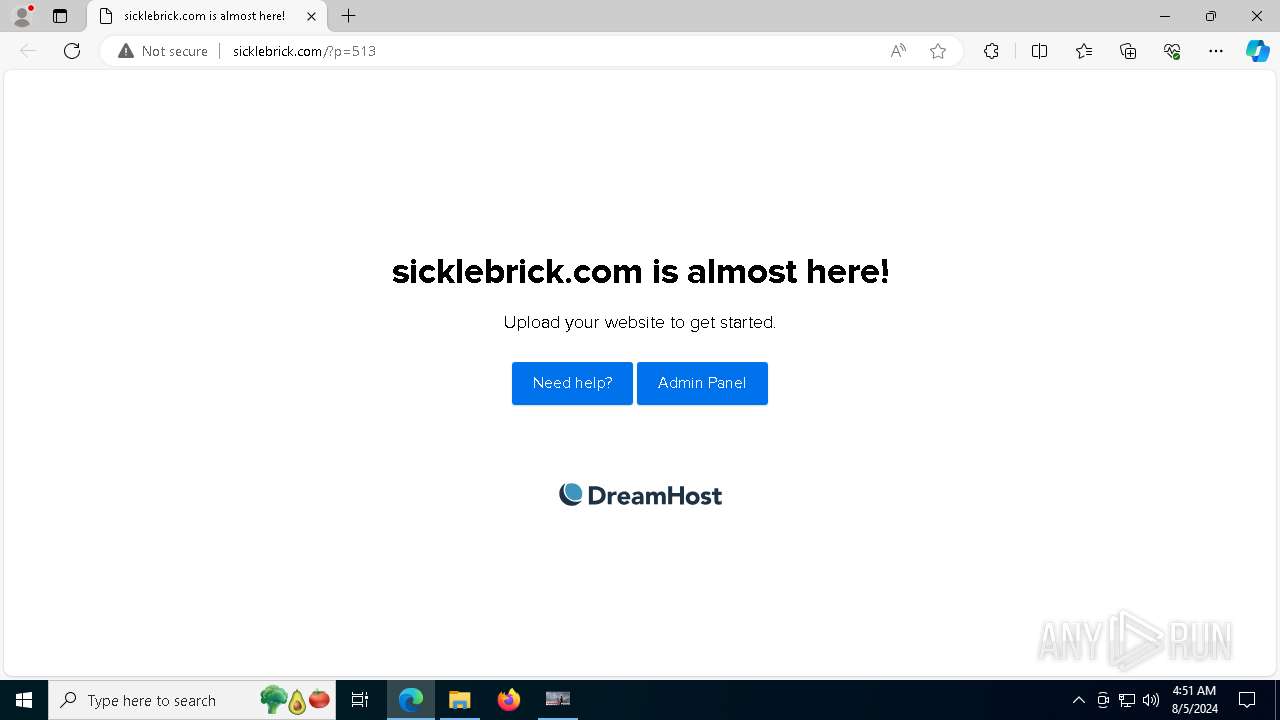
6744 | msedge.exe | GET | 200 | 75.119.207.34:80 | http://sicklebrick.com/?p=513 | unknown | — | — | unknown |
6744 | msedge.exe | GET | 200 | 18.245.33.69:80 | http://d1a6zytsvzb7ig.cloudfront.net/newpanel/css/singlepage.css | unknown | — | — | whitelisted |
6744 | msedge.exe | GET | 200 | 18.245.33.69:80 | http://d1a6zytsvzb7ig.cloudfront.net/newpanel/images/logo-a.svg | unknown | — | — | whitelisted |
6744 | msedge.exe | GET | 200 | 75.119.207.34:80 | http://sicklebrick.com/favicon.ico | unknown | — | — | unknown |
6744 | msedge.exe | GET | 200 | 18.245.33.69:80 | http://d1a6zytsvzb7ig.cloudfront.net/newpanel/fonts/proxima-nova/proximanova-reg-webfont.woff2 | unknown | — | — | whitelisted |
5196 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6784 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6832 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4208 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4016 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4208 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 104.126.37.186:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5196 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |