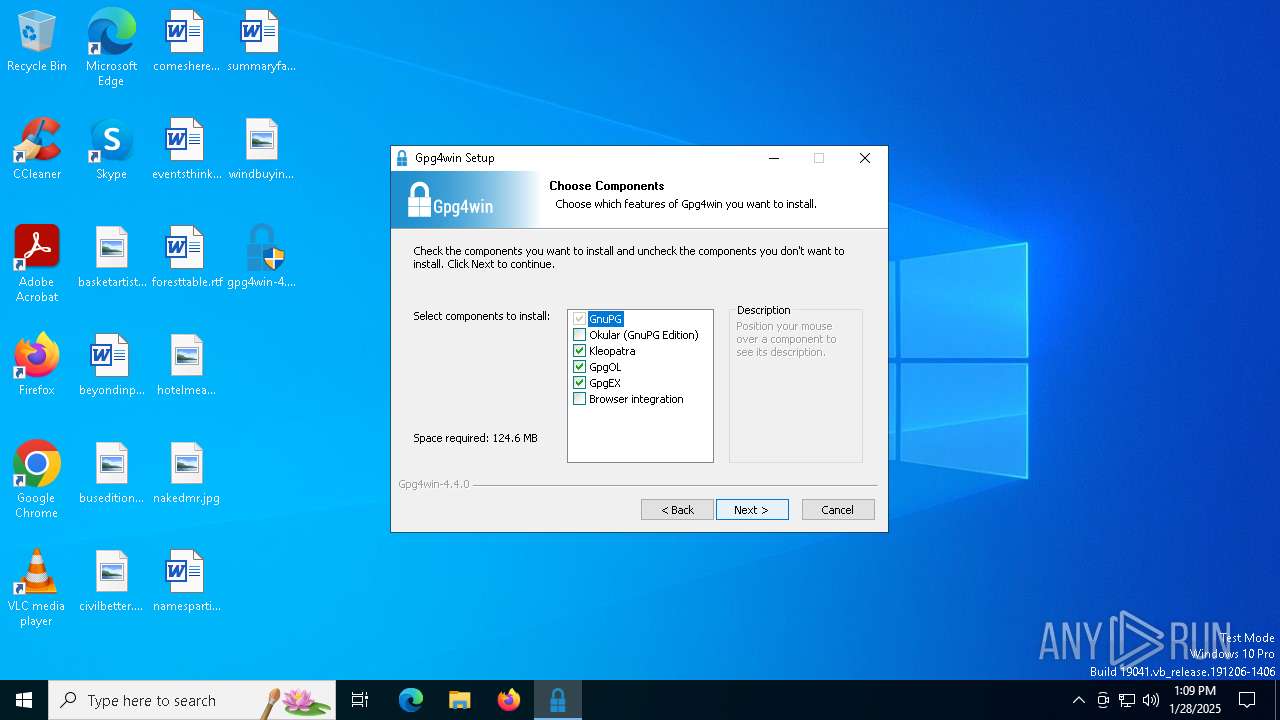
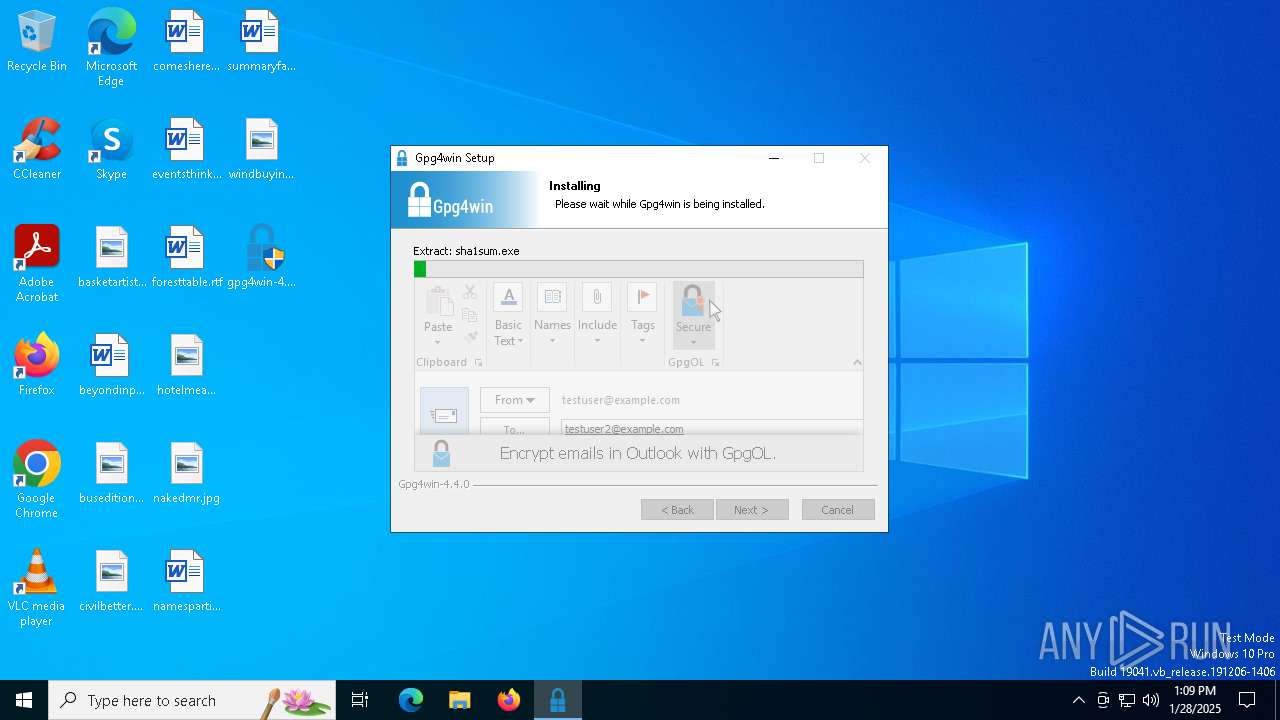
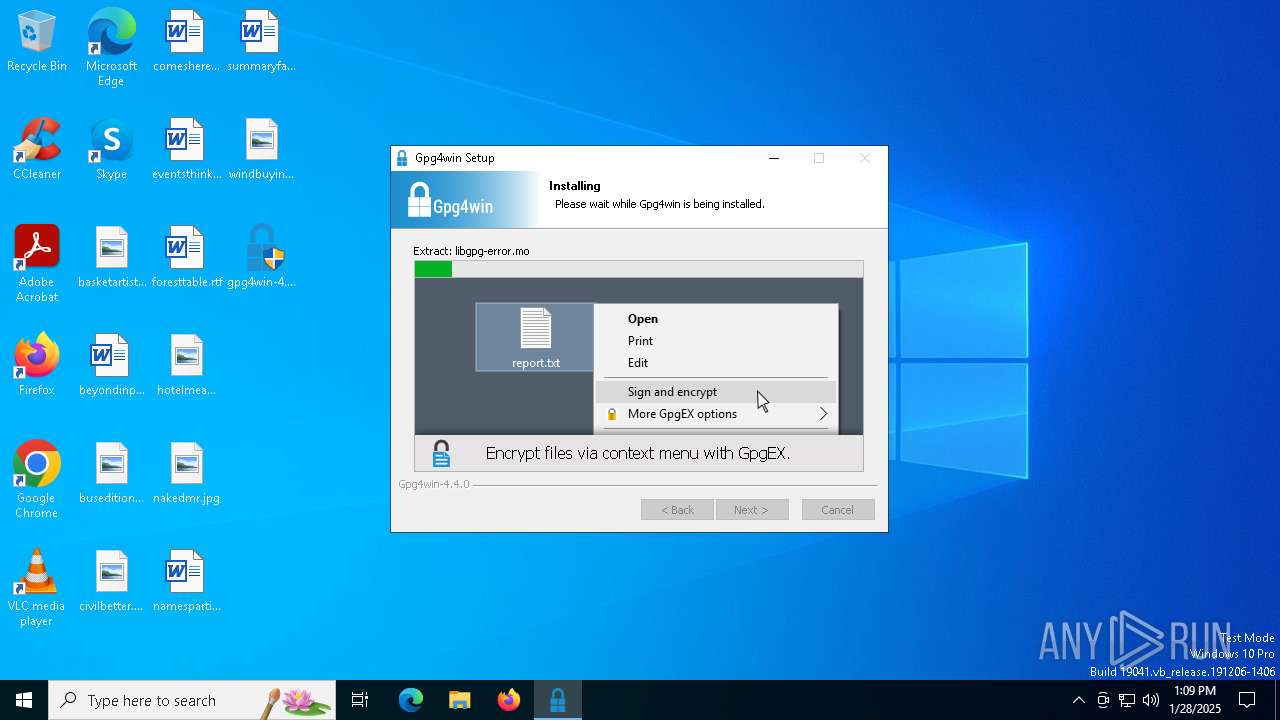
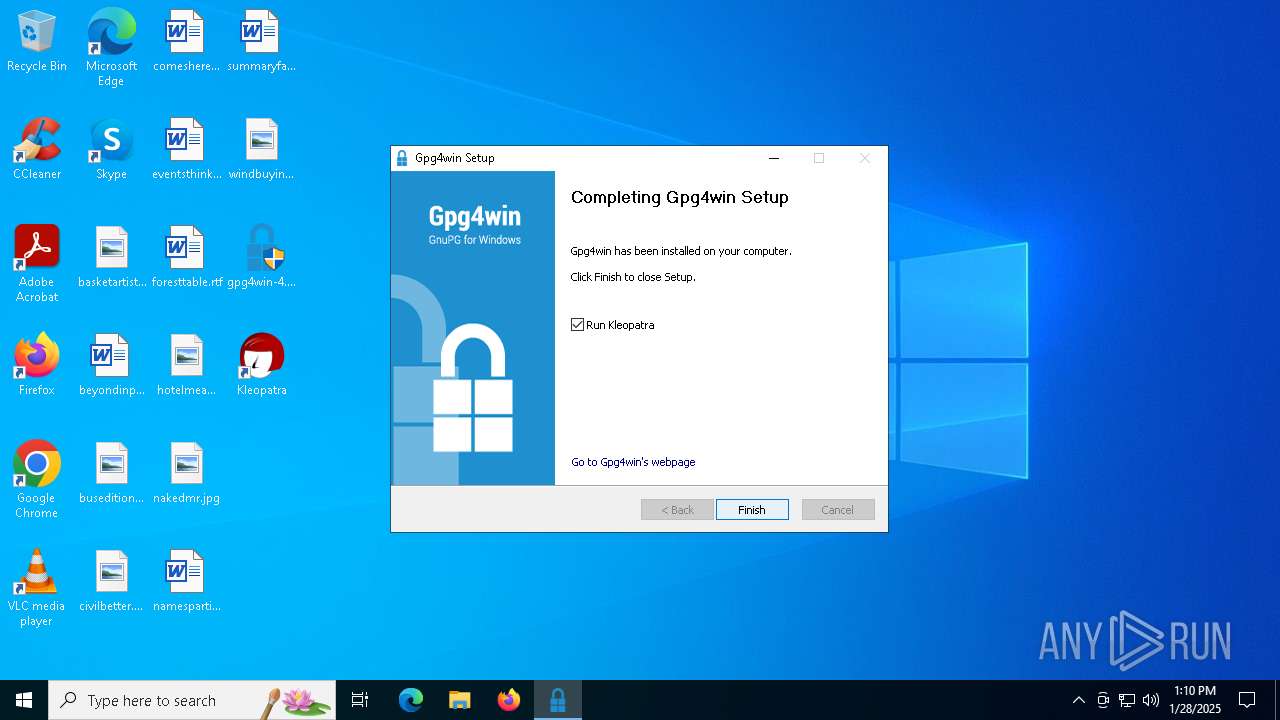
| File name: | gpg4win-4.4.0.exe |
| Full analysis: | https://app.any.run/tasks/a1d6a5b5-87cf-4917-88dc-6bbcc1a92b00 |
| Verdict: | Malicious activity |
| Analysis date: | January 28, 2025, 13:08:46 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, Nullsoft Installer self-extracting archive, 7 sections |
| MD5: | 3299AC2698D997B1A8A0E3C2C393C45A |
| SHA1: | 5C5E06F9F36D816BA14847D813127C9510836394 |
| SHA256: | 765673854C1503602B09C97BFA6C72B534E2414185FB2F23A0CE19CF8CECD891 |
| SSDEEP: | 196608:nAsmKs5/H+JRSVyTws1cnQs/u4oIIGlxT8jDZXIsa62y91wXcvTDB:AMw/HlVyEsAL1ldKtLnyX+Tt |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- gpg4win-4.4.0.exe (PID: 6924)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- gpg4win-4.4.0.exe (PID: 6924)
- gnupg-w32-2.4.7_20241125-bin.exe (PID: 7056)
There is functionality for taking screenshot (YARA)
- gpg4win-4.4.0.exe (PID: 6924)
- kleopatra.exe (PID: 2928)
Reads security settings of Internet Explorer
- gpg4win-4.4.0.exe (PID: 6924)
Executable content was dropped or overwritten
- gpg4win-4.4.0.exe (PID: 6924)
- gnupg-w32-2.4.7_20241125-bin.exe (PID: 7056)
Reads Microsoft Outlook installation path
- gpg4win-4.4.0.exe (PID: 6924)
The process creates files with name similar to system file names
- gnupg-w32-2.4.7_20241125-bin.exe (PID: 7056)
- gpg4win-4.4.0.exe (PID: 6924)
Creates a software uninstall entry
- gnupg-w32-2.4.7_20241125-bin.exe (PID: 7056)
- gpg4win-4.4.0.exe (PID: 6924)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 5488)
- regsvr32.exe (PID: 6444)
- gpg4win-4.4.0.exe (PID: 6924)
INFO
Checks supported languages
- gpg4win-4.4.0.exe (PID: 6924)
- gnupg-w32-2.4.7_20241125-bin.exe (PID: 7056)
- kleopatra.exe (PID: 2928)
- gpgme-w32spawn.exe (PID: 4716)
- gpgme-w32spawn.exe (PID: 624)
- gpgconf.exe (PID: 836)
- gpgme-w32spawn.exe (PID: 6160)
- gpgconf.exe (PID: 6004)
- gpgme-w32spawn.exe (PID: 5004)
- gpg.exe (PID: 5244)
- gpgsm.exe (PID: 2804)
- gpgconf.exe (PID: 1792)
- gpgconf.exe (PID: 6564)
- gpgconf.exe (PID: 6412)
- gpg-agent.exe (PID: 1016)
- gpg-connect-agent.exe (PID: 6588)
- gpg-agent.exe (PID: 6596)
- dirmngr.exe (PID: 6072)
- gpgconf.exe (PID: 3700)
- gpgme-w32spawn.exe (PID: 3040)
- gpg.exe (PID: 6908)
- gpgme-w32spawn.exe (PID: 6700)
- gpgconf.exe (PID: 6220)
- gpg.exe (PID: 6784)
- gpgme-w32spawn.exe (PID: 6760)
- gpgconf.exe (PID: 556)
- gpgsm.exe (PID: 7004)
- gpgconf.exe (PID: 3488)
- gpgconf.exe (PID: 7080)
- keyboxd.exe (PID: 7100)
- gpgme-w32spawn.exe (PID: 1704)
- gpg-agent.exe (PID: 6956)
- gpg-agent.exe (PID: 2904)
- gpgme-w32spawn.exe (PID: 7040)
Reads the computer name
- gpg4win-4.4.0.exe (PID: 6924)
- gnupg-w32-2.4.7_20241125-bin.exe (PID: 7056)
- kleopatra.exe (PID: 2928)
Creates files in the program directory
- gpg4win-4.4.0.exe (PID: 6924)
- gnupg-w32-2.4.7_20241125-bin.exe (PID: 7056)
The sample compiled with english language support
- gpg4win-4.4.0.exe (PID: 6924)
- gnupg-w32-2.4.7_20241125-bin.exe (PID: 7056)
Create files in a temporary directory
- gpg4win-4.4.0.exe (PID: 6924)
- gnupg-w32-2.4.7_20241125-bin.exe (PID: 7056)
- kleopatra.exe (PID: 2928)
Manual execution by a user
- kleopatra.exe (PID: 2928)
Creates files or folders in the user directory
- kleopatra.exe (PID: 2928)
- gpgconf.exe (PID: 836)
- gpg-connect-agent.exe (PID: 6588)
- gpg-agent.exe (PID: 6596)
Reads the machine GUID from the registry
- kleopatra.exe (PID: 2928)
- gpg-agent.exe (PID: 6596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:08:29 19:32:12+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 2.34 |
| CodeSize: | 38400 |
| InitializedDataSize: | 41472 |
| UninitializedDataSize: | 131072 |
| EntryPoint: | 0x4648 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.4.0.22704 |
| ProductVersionNumber: | 4.4.0.22704 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | Gpg4win is Free Software; you can redistribute it and/or modify it under the terms of the GNU General Public License. You should have received a copy of the GNU General Public License along with this software; if not, write to the Free Software Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301, USA |
| CompanyName: | g10 Code GmbH |
| FileDescription: | Gpg4win: The GNU Privacy Guard and Tools for Windows |
| FileVersion: | 4.4.0.22704 |
| LegalCopyright: | Copyright (C) 2023 g10 Code GmbH |
| LegalTrademarks: | - |
| ProductName: | Gpg4win (4.4.0) |
Total processes
170
Monitored processes
58
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 488 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | gpgconf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 556 | "C:\\\\Program Files (x86)\\\\GnuPG\\\\bin\\\\gpgconf.exe" "--list-options" "gpgsm" | C:\Program Files (x86)\GnuPG\bin\gpgconf.exe | — | gpgme-w32spawn.exe | |||||||||||
User: admin Company: g10 Code GmbH Integrity Level: MEDIUM Description: GnuPG’s config tool Exit code: 0 Version: 2.4.7 (7bdaf5647) built on <anon> at <none> | |||||||||||||||
| 624 | "C:\\Program Files (x86)\\Gpg4win\\bin\\gpgme-w32spawn.exe" "C:\\Users\\admin\\AppData\\Local\\Temp\\gpgme-tw2skO" "C:\\Program Files (x86)\\GnuPG\\bin\\gpgconf.exe" "--list-components" | C:\Program Files (x86)\Gpg4win\bin\gpgme-w32spawn.exe | — | kleopatra.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 836 | "C:\\\\Program Files (x86)\\\\GnuPG\\\\bin\\\\gpgconf.exe" "--list-dirs" | C:\Program Files (x86)\GnuPG\bin\gpgconf.exe | — | gpgme-w32spawn.exe | |||||||||||
User: admin Company: g10 Code GmbH Integrity Level: MEDIUM Description: GnuPG’s config tool Exit code: 0 Version: 2.4.7 (7bdaf5647) built on <anon> at <none> Modules
| |||||||||||||||
| 1016 | "C:\Program Files (x86)\GnuPG\bin\gpg-agent.exe" --gpgconf-test | C:\Program Files (x86)\GnuPG\bin\gpg-agent.exe | — | gpgconf.exe | |||||||||||
User: admin Company: g10 Code GmbH Integrity Level: MEDIUM Description: GnuPG’s private key daemon Exit code: 0 Version: 2.4.7 (7bdaf5647) built on <anon> at <none> Modules
| |||||||||||||||
| 1292 | "C:\\\\Program Files (x86)\\\\GnuPG\\\\bin\\\\gpgconf.exe" "--list-options" "scdaemon" | C:\Program Files (x86)\GnuPG\bin\gpgconf.exe | — | gpgme-w32spawn.exe | |||||||||||
User: admin Company: g10 Code GmbH Integrity Level: MEDIUM Description: GnuPG’s config tool Version: 2.4.7 (7bdaf5647) built on <anon> at <none> | |||||||||||||||
| 1704 | "C:\\Program Files (x86)\\Gpg4win\\bin\\gpgme-w32spawn.exe" "C:\\Users\\admin\\AppData\\Local\\Temp\\gpgme-4eSM3o" "C:\\Program Files (x86)\\GnuPG\\bin\\gpgconf.exe" "--list-options" "gpg-agent" | C:\Program Files (x86)\Gpg4win\bin\gpgme-w32spawn.exe | — | kleopatra.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 | |||||||||||||||
| 1792 | "C:\\\\Program Files (x86)\\\\GnuPG\\\\bin\\\\gpgconf.exe" "--version" | C:\Program Files (x86)\GnuPG\bin\gpgconf.exe | — | gpgme-w32spawn.exe | |||||||||||
User: admin Company: g10 Code GmbH Integrity Level: MEDIUM Description: GnuPG’s config tool Exit code: 0 Version: 2.4.7 (7bdaf5647) built on <anon> at <none> Modules
| |||||||||||||||
| 2292 | "C:\Program Files (x86)\GnuPG\bin\gpgsm.exe" --dump-option-table | C:\Program Files (x86)\GnuPG\bin\gpgsm.exe | — | gpgconf.exe | |||||||||||
User: admin Company: g10 Code GmbH Integrity Level: MEDIUM Description: GnuPG’s X.509/CMS tool Exit code: 0 Version: 2.4.7 (7bdaf5647) built on <anon> at <none> | |||||||||||||||
| 2452 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | gpgconf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 277
Read events
5 155
Write events
121
Delete events
1
Modification events
| (PID) Process: | (6924) gpg4win-4.4.0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Gpg4win |
| Operation: | write | Name: | Install Directory |
Value: C:\Program Files (x86)\Gpg4win | |||
| (PID) Process: | (7056) gnupg-w32-2.4.7_20241125-bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\GnuPG |
| Operation: | write | Name: | Install Directory |
Value: C:\Program Files (x86)\Gpg4win\..\GnuPG | |||
| (PID) Process: | (7056) gnupg-w32-2.4.7_20241125-bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\GnuPG |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files (x86)\Gpg4win\..\GnuPG\gnupg-uninstall.exe" | |||
| (PID) Process: | (7056) gnupg-w32-2.4.7_20241125-bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\GnuPG |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\Gpg4win\..\GnuPG | |||
| (PID) Process: | (7056) gnupg-w32-2.4.7_20241125-bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\GnuPG |
| Operation: | write | Name: | DisplayName |
Value: GNU Privacy Guard | |||
| (PID) Process: | (7056) gnupg-w32-2.4.7_20241125-bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\GnuPG |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files (x86)\Gpg4win\..\GnuPG\bin\gpg.exe,0 | |||
| (PID) Process: | (7056) gnupg-w32-2.4.7_20241125-bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\GnuPG |
| Operation: | write | Name: | DisplayVersion |
Value: 2.4.7 | |||
| (PID) Process: | (7056) gnupg-w32-2.4.7_20241125-bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\GnuPG |
| Operation: | write | Name: | Publisher |
Value: The GnuPG Project | |||
| (PID) Process: | (7056) gnupg-w32-2.4.7_20241125-bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\GnuPG |
| Operation: | write | Name: | URLInfoAbout |
Value: https://gnupg.org | |||
| (PID) Process: | (7056) gnupg-w32-2.4.7_20241125-bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\GnuPG |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
Executable files
134
Suspicious files
953
Text files
146
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6924 | gpg4win-4.4.0.exe | C:\Users\admin\AppData\Local\Temp\nsjADD9.tmp\g4wihelp.dll | executable | |
MD5:C022BC86C92527FEAF2A56707A7B87E9 | SHA256:38F88B073083ACBA5780D202233EDF851CABBCF6C1E1853830AC2119CFC740DF | |||
| 6924 | gpg4win-4.4.0.exe | C:\Users\admin\AppData\Local\Temp\nsjADD9.tmp\UserInfo.dll | executable | |
MD5:9C8190BF734E58469EEB894B04C9FDA0 | SHA256:88860534A424835A4BC47D3DB8D0F4B1481442ED3EFDEB7338A7DDF616651A60 | |||
| 6924 | gpg4win-4.4.0.exe | C:\Users\admin\AppData\Local\Temp\nsjADD9.tmp\Slides\slides.dat | text | |
MD5:0EA70BBEA63503A27AC45DE3FA9FE26E | SHA256:49AA701ADA0A7FE559E61F53A853B4730495AD2BB21A0429F39A2A27701BAAC3 | |||
| 6924 | gpg4win-4.4.0.exe | C:\Users\admin\AppData\Local\Temp\nsjADD9.tmp\modern-header.bmp | image | |
MD5:7823DFF3B752711D4A98B89FF52EB60A | SHA256:5364168D3EFEFED24331CF89B7A54DE4907D524C3A6BAC98D0DFD626B967A16B | |||
| 6924 | gpg4win-4.4.0.exe | C:\Users\admin\AppData\Local\Temp\nsjADD9.tmp\nsDialogs.dll | executable | |
MD5:2029C44871670EEC937D1A8C1E9FAA21 | SHA256:A4AE6D33F940A80E8FE34537C5CC1F8B8679C979607969320CFB750C15809AC2 | |||
| 6924 | gpg4win-4.4.0.exe | C:\Users\admin\AppData\Local\Temp\nsjADD9.tmp\System.dll | executable | |
MD5:4F25D99BF1375FE5E61B037B2616695D | SHA256:803931797D95777248DEE4F2A563AED51FE931D2DD28FAEC507C69ED0F26F647 | |||
| 6924 | gpg4win-4.4.0.exe | C:\Users\admin\AppData\Local\Temp\nsjADD9.tmp\Slides\slide1-gpgol.png | image | |
MD5:205B928C28E330575CD59D5CD8E1A914 | SHA256:88A049FF7878F56E4E15B412E0A3E1CD1FA690943AD1E79400B50C7F9116400E | |||
| 6924 | gpg4win-4.4.0.exe | C:\Program Files (x86)\Gpg4win\share\gpg4win\versioninfo.txt | text | |
MD5:D7AD55D6538298B2669A274403100157 | SHA256:7E1DAAA1C0CD8E5171B3C17117A2CF1D8E05ACB67D47F0E603179545EC0AE47B | |||
| 6924 | gpg4win-4.4.0.exe | C:\Program Files (x86)\Gpg4win\share\gpg4win\HOWTO-SMIME.de.txt | text | |
MD5:D764AC539DF4C810195A7DF7FD05A014 | SHA256:E0078E793C0604D77B09AD33706F071F22E63B6F22C4E5BE787FFC3F2221ADAE | |||
| 6924 | gpg4win-4.4.0.exe | C:\Program Files (x86)\Gpg4win\VERSION | text | |
MD5:0C4124BD7837CB8DC1A6A79AF66B673C | SHA256:318532B46A867E5D3F4CCF6E68CDAB398790BC85250CEC5ADC5A4A28AA87922F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
81
DNS requests
60
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.192:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 401 | 13.107.6.158:443 | https://business.bing.com/api/v1/user/token/microsoftgraph?&clienttype=edge-omnibox | unknown | — | — | unknown |
— | — | GET | — | 209.51.188.116:443 | https://www.gnu.org/licenses/ | unknown | — | — | unknown |
— | — | GET | — | 209.51.188.174:443 | https://www.fsf.org/blogs/community/psychological-care-should-grant-you-freedom-and-protection/@@images/11a058d4-e7c7-420d-9525-ca67857dc239.png | unknown | — | — | unknown |
— | — | GET | 401 | 13.107.6.158:443 | https://business.bing.com/work/api/v2/tenant/my/settingswithflights?&clienttype=edge-omnibox | unknown | binary | 587 b | whitelisted |
— | — | GET | — | 209.51.188.233:443 | https://static.fsf.org/nosvn/images/socials/peertube.png | unknown | — | — | unknown |
— | — | GET | 200 | 13.107.42.16:443 | https://config.edge.skype.com/config/v1/Edge/122.0.2365.59?clientId=4489578223053569932&agents=EdgeFirstRun%2CEdgeFirstRunConfig&osname=win&client=edge&channel=stable&scpfre=0&osarch=x86_64&osver=10.0.19045&wu=1&devicefamily=desktop&uma=0&sessionid=44&mngd=0&installdate=1661339457&edu=0&bphint=2&soobedate=1504771245&fg=1 | unknown | binary | 768 b | whitelisted |
— | — | GET | 200 | 13.107.42.16:443 | https://config.edge.skype.com/config/v1/Edge/122.0.2365.59?clientId=4489578223053569932&agents=Edge%2CEdgeConfig%2CEdgeServices%2CEdgeFirstRun%2CEdgeFirstRunConfig&osname=win&client=edge&channel=stable&scpfre=0&osarch=x86_64&osver=10.0.19045&wu=1&devicefamily=desktop&uma=0&sessionid=44&mngd=0&installdate=1661339457&edu=0&bphint=2&soobedate=1504771245&fg=1 | unknown | binary | 10.1 Kb | whitelisted |
— | — | GET | 200 | 13.107.21.239:443 | https://edge.microsoft.com/serviceexperimentation/v3/?osname=win&channel=stable&osver=10.0.19045&devicefamily=desktop&installdate=1661339457&clientversion=122.0.2365.59&experimentationmode=2&scpguard=0&scpfull=0&scpver=0 | unknown | binary | 1.01 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 104.126.37.136:443 | — | Akamai International B.V. | DE | unknown |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.192:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.153:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
fsf.org |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
Threats
Process | Message |
|---|---|
gpg4win-4.4.0.exe | Created: |
gpg4win-4.4.0.exe | CLSID\{42d30988-1a3a-11da-c687-000d6080e735} |
regsvr32.exe | Created: |
regsvr32.exe | CLSID\{42d30988-1a3a-11da-c687-000d6080e735} |
kleopatra.exe | org.kde.pim.kleopatra: Startup timing: 72 ms: Application created
|
kleopatra.exe | org.kde.pim.kleopatra: Responder handle: 0x0
|
kleopatra.exe | org.kde.pim.kleopatra: Application created
|
kleopatra.exe | org.kde.pim.kleopatra: Created responder: "kleopatraResponder" with handle: 0x50288
|
kleopatra.exe | org.kde.pim.kleopatra: Startup timing: 81 ms: Starting version info check
|
kleopatra.exe | org.kde.pim.kleopatra: Startup timing: 80 ms: GPGME Initialized
|