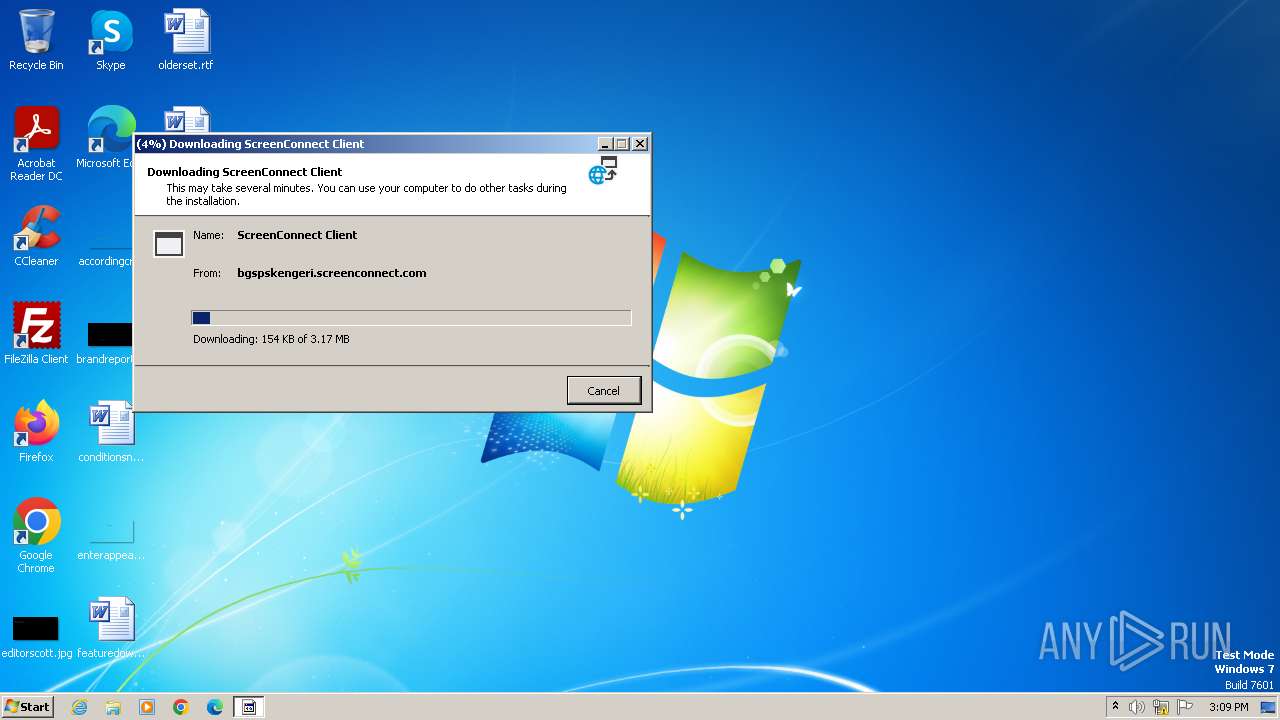
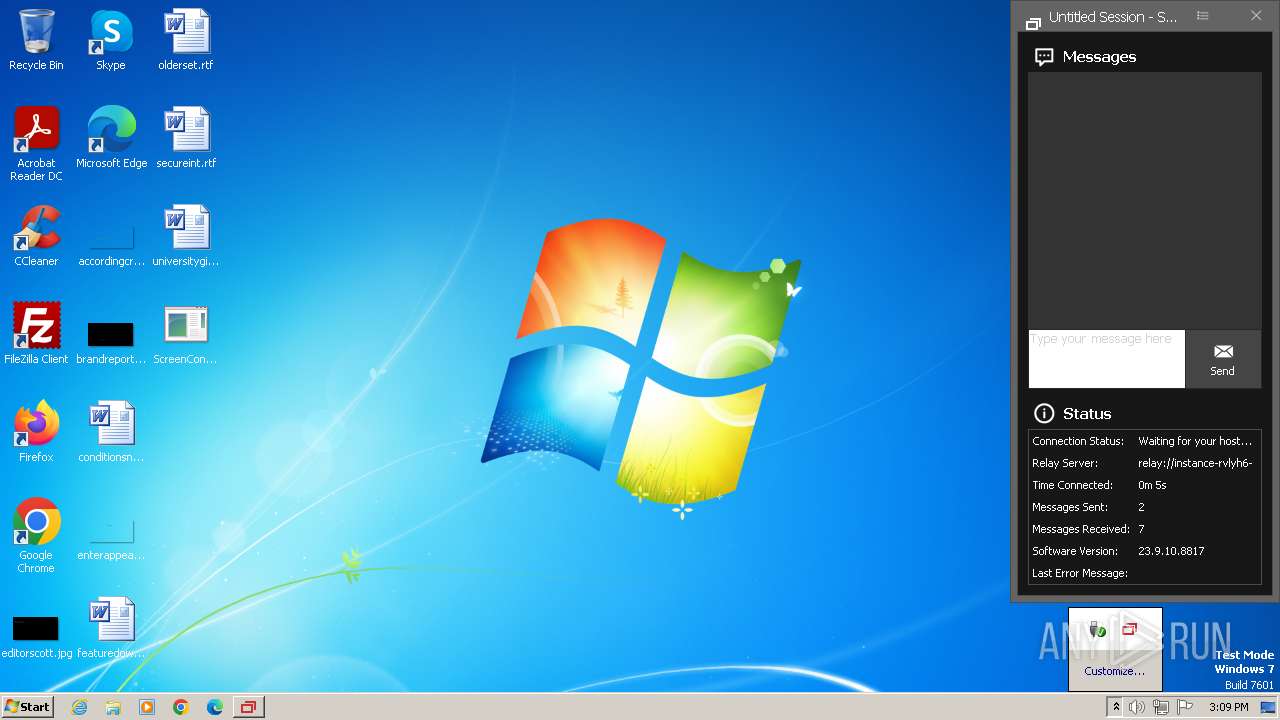
| File name: | ScreenConnect.Client.exe |
| Full analysis: | https://app.any.run/tasks/c640ba9a-21e5-48a8-a1ee-9eb65802f1bc |
| Verdict: | Malicious activity |
| Analysis date: | April 27, 2024, 14:09:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C95A42CA3D93DAC7E9B2211E36AEAF5A |
| SHA1: | 2C281D5C2BF9274F3E7C2A405318CBA0DC2A83DE |
| SHA256: | 76021A58B3C36E6BF0C21729EF5F7FA769585E1409C53AFAFA89102B9832D15D |
| SSDEEP: | 1536:tejLH3MVw8licIgWQog5Mzg+MoCdqQsWQcd69jPVfqUNKg4v:UjLHcVw8licpWQog5Ms+f+l6xPVfq84v |
MALICIOUS
Drops the executable file immediately after the start
- ScreenConnect.Client.exe (PID: 3980)
- dfsvc.exe (PID: 4028)
Creates a writable file in the system directory
- ScreenConnect.WindowsClient.exe (PID: 2256)
SUSPICIOUS
Reads the Internet Settings
- dfsvc.exe (PID: 4028)
- ScreenConnect.WindowsClient.exe (PID: 1440)
- ScreenConnect.ClientService.exe (PID: 1588)
- ScreenConnect.WindowsClient.exe (PID: 1844)
Reads settings of System Certificates
- dfsvc.exe (PID: 4028)
- ScreenConnect.Client.exe (PID: 3980)
Adds/modifies Windows certificates
- ScreenConnect.Client.exe (PID: 3980)
- dfsvc.exe (PID: 4028)
Reads security settings of Internet Explorer
- dfsvc.exe (PID: 4028)
- ScreenConnect.WindowsClient.exe (PID: 1440)
- ScreenConnect.ClientService.exe (PID: 1588)
- ScreenConnect.ClientService.exe (PID: 1704)
- ScreenConnect.WindowsClient.exe (PID: 2256)
- ScreenConnect.WindowsClient.exe (PID: 1844)
Checks Windows Trust Settings
- dfsvc.exe (PID: 4028)
Reads Internet Explorer settings
- dfsvc.exe (PID: 4028)
Executable content was dropped or overwritten
- dfsvc.exe (PID: 4028)
The process creates files with name similar to system file names
- dfsvc.exe (PID: 4028)
Creates or modifies Windows services
- ScreenConnect.ClientService.exe (PID: 1704)
Executes as Windows Service
- ScreenConnect.ClientService.exe (PID: 1704)
INFO
Reads the machine GUID from the registry
- dfsvc.exe (PID: 4028)
- ScreenConnect.Client.exe (PID: 3980)
- ScreenConnect.ClientService.exe (PID: 1588)
- ScreenConnect.WindowsClient.exe (PID: 1440)
- ScreenConnect.ClientService.exe (PID: 1704)
- ScreenConnect.WindowsClient.exe (PID: 1844)
- ScreenConnect.WindowsClient.exe (PID: 2256)
Creates files or folders in the user directory
- dfsvc.exe (PID: 4028)
- ScreenConnect.WindowsClient.exe (PID: 1440)
- ScreenConnect.ClientService.exe (PID: 1704)
Checks supported languages
- ScreenConnect.Client.exe (PID: 3980)
- dfsvc.exe (PID: 4028)
- ScreenConnect.WindowsClient.exe (PID: 1440)
- ScreenConnect.ClientService.exe (PID: 1588)
- wmpnscfg.exe (PID: 1628)
- ScreenConnect.ClientService.exe (PID: 1704)
- ScreenConnect.WindowsClient.exe (PID: 1844)
- ScreenConnect.WindowsClient.exe (PID: 2256)
Reads Environment values
- dfsvc.exe (PID: 4028)
Reads the computer name
- ScreenConnect.Client.exe (PID: 3980)
- wmpnscfg.exe (PID: 1628)
- ScreenConnect.WindowsClient.exe (PID: 1440)
- ScreenConnect.ClientService.exe (PID: 1588)
- ScreenConnect.ClientService.exe (PID: 1704)
- ScreenConnect.WindowsClient.exe (PID: 1844)
- ScreenConnect.WindowsClient.exe (PID: 2256)
- dfsvc.exe (PID: 4028)
Create files in a temporary directory
- dfsvc.exe (PID: 4028)
Process checks whether UAC notifications are on
- dfsvc.exe (PID: 4028)
Reads the software policy settings
- dfsvc.exe (PID: 4028)
Checks proxy server information
- dfsvc.exe (PID: 4028)
Manual execution by a user
- wmpnscfg.exe (PID: 1628)
Reads CPU info
- ScreenConnect.WindowsClient.exe (PID: 2256)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:11:18 19:55:37+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.33 |
| CodeSize: | 40448 |
| InitializedDataSize: | 32768 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x14ba |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
45
Monitored processes
8
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1440 | "C:\Users\admin\AppData\Local\Apps\2.0\OQVLXTZK.4P5\AK6KX289.K1P\scre..tion_25b0fbb6ef7eb094_0017.0009_ae1b8485b1f96f25\ScreenConnect.WindowsClient.exe" | C:\Users\admin\AppData\Local\Apps\2.0\OQVLXTZK.4P5\AK6KX289.K1P\scre..tion_25b0fbb6ef7eb094_0017.0009_ae1b8485b1f96f25\ScreenConnect.WindowsClient.exe | — | dfsvc.exe | |||||||||||
User: admin Company: ScreenConnect Software Integrity Level: MEDIUM Description: ScreenConnect Client Exit code: 0 Version: 23.9.10.8817 Modules
| |||||||||||||||
| 1588 | "C:\Users\admin\AppData\Local\Apps\2.0\OQVLXTZK.4P5\AK6KX289.K1P\scre..tion_25b0fbb6ef7eb094_0017.0009_ae1b8485b1f96f25\ScreenConnect.ClientService.exe" "?e=Support&y=Guest&h=instance-rvlyh6-relay.screenconnect.com&p=443&s=a39e54bf-9e6c-4e52-b954-1d58bfaf1fb7&k=BgIAAACkAABSU0ExAAgAAAEAAQA1kL2nT8bYuaQJT8LCcjr12VBplwqMDuYd6ykrGWZJC96iAj7HkuRYu6keJ4J1S8Sth%2bwVq8Ui1iHP3%2buQps2QvtX1gUOZyOR49TIKnAMY6O1vAs%2bze8l8V1fvIWxADuYjoqV1340pjNZCcA27sBMGjSKihloqeErCoA6IJRltJPXyn1TFfZHlcgiQnPCNjgBZ%2fzfbBv2%2bjGb5WiBzx9WkhMvnmkCLP9FAoWeSa6Rjr7XDiLlfoIYgk4zDz%2biKpvr1ThHE0j46d0T2S9u3b7vX5bqsJjj0dnsmH1VhUUJ4AEO3zns4kZ0AAsQpZKM0HkqQYuWY7TeqR%2fJIrwymgXm1&r=&i=" "1" | C:\Users\admin\AppData\Local\Apps\2.0\OQVLXTZK.4P5\AK6KX289.K1P\scre..tion_25b0fbb6ef7eb094_0017.0009_ae1b8485b1f96f25\ScreenConnect.ClientService.exe | ScreenConnect.WindowsClient.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 23.9.10.8817 Modules
| |||||||||||||||
| 1628 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1704 | "C:\Users\admin\AppData\Local\Apps\2.0\OQVLXTZK.4P5\AK6KX289.K1P\scre..tion_25b0fbb6ef7eb094_0017.0009_ae1b8485b1f96f25\ScreenConnect.ClientService.exe" "?e=Support&y=Guest&h=instance-rvlyh6-relay.screenconnect.com&p=443&s=a39e54bf-9e6c-4e52-b954-1d58bfaf1fb7&k=BgIAAACkAABSU0ExAAgAAAEAAQA1kL2nT8bYuaQJT8LCcjr12VBplwqMDuYd6ykrGWZJC96iAj7HkuRYu6keJ4J1S8Sth%2bwVq8Ui1iHP3%2buQps2QvtX1gUOZyOR49TIKnAMY6O1vAs%2bze8l8V1fvIWxADuYjoqV1340pjNZCcA27sBMGjSKihloqeErCoA6IJRltJPXyn1TFfZHlcgiQnPCNjgBZ%2fzfbBv2%2bjGb5WiBzx9WkhMvnmkCLP9FAoWeSa6Rjr7XDiLlfoIYgk4zDz%2biKpvr1ThHE0j46d0T2S9u3b7vX5bqsJjj0dnsmH1VhUUJ4AEO3zns4kZ0AAsQpZKM0HkqQYuWY7TeqR%2fJIrwymgXm1&r=&i=" "1" | C:\Users\admin\AppData\Local\Apps\2.0\OQVLXTZK.4P5\AK6KX289.K1P\scre..tion_25b0fbb6ef7eb094_0017.0009_ae1b8485b1f96f25\ScreenConnect.ClientService.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Version: 23.9.10.8817 Modules
| |||||||||||||||
| 1844 | "C:\Users\admin\AppData\Local\Apps\2.0\OQVLXTZK.4P5\AK6KX289.K1P\scre..tion_25b0fbb6ef7eb094_0017.0009_ae1b8485b1f96f25\ScreenConnect.WindowsClient.exe" "RunRole" "e7149fa5-7bef-48a8-a658-c263840e479c" "User" | C:\Users\admin\AppData\Local\Apps\2.0\OQVLXTZK.4P5\AK6KX289.K1P\scre..tion_25b0fbb6ef7eb094_0017.0009_ae1b8485b1f96f25\ScreenConnect.WindowsClient.exe | — | ScreenConnect.ClientService.exe | |||||||||||
User: admin Company: ScreenConnect Software Integrity Level: MEDIUM Description: ScreenConnect Client Version: 23.9.10.8817 Modules
| |||||||||||||||
| 2256 | "C:\Users\admin\AppData\Local\Apps\2.0\OQVLXTZK.4P5\AK6KX289.K1P\scre..tion_25b0fbb6ef7eb094_0017.0009_ae1b8485b1f96f25\ScreenConnect.WindowsClient.exe" "RunRole" "e3b56b5d-f70d-44d2-9f25-faa82cb7ec3b" "System" | C:\Users\admin\AppData\Local\Apps\2.0\OQVLXTZK.4P5\AK6KX289.K1P\scre..tion_25b0fbb6ef7eb094_0017.0009_ae1b8485b1f96f25\ScreenConnect.WindowsClient.exe | — | ScreenConnect.ClientService.exe | |||||||||||
User: SYSTEM Company: ScreenConnect Software Integrity Level: SYSTEM Description: ScreenConnect Client Exit code: 0 Version: 23.9.10.8817 Modules
| |||||||||||||||
| 3980 | "C:\Users\admin\Desktop\ScreenConnect.Client.exe" | C:\Users\admin\Desktop\ScreenConnect.Client.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 4028 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\dfsvc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\dfsvc.exe | ScreenConnect.Client.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: ClickOnce Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
Total events
13 361
Read events
13 069
Write events
239
Delete events
53
Modification events
| (PID) Process: | (3980) ScreenConnect.Client.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3980) ScreenConnect.Client.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\SystemCertificates\TrustedPublisher\Certificates |
| Operation: | delete value | Name: | 7B0F360B775F76C94A12CA48445AA2D2A875701C |
Value: | |||
| (PID) Process: | (3980) ScreenConnect.Client.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\SystemCertificates\TrustedPublisher\Certificates\7B0F360B775F76C94A12CA48445AA2D2A875701C |
| Operation: | write | Name: | Blob |
Value: 0300000001000000140000007B0F360B775F76C94A12CA48445AA2D2A875701C2000000001000000B4060000308206B030820498A003020102021008AD40B260D29C4C9F5ECDA9BD93AED9300D06092A864886F70D01010C05003062310B300906035504061302555331153013060355040A130C446967694365727420496E6331193017060355040B13107777772E64696769636572742E636F6D3121301F060355040313184469676943657274205472757374656420526F6F74204734301E170D3231303432393030303030305A170D3336303432383233353935395A3069310B300906035504061302555331173015060355040A130E44696769436572742C20496E632E3141303F060355040313384469676943657274205472757374656420473420436F6465205369676E696E6720525341343039362053484133383420323032312043413130820222300D06092A864886F70D01010105000382020F003082020A0282020100D5B42F42D028AD78B75DD539591BB18842F5338CEB3D819770C5BBC48526309FA48E68D85CF5EB342407E14B4FD37843F417D71EDAF9D2D5671A524F0EA157FC8899C191CC81033E4D702464B38DE2087D347D4C8057126B439A99F2C53B1FF2EFCB475A13A64CB3012025F310D38BB2FB08F08AE09D09C065A7FA98804935873D5119E8902178452EA19F2CE118C21ACCC5EE93497042328FFBC6EA1CF3656891A24D4C8211485268DE10BD14575DE8181365C57FB24F852C48A4568435D6F92E9CAA0015D137FE1A0694C27CC8EA1B32E6CAC2F4A7A3030E74A5AF39B6AB6012E3E8D6B9F731E1DCADE418A0D8C1234747B3A10F6EA3AB6D9806831BB76A672DD2BD441A9210818FB03B09D7C79B325AC2FF6A60548B49C193EDE1B45CE06FEB26F98CD5B2F93810E6EACE91F5BED3FB6F9361345CBC93452883362A66285FB073CE8B262506B283D45CF615194CED62E05E33F2E8E8EC0AA7B0032B91B23679BEF7AD081E75A665CCBBE34850F377911AFEDB50A246C8615898F57C02163C8328AD3986ECD4B70D53D0F847E675308DEC30937614A65B4B5D74614D3F129176DEBF58CB72102941F0D5C56D267668114113589ADC262B01F4894D59DB78CF814A3E40475FC98150738510232159608A6454C1CC211AE838197C661CCD78384530994FFF634F4CBBAA0D0853417C583D47B3FAB6EC8C320902CC6C3C0C56110203010001A38201593082015530120603551D130101FF040830060101FF020100301D0603551D0E041604146837E0EBB63BF85F1186FBFE617B088865F44E42301F0603551D23041830168014ECD7E382D2715D644CDF2E673FE7BA98AE1C0F4F300E0603551D0F0101FF04040302018630130603551D25040C300A06082B06010505070303307706082B06010505070101046B3069302406082B060105050730018618687474703A2F2F6F6373702E64696769636572742E636F6D304106082B060105050730028635687474703A2F2F636163657274732E64696769636572742E636F6D2F446967694365727454727573746564526F6F7447342E63727430430603551D1F043C303A3038A036A0348632687474703A2F2F63726C332E64696769636572742E636F6D2F446967694365727454727573746564526F6F7447342E63726C301C0603551D20041530133007060567810C01033008060667810C010401300D06092A864886F70D01010C050003820201003A23443D8D0876EE8FBC3A99D356E0021AA5F84834F32CB6E67466F79472B100CAAF6C302713129E90449F4BFD9EA37C26D537BC3A5D486D95D53F49F427BB16814550FD9CBDB685E0767E3771CB22F75AAA90CFF5936AE3EB20D1D55079889A8A8AC1B6BDA148187EDCD8801A111918CD61998156F6C9E376E7C4E41B5F43F83E94FF76393D9ED499CF4ADD28EB5F26A1955848D51AFED7273FFD90D17686DD1CB0605CF30DA8EEE089A1BD39E1384EDA6EBB369DFBE521535AC3CAE96AF1A23EDB43B833C84F38149299F5DDCE546DD95D02141F40337C03E295B2C221757352CB46D8C4341CA2A54B8DCD6F76372C853F1ACE26E918BE9007B0437F9588208270F0CCCAEFFD29355C1F893855F7378A8B09A1CB0BE9311AFF2E195C3971E1BE9CA70A06D62667B792E64E5FDE7AAC49CF2EA47492ADDB3CA49C861FE3C1561B2B23FF8FB5EA887B706BE6A0BAFD3A3F45A6C4E81691528B41C048844B964DAB4440E38DF01528CEEDF11856072A2F10C40C08643C338FAE288C3CCB8F880B0DBF3BF4CE1E7B8EEFB5EBCBB7F07713E6E7283FAC12AEA52F226C41F9825C1566CC6C0ECAC586C3F626330C074BA0D307026A6A4030484B34A85120BBAD1B8508E2590D6DCA05502BEA4A1C9EA5FDA0A71F0674E7F2D65290FDAF854821F9573BB49C03ED8645F4B4616EBF68E2266086EAC8AFA9FE941DE7631B3A8656784E | |||
| (PID) Process: | (3980) ScreenConnect.Client.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\SystemCertificates\TrustedPublisher\Certificates |
| Operation: | delete value | Name: | 4C2272FBA7A7380F55E2A424E9E624AEE1C14579 |
Value: | |||
| (PID) Process: | (3980) ScreenConnect.Client.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\SystemCertificates\TrustedPublisher\Certificates\4C2272FBA7A7380F55E2A424E9E624AEE1C14579 |
| Operation: | write | Name: | Blob |
Value: 0300000001000000140000004C2272FBA7A7380F55E2A424E9E624AEE1C145792000000001000000640700003082076030820548A00302010202100B9360051BCCF66642998998D5BA97CE300D06092A864886F70D01010B05003069310B300906035504061302555331173015060355040A130E44696769436572742C20496E632E3141303F060355040313384469676943657274205472757374656420473420436F6465205369676E696E67205253413430393620534841333834203230323120434131301E170D3232303831373030303030305A170D3235303831353233353935395A3065310B30090603550406130255533110300E06035504081307466C6F72696461310E300C0603550407130554616D706131193017060355040A1310436F6E6E656374776973652C204C4C433119301706035504031310436F6E6E656374776973652C204C4C4330820222300D06092A864886F70D01010105000382020F003082020A0282020100EC489826D08D2C6DE21B3CD3676DB1E0E50CB1FF75FF564E9741F9574AA3640AA8297294A05B4DB68ABD0760B6B05B50CE92FF42A4E390BE776A43E9961C722F6B3A4D5C880BCC6A61B4026F9137D36B2B7E9B86055876B9FA860DBCB164FE7F4B5B9DE4799AE4E02DC1F0BEE01E5D032933A2827388F8DB0B482E76C441B1BD50909EF2023E1FB62196C994CE052266B28CD89253E6416044133139764DB5FC45702529536BF82C775F9EC81FA27DC409530325F40CDEF95B81B9CE0D42791CEE72E7BD1B36C257B52257C65A28970E457513989434BFC239E2992B193E1B3CC3F11CCDD1D26D4EC9845099AB913906A42069AF999C0071169B45A2EA1AA666F1904E8ACB05E1823A359A291FD46B4EF7AED5935BB6AB17EBF077210726930C90F01761D6544A94E8FA614CC41D817EEC734B1C3D3AFB7C58FB256F0C09EDC1459BDDBFF9940ED1958570265D67AF79A9B6A16AFFD70FC6328C9810D5DC186E39AF6FBCAD49A270F237E6BCD5DE0BC014BC3179CD79776591340311A42CA94F33416C2E01B59BD1D71DE86ACE6716BC90B2D7695D155039AA08FBAC19A4D93FB784230A20A485287A16355645FC09142C602D140FA046B7BFD75328184FF7BDF8F9E0D65E6201C8D242931047F59BD328AC353777CCEFA60408887B84FC3631301463461A1D73C0B5CC74D6D82905DDF923BDBAB027A311CC38D3FA16F639A50203010001A382020630820202301F0603551D230418301680146837E0EBB63BF85F1186FBFE617B088865F44E42301D0603551D0E04160414338CE10A6E06D9C6ED0BC6CAE736CEFB8188646A300E0603551D0F0101FF04040302078030130603551D25040C300A06082B060105050703033081B50603551D1F0481AD3081AA3053A051A04F864D687474703A2F2F63726C332E64696769636572742E636F6D2F4469676943657274547275737465644734436F64655369676E696E6752534134303936534841333834323032314341312E63726C3053A051A04F864D687474703A2F2F63726C342E64696769636572742E636F6D2F4469676943657274547275737465644734436F64655369676E696E6752534134303936534841333834323032314341312E63726C303E0603551D20043730353033060667810C0104013029302706082B06010505070201161B687474703A2F2F7777772E64696769636572742E636F6D2F43505330819406082B06010505070101048187308184302406082B060105050730018618687474703A2F2F6F6373702E64696769636572742E636F6D305C06082B060105050730028650687474703A2F2F636163657274732E64696769636572742E636F6D2F4469676943657274547275737465644734436F64655369676E696E6752534134303936534841333834323032314341312E637274300C0603551D130101FF04023000300D06092A864886F70D01010B050003820201000AD79F00CF4984864C8981ECCE8718AA875647F6A74608C968E16568C7AA9D711ED7341676038067F01330C91621B27A2A8894C4108C268162A31F13F9757A7D6BB3C6F19BF27C3A29896D712D85873627D827CD6471761444FABF1D31E903F791143C5B4CE5E7444AACBA36D759AEBA3069D195226755CBC675AA747F77596C53C96E083C45BBA24479D6845EEA9F2B28BA29B4DCF0BCF14AA4CE176C24E2C1B8FEC3EE16E1C086DB6FDA97388859E83BE65C03F701395B78B842C6DD1533EF642CCA6FE50F6337D3F2DFEDD8B28F2B28E0C98EDD2151392E7CC75489F48859F1DE14C81B306EB50EED7BB78BE30EAADA76767C4CA523A11EEC5A2372D6122926AB1801A6A6778E9504791487EE47D4577154988802070F80FC535957658F954CD083546C5AFB5A6567B6761275F5DB20F70AB86FEEF94C7CFC65369D325121B69A82399BC7DC1962416F0F05CF1EEE64D495A3527E464E2C68DA0187093F97B673E43DDDBCC067E00713F1565FCFF8C3772D44B40A04E600644F22A990345F9A6B5B52963E82C81A0CE91D43A230F67B37D8DEBDA40EA3D59D305E18ADC1976516C12A8BA2BCA24143B12E9527B4DCA58872AA9B3A8C6AC563FC2DC02BF51BE889516D35A4BA9D062417B5BDCC50BA945FAE26B60D6AEC03984798A6A21D3FF793CC0849E81ED55B8027411C50DB776AE8FEEF2FDC2DAFB04345261DEDC054 | |||
| (PID) Process: | (4028) dfsvc.exe | Key: | HKEY_CLASSES_ROOT\Software\Microsoft\Windows\CurrentVersion\Deployment\SideBySide\2.0\StateManager |
| Operation: | write | Name: | StateStore_RandomString |
Value: CNCE0GQDVTZAJ5V3JPQ9NKD9 | |||
| (PID) Process: | (4028) dfsvc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\dfsvc_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4028) dfsvc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\dfsvc_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4028) dfsvc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\dfsvc_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (4028) dfsvc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\dfsvc_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
16
Suspicious files
12
Text files
23
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4028 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\9DJTAH67.QNC\2RDK6WYD.VG1\ScreenConnect.WindowsBackstageShell.exe | executable | |
MD5:10DBA57F22A6AB4039330000570F39F8 | SHA256:9BD8D15759F83D99EDD1F2617D59A94E1C2BB4BD7C4977958F5D5F22C5A7C469 | |||
| 4028 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\782DQVAA.M72\NP0J2N2Z.VZL.application | xml | |
MD5:75F072DB717ADF065F2D4DDD705A2D49 | SHA256:3C7DD342A48BDACB6CC05C422AE960D7BAF899593C7A14A075C70F478F17825C | |||
| 4028 | dfsvc.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1302019708-1500728564-335382590-1000\932a2db58c237abd381d22df4c63a04a_90059c37-1320-41a4-b58d-2b75a9850d2f | dbf | |
MD5:D2DED43CE07BFCE4D1C101DFCAA178C8 | SHA256:8EEE9284E733B9D4F2E5C43F71B81E27966F5CD8900183EB3BB77A1F1160D050 | |||
| 4028 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\9DJTAH67.QNC\2RDK6WYD.VG1\ScreenConnect.WindowsClient.exe.manifest | xml | |
MD5:F4B84E283123B025A90BBDE33E2080FD | SHA256:93F9EB492B6952D8C7AA1EF1EE5A901234BA1FD2D5EF58D24E1FAEF597EA8E02 | |||
| 4028 | dfsvc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C56C4404C4DEF0DC88E5FCD9F09CB2F1 | binary | |
MD5:EE76CDC60D27197B93ABF1F0ADFD00D5 | SHA256:B6B1CD0CEAF8DA29C607CB8E0FFBE1D2CC4C711E42052D30B8D2D914FE09531E | |||
| 4028 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\9DJTAH67.QNC\2RDK6WYD.VG1\ScreenConnect.WindowsBackstageShell.exe.config | xml | |
MD5:728175E20FFBCEB46760BB5E1112F38B | SHA256:87C640D3184C17D3B446A72D5F13D643A774B4ECC7AFBEDFD4E8DA7795EA8077 | |||
| 4028 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\9DJTAH67.QNC\2RDK6WYD.VG1\ScreenConnect.WindowsClient.exe.config | xml | |
MD5:728175E20FFBCEB46760BB5E1112F38B | SHA256:87C640D3184C17D3B446A72D5F13D643A774B4ECC7AFBEDFD4E8DA7795EA8077 | |||
| 4028 | dfsvc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C56C4404C4DEF0DC88E5FCD9F09CB2F1 | binary | |
MD5:D91299E84355CD8D5A86795A0118B6E9 | SHA256:46011EDE1C147EB2BC731A539B7C047B7EE93E48B9D3C3BA710CE132BBDFAC6B | |||
| 4028 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\9DJTAH67.QNC\2RDK6WYD.VG1\ScreenConnect.WindowsFileManager.exe | executable | |
MD5:C333D3A6EEB74E4D76C3B9E0F6BFD04C | SHA256:998D7A0CD6B1A837489E55E99CB992088B9FDE220A1025346A461849E1F50D22 | |||
| 4028 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\9DJTAH67.QNC\2RDK6WYD.VG1\ScreenConnect.WindowsClient.exe | executable | |
MD5:5DEC65C4047DE914C78816B8663E3602 | SHA256:71602F6B0B27C8B7D8AD624248E6126970939EFFDE785EC913ACE19052E9960E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
4
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4028 | dfsvc.exe | GET | 200 | 192.229.221.95:80 | http://cacerts.digicert.com/DigiCertTrustedG4CodeSigningRSA4096SHA3842021CA1.crt | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4028 | dfsvc.exe | 147.28.147.62:443 | bgspskengeri.screenconnect.com | PACKET | US | unknown |
4028 | dfsvc.exe | 192.229.221.95:80 | cacerts.digicert.com | EDGECAST | US | whitelisted |
1704 | ScreenConnect.ClientService.exe | 147.28.147.60:443 | instance-rvlyh6-relay.screenconnect.com | PACKET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bgspskengeri.screenconnect.com |
| unknown |
cacerts.digicert.com |
| whitelisted |
instance-rvlyh6-relay.screenconnect.com |
| unknown |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Misc activity | ET INFO Observed DNS Query to Known ScreenConnect/ConnectWise Remote Desktop Service Domain |
1088 | svchost.exe | Misc activity | ET INFO Observed DNS Query to Known ScreenConnect/ConnectWise Remote Desktop Service Domain |
— | — | Misc activity | ET INFO ScreenConnect/ConnectWise Initial Checkin Packet M2 |
— | — | Potential Corporate Privacy Violation | REMOTE [ANY.RUN] ScreenConnect Server Response |
Process | Message |
|---|---|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status Originated: -1073741772
*** Source File: d:\iso_whid\x86fre\base\isolation\win32\isoreg_direct.cpp, line 1127
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status Originated: -1073741772
*** Source File: d:\iso_whid\x86fre\base\isolation\win32\isoreg_direct.cpp, line 1127
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|