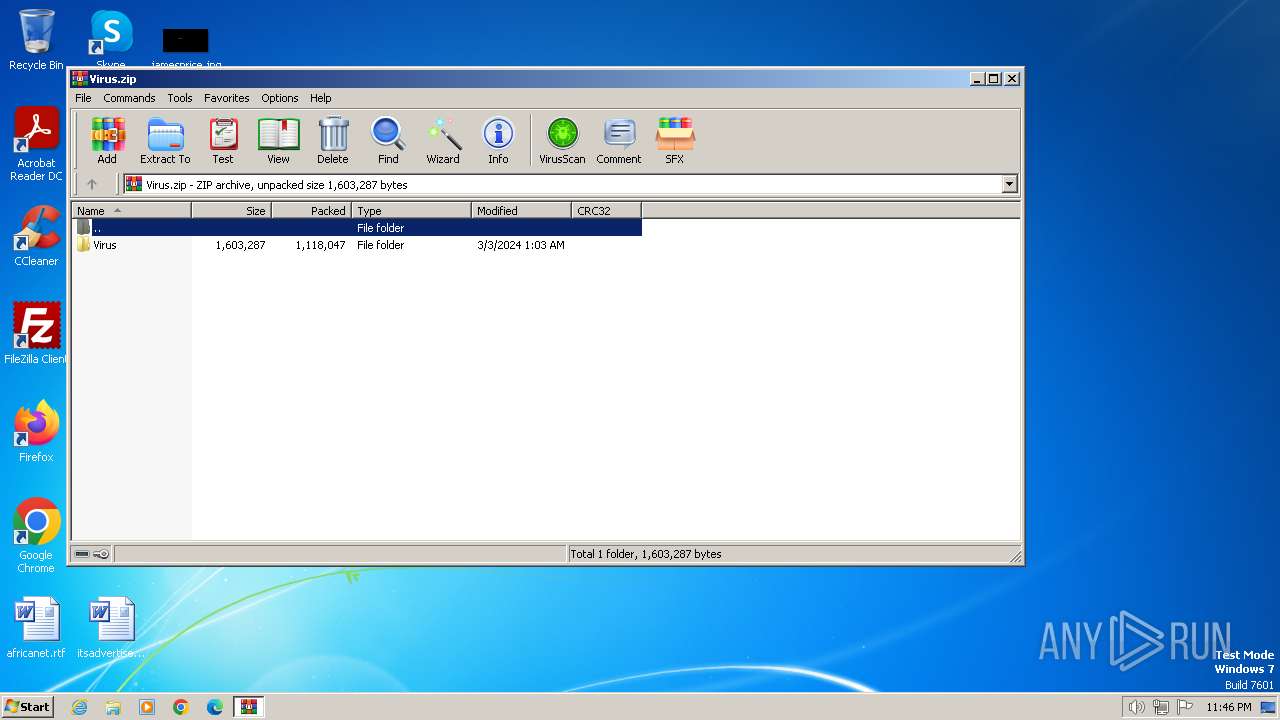
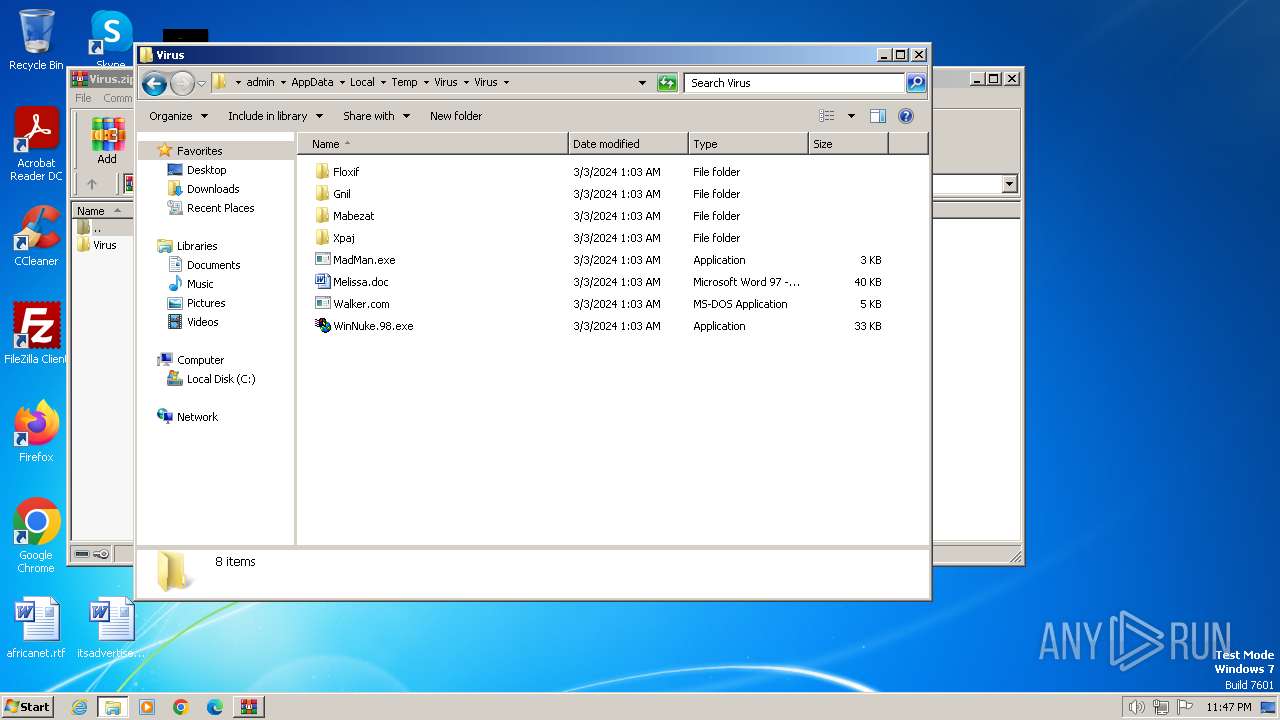
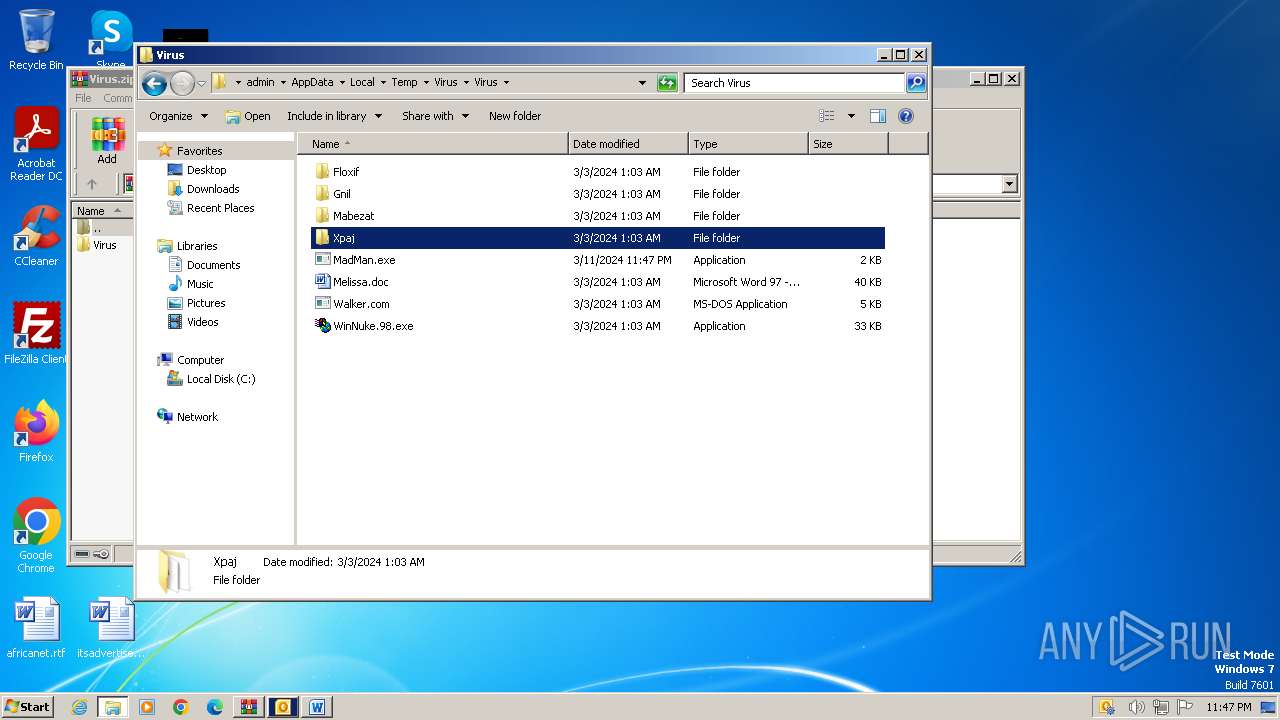
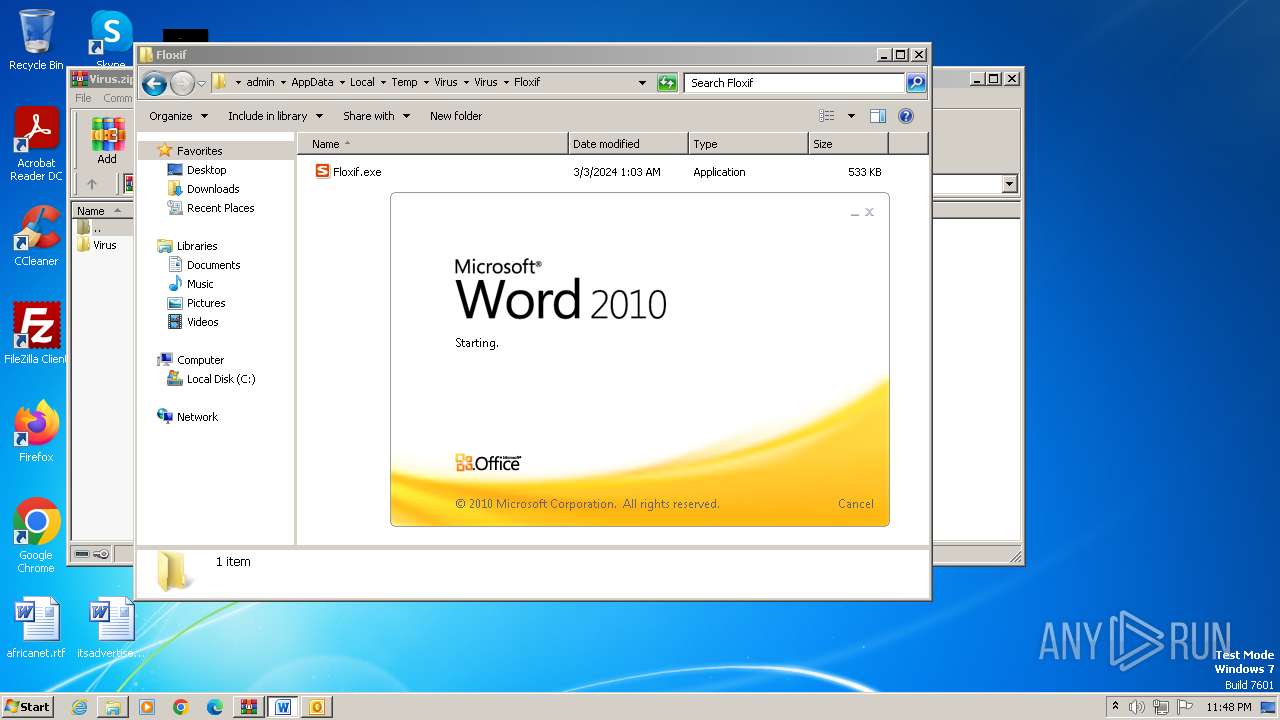
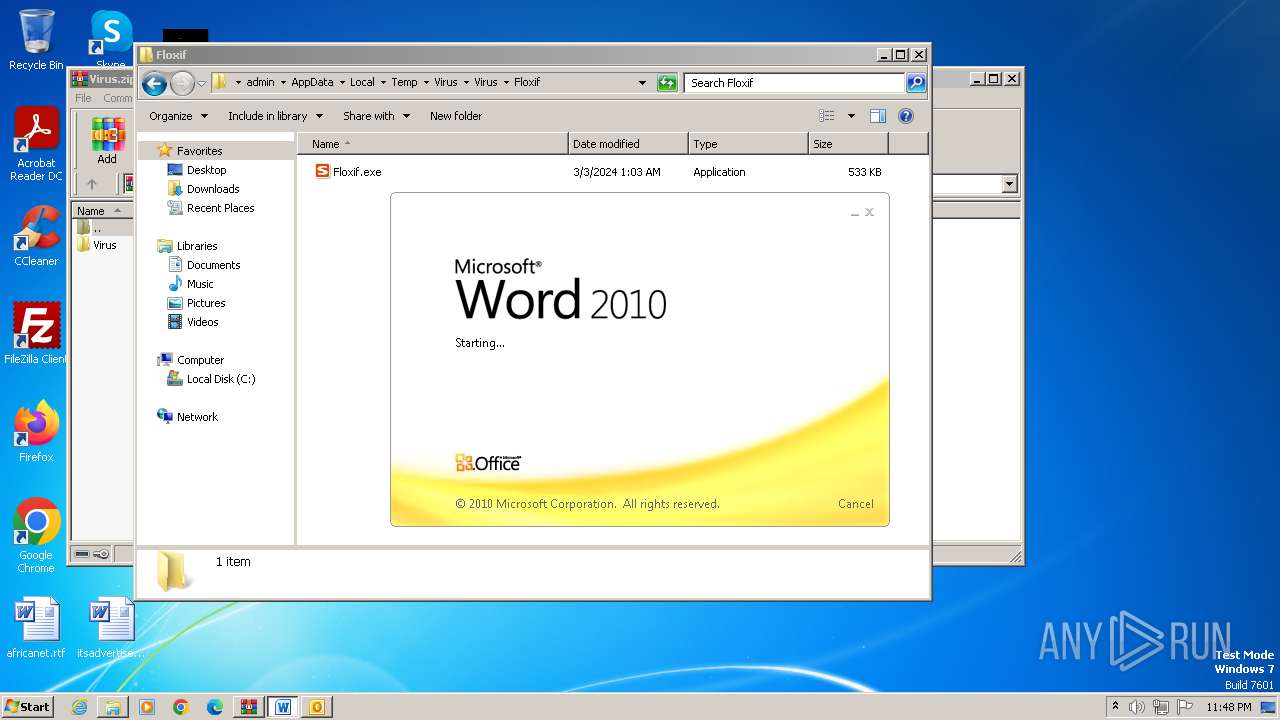
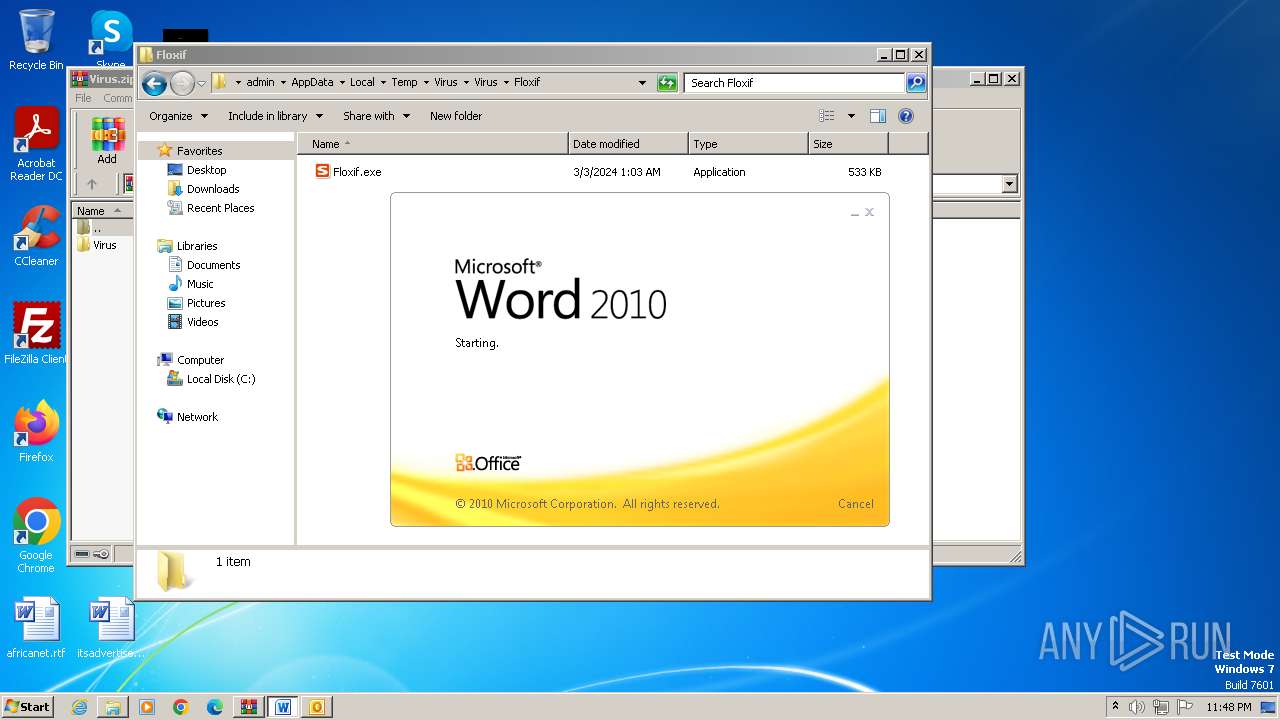
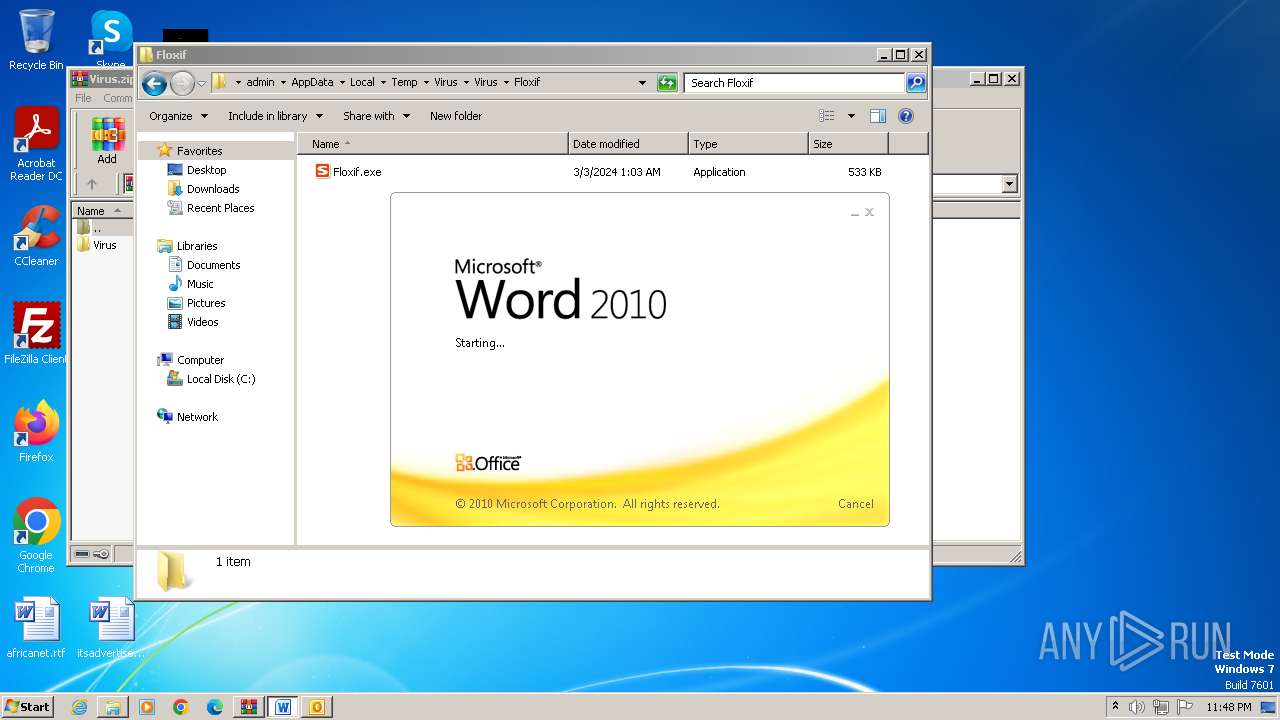
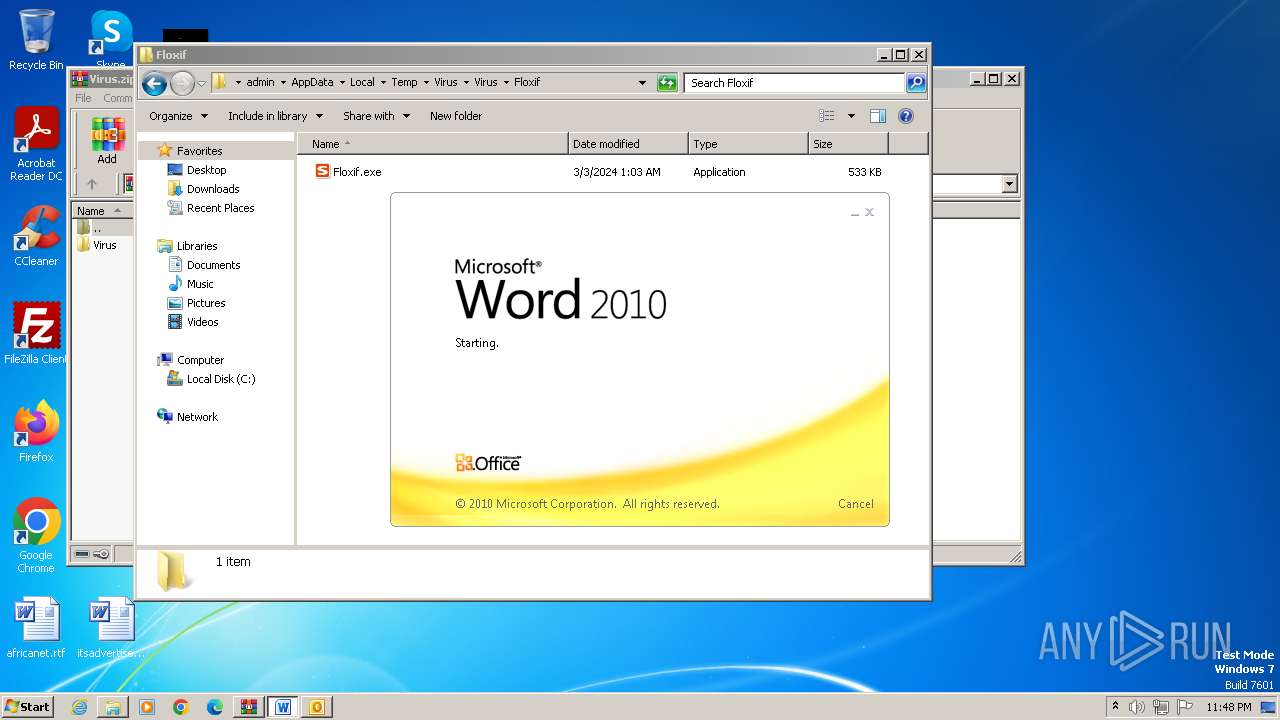
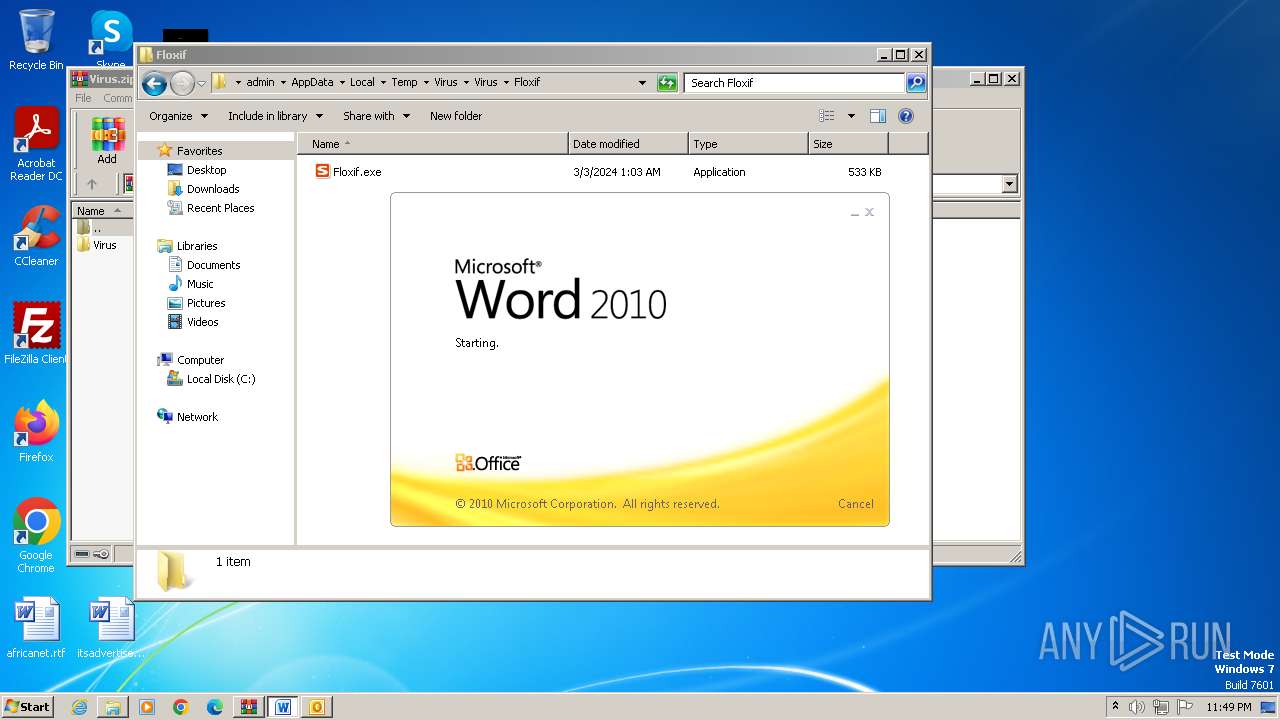
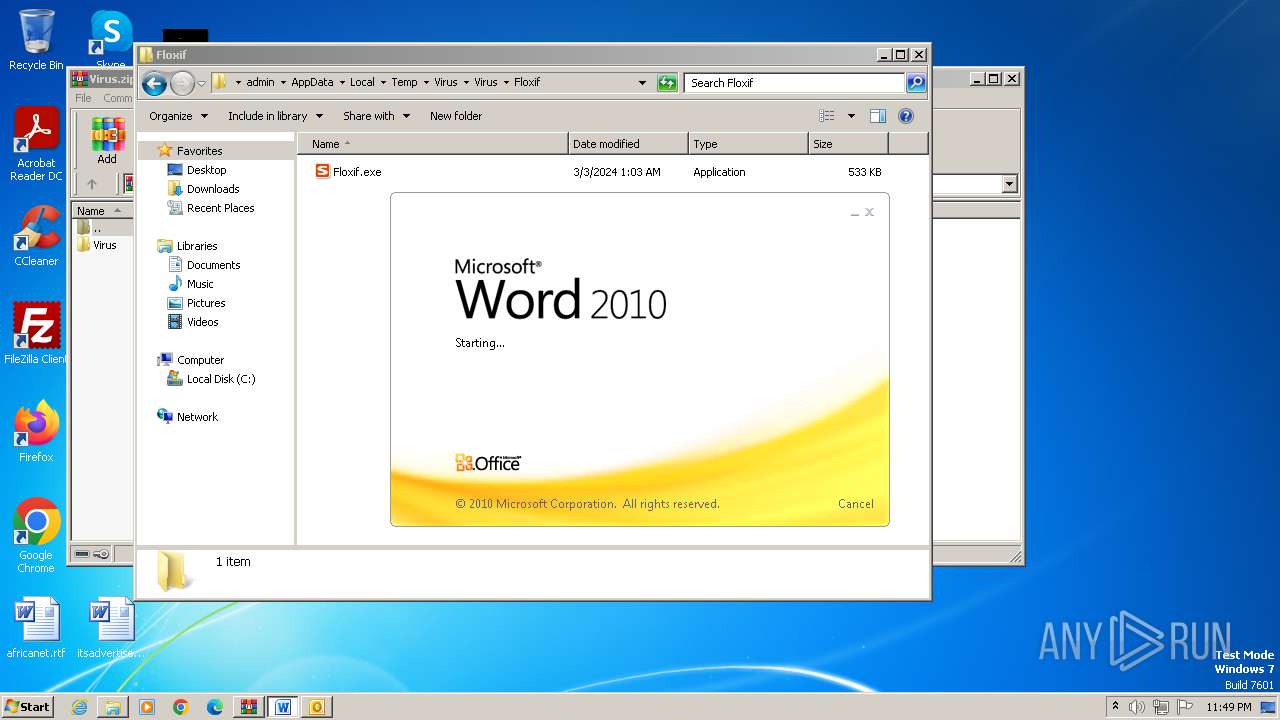
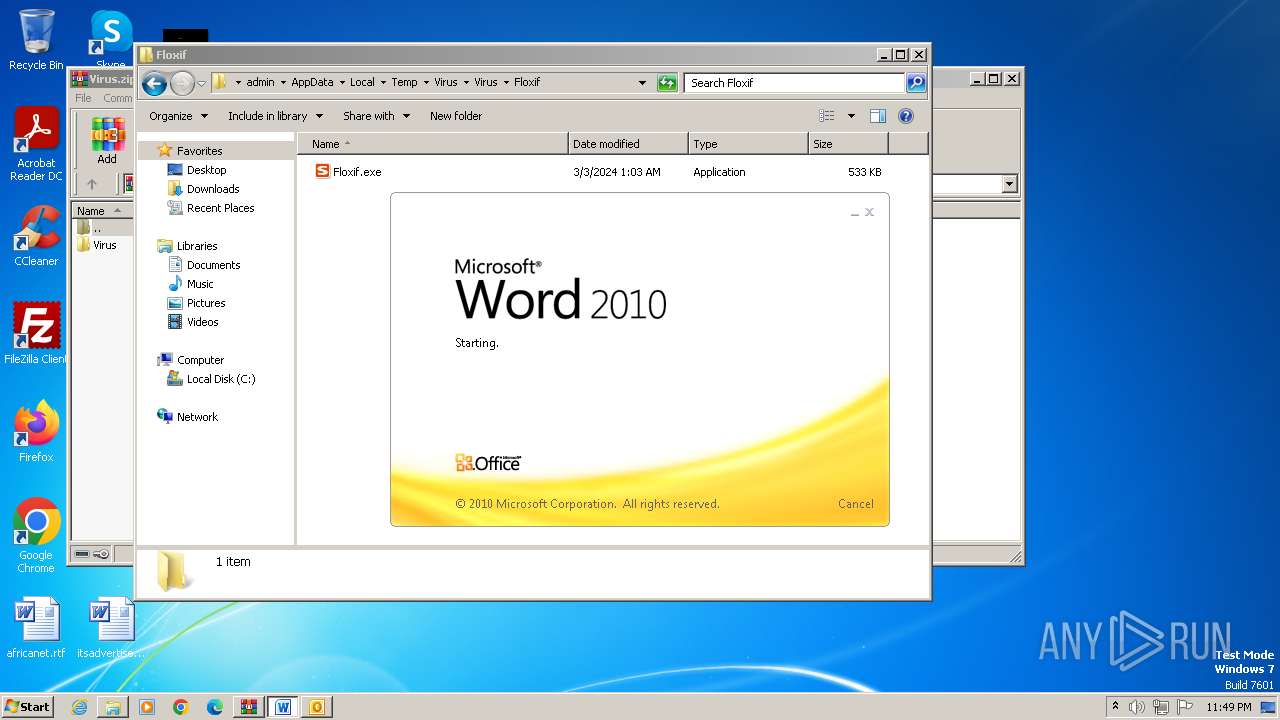
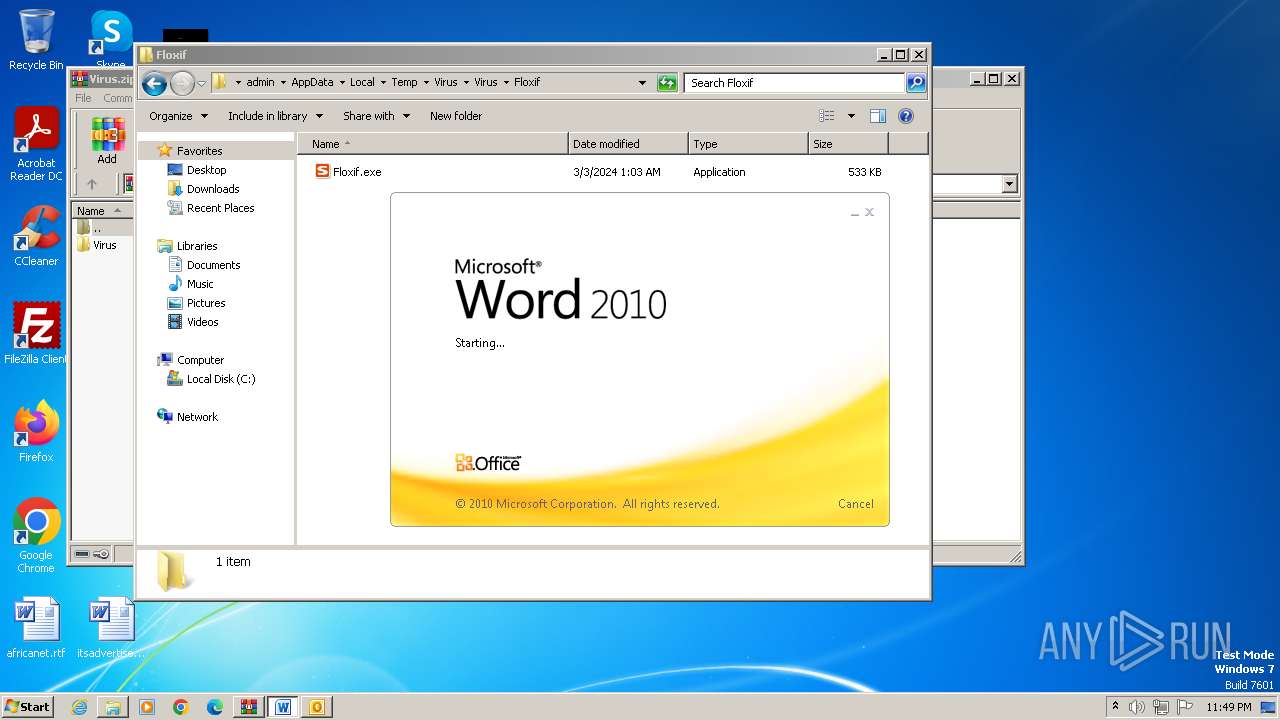
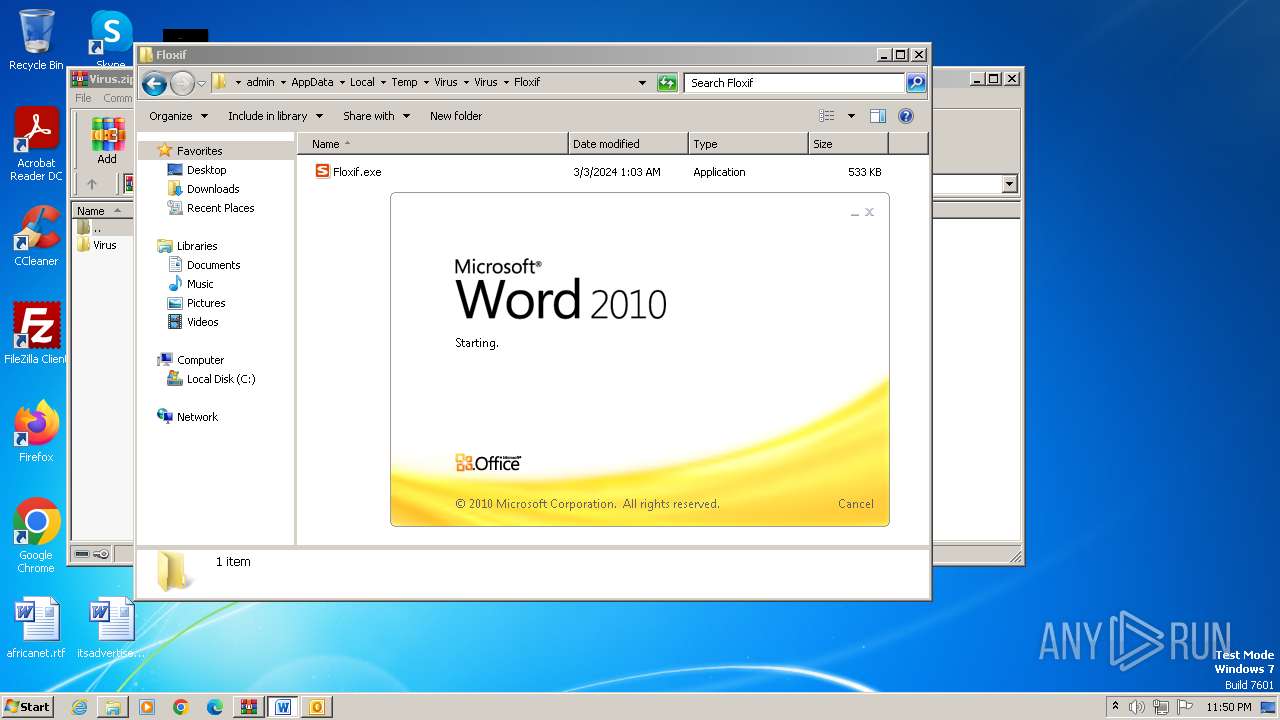
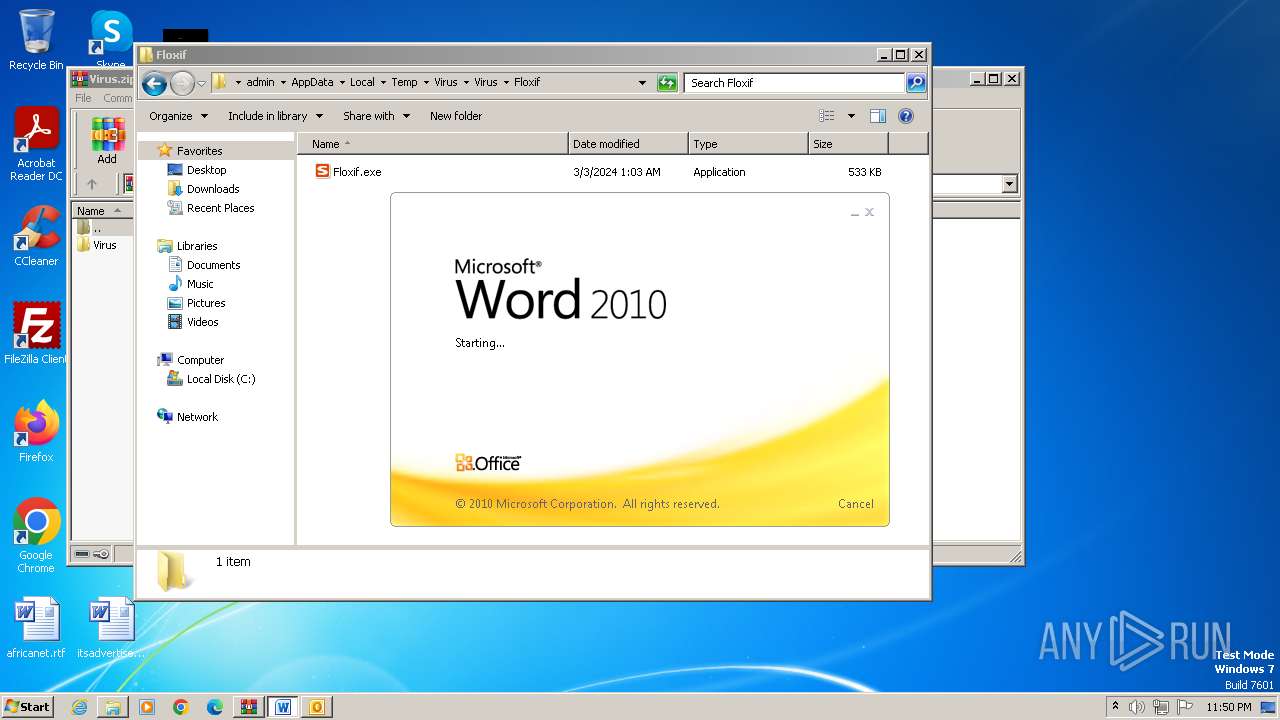
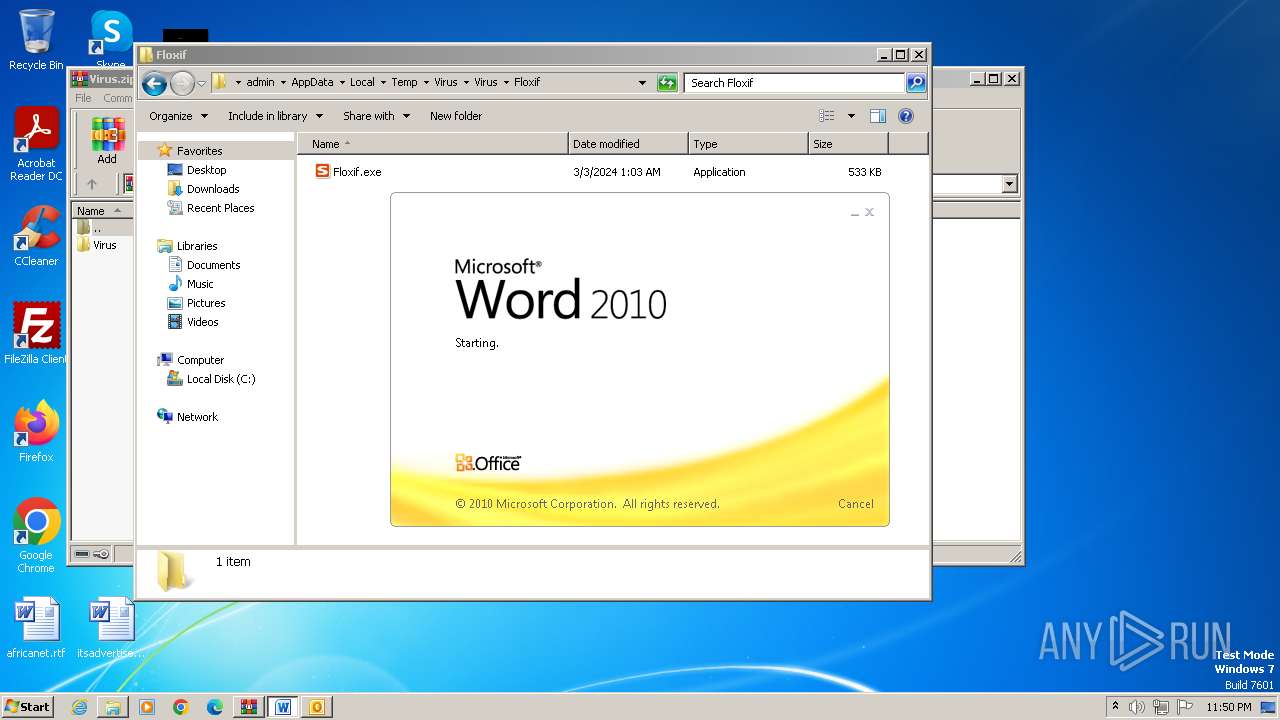
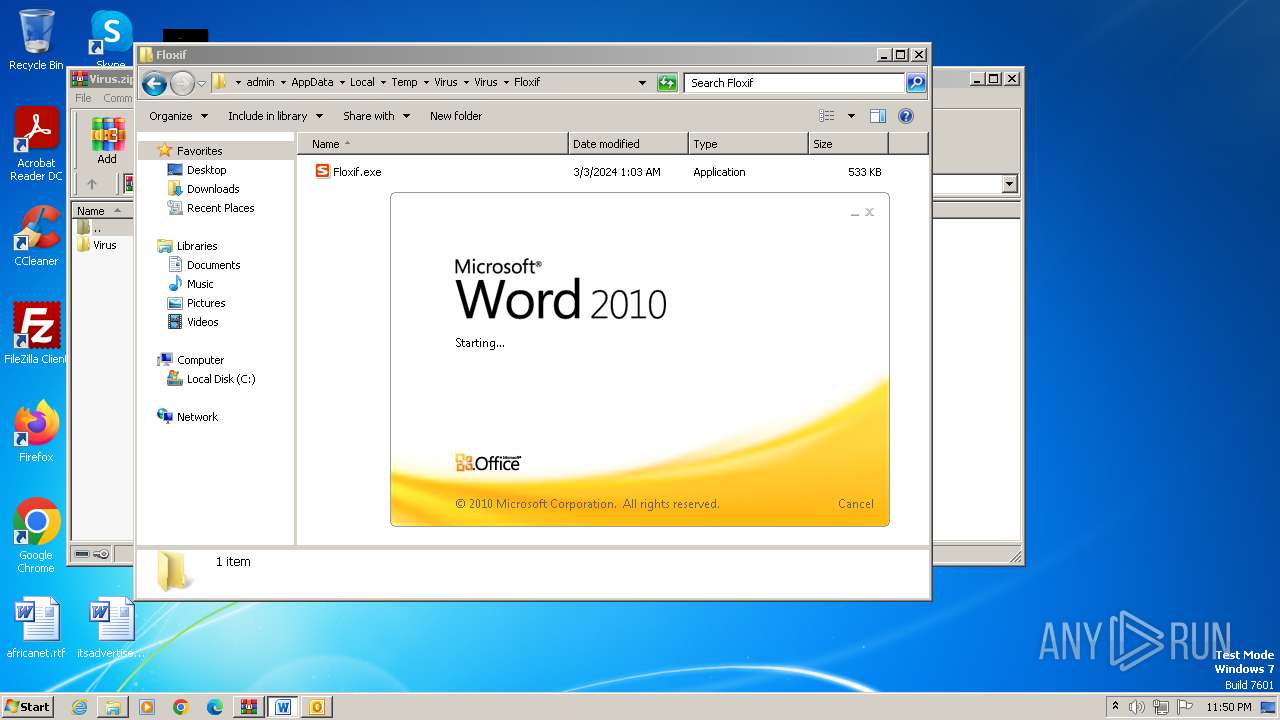
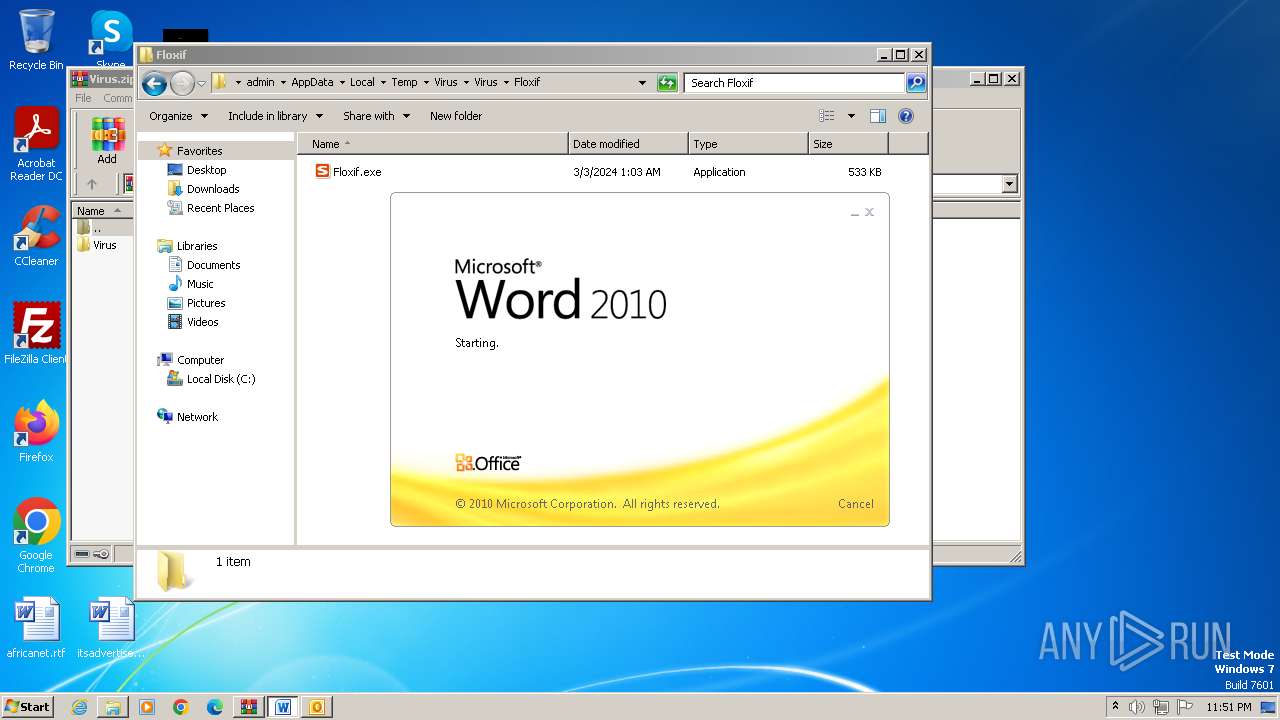
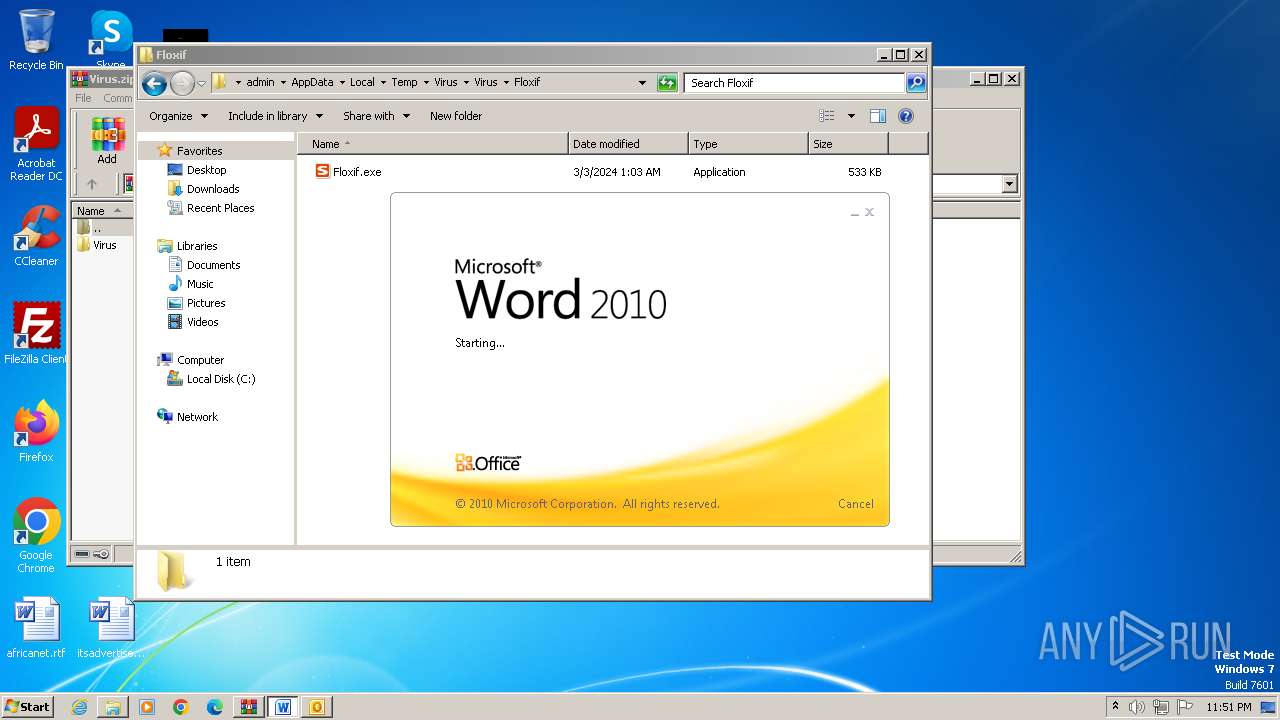
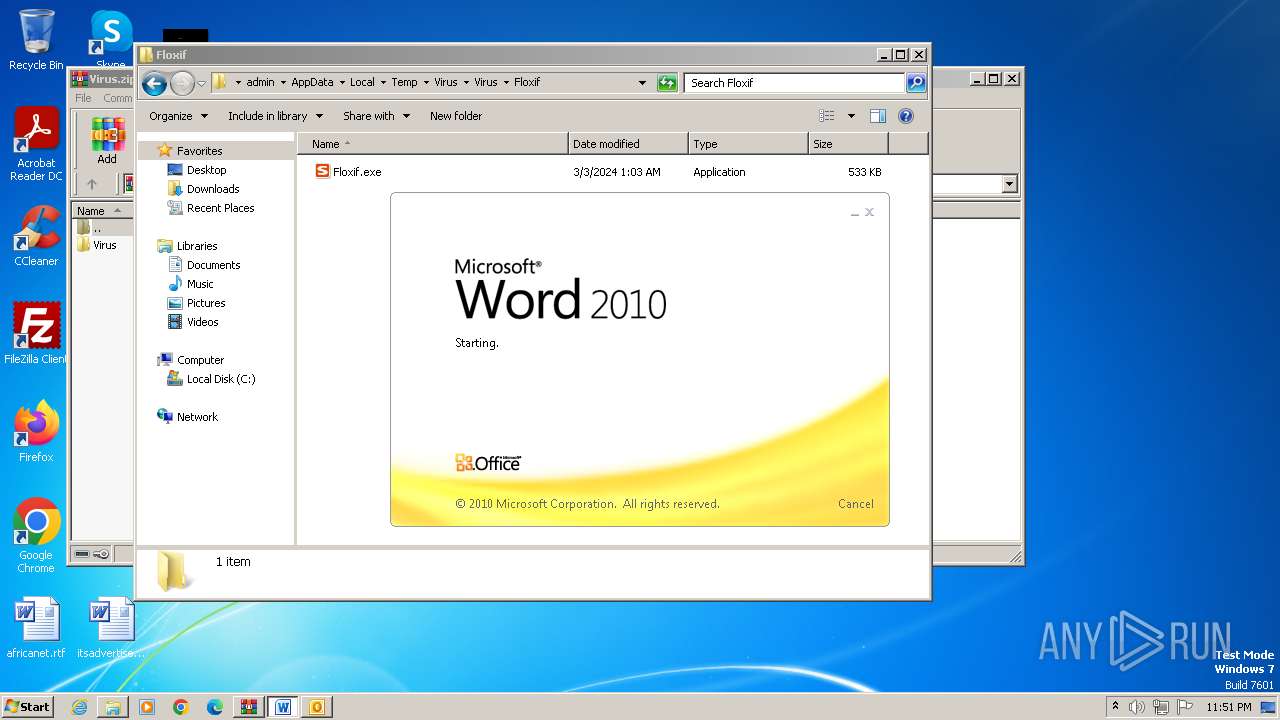
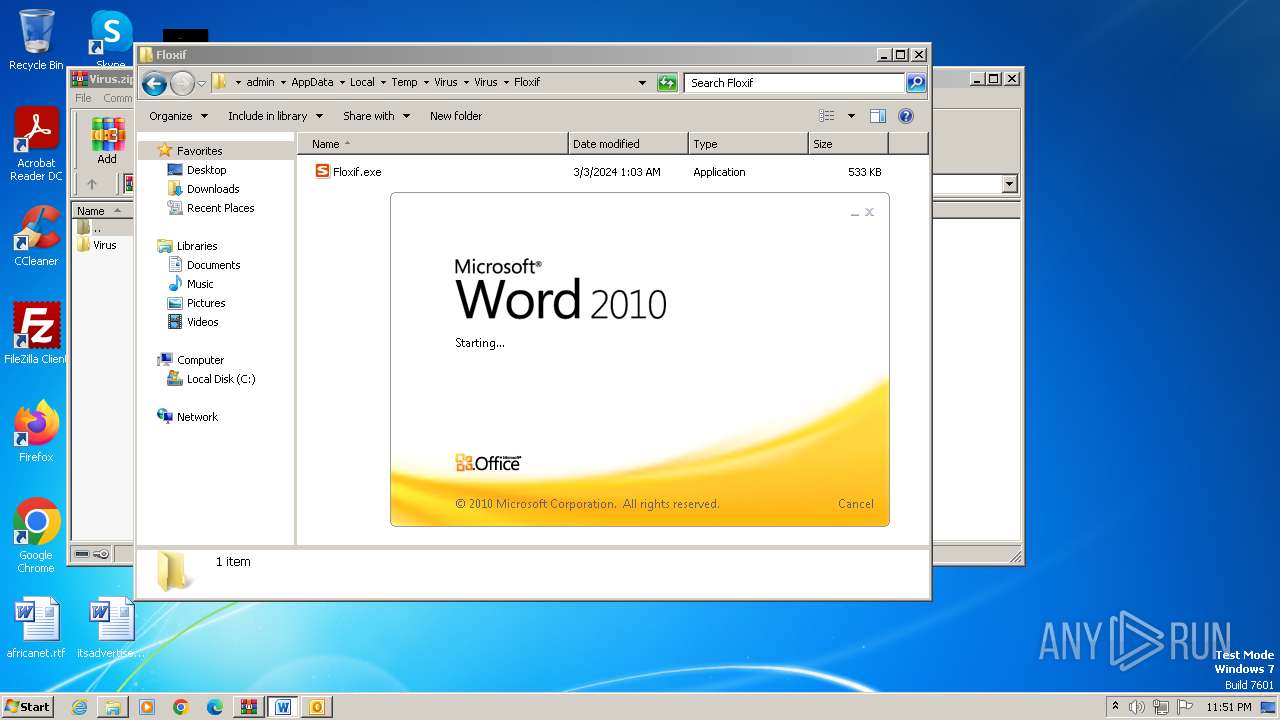
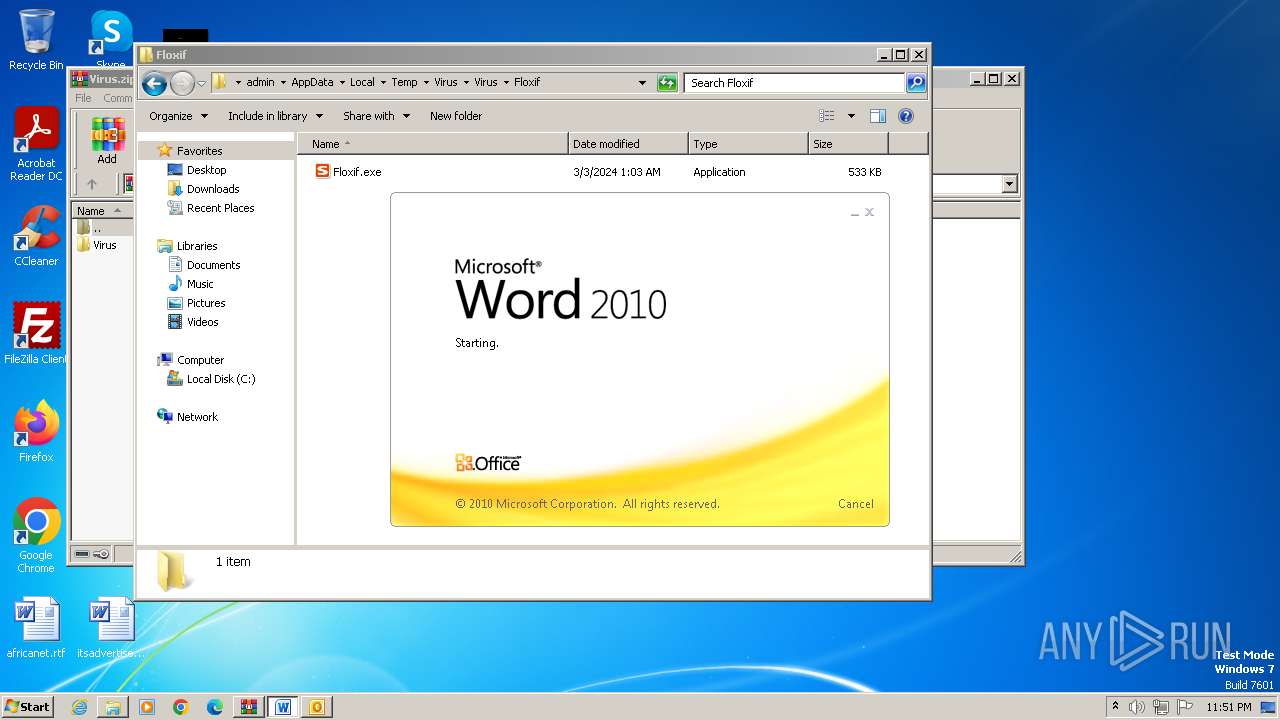
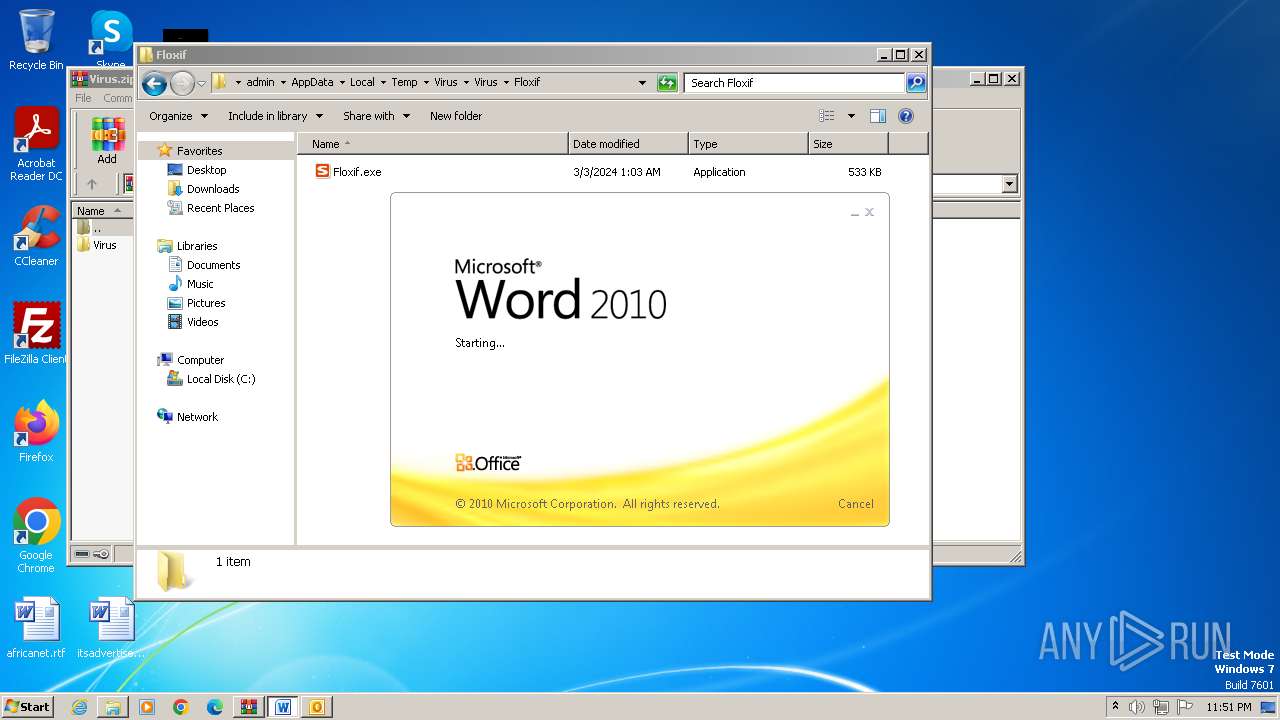
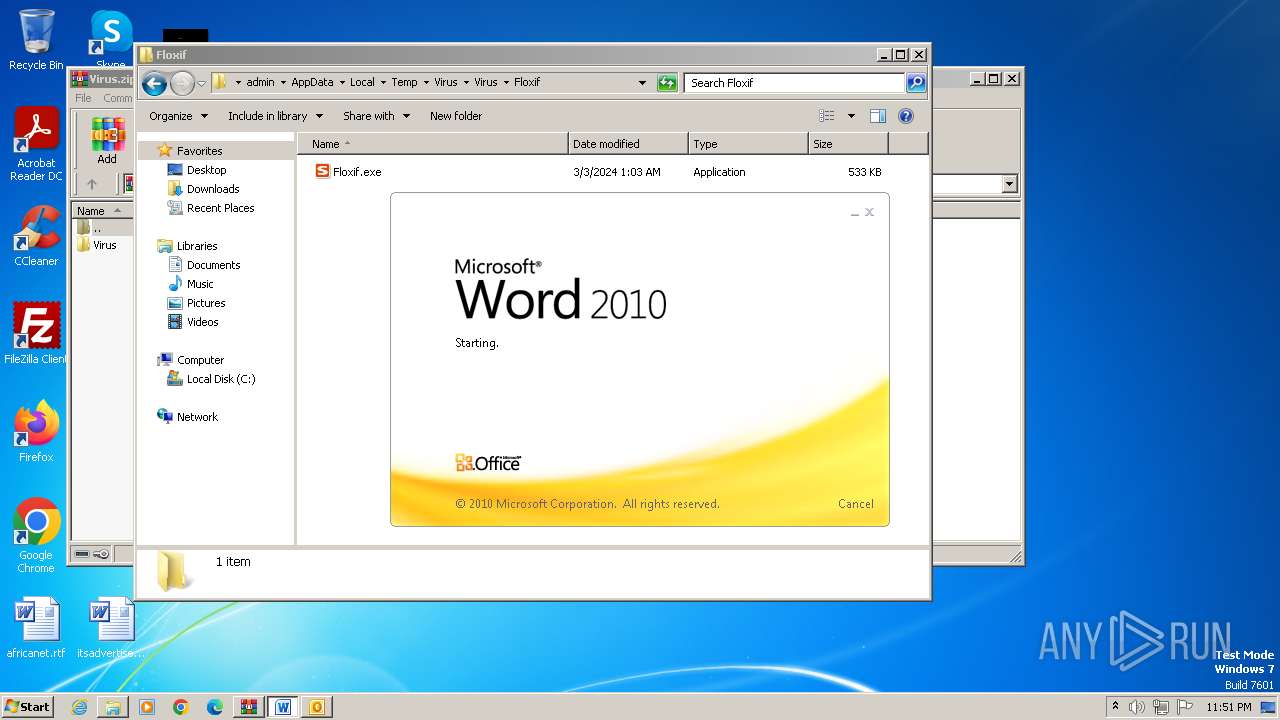
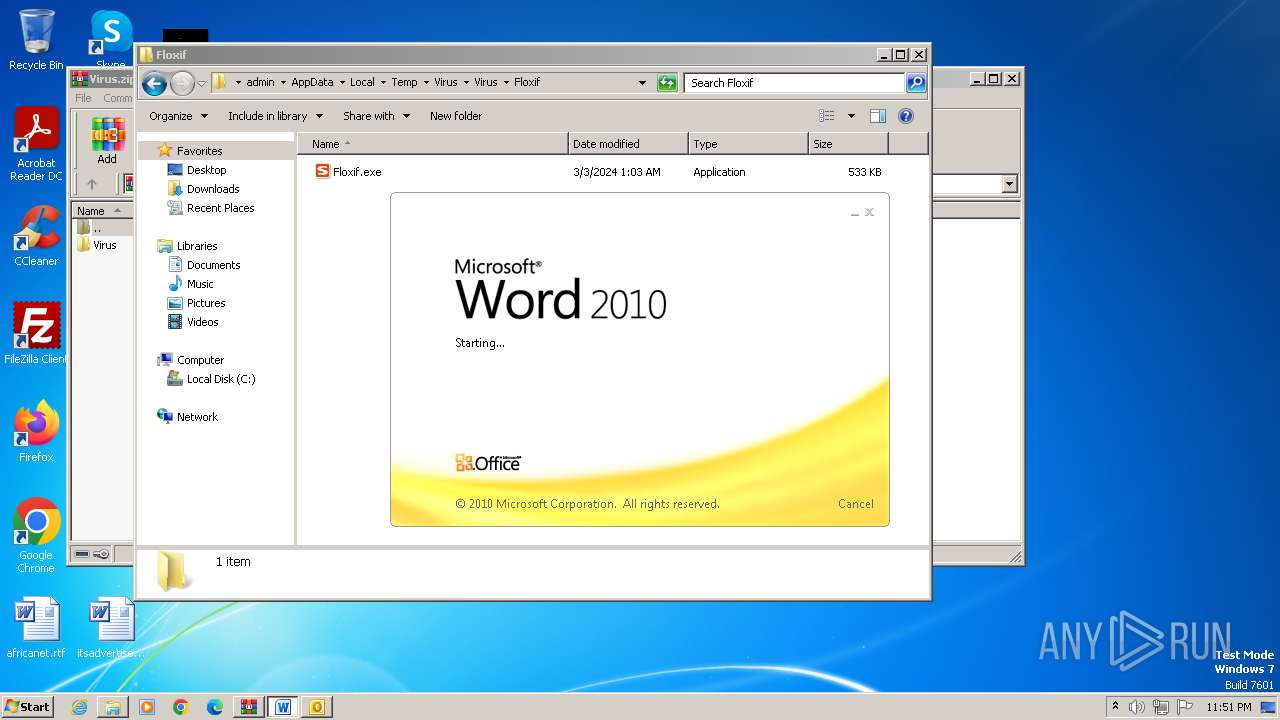
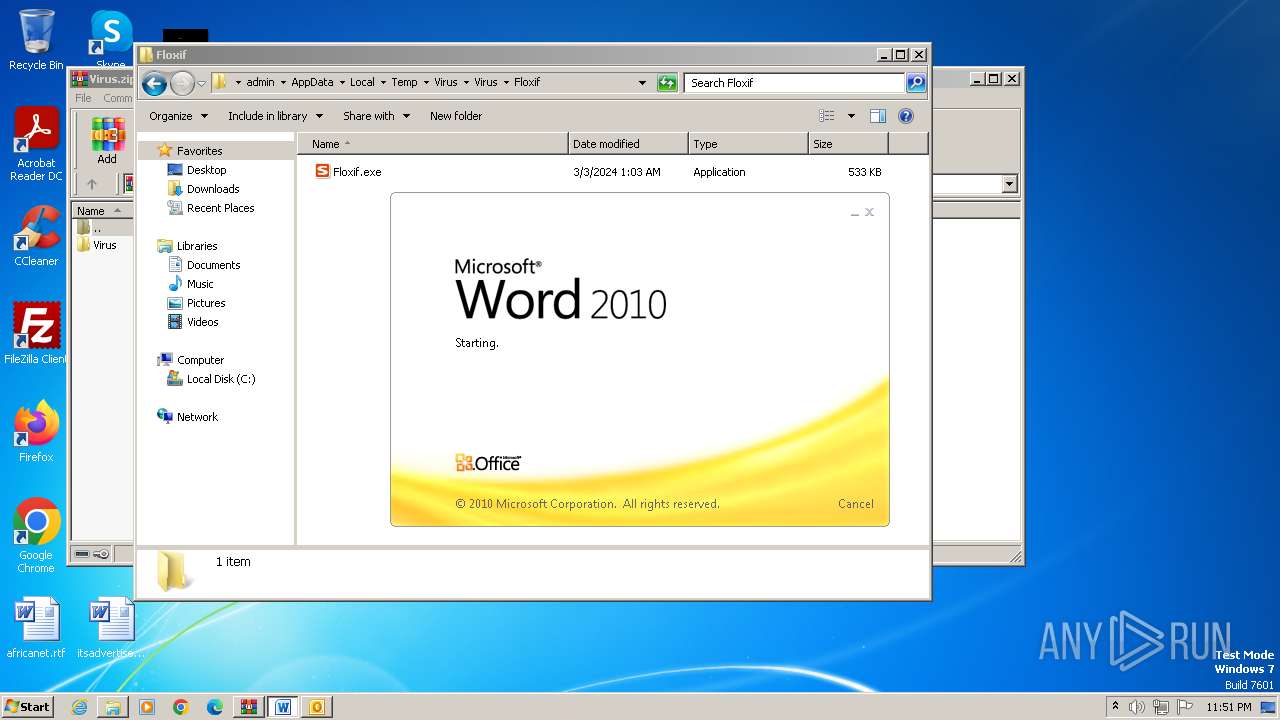
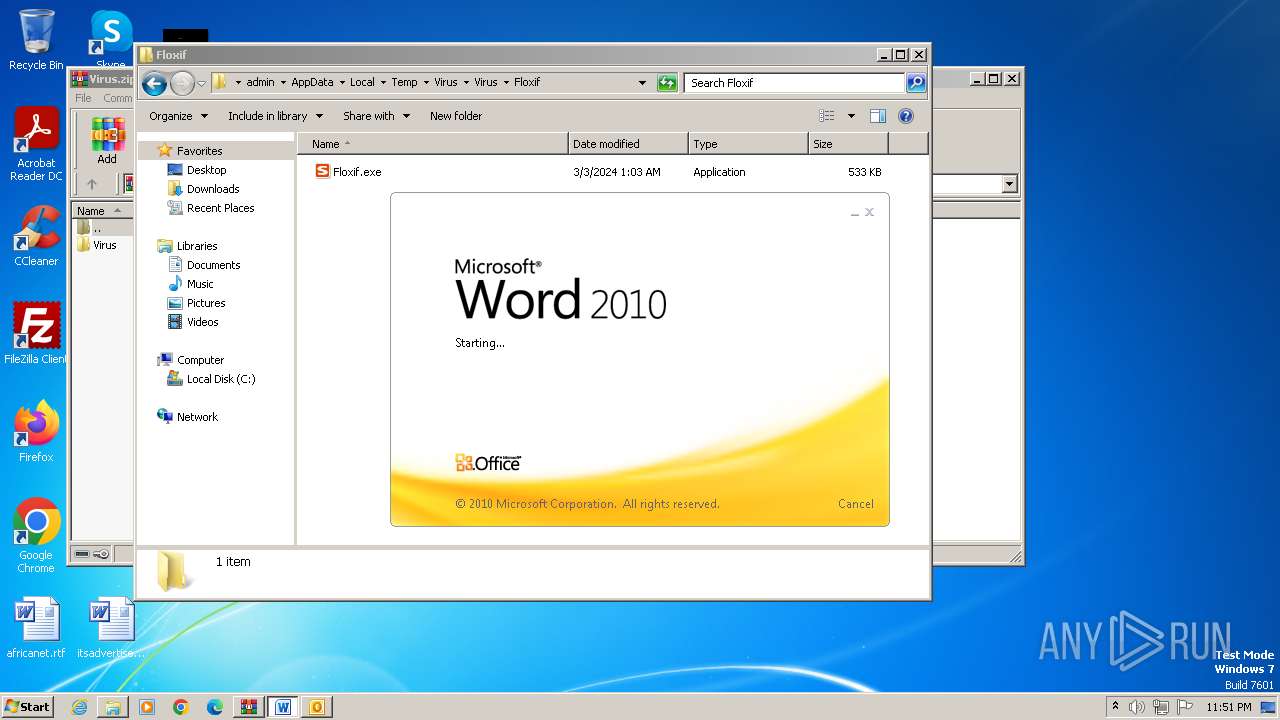
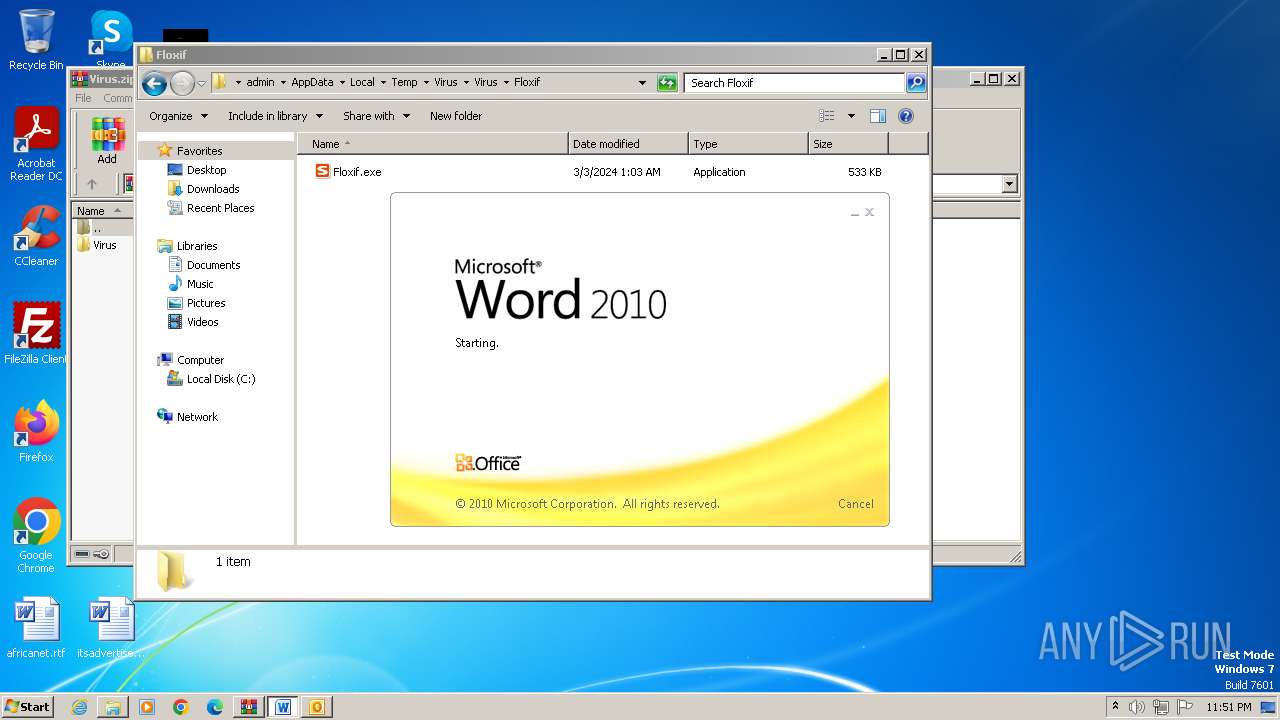
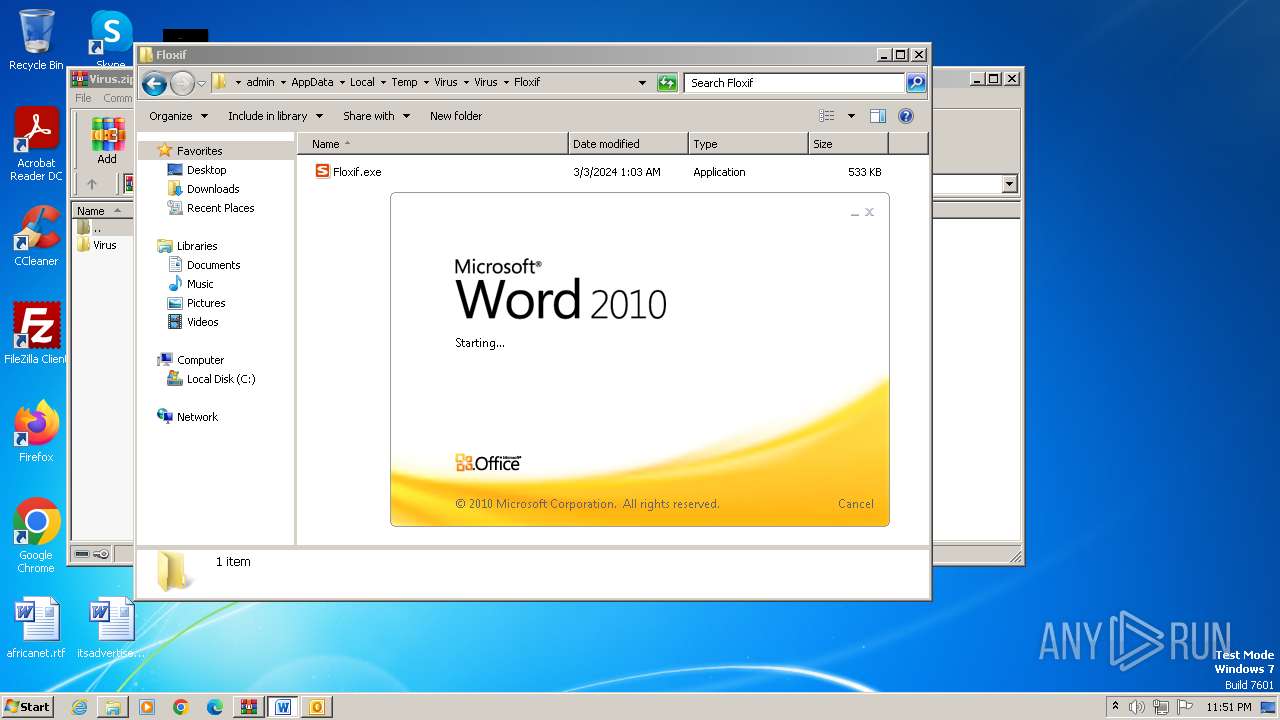
| File name: | Virus.zip |
| Full analysis: | https://app.any.run/tasks/b69e8581-efcb-4c05-af61-5c560443569b |
| Verdict: | Malicious activity |
| Analysis date: | March 11, 2024, 23:46:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract, compression method=deflate |
| MD5: | 6DF3FE1377C96F187DA2ECD6CFEF5CDF |
| SHA1: | 175D456F507ED915ED81DC90AD575AE735CA7487 |
| SHA256: | 75F66F67490CF4242D4304F7101F706CC3DF30310F727EA02945158C3A9F715D |
| SSDEEP: | 49152:zMfcSQRvQXTtQ4TzOZcwNPsYI3Ha31zZF8HR4exJXdmiOTu8JkRbIJND53hAO5g0:ztvVOTtRqaKPslHKFY42JtmiOTuWYmNt |
MALICIOUS
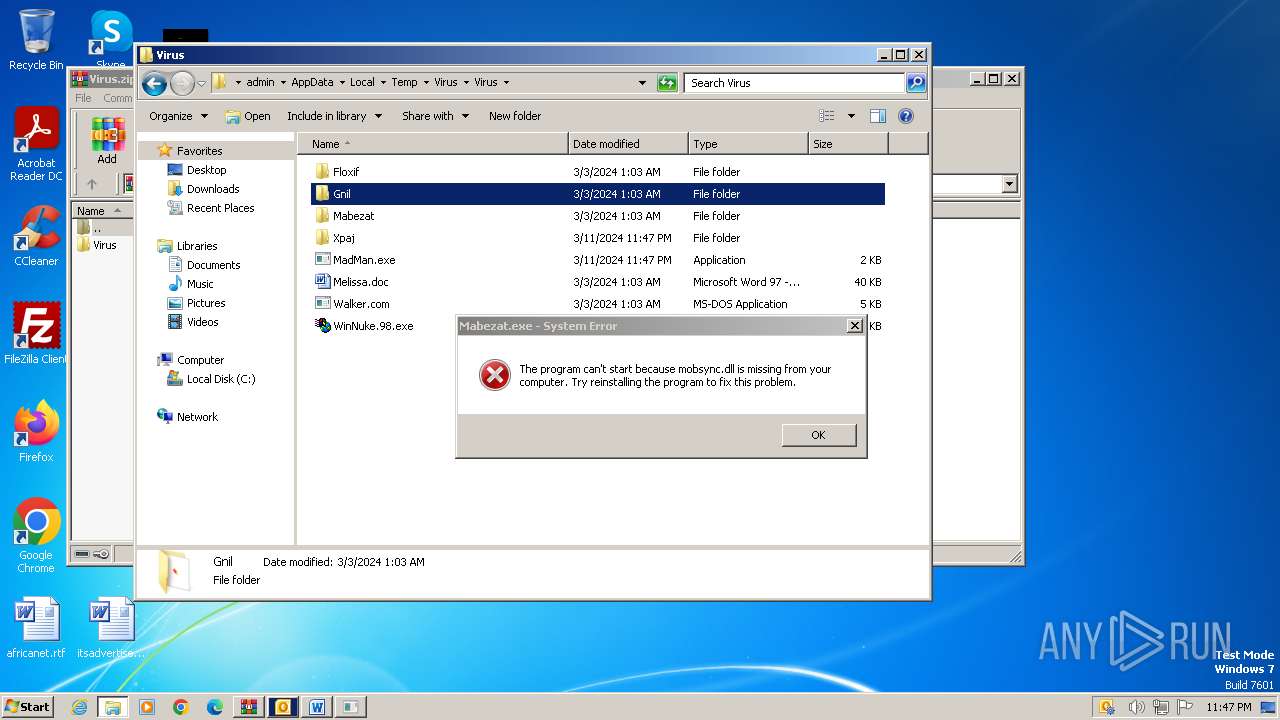
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3668)
- xpaj.exe (PID: 2564)
- xpajB.exe (PID: 1572)
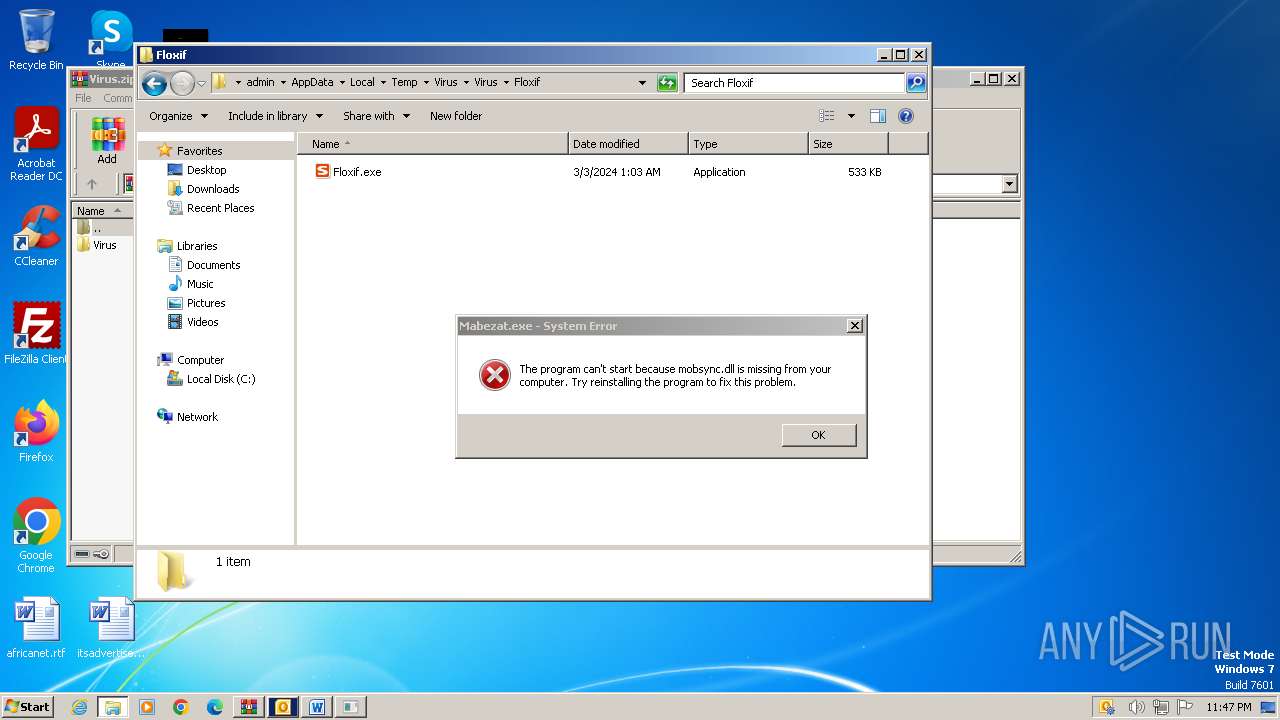
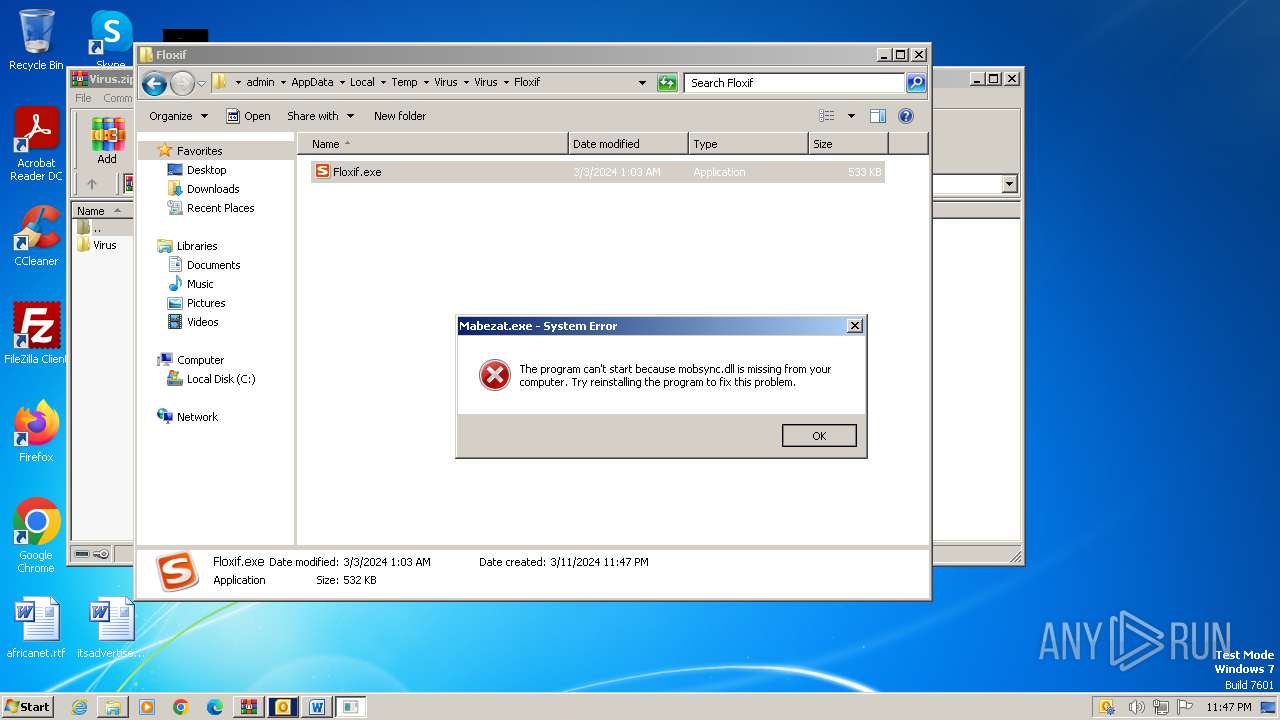
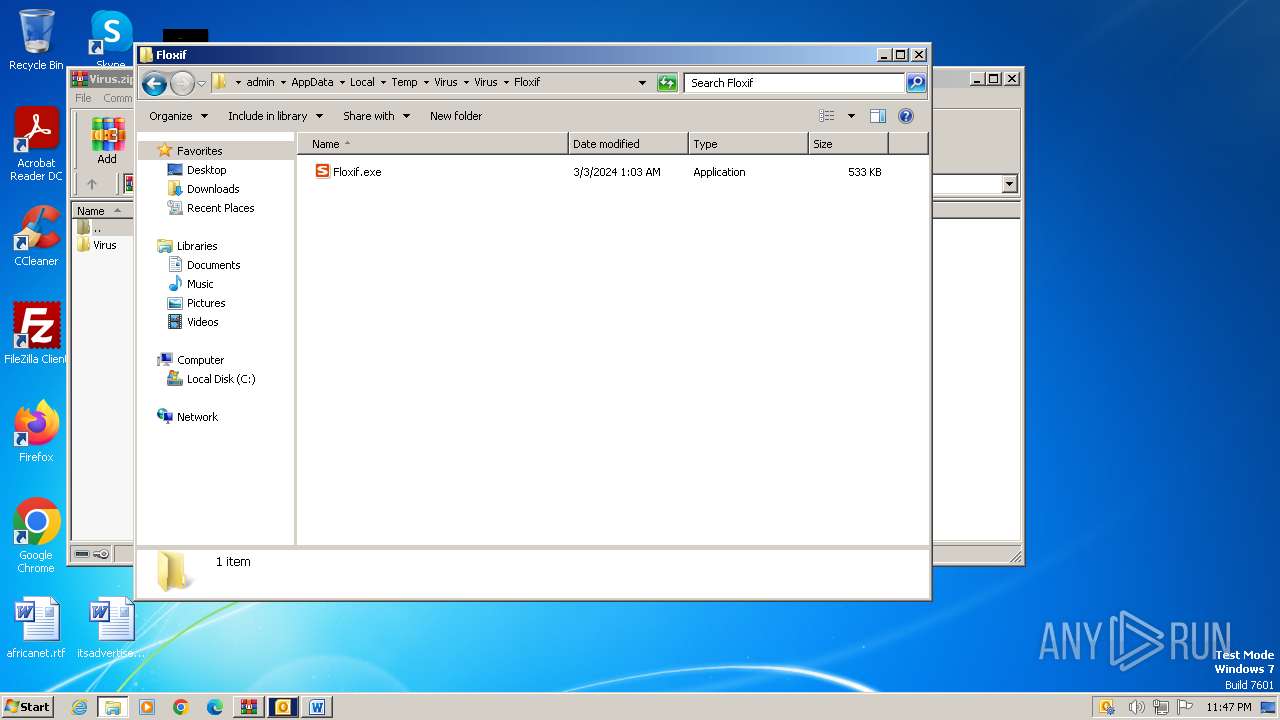
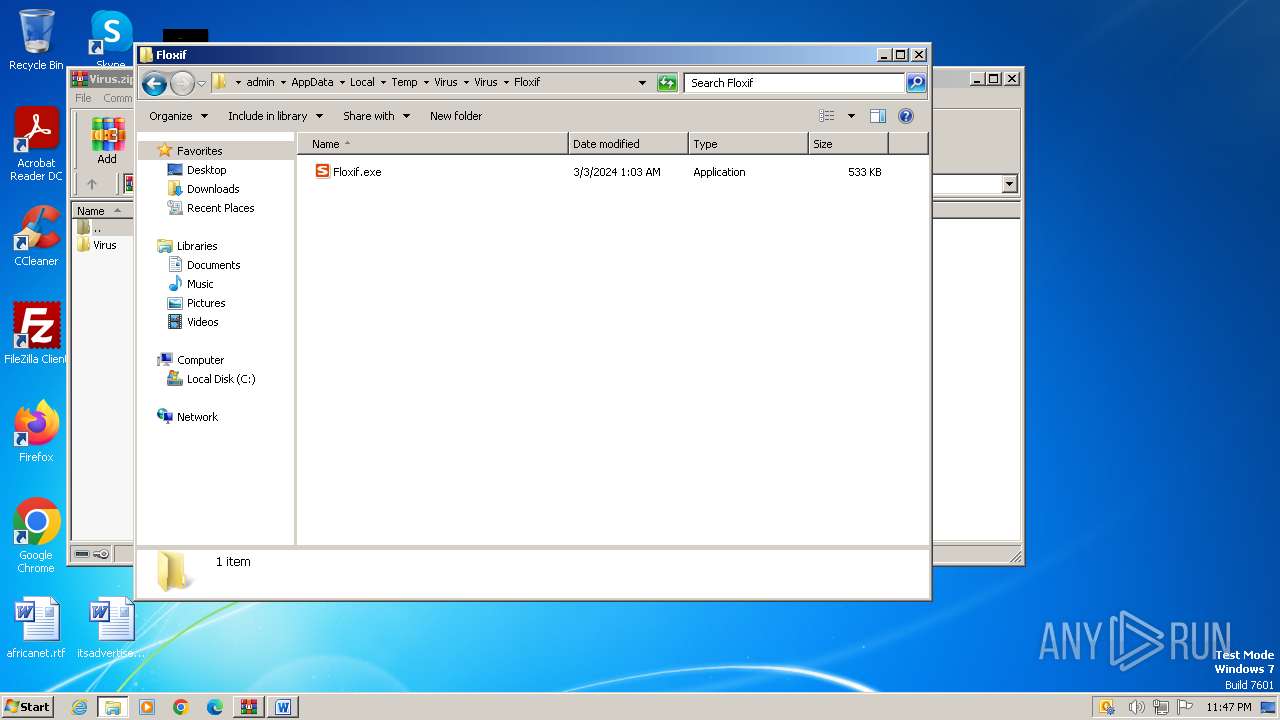
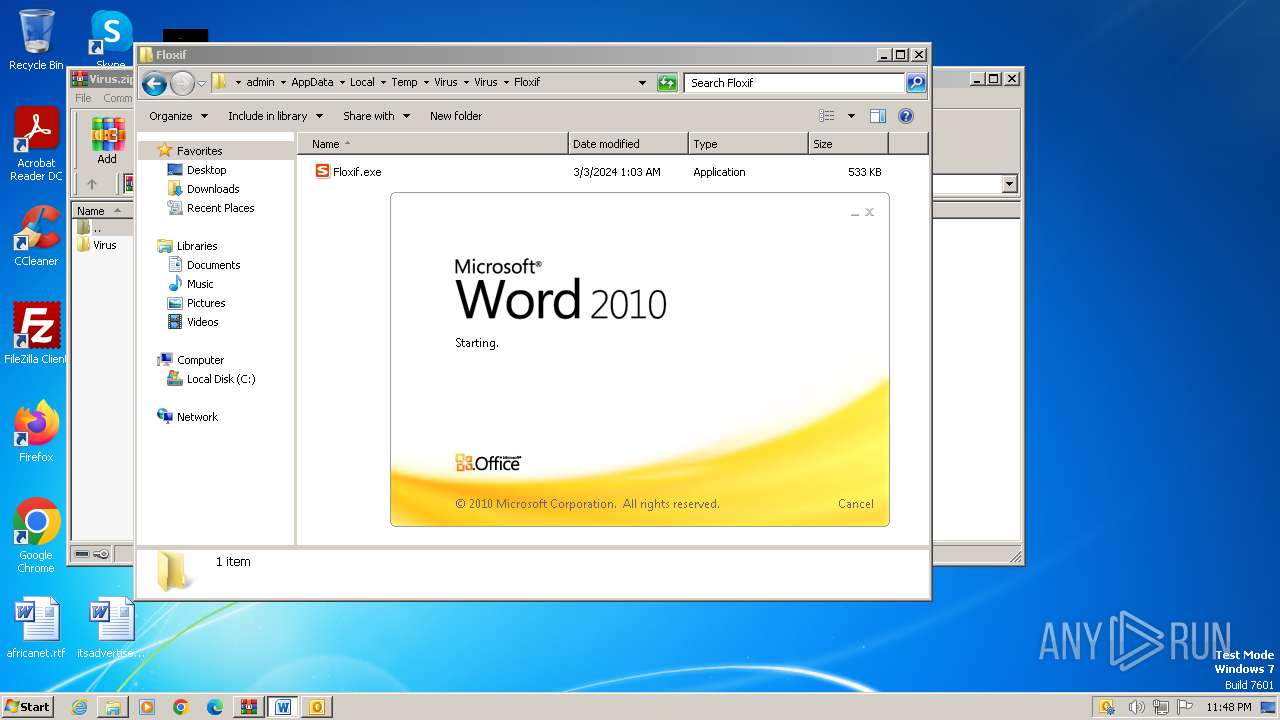
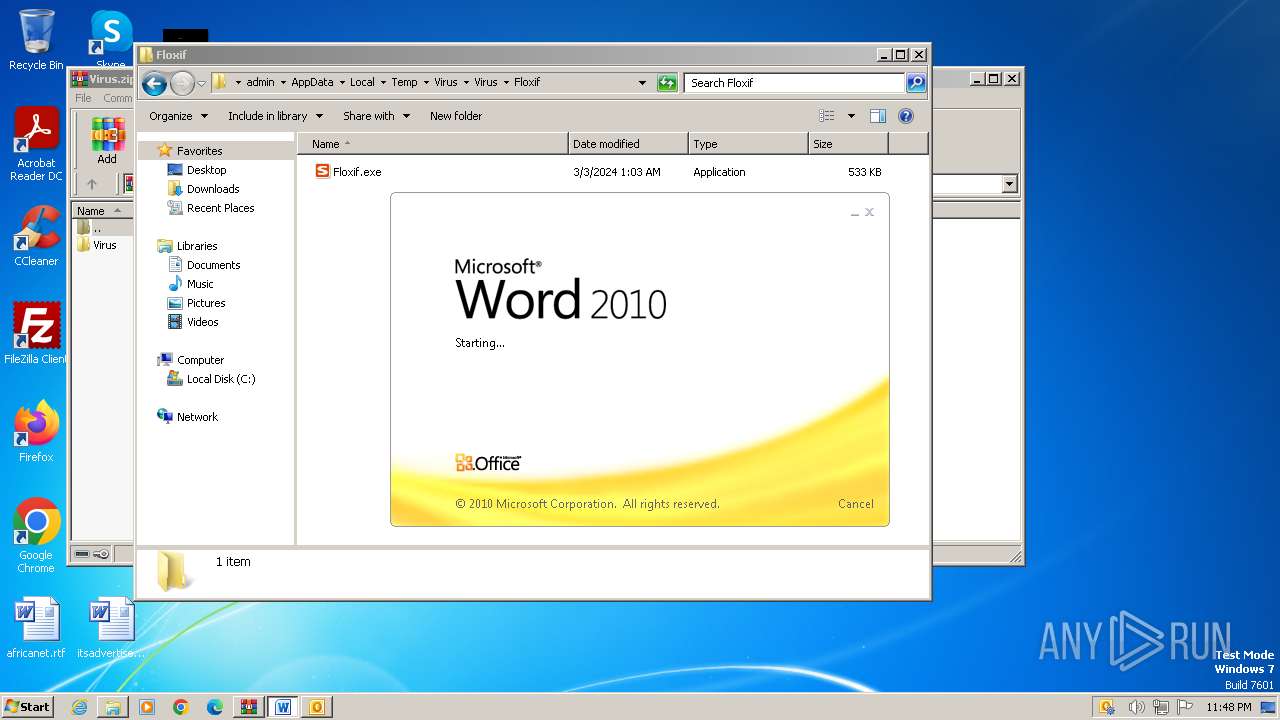
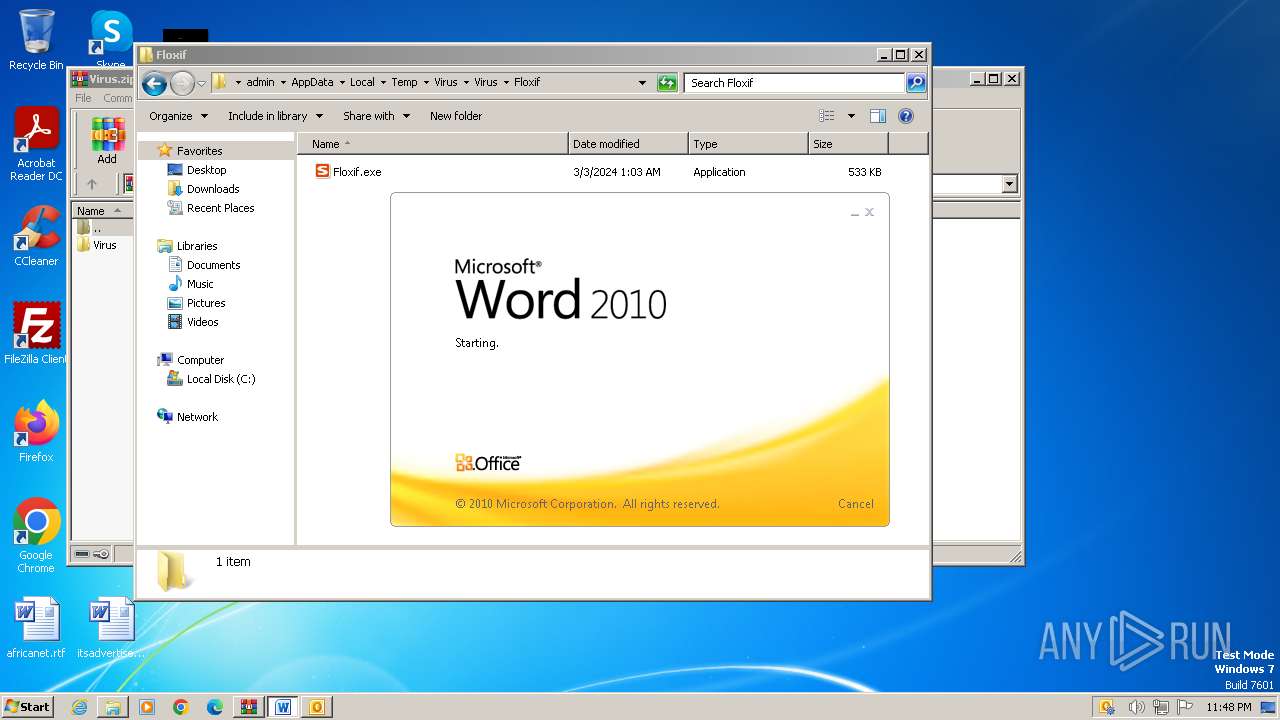
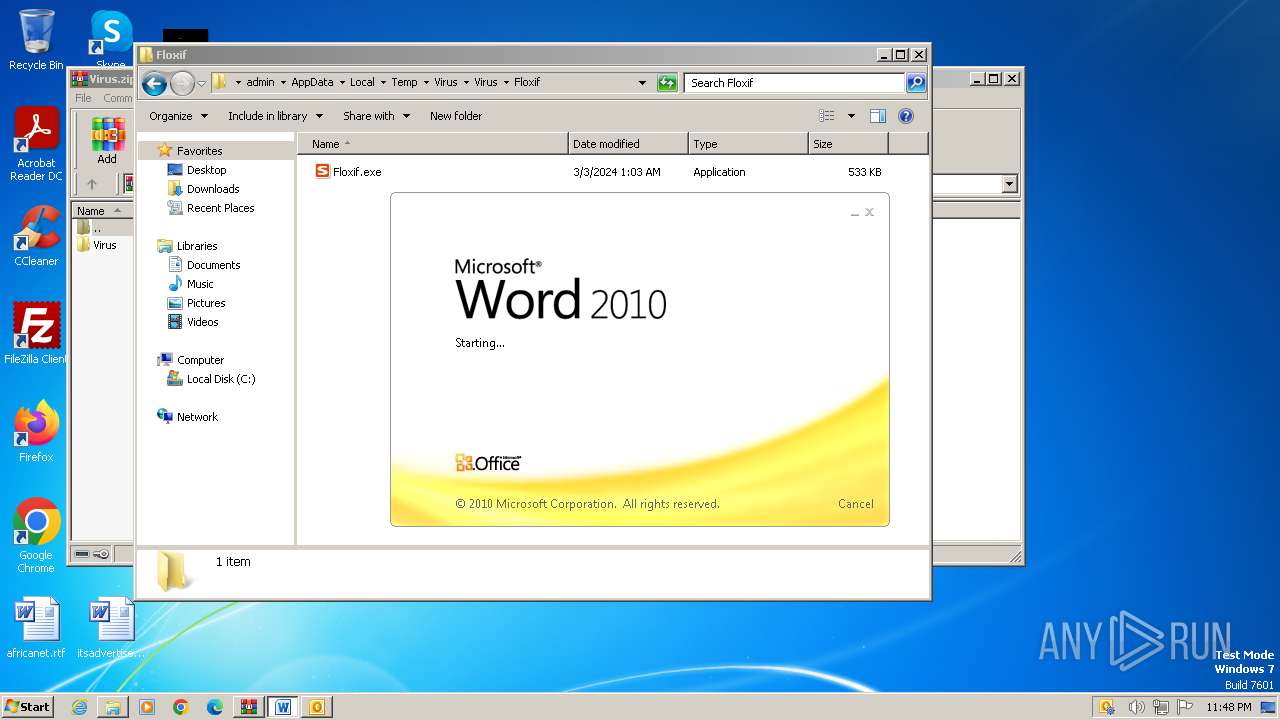
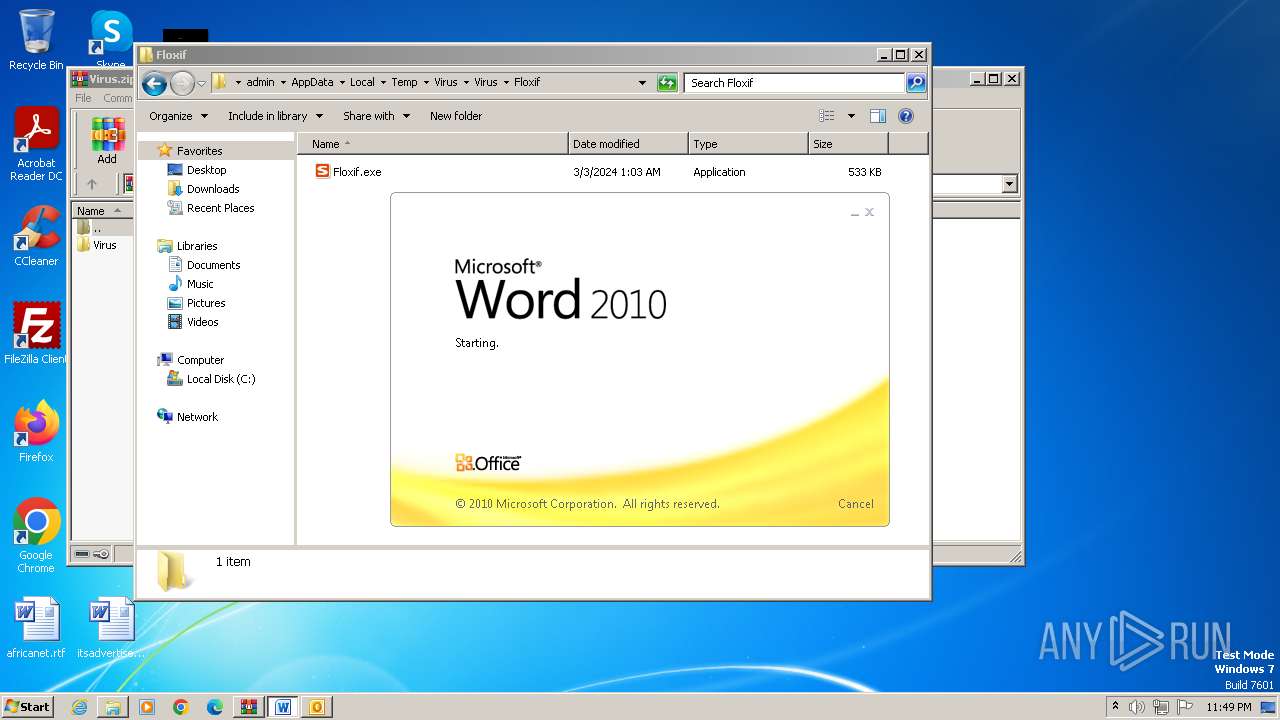
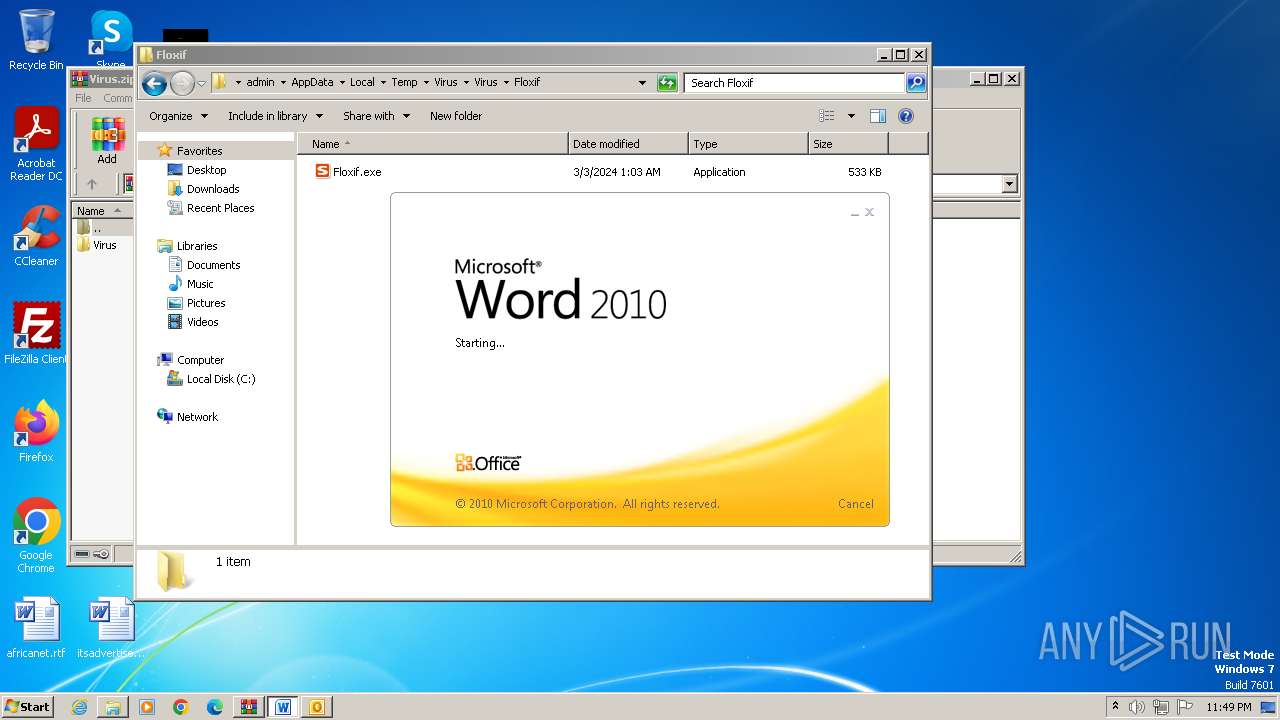
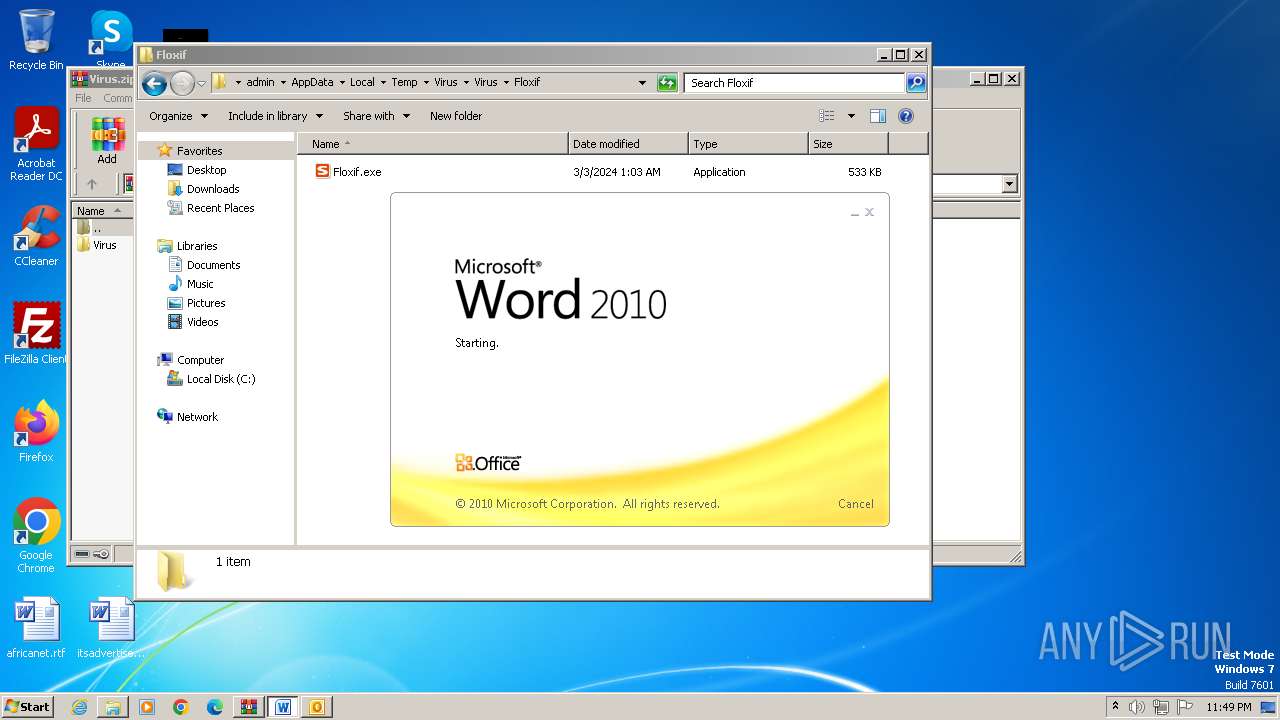
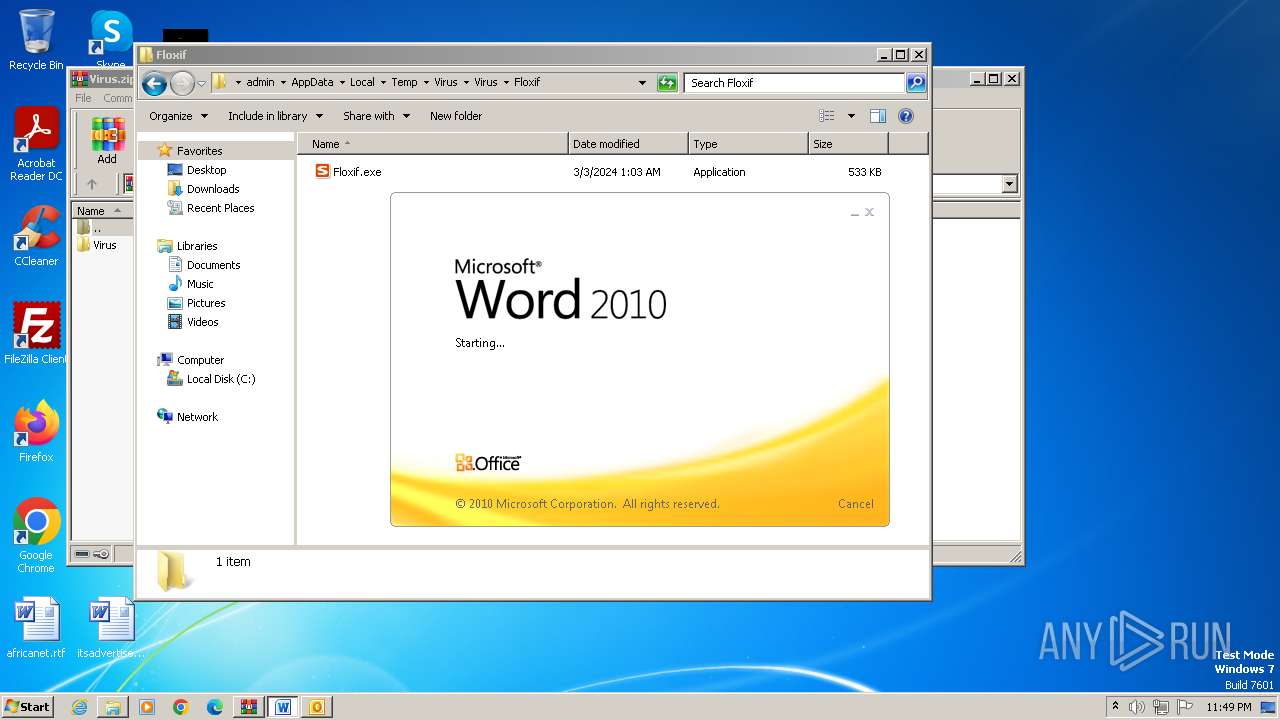
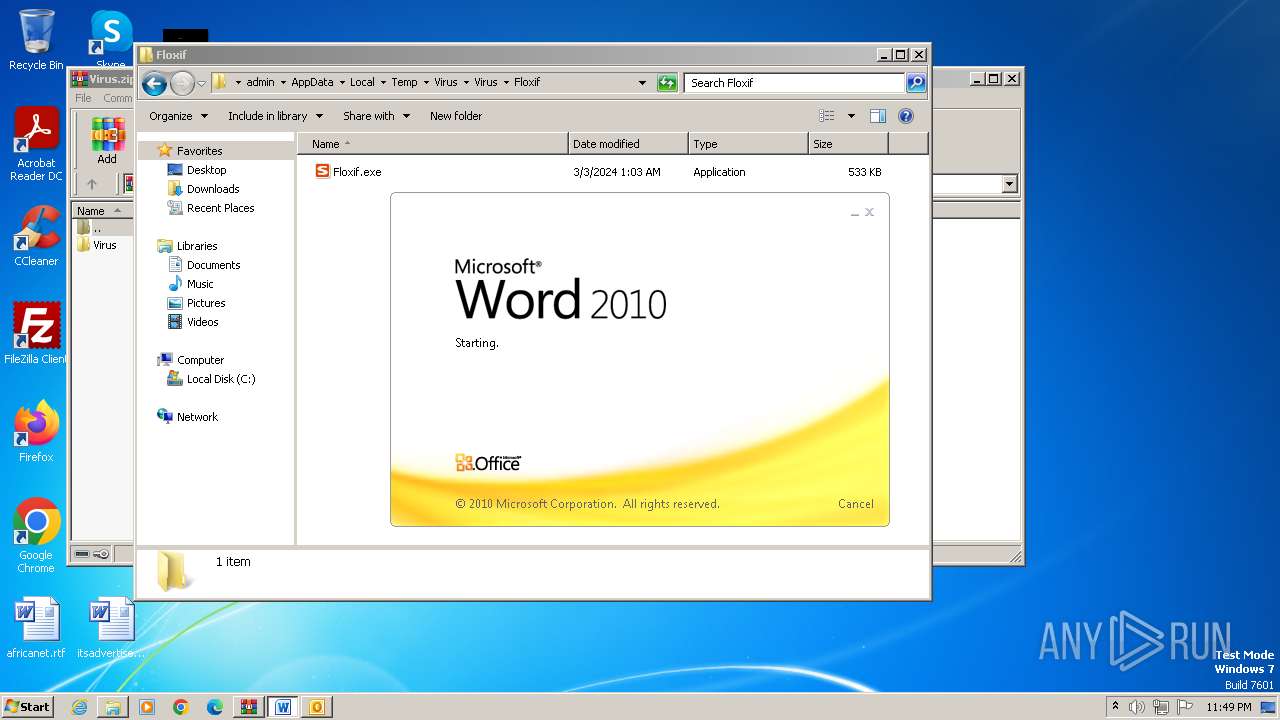
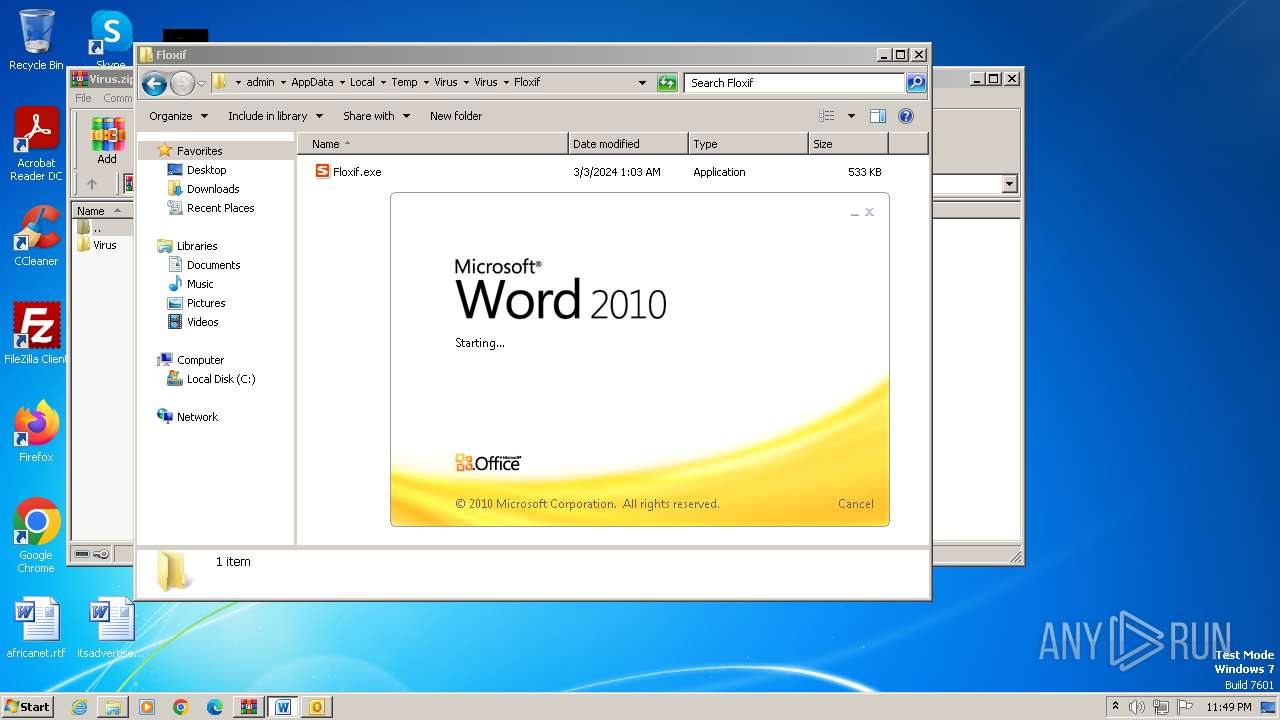
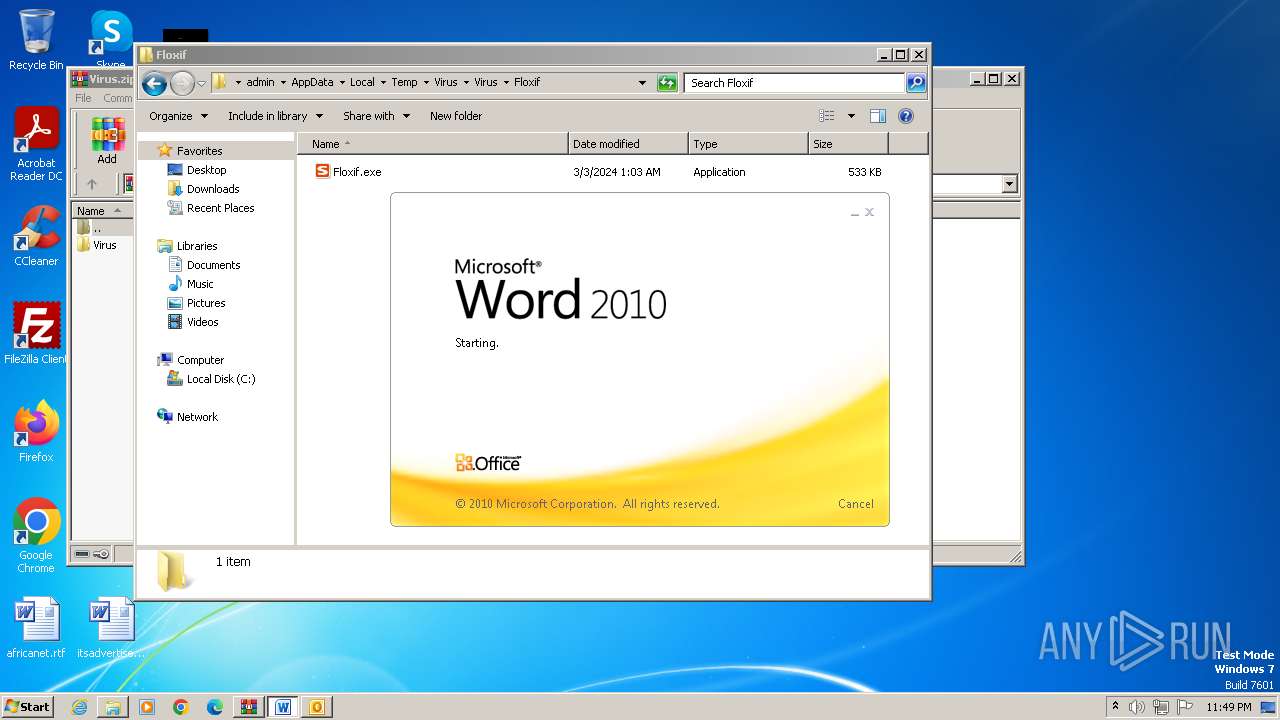
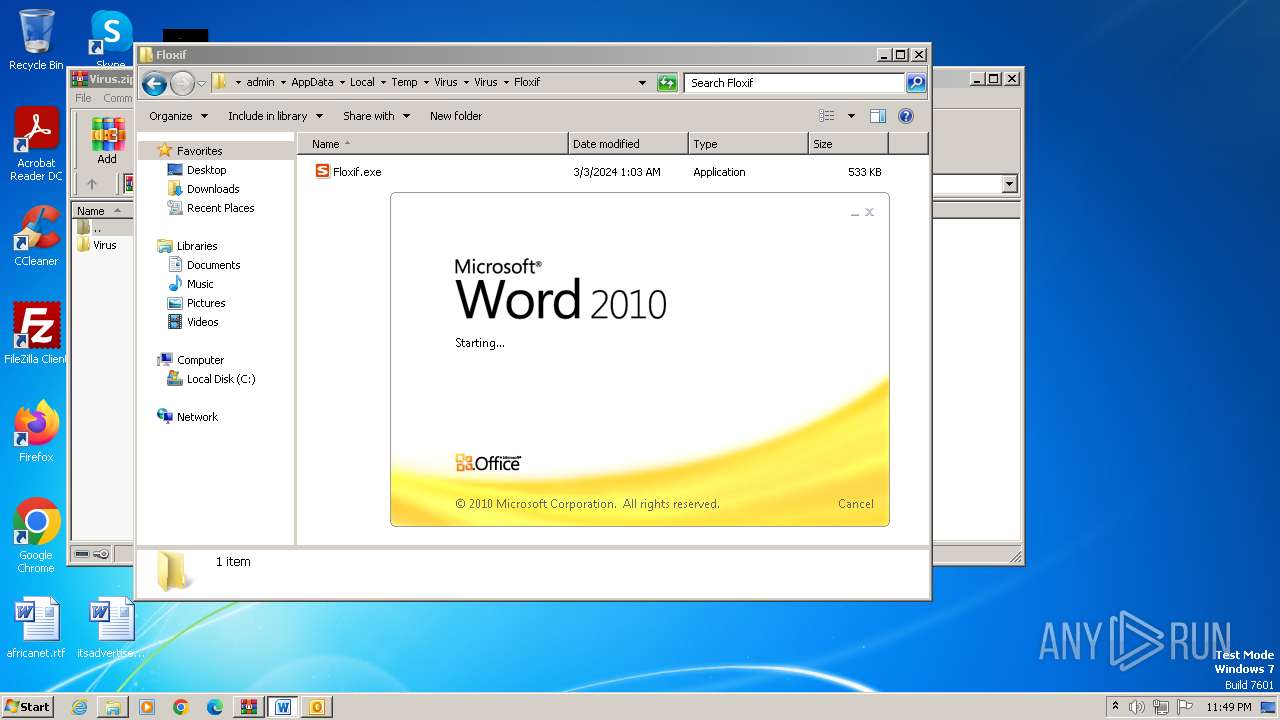
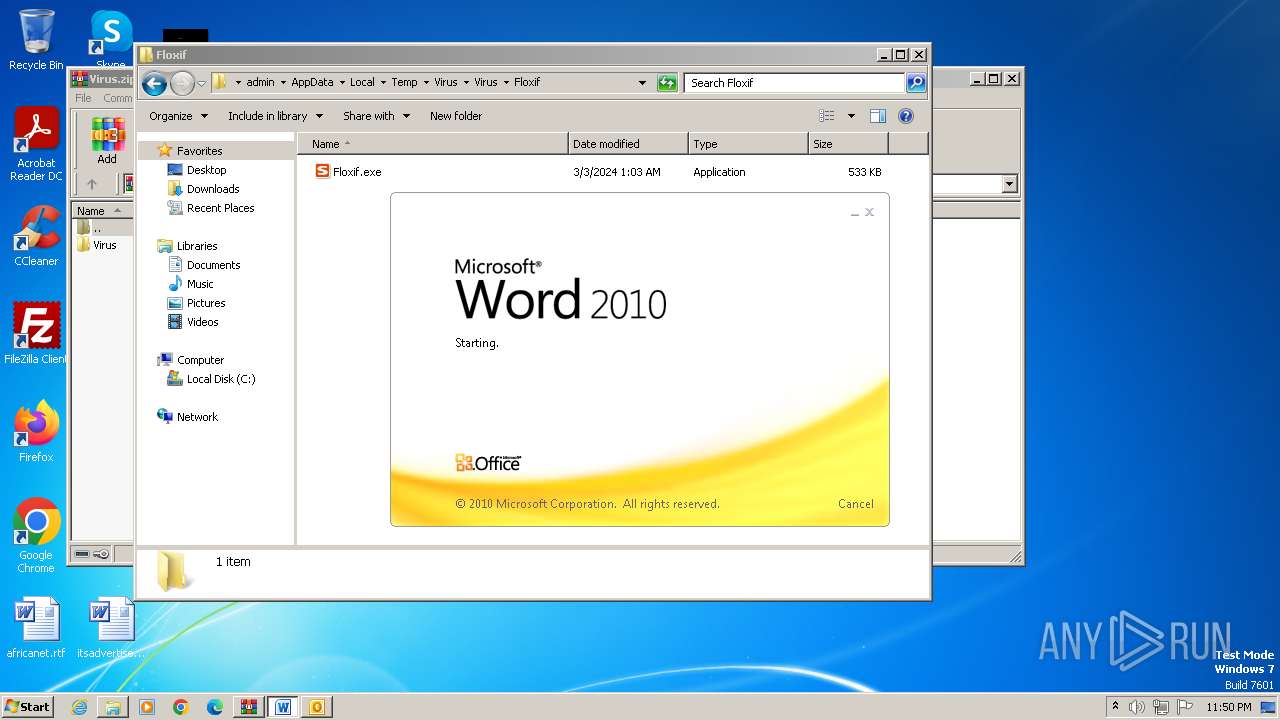
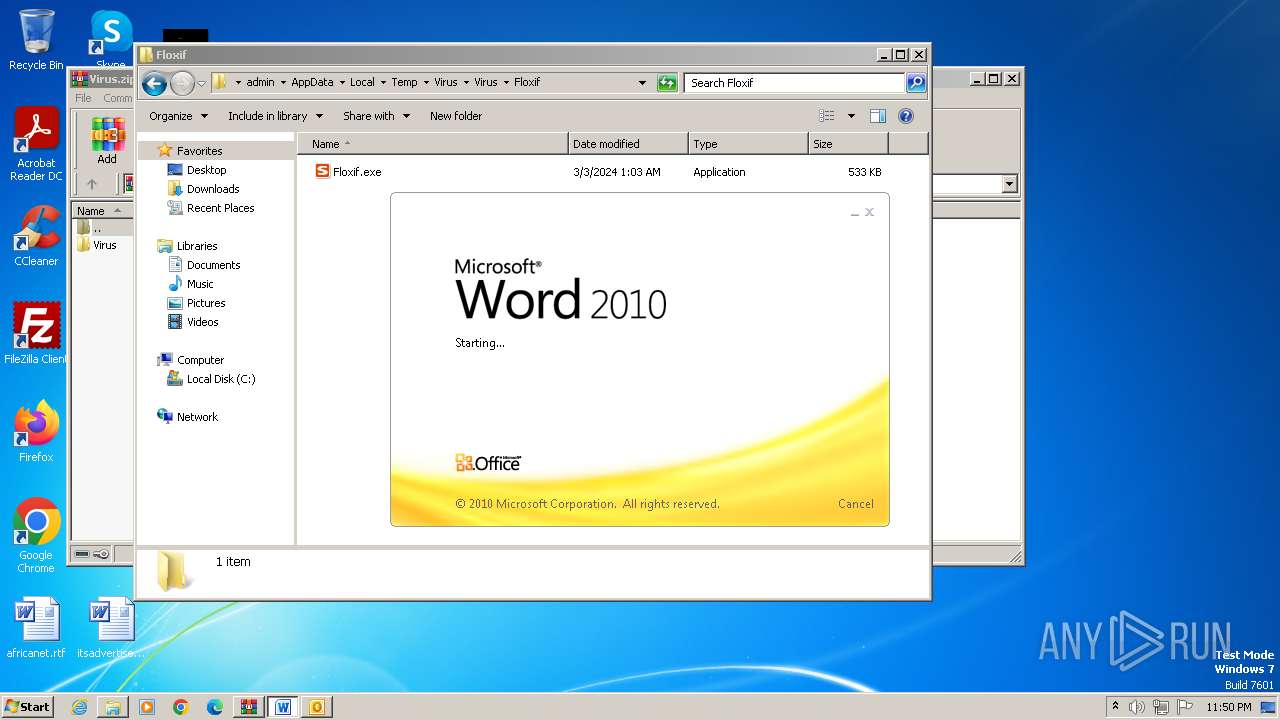
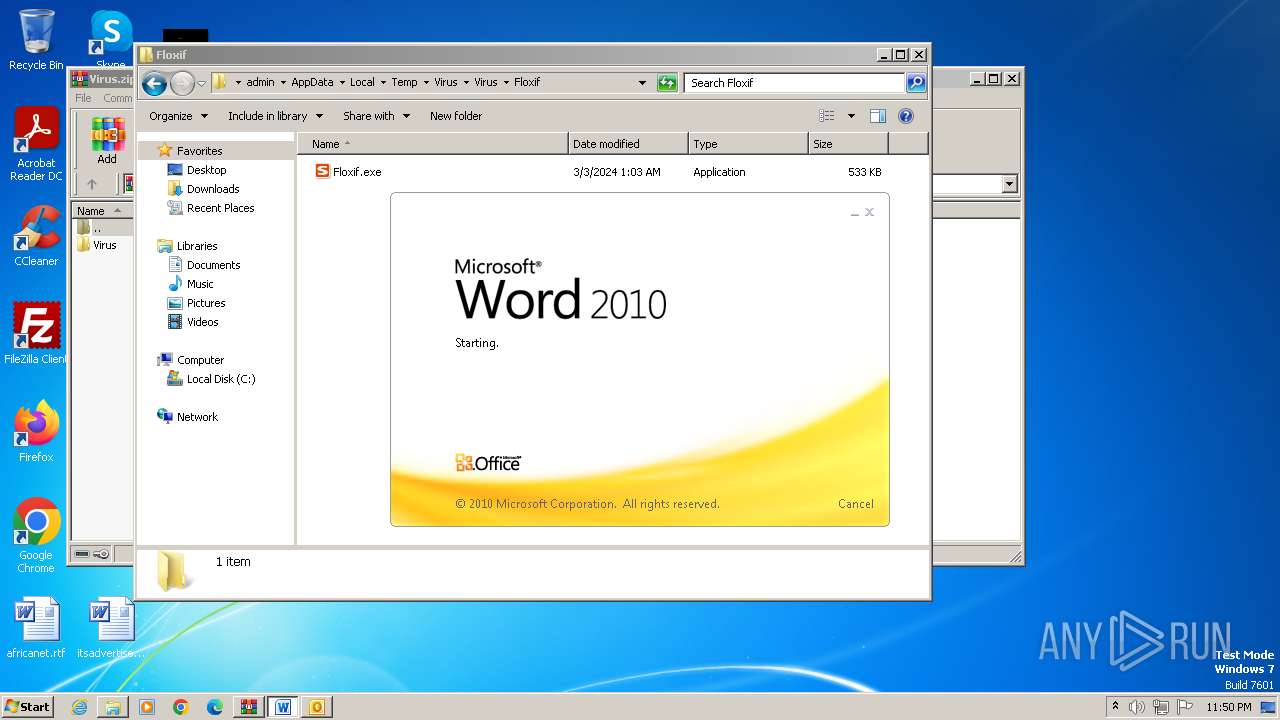
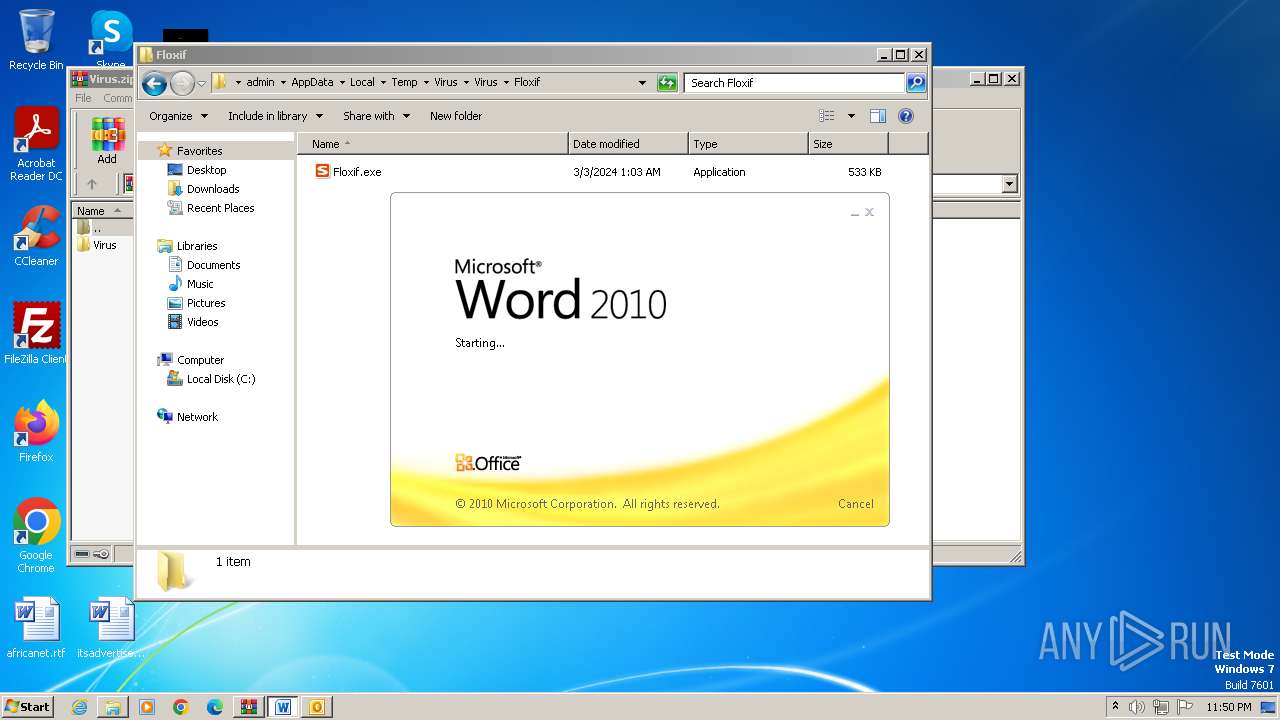
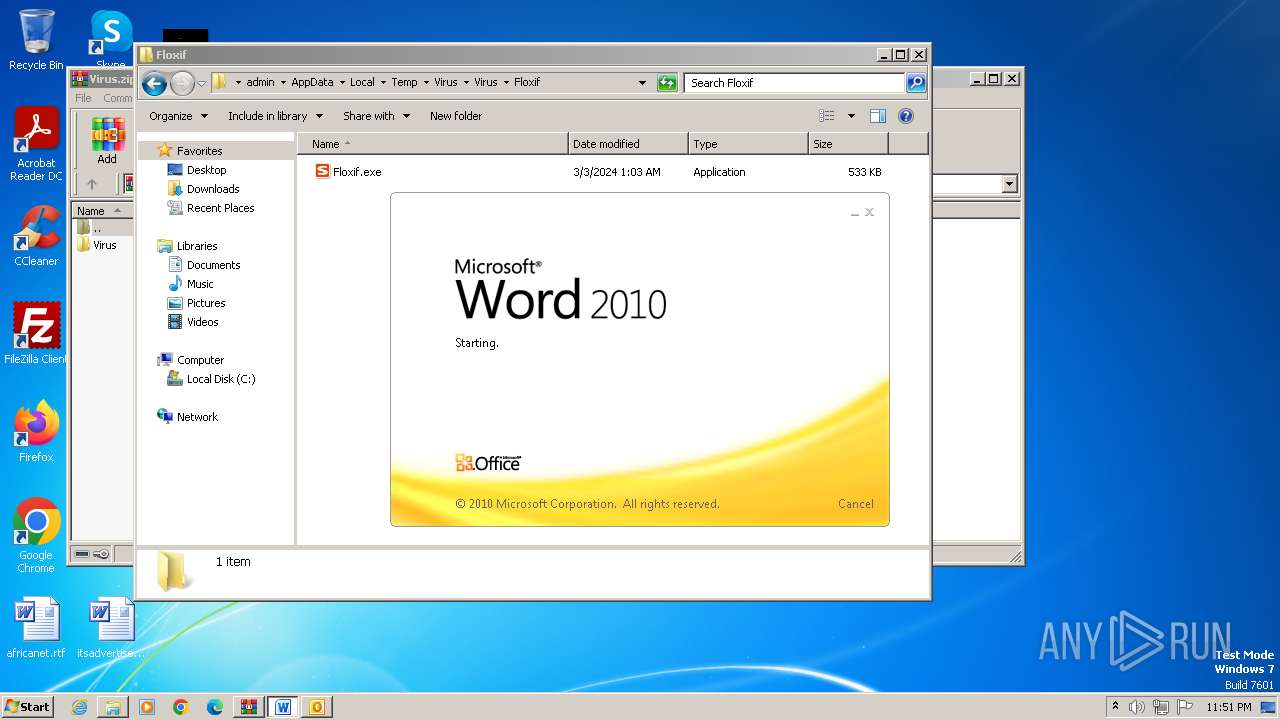
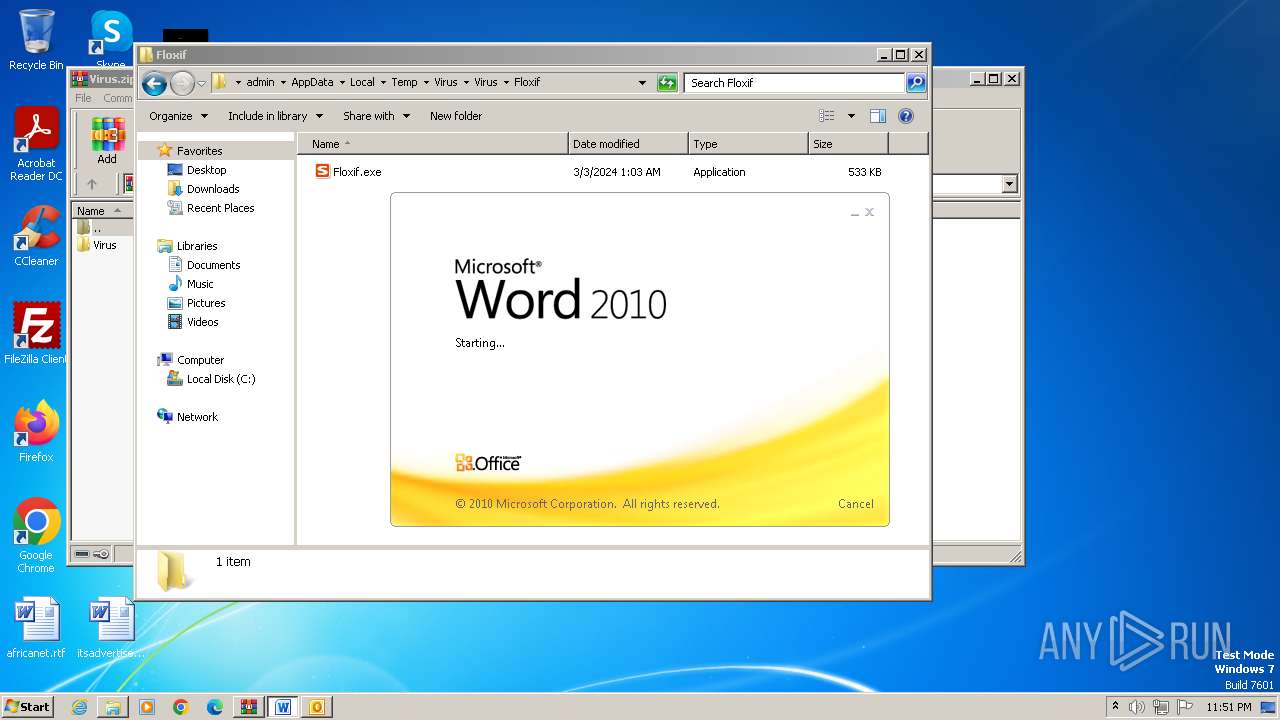
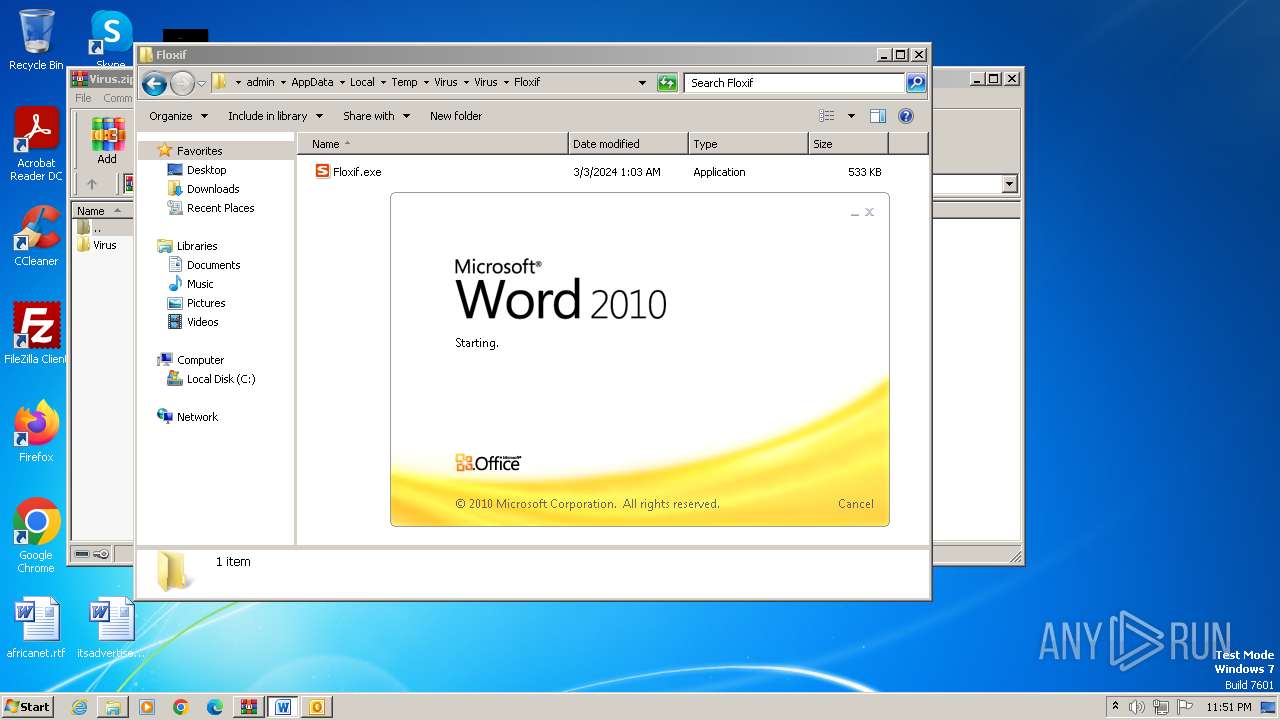
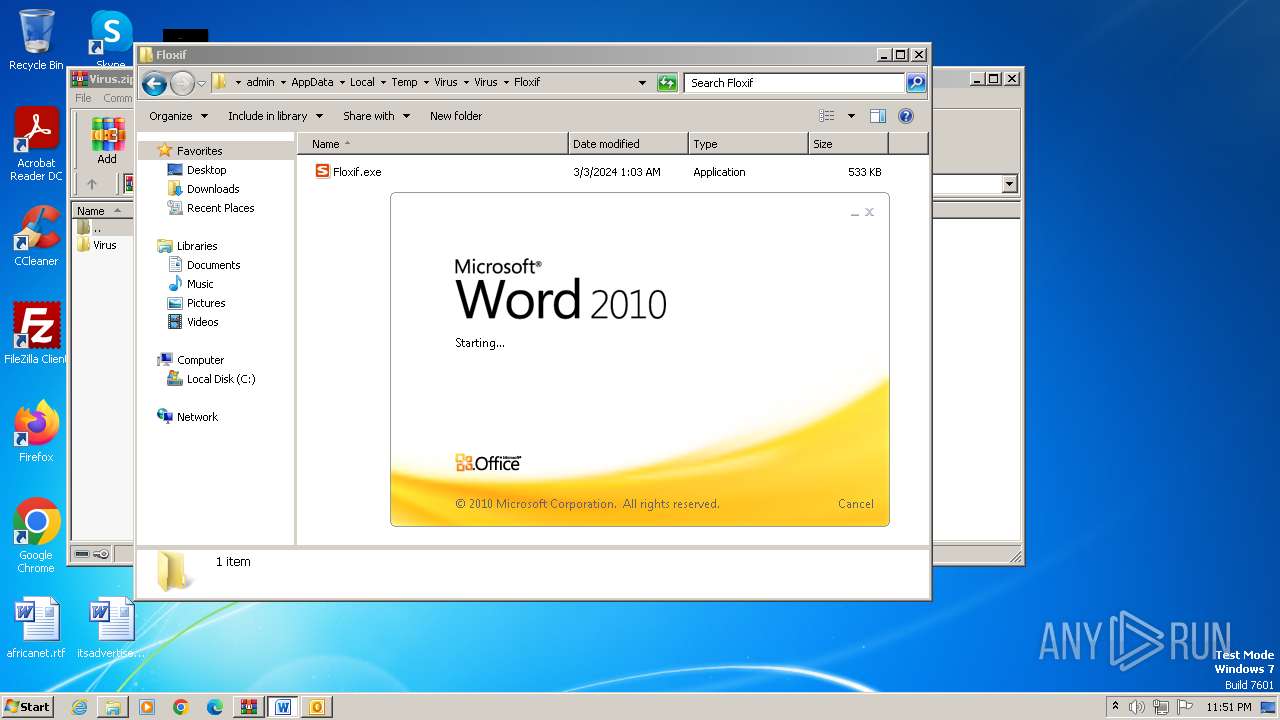
- Floxif.exe (PID: 2548)
Runs injected code in another process
- xpaj.exe (PID: 2564)
Application was injected by another process
- dwm.exe (PID: 612)
Creates a writable file in the system directory
- dllhost.exe (PID: 2240)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3668)
- Floxif.exe (PID: 2548)
Creates file in the systems drive root
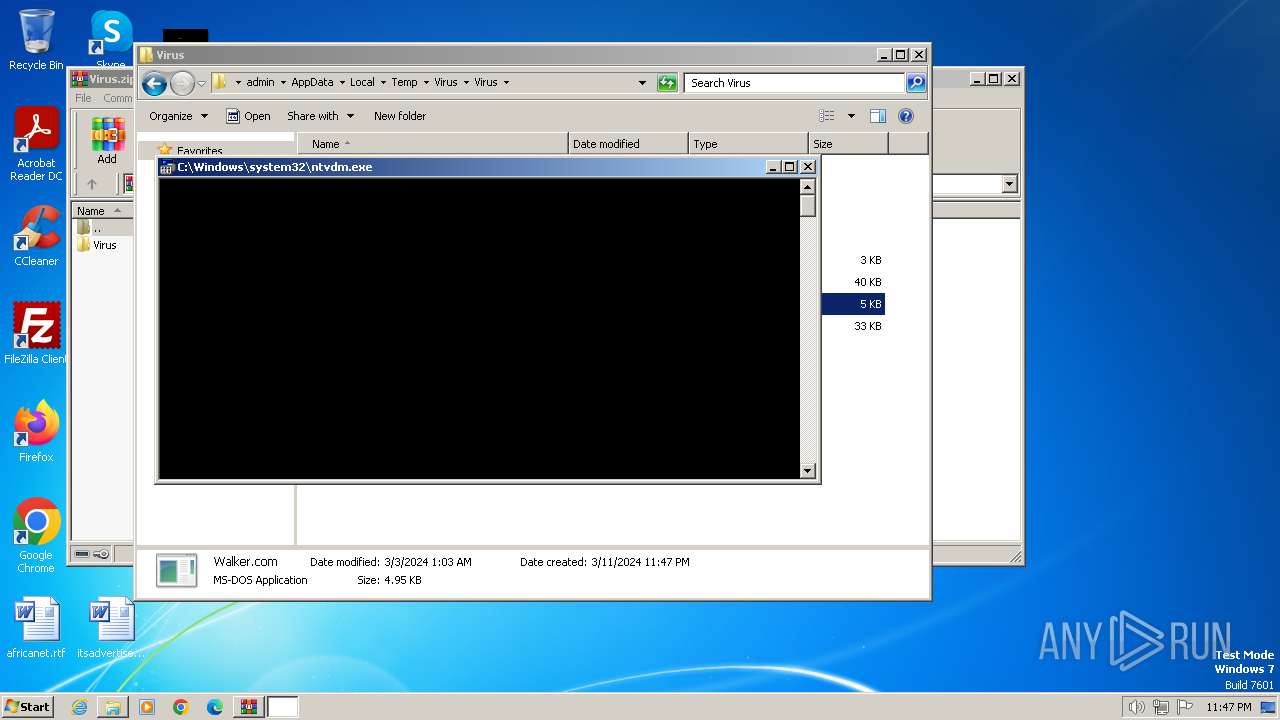
- ntvdm.exe (PID: 3304)
Non-standard symbols in registry
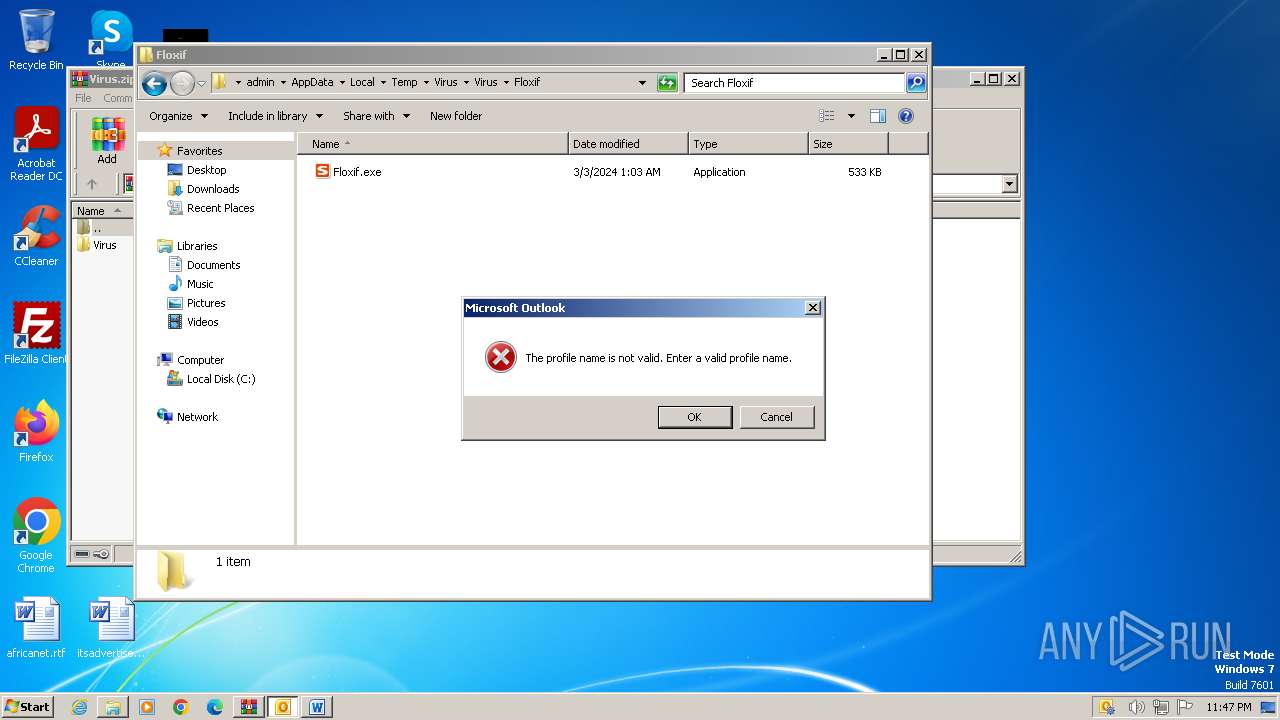
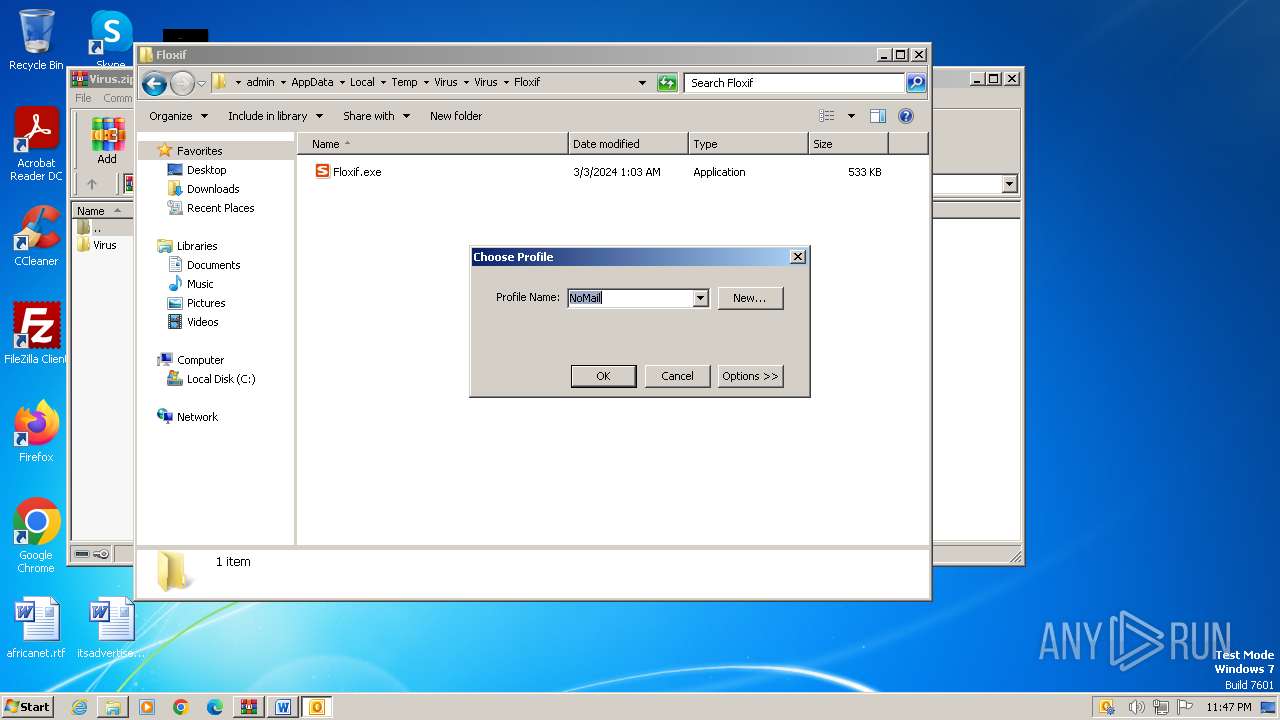
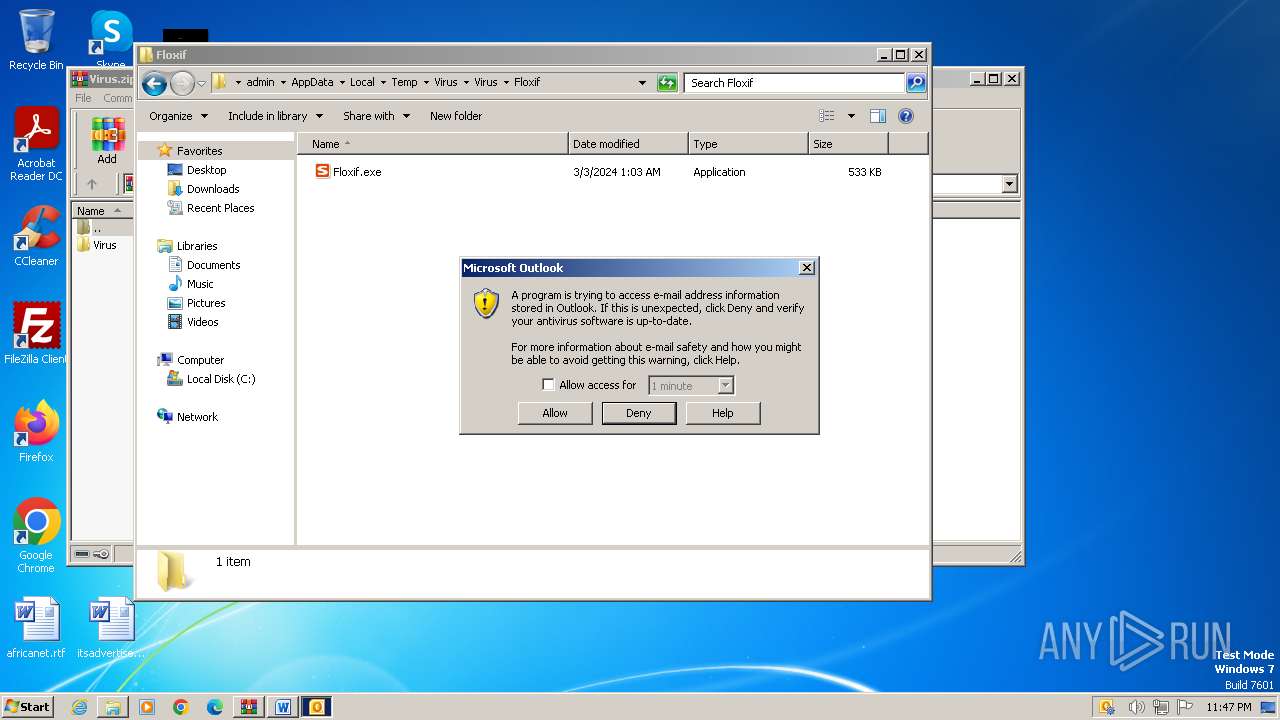
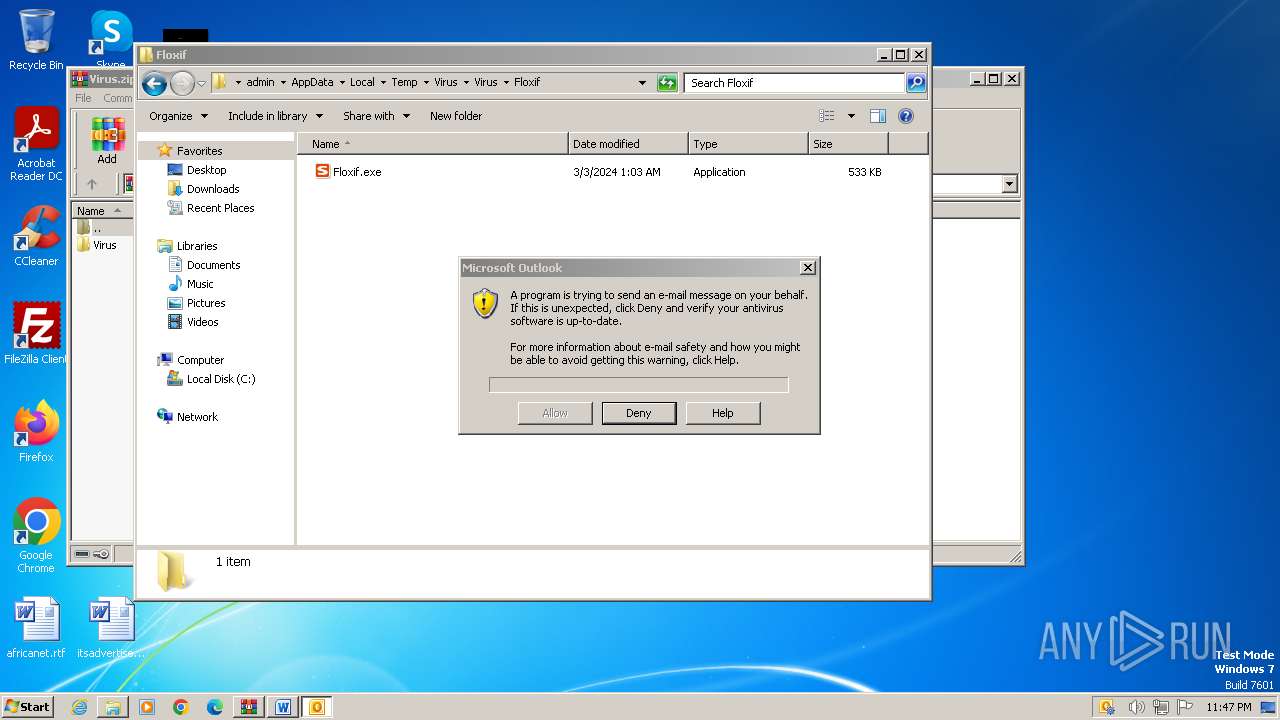
- WINWORD.EXE (PID: 2648)
- OUTLOOK.EXE (PID: 4044)
Executable content was dropped or overwritten
- xpaj.exe (PID: 2564)
- dllhost.exe (PID: 2240)
- xpajB.exe (PID: 1572)
- Floxif.exe (PID: 2548)
Reads the Internet Settings
- dwm.exe (PID: 612)
Starts a Microsoft application from unusual location
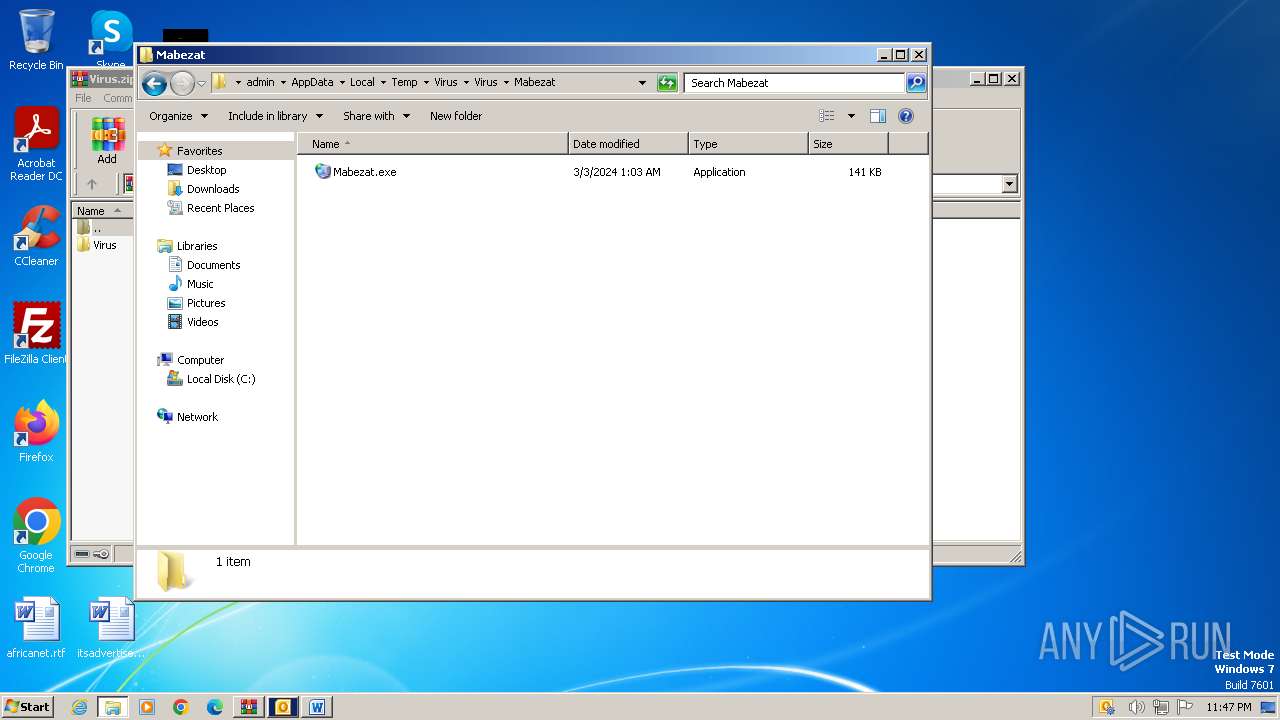
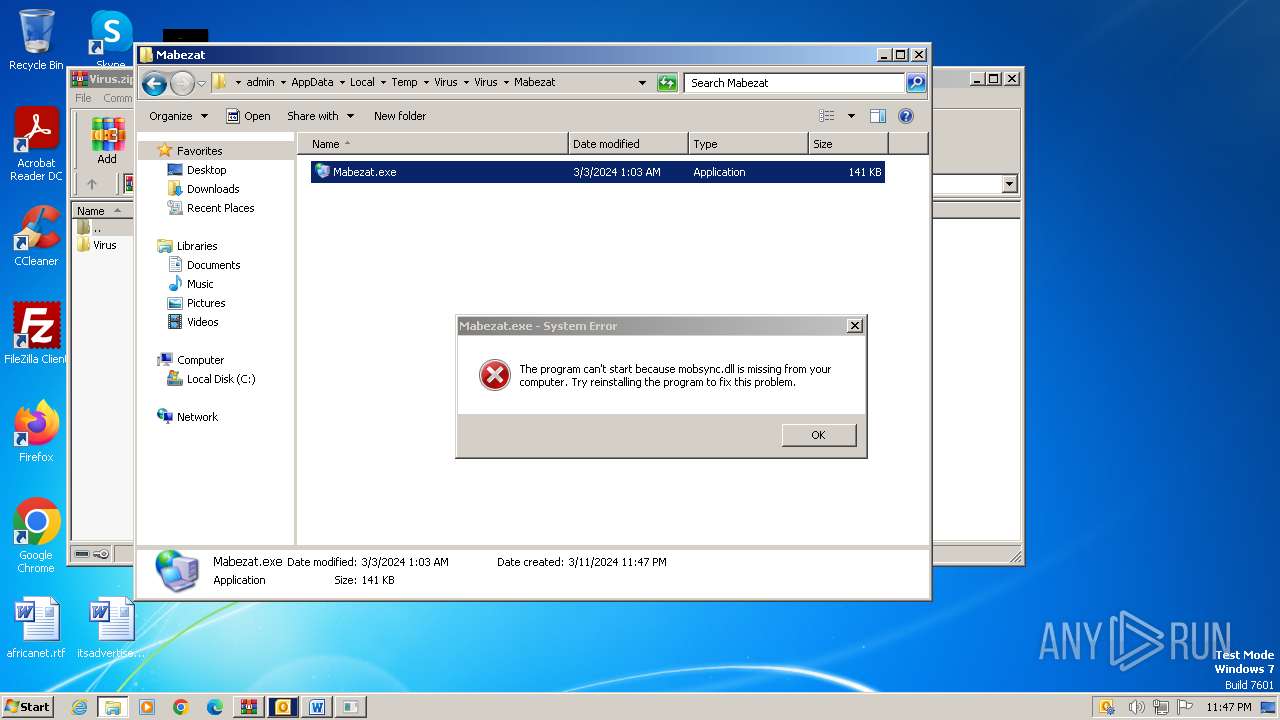
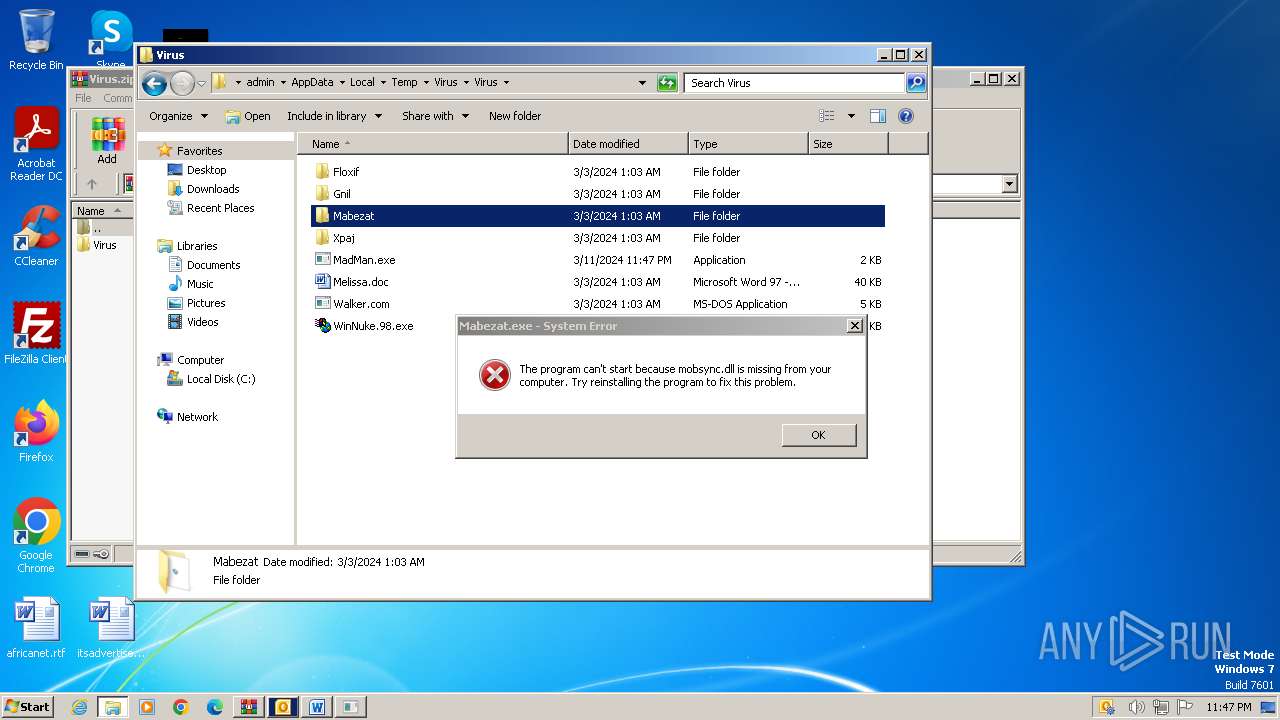
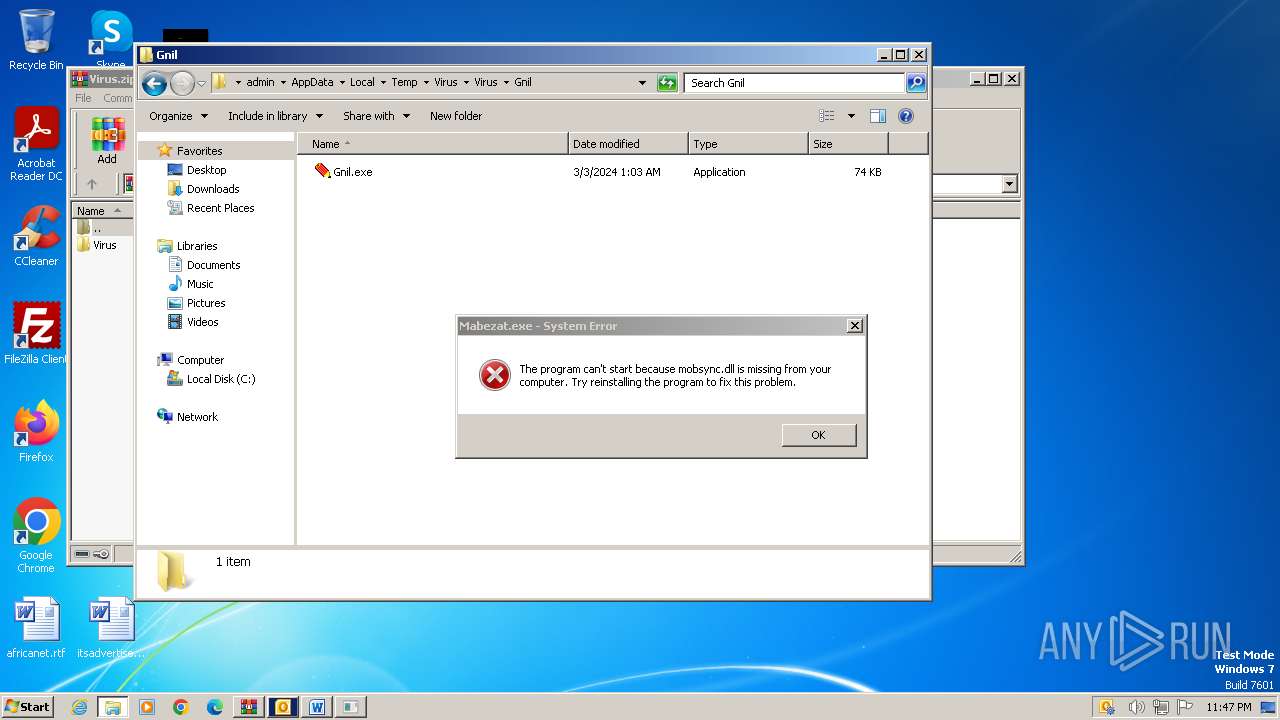
- Mabezat.exe (PID: 2396)
Drops 7-zip archiver for unpacking
- xpajB.exe (PID: 1572)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3668)
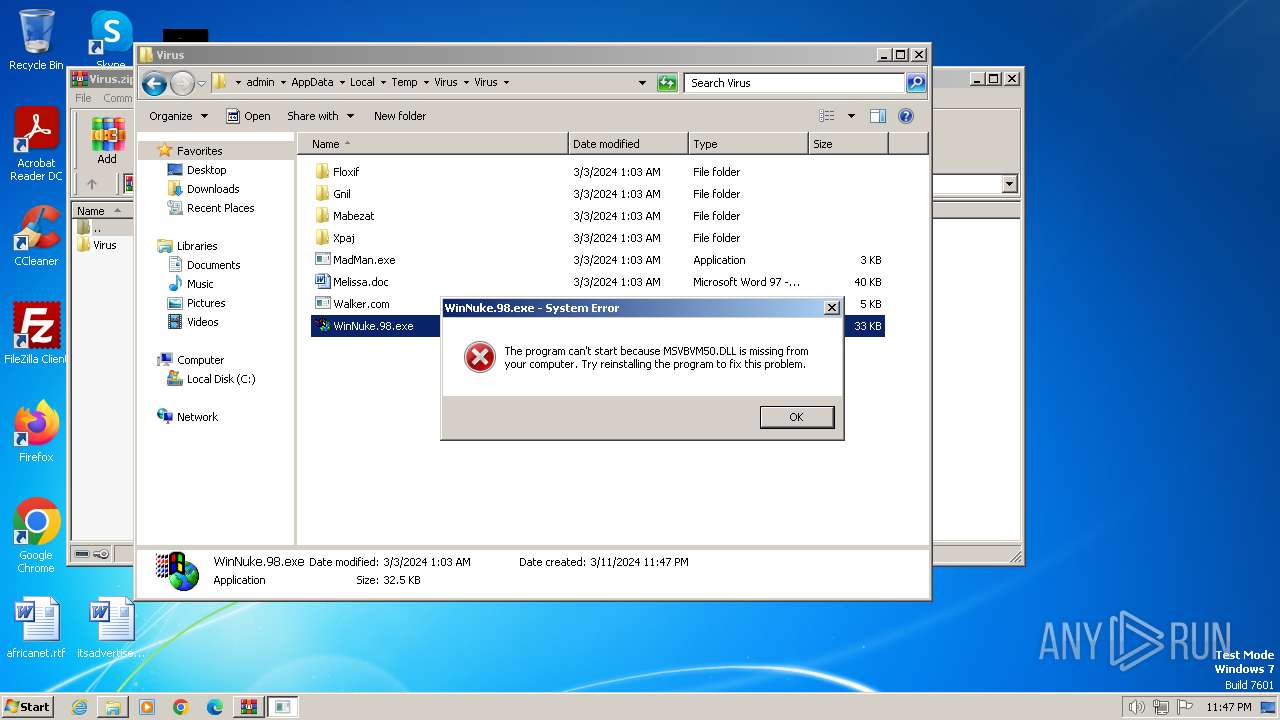
Manual execution by a user
- WinNuke.98.exe (PID: 3464)
- ntvdm.exe (PID: 3992)
- ntvdm.exe (PID: 3304)
- WINWORD.EXE (PID: 2648)
- xpajB.exe (PID: 1572)
- xpaj.exe (PID: 2564)
- Mabezat.exe (PID: 2396)
- Floxif.exe (PID: 2548)
- Gnil.exe (PID: 3352)
- Gnil.exe (PID: 3900)
Create files in a temporary directory
- ntvdm.exe (PID: 3304)
- xpaj.exe (PID: 2564)
- Floxif.exe (PID: 2548)
- xpajB.exe (PID: 1572)
Checks supported languages
- xpajB.exe (PID: 1572)
- xpaj.exe (PID: 2564)
- Gnil.exe (PID: 3352)
- Gnil.exe (PID: 3900)
- Floxif.exe (PID: 2548)
Reads the computer name
- xpajB.exe (PID: 1572)
- xpaj.exe (PID: 2564)
- Floxif.exe (PID: 2548)
Checks transactions between databases Windows and Oracle
- dwm.exe (PID: 612)
Drops the executable file immediately after the start
- dllhost.exe (PID: 2240)
Reads security settings of Internet Explorer
- dwm.exe (PID: 612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 45 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:03:03 01:03:38 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 2 |
| ZipUncompressedSize: | - |
| ZipFileName: | Virus/ |
Total processes
69
Monitored processes
14
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 612 | "C:\Windows\system32\Dwm.exe" | C:\Windows\System32\dwm.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Desktop Window Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1572 | "C:\Users\admin\AppData\Local\Temp\Virus\Virus\Xpaj\xpajB.exe" | C:\Users\admin\AppData\Local\Temp\Virus\Virus\Xpaj\xpajB.exe | explorer.exe | ||||||||||||
User: admin Company: Корпорация Майкрософт Integrity Level: MEDIUM Description: Основная библиотека общего доступа к приложениям Exit code: 0 Version: 5.1.2600.5512 Modules
| |||||||||||||||
| 2240 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\System32\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2396 | "C:\Users\admin\AppData\Local\Temp\Virus\Virus\Mabezat\Mabezat.exe" | C:\Users\admin\AppData\Local\Temp\Virus\Virus\Mabezat\Mabezat.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Synchronisatiebeheer Exit code: 3221225781 Version: 5.1.2600.5512 (xpsp.080413-2108) Modules
| |||||||||||||||
| 2548 | "C:\Users\admin\AppData\Local\Temp\Virus\Virus\Floxif\Floxif.exe" | C:\Users\admin\AppData\Local\Temp\Virus\Virus\Floxif\Floxif.exe | explorer.exe | ||||||||||||
User: admin Company: Sogou.com Inc. Integrity Level: MEDIUM Description: 搜狗下载器 Exit code: 3221225477 Version: 6.7.0.0329 Modules
| |||||||||||||||
| 2564 | "C:\Users\admin\AppData\Local\Temp\Virus\Virus\Xpaj\xpaj.exe" | C:\Users\admin\AppData\Local\Temp\Virus\Virus\Xpaj\xpaj.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2648 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Virus\Virus\Melissa.doc" | C:\Program Files\microsoft office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3304 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\System32\ntvdm.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3352 | "C:\Users\admin\AppData\Local\Temp\Virus\Virus\Gnil\Gnil.exe" | C:\Users\admin\AppData\Local\Temp\Virus\Virus\Gnil\Gnil.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3464 | "C:\Users\admin\AppData\Local\Temp\Virus\Virus\WinNuke.98.exe" | C:\Users\admin\AppData\Local\Temp\Virus\Virus\WinNuke.98.exe | — | explorer.exe | |||||||||||
User: admin Company: Ksc-Wimol Internet Branch Integrity Level: MEDIUM Exit code: 3221225781 Version: 1.00 Modules
| |||||||||||||||
Total events
18 560
Read events
18 176
Write events
219
Delete events
165
Modification events
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Virus.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
14
Suspicious files
8
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2648 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR7D0B.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 4044 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR8344.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Virus\Virus\MadMan.exe | executable | |
MD5:A56D479405B23976F162F3A4A74E48AA | SHA256:17D81134A5957FB758B9D69A90B033477A991C8B0F107D9864DC790CA37E6A23 | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Virus\Virus\Melissa.doc | document | |
MD5:4B68FDEC8E89B3983CEB5190A2924003 | SHA256:554701BC874DA646285689DF79E5002B3B1A1F76DAF705BEA9586640026697CA | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Virus\Virus\Xpaj\xpajB.exe | executable | |
MD5:BD76FC01DEED43CD6E368A1F860D44ED | SHA256:E04C85CD4BFFA1F5465FF62C9BAF0B29B7B2FADDF7362789013FBAC8C90268BF | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Virus\Virus\WinNuke.98.exe | executable | |
MD5:EB9324121994E5E41F1738B5AF8944B1 | SHA256:2F1F93EDE80502D153E301BAF9B7F68E7C7A9344CFA90CFAE396AAC17E81CE5A | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Virus\Virus\Gnil\Gnil.exe | executable | |
MD5:37E887B7A048DDB9013C8D2A26D5B740 | SHA256:24C0638FF7571C7F4DF5BCDDD50BC478195823E934481FA3EE96EB1D1C4B4A1B | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Virus\Virus\Xpaj\xpaj.exe | executable | |
MD5:D5C12FCFEEBBE63F74026601CD7F39B2 | SHA256:9DB7EF2D1495DBA921F3084B05D95E418A16F4C5E8DE93738ABEF2479AD5B0DA | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Virus\Virus\Mabezat\Mabezat.exe | executable | |
MD5:DE8D08A3018DFE8FD04ED525D30BB612 | SHA256:2AE0C4A5F1FEDF964E2F8A486BF0EE5D1816AAC30C889458A9AC113D13B50CEB | |||
| 2648 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Virus\Virus\~$elissa.doc | pgc | |
MD5:F9CA7FE85A8568D8792BA2C0D338F2A6 | SHA256:CC578B5A8DDE8E42A0BAC10EC0BE6389D10B071B811C4B0ED9685555D5B0EB80 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
5
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4044 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
nortiniolosto.com |
| unknown |
infoserv52.com |
| unknown |
config.messenger.msn.com |
| whitelisted |