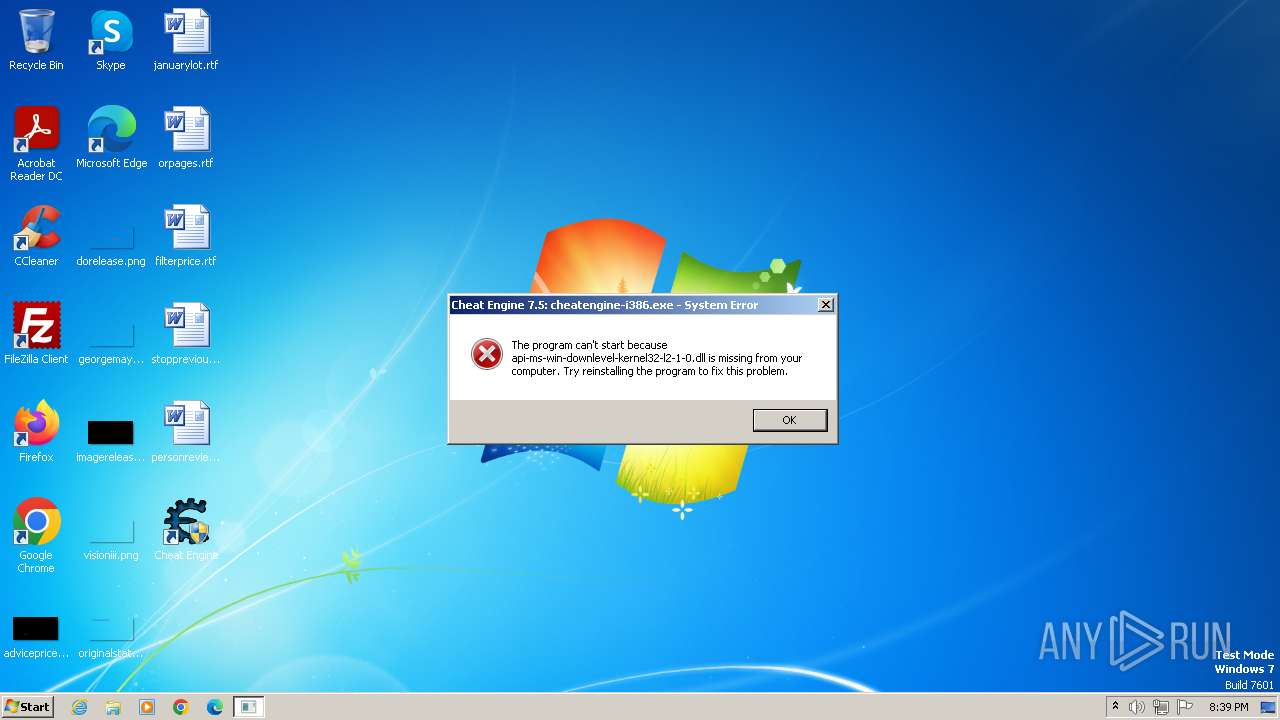
| File name: | CheatEngine75.exe |
| Full analysis: | https://app.any.run/tasks/a825ca68-b8c1-43b3-aae5-b0bd6539f517 |
| Verdict: | Malicious activity |
| Analysis date: | November 09, 2023, 20:38:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 96D1196BD8E52D9889656B2960A27E5B |
| SHA1: | 75B17106B9AA54CCEA7583C8339B81993F27E69E |
| SHA256: | 75F32AB1A2E666CA53D9D8E3D9D6D7E64EE068AA92AF66BDD1E4F6527E83E1EC |
| SSDEEP: | 98304:p+cD4dn4FEEnnT/6wIIeFEEnnT/6wIIeFEEnnT/6wIIDO7UClKtIu/uuf+EE2nuG:i/U |
MALICIOUS
Drops the executable file immediately after the start
- CheatEngine75.exe (PID: 3128)
- CheatEngine75.exe (PID: 3572)
- CheatEngine75.tmp (PID: 3464)
- CheatEngine75.exe (PID: 3664)
- CheatEngine75.tmp (PID: 3656)
Starts NET.EXE for service management
- net.exe (PID: 3640)
- CheatEngine75.tmp (PID: 3656)
- net.exe (PID: 3828)
SUSPICIOUS
Reads the Windows owner or organization settings
- CheatEngine75.tmp (PID: 3464)
- CheatEngine75.tmp (PID: 3656)
Reads settings of System Certificates
- CheatEngine75.tmp (PID: 3464)
Reads the Internet Settings
- CheatEngine75.tmp (PID: 3464)
- Cheat Engine.exe (PID: 3712)
Uses ICACLS.EXE to modify access control lists
- CheatEngine75.tmp (PID: 3656)
Starts SC.EXE for service management
- CheatEngine75.tmp (PID: 3656)
Process drops legitimate windows executable
- CheatEngine75.tmp (PID: 3656)
Process drops SQLite DLL files
- CheatEngine75.tmp (PID: 3656)
INFO
Reads the computer name
- CheatEngine75.tmp (PID: 3432)
- CheatEngine75.tmp (PID: 3464)
- wmpnscfg.exe (PID: 3276)
- CheatEngine75.tmp (PID: 3656)
- Kernelmoduleunloader.exe (PID: 4000)
- Cheat Engine.exe (PID: 3712)
- cheatengine-i386.exe (PID: 3708)
Checks supported languages
- CheatEngine75.exe (PID: 3128)
- CheatEngine75.tmp (PID: 3432)
- CheatEngine75.exe (PID: 3572)
- CheatEngine75.tmp (PID: 3464)
- wmpnscfg.exe (PID: 3276)
- CheatEngine75.exe (PID: 3664)
- CheatEngine75.tmp (PID: 3656)
- Kernelmoduleunloader.exe (PID: 4000)
- cheatengine-i386.exe (PID: 3708)
- windowsrepair.exe (PID: 2064)
- Cheat Engine.exe (PID: 3712)
Create files in a temporary directory
- CheatEngine75.exe (PID: 3128)
- CheatEngine75.exe (PID: 3572)
- CheatEngine75.tmp (PID: 3464)
- CheatEngine75.exe (PID: 3664)
Reads the machine GUID from the registry
- CheatEngine75.tmp (PID: 3464)
- wmpnscfg.exe (PID: 3276)
Manual execution by a user
- wmpnscfg.exe (PID: 3276)
Creates files in the program directory
- CheatEngine75.tmp (PID: 3656)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 15:54:16+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 89600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.5.0.0 |
| ProductVersionNumber: | 7.5.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | EngineGame Installer |
| FileVersion: | 7.5.0 |
| LegalCopyright: | © EngineGame |
| OriginalFileName: | |
| ProductName: | EngineGame |
| ProductVersion: | 7.5.0 |
Total processes
62
Monitored processes
19
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2064 | "C:\Program Files\Cheat Engine 7.5\windowsrepair.exe" /s | C:\Program Files\Cheat Engine 7.5\windowsrepair.exe | — | CheatEngine75.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3128 | "C:\Users\admin\AppData\Local\Temp\CheatEngine75.exe" | C:\Users\admin\AppData\Local\Temp\CheatEngine75.exe | — | explorer.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: EngineGame Installer Exit code: 0 Version: 7.5.0 Modules
| |||||||||||||||
| 3276 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3432 | "C:\Users\admin\AppData\Local\Temp\is-DVJO7.tmp\CheatEngine75.tmp" /SL5="$60134,2349502,832512,C:\Users\admin\AppData\Local\Temp\CheatEngine75.exe" | C:\Users\admin\AppData\Local\Temp\is-DVJO7.tmp\CheatEngine75.tmp | — | CheatEngine75.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3464 | "C:\Users\admin\AppData\Local\Temp\is-VF2TK.tmp\CheatEngine75.tmp" /SL5="$60186,2349502,832512,C:\Users\admin\AppData\Local\Temp\CheatEngine75.exe" /SPAWNWND=$501F6 /NOTIFYWND=$60134 | C:\Users\admin\AppData\Local\Temp\is-VF2TK.tmp\CheatEngine75.tmp | CheatEngine75.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3572 | "C:\Users\admin\AppData\Local\Temp\CheatEngine75.exe" /SPAWNWND=$501F6 /NOTIFYWND=$60134 | C:\Users\admin\AppData\Local\Temp\CheatEngine75.exe | CheatEngine75.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: EngineGame Installer Exit code: 0 Version: 7.5.0 Modules
| |||||||||||||||
| 3640 | "net" stop BadlionAntic | C:\Windows\System32\net.exe | — | CheatEngine75.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3656 | "C:\Users\admin\AppData\Local\Temp\is-6GR09.tmp\CheatEngine75.tmp" /SL5="$5012E,26511452,832512,C:\Users\admin\AppData\Local\Temp\is-V1JNR.tmp\CheatEngine75.exe" /VERYSILENT /ZBDIST | C:\Users\admin\AppData\Local\Temp\is-6GR09.tmp\CheatEngine75.tmp | — | CheatEngine75.exe | |||||||||||
User: admin Company: Cheat Engine Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3664 | "C:\Users\admin\AppData\Local\Temp\is-V1JNR.tmp\CheatEngine75.exe" /VERYSILENT /ZBDIST | C:\Users\admin\AppData\Local\Temp\is-V1JNR.tmp\CheatEngine75.exe | — | CheatEngine75.tmp | |||||||||||
User: admin Company: Cheat Engine Integrity Level: HIGH Description: Cheat Engine Setup Exit code: 0 Version: 7.5.0.0 Modules
| |||||||||||||||
| 3708 | "C:\Program Files\Cheat Engine 7.5\cheatengine-i386.exe" | C:\Program Files\Cheat Engine 7.5\cheatengine-i386.exe | Cheat Engine.exe | ||||||||||||
User: admin Company: Cheat Engine Integrity Level: HIGH Description: Cheat Engine Exit code: 217 Version: 7.5.0.7431 Modules
| |||||||||||||||
Total events
4 702
Read events
4 668
Write events
21
Delete events
13
Modification events
| (PID) Process: | (3464) CheatEngine75.tmp | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3276) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{EE9E3BF7-639C-44EB-AFD7-04464A230674}\{A4C3288F-F643-4DA3-BF1F-77DB0A60E821} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3276) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{EE9E3BF7-639C-44EB-AFD7-04464A230674} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3276) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{5D4F4A2A-30C8-41EB-BCF5-2605B03DAE02} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3656) CheatEngine75.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 115 | |||
| (PID) Process: | (3656) CheatEngine75.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0001 |
| Operation: | delete value | Name: | RegFilesHash |
Value: 794C2E694FD8D565C39FDB202EF0116769A417C7F3EBCC764A3D86DE2291BC05 | |||
| (PID) Process: | (3656) CheatEngine75.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0001 |
| Operation: | delete value | Name: | RegFiles0000 |
Value: C:\Program Files\Cheat Engine 7.5\windowsrepair.exe | |||
| (PID) Process: | (3656) CheatEngine75.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0001 |
| Operation: | delete value | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3656) CheatEngine75.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0001 |
| Operation: | delete value | Name: | SessionHash |
Value: 21DF20EB95504191076B554619EE3029A7DE8274CBD04A907F22F414F609E446 | |||
| (PID) Process: | (3656) CheatEngine75.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0001 |
| Operation: | delete value | Name: | Owner |
Value: 480E0000E060E7C84C13DA01 | |||
Executable files
124
Suspicious files
44
Text files
430
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3128 | CheatEngine75.exe | C:\Users\admin\AppData\Local\Temp\is-DVJO7.tmp\CheatEngine75.tmp | executable | |
MD5:2DBB23C62848635C596FA85BA7DEE128 | SHA256:296DF81AD382686280652E45750AB5D9C0C35D4B308265FE5FF039017B7345A3 | |||
| 3656 | CheatEngine75.tmp | C:\Program Files\Cheat Engine 7.5\unins000.exe | executable | |
MD5:9AA2ACD4C96F8BA03BB6C3EA806D806F | SHA256:1B81562FDAEAA1BC22CBAA15C92BAB90A12080519916CFA30C843796021153BB | |||
| 3464 | CheatEngine75.tmp | C:\Users\admin\AppData\Local\Temp\is-V1JNR.tmp\finish.png | image | |
MD5:6B7CB2A5A8B301C788C3792802696FE8 | SHA256:3EED2E41BC6CA0AE9A5D5EE6D57CA727E5CBA6AC8E8C5234AC661F9080CEDADF | |||
| 3656 | CheatEngine75.tmp | C:\Program Files\Cheat Engine 7.5\Cheat Engine.exe | executable | |
MD5:F921416197C2AE407D53BA5712C3930A | SHA256:E31B233DDF070798CC0381CC6285F6F79EA0C17B99737F7547618DCFD36CDC0E | |||
| 3464 | CheatEngine75.tmp | C:\Users\admin\AppData\Local\Temp\is-V1JNR.tmp\error.png | image | |
MD5:6B7CB2A5A8B301C788C3792802696FE8 | SHA256:3EED2E41BC6CA0AE9A5D5EE6D57CA727E5CBA6AC8E8C5234AC661F9080CEDADF | |||
| 3464 | CheatEngine75.tmp | C:\Users\admin\AppData\Local\Temp\is-V1JNR.tmp\logo.png | image | |
MD5:6B7CB2A5A8B301C788C3792802696FE8 | SHA256:3EED2E41BC6CA0AE9A5D5EE6D57CA727E5CBA6AC8E8C5234AC661F9080CEDADF | |||
| 3656 | CheatEngine75.tmp | C:\Program Files\Cheat Engine 7.5\is-6T81N.tmp | executable | |
MD5:9AA2ACD4C96F8BA03BB6C3EA806D806F | SHA256:1B81562FDAEAA1BC22CBAA15C92BAB90A12080519916CFA30C843796021153BB | |||
| 3464 | CheatEngine75.tmp | C:\Users\admin\AppData\Local\Temp\is-V1JNR.tmp\is-0I0U9.tmp | executable | |
MD5:E0F666FE4FF537FB8587CCD215E41E5F | SHA256:F88B0E5A32A395AB9996452D461820679E55C19952EFFE991DEE8FEDEA1968AF | |||
| 3656 | CheatEngine75.tmp | C:\Program Files\Cheat Engine 7.5\windowsrepair.exe | executable | |
MD5:9A4D1B5154194EA0C42EFEBEB73F318F | SHA256:2F3214F799B0F0A2F3955DBDC64C7E7C0E216F1A09D2C1AD5D0A99921782E363 | |||
| 3656 | CheatEngine75.tmp | C:\Program Files\Cheat Engine 7.5\is-DBI9D.tmp | executable | |
MD5:5BE6A65F186CF219FA25BDD261616300 | SHA256:274E91A91A7A520F76C8E854DC42F96484AF2D69277312D861071BDE5A91991C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3464 | CheatEngine75.tmp | 13.32.23.44:443 | d3cored83b0wp2.cloudfront.net | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
d3cored83b0wp2.cloudfront.net |
| unknown |
Threats
Process | Message |
|---|---|
Kernelmoduleunloader.exe | Setup. So do not show messages |
Kernelmoduleunloader.exe | Kernelmodule unloader |
Kernelmoduleunloader.exe | count=0 |
Kernelmoduleunloader.exe | SCManager opened |
Kernelmoduleunloader.exe | attempting to unload |
Kernelmoduleunloader.exe | setup=true |
cheatengine-i386.exe | p3 |