| File name: | e7f605c5820929d2ac13.zip |
| Full analysis: | https://app.any.run/tasks/13014656-4992-4267-a904-b9f5e7dd68d8 |
| Verdict: | Malicious activity |
| Analysis date: | October 30, 2020, 15:21:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | DD1A874F7E60300D9B80C30BD2AA876E |
| SHA1: | B16983CF95DE6A1735D8AE6576D971C43A086DE0 |
| SHA256: | 75E9CDC7351A74C67CA6B242383C856F88B2AC7652425F9FE7CBDDA2F504B9F0 |
| SSDEEP: | 768:C6x2kEy6shOgDM2qO9Eu0LphSxKhx90YaxSs7TXYdQdCEKk:C6xH6qOgwVO9Eu0LpYQ0Y91AWk |
MALICIOUS
Application was dropped or rewritten from another process
- temp2.exe (PID: 2872)
- e7f605c5820929d2ac13728fd85db22c3c2292107cd11120f168f735ca55a5c9.exe (PID: 2512)
- temp1.exe (PID: 3500)
Runs app for hidden code execution
- temp2.exe (PID: 2872)
Changes the autorun value in the registry
- temp1.exe (PID: 3500)
SUSPICIOUS
Executable content was dropped or overwritten
- e7f605c5820929d2ac13728fd85db22c3c2292107cd11120f168f735ca55a5c9.exe (PID: 2512)
Starts CMD.EXE for commands execution
- temp2.exe (PID: 2872)
Creates files in the Windows directory
- e7f605c5820929d2ac13728fd85db22c3c2292107cd11120f168f735ca55a5c9.exe (PID: 2512)
INFO
Manual execution by user
- e7f605c5820929d2ac13728fd85db22c3c2292107cd11120f168f735ca55a5c9.exe (PID: 2512)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:10:30 15:19:19 |
| ZipCRC: | 0x6dfd32ac |
| ZipCompressedSize: | 47093 |
| ZipUncompressedSize: | 70207 |
| ZipFileName: | e7f605c5820929d2ac13728fd85db22c3c2292107cd11120f168f735ca55a5c9.bin |
Total processes
47
Monitored processes
5
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1204 | C:\Windows\system32\cmd.exe | C:\Windows\system32\cmd.exe | — | temp2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2508 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\e7f605c5820929d2ac13.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2512 | "C:\Users\admin\Desktop\e7f605c5820929d2ac13728fd85db22c3c2292107cd11120f168f735ca55a5c9.exe" | C:\Users\admin\Desktop\e7f605c5820929d2ac13728fd85db22c3c2292107cd11120f168f735ca55a5c9.exe | explorer.exe | ||||||||||||
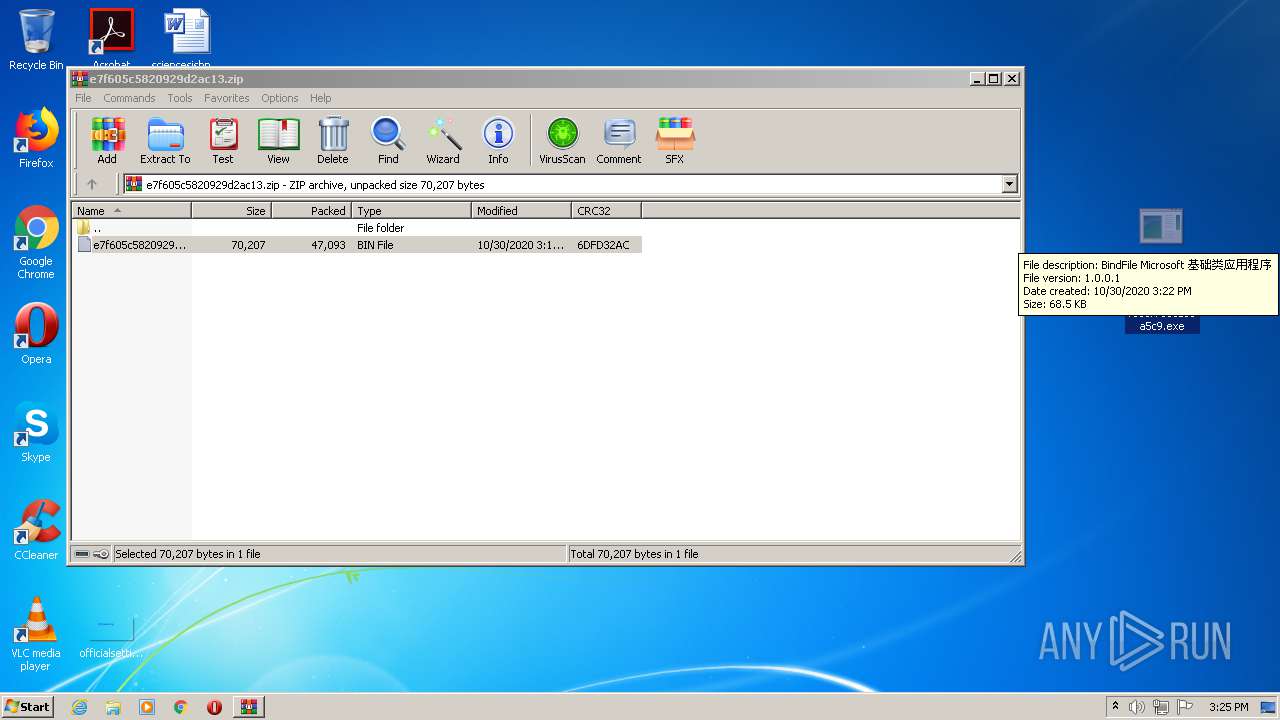
User: admin Integrity Level: HIGH Description: BindFile Microsoft 基础类应用程序 Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2872 | "C:\Windows\system32\temp2.exe" | C:\Windows\system32\temp2.exe | e7f605c5820929d2ac13728fd85db22c3c2292107cd11120f168f735ca55a5c9.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3500 | "C:\Windows\system32\temp1.exe" | C:\Windows\system32\temp1.exe | e7f605c5820929d2ac13728fd85db22c3c2292107cd11120f168f735ca55a5c9.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
330
Read events
320
Write events
10
Delete events
0
Modification events
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\e7f605c5820929d2ac13.zip | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3500) temp1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows |
| Operation: | write | Name: | load |
Value: C:\Windows\svchost.exe | |||
Executable files
2
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2508 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2508.16179\e7f605c5820929d2ac13728fd85db22c3c2292107cd11120f168f735ca55a5c9.bin | — | |
MD5:— | SHA256:— | |||
| 2512 | e7f605c5820929d2ac13728fd85db22c3c2292107cd11120f168f735ca55a5c9.exe | C:\Windows\system32\temp2.exe | executable | |
MD5:6350FAF65F311C04CB4808EA3CAD7CE7 | SHA256:9D21F9E9C4368465AD1B00357D9E8834899563D5952F0157C49DB6D410C25F93 | |||
| 2512 | e7f605c5820929d2ac13728fd85db22c3c2292107cd11120f168f735ca55a5c9.exe | C:\Windows\system32\temp1.exe | executable | |
MD5:A5F8018DF4209AE978B0907CE1664FF2 | SHA256:7DC39A7115F1BED89EFC349B703D2A4D0DE58F2748F3F642262D33ABA0E0191F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
1
Threats
3
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2872 | temp2.exe | 183.236.2.18:8888 | hnmy.3322.org | Guangdong Mobile Communication Co.Ltd. | CN | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
hnmy.3322.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to 3322.org Domain |
2872 | temp2.exe | Generic Protocol Command Decode | SURICATA STREAM suspected RST injection |
2872 | temp2.exe | A Network Trojan was detected | SUSPICIOUS [PTsecurity] Metasploit Server Response |