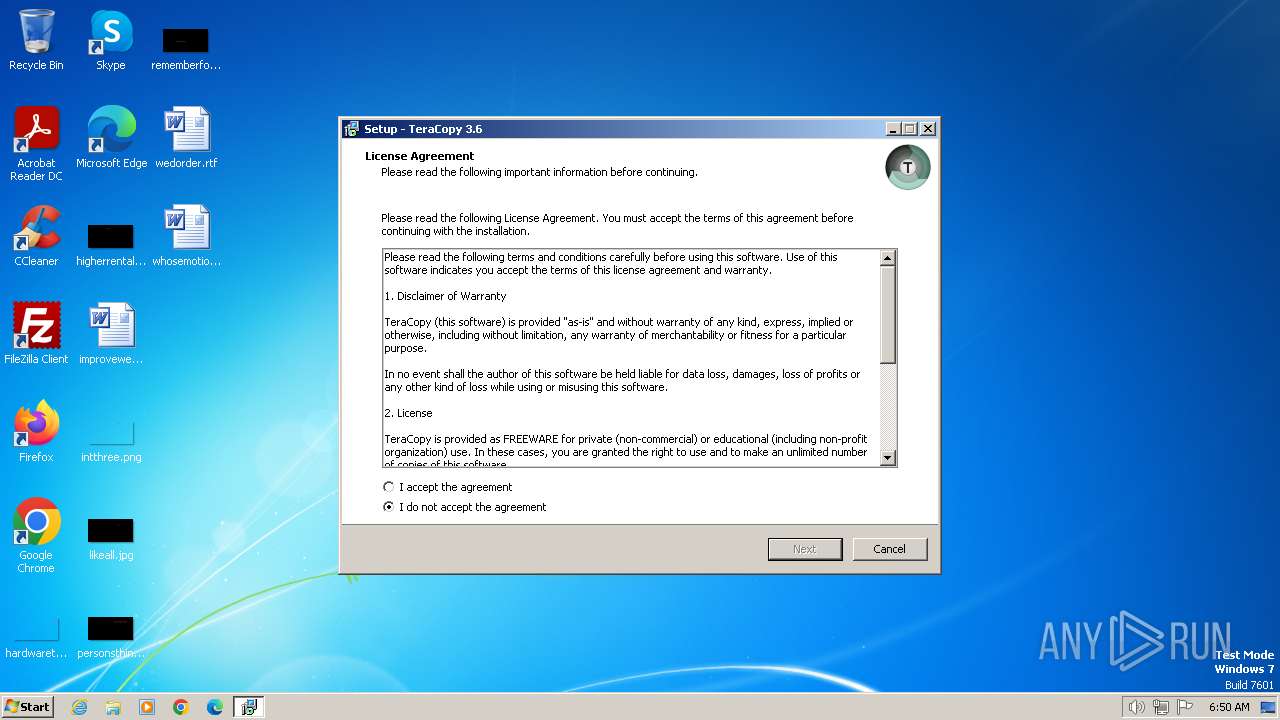
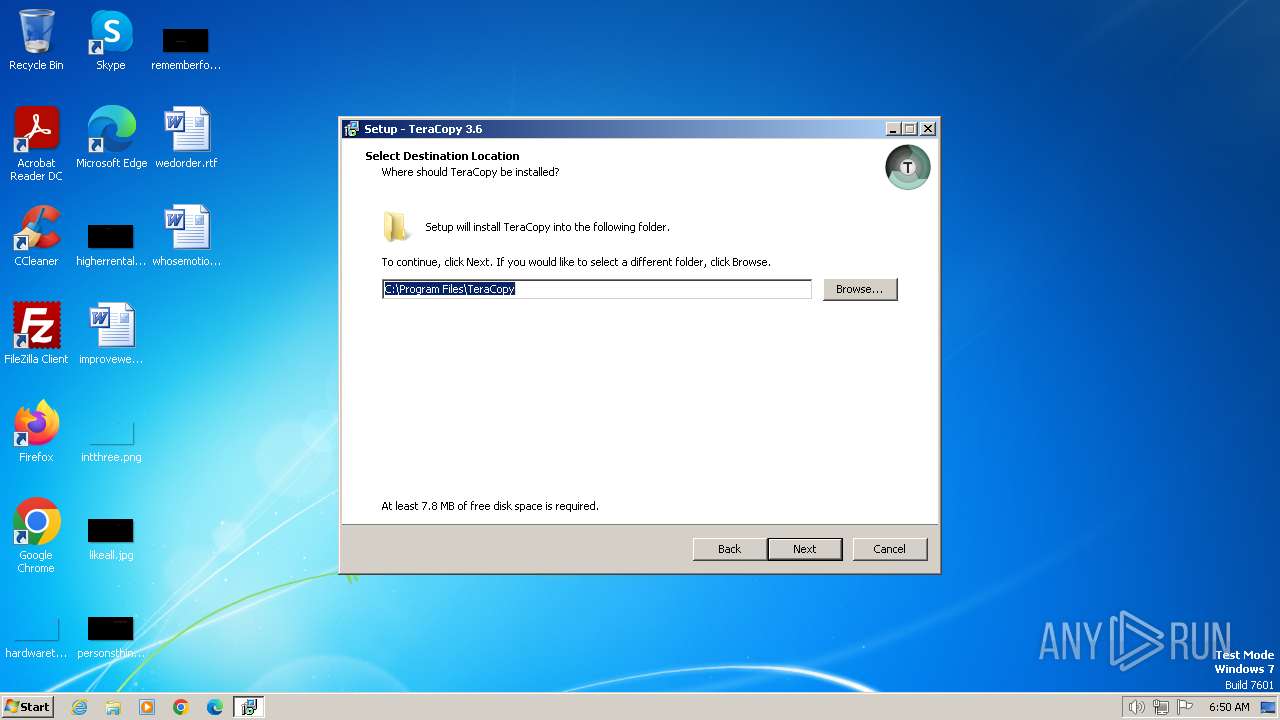
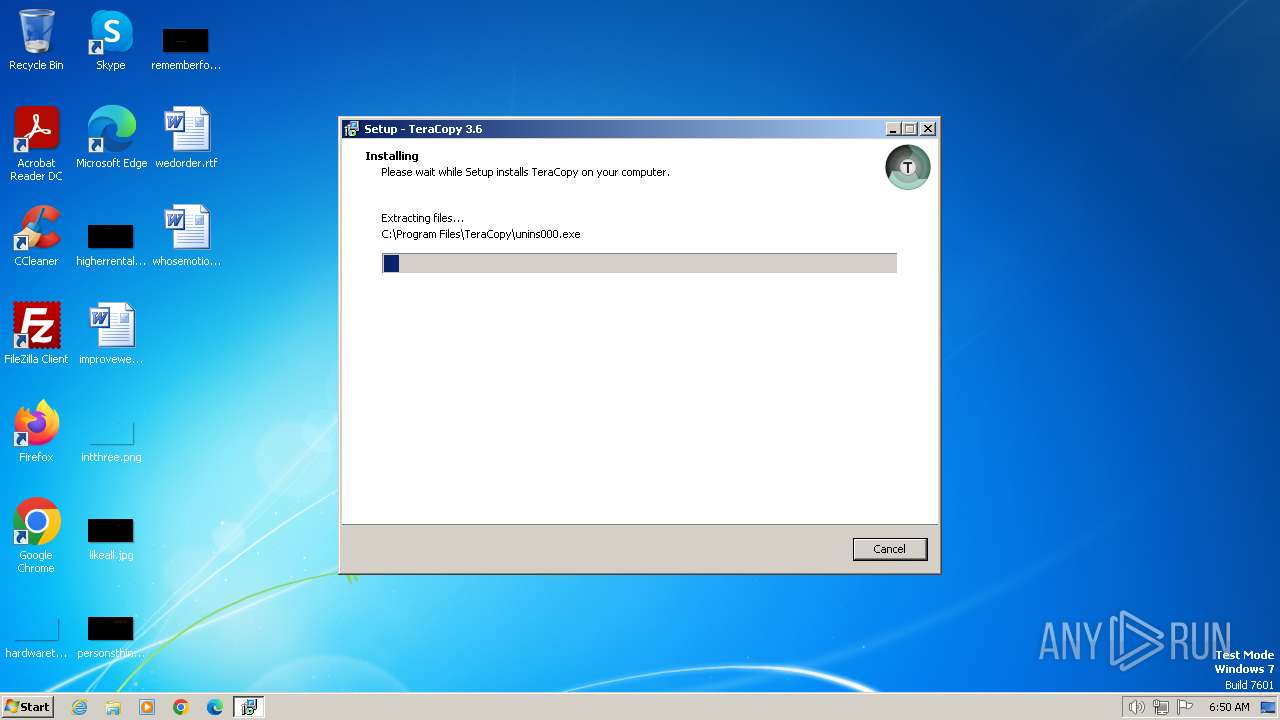
| File name: | teracopy.exe |
| Full analysis: | https://app.any.run/tasks/be3bcb1c-7c76-4b32-899b-e47f9b31a00d |
| Verdict: | Malicious activity |
| Analysis date: | February 20, 2024, 06:49:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | FAB37EA52A92EFF9C0C6290923794547 |
| SHA1: | 133860EA8F33CF4C0FC51E60052AED04F762F44C |
| SHA256: | 75CF81F368490B385F3F7A9B88204C0A1B01B7764D246735DC0430108DD35621 |
| SSDEEP: | 98304:f+QqZ8fULL3Ya9sv8YEJOz+TWrmYECf3D5G3u1Fksa4pyccUABpbAtdLwpN1jGot:LopDJXf/YvG |
MALICIOUS
Drops the executable file immediately after the start
- teracopy.exe (PID: 3656)
- teracopy.exe (PID: 3948)
- teracopy.tmp (PID: 3464)
Starts NET.EXE for service management
- teracopy.tmp (PID: 3464)
- net.exe (PID: 1040)
Registers / Runs the DLL via REGSVR32.EXE
- teracopy.tmp (PID: 3464)
SUSPICIOUS
Executable content was dropped or overwritten
- teracopy.exe (PID: 3948)
- teracopy.exe (PID: 3656)
- teracopy.tmp (PID: 3464)
Reads the Windows owner or organization settings
- teracopy.tmp (PID: 3464)
Reads the Internet Settings
- teracopy.tmp (PID: 3464)
Reads security settings of Internet Explorer
- teracopy.tmp (PID: 3464)
Creates/Modifies COM task schedule object
- teracopy.tmp (PID: 3464)
- regsvr32.exe (PID: 3936)
Executes as Windows Service
- TeraCopyService.exe (PID: 2856)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 3288)
- teracopy.tmp (PID: 3536)
- teracopy.tmp (PID: 3464)
- TeraCopyService.exe (PID: 1696)
- TeraCopyService.exe (PID: 2860)
- TeraCopyService.exe (PID: 2856)
- TeraCopy.exe (PID: 848)
- TeraCopy.exe (PID: 2896)
Checks supported languages
- wmpnscfg.exe (PID: 3288)
- teracopy.exe (PID: 3656)
- teracopy.tmp (PID: 3536)
- teracopy.exe (PID: 3948)
- teracopy.tmp (PID: 3464)
- TeraCopyService.exe (PID: 2860)
- TeraCopyService.exe (PID: 1696)
- TeraCopyService.exe (PID: 2856)
- TeraCopy.exe (PID: 2896)
- TeraCopy.exe (PID: 848)
Create files in a temporary directory
- teracopy.exe (PID: 3948)
- teracopy.exe (PID: 3656)
- TeraCopy.exe (PID: 2896)
Creates files in the program directory
- teracopy.tmp (PID: 3464)
Creates files or folders in the user directory
- teracopy.tmp (PID: 3464)
- TeraCopy.exe (PID: 848)
- TeraCopy.exe (PID: 2896)
Creates a software uninstall entry
- teracopy.tmp (PID: 3464)
Manual execution by a user
- TeraCopy.exe (PID: 848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (51.8) |
|---|---|---|
| .exe | | | InstallShield setup (20.3) |
| .exe | | | Win32 EXE PECompact compressed (generic) (19.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.1) |
| .exe | | | Win32 Executable (generic) (2.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:11:15 09:48:30+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741376 |
| InitializedDataSize: | 38400 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.6.0.4 |
| ProductVersionNumber: | 3.6.0.4 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Code Sector |
| FileDescription: | TeraCopy Setup |
| FileVersion: | 3.6.0.4 |
| LegalCopyright: | © 2007-2021 Code Sector. |
| OriginalFileName: | |
| ProductName: | TeraCopy |
| ProductVersion: | 3.6.0.4 |
Total processes
53
Monitored processes
13
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 848 | "C:\Program Files\TeraCopy\TeraCopy.exe" | C:\Program Files\TeraCopy\TeraCopy.exe | explorer.exe | ||||||||||||
User: admin Company: Code Sector Integrity Level: MEDIUM Description: TeraCopy Exit code: 0 Version: 3.6.0.3 Modules
| |||||||||||||||
| 1040 | "C:\Windows\System32\net.exe" stop TeraCopyService | C:\Windows\System32\net.exe | — | teracopy.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1696 | "C:\Program Files\TeraCopy\TeraCopyService.exe" /remove /s | C:\Program Files\TeraCopy\TeraCopyService.exe | — | teracopy.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2856 | "C:\Program Files\TeraCopy\TeraCopyService.exe" | C:\Program Files\TeraCopy\TeraCopyService.exe | — | services.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 2860 | "C:\Program Files\TeraCopy\TeraCopyService.exe" /i | C:\Program Files\TeraCopy\TeraCopyService.exe | — | teracopy.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2896 | "C:\Program Files\TeraCopy\TeraCopy.exe" | C:\Program Files\TeraCopy\TeraCopy.exe | teracopy.tmp | ||||||||||||
User: admin Company: Code Sector Integrity Level: MEDIUM Description: TeraCopy Exit code: 0 Version: 3.6.0.3 Modules
| |||||||||||||||
| 3288 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3428 | C:\Windows\system32\net1 stop TeraCopyService | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3464 | "C:\Users\admin\AppData\Local\Temp\is-FMTQA.tmp\teracopy.tmp" /SL5="$100130,7118209,780800,C:\Users\admin\AppData\Local\Temp\teracopy.exe" /SPAWNWND=$150180 /NOTIFYWND=$E0170 | C:\Users\admin\AppData\Local\Temp\is-FMTQA.tmp\teracopy.tmp | teracopy.exe | ||||||||||||
User: admin Company: Code Sector Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3536 | "C:\Users\admin\AppData\Local\Temp\is-RQHM3.tmp\teracopy.tmp" /SL5="$E0170,7118209,780800,C:\Users\admin\AppData\Local\Temp\teracopy.exe" | C:\Users\admin\AppData\Local\Temp\is-RQHM3.tmp\teracopy.tmp | — | teracopy.exe | |||||||||||
User: admin Company: Code Sector Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
4 995
Read events
4 940
Write events
49
Delete events
6
Modification events
| (PID) Process: | (3464) teracopy.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 880D000032357907C963DA01 | |||
| (PID) Process: | (3464) teracopy.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: E1314A2C75380FBD1B7F785B1E24358D6BA03377169C9117F5831484B5DA1D25 | |||
| (PID) Process: | (3464) teracopy.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3464) teracopy.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3464) teracopy.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3464) teracopy.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3464) teracopy.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3464) teracopy.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\TeraCopy\TeraCopy.dll | |||
| (PID) Process: | (3464) teracopy.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 2C04D36F13DF376F2E2493B5B358B7DDA2BF64E6A8465217E120B734F6C521ED | |||
| (PID) Process: | (3464) teracopy.tmp | Key: | HKEY_CURRENT_USER\Software\Code Sector\TeraCopy |
| Operation: | write | Name: | InstallDir |
Value: C:\Program Files\TeraCopy | |||
Executable files
14
Suspicious files
72
Text files
105
Unknown types
31
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3656 | teracopy.exe | C:\Users\admin\AppData\Local\Temp\is-RQHM3.tmp\teracopy.tmp | executable | |
MD5:5AF7ADBC5255C7F3AFA004BD0CF13DF6 | SHA256:422D4320635A06C7D282B25B69CB0B1D70709AF2EAB8F3368C8C5D1C24323D38 | |||
| 3464 | teracopy.tmp | C:\Program Files\TeraCopy\Directory Opus.txt | text | |
MD5:DA536A00C47327CF9750AFB7798E6EB8 | SHA256:727633B122C814BDB58D83737AE0BCC0613CCFFA2808CE319910A4567FAAECA3 | |||
| 3464 | teracopy.tmp | C:\Program Files\TeraCopy\License.txt | text | |
MD5:0C020E9EC866A7426AA62A593D77A894 | SHA256:7DCFBD0351C64C0798EC5CC14BB32BAB7B224A854A456A7E20CA15E103BB8D7F | |||
| 3464 | teracopy.tmp | C:\Program Files\TeraCopy\is-8L76I.tmp | text | |
MD5:453C71A1AB54A2E97D4BB89BB03A9993 | SHA256:7DFD1F7111E2594E5E278F724E377CBDB6DA2A9932489B4A05F520F867747509 | |||
| 3464 | teracopy.tmp | C:\Program Files\TeraCopy\sorttable.js | text | |
MD5:C465D96C2035408602F71B29B06D722C | SHA256:72FA6DDC5DFDB54DD35935FEAAAD9B2A68CA1E872CAA4EDF03C1A26F1C3E4931 | |||
| 3464 | teracopy.tmp | C:\Program Files\TeraCopy\is-15C2J.tmp | executable | |
MD5:1809B2666ED1FA4A10EBCC02A828D98F | SHA256:FD4ADD57B107163F881501FD137B89453DEE5C69FEE2952A924F7C34394344AE | |||
| 3464 | teracopy.tmp | C:\Program Files\TeraCopy\Readme.txt | text | |
MD5:453C71A1AB54A2E97D4BB89BB03A9993 | SHA256:7DFD1F7111E2594E5E278F724E377CBDB6DA2A9932489B4A05F520F867747509 | |||
| 3464 | teracopy.tmp | C:\Program Files\TeraCopy\share.html | html | |
MD5:E80BBE1AF941EE5F500C1F2842EEE27D | SHA256:B309A734A6C4DC05AD32D29EF12D5A477EB61ED465302414B0AEC3C8FA317F43 | |||
| 3464 | teracopy.tmp | C:\Program Files\TeraCopy\TeraCopy64.dll | executable | |
MD5:DFE875D6515A7093950E00D2CB64217D | SHA256:5765C1565C71F4D90A19BA256D191D7A3FB8DEE8758E5DC65FB3842ACCE5F97D | |||
| 3464 | teracopy.tmp | C:\Program Files\TeraCopy\is-CPUOM.tmp | executable | |
MD5:DFE875D6515A7093950E00D2CB64217D | SHA256:5765C1565C71F4D90A19BA256D191D7A3FB8DEE8758E5DC65FB3842ACCE5F97D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Threats
Process | Message |
|---|---|
TeraCopy.exe | chromeLow |
TeraCopy.exe | 1593687 : File list created: 240220-065023-721-846.db |
TeraCopy.exe | 1593843 : on activate |
TeraCopy.exe | 1616281 : archive |
TeraCopy.exe | chromeLow |
TeraCopy.exe | 1623031 : File list created: 240220-065053-065-695.db |
TeraCopy.exe | 1623187 : on activate |
TeraCopy.exe | 1627296 : archive |