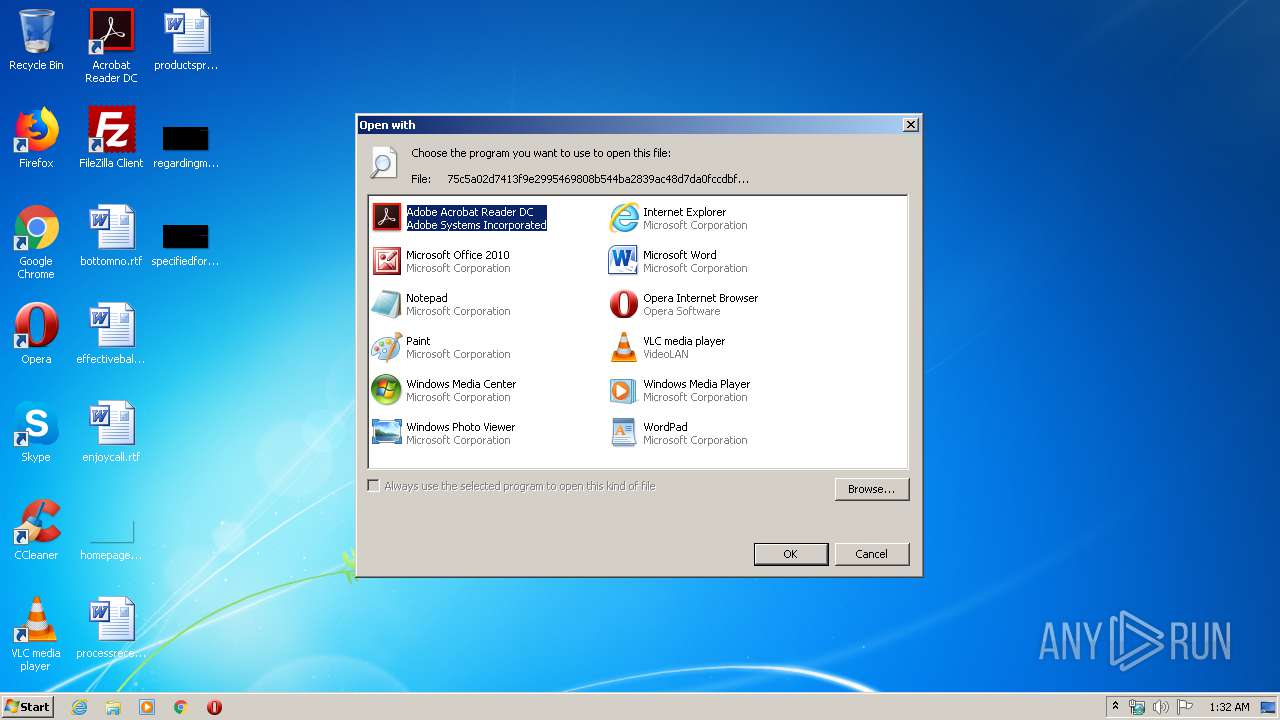
| File name: | 75c5a02d7413f9e2995469808b544ba2839ac48d7da0fccdbf3259e81ae4734a |
| Full analysis: | https://app.any.run/tasks/e3909dc2-0454-4010-9b0a-a0c379cc9397 |
| Verdict: | Malicious activity |
| Analysis date: | February 22, 2020, 01:32:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | data |
| MD5: | D1523C52E56EC8719C9B77424E3AA3CC |
| SHA1: | 1B5F2B03427FED76E1296A0494711703A1364B1B |
| SHA256: | 75C5A02D7413F9E2995469808B544BA2839AC48D7DA0FCCDBF3259E81AE4734A |
| SSDEEP: | 384:xUfNIKllBCtTcnhSwdgm+6+ItU8r0yJ5fwXXyAuiILK4Tzdv7QwX1NjPjKP:uvdgmsItTLgyA4j1NjGP |
MALICIOUS
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 1944)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 1944)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 1944)
SUSPICIOUS
Starts Microsoft Office Application
- rundll32.exe (PID: 3000)
Reads Internet Cache Settings
- WINWORD.EXE (PID: 1944)
Creates executable files which already exist in Windows
- WINWORD.EXE (PID: 1944)
Unusual connect from Microsoft Office
- WINWORD.EXE (PID: 1944)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1944)
Creates files in the user directory
- WINWORD.EXE (PID: 1944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1944 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\75c5a02d7413f9e2995469808b544ba2839ac48d7da0fccdbf3259e81ae4734a" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3000 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\75c5a02d7413f9e2995469808b544ba2839ac48d7da0fccdbf3259e81ae4734a | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3164 | cmd /c %tmp%\services.exe | C:\Windows\system32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 001
Read events
872
Write events
127
Delete events
2
Modification events
| (PID) Process: | (3000) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe |
Value: Adobe Acrobat Reader DC | |||
| (PID) Process: | (3000) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\eHome\ehshell.exe |
Value: Windows Media Center | |||
| (PID) Process: | (3000) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\mspaint.exe |
Value: Paint | |||
| (PID) Process: | (3000) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (3000) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (3000) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Opera\Opera.exe |
Value: Opera Internet Browser | |||
| (PID) Process: | (3000) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Windows Photo Viewer\PhotoViewer.dll |
Value: Windows Photo Viewer | |||
| (PID) Process: | (3000) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\VideoLAN\VLC\vlc.exe |
Value: VLC media player | |||
| (PID) Process: | (3000) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE |
Value: Microsoft Word | |||
| (PID) Process: | (3000) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
2
Suspicious files
5
Text files
0
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1944 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR8499.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1944 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CabB659.tmp | — | |
MD5:— | SHA256:— | |||
| 1944 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\TarB65A.tmp | — | |
MD5:— | SHA256:— | |||
| 1944 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$c5a02d7413f9e2995469808b544ba2839ac48d7da0fccdbf3259e81ae4734a | pgc | |
MD5:— | SHA256:— | |||
| 1944 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1944 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\644B8874112055B5E195ECB0E8F243A4 | der | |
MD5:— | SHA256:— | |||
| 1944 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\services.exe | executable | |
MD5:— | SHA256:— | |||
| 1944 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\putty[1].exe | executable | |
MD5:— | SHA256:— | |||
| 1944 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{562FA5B7-4E64-458C-A4EF-A685058F4AFB}.tmp | binary | |
MD5:— | SHA256:— | |||
| 1944 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\644B8874112055B5E195ECB0E8F243A4 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1944 | WINWORD.EXE | GET | 200 | 192.35.177.64:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | US | der | 994 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1944 | WINWORD.EXE | 97.107.141.160:443 | ryara.net | Linode, LLC | US | suspicious |
1944 | WINWORD.EXE | 192.35.177.64:80 | crl.identrust.com | IdenTrust | US | malicious |
1944 | WINWORD.EXE | 2.16.186.11:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ryara.net |
| suspicious |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
crl.identrust.com |
| whitelisted |