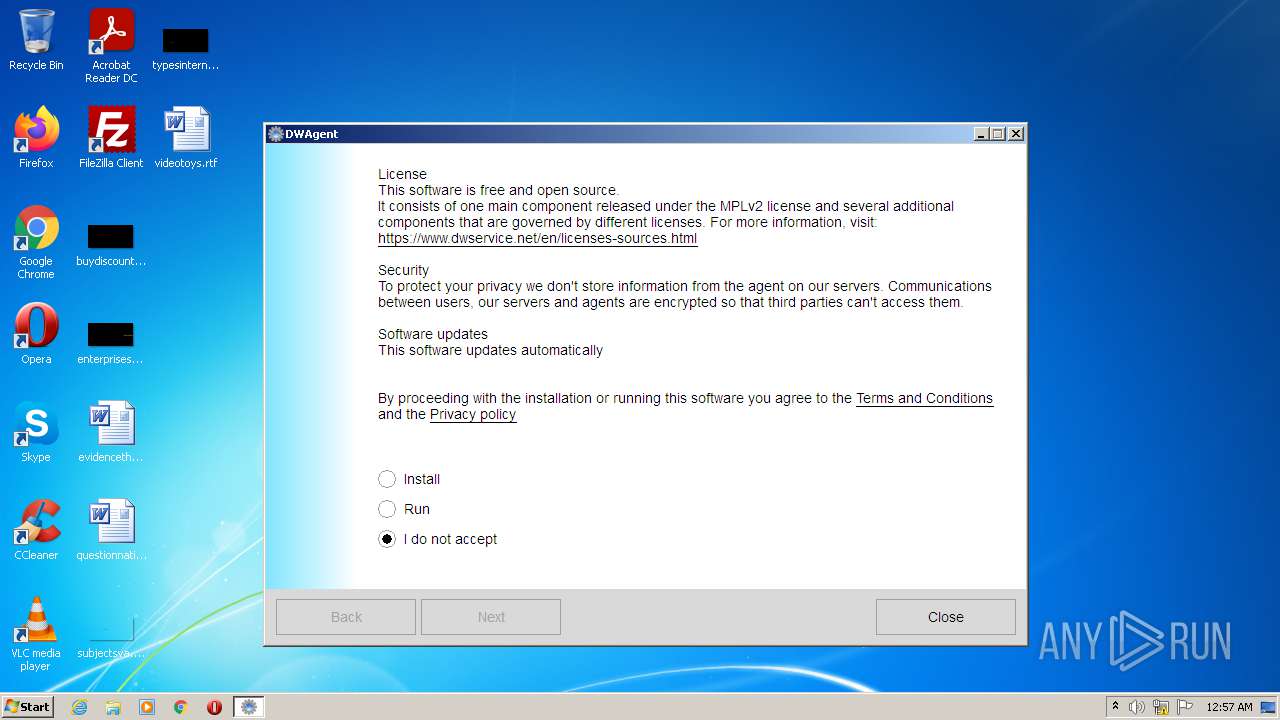
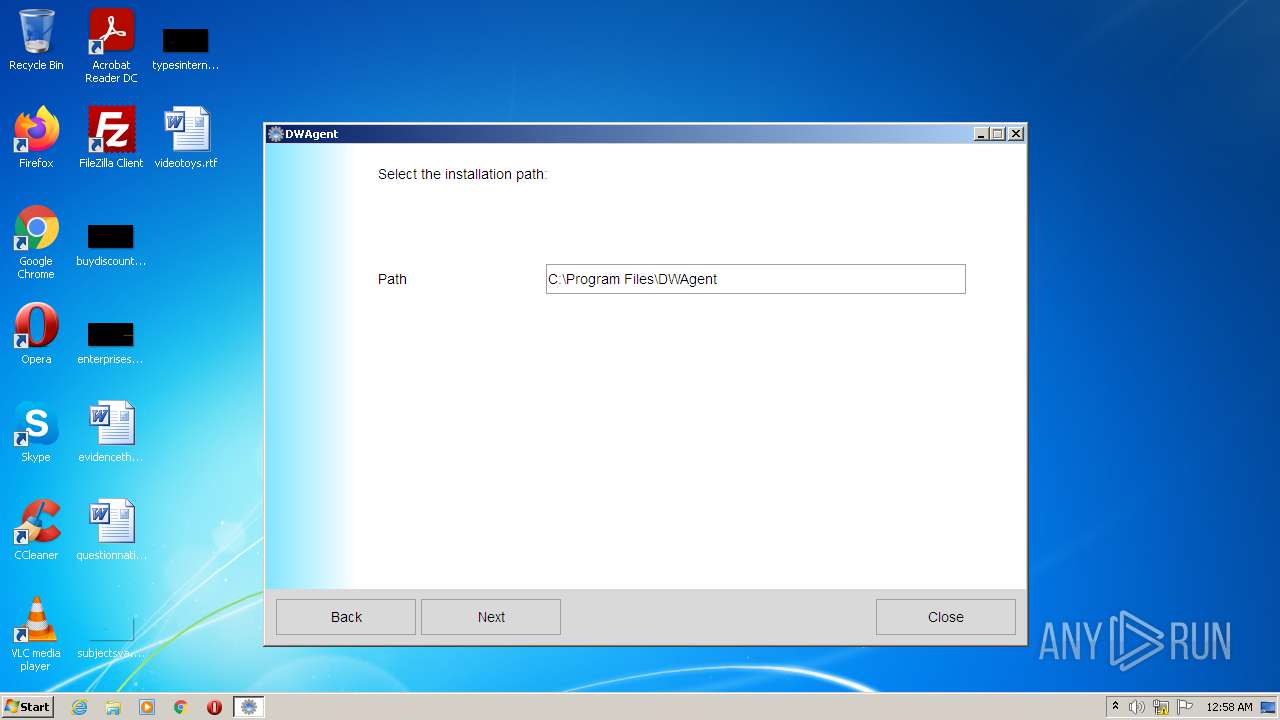
| File name: | dwagent.exe |
| Full analysis: | https://app.any.run/tasks/e10f885c-b81f-4b35-ba43-9573c66cebc4 |
| Verdict: | Malicious activity |
| Analysis date: | October 14, 2021, 23:57:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows |
| MD5: | CD1D70EB4D83B30B04C01A552C8E09F3 |
| SHA1: | BBF8C86FBD331AA6539169FEC665F518FE6F1DD2 |
| SHA256: | 75842F5D50818707909E3A09E0C3C3725390BA2F9A5D9730AB2B0B187E9AAA60 |
| SSDEEP: | 196608:z/a0+ibAbkQXMrMLWPpBJlXz6X+LmL6pHM1K+SlyMW:zFULXMrMLWhJXzXIosg+7J |
MALICIOUS
Drops executable file immediately after starts
- dwagent.exe (PID: 2796)
Application was dropped or rewritten from another process
- dwagent.exe (PID: 3732)
- dwagent.exe (PID: 2848)
Loads dropped or rewritten executable
- dwagent.exe (PID: 3732)
- dwagent.exe (PID: 2848)
SUSPICIOUS
Reads the computer name
- dwagent.exe (PID: 2796)
- dwagent.exe (PID: 3732)
- dwagent.exe (PID: 3060)
- dwagent.exe (PID: 2848)
Checks supported languages
- dwagent.exe (PID: 2796)
- dwagent.exe (PID: 3732)
- dwagent.exe (PID: 3060)
- dwagent.exe (PID: 2848)
Loads Python modules
- dwagent.exe (PID: 3732)
- dwagent.exe (PID: 2848)
Drops a file with too old compile date
- dwagent.exe (PID: 2796)
Executable content was dropped or overwritten
- dwagent.exe (PID: 2796)
Drops a file that was compiled in debug mode
- dwagent.exe (PID: 2796)
Application launched itself
- dwagent.exe (PID: 2796)
Creates files in the program directory
- dwagent.exe (PID: 2848)
Creates a directory in Program Files
- dwagent.exe (PID: 2848)
INFO
Dropped object may contain Bitcoin addresses
- dwagent.exe (PID: 2796)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:11:12 17:26:13+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.3 |
| CodeSize: | 290304 |
| InitializedDataSize: | 352256 |
| UninitializedDataSize: | 26112 |
| EntryPoint: | 0x1490 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 12-Nov-2019 16:26:13 |
| Detected languages: |
|
| TLS Callbacks: | 2 callback(s) detected. |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 12-Nov-2019 16:26:13 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00046D64 | 0x00046E00 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_1BYTES, IMAGE_SCN_ALIGN_2048BYTES, IMAGE_SCN_ALIGN_256BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_8BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.16627 |
.data | 0x00048000 | 0x000000AC | 0x00000200 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_1BYTES, IMAGE_SCN_ALIGN_256BYTES, IMAGE_SCN_ALIGN_2BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_512BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.19932 |
.rdata | 0x00049000 | 0x00004140 | 0x00004200 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_2048BYTES, IMAGE_SCN_ALIGN_2BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_512BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_8BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.55942 |
.bss | 0x0004E000 | 0x00006588 | 0x00000000 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_2048BYTES, IMAGE_SCN_ALIGN_2BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_512BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_8BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x00055000 | 0x000014A8 | 0x00001600 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_1BYTES, IMAGE_SCN_ALIGN_256BYTES, IMAGE_SCN_ALIGN_2BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_512BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.16995 |
.CRT | 0x00057000 | 0x00000034 | 0x00000200 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_1BYTES, IMAGE_SCN_ALIGN_256BYTES, IMAGE_SCN_ALIGN_2BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_512BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.273546 |
.tls | 0x00058000 | 0x00000008 | 0x00000200 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_1BYTES, IMAGE_SCN_ALIGN_256BYTES, IMAGE_SCN_ALIGN_2BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_512BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x00059000 | 0x00009208 | 0x00009400 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_1BYTES, IMAGE_SCN_ALIGN_256BYTES, IMAGE_SCN_ALIGN_2BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_512BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.29315 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.2684 | 296 | UNKNOWN | English - United States | RT_ICON |
2 | 5.07571 | 1384 | UNKNOWN | English - United States | RT_ICON |
3 | 6.10549 | 872 | UNKNOWN | English - United States | RT_ICON |
4 | 3.74743 | 744 | UNKNOWN | English - United States | RT_ICON |
5 | 6.23414 | 2216 | UNKNOWN | English - United States | RT_ICON |
6 | 5.96389 | 3240 | UNKNOWN | English - United States | RT_ICON |
7 | 3.28585 | 1640 | UNKNOWN | English - United States | RT_ICON |
8 | 5.35345 | 3752 | UNKNOWN | English - United States | RT_ICON |
9 | 4.94859 | 7336 | UNKNOWN | English - United States | RT_ICON |
10 | 5.55446 | 1128 | UNKNOWN | English - United States | RT_ICON |
Imports
ADVAPI32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
msvcrt.dll |
Total processes
39
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2796 | "C:\Users\admin\AppData\Local\Temp\dwagent.exe" | C:\Users\admin\AppData\Local\Temp\dwagent.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2848 | "C:\Users\admin\AppData\Local\Temp\dwagent20211014235749\runtime\dwagent.exe" -S -m installer gotoopt=install | C:\Users\admin\AppData\Local\Temp\dwagent20211014235749\runtime\dwagent.exe | dwagent.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3060 | "C:\Users\admin\AppData\Local\Temp\dwagent.exe" "-asadmin=C:\Users\admin\AppData\Local\Temp\dwagent20211014235749\\" | C:\Users\admin\AppData\Local\Temp\dwagent.exe | dwagent.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3732 | "C:\Users\admin\AppData\Local\Temp\dwagent20211014235749\runtime\dwagent.exe" -S -m installer | C:\Users\admin\AppData\Local\Temp\dwagent20211014235749\runtime\dwagent.exe | — | dwagent.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 909
Read events
1 893
Write events
16
Delete events
0
Modification events
| (PID) Process: | (2796) dwagent.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2796) dwagent.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2796) dwagent.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2796) dwagent.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3060) dwagent.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3060) dwagent.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3060) dwagent.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3060) dwagent.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
43
Suspicious files
0
Text files
19
Unknown types
540
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2796 | dwagent.exe | C:\Users\admin\AppData\Local\Temp\dwagent20211014235749\win.7z | — | |
MD5:— | SHA256:— | |||
| 2796 | dwagent.exe | C:\Users\admin\AppData\Local\Temp\dwagent20211014235749\runtime\bit64\DLLs\bz2.pyd | executable | |
MD5:51FDB7790E680A394E9936498D3A73FA | SHA256:985902E0813564981059C2F57282614F5A907DC3DF0273BA7BEF2AD64123C921 | |||
| 2796 | dwagent.exe | C:\Users\admin\AppData\Local\Temp\dwagent20211014235749\runtime\bit64\DLLs\_ssl.pyd | executable | |
MD5:9C6D526768F8395AECFF0AF0D27F0063 | SHA256:2C4CB4459C37A2152698E19F27350A7DBF56C51509689B1D7A65C60FB5A75751 | |||
| 2796 | dwagent.exe | C:\Users\admin\AppData\Local\Temp\dwagent20211014235749\runtime\bit64\DLLs\_elementtree.pyd | executable | |
MD5:F9D164C37E8D72E2BE240A2755FDCE53 | SHA256:099F356F4E009EF551F483EB009D39516D49E924C93B365E1F759F2686A6D8A8 | |||
| 2796 | dwagent.exe | C:\Users\admin\AppData\Local\Temp\dwagent20211014235749\runtime\bit64\DLLs\_multiprocessing.pyd | executable | |
MD5:739E1F883C32B2D197F5B040835C3223 | SHA256:1B9DC884EBB3D5E2C21434A6D0AC7831BFACDA400F4E71D0250CD38DC113FE37 | |||
| 2796 | dwagent.exe | C:\Users\admin\AppData\Local\Temp\dwagent20211014235749\runtime\bit64\DLLs\_ctypes_test.pyd | executable | |
MD5:E60F1CDEFB649CC95D55DB326DBCCC50 | SHA256:8547AADE3E20B6CA46C6A6D98F2A89D1C51F5EFC511B3837083DAA145F2640BB | |||
| 2796 | dwagent.exe | C:\Users\admin\AppData\Local\Temp\dwagent20211014235749\runtime\bit64\DLLs\unicodedata.pyd | executable | |
MD5:6C38211CC951D7800CB961F4BB16716C | SHA256:45EDCE458A292465D784E07A3FFD46580AAB0A4F925C40704BC45A60325E7537 | |||
| 2796 | dwagent.exe | C:\Users\admin\AppData\Local\Temp\dwagent20211014235749\runtime\bit64\DLLs\_socket.pyd | executable | |
MD5:F28DC3A4451C29FEA272D7AE063425C5 | SHA256:A75AA54781DE3C97F5B4C2E0389D5AD39602CDA6FCD5A3810667A4CF24F4286A | |||
| 2796 | dwagent.exe | C:\Users\admin\AppData\Local\Temp\dwagent20211014235749\runtime\DLLs\select.pyd | executable | |
MD5:E6ECFF0D1588FED3A61EDC1A1A5EB9BB | SHA256:345969D43B33717415BD5796D5A7B266592DC79A96543714828FF8FC1F249D18 | |||
| 2796 | dwagent.exe | C:\Users\admin\AppData\Local\Temp\dwagent20211014235749\runtime\bit64\DLLs\select.pyd | executable | |
MD5:C76CCF3E7883917832C3B2FA2B980AA1 | SHA256:417ECB5FE0CAF271AE53FD9132F4A6D50CB5304D586548F964A546CD5858F347 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2848 | dwagent.exe | 147.135.78.236:443 | www.dwservice.net | OVH SAS | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.dwservice.net |
| unknown |
dns.msftncsi.com |
| shared |