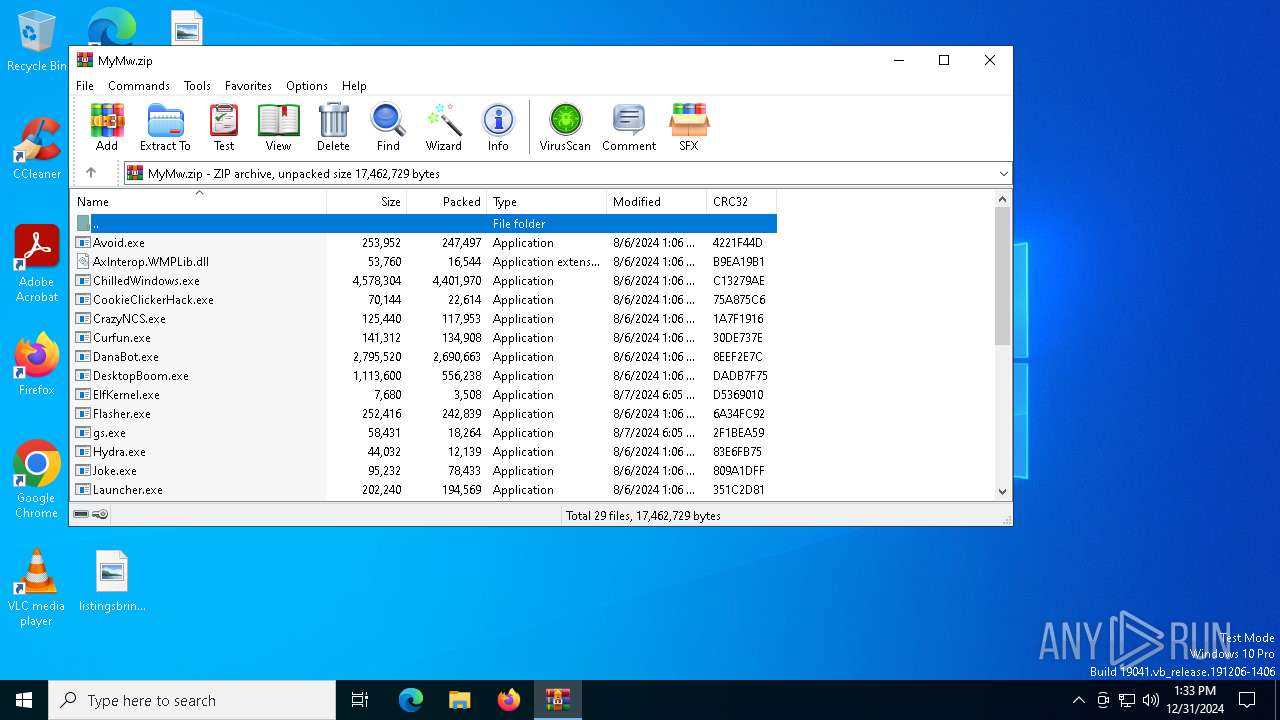
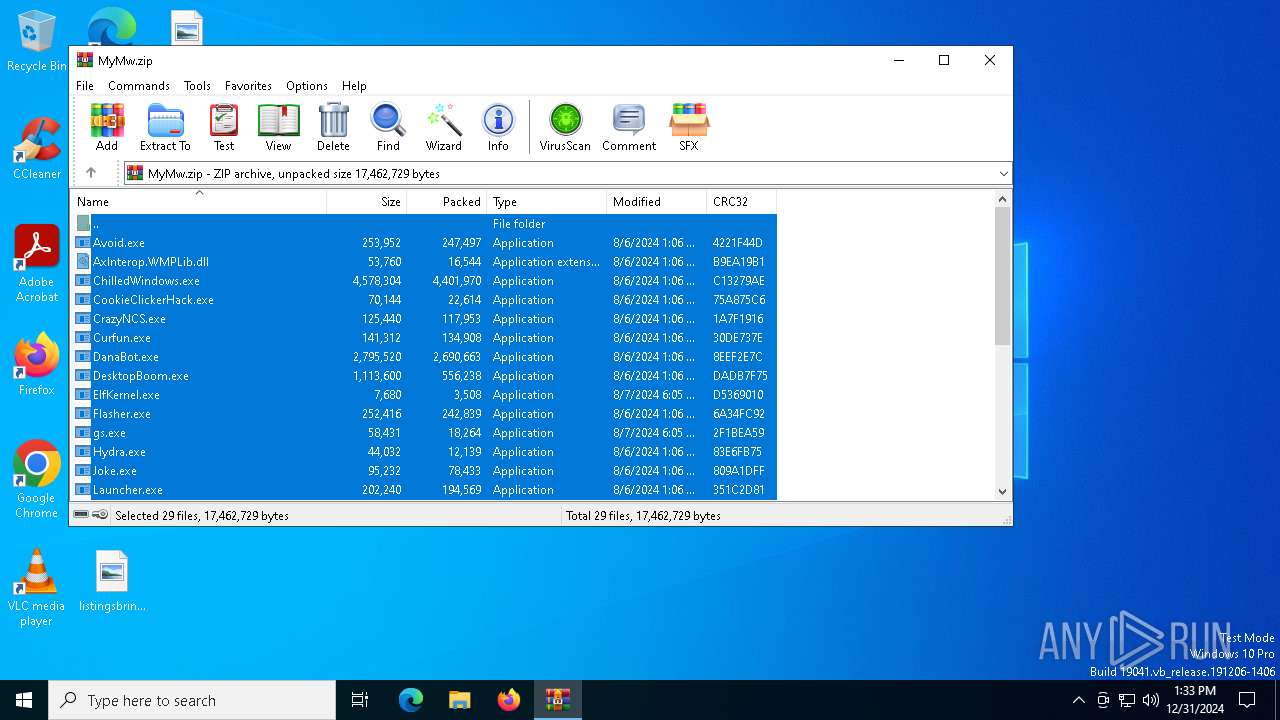
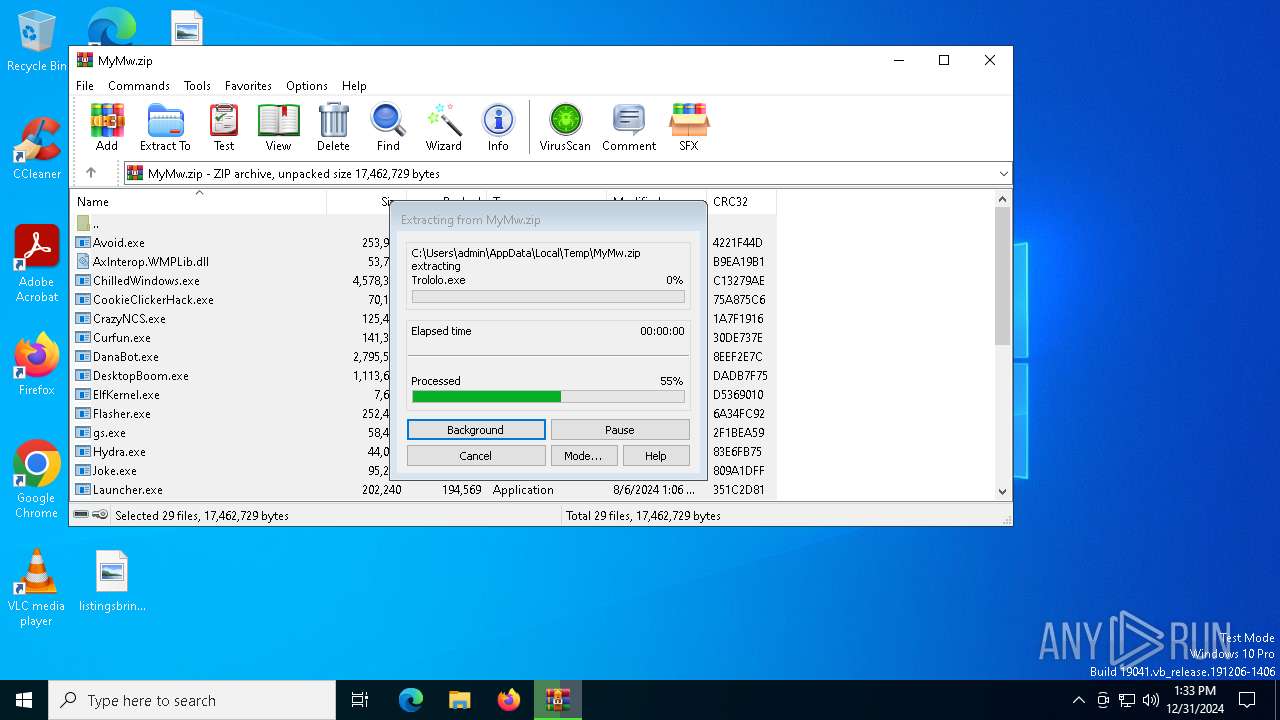
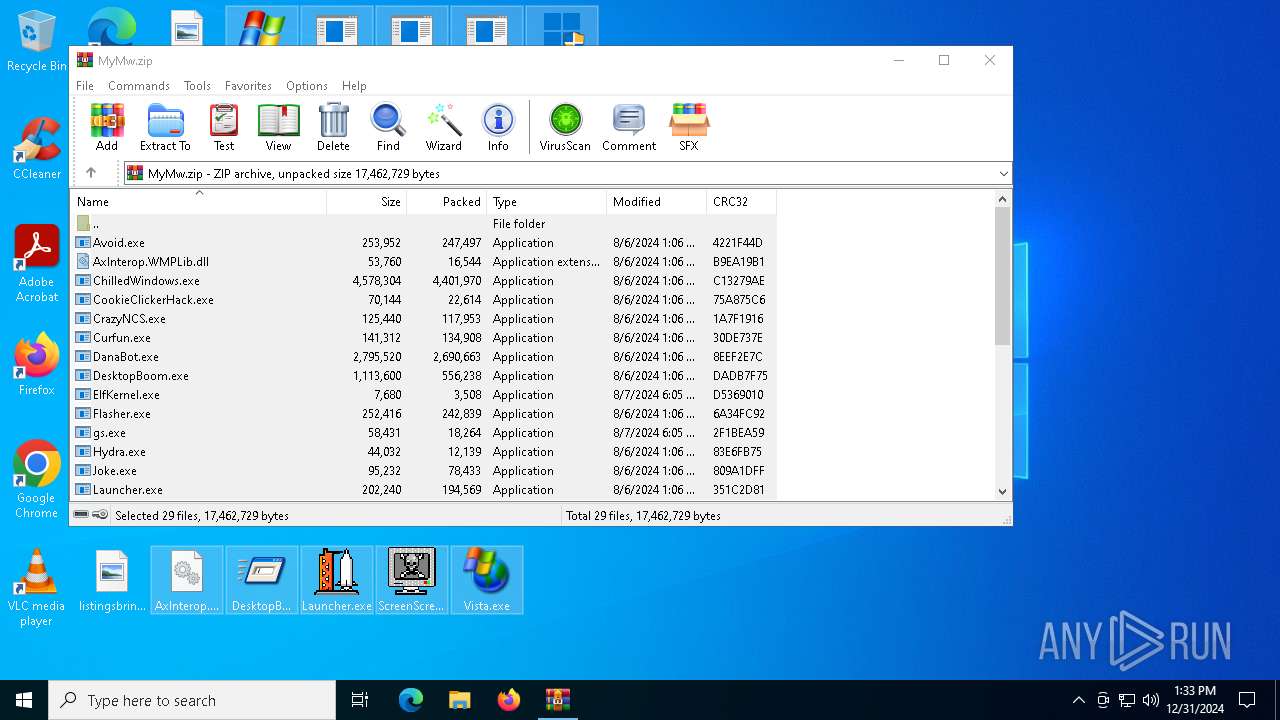
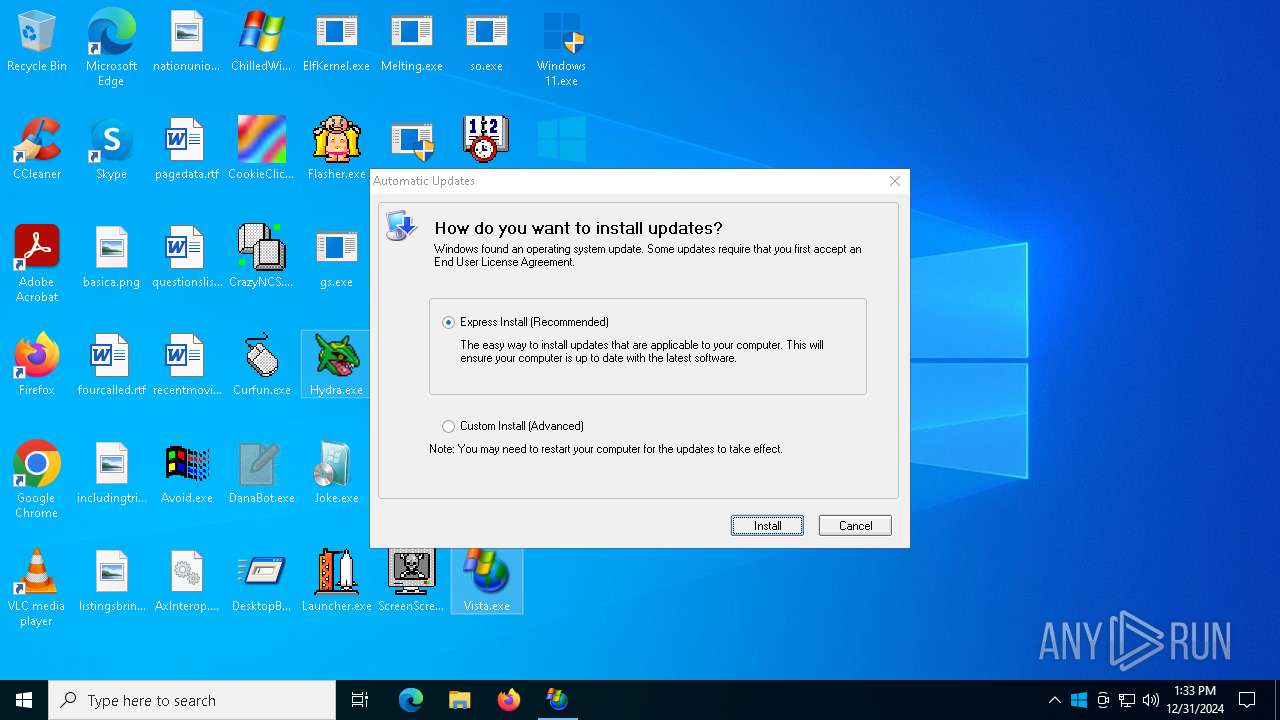
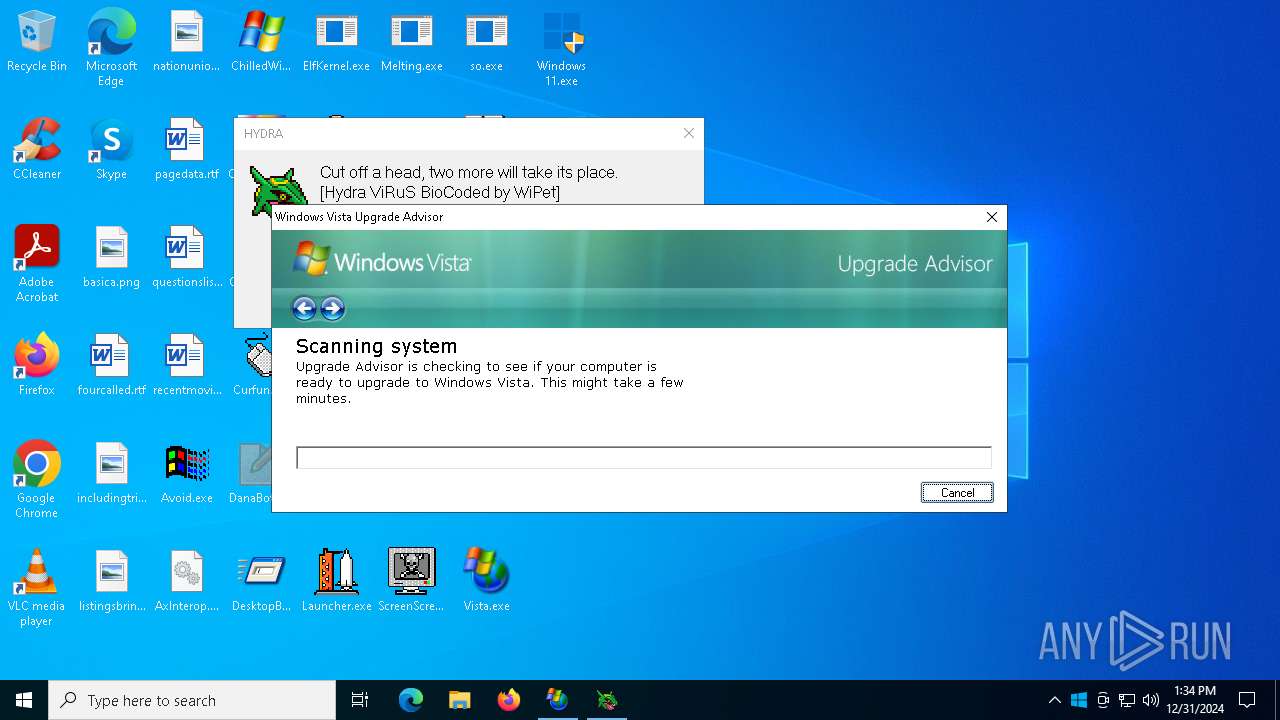
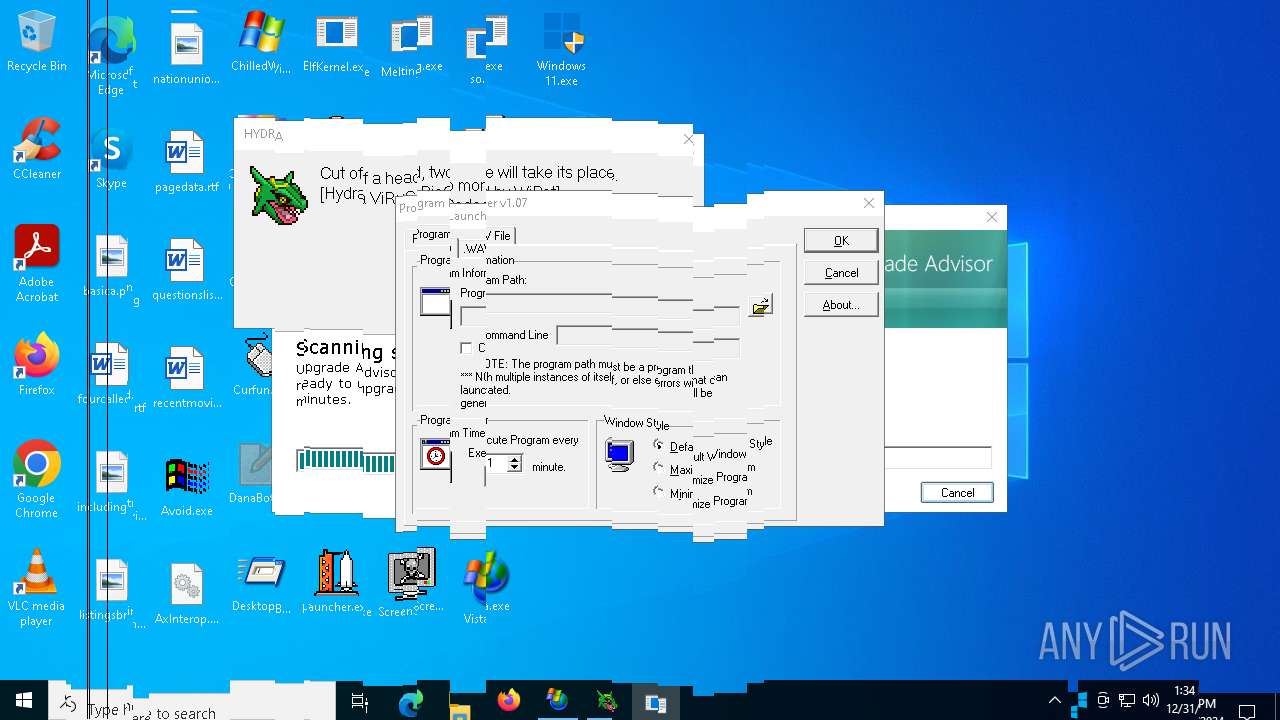
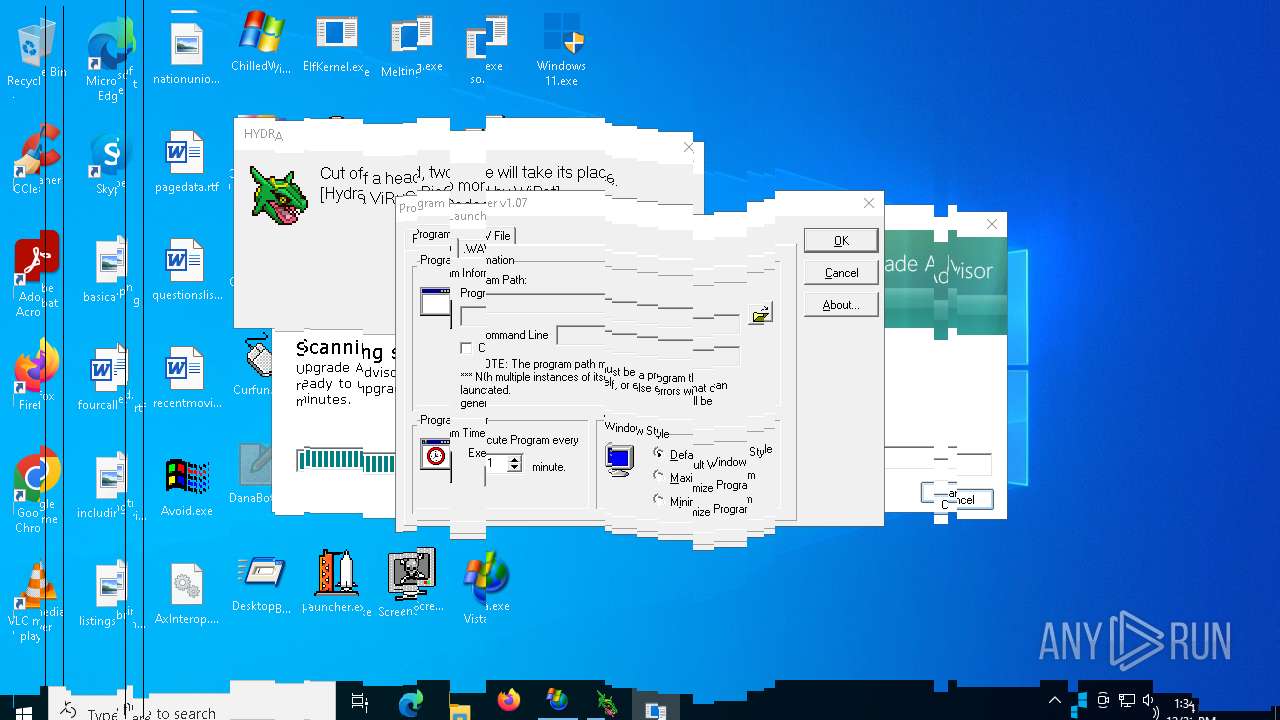
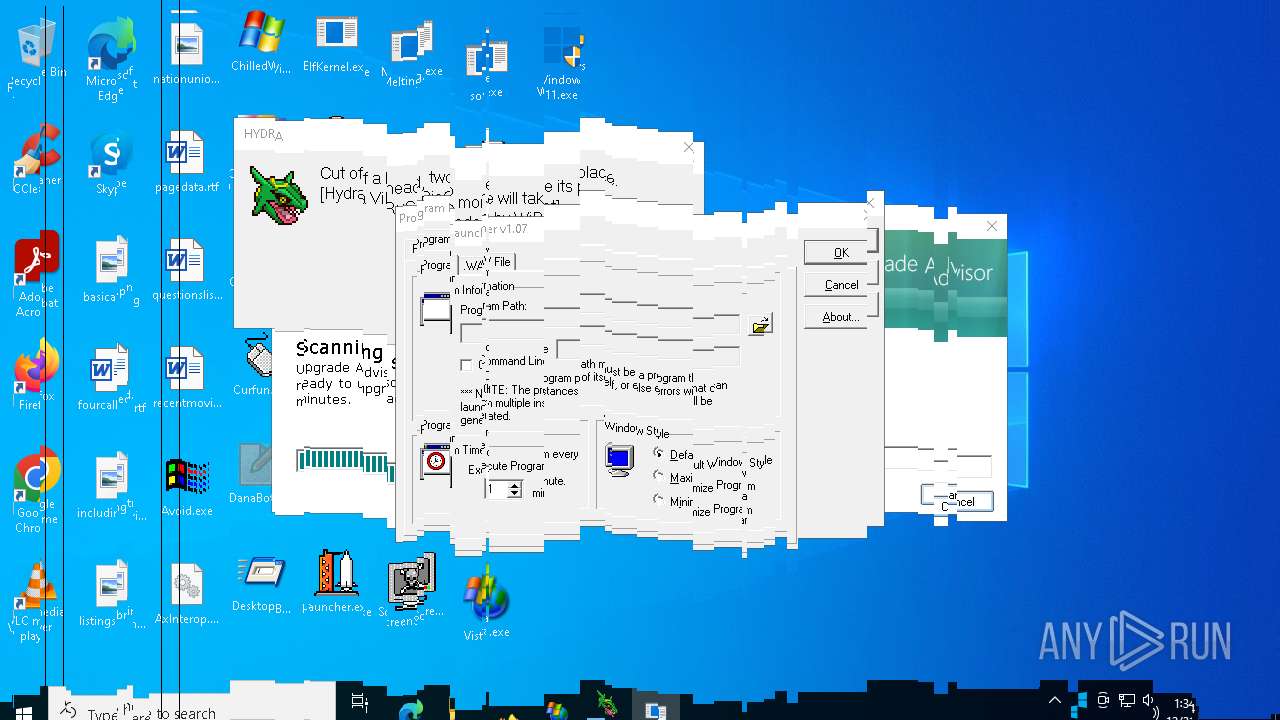
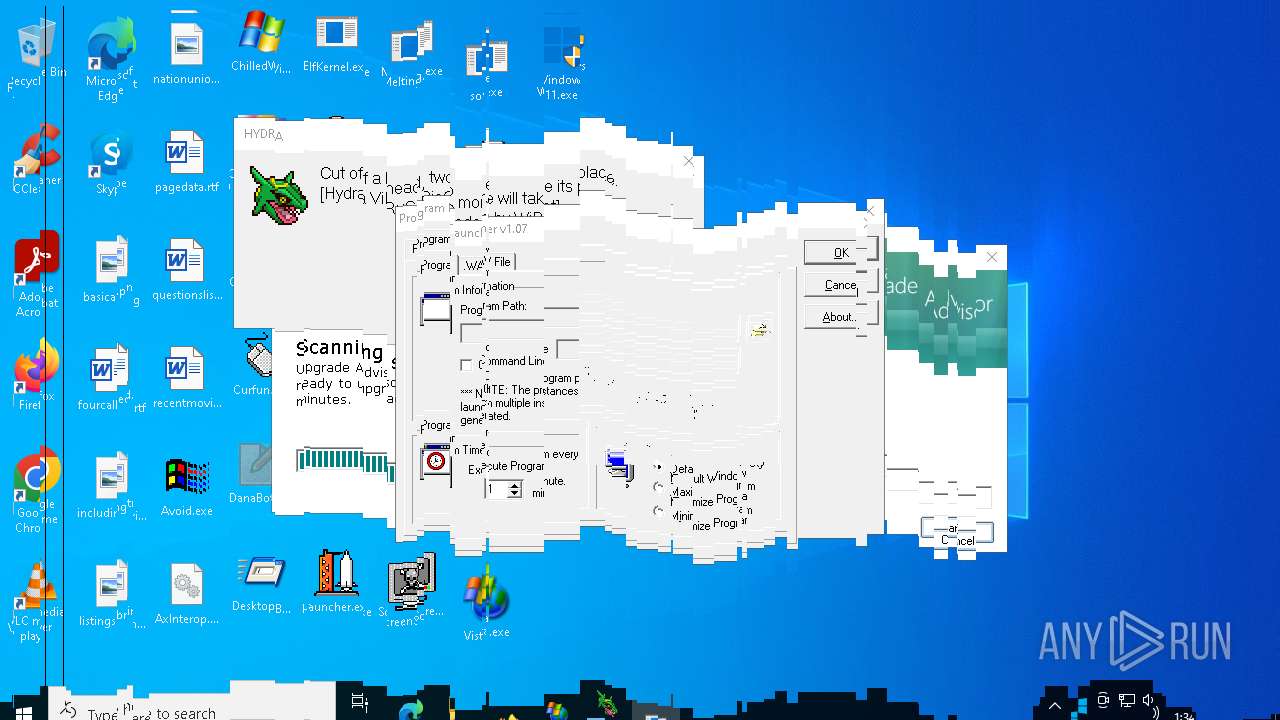
| File name: | MyMw.zip |
| Full analysis: | https://app.any.run/tasks/31f11f63-ce0b-479f-96be-bb6a62760daf |
| Verdict: | Malicious activity |
| Analysis date: | December 31, 2024, 13:33:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | D20309EAE3CDB8813D3562633663E936 |
| SHA1: | 28B34EC92C4788F7B3A477B7E0333B1C3D01DFC4 |
| SHA256: | 757B110744733CD80C6E6957F2DE5FFD628559A14BB5B1B22EE17C4F2D41BF6F |
| SSDEEP: | 196608:AWfzLwt4tGTnLBbn+iuYr2aCn/Eh20W3gZm:rLwbTndbn+iuhn/cZWwU |
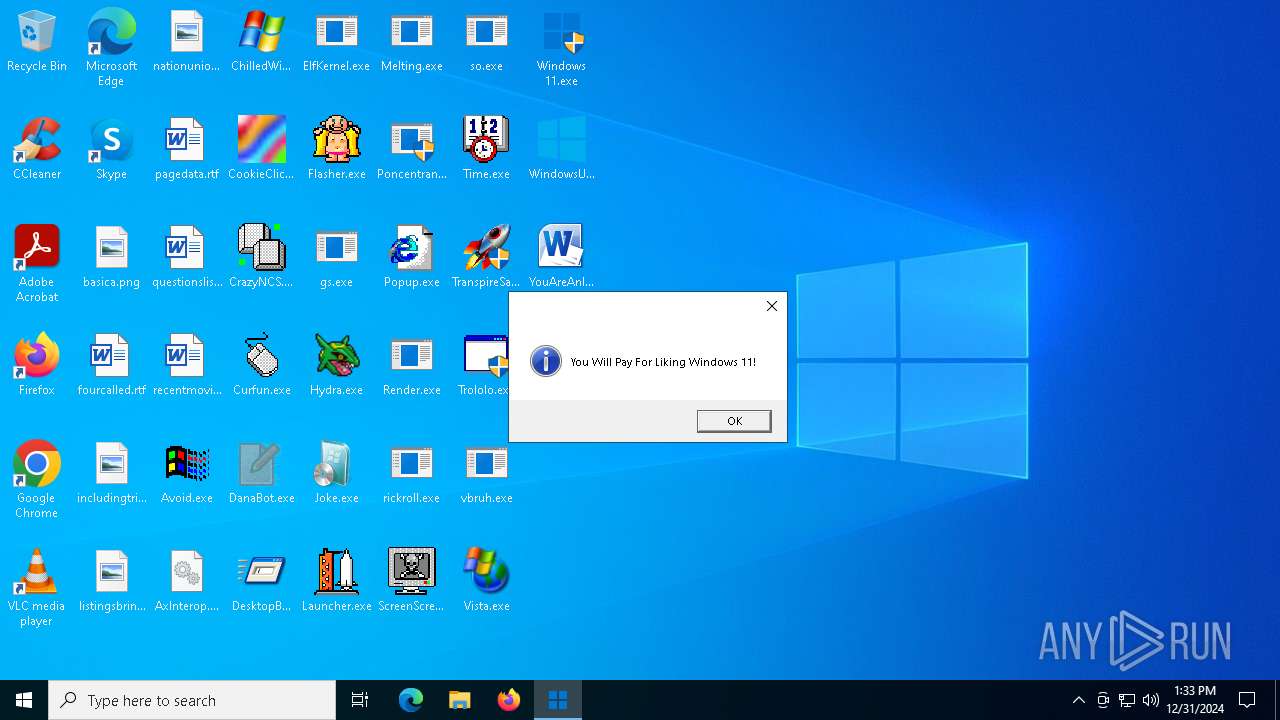
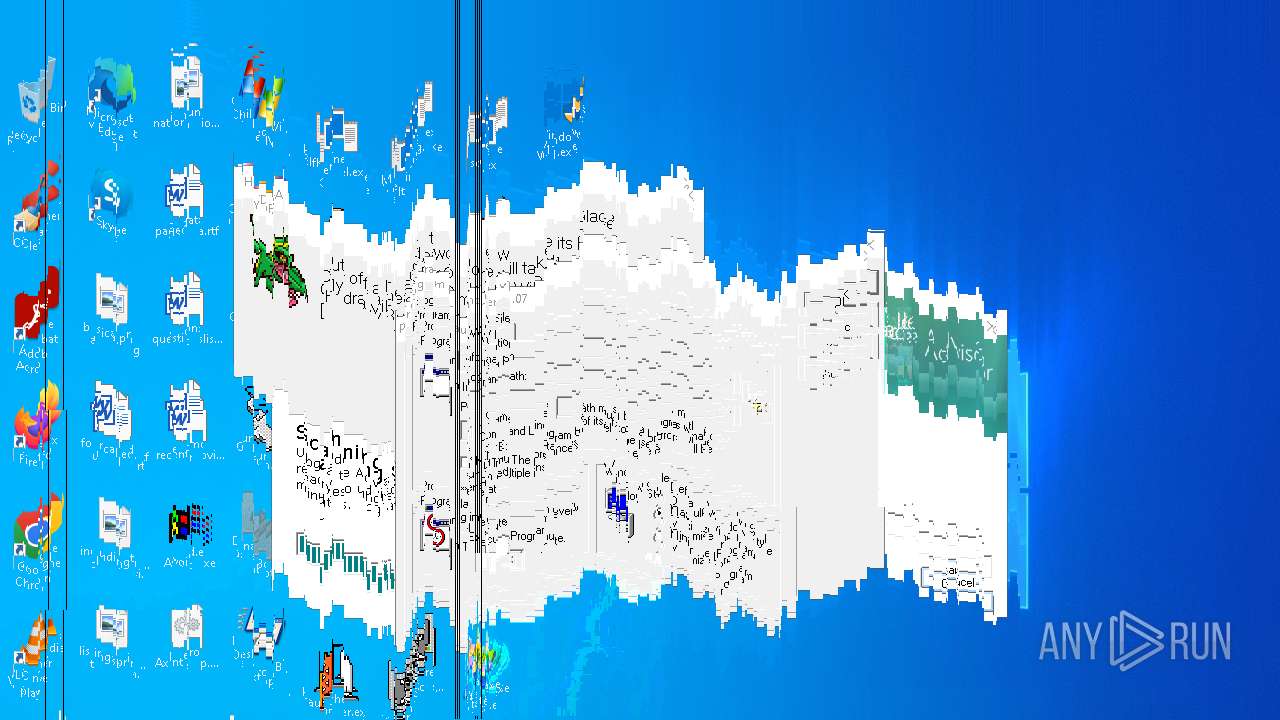
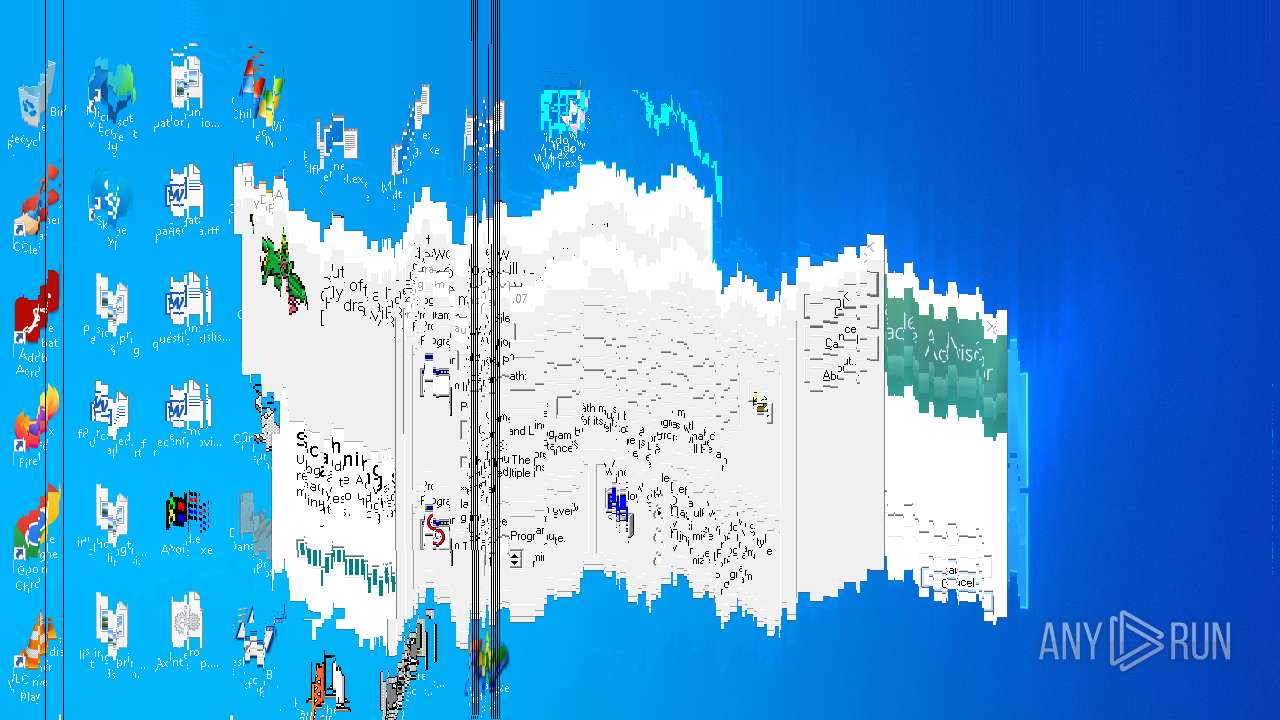
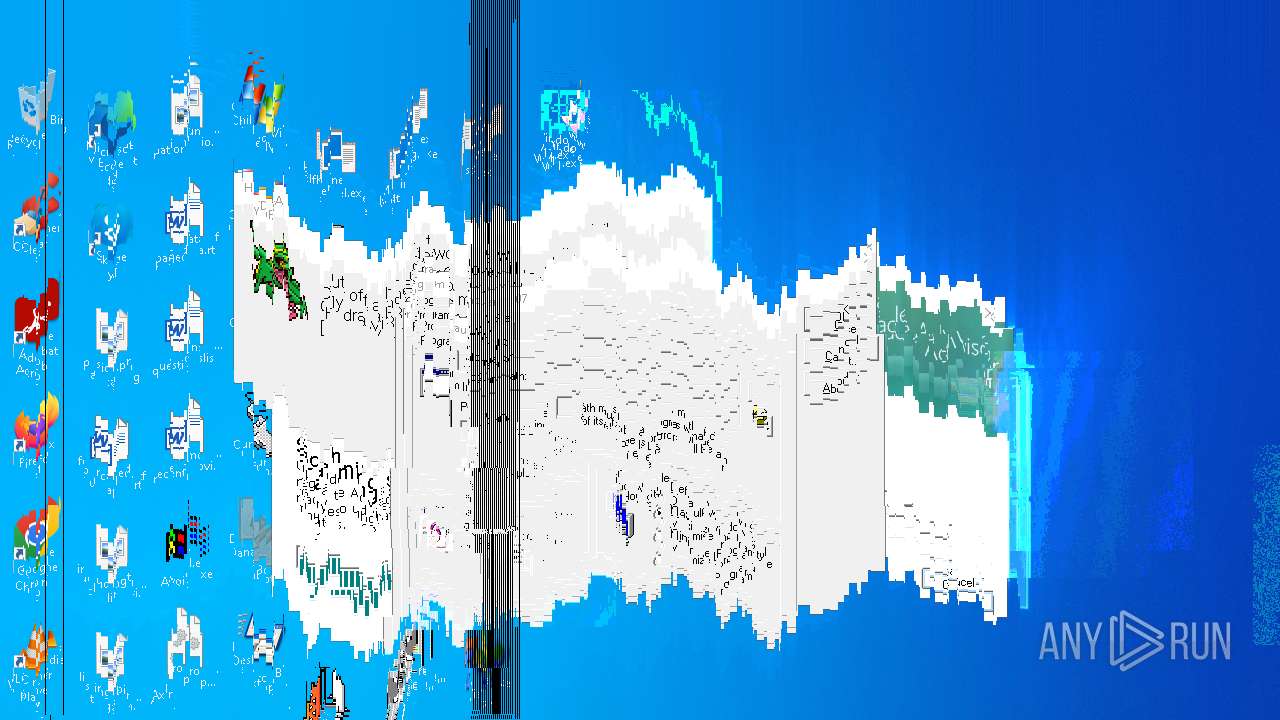
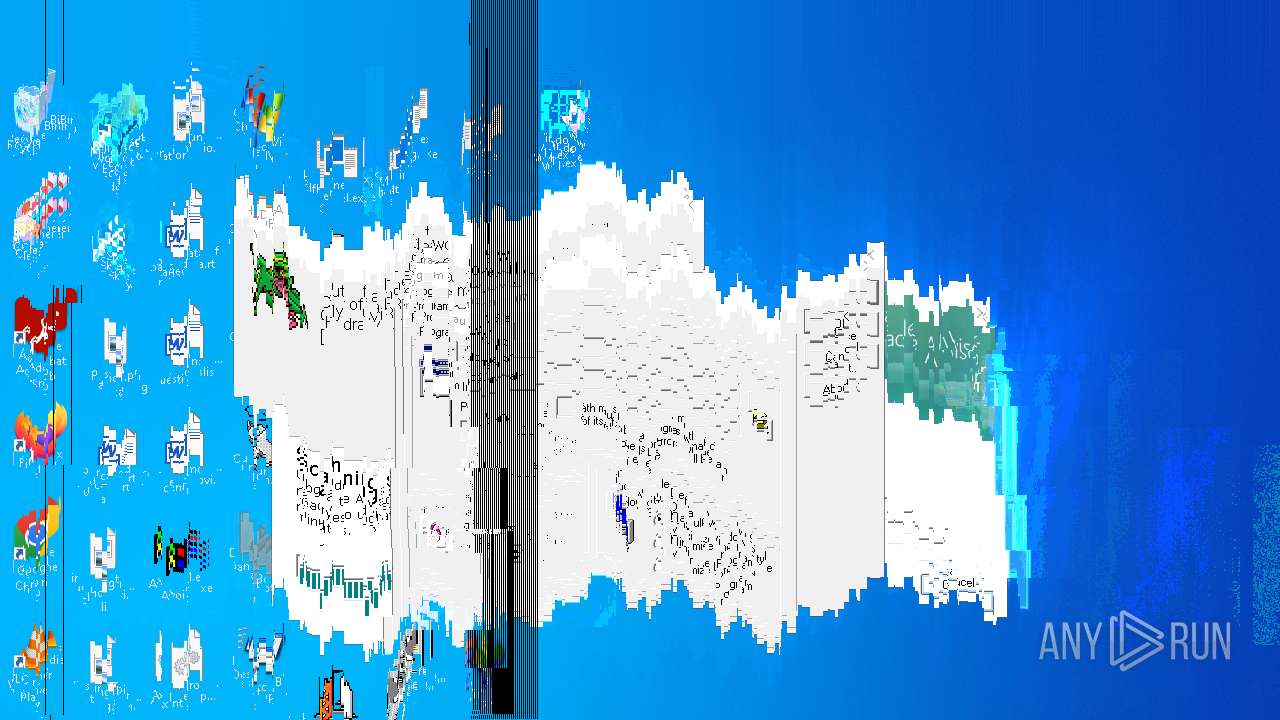
MALICIOUS
DESKTOPBOOM has been detected
- WinRAR.exe (PID: 1744)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 1744)
Starts a Microsoft application from unusual location
- Hydra.exe (PID: 188)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 1744)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1744)
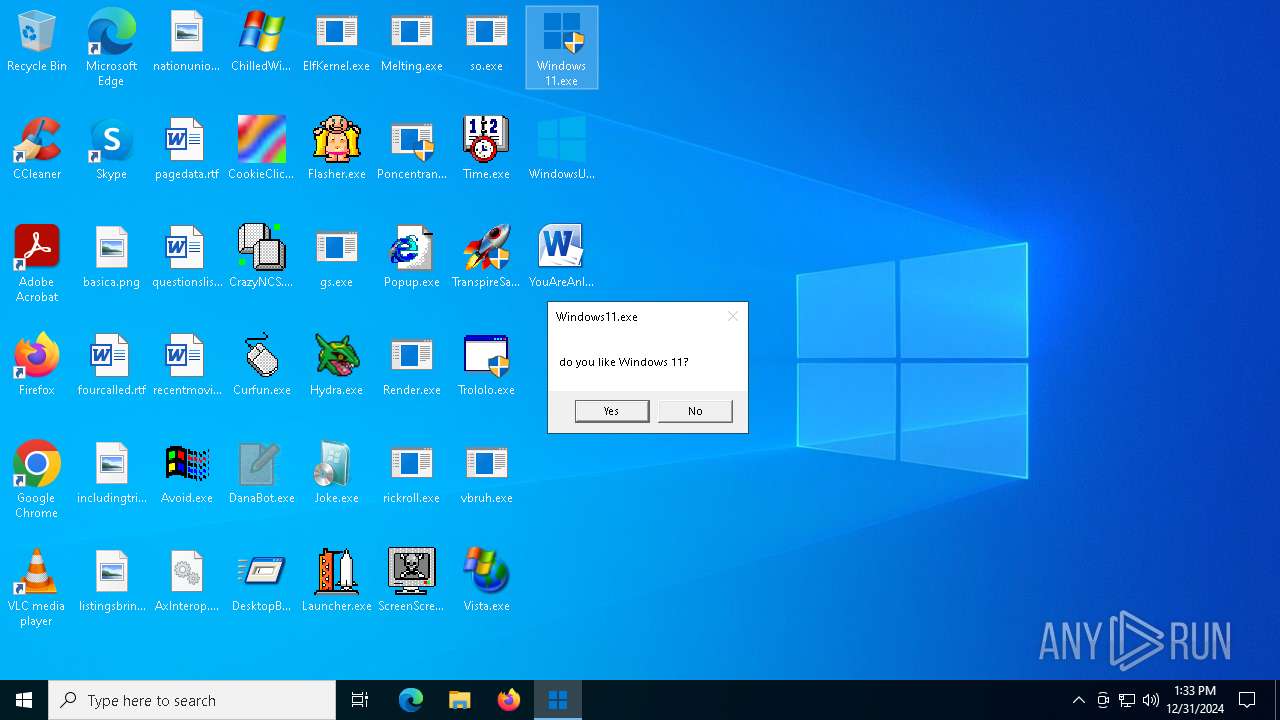
Manual execution by a user
- Windows 11.exe (PID: 7032)
- Windows 11.exe (PID: 7084)
- WindowsUpdate.exe (PID: 4708)
- Vista.exe (PID: 5652)
- Hydra.exe (PID: 188)
- Avoid.exe (PID: 5304)
- Launcher.exe (PID: 4384)
- Launcher.exe (PID: 936)
- ScreenScrew.exe (PID: 4556)
- ScreenScrew.exe (PID: 5640)
- Melting.exe (PID: 3080)
Reads the computer name
- Windows 11.exe (PID: 7084)
- WindowsUpdate.exe (PID: 4708)
- Vista.exe (PID: 5652)
- Hydra.exe (PID: 188)
- Launcher.exe (PID: 936)
- Melting.exe (PID: 3080)
Reads Environment values
- Vista.exe (PID: 5652)
Checks supported languages
- WindowsUpdate.exe (PID: 4708)
- Vista.exe (PID: 5652)
- Hydra.exe (PID: 188)
- Avoid.exe (PID: 5304)
- Launcher.exe (PID: 4384)
- Launcher.exe (PID: 936)
- ScreenScrew.exe (PID: 4556)
- ScreenScrew.exe (PID: 5640)
- Melting.exe (PID: 3080)
The process uses the downloaded file
- WinRAR.exe (PID: 1744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:08:06 20:06:30 |
| ZipCRC: | 0x4221f44d |
| ZipCompressedSize: | 247497 |
| ZipUncompressedSize: | 253952 |
| ZipFileName: | Avoid.exe |
Total processes
142
Monitored processes
12
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Users\admin\Desktop\Hydra.exe" | C:\Users\admin\Desktop\Hydra.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Hydra Version: 1.0.0.0 Modules
| |||||||||||||||
| 936 | "C:\Users\admin\Desktop\Launcher.exe" | C:\Users\admin\Desktop\Launcher.exe | — | explorer.exe | |||||||||||
User: admin Company: RJL Software, Inc. Integrity Level: MEDIUM Description: Launches any program every X minutes Version: 1.0.7.0 Modules
| |||||||||||||||
| 1744 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\MyMw.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3080 | "C:\Users\admin\Desktop\Melting.exe" | C:\Users\admin\Desktop\Melting.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4384 | "C:\Users\admin\Desktop\Launcher.exe" | C:\Users\admin\Desktop\Launcher.exe | — | explorer.exe | |||||||||||
User: admin Company: RJL Software, Inc. Integrity Level: MEDIUM Description: Launches any program every X minutes Version: 1.0.7.0 Modules
| |||||||||||||||
| 4556 | "C:\Users\admin\Desktop\ScreenScrew.exe" | C:\Users\admin\Desktop\ScreenScrew.exe | — | explorer.exe | |||||||||||
User: admin Company: RJL Software, Inc. Integrity Level: MEDIUM Description: Screws with your screen :) Version: 1.0.0.0 Modules
| |||||||||||||||
| 4708 | "C:\Users\admin\Desktop\WindowsUpdate.exe" | C:\Users\admin\Desktop\WindowsUpdate.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Windows 10 Update Center Version: 1.0.0.0 Modules
| |||||||||||||||
| 5304 | "C:\Users\admin\Desktop\Avoid.exe" | C:\Users\admin\Desktop\Avoid.exe | — | explorer.exe | |||||||||||
User: admin Company: RJL Software, Inc. Integrity Level: MEDIUM Description: Start Button avoids the mouse cursor. Version: 1.0.1.0 Modules
| |||||||||||||||
| 5640 | "C:\Users\admin\Desktop\ScreenScrew.exe" | C:\Users\admin\Desktop\ScreenScrew.exe | — | explorer.exe | |||||||||||
User: admin Company: RJL Software, Inc. Integrity Level: MEDIUM Description: Screws with your screen :) Version: 1.0.0.0 Modules
| |||||||||||||||
| 5652 | "C:\Users\admin\Desktop\Vista.exe" | C:\Users\admin\Desktop\Vista.exe | — | explorer.exe | |||||||||||
User: admin Company: RJL Software, Inc. Integrity Level: MEDIUM Description: A gag that fakes a Windows Vista upgrade Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
2 075
Read events
2 057
Write events
18
Delete events
0
Modification events
| (PID) Process: | (1744) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1744) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1744) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1744) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\MyMw.zip | |||
| (PID) Process: | (1744) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1744) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1744) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1744) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1744) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (1744) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
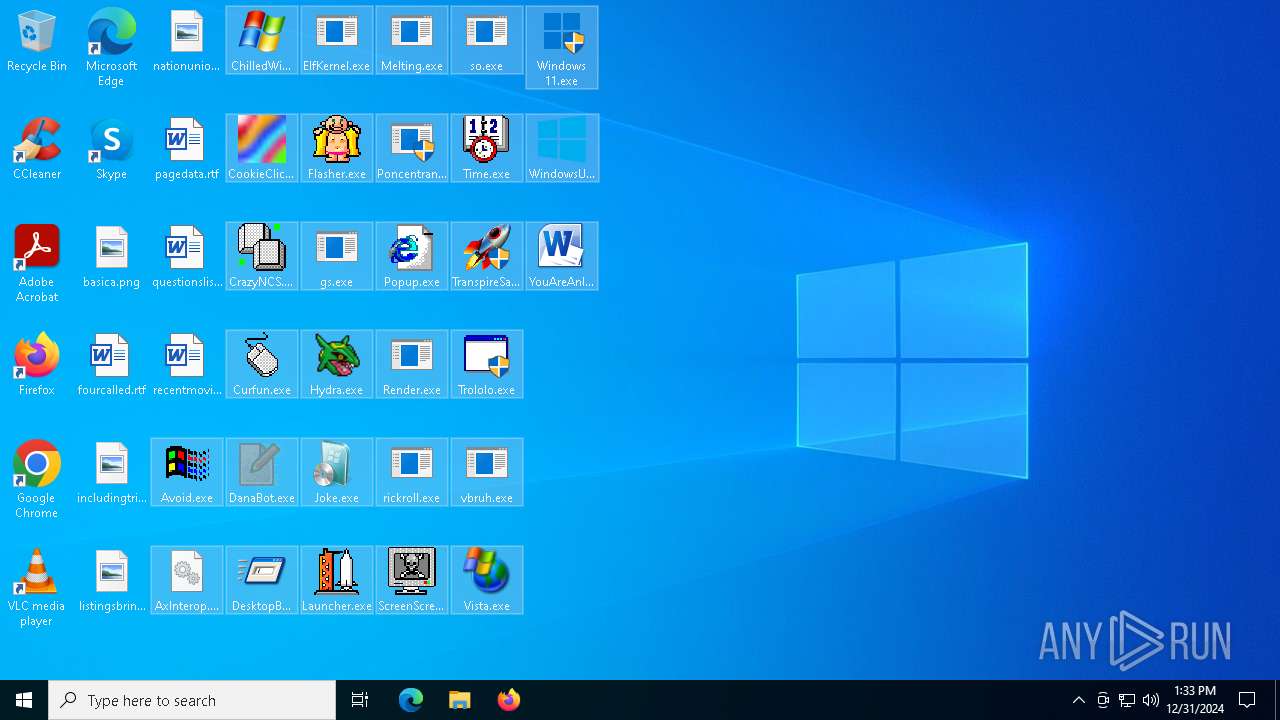
Executable files
29
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1744 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1744.33202\Hydra.exe | executable | |
MD5:B2ECA909A91E1946457A0B36EAF90930 | SHA256:0B6C0AF51CDE971B3E5F8AA204F8205418AB8C180B79A5AC1C11A6E0676F0F7C | |||
| 1744 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1744.33202\Avoid.exe | executable | |
MD5:20D2C71D6D9DAF4499FFC4A5D164F1C3 | SHA256:3AC8CC58DCBCEAEC3DAB046AEA050357E0E2248D30B0804C738C9A5B037C220D | |||
| 1744 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1744.33202\ChilledWindows.exe | executable | |
MD5:6A4853CD0584DC90067E15AFB43C4962 | SHA256:CCB9502BF8BA5BECF8B758CA04A5625C30B79E2D10D2677CC43AE4253E1288EC | |||
| 1744 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1744.33202\DanaBot.exe | executable | |
MD5:48D8F7BBB500AF66BAA765279CE58045 | SHA256:DB0D72BC7D10209F7FA354EC100D57ABBB9FE2E57CE72789F5F88257C5D3EBD1 | |||
| 1744 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1744.33202\DesktopBoom.exe | executable | |
MD5:F0A661D33AAC3A3CE0C38C89BEC52F89 | SHA256:C20E78CE9028299D566684D35B1230D055E5EA0E9B94D0AFF58F650E0468778A | |||
| 1744 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1744.33202\AxInterop.WMPLib.dll | executable | |
MD5:10A4C3C3D25BE89ECC972A3814029EE8 | SHA256:265F3A00DDA861B726A1D465BE53E6A421A289D17A7C5E05BC41ADD9316B6947 | |||
| 1744 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1744.33202\CookieClickerHack.exe | executable | |
MD5:BC1E7D033A999C4FD006109C24599F4D | SHA256:13ADAE722719839AF8102F98730F3AF1C5A56B58069BFCE8995ACD2123628401 | |||
| 1744 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1744.33202\CrazyNCS.exe | executable | |
MD5:D043BA91E42E0D9A68C9866F002E8A21 | SHA256:6820C71DF417E434C5AD26438C901C780FC5A80B28A466821B47D20B8424EF08 | |||
| 1744 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1744.33202\Joke.exe | executable | |
MD5:7B821EC1D15CA5121A8A7032128CDE1C | SHA256:9DECD270CC489190FD307B2F2F868F79963E9FCFA722702FC26EF6D5CBDE5BFF | |||
| 1744 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1744.33202\Launcher.exe | executable | |
MD5:7506EB94C661522AFF09A5C96D6F182B | SHA256:D5B962DFE37671B5134F0B741A662610B568C2B5374010EE92B5B7857D87872C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
31
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5448 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6432 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5448 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1868 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.19.217.218:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4008 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3976 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 23.212.110.208:443 | www.bing.com | Akamai International B.V. | CZ | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| unknown |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |