| File name: | msrdpcli.exe |
| Full analysis: | https://app.any.run/tasks/e79b8114-2eba-4ae6-acc3-a708f6571a6b |
| Verdict: | Malicious activity |
| Analysis date: | July 11, 2024, 09:25:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, MS CAB-Installer self-extracting archive |
| MD5: | C5BCC761BA5A2614B009045EAA2DEA21 |
| SHA1: | 3E228139C2EBD2A8A074BC019472FB3912CC577A |
| SHA256: | 7566ADB2E835C6C816ABAAE8AFEB4B7D0C275DD19969F94945EBEB09F558D933 |
| SSDEEP: | 98304:zlHih1z5Cl15Hys6FtGVBICcJeVc8fE1Zm8VIcEF35ya6Oh6flQZQ1FmlzidCBUo:zOEZqlve |
MALICIOUS
Drops the executable file immediately after the start
- msrdpcli.exe (PID: 3252)
- msiexec.exe (PID: 2900)
Changes the autorun value in the registry
- msrdpcli.exe (PID: 3252)
SUSPICIOUS
Starts a Microsoft application from unusual location
- msrdpcli.exe (PID: 3252)
Process drops legitimate windows executable
- msrdpcli.exe (PID: 3252)
- msiexec.exe (PID: 2900)
Executable content was dropped or overwritten
- msrdpcli.exe (PID: 3252)
Reads the history of recent RDP connections
- msiexec.exe (PID: 1476)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 2900)
Executes as Windows Service
- VSSVC.exe (PID: 996)
INFO
Checks supported languages
- msrdpcli.exe (PID: 3252)
- msiexec.exe (PID: 2900)
- setup.exe (PID: 540)
- msiexec.exe (PID: 1476)
Reads the computer name
- msrdpcli.exe (PID: 3252)
- msiexec.exe (PID: 2900)
- setup.exe (PID: 540)
- msiexec.exe (PID: 1476)
Reads the machine GUID from the registry
- msiexec.exe (PID: 2900)
- msiexec.exe (PID: 1476)
Create files in a temporary directory
- msrdpcli.exe (PID: 3252)
- msiexec.exe (PID: 2900)
- msiexec.exe (PID: 1504)
Creates a software uninstall entry
- msiexec.exe (PID: 2900)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2900)
Application launched itself
- msiexec.exe (PID: 2900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 MS Cabinet Self-Extractor (WExtract stub) (80.4) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (8.2) |
| .exe | | | Win64 Executable (generic) (7.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.7) |
| .exe | | | Win32 Executable (generic) (1.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2001:03:01 21:56:32+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 7 |
| CodeSize: | 34304 |
| InitializedDataSize: | 3435520 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5a8b |
| OSVersion: | 5.1 |
| ImageVersion: | 5.1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.0.2448.0 |
| ProductVersionNumber: | 6.0.2448.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Private build |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Win32 Cabinet Self-Extractor |
| FileVersion: | 6.00.2448.0000 (Lab04_N(rahulth).010206-1320) |
| InternalName: | Wextract |
| LegalCopyright: | Copyright (C) Microsoft Corporation. 1981-2001 |
| OriginalFileName: | WEXTRACT.EXE |
| ProductName: | Microsoft(R) Windows (R) 2000 Operating System |
| ProductVersion: | 6.00.2448.0000 |
Total processes
49
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\setup.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\setup.exe | msrdpcli.exe | ||||||||||||
User: admin Company: Installshield Software Corporation Integrity Level: HIGH Description: Setup Launcher Exit code: 0 Version: 1.10.0872 Modules
| |||||||||||||||
| 996 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1476 | C:\Windows\system32\MsiExec.exe -Embedding 49A6B7C0F8D9DF86A5C7DC244DE16352 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
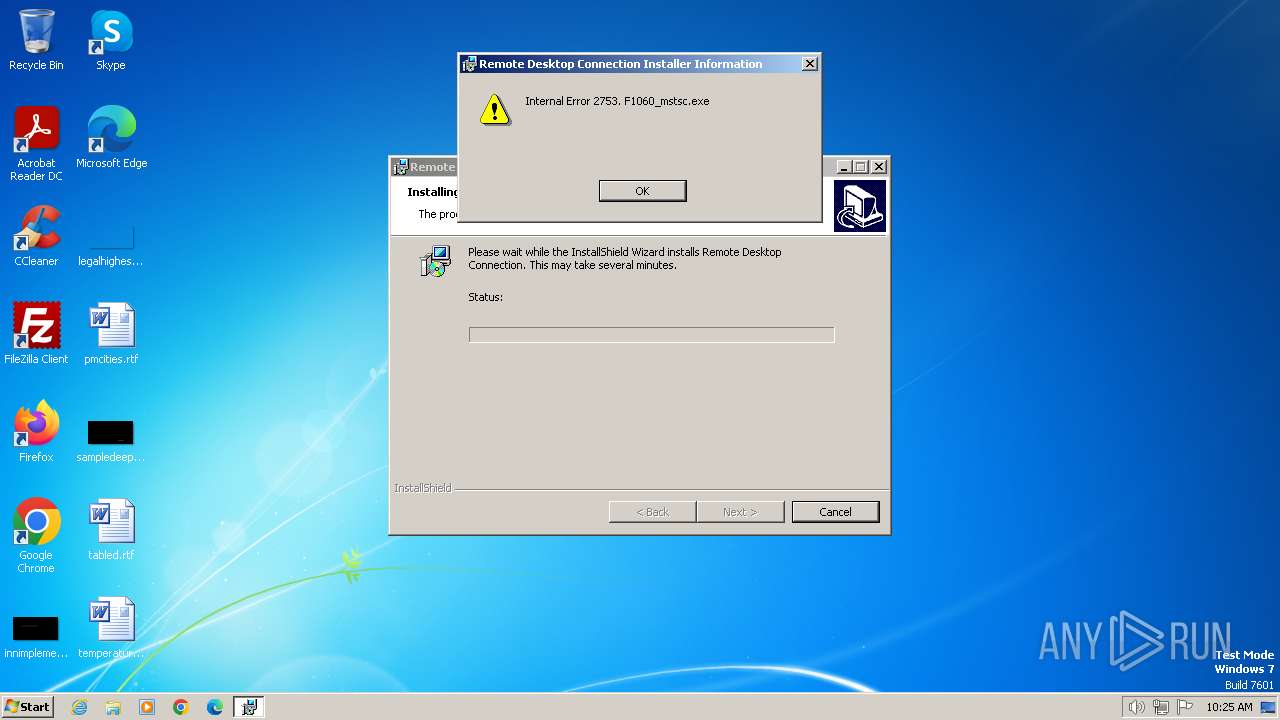
| 1504 | MSIEXEC.EXE /i "C:\Users\admin\AppData\Local\Temp\IXP000.TMP\msrdpcli.msi" | C:\Windows\System32\msiexec.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 1603 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2900 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3252 | "C:\Users\admin\AppData\Local\Temp\msrdpcli.exe" | C:\Users\admin\AppData\Local\Temp\msrdpcli.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 6.00.2448.0000 (Lab04_N(rahulth).010206-1320) Modules
| |||||||||||||||
| 3308 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\setup.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\setup.exe | — | msrdpcli.exe | |||||||||||
User: admin Company: Installshield Software Corporation Integrity Level: MEDIUM Description: Setup Launcher Exit code: 3221226540 Version: 1.10.0872 Modules
| |||||||||||||||
| 3332 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 199
Read events
4 952
Write events
234
Delete events
13
Modification events
| (PID) Process: | (3252) msrdpcli.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | wextract_cleanup0 |
Value: rundll32.exe C:\Windows\system32\advpack.dll,DelNodeRunDLL32 "C:\Users\admin\AppData\Local\Temp\IXP000.TMP\" | |||
| (PID) Process: | (2900) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000C0E3D84574D3DA01540B000090080000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2900) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000C0E3D84574D3DA01540B000090080000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2900) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 75 | |||
| (PID) Process: | (2900) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4000000000000000B62A824674D3DA01540B000090080000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2900) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000108D844674D3DA01540B0000640E0000E8030000010000000000000000000000AA33A9AD55EB9740BA62035EC7B32F310000000000000000 | |||
| (PID) Process: | (996) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000078168E4674D3DA01E4030000FC0D0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (996) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000078168E4674D3DA01E4030000580E0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (996) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000078168E4674D3DA01E4030000DC0C0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (996) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000078168E4674D3DA01E40300009C0D0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
15
Suspicious files
10
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2900 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2900 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{ada933aa-eb55-4097-ba62-035ec7b32f31}_OnDiskSnapshotProp | binary | |
MD5:E6C26E5F441E9CFD0166CC0F7D542EEF | SHA256:DFD2B1D357FDF16D0B1131EC9CD1B941AA85A91A39B1C0941CA9C8C5F8289DF4 | |||
| 2900 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:E6C26E5F441E9CFD0166CC0F7D542EEF | SHA256:DFD2B1D357FDF16D0B1131EC9CD1B941AA85A91A39B1C0941CA9C8C5F8289DF4 | |||
| 2900 | msiexec.exe | C:\Windows\Installer\531e5.msi | executable | |
MD5:13FB585D7981D700FBA8FB61C3584A72 | SHA256:792D59D9A0706193B291B4BAB0E2AC9DA12603062F67568228D381622367710B | |||
| 2900 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF2532232D96F4988A.TMP | gmc | |
MD5:E2002A69B2AD2E87F5CB5BA6CC13396F | SHA256:AAA0EB881C34E1854EF26DE9D885CA8DEBD06FC2184F6AF4499B3196B7CF95AF | |||
| 2900 | msiexec.exe | C:\Windows\Installer\531e6.ipi | binary | |
MD5:08E8F3100409B9CC2069916B250A8F02 | SHA256:093265093C2F5238D8EF6D9B82721BADCA927576D5E9A94AE63B2611C3F3B0F3 | |||
| 2900 | msiexec.exe | C:\Windows\Installer\MSI3530.tmp | executable | |
MD5:2F95867C8EB79AA8854729CC81DBAB46 | SHA256:F353F0BC443A6CB2BD0EB61B2B4413B2261376B89C7491CA120E19EF2C255C80 | |||
| 2900 | msiexec.exe | C:\Windows\Installer\MSI3581.tmp | executable | |
MD5:2F95867C8EB79AA8854729CC81DBAB46 | SHA256:F353F0BC443A6CB2BD0EB61B2B4413B2261376B89C7491CA120E19EF2C255C80 | |||
| 2900 | msiexec.exe | C:\Windows\Installer\MSI3591.tmp | executable | |
MD5:2F95867C8EB79AA8854729CC81DBAB46 | SHA256:F353F0BC443A6CB2BD0EB61B2B4413B2261376B89C7491CA120E19EF2C255C80 | |||
| 2900 | msiexec.exe | C:\Windows\Installer\MSI3570.tmp | executable | |
MD5:2F95867C8EB79AA8854729CC81DBAB46 | SHA256:F353F0BC443A6CB2BD0EB61B2B4413B2261376B89C7491CA120E19EF2C255C80 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
13
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 23.50.131.216:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1060 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8f69642324cc87bd | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1372 | svchost.exe | 23.50.131.216:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |