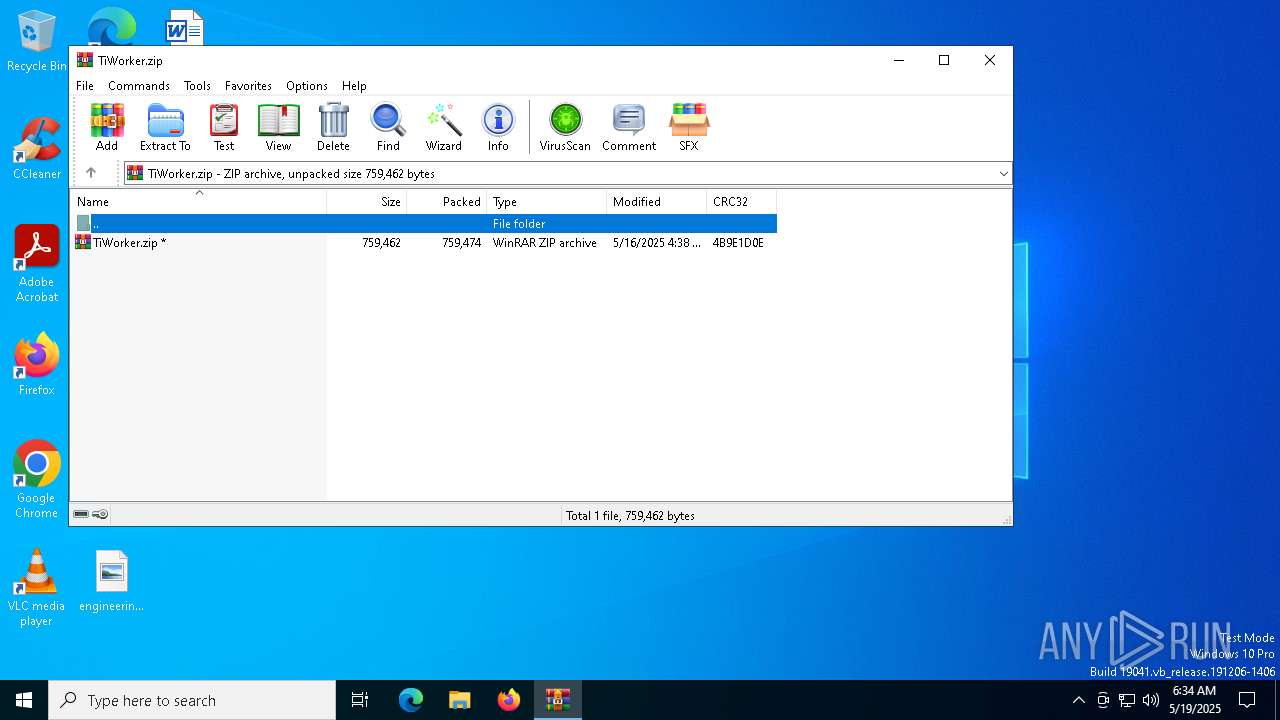
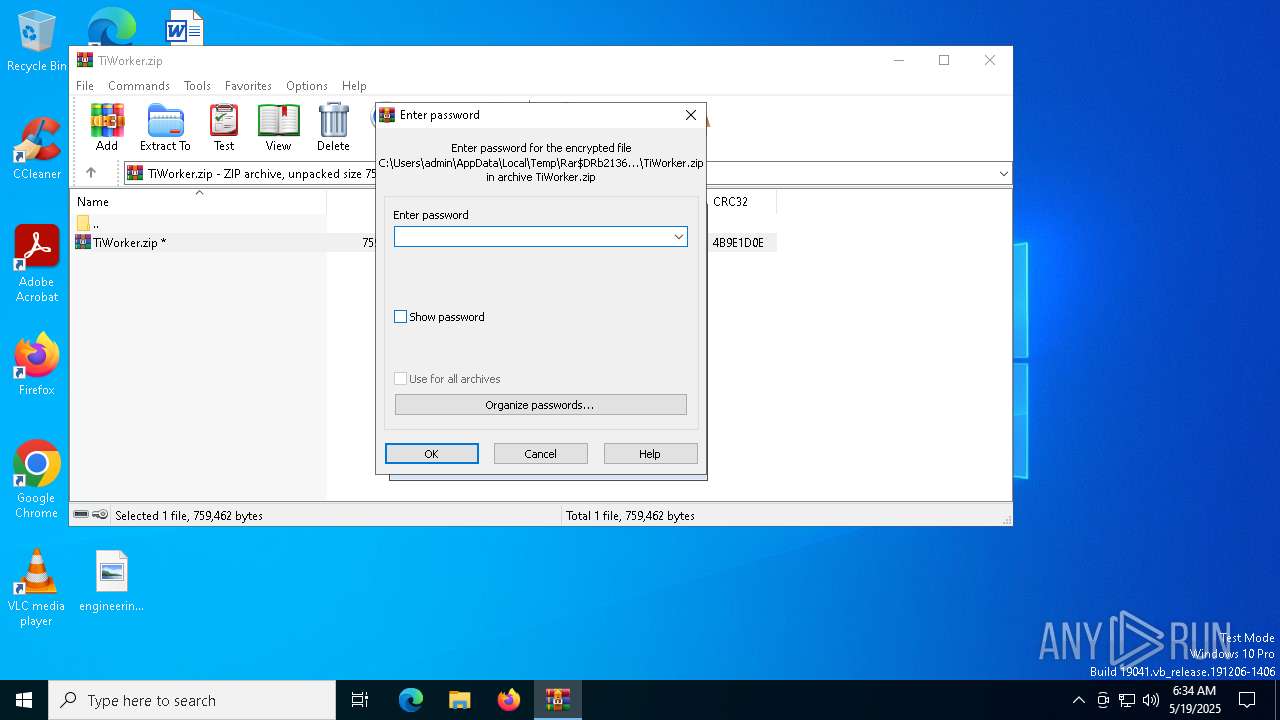
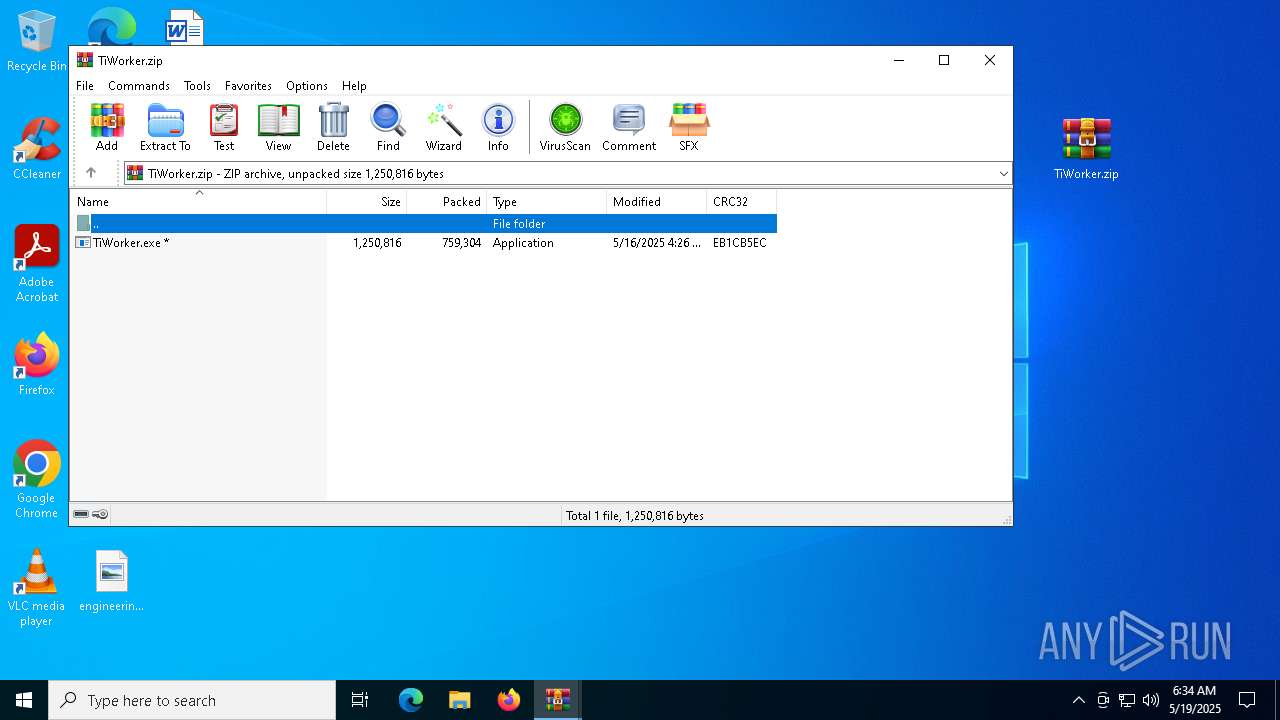
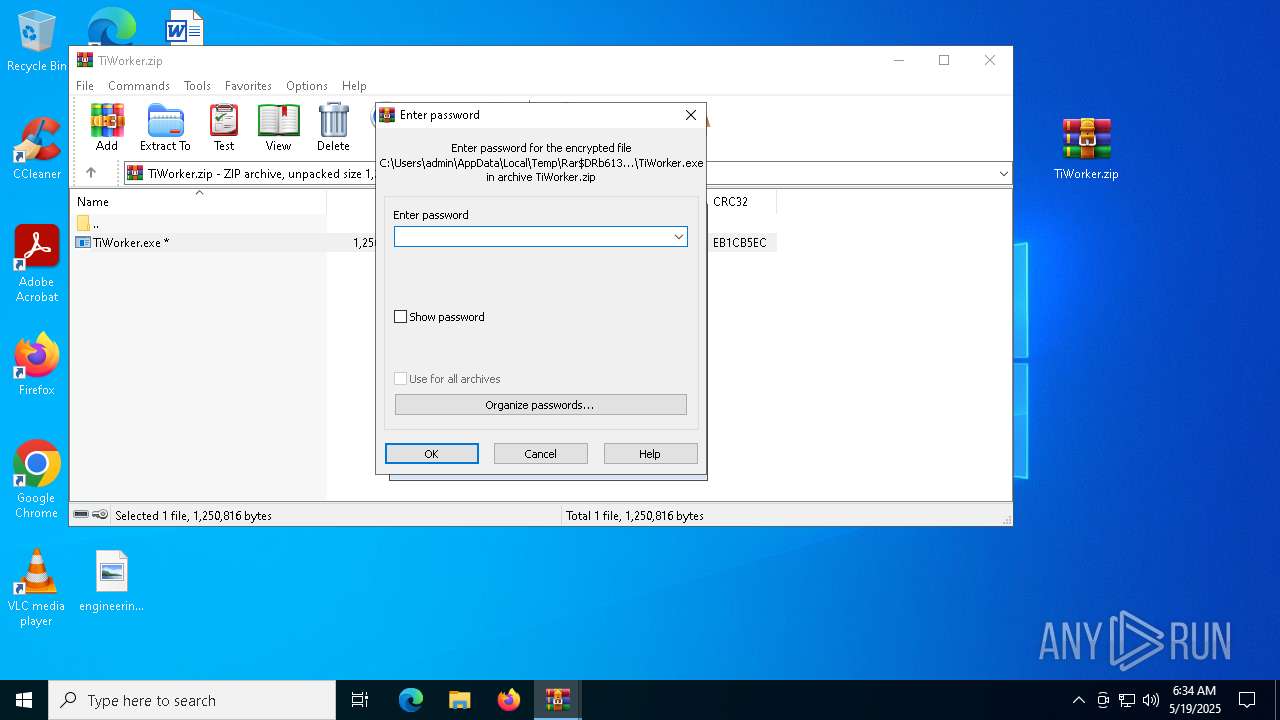
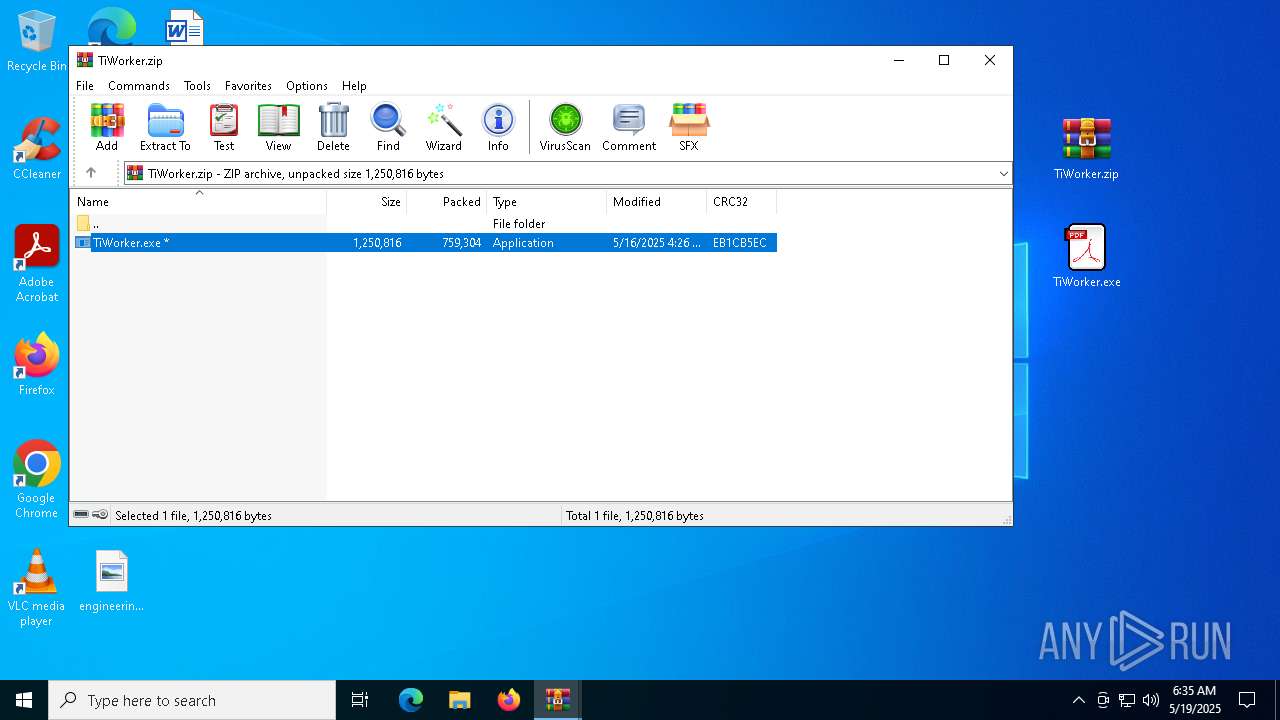
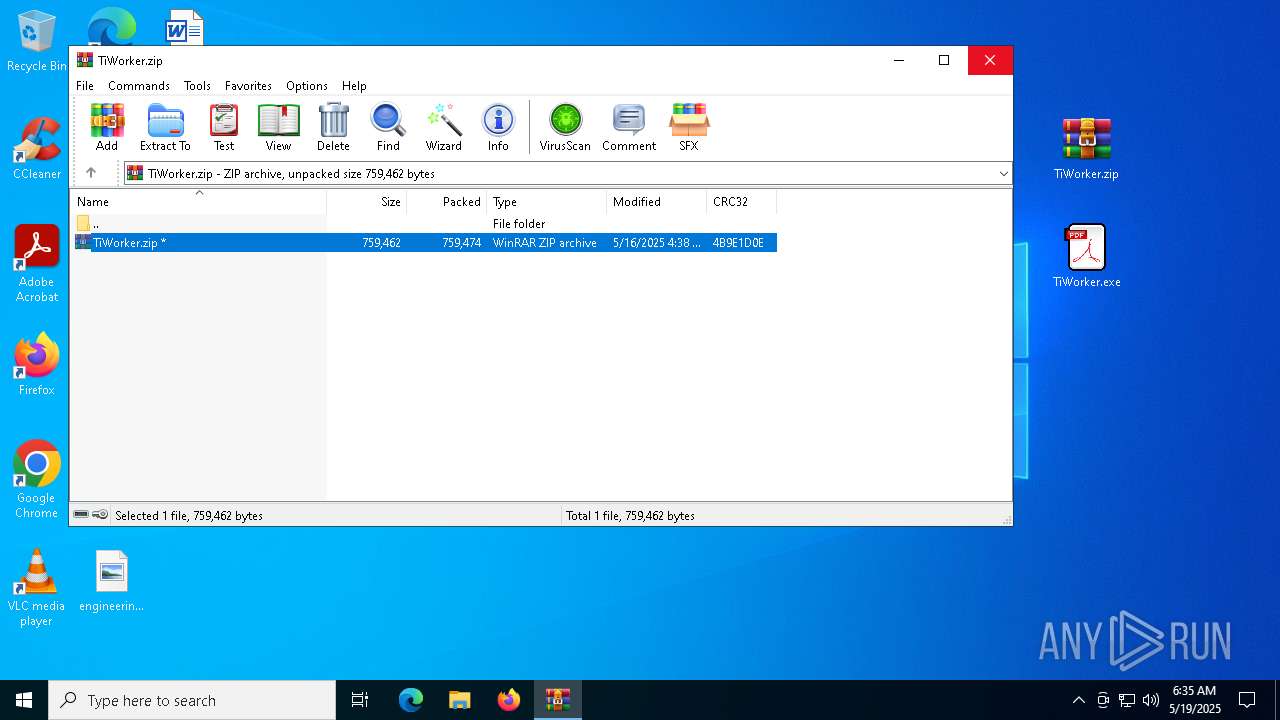
| File name: | TiWorker.zip |
| Full analysis: | https://app.any.run/tasks/7ba4e2c9-26e2-466a-8e37-c6a7693f0dfb |
| Verdict: | Malicious activity |
| Analysis date: | May 19, 2025, 06:34:35 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | BA7C769031E04EE7745FB09A00E8664F |
| SHA1: | 8657A075542AAE609C2864C8E7FD89FE3A654F8C |
| SHA256: | 75605490B9D7C94C55E0D824BFA9F4AB59C790292285FAF8DD85D1E25EB8565D |
| SSDEEP: | 24576:8yNuXj1O653Quzgv1b/6KxWQBl3DqeNTTxrBF9Ss7sE2TwqYDyfN4B0eKN7OinUi:8yNuXj1O653Quzgv1b/nxWQl3D7NTTxu |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2136)
SUSPICIOUS
Executes application which crashes
- TiWorker.exe (PID: 4944)
- TiWorker.exe (PID: 1184)
INFO
Manual execution by a user
- TiWorker.exe (PID: 1184)
- WinRAR.exe (PID: 6132)
- notepad++.exe (PID: 6740)
- TiWorker.exe (PID: 4944)
- mspaint.exe (PID: 856)
Reads mouse settings
- TiWorker.exe (PID: 1184)
- TiWorker.exe (PID: 4944)
Checks supported languages
- TiWorker.exe (PID: 1184)
- TiWorker.exe (PID: 4944)
Create files in a temporary directory
- TiWorker.exe (PID: 1184)
- TiWorker.exe (PID: 4944)
The sample compiled with english language support
- WinRAR.exe (PID: 2136)
- WinRAR.exe (PID: 6132)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6132)
Creates files or folders in the user directory
- WerFault.exe (PID: 5200)
- WerFault.exe (PID: 6828)
Reads the software policy settings
- slui.exe (PID: 5072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | None |
| ZipModifyDate: | 2025:05:16 16:38:58 |
| ZipCRC: | 0x4b9e1d0e |
| ZipCompressedSize: | 759474 |
| ZipUncompressedSize: | 759474 |
| ZipFileName: | TiWorker.zip |
Total processes
148
Monitored processes
13
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 668 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\engineeringshow.jpg" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | "C:\Users\admin\Desktop\TiWorker.exe" | C:\Users\admin\Desktop\TiWorker.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 1532 | "C:\Users\admin\Desktop\TiWorker.exe" | C:\Windows\SysWOW64\svchost.exe | — | TiWorker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 2136 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\TiWorker.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4944 | "C:\Users\admin\Desktop\TiWorker.exe" | C:\Users\admin\Desktop\TiWorker.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 5072 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5200 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 1184 -s 696 | C:\Windows\SysWOW64\WerFault.exe | — | TiWorker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6132 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\TiWorker.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
7 511
Read events
7 438
Write events
69
Delete events
4
Modification events
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\TiWorker.zip | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6132) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
Executable files
1
Suspicious files
11
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5200 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_TiWorker.exe_55ce2d8080ff10a9f113a930f4f8ed3817cbe7e_d8632c2d_840e7a25-19b6-4d27-871b-c7556b21509f\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6828 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_TiWorker.exe_55ce2d8080ff10a9f113a930f4f8ed3817cbe7e_d8632c2d_65f7ca4a-ef70-41fd-bf10-f60e6b1f629a\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5200 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER17DB.tmp.WERInternalMetadata.xml | binary | |
MD5:4BC31C9C7058A8B128708C07EE5ACB48 | SHA256:534B2D174A8643CE75741DE6860F2B46AF8633E6F06D3DF1A3C193FCD3C64926 | |||
| 5200 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER16A2.tmp.dmp | binary | |
MD5:FF23348C801CE514A43F75DBEE236C59 | SHA256:7CB823635242DEC7AD3F3F48DE9669A93AC9FBD2F6DC60F4CFD224D577AEE5F7 | |||
| 5200 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\TiWorker.exe.1184.dmp | binary | |
MD5:54EAB19C1DCCE9CE8AD8B03909805928 | SHA256:459186388AA4D79DFAA760CF4BC6B4ACA6EB9BE700E9D4C8C4A2BD3C4D3349EF | |||
| 6740 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\plugins\config\converter.ini | text | |
MD5:F70F579156C93B097E656CABA577A5C9 | SHA256:B926498A19CA95DC28964B7336E5847107DD3C0F52C85195C135D9DD6CA402D4 | |||
| 5200 | WerFault.exe | C:\Windows\appcompat\Programs\Amcache.hve | binary | |
MD5:2EE234E098A654CE0521D814A51FA69A | SHA256:40FF66AE288920BF3CF2CE6936327A53FFD581250AA1AF22B2F24A45CCA83D68 | |||
| 6828 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER305F.tmp.dmp | binary | |
MD5:C40B647980EB86D9976DD257F8717CAB | SHA256:6E989E8F04477C0F04DFDBF6436B50FEFD2167E041DB2828FBB136204F79E8B4 | |||
| 6740 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\shortcuts.xml | text | |
MD5:F11D96162BC521F5CF49FFE6B6841C9B | SHA256:BE9AEAEAB5A2E4899BA7E582274BA592C1B9BAF688B340A754B8EF32B23CFA9C | |||
| 6740 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\config.xml | xml | |
MD5:A2ED875AA42589077C4D08F4F8912018 | SHA256:77B0174D655F327C1FC9520B4F8831ECD82E98351B26BB9C2EDD98FF0CD63A2D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
22
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
632 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
632 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |