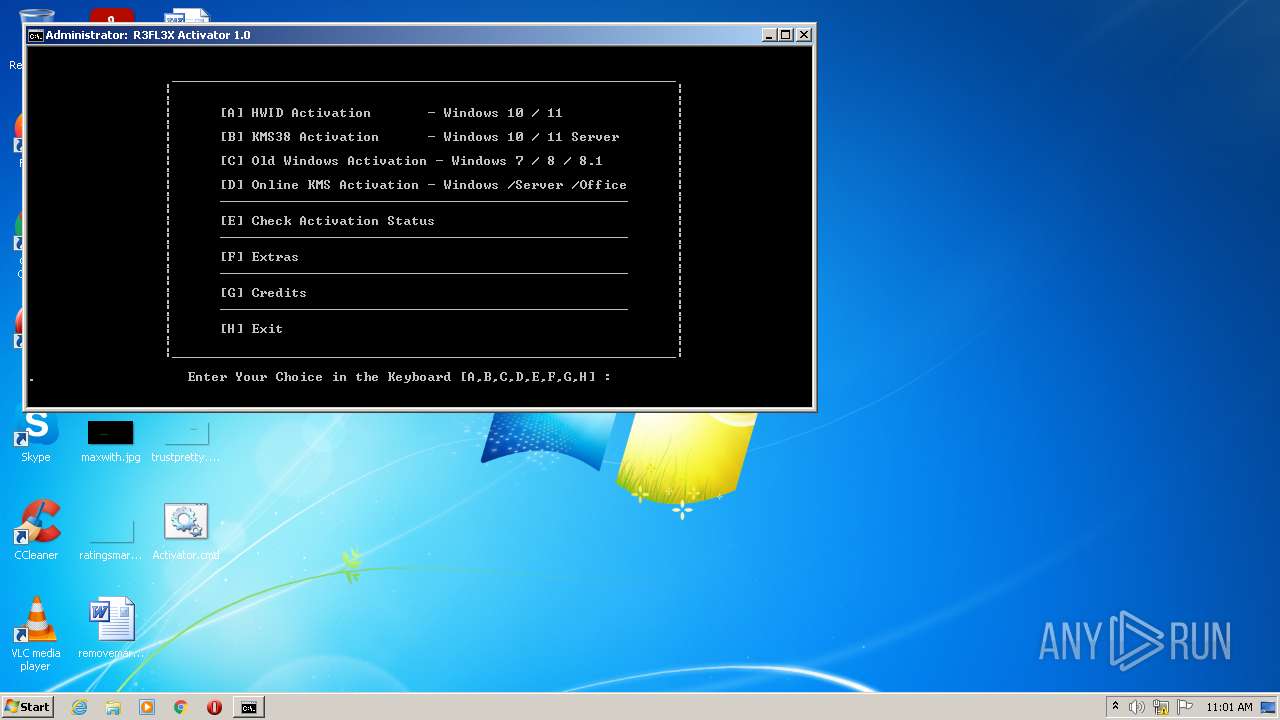
| File name: | Activator.cmd |
| Full analysis: | https://app.any.run/tasks/74a9fc13-c17c-4e15-b291-001ee2064c22 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 10:00:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 40FA4448A78F5AC2CD035CA172FDF30C |
| SHA1: | 0EABEFD14F50F9F0FFD2BF077F5EC3A3637D2C6E |
| SHA256: | 755AD56525460AB71725B77797922BE622A3EA8AAFCBC49C489BDFE11A4852C4 |
| SSDEEP: | 49152:XMLDN/hZw3m99EkHDu5xnAHItDatbEANPpxU/:SEm8kHS56oEy |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3160)
- cscript.exe (PID: 4036)
- cmd.exe (PID: 1080)
Checks supported languages
- cmd.exe (PID: 3160)
- cmd.exe (PID: 3384)
- cmd.exe (PID: 3280)
- cmd.exe (PID: 3604)
- cmd.exe (PID: 3104)
- cscript.exe (PID: 4036)
- cmd.exe (PID: 1080)
- cmd.exe (PID: 1952)
- cmd.exe (PID: 2968)
- mode.com (PID: 964)
Application launched itself
- cmd.exe (PID: 3160)
- cmd.exe (PID: 1080)
Executes scripts
- cmd.exe (PID: 3160)
Reads the computer name
- cscript.exe (PID: 4036)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 3160)
- cmd.exe (PID: 1080)
Starts CHOICE.EXE (used to create a delay)
- cmd.exe (PID: 1080)
INFO
Checks supported languages
- findstr.exe (PID: 3440)
- reg.exe (PID: 3768)
- reg.exe (PID: 1872)
- findstr.exe (PID: 3148)
- choice.exe (PID: 3404)
Checks Windows Trust Settings
- cscript.exe (PID: 4036)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
53
Monitored processes
15
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 964 | mode con cols=98 lines=30 | C:\Windows\system32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1080 | "C:\Windows\System32\cmd.exe" /c set -ElevError=Y&call "C:\Users\admin\Desktop\Activator.cmd" | C:\Windows\System32\cmd.exe | cscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1872 | reg query HKU\S-1-5-19 | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1952 | C:\Windows\system32\cmd.exe /c ver | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2968 | C:\Windows\system32\cmd.exe /c "prompt #$H#$E# & echo on & for %b in (1) do rem" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3104 | cmd /v:on /c echo(^!param^! | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3148 | findstr /R "[| ` ~ ! @ % \^ & ( ) \[ \] { } + = ; ' , |]*^" | C:\Windows\system32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3160 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\Activator.cmd" " | C:\Windows\system32\cmd.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3280 | C:\Windows\system32\cmd.exe /c "prompt #$H#$E# & echo on & for %b in (1) do rem" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3384 | C:\Windows\system32\cmd.exe /c ver | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
378
Read events
370
Write events
8
Delete events
0
Modification events
| (PID) Process: | (4036) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4036) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4036) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4036) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3160 | cmd.exe | C:\Users\admin\AppData\Local\Temp\elev.vbs | text | |
MD5:EFD88876976646C181001D1AFACFFF6E | SHA256:28DCB1CA4FA7B99BD64DC57F8E754A7DB595B4FE76258327241B53A052F3E73D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report