| URL: | https://www.gpg4win.org/download.html |
| Full analysis: | https://app.any.run/tasks/efe1b154-8a24-48dc-a7bc-597b2446d184 |
| Verdict: | Malicious activity |
| Analysis date: | July 25, 2024, 09:29:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | EB1013098CC1013FE51E8136E35D9AE7 |
| SHA1: | 89FB1599C66FFE9E6EDFBD7F243FA6FBEF434F72 |
| SHA256: | 75296B5B84DEB8CD77BDA0C4603C37D6E46E10BC3181DFBDD3A616DB40E5DE8A |
| SSDEEP: | 3:N8DSLb/K53Q:2OLK3Q |
MALICIOUS
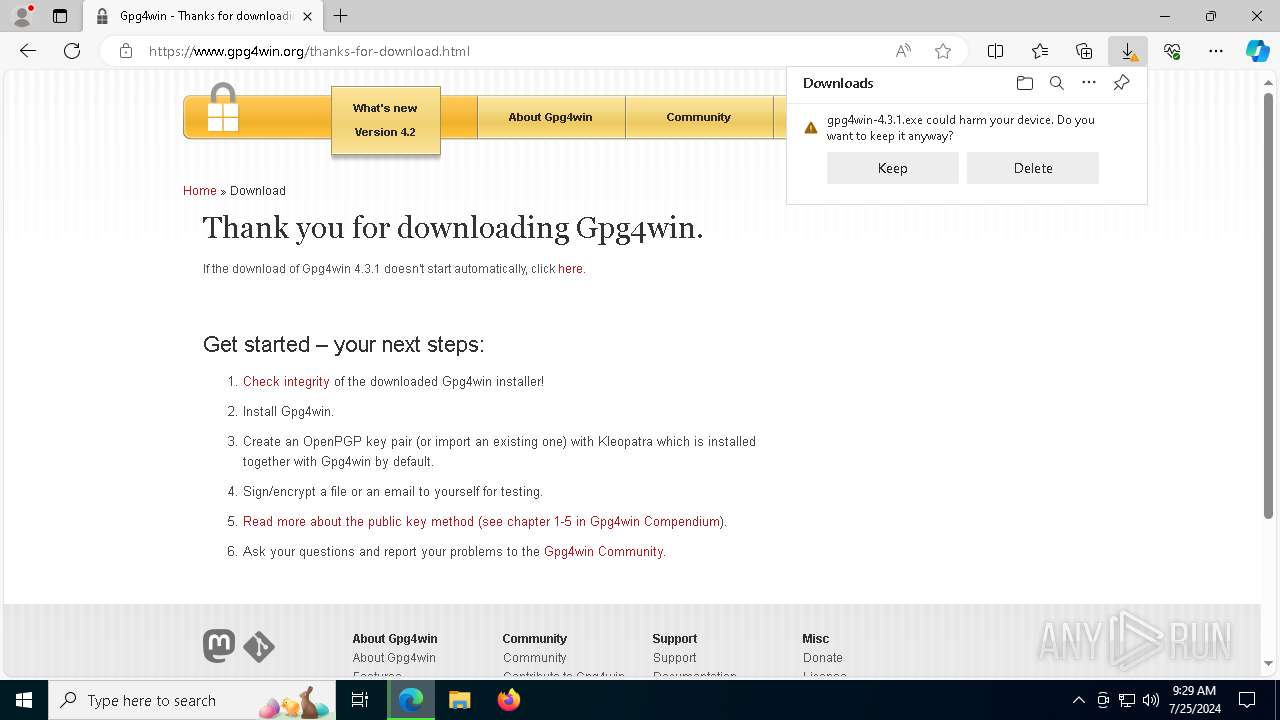
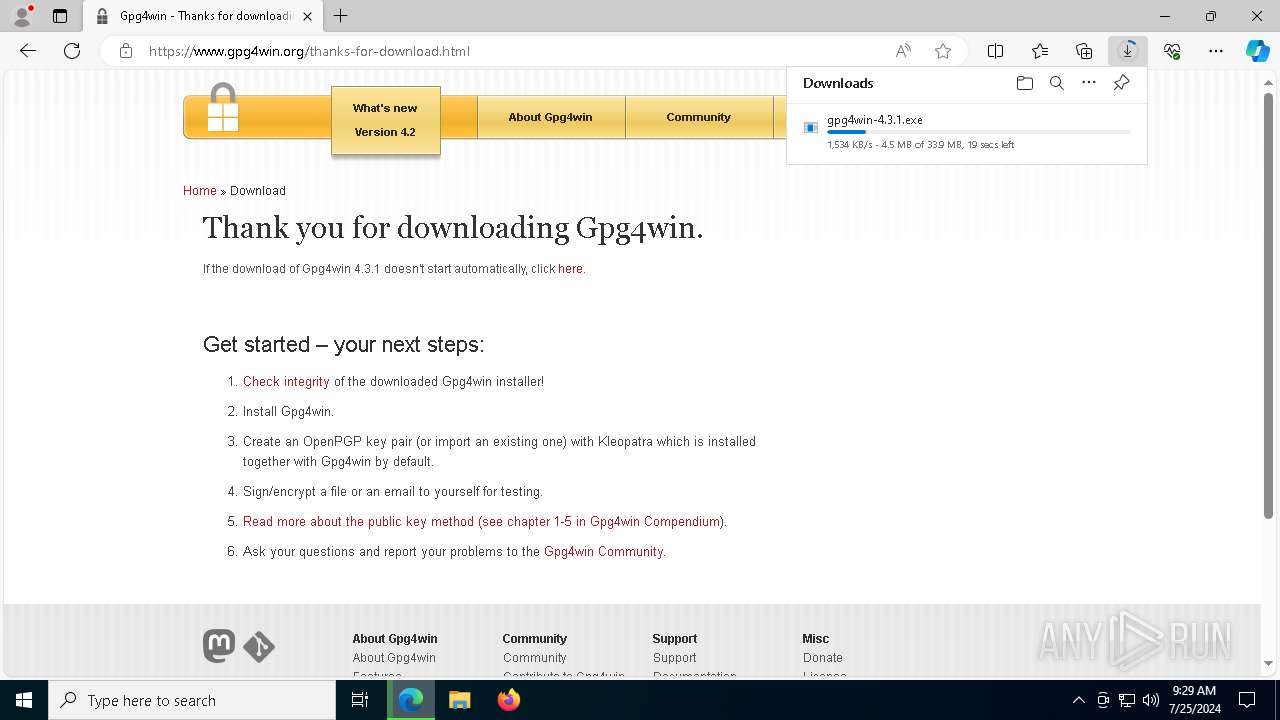
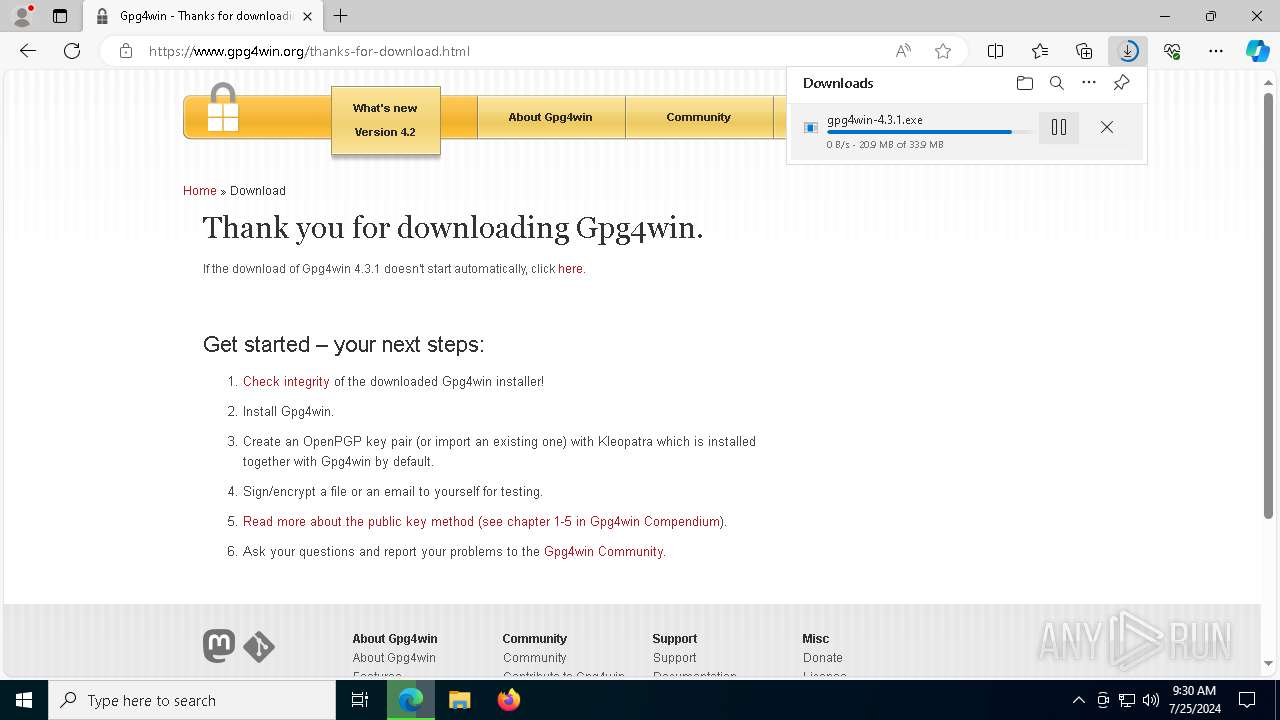
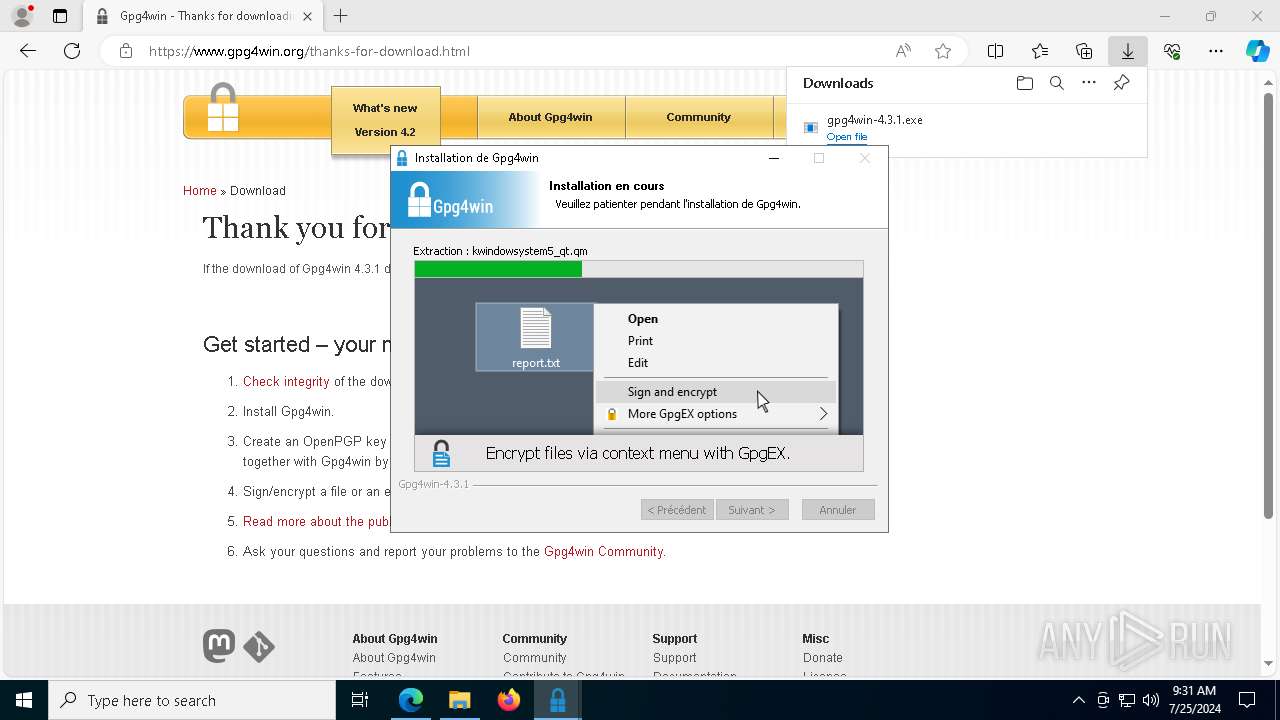
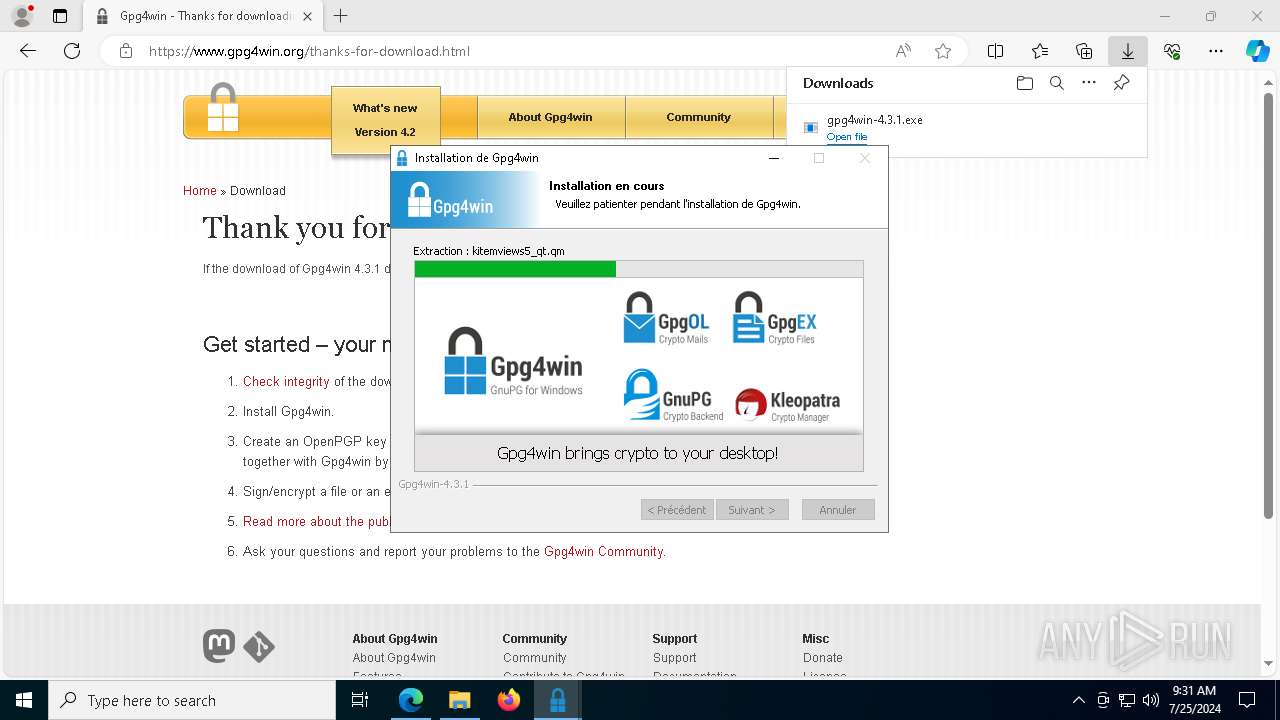
Drops the executable file immediately after the start
- gpg4win-4.3.1.exe (PID: 6400)
- gpg4win-4.3.1.exe (PID: 4272)
- gnupg-w32-2.4.5_20240307-bin.exe (PID: 1676)
- gpg4win-4.3.1.exe (PID: 7456)
Registers / Runs the DLL via REGSVR32.EXE
- gpg4win-4.3.1.exe (PID: 7456)
SUSPICIOUS
Reads security settings of Internet Explorer
- cookie_exporter.exe (PID: 4188)
- gpg4win-4.3.1.exe (PID: 7456)
Executable content was dropped or overwritten
- gpg4win-4.3.1.exe (PID: 6400)
- gpg4win-4.3.1.exe (PID: 4272)
- gnupg-w32-2.4.5_20240307-bin.exe (PID: 1676)
- gpg4win-4.3.1.exe (PID: 7456)
The process creates files with name similar to system file names
- gpg4win-4.3.1.exe (PID: 7456)
- gnupg-w32-2.4.5_20240307-bin.exe (PID: 1676)
Reads Microsoft Outlook installation path
- gpg4win-4.3.1.exe (PID: 7456)
Malware-specific behavior (creating "System.dll" in Temp)
- gpg4win-4.3.1.exe (PID: 7456)
- gnupg-w32-2.4.5_20240307-bin.exe (PID: 1676)
Creates a software uninstall entry
- gnupg-w32-2.4.5_20240307-bin.exe (PID: 1676)
- gpg4win-4.3.1.exe (PID: 7456)
Creates/Modifies COM task schedule object
- gpg4win-4.3.1.exe (PID: 7456)
- regsvr32.exe (PID: 8172)
- regsvr32.exe (PID: 6324)
INFO
Reads the computer name
- identity_helper.exe (PID: 4112)
- cookie_exporter.exe (PID: 4188)
- gpg4win-4.3.1.exe (PID: 7456)
- gpg4win-4.3.1.exe (PID: 6400)
- gpg4win-4.3.1.exe (PID: 4272)
- gnupg-w32-2.4.5_20240307-bin.exe (PID: 1676)
- kleopatra.exe (PID: 6400)
- scdaemon.exe (PID: 1028)
- TextInputHost.exe (PID: 5628)
Reads Microsoft Office registry keys
- msedge.exe (PID: 464)
Reads Environment values
- identity_helper.exe (PID: 4112)
- cookie_exporter.exe (PID: 4188)
Checks supported languages
- identity_helper.exe (PID: 4112)
- cookie_exporter.exe (PID: 4188)
- gnupg-w32-2.4.5_20240307-bin.exe (PID: 1676)
- gpg4win-4.3.1.exe (PID: 4272)
- gpg4win-4.3.1.exe (PID: 6400)
- kleopatra.exe (PID: 6400)
- gpgme-w32spawn.exe (PID: 7572)
- gpgconf.exe (PID: 7200)
- gpgme-w32spawn.exe (PID: 5080)
- gpgme-w32spawn.exe (PID: 7760)
- gpgme-w32spawn.exe (PID: 3800)
- gpgconf.exe (PID: 2776)
- gpg.exe (PID: 7896)
- gpgsm.exe (PID: 528)
- gpgme-w32spawn.exe (PID: 5548)
- gpgconf.exe (PID: 7728)
- gpgconf.exe (PID: 1816)
- gpg-agent.exe (PID: 7644)
- gpg-connect-agent.exe (PID: 6732)
- gpgme-w32spawn.exe (PID: 2792)
- gpgconf.exe (PID: 5856)
- dirmngr.exe (PID: 7508)
- gpgconf.exe (PID: 2924)
- gpg.exe (PID: 5788)
- gpgconf.exe (PID: 7252)
- gpg.exe (PID: 7224)
- gpgme-w32spawn.exe (PID: 7816)
- gpgsm.exe (PID: 4940)
- gpgconf.exe (PID: 7924)
- gpgsm.exe (PID: 7908)
- gpg-agent.exe (PID: 5684)
- gpgme-w32spawn.exe (PID: 4476)
- gpg-agent.exe (PID: 5628)
- gpg-agent.exe (PID: 7520)
- scdaemon.exe (PID: 7008)
- gpgme-w32spawn.exe (PID: 4304)
- gpgconf.exe (PID: 6344)
- scdaemon.exe (PID: 3404)
- gpgme-w32spawn.exe (PID: 7504)
- keyboxd.exe (PID: 1164)
- gpgme-w32spawn.exe (PID: 8180)
- gpgconf.exe (PID: 4660)
- gpgconf.exe (PID: 5664)
- keyboxd.exe (PID: 1124)
- gpg4win-4.3.1.exe (PID: 7456)
- gpgme-w32spawn.exe (PID: 7412)
- gpgconf.exe (PID: 7272)
- gpgme-w32spawn.exe (PID: 8136)
- dirmngr.exe (PID: 7212)
- dirmngr.exe (PID: 6352)
- gpgconf.exe (PID: 8108)
- gpgme-w32spawn.exe (PID: 6752)
- gpgconf.exe (PID: 3112)
- gpgme-w32spawn.exe (PID: 7832)
- gpgsm.exe (PID: 4132)
- gpgme-w32spawn.exe (PID: 7076)
- gpg.exe (PID: 2824)
- keyboxd.exe (PID: 7676)
- scdaemon.exe (PID: 1028)
- gpgme-w32spawn.exe (PID: 6180)
- gpg.exe (PID: 6760)
- gpgme-w32spawn.exe (PID: 3376)
- gpgsm.exe (PID: 8120)
- TextInputHost.exe (PID: 5628)
Checks proxy server information
- cookie_exporter.exe (PID: 4188)
- slui.exe (PID: 1544)
Reads the software policy settings
- slui.exe (PID: 1544)
Drops the executable file immediately after the start
- msedge.exe (PID: 464)
Executable content was dropped or overwritten
- msedge.exe (PID: 464)
The process uses the downloaded file
- msedge.exe (PID: 7908)
- msedge.exe (PID: 464)
Application launched itself
- msedge.exe (PID: 464)
Create files in a temporary directory
- gpg4win-4.3.1.exe (PID: 6400)
- gpg4win-4.3.1.exe (PID: 4272)
- gnupg-w32-2.4.5_20240307-bin.exe (PID: 1676)
- kleopatra.exe (PID: 6400)
- gpg4win-4.3.1.exe (PID: 7456)
Creates files in the program directory
- gnupg-w32-2.4.5_20240307-bin.exe (PID: 1676)
- gpg4win-4.3.1.exe (PID: 7456)
Dropped object may contain TOR URL's
- gnupg-w32-2.4.5_20240307-bin.exe (PID: 1676)
Manual execution by a user
- kleopatra.exe (PID: 6400)
Reads the machine GUID from the registry
- kleopatra.exe (PID: 6400)
- gpg-agent.exe (PID: 5684)
- keyboxd.exe (PID: 7676)
- scdaemon.exe (PID: 1028)
Creates files or folders in the user directory
- gpg-connect-agent.exe (PID: 6732)
- kleopatra.exe (PID: 6400)
- gpgconf.exe (PID: 7200)
- gpg-agent.exe (PID: 5684)
- gpgsm.exe (PID: 4132)
- gpg.exe (PID: 2824)
- scdaemon.exe (PID: 1028)
- keyboxd.exe (PID: 7676)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
301
Monitored processes
149
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 464 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --from-ie-to-edge=8 -- "https://www.gpg4win.org/download.html" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 528 | "C:\\\\Program Files (x86)\\\\GnuPG\\\\bin\\\\gpgsm.exe" "--version" | C:\Program Files (x86)\GnuPG\bin\gpgsm.exe | — | gpgme-w32spawn.exe | |||||||||||
User: admin Company: g10 Code GmbH Integrity Level: MEDIUM Description: GnuPG’s X.509/CMS tool Exit code: 0 Version: 2.4.5 (cbff323b3) built on <anon> at <none> Modules
| |||||||||||||||
| 712 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5932 --field-trial-handle=2372,i,5453772331573795500,7475242618037207700,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 712 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_collections.mojom.CollectionsDataManager --lang=en-US --service-sandbox-type=collections --no-appcompat-clear --mojo-platform-channel-handle=5288 --field-trial-handle=2372,i,5453772331573795500,7475242618037207700,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 892 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1028 | "C:\Program Files (x86)\GnuPG\bin\scdaemon.exe" --multi-server | C:\Program Files (x86)\GnuPG\bin\scdaemon.exe | — | gpg-agent.exe | |||||||||||
User: admin Company: g10 Code GmbH Integrity Level: MEDIUM Description: GnuPG’s smartcard daemon Version: 2.4.5 (cbff323b3) built on <anon> at <none> Modules
| |||||||||||||||
| 1080 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | gpgconf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1124 | "C:\Program Files (x86)\GnuPG\bin\keyboxd.exe" --gpgconf-list | C:\Program Files (x86)\GnuPG\bin\keyboxd.exe | — | gpgconf.exe | |||||||||||
User: admin Company: g10 Code GmbH Integrity Level: MEDIUM Description: GnuPG’s public key daemon Exit code: 0 Version: 2.4.5 (cbff323b3) built on <anon> at <none> Modules
| |||||||||||||||
| 1148 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5496 --field-trial-handle=2372,i,5453772331573795500,7475242618037207700,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1156 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3708 --field-trial-handle=2372,i,5453772331573795500,7475242618037207700,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
35 648
Read events
35 416
Write events
226
Delete events
6
Modification events
| (PID) Process: | (1328) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkLowPart |
Value: 0 | |||
| (PID) Process: | (1328) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkHighPart |
Value: 0 | |||
| (PID) Process: | (1328) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 0 | |||
| (PID) Process: | (1328) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 0 | |||
| (PID) Process: | (1328) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (1328) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31121013 | |||
| (PID) Process: | (1328) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1328) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1328) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1328) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
Executable files
138
Suspicious files
1 095
Text files
254
Unknown types
255
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RFe1f7a.TMP | — | |
MD5:— | SHA256:— | |||
| 464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RFe1fb9.TMP | — | |
MD5:— | SHA256:— | |||
| 464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RFe1fb9.TMP | — | |
MD5:— | SHA256:— | |||
| 464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RFe1fb9.TMP | — | |
MD5:— | SHA256:— | |||
| 464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RFe1fc8.TMP | — | |
MD5:— | SHA256:— | |||
| 464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
113
DNS requests
86
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7232 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5272 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5272 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7172 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7280 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68eda192-d0f3-46cf-b3be-1a828f951b21?P1=1722412312&P2=404&P3=2&P4=PgKVq77Rj2sfhbdaFbW2J9zPQ5kRR6rVyUZXBhRFnPD8vd340TzK0GQApVzwDkGnCaopejBGWqUuHONjghOfrQ%3d%3d | unknown | — | — | whitelisted |
7280 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68eda192-d0f3-46cf-b3be-1a828f951b21?P1=1722412312&P2=404&P3=2&P4=PgKVq77Rj2sfhbdaFbW2J9zPQ5kRR6rVyUZXBhRFnPD8vd340TzK0GQApVzwDkGnCaopejBGWqUuHONjghOfrQ%3d%3d | unknown | — | — | whitelisted |
7280 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68eda192-d0f3-46cf-b3be-1a828f951b21?P1=1722412312&P2=404&P3=2&P4=PgKVq77Rj2sfhbdaFbW2J9zPQ5kRR6rVyUZXBhRFnPD8vd340TzK0GQApVzwDkGnCaopejBGWqUuHONjghOfrQ%3d%3d | unknown | — | — | whitelisted |
7280 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68eda192-d0f3-46cf-b3be-1a828f951b21?P1=1722412312&P2=404&P3=2&P4=PgKVq77Rj2sfhbdaFbW2J9zPQ5kRR6rVyUZXBhRFnPD8vd340TzK0GQApVzwDkGnCaopejBGWqUuHONjghOfrQ%3d%3d | unknown | — | — | whitelisted |
7280 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68eda192-d0f3-46cf-b3be-1a828f951b21?P1=1722412312&P2=404&P3=2&P4=PgKVq77Rj2sfhbdaFbW2J9zPQ5kRR6rVyUZXBhRFnPD8vd340TzK0GQApVzwDkGnCaopejBGWqUuHONjghOfrQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3704 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6012 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3220 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6956 | msedge.exe | 46.4.134.23:443 | www.gpg4win.org | Hetzner Online GmbH | DE | unknown |
464 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6956 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6956 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6956 | msedge.exe | 13.107.246.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.gpg4win.org |
| unknown |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
www.bing.com |
| whitelisted |
xpaywalletcdn.azureedge.net |
| whitelisted |
Threats
Process | Message |
|---|---|
gpg4win-4.3.1.exe | Created: |
gpg4win-4.3.1.exe | CLSID\{42d30988-1a3a-11da-c687-000d6080e735} |
regsvr32.exe | Created: |
regsvr32.exe | CLSID\{42d30988-1a3a-11da-c687-000d6080e735} |
kleopatra.exe | org.kde.pim.kleopatra: Created responder: "kleopatraResponder" with handle: 0x602b2
|
kleopatra.exe | org.kde.pim.kleopatra: Startup timing: 115 ms: Service created
|
kleopatra.exe | org.kde.pim.kleopatra: Application created
|
kleopatra.exe | org.kde.pim.kleopatra: Startup timing: 111 ms: Application created
|
kleopatra.exe | org.kde.pim.kleopatra: Responder handle: 0x0
|
kleopatra.exe | org.kde.pim.kleopatra: Startup timing: 120 ms: GPGME Initialized
|