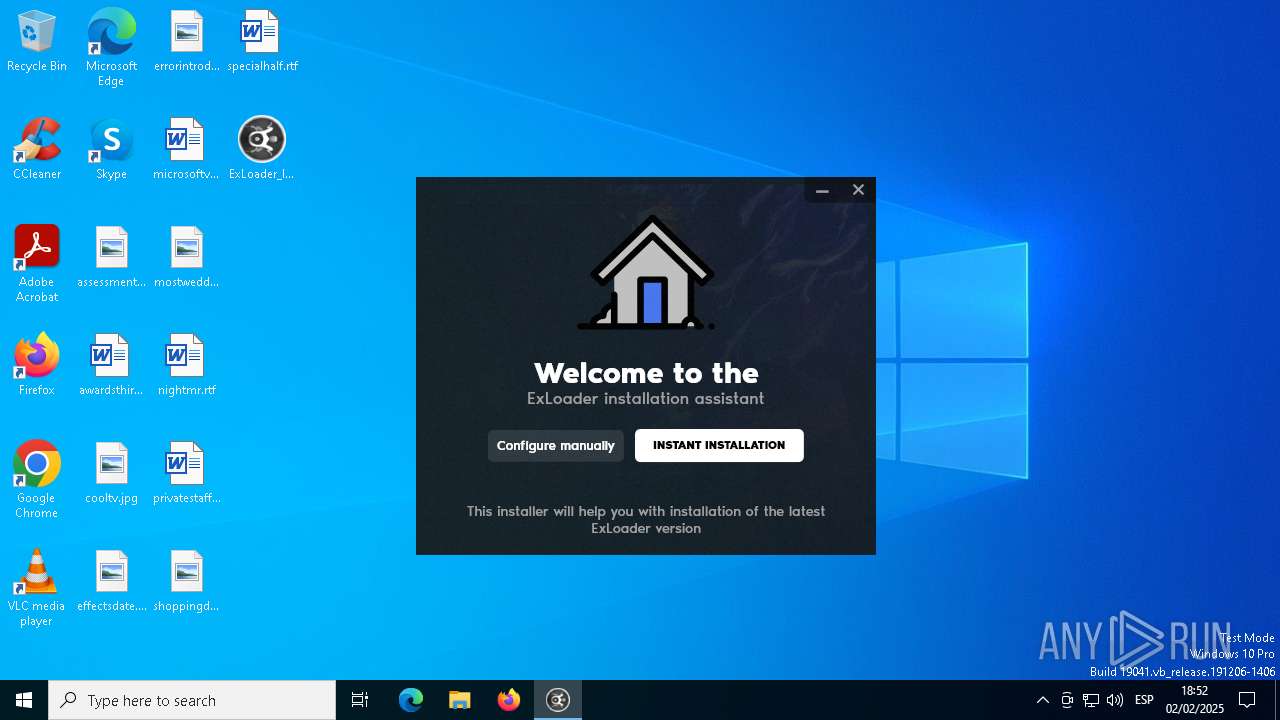
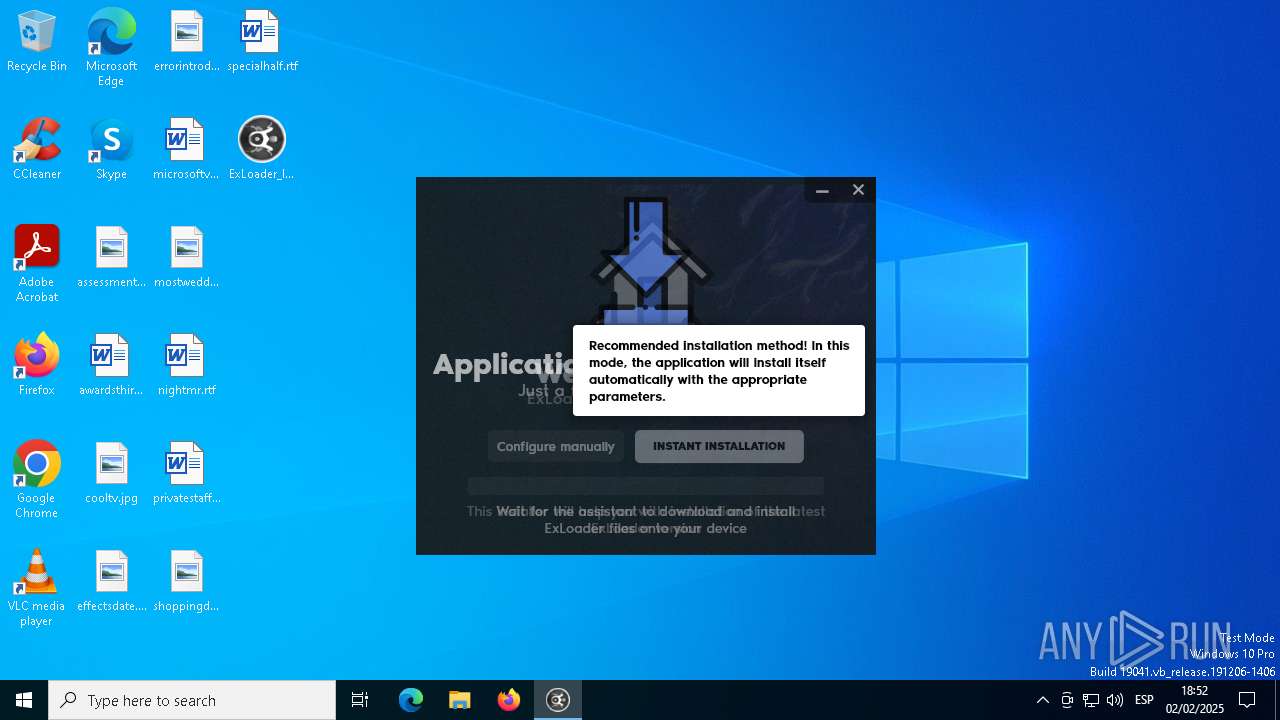
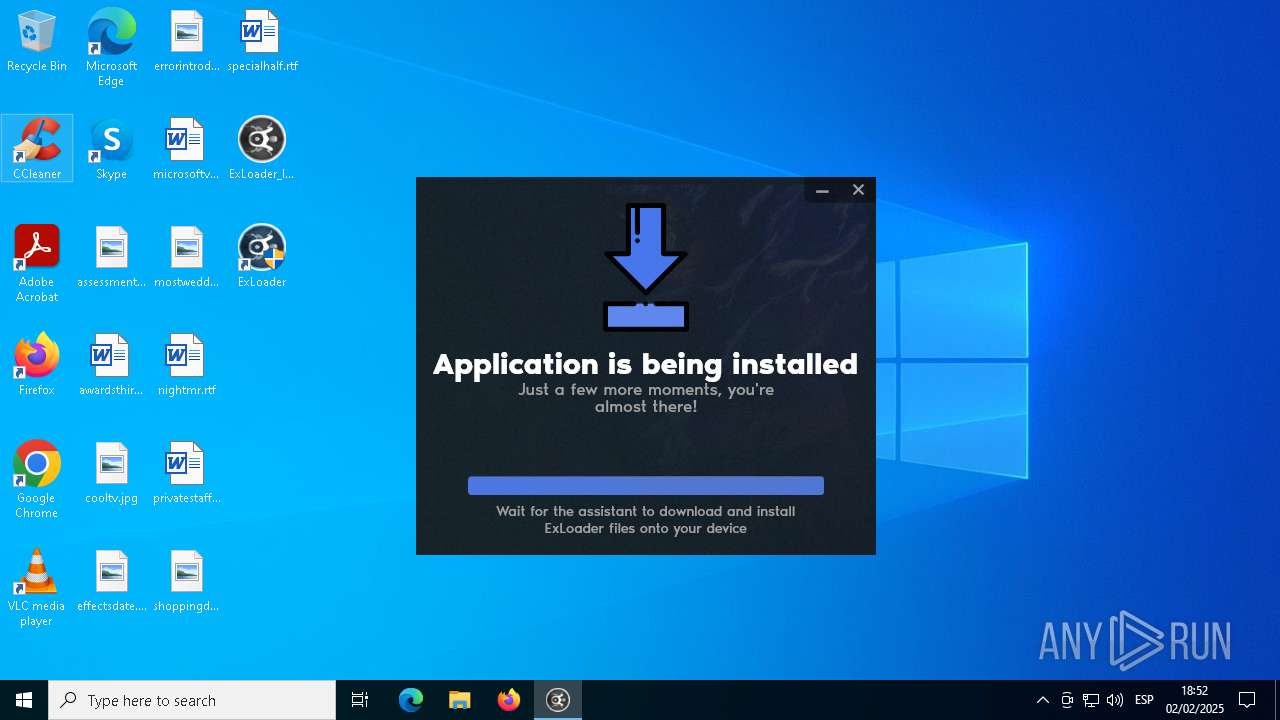
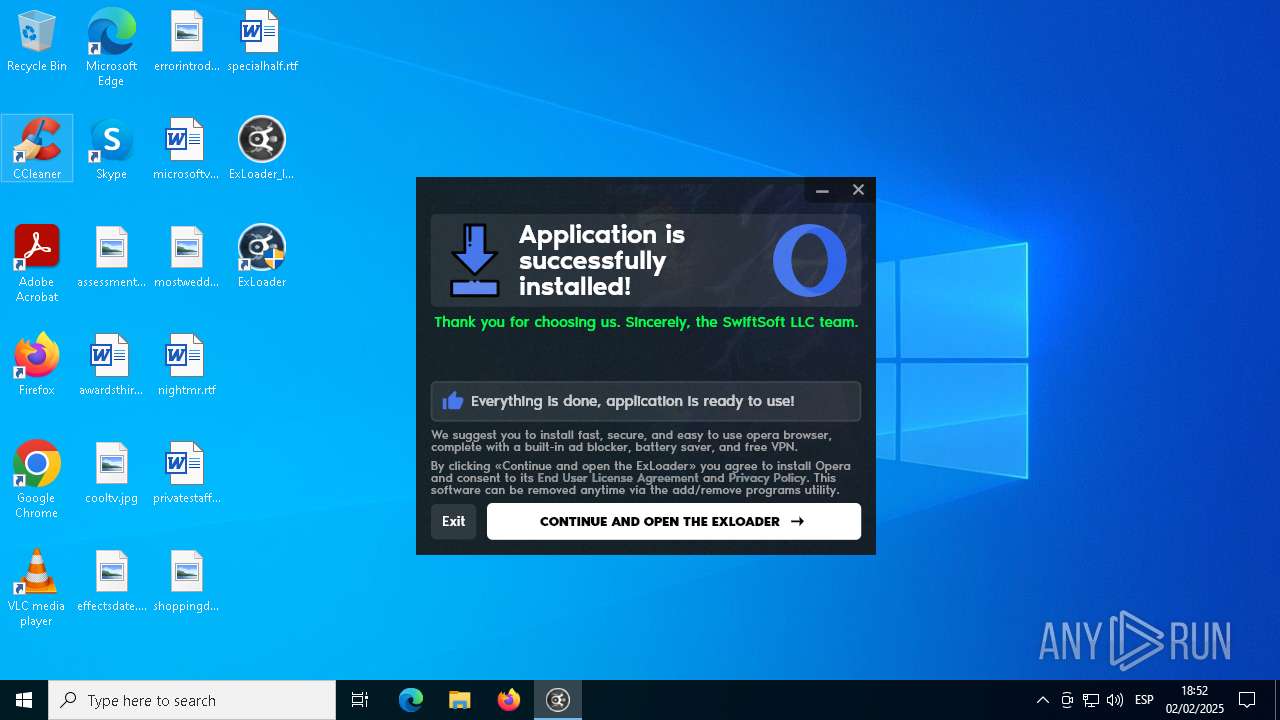
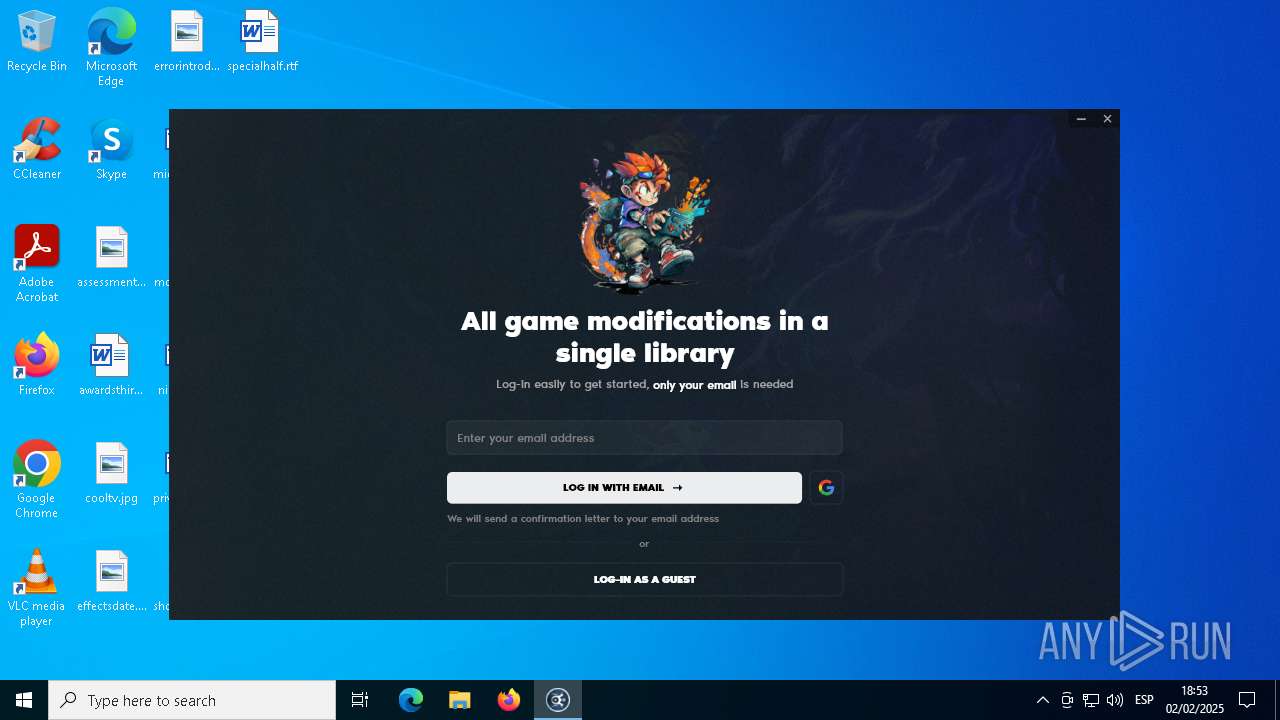
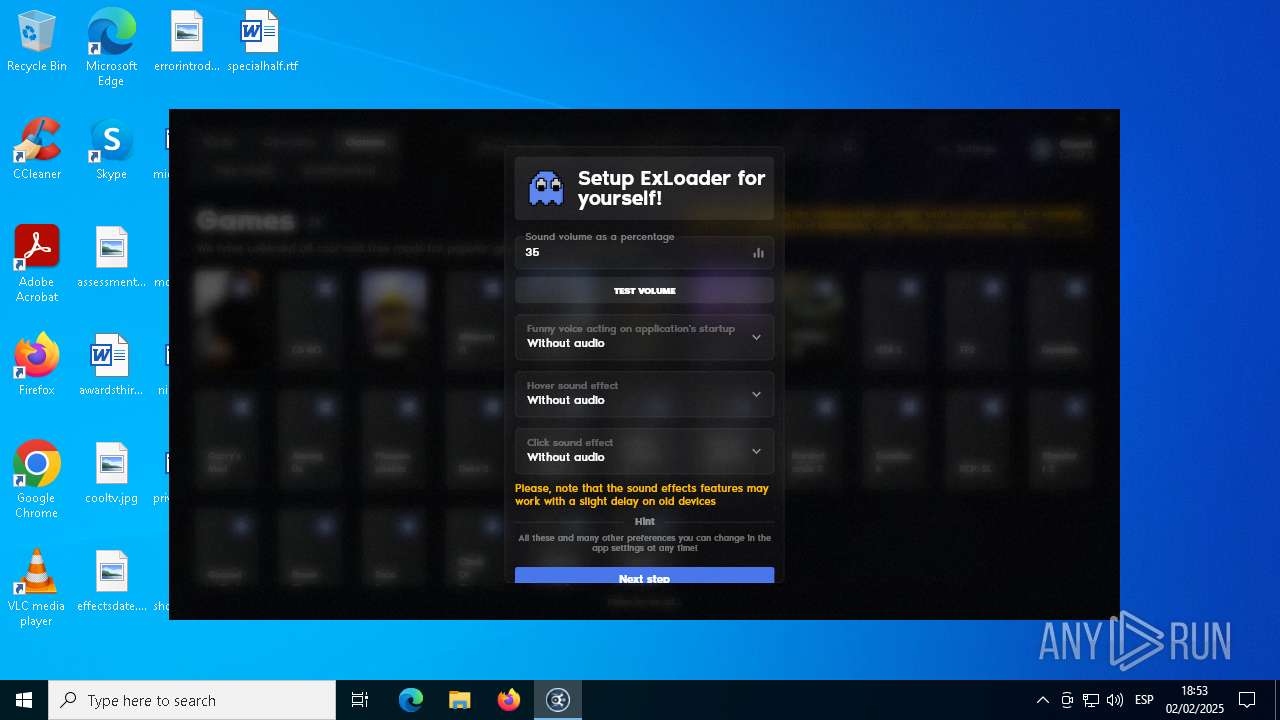
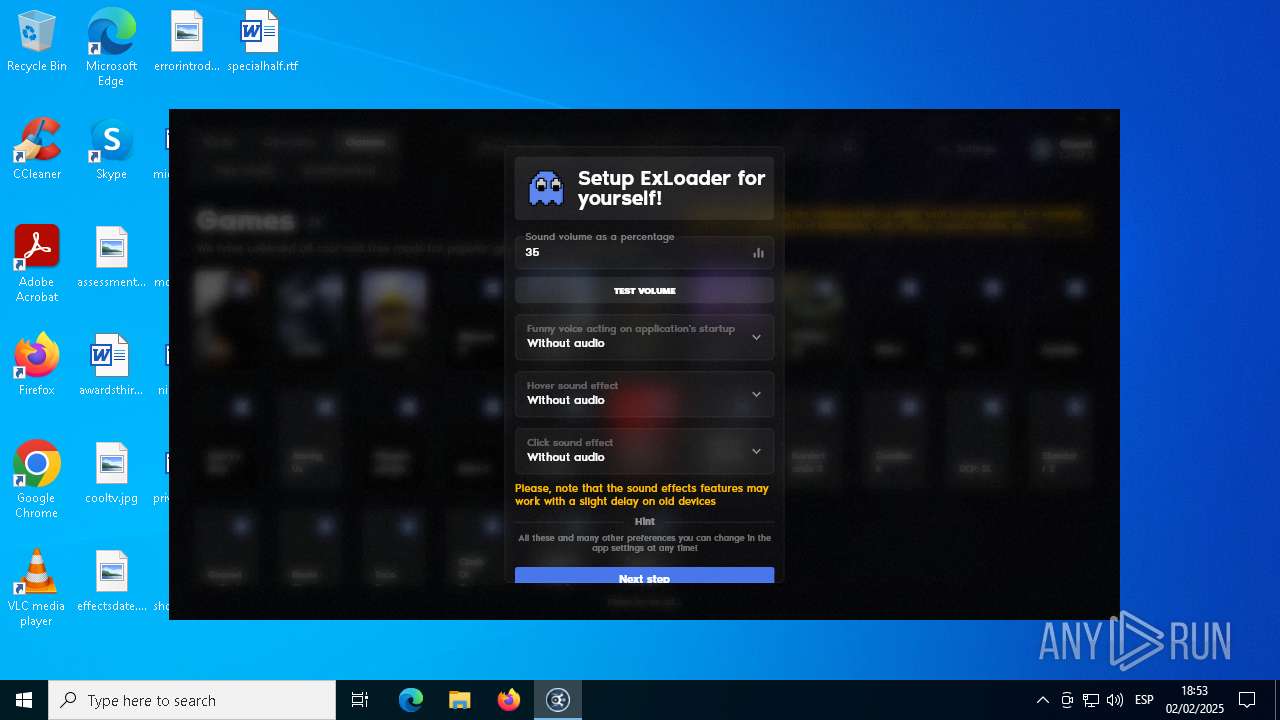
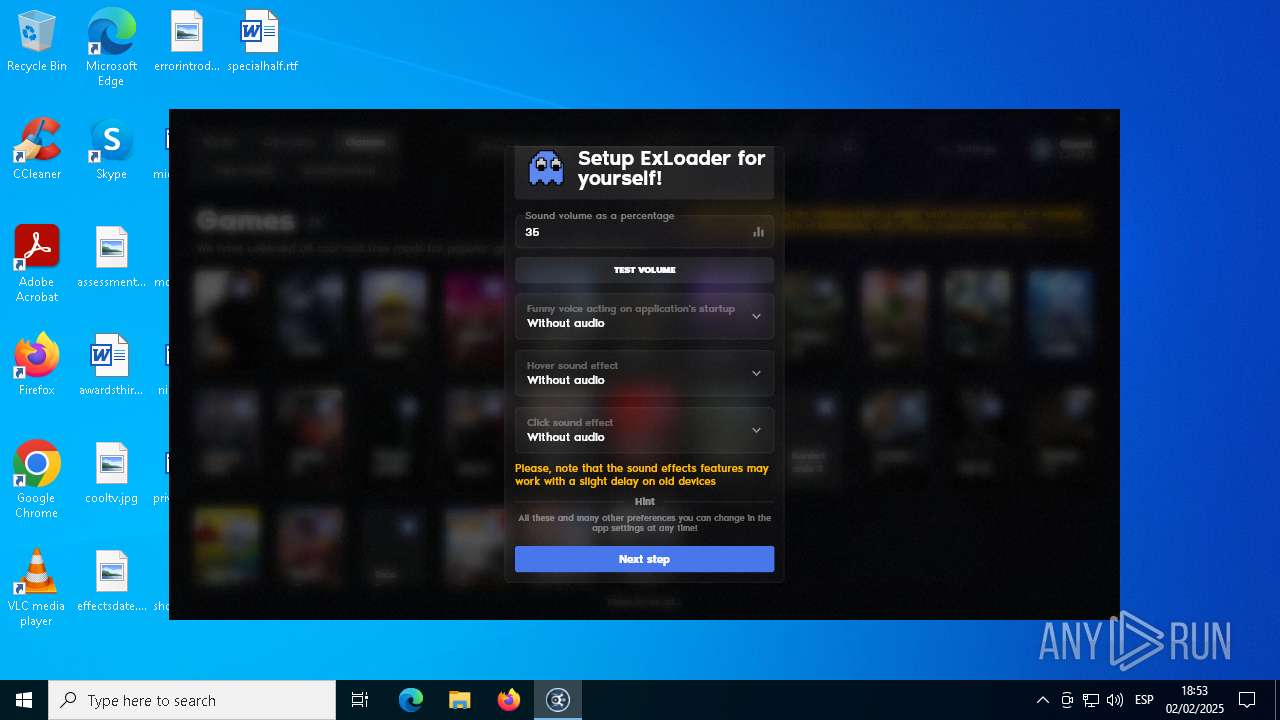
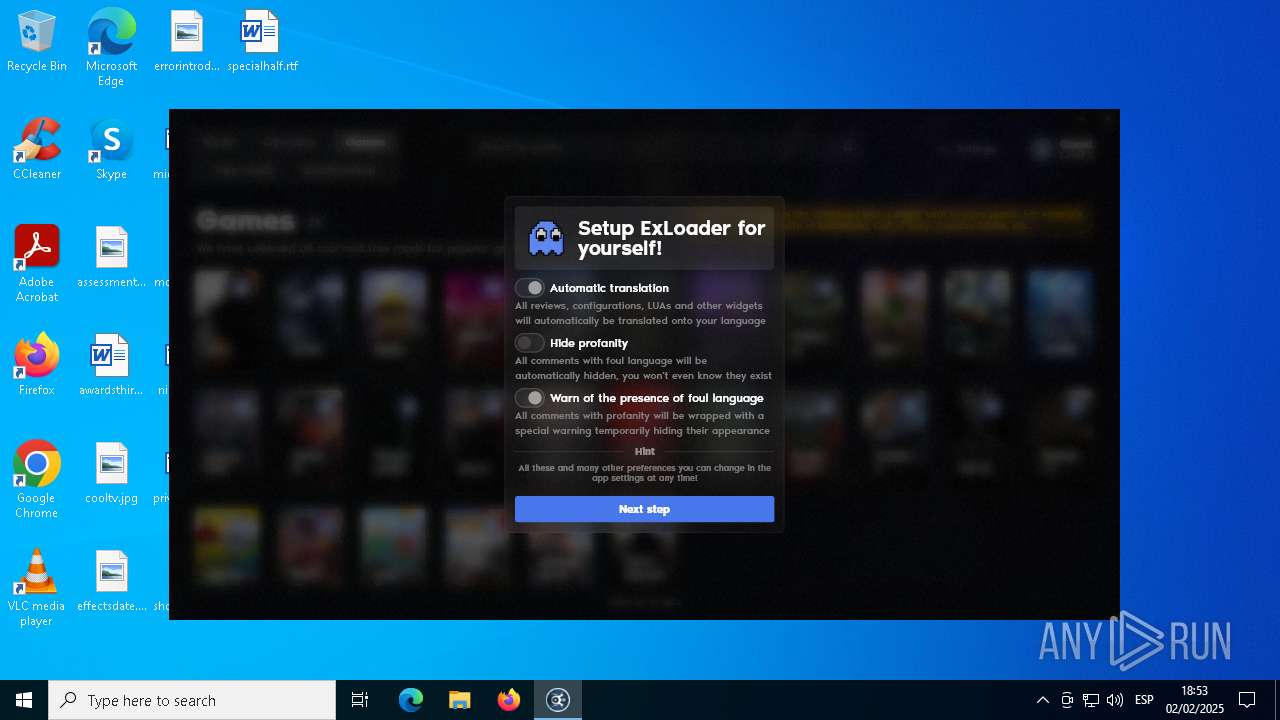
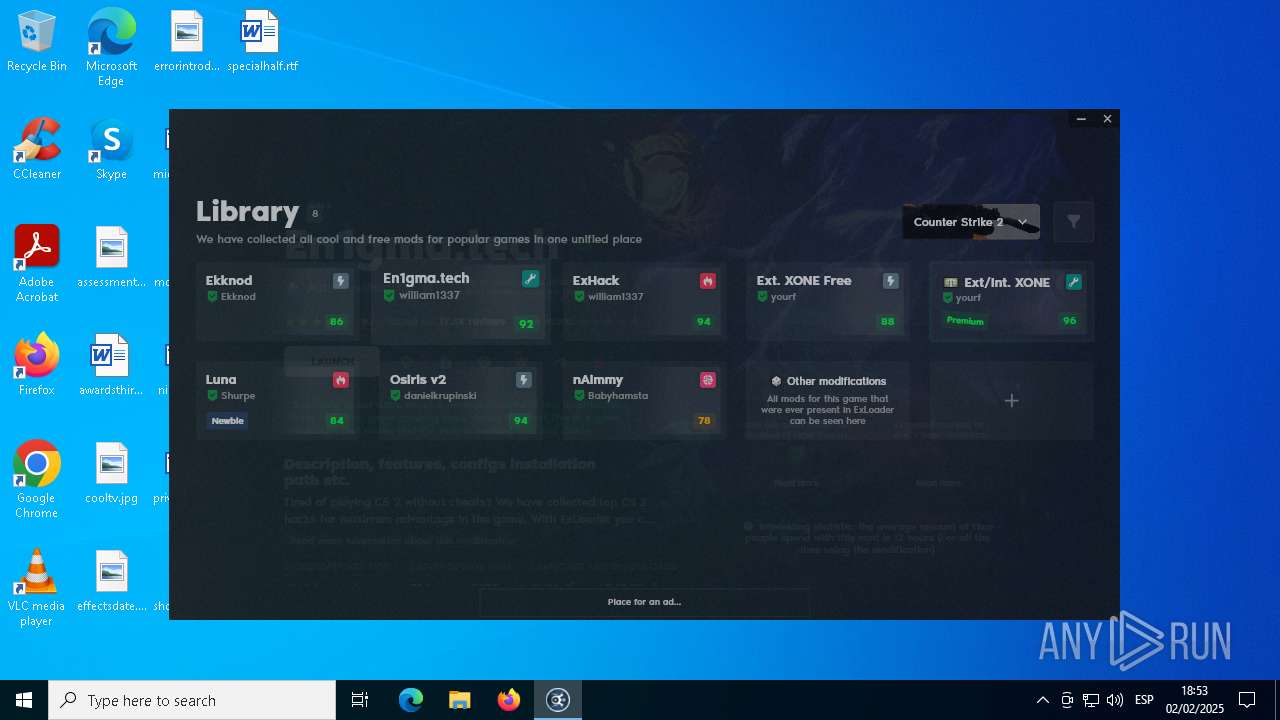
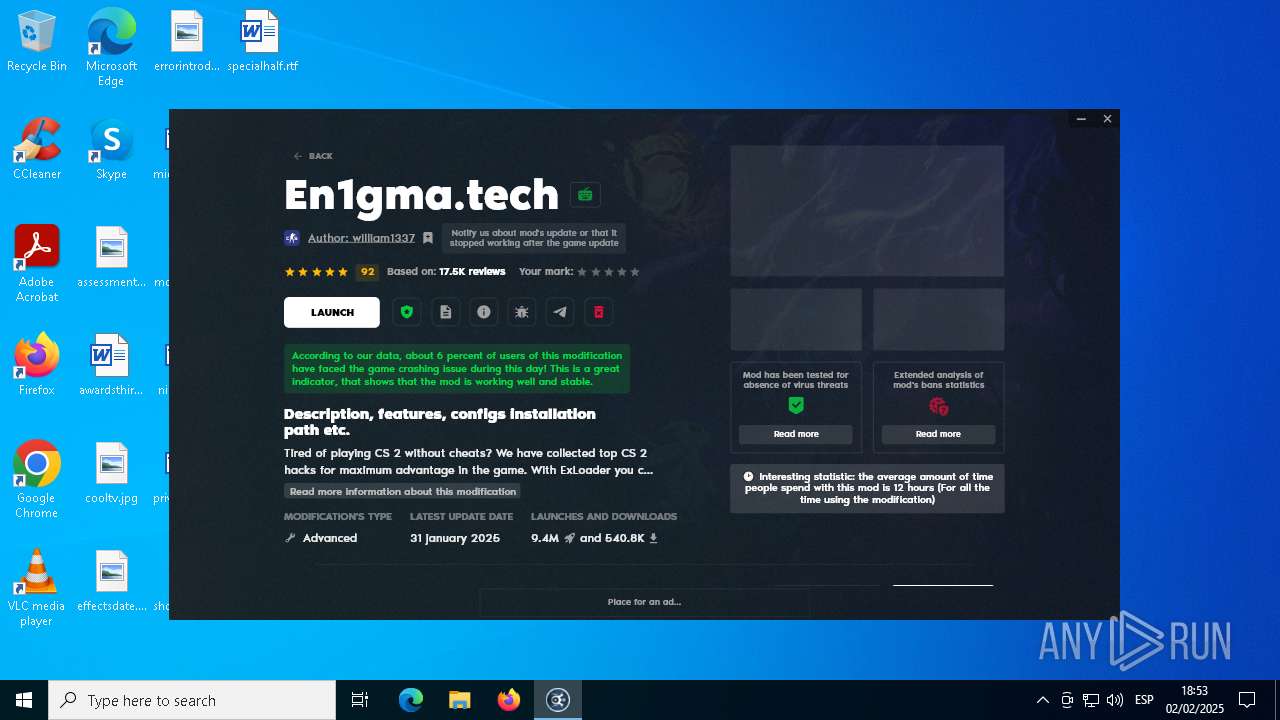
| File name: | ExLoader_Installer.exe |
| Full analysis: | https://app.any.run/tasks/71651349-c732-4dde-88a3-2ef91fafbf8a |
| Verdict: | Malicious activity |
| Analysis date: | February 02, 2025, 17:51:44 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 6 sections |
| MD5: | DCD3344E5BDCA9492706ED74CBF8B233 |
| SHA1: | ED0AD8D0E65D27D34644B75FBD73B7EE8A825BC6 |
| SHA256: | 75243DBDD7668C07417EB463D1B4F24D8FF4781B6D5AA0522AFB2509B920CF9C |
| SSDEEP: | 393216:4Rvd4zk9IHG+8tEbQq/TkYgXUfi0UO3YM8:4RF8kmm+YEblfi0Urv |
MALICIOUS
Adds path to the Windows Defender exclusion list
- ExLoader_Installer.exe (PID: 4652)
- sendingoptionbelow.exe (PID: 5036)
SUSPICIOUS
The process drops C-runtime libraries
- ExLoader_Installer.exe (PID: 6012)
- ExLoader_Installer.exe (PID: 4652)
Process drops legitimate windows executable
- ExLoader_Installer.exe (PID: 6012)
- ExLoader_Installer.exe (PID: 4652)
- sendingoptionbelow.exe (PID: 5036)
Reads security settings of Internet Explorer
- ExLoader_Installer.exe (PID: 6012)
Executable content was dropped or overwritten
- ExLoader_Installer.exe (PID: 6012)
- ExLoader_Installer.exe (PID: 4652)
- ExLoader.exe (PID: 4976)
- sendingoptionbelow.exe (PID: 5036)
- ExLoader.exe (PID: 6220)
Reads the date of Windows installation
- ExLoader_Installer.exe (PID: 6012)
Script adds exclusion path to Windows Defender
- ExLoader_Installer.exe (PID: 4652)
- sendingoptionbelow.exe (PID: 5036)
Starts POWERSHELL.EXE for commands execution
- ExLoader_Installer.exe (PID: 4652)
- sendingoptionbelow.exe (PID: 5036)
There is functionality for taking screenshot (YARA)
- ExLoader_Installer.exe (PID: 6012)
- ExLoader_Installer.exe (PID: 4652)
Checks for external IP
- svchost.exe (PID: 2192)
Connects to unusual port
- ExLoader_Installer.exe (PID: 4652)
- ExLoader.exe (PID: 4976)
- sendingoptionbelow.exe (PID: 5036)
- tipscheaperreviews.exe (PID: 732)
Starts itself from another location
- ExLoader.exe (PID: 4976)
- ExLoader.exe (PID: 6220)
Starts CMD.EXE for commands execution
- sendingoptionbelow.exe (PID: 5036)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6524)
INFO
The sample compiled with english language support
- ExLoader_Installer.exe (PID: 6012)
- ExLoader_Installer.exe (PID: 4652)
- ExLoader.exe (PID: 4976)
- sendingoptionbelow.exe (PID: 5036)
- ExLoader.exe (PID: 6220)
Reads the computer name
- ExLoader_Installer.exe (PID: 6012)
- ExLoader_Installer.exe (PID: 4652)
- ExLoader.exe (PID: 4976)
- sendingoptionbelow.exe (PID: 5036)
- tipscheaperreviews.exe (PID: 732)
- ExLoader.exe (PID: 6220)
Create files in a temporary directory
- ExLoader_Installer.exe (PID: 6012)
- powershell.exe (PID: 4528)
- sendingoptionbelow.exe (PID: 5036)
Checks supported languages
- ExLoader_Installer.exe (PID: 6012)
- ExLoader_Installer.exe (PID: 4652)
- ExLoader.exe (PID: 4976)
- ExLoader.exe (PID: 6220)
- sendingoptionbelow.exe (PID: 5036)
- tipscheaperreviews.exe (PID: 732)
Creates files in the program directory
- ExLoader_Installer.exe (PID: 4652)
- ExLoader.exe (PID: 4976)
- sendingoptionbelow.exe (PID: 5036)
- ExLoader.exe (PID: 6220)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6536)
- powershell.exe (PID: 5640)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6536)
- powershell.exe (PID: 5640)
Reads the software policy settings
- powershell.exe (PID: 4528)
Reads security settings of Internet Explorer
- powershell.exe (PID: 4528)
Manual execution by a user
- ExLoader.exe (PID: 4976)
- ExLoader.exe (PID: 6912)
- ExLoader.exe (PID: 6652)
- ExLoader.exe (PID: 6220)
Reads product name
- sendingoptionbelow.exe (PID: 5036)
- tipscheaperreviews.exe (PID: 732)
Reads Environment values
- sendingoptionbelow.exe (PID: 5036)
- tipscheaperreviews.exe (PID: 732)
Creates files or folders in the user directory
- sendingoptionbelow.exe (PID: 5036)
- ExLoader.exe (PID: 6220)
- tipscheaperreviews.exe (PID: 732)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2010:03:15 06:28:02+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 9 |
| CodeSize: | 59904 |
| InitializedDataSize: | 128512 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xaa10 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
150
Monitored processes
21
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 396 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | "C:\Program Files\ExLoader\tipscheaperreviews.exe" | C:\Program Files\ExLoader\tipscheaperreviews.exe | ExLoader.exe | ||||||||||||
User: admin Company: com.swiftsoft Integrity Level: HIGH Description: Unified library of game modifications. Version: 3.5.111+1573 Modules
| |||||||||||||||
| 1080 | C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe -command (gwmi Win32_BaseBoard) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | sendingoptionbelow.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1448 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2424 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4400 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\ExLoader_Installer.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\ExLoader_Installer.exe | — | ExLoader_Installer.exe | |||||||||||
User: admin Company: com.swiftsoft Integrity Level: MEDIUM Description: Installer for unified library of game modifications. Exit code: 3221226540 Version: 1.8.2+1572 Modules
| |||||||||||||||
| 4528 | C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe -command "$WshShell = New-Object -comObject WScript.Shell $Shortcut = $WshShell.CreateShortcut(\"c:\users\admin\desktop\ExLoader.lnk\") $Shortcut.TargetPath = \"C:\Program Files\ExLoader\ExLoader.exe\" $Shortcut.Save()" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | ExLoader_Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4652 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\ExLoader_Installer.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\ExLoader_Installer.exe | ExLoader_Installer.exe | ||||||||||||
User: admin Company: com.swiftsoft Integrity Level: HIGH Description: Installer for unified library of game modifications. Exit code: 0 Version: 1.8.2+1572 Modules
| |||||||||||||||
| 4976 | "C:\Program Files\ExLoader\ExLoader.exe" | C:\Program Files\ExLoader\ExLoader.exe | explorer.exe | ||||||||||||
User: admin Company: com.swiftsoft Integrity Level: HIGH Description: Unified library of game modifications. Exit code: 0 Version: 3.5.111+1573 Modules
| |||||||||||||||
Total events
155 042
Read events
155 041
Write events
1
Delete events
0
Modification events
| (PID) Process: | (6012) ExLoader_Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR SFX |
| Operation: | write | Name: | C%%Users%admin%AppData%Local%Temp |
Value: C:\Users\admin\AppData\Local\Temp\RarSFX0 | |||
Executable files
93
Suspicious files
81
Text files
497
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6012 | ExLoader_Installer.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\data\app.so | — | |
MD5:— | SHA256:— | |||
| 6012 | ExLoader_Installer.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\vcruntime140.dll | executable | |
MD5:E9B690FBE5C4B96871214379659DD928 | SHA256:A06C9EA4F815DAC75D2C99684D433FBFC782010FAE887837A03F085A29A217E8 | |||
| 6012 | ExLoader_Installer.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\api-ms-win-crt-runtime-l1-1-0.dll | executable | |
MD5:F1A23C251FCBB7041496352EC9BCFFBE | SHA256:D899C2F061952B3B97AB9CDBCA2450290B0F005909DDD243ED0F4C511D32C198 | |||
| 6012 | ExLoader_Installer.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\vcruntime140_1.dll | executable | |
MD5:EB49C1D33B41EB49DFED58AAFA9B9A8F | SHA256:6D3A6CDE6FC4D3C79AABF785C04D2736A3E2FD9B0366C9B741F054A13ECD939E | |||
| 6012 | ExLoader_Installer.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\flutter_windows.dll | executable | |
MD5:225782E5D02F400A76B8FABE8A6F5CD1 | SHA256:B66713715A7AEAA2F88BA18838AA7C245556EAAEB31C82DA3F5AEBCB71A7715E | |||
| 6012 | ExLoader_Installer.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\ExLoader_Installer.exe | executable | |
MD5:672D8F840DF04DA81A68C12354C67602 | SHA256:CC8522A81CA478837E76EE0975F820C0211242F859769DAD4349AFC9892DD6B2 | |||
| 6012 | ExLoader_Installer.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\data\flutter_assets\fonts\MaterialIcons-Regular.otf | binary | |
MD5:E7069DFD19B331BE16BED984668FE080 | SHA256:D9865B671A09D683D13A863089D8825E0F61A37696CE5D7D448BC8023AA62453 | |||
| 6012 | ExLoader_Installer.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\msvcp140.dll | executable | |
MD5:C3D497B0AFEF4BD7E09C7559E1C75B05 | SHA256:1E57A6DF9E3742E31A1C6D9BFF81EBEEAE8A7DE3B45A26E5079D5E1CCE54CD98 | |||
| 6012 | ExLoader_Installer.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\data\flutter_assets\resources\audio\Fortnite_hover.wav | binary | |
MD5:B66B7D55B6EEB2FF344A1AF41E42A27F | SHA256:3E3ABB7E29D38FA4B0261AC78427633E8BF6DDF3708DE5A45BBDDDC2A9F4AA6B | |||
| 6012 | ExLoader_Installer.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\data\flutter_assets\FontManifest.json | text | |
MD5:FB1230BB41C3C1290008B9E44059DD39 | SHA256:2429B610BA9010211D18626D311D3DEA7274473C2DD50FAE833ED739B67B1292 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
132
DNS requests
50
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2144 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2144 | svchost.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6152 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5680 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5680 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5064 | SearchApp.exe | 2.21.65.132:443 | www.bing.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2144 | svchost.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2144 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.msn.com |
| whitelisted |
meteum.ai |
| unknown |
www.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2192 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
2192 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
— | — | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2192 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain (ipapi .co in DNS lookup) |
2192 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain (ipapi .co in DNS lookup) |