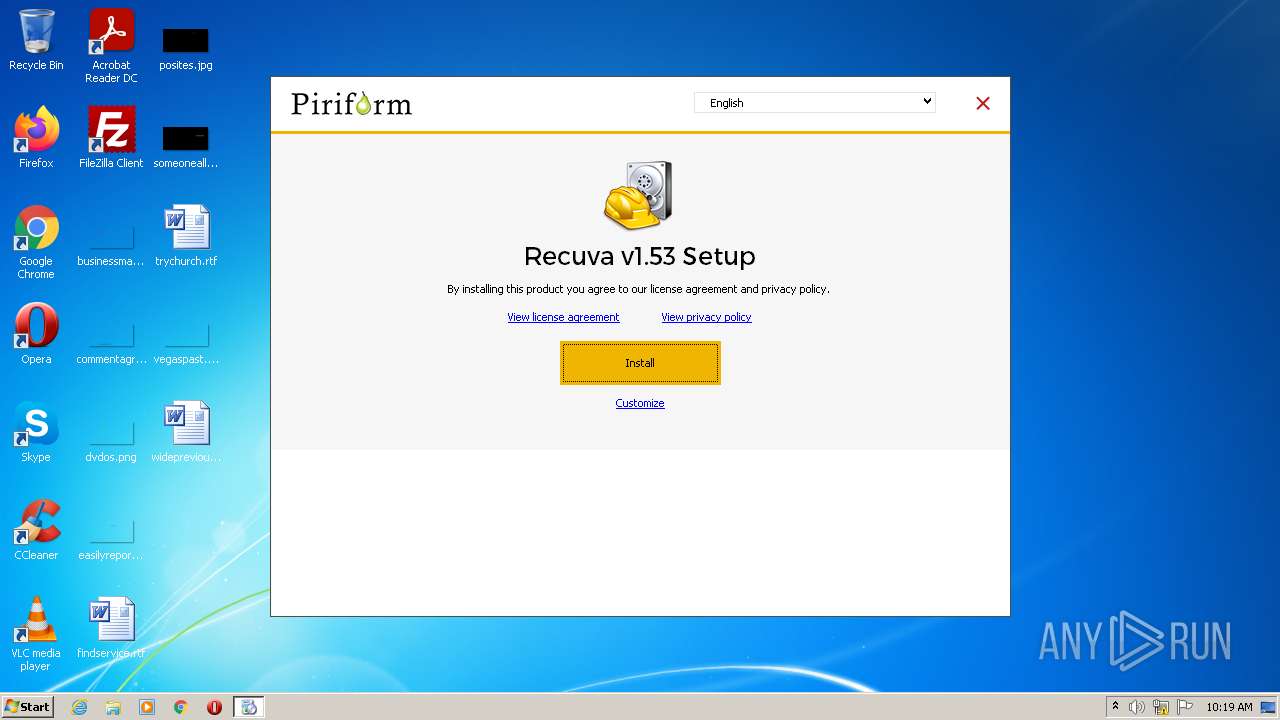
| File name: | rcsetup153.exe |
| Full analysis: | https://app.any.run/tasks/4ea8d2a1-4479-42f9-8c7f-d22e5f243a0a |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | January 20, 2022, 10:19:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 264474AE9B9FD039AC0C113F88F7BD2D |
| SHA1: | 4A3CDBD119BB149FFD96BAB9DDDB768E505460B0 |
| SHA256: | 75155568D64E958D8003F9FBB36839FC9A53BFAB3B51A8A1106A78E5BE98B2E9 |
| SSDEEP: | 98304:+wTlDCSkHS5PmyHZhMFdnr7lZI4jum8h0AYbg9o7iER1LcKn/qPP:+w1CST35hMnHI4jf5zbg9scrP |
MALICIOUS
Drops executable file immediately after starts
- rcsetup153.exe (PID: 2520)
- PF-Toolbar-2016.exe (PID: 2300)
- GoogleToolbarManager_8B0481A9A34D47CD.exe (PID: 2056)
- GoogleUpdaterService_B33FC4DD36A473C6.exe (PID: 2488)
- SearchWithGoogleUpdate_CA8A7236098B8F9A.exe (PID: 3136)
Steals credentials from Web Browsers
- rcsetup153.exe (PID: 2520)
Actions looks like stealing of personal data
- rcsetup153.exe (PID: 2520)
Loads dropped or rewritten executable
- rcsetup153.exe (PID: 2520)
- GoogleUpdate.exe (PID: 2748)
- PF-Toolbar-2016.exe (PID: 2300)
- GoogleToolbarNotifier.exe (PID: 3348)
- GoogleToolbarManager_8B0481A9A34D47CD.exe (PID: 2056)
- GoogleToolbarNotifier.exe (PID: 2448)
Application was dropped or rewritten from another process
- PF-Toolbar-2016.exe (PID: 2300)
- GoogleUpdate.exe (PID: 2748)
- googletoolbarinstaller_en_signed.exe (PID: 3488)
- GoogleUpdateSetup_1.3.21.169.exe (PID: 3864)
- GoogleToolbarManager_8B0481A9A34D47CD.exe (PID: 2676)
- GoogleToolbarManager_8B0481A9A34D47CD.exe (PID: 2056)
- GoogleUpdaterService_B33FC4DD36A473C6.exe (PID: 2488)
- GoogleToolbarManager_8B0481A9A34D47CD.exe (PID: 960)
- SearchWithGoogleUpdate_CA8A7236098B8F9A.exe (PID: 3136)
- GoogleUpdaterService.exe (PID: 3544)
- GoogleToolbarNotifier.exe (PID: 2448)
- GoogleToolbarNotifier.exe (PID: 3348)
- GoogleUpdaterService.exe (PID: 2260)
Changes settings of System certificates
- GoogleUpdate.exe (PID: 508)
- googletoolbarinstaller_en_signed.exe (PID: 3488)
Loads the Task Scheduler DLL interface
- GoogleUpdaterService_B33FC4DD36A473C6.exe (PID: 2488)
- GoogleUpdaterService.exe (PID: 3544)
SUSPICIOUS
Reads Environment values
- rcsetup153.exe (PID: 2520)
Reads the computer name
- rcsetup153.exe (PID: 2520)
- PF-Toolbar-2016.exe (PID: 2300)
- GoogleUpdate.exe (PID: 2748)
- GoogleUpdate.exe (PID: 508)
- googletoolbarinstaller_en_signed.exe (PID: 3488)
- GoogleUpdate.exe (PID: 284)
- GoogleToolbarManager_8B0481A9A34D47CD.exe (PID: 2056)
- GoogleUpdaterService_B33FC4DD36A473C6.exe (PID: 2488)
- GoogleUpdaterService.exe (PID: 2260)
- GoogleUpdaterService.exe (PID: 3544)
- GoogleToolbarNotifier.exe (PID: 2448)
- SearchWithGoogleUpdate_CA8A7236098B8F9A.exe (PID: 3136)
- GoogleToolbarNotifier.exe (PID: 3348)
- GoogleToolbarManager_8B0481A9A34D47CD.exe (PID: 2676)
- GoogleToolbarManager_8B0481A9A34D47CD.exe (PID: 960)
- GoogleUpdate.exe (PID: 3628)
Checks supported languages
- rcsetup153.exe (PID: 2520)
- nsBBCD.tmp (PID: 3520)
- PF-Toolbar-2016.exe (PID: 2300)
- GoogleUpdateSetup_1.3.21.169.exe (PID: 3864)
- GoogleUpdate.exe (PID: 2748)
- GoogleUpdate.exe (PID: 508)
- googletoolbarinstaller_en_signed.exe (PID: 3488)
- GoogleUpdate.exe (PID: 284)
- GoogleToolbarManager_8B0481A9A34D47CD.exe (PID: 2056)
- GoogleUpdaterService.exe (PID: 2260)
- SearchWithGoogleUpdate_CA8A7236098B8F9A.exe (PID: 3136)
- GoogleUpdaterService_B33FC4DD36A473C6.exe (PID: 2488)
- GoogleToolbarNotifier.exe (PID: 2448)
- GoogleUpdaterService.exe (PID: 3544)
- GoogleToolbarNotifier.exe (PID: 3348)
- GoogleToolbarManager_8B0481A9A34D47CD.exe (PID: 2676)
- GoogleToolbarManager_8B0481A9A34D47CD.exe (PID: 960)
- GoogleUpdate.exe (PID: 3628)
Drops a file that was compiled in debug mode
- rcsetup153.exe (PID: 2520)
- GoogleUpdateSetup_1.3.21.169.exe (PID: 3864)
- PF-Toolbar-2016.exe (PID: 2300)
- GoogleToolbarManager_8B0481A9A34D47CD.exe (PID: 2056)
- googletoolbarinstaller_en_signed.exe (PID: 3488)
- GoogleUpdaterService_B33FC4DD36A473C6.exe (PID: 2488)
- SearchWithGoogleUpdate_CA8A7236098B8F9A.exe (PID: 3136)
Reads Microsoft Outlook installation path
- rcsetup153.exe (PID: 2520)
Executable content was dropped or overwritten
- rcsetup153.exe (PID: 2520)
- PF-Toolbar-2016.exe (PID: 2300)
- GoogleUpdateSetup_1.3.21.169.exe (PID: 3864)
- GoogleUpdate.exe (PID: 284)
- googletoolbarinstaller_en_signed.exe (PID: 3488)
- GoogleToolbarManager_8B0481A9A34D47CD.exe (PID: 2056)
- msiexec.exe (PID: 3732)
- GoogleUpdaterService_B33FC4DD36A473C6.exe (PID: 2488)
- SearchWithGoogleUpdate_CA8A7236098B8F9A.exe (PID: 3136)
Reads internet explorer settings
- rcsetup153.exe (PID: 2520)
Drops a file with too old compile date
- rcsetup153.exe (PID: 2520)
- PF-Toolbar-2016.exe (PID: 2300)
- SearchWithGoogleUpdate_CA8A7236098B8F9A.exe (PID: 3136)
Reads the cookies of Mozilla Firefox
- rcsetup153.exe (PID: 2520)
Creates files in the user directory
- rcsetup153.exe (PID: 2520)
Reads the cookies of Google Chrome
- rcsetup153.exe (PID: 2520)
Starts application with an unusual extension
- rcsetup153.exe (PID: 2520)
Creates a directory in Program Files
- GoogleUpdate.exe (PID: 2748)
- GoogleUpdateSetup_1.3.21.169.exe (PID: 3864)
- GoogleUpdate.exe (PID: 284)
- googletoolbarinstaller_en_signed.exe (PID: 3488)
- GoogleUpdaterService_B33FC4DD36A473C6.exe (PID: 2488)
- SearchWithGoogleUpdate_CA8A7236098B8F9A.exe (PID: 3136)
- rcsetup153.exe (PID: 2520)
Creates files in the program directory
- GoogleUpdateSetup_1.3.21.169.exe (PID: 3864)
- GoogleUpdate.exe (PID: 284)
- googletoolbarinstaller_en_signed.exe (PID: 3488)
- GoogleToolbarManager_8B0481A9A34D47CD.exe (PID: 2056)
- GoogleUpdaterService_B33FC4DD36A473C6.exe (PID: 2488)
- SearchWithGoogleUpdate_CA8A7236098B8F9A.exe (PID: 3136)
- GoogleToolbarManager_8B0481A9A34D47CD.exe (PID: 960)
Adds / modifies Windows certificates
- GoogleUpdate.exe (PID: 508)
- googletoolbarinstaller_en_signed.exe (PID: 3488)
Creates a software uninstall entry
- GoogleToolbarManager_8B0481A9A34D47CD.exe (PID: 2056)
- msiexec.exe (PID: 3732)
Executed as Windows Service
- msiexec.exe (PID: 3732)
Creates/Modifies COM task schedule object
- GoogleToolbarManager_8B0481A9A34D47CD.exe (PID: 2056)
- GoogleToolbarNotifier.exe (PID: 2448)
Reads the Windows organization settings
- msiexec.exe (PID: 3732)
Reads Windows owner or organization settings
- msiexec.exe (PID: 3732)
Executed via COM
- GoogleToolbarNotifier.exe (PID: 3348)
Application launched itself
- GoogleUpdate.exe (PID: 284)
INFO
Checks supported languages
- ping.exe (PID: 3020)
- msiexec.exe (PID: 3732)
Reads the computer name
- ping.exe (PID: 3020)
- msiexec.exe (PID: 3732)
Reads settings of System Certificates
- GoogleUpdate.exe (PID: 508)
- GoogleUpdate.exe (PID: 284)
- googletoolbarinstaller_en_signed.exe (PID: 3488)
- msiexec.exe (PID: 3732)
- GoogleUpdate.exe (PID: 3628)
- rcsetup153.exe (PID: 2520)
Checks Windows Trust Settings
- googletoolbarinstaller_en_signed.exe (PID: 3488)
- msiexec.exe (PID: 3732)
- rcsetup153.exe (PID: 2520)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| ProductName: | Recuva |
|---|---|
| LegalCopyright: | Copyright © 2006-2016 Piriform Ltd |
| FileVersion: | 1.0.0.0 |
| FileDescription: | Recuva Installer |
| CompanyName: | Piriform Ltd |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x0000 |
| ProductVersionNumber: | 1.0.0.0 |
| FileVersionNumber: | 1.0.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 5 |
| ImageVersion: | 6 |
| OSVersion: | 5 |
| EntryPoint: | 0x3a1c |
| UninitializedDataSize: | 16896 |
| InitializedDataSize: | 441856 |
| CodeSize: | 29696 |
| LinkerVersion: | 9 |
| PEType: | PE32 |
| TimeStamp: | 2015:12:29 22:34:49+01:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 29-Dec-2015 21:34:49 |
| Detected languages: |
|
| CompanyName: | Piriform Ltd |
| FileDescription: | Recuva Installer |
| FileVersion: | 1.0.0.0 |
| LegalCopyright: | Copyright © 2006-2016 Piriform Ltd |
| ProductName: | Recuva |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 29-Dec-2015 21:34:49 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00007250 | 0x00007400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.46491 |
.rdata | 0x00009000 | 0x00002B38 | 0x00002C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.41939 |
.data | 0x0000C000 | 0x00067EDC | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.89689 |
.ndata | 0x00074000 | 0x00309000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x0037D000 | 0x00007A68 | 0x00007C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.01418 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.21562 | 968 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 5.62687 | 4264 | UNKNOWN | English - United States | RT_ICON |
3 | 4.7389 | 2216 | UNKNOWN | English - United States | RT_ICON |
4 | 3.91559 | 1384 | UNKNOWN | English - United States | RT_ICON |
5 | 5.97397 | 1128 | UNKNOWN | English - United States | RT_ICON |
6 | 3.89369 | 744 | UNKNOWN | English - United States | RT_ICON |
103 | 2.72033 | 90 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.704 | 688 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.92897 | 344 | UNKNOWN | English - United States | RT_DIALOG |
111 | 2.92787 | 238 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
61
Monitored processes
21
Malicious processes
9
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | "C:\Program Files\Google\Update\GoogleUpdate.exe" /handoff "appguid={F69EABDD-A4BB-4555-BE7E-1EA5F59BBA24}&appname=Google%20Toolbar&needsadmin=True&brand=PRFD&usagestats=0" /appargs "appguid={F69EABDD-A4BB-4555-BE7E-1EA5F59BBA24}&installerdata=d%3Dask%26h%3Dask2" /installsource otherinstallcmd /sessionid "{1B0F0D33-33A2-4B06-8B10-C4C7351E1FC2}" /silent | C:\Program Files\Google\Update\GoogleUpdate.exe | GoogleUpdate.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: HIGH Description: Google Installer Exit code: 0 Version: 1.3.33.23 Modules
| |||||||||||||||
| 508 | "C:\Program Files\Google\Update\GoogleUpdate.exe" /ping PD94bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0iVVRGLTgiPz48cmVxdWVzdCBwcm90b2NvbD0iMy4wIiB2ZXJzaW9uPSIxLjMuMjEuMTY5IiBzaGVsbF92ZXJzaW9uPSIxLjMuMjEuMTAzIiBpc21hY2hpbmU9IjEiIHNlc3Npb25pZD0iezFCMEYwRDMzLTMzQTItNEIwNi04QjEwLUM0QzczNTFFMUZDMn0iIGluc3RhbGxzb3VyY2U9Im90aGVyaW5zdGFsbGNtZCIgcmVxdWVzdGlkPSJ7NjVGMDk0MzUtMDMyRC00QTM4LTlBMUEtNTJDNDgyMDRGMTBBfSIgZGVkdXA9ImNyIj48b3MgcGxhdGZvcm09IndpbiIgdmVyc2lvbj0iNi4xIiBzcD0iU2VydmljZSBQYWNrIDEiIGFyY2g9Ing4NiIvPjxhcHAgYXBwaWQ9Ins0MzBGRDREMC1CNzI5LTRGNjEtQUEzNC05MTUyNjQ4MTc5OUR9IiB2ZXJzaW9uPSIxLjMuMzYuMzIiIG5leHR2ZXJzaW9uPSIxLjMuMjEuMTY5IiBsYW5nPSIiIGJyYW5kPSJQUkZEIiBjbGllbnQ9IiI-PGV2ZW50IGV2ZW50dHlwZT0iMiIgZXZlbnRyZXN1bHQ9IjEiIGVycm9yY29kZT0iMCIgZXh0cmFjb2RlMT0iMCIgaW5zdGFsbF90aW1lX21zPSIxNSIvPjwvYXBwPjwvcmVxdWVzdD4 | C:\Program Files\Google\Update\GoogleUpdate.exe | GoogleUpdate.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: HIGH Description: Google Installer Exit code: 0 Version: 1.3.33.23 Modules
| |||||||||||||||
| 960 | "C:\Program Files\Google\Google Toolbar\Component\GoogleToolbarManager_8B0481A9A34D47CD.exe" /custombuttonsinstall | C:\Program Files\Google\Google Toolbar\Component\GoogleToolbarManager_8B0481A9A34D47CD.exe | — | googletoolbarinstaller_en_signed.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: HIGH Description: Google Toolbar Manager Exit code: 0 Version: 7, 5, 8231, 2252 Modules
| |||||||||||||||
| 2056 | "C:\Program Files\Google\Google Toolbar\Component\GoogleToolbarManager_8B0481A9A34D47CD.exe" /install /sid:S-1-5-21-1302019708-1500728564-335382590-1000 /q /expon:PUMA /installerdata="C:\Users\admin\AppData\Local\Temp\guiE357.tmp" /d:ask /h:ask2 /r:PRFD /e:asknot | C:\Program Files\Google\Google Toolbar\Component\GoogleToolbarManager_8B0481A9A34D47CD.exe | googletoolbarinstaller_en_signed.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: HIGH Description: Google Toolbar Manager Exit code: 0 Version: 7, 5, 8231, 2252 Modules
| |||||||||||||||
| 2260 | "C:\Program Files\Google\Common\Google Updater\GoogleUpdaterService.exe" /Service | C:\Program Files\Google\Common\Google Updater\GoogleUpdaterService.exe | — | GoogleUpdaterService_B33FC4DD36A473C6.exe | |||||||||||
User: admin Company: Google Integrity Level: HIGH Description: gusvc Exit code: 0 Version: 2.4.2617.4952.beta Modules
| |||||||||||||||
| 2300 | C:\Users\admin\AppData\Local\Temp\nsr33CF.tmp\g\PF-Toolbar-2016.exe | C:\Users\admin\AppData\Local\Temp\nsr33CF.tmp\g\PF-Toolbar-2016.exe | rcsetup153.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: HIGH Description: Google Toolbar installer Exit code: 0 Version: 1.0.0.5 Modules
| |||||||||||||||
| 2448 | "C:\Program Files\Google\GoogleToolbarNotifier\GoogleToolbarNotifier.exe" /RegServer "/dll=C:\Program Files\Google\GoogleToolbarNotifier\5.12.11510.1228\gtn.dll" | C:\Program Files\Google\GoogleToolbarNotifier\GoogleToolbarNotifier.exe | — | SearchWithGoogleUpdate_CA8A7236098B8F9A.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: HIGH Description: GoogleToolbarNotifier Exit code: 0 Version: 4, 1, 509, 1944 Modules
| |||||||||||||||
| 2488 | "C:\Program Files\Google\Google Toolbar\Component\GoogleUpdaterService_B33FC4DD36A473C6.exe" /install /appid=tbie | C:\Program Files\Google\Google Toolbar\Component\GoogleUpdaterService_B33FC4DD36A473C6.exe | GoogleToolbarManager_8B0481A9A34D47CD.exe | ||||||||||||
User: admin Company: Google Integrity Level: HIGH Description: gusvc Exit code: 0 Version: 2.4.2617.4952.beta Modules
| |||||||||||||||
| 2520 | "C:\Users\admin\AppData\Local\Temp\rcsetup153.exe" | C:\Users\admin\AppData\Local\Temp\rcsetup153.exe | Explorer.EXE | ||||||||||||
User: admin Company: Piriform Ltd Integrity Level: HIGH Description: Recuva Installer Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2540 | "C:\Users\admin\AppData\Local\Temp\rcsetup153.exe" | C:\Users\admin\AppData\Local\Temp\rcsetup153.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Piriform Ltd Integrity Level: MEDIUM Description: Recuva Installer Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
26 594
Read events
25 566
Write events
1 001
Delete events
27
Modification events
| (PID) Process: | (2520) rcsetup153.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Google Toolbar |
| Operation: | write | Name: | test |
Value: test | |||
| (PID) Process: | (2520) rcsetup153.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Google Toolbar |
| Operation: | delete value | Name: | test |
Value: test | |||
| (PID) Process: | (2520) rcsetup153.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Google Toolbar |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2520) rcsetup153.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2520) rcsetup153.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2520) rcsetup153.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2520) rcsetup153.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2520) rcsetup153.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2520) rcsetup153.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2520) rcsetup153.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
151
Suspicious files
8
Text files
50
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2520 | rcsetup153.exe | C:\Users\admin\AppData\Local\Temp\nsr33CF.tmp\System.dll | executable | |
MD5:41A3C964232EDD2D7D5EDEA53E8245CD | SHA256:8B65FEC615C7B371C23F8F7F344B12DC5085E40A556F96DB318ED757494D62D5 | |||
| 2520 | rcsetup153.exe | C:\Users\admin\AppData\Local\Temp\nsr33CF.tmp\g\gtb\toolbar_1038.html | html | |
MD5:95988D3A1D36D92D4CF3AD320C80FDCD | SHA256:65432A8FE5518F97A6A1EBBBD47946DEA7ECF34EB5712CF5E51D169BB100075B | |||
| 2520 | rcsetup153.exe | C:\Users\admin\AppData\Local\Temp\nsr33CF.tmp\g\gcapi_dll.dll | executable | |
MD5:2973AF8515EFFD0A3BFC7A43B03B3FCC | SHA256:D0E4581210A22135CE5DEB47D9DF4D636A94B3813E0649AAB84822C9F08AF2A0 | |||
| 2520 | rcsetup153.exe | C:\Users\admin\AppData\Local\Temp\nsr33CF.tmp\g\gtb\toolbar_1032.html | html | |
MD5:F43271F4ADA4E852F7070088BB6F0899 | SHA256:DFE0EB278590B958201DA9B6DE03D7C5AB0B6E661AFABAEFC244AC6FEE57B932 | |||
| 2520 | rcsetup153.exe | C:\Users\admin\AppData\Local\Temp\nsr33CF.tmp\g\gtb\toolbar_1034.html | html | |
MD5:B3F6A763C9911E00B17268811D0614C1 | SHA256:5289568D0499C23553E66CA228110333D67E43EC720310ACE023BD1CF69F02C1 | |||
| 2520 | rcsetup153.exe | C:\Users\admin\AppData\Local\Temp\nsr33CF.tmp\g\gtb\toolbar_1033.html | html | |
MD5:32089637539CA778D0C37ABDA145BFBC | SHA256:BBE9DA05899E5B0AF45890DD177AB58DE14C7CE8D0CB5B1964FD56B9BB27E661 | |||
| 2520 | rcsetup153.exe | C:\Users\admin\AppData\Local\Temp\nsr33CF.tmp\g\gtb\toolbar_1035.html | html | |
MD5:03108766F8027770E444796B18E7EE0B | SHA256:B76A1A1DD982F7BD19153EB6B078C2A93AF13A3FD1B77925A71FAFAEBDD379DC | |||
| 2520 | rcsetup153.exe | C:\Users\admin\AppData\Local\Temp\nsr33CF.tmp\g\gtb\toolbar_1036.html | html | |
MD5:BB4B0266716B8911137756DDDA1D64F5 | SHA256:AB8993F0C1279720A8D5D575833531E9921201995D51B1F6C27F680C45E74528 | |||
| 2520 | rcsetup153.exe | C:\Users\admin\AppData\Local\Temp\nsr33CF.tmp\g\gtb\toolbar_1041.html | html | |
MD5:F3D6CDC87A1E811A4D845A1025E4DC2E | SHA256:B6B404473B73783602062AFE68C5F73FC5CF0525DF06C2AF447B97DFAAE9BC69 | |||
| 2520 | rcsetup153.exe | C:\Users\admin\AppData\Local\Temp\nsr33CF.tmp\g\gtb\toolbar_1027.html | html | |
MD5:187DAFC912E93302CE08CB857A05C7A6 | SHA256:535F34E32F2AC56844E9503971DDFE1E0EEC14985BDA92E6956B395567EFA36C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
11
DNS requests
8
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
872 | svchost.exe | HEAD | 200 | 142.250.184.206:80 | http://dl.google.com/dl/toolbar/t7/data/7.5.8231.2252/googletoolbarinstaller_en_signed.exe | US | — | — | whitelisted |
2520 | rcsetup153.exe | GET | 302 | 151.101.0.64:80 | http://service.piriform.com/installcheck.aspx?p=2&v=1.53.1087&vx=&l=1033&b=1&o=6.1W3&g=1&i=1&a=0&e=0&n=rcsetup153.exe&id=003 | US | — | — | whitelisted |
3348 | GoogleToolbarNotifier.exe | GET | — | 142.250.186.174:80 | http://clients1.google.com/tools/swg2/update?type=c&as=swg&os=win-u&osv=6.1.7601&hl=en&ie=11.0.9600.19597&ds=0&pds=0&su=0&hpi=-1&brand=PRFD&pa=0&cl=1&tbv=&id=27804676f73e43a8ab5fe73941e04727035b210c45&from=&to=5.12.11510.1228 | US | — | — | whitelisted |
872 | svchost.exe | GET | 200 | 142.250.184.206:80 | http://dl.google.com/dl/toolbar/t7/data/7.5.8231.2252/googletoolbarinstaller_en_signed.exe | US | executable | 4.80 Mb | whitelisted |
3488 | googletoolbarinstaller_en_signed.exe | GET | 200 | 142.250.186.174:80 | http://clients1.google.com/tools/pso/ping?as=tbin&gu=pi&mode=3&sin=1&ein=0&version=7.5.8231.2252&brand=PRFD&hl=en&tbiv=7.5.8231.2252&time=1642674025&fitime=1642674025&browser=9.11.9600.19596&osver=6.1&ossp=1.0&osarch=32&ext=EXE&id=EE71FA15ED6E344B84AAF92B7FAAA3D6614BFcQWMW | US | text | 2 b | whitelisted |
2520 | rcsetup153.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9fc65c6bac470254 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
508 | GoogleUpdate.exe | 216.58.212.163:443 | update.googleapis.com | Google Inc. | US | whitelisted |
284 | GoogleUpdate.exe | 216.58.212.163:443 | update.googleapis.com | Google Inc. | US | whitelisted |
872 | svchost.exe | 142.250.184.206:80 | dl.google.com | Google Inc. | US | whitelisted |
3348 | GoogleToolbarNotifier.exe | 142.250.186.174:80 | clients1.google.com | Google Inc. | US | whitelisted |
3488 | googletoolbarinstaller_en_signed.exe | 142.250.186.174:80 | clients1.google.com | Google Inc. | US | whitelisted |
3628 | GoogleUpdate.exe | 216.58.212.163:443 | update.googleapis.com | Google Inc. | US | whitelisted |
2520 | rcsetup153.exe | 151.101.0.64:80 | www.piriform.com | Fastly | US | whitelisted |
2520 | rcsetup153.exe | 44.199.109.57:443 | license-api.ccleaner.com | University of California, San Diego | US | unknown |
2520 | rcsetup153.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
2520 | rcsetup153.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.piriform.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
dl.google.com |
| whitelisted |
clients1.google.com |
| whitelisted |
service.piriform.com |
| whitelisted |
license-api.ccleaner.com |
| suspicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
872 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
872 | svchost.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
Process | Message |
|---|---|
GoogleUpdate.exe | LOG_SYSTEM: [GoogleUpdate:goopdate]: ERROR - Cannot create ETW log writer |