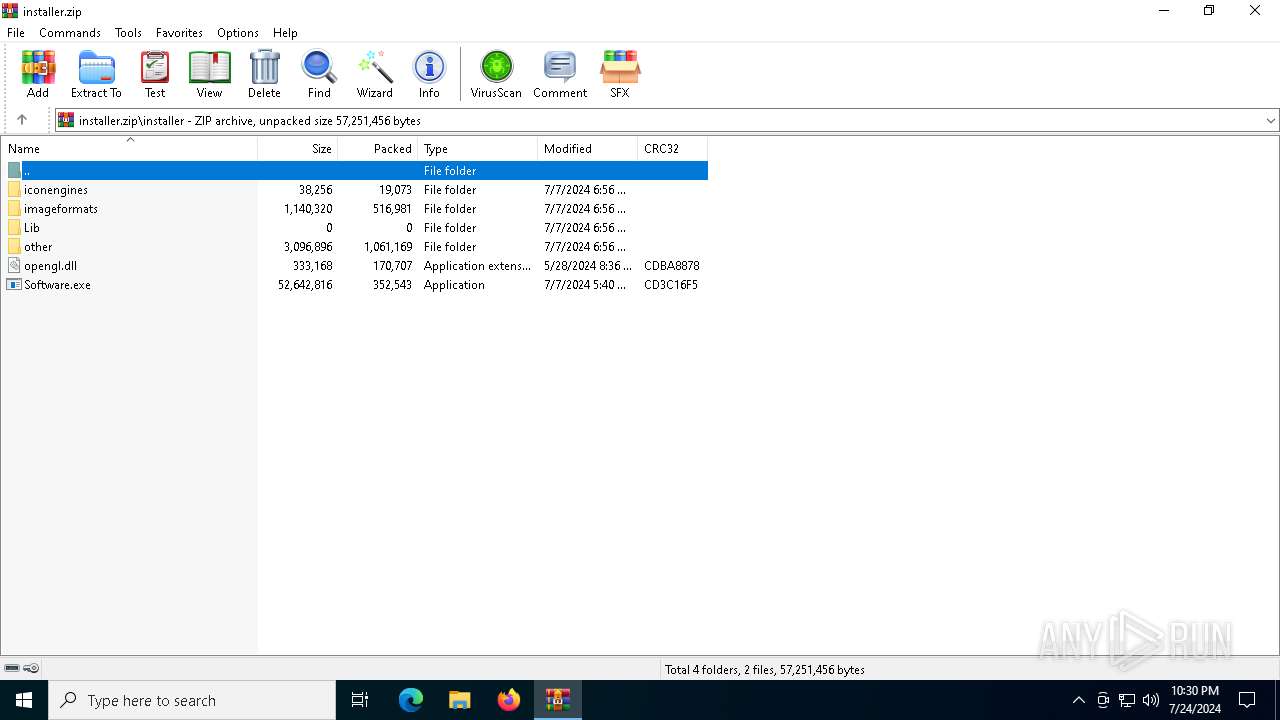
| download: | /aassiinnuuss/Fortnite-skin-changer/releases/download/download/installer.zip |
| Full analysis: | https://app.any.run/tasks/e3e29808-10d2-4e38-9c54-07ba409a8dee |
| Verdict: | Malicious activity |
| Analysis date: | July 24, 2024, 22:29:58 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 21959B72DF39A638F8717080927E7A9F |
| SHA1: | 8F0A0CD6FD2F9E9C031A2E5B9A00427FFD1CE8DE |
| SHA256: | 7506984A531611E36D2AC7F4016E08D8A08A03BA863343DF746DCB3C62E291B9 |
| SSDEEP: | 98304:BAQkkf2RivulIM7OhdXl5k0Z0OhdXl5k0Zt425xTb6I8Yl7r7/Z//qfpGay1Dyb5:71blkj |
MALICIOUS
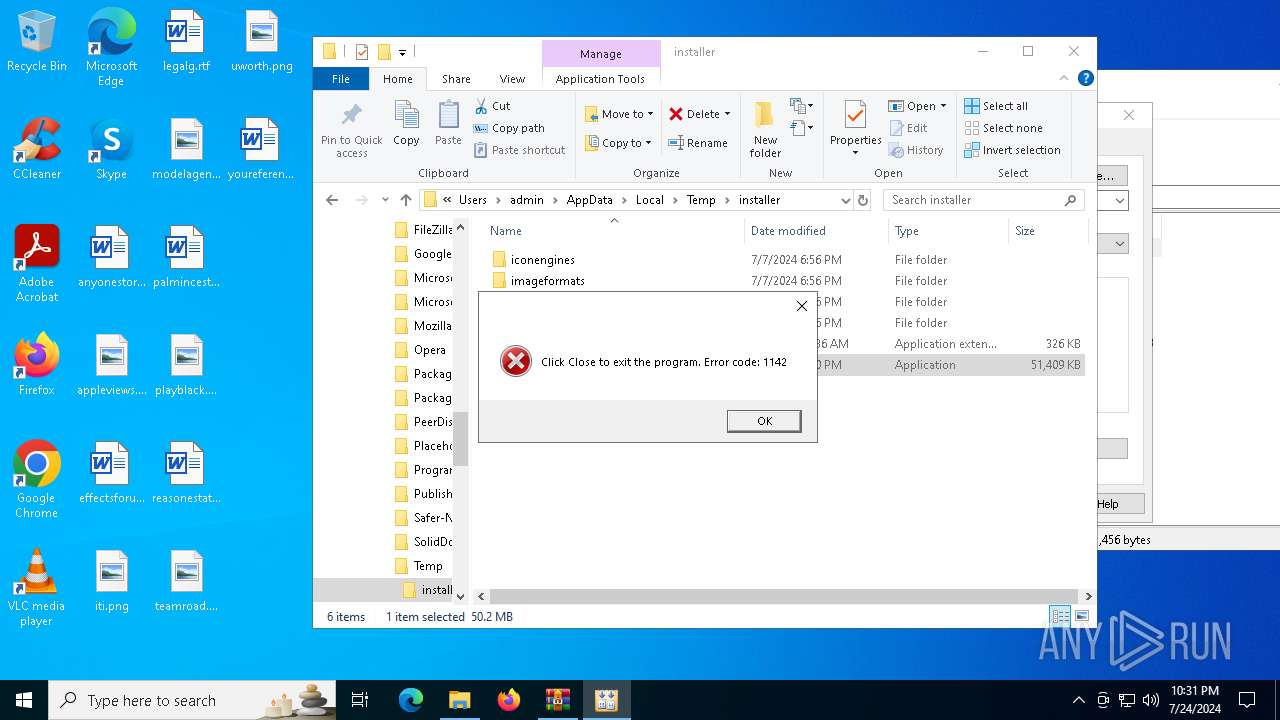
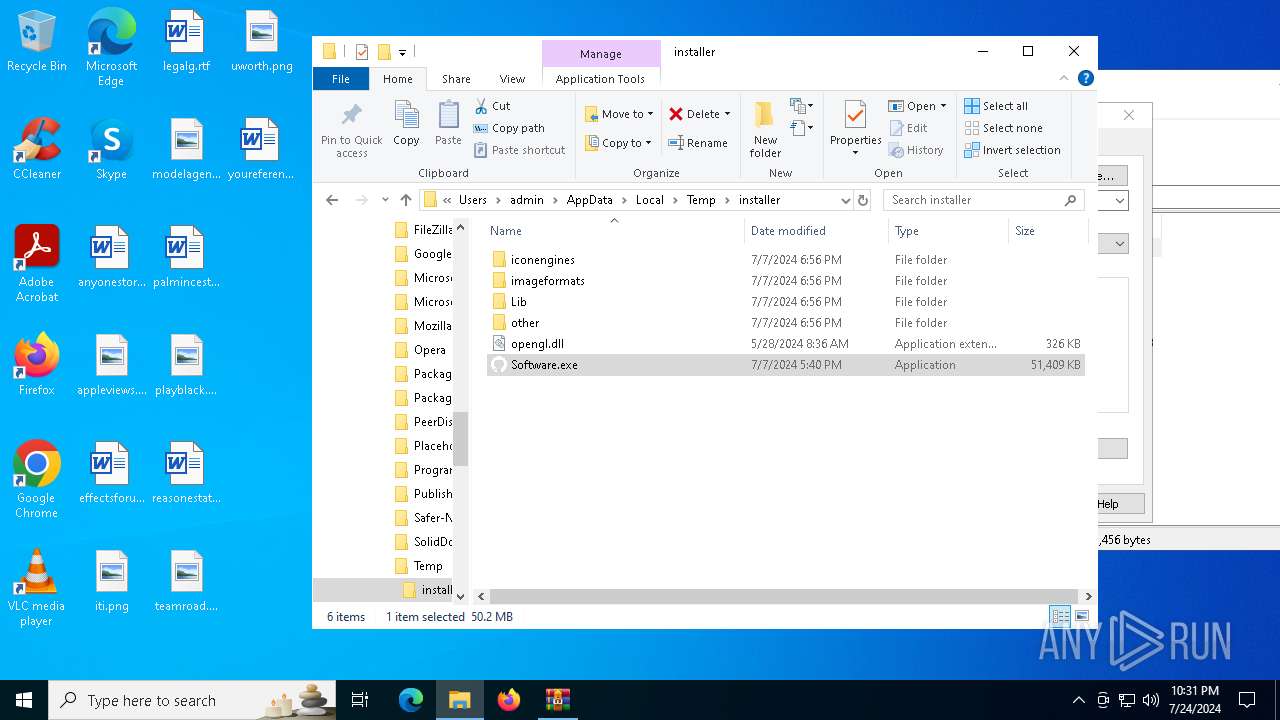
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1096)
- Software.exe (PID: 1008)
- Software.exe (PID: 4656)
SUSPICIOUS
Executable content was dropped or overwritten
- Software.exe (PID: 1008)
- Software.exe (PID: 4656)
INFO
Checks supported languages
- TextInputHost.exe (PID: 4288)
- Software.exe (PID: 1008)
- MSBuild.exe (PID: 6772)
- Software.exe (PID: 4656)
- MSBuild.exe (PID: 6916)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1096)
Reads the computer name
- Software.exe (PID: 1008)
- MSBuild.exe (PID: 6772)
- Software.exe (PID: 4656)
- MSBuild.exe (PID: 6916)
- TextInputHost.exe (PID: 4288)
Reads the machine GUID from the registry
- Software.exe (PID: 1008)
- MSBuild.exe (PID: 6772)
- Software.exe (PID: 4656)
- MSBuild.exe (PID: 6916)
Creates files or folders in the user directory
- Software.exe (PID: 1008)
- Software.exe (PID: 4656)
Manual execution by a user
- Software.exe (PID: 4656)
- Software.exe (PID: 1008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:07:07 22:56:42 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | installer/ |
Total processes
148
Monitored processes
10
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 836 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Software.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
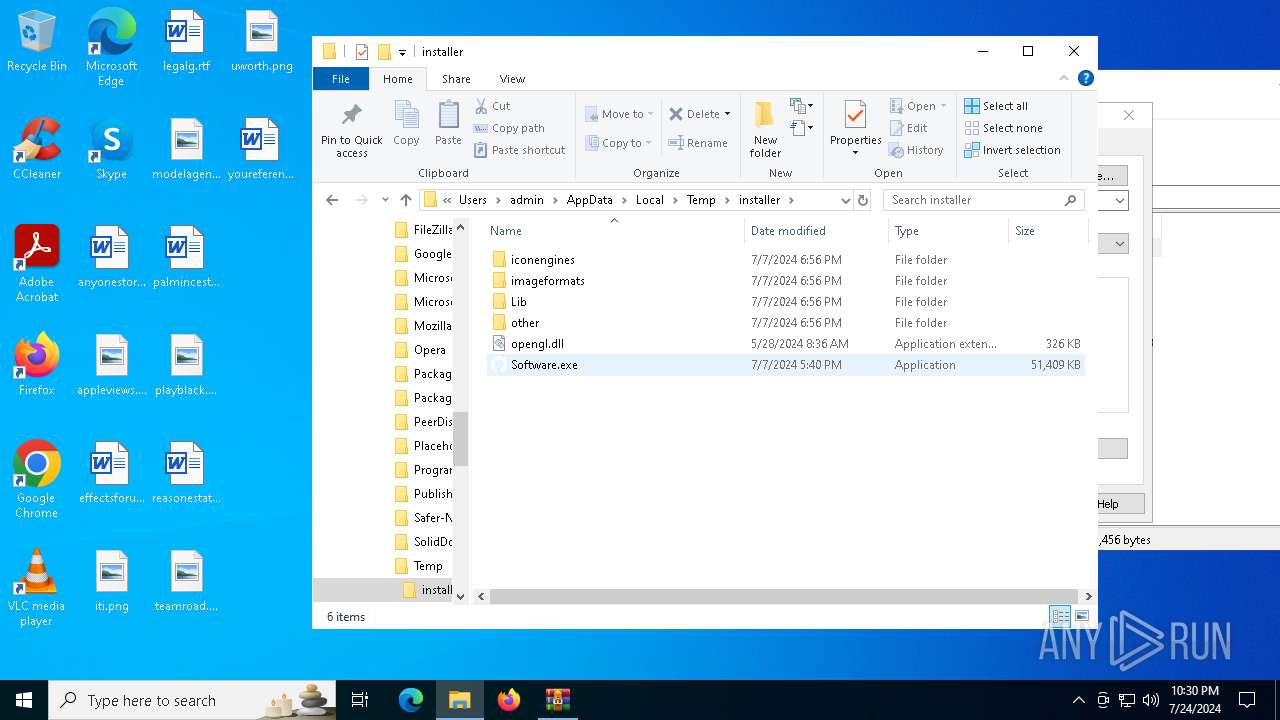
| 1008 | "C:\Users\admin\AppData\Local\Temp\installer\Software.exe" | C:\Users\admin\AppData\Local\Temp\installer\Software.exe | explorer.exe | ||||||||||||
User: admin Company: Github Launcher Integrity Level: MEDIUM Description: Github Launcher Exit code: 0 Version: 1.3.5.0 Modules
| |||||||||||||||
| 1096 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\installer.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2120 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3472 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Software.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4288 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 4656 | "C:\Users\admin\AppData\Local\Temp\installer\Software.exe" | C:\Users\admin\AppData\Local\Temp\installer\Software.exe | explorer.exe | ||||||||||||
User: admin Company: Github Launcher Integrity Level: MEDIUM Description: Github Launcher Exit code: 0 Version: 1.3.5.0 Modules
| |||||||||||||||
| 6336 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6772 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | Software.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 6916 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | Software.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
Total events
13 566
Read events
13 518
Write events
45
Delete events
3
Modification events
| (PID) Process: | (1096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (1096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\installer.zip | |||
| (PID) Process: | (1096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\installer | |||
| (PID) Process: | (1096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | delete value | Name: | MRUList |
Value: | |||
Executable files
15
Suspicious files
13
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\installer\imageformats\qjpeg.dll | executable | |
MD5:3232706A63E7CDF217B8ED674179706C | SHA256:45C1F50C922AC1D9D4108E37F49981FD94F997667E23085CB2EA226D406C5602 | |||
| 1096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\installer\imageformats\qico.dll | executable | |
MD5:EDDF7FB99F2FCAEA6FE4FD34B8FD5D39 | SHA256:9D942215A80A25E10EE1A2BB3D7C76003642D3A2D704C38C822E6A2CA82227BF | |||
| 1096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\installer\imageformats\qtga.dll | executable | |
MD5:D0604A5F13B32A08D5FA5BD887F869A6 | SHA256:2B6444D2A8146A066109CA19618CEEE98444127A5B422C14635AB837887E55BF | |||
| 1096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\installer\other\translations\qt_cs.qm | qm | |
MD5:C32E1507B5BC25E5C34C1EC0262141E1 | SHA256:6862CE2BBFFE5171DCC67B046E5AE6E2E9984C3E981D64B7FBD4A1FC4763A61E | |||
| 1096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\installer\imageformats\qtiff.dll | executable | |
MD5:756D047A93D72771578286E621585ED2 | SHA256:F9EBF4C98C1E0179CD76A1985386928FDB9E6F459E2238ED5530D160DF4F0923 | |||
| 1096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\installer\imageformats\qsvg.dll | executable | |
MD5:2831B334B8EDF842CE273B3DD0ACE1F8 | SHA256:6BAE9AF6A7790FBDEE87B7EFA53D31D8AFF0AB49BDAAEFD3FB87A8CC7D4E8A90 | |||
| 1096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\installer\imageformats\qdds.dll | executable | |
MD5:3FDB8D8407CCCFAA0290036CC0107906 | SHA256:3A71A119EEABCE867B57636070ADEB057443A6EC262BE1360F344CB3905545DB | |||
| 1096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\installer\other\translations\qt_de.qm | qm | |
MD5:91899280EFB4496C8AC0A004CD1469E2 | SHA256:CD711E09012F37003AF75E982E2E40DF14445ACA2800A3702A18612074AD660B | |||
| 1096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\installer\imageformats\qwbmp.dll | executable | |
MD5:131A58669BE7B3850C46D8E841DA5D4E | SHA256:043F3ACF1DC4F4780721DF106046C597262D7344C4B4894E0BE55858B9FAD00E | |||
| 1096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\installer\Software.exe | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
62
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5272 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6636 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5272 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
812 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6012 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3960 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5456 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5368 | SearchApp.exe | 104.126.37.153:443 | — | Akamai International B.V. | DE | unknown |
— | — | 4.209.32.198:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4204 | svchost.exe | 4.209.32.198:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5272 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
r.bing.com |
| whitelisted |