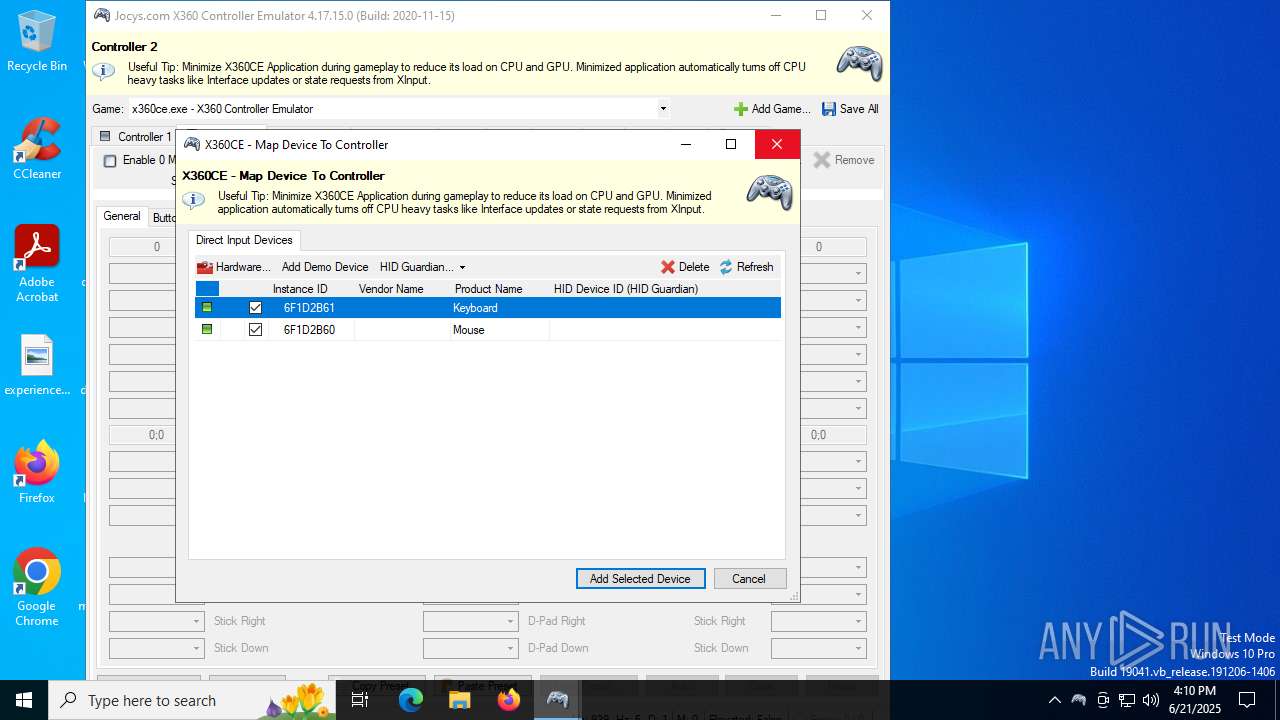
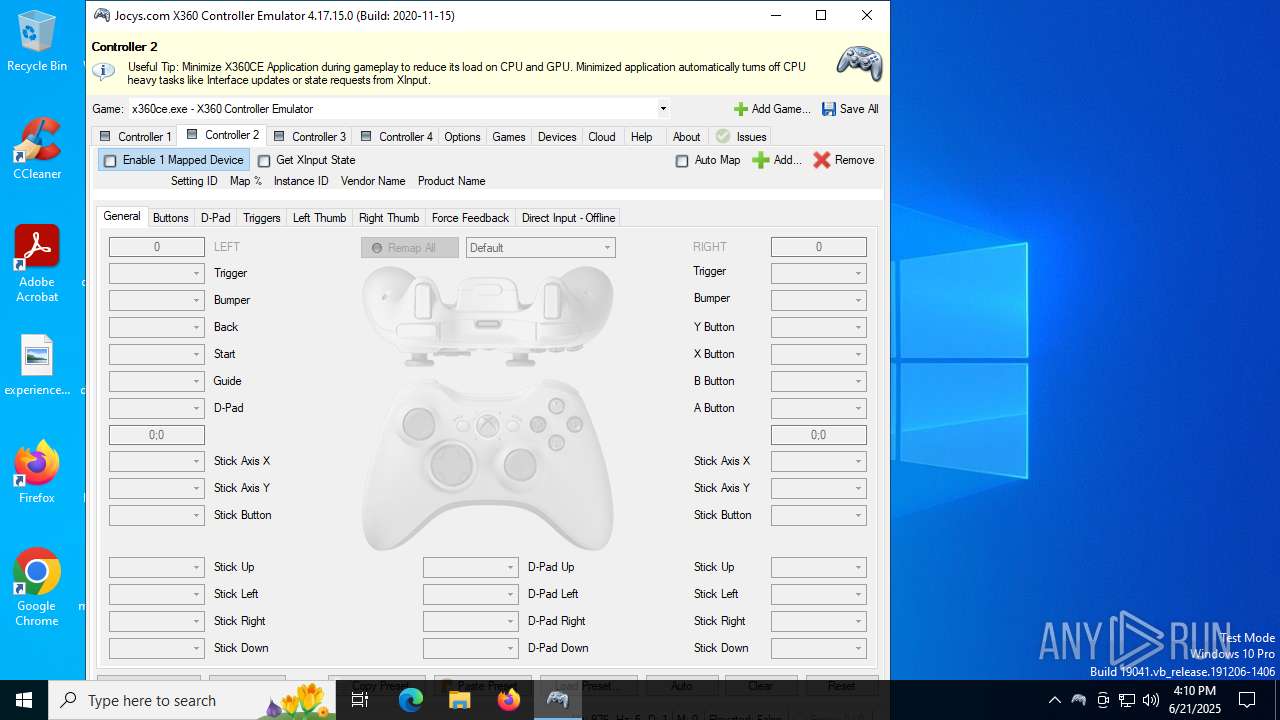
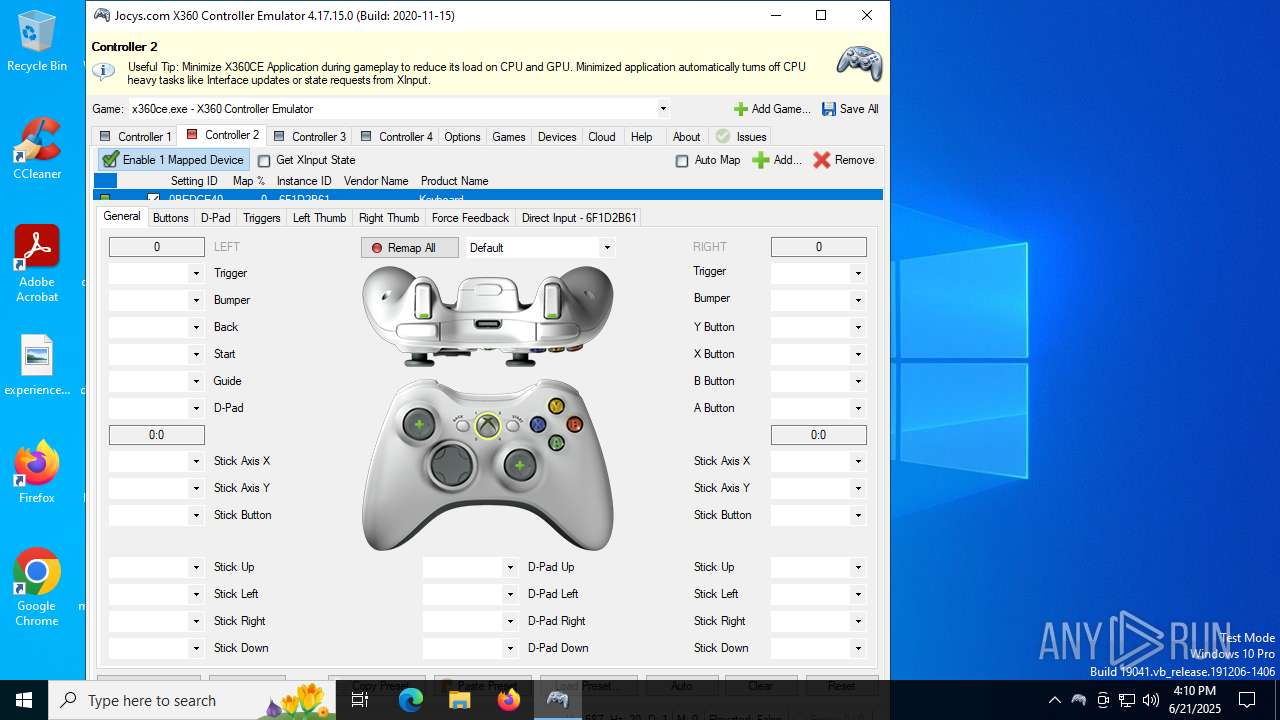
| File name: | x360ce.exe |
| Full analysis: | https://app.any.run/tasks/8ef7feb5-210e-4fe0-a1a7-39cbf9dcfb4d |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 16:10:25 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | BE80F3348B240BCEE1AA96D33FE0E768 |
| SHA1: | 40EA5DE9A7A15F6E0D891CD1BA4BCA8519BB85ED |
| SHA256: | 74FAF334CB0BDD3E9DFAB8C323D4EB3B9B089BCAADC7DBD639D9AA93A4F6F829 |
| SSDEEP: | 196608:n+/7/fO/vBSVnf+viDyJBwhsCArf+viDyJBQhsCAaIF/f+viDyJBaF9hsCA6EJ0k:nX/vu0Bwhs8vu0BQhsvFOvu0BaF9hsR |
MALICIOUS
No malicious indicators.SUSPICIOUS
Searches for installed software
- x360ce.exe (PID: 3640)
Executable content was dropped or overwritten
- x360ce.exe (PID: 3640)
INFO
Checks supported languages
- x360ce.exe (PID: 3640)
Creates files in the program directory
- x360ce.exe (PID: 3640)
Reads the computer name
- x360ce.exe (PID: 3640)
Reads the machine GUID from the registry
- x360ce.exe (PID: 3640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (50.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (32.2) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.6) |
| .exe | | | Win32 Executable (generic) (5.2) |
| .exe | | | Generic Win/DOS Executable (2.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:11:15 17:43:55+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 15299584 |
| InitializedDataSize: | 150016 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xe99302 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.17.15.0 |
| ProductVersionNumber: | 4.17.15.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Wrapper library that translates XInput calls to DirectInput calls, for support old, no XInput compatible gamepads. |
| CompanyName: | Jocys.com |
| FileDescription: | Jocys.com X360 Controller Emulator |
| FileVersion: | 4.17.15.0 |
| InternalName: | x360ce.exe |
| LegalCopyright: | Copyright © Jocys.com 2020 |
| LegalTrademarks: | - |
| OriginalFileName: | x360ce.exe |
| ProductName: | X360 Controller Emulator |
| ProductVersion: | 4.17.15.0 |
| AssemblyVersion: | 4.17.15.0 |
Total processes
132
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3640 | "C:\Users\admin\AppData\Local\Temp\x360ce.exe" | C:\Users\admin\AppData\Local\Temp\x360ce.exe | explorer.exe | ||||||||||||
User: admin Company: Jocys.com Integrity Level: MEDIUM Description: Jocys.com X360 Controller Emulator Version: 4.17.15.0 Modules
| |||||||||||||||
Total events
5 367
Read events
5 360
Write events
7
Delete events
0
Modification events
| (PID) Process: | (3640) x360ce.exe | Key: | HKEY_CURRENT_USER\System\CurrentControlSet\Control\MediaProperties\PrivateProperties\DirectInput\VID_0627&PID_0001\Calibration\0 |
| Operation: | write | Name: | GUID |
Value: B0A7F642BA4EF0118001444553540000 | |||
| (PID) Process: | (3640) x360ce.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\X360CE.EXE5FB168DB00EBE910 |
| Operation: | write | Name: | Name |
Value: X360CE.EXE | |||
| (PID) Process: | (3640) x360ce.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\X360CE.EXE5FB168DB00EBE910 |
| Operation: | write | Name: | UsesMapper |
Value: 00000000 | |||
| (PID) Process: | (3640) x360ce.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: X360CE.EXE | |||
| (PID) Process: | (3640) x360ce.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | Id |
Value: X360CE.EXE5FB168DB00EBE910 | |||
| (PID) Process: | (3640) x360ce.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | Version |
Value: 00080000 | |||
| (PID) Process: | (3640) x360ce.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | MostRecentStart |
Value: 89A84C05C7E2DB01 | |||
Executable files
1
Suspicious files
0
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3640 | x360ce.exe | C:\ProgramData\X360CE\Settings\x360ce.Options.xml | text | |
MD5:0345954272C3992AA160F10A89DAF02C | SHA256:758CFD9446A8850B43C974344C1B464B77D2A825D2771D65FBDDEB040B0EBA14 | |||
| 3640 | x360ce.exe | C:\ProgramData\X360CE\Settings\x360ce.PadSettings.xml | text | |
MD5:518B7E8043729212AEF492310F8CF421 | SHA256:9AA4B9AC4E8A18BB2C9ECE24E007171B19999CBAC70A6567D171811599010732 | |||
| 3640 | x360ce.exe | C:\ProgramData\X360CE\Settings\x360ce.UserDevices.xml | text | |
MD5:C59E2E26ABA4EB3B1C699838DD452276 | SHA256:613E34FD780F73E981004D0B3AF9D6F39C86438B3B665DFFC230A9F852A206FC | |||
| 3640 | x360ce.exe | C:\ProgramData\X360CE\Settings\x360ce.Presets.xml | text | |
MD5:E22EF49BE69AF14AAA588938A80FFB3C | SHA256:D874CCA7E90E93FBD217C3924E5F01FE7DD5B92D83456C0B86284AB1693B923F | |||
| 3640 | x360ce.exe | C:\ProgramData\X360CE\Settings\x360ce.XInputMask.xml | text | |
MD5:2736469BA90BDF85E8C04C778114A656 | SHA256:FBB85DD2F408CD3D442D2511A41B0032524E31BA5F3166589E860A698BF5D2A0 | |||
| 3640 | x360ce.exe | C:\ProgramData\X360CE\Settings\x360ce.Layouts.xml | text | |
MD5:E6C10E8851EB987D3FBF5F146066870A | SHA256:A61D1C2E1AC1EC273A40B1069A31E15C3FCA76F9792E2B0C156B124A4A7C32FA | |||
| 3640 | x360ce.exe | C:\ProgramData\X360CE\Temp\ViGEmClient.dll.84A31178\ViGEmClient.dll | executable | |
MD5:A8781AFCBA77CCB180939FDBD5767168 | SHA256:02B50CBE797600959F43148991924D93407F04776E879BCE7B979F30DD536BA9 | |||
| 3640 | x360ce.exe | C:\ProgramData\X360CE\Settings\x360ce.UserSettings.xml | text | |
MD5:9D099E80ECF73BE1610855B3A84EC8B5 | SHA256:A30B3506B24AD894638E6995FD7E0D257F4A5378B7F8105298D56C996EAD9493 | |||
| 3640 | x360ce.exe | C:\ProgramData\X360CE\Settings\x360ce.Summaries.xml | text | |
MD5:86EF143234C7C15066AE67732A42A257 | SHA256:352789A74CB6D9187BFEDED112F8A780E9A5F59D0BD713F896A9AF736C4CCA92 | |||
| 3640 | x360ce.exe | C:\ProgramData\X360CE\Settings\x360ce.Programs.xml | text | |
MD5:FF3EE9530247EFA888D7A24611B1BDCD | SHA256:57C26E543061F382AA15F2621C0891BD7428424CA49D6155B0257CE2AE83277C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
12
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 184.24.77.23:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3788 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 184.24.77.23:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
x360ce.exe | InitializeServices
|
x360ce.exe | x360ce.exe Information: 0 : |
x360ce.exe | InitializeCloudClient
|
x360ce.exe | x360ce.exe Information: 0 : |
x360ce.exe | Stopping remote server... |
x360ce.exe | already stopped.
|