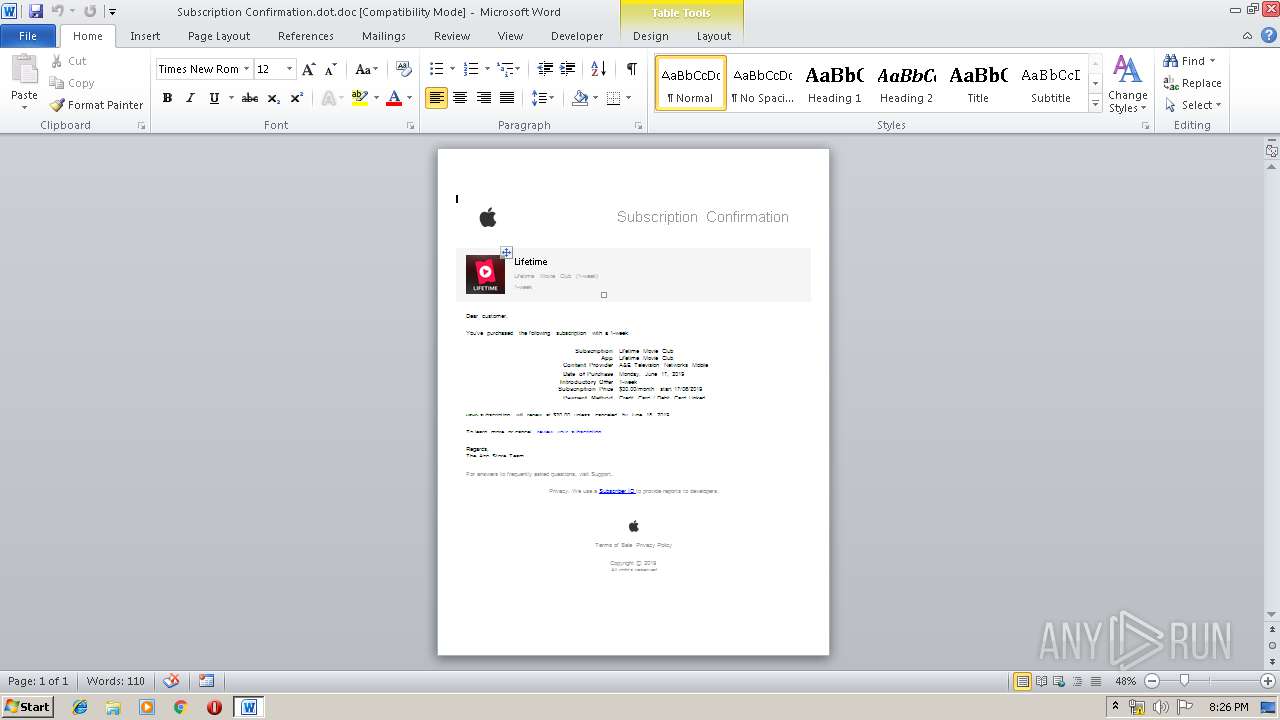
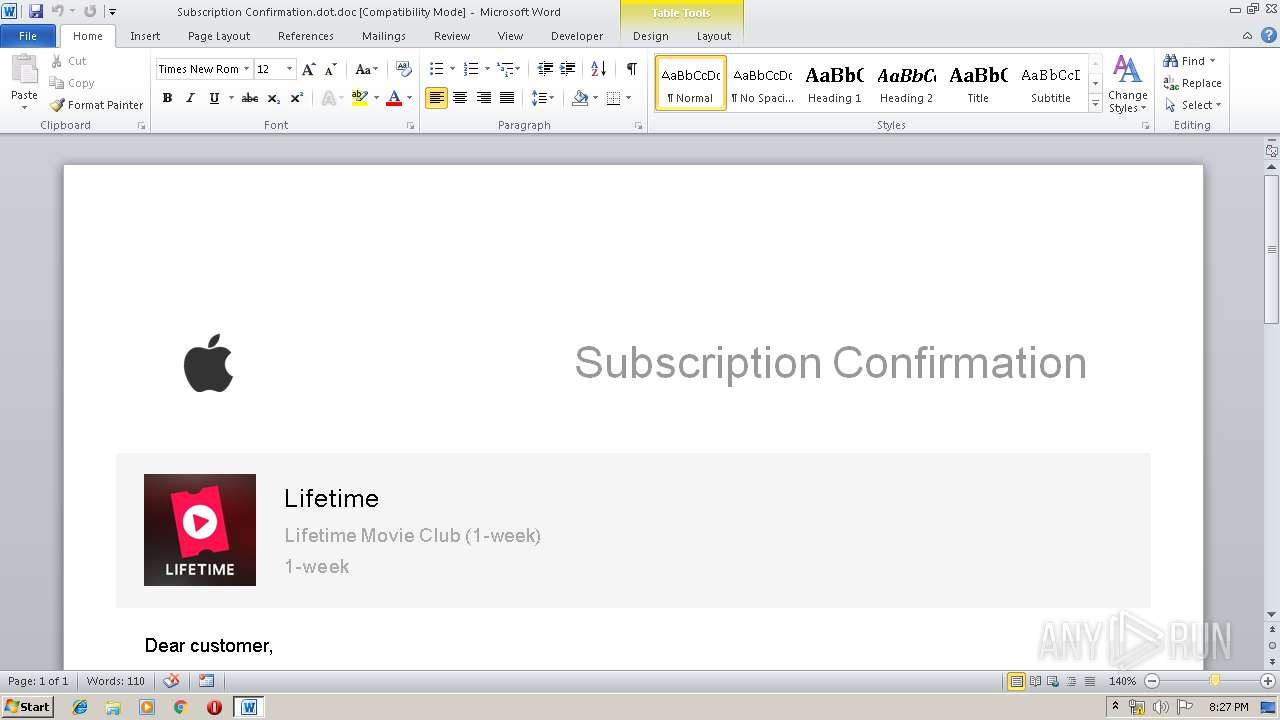
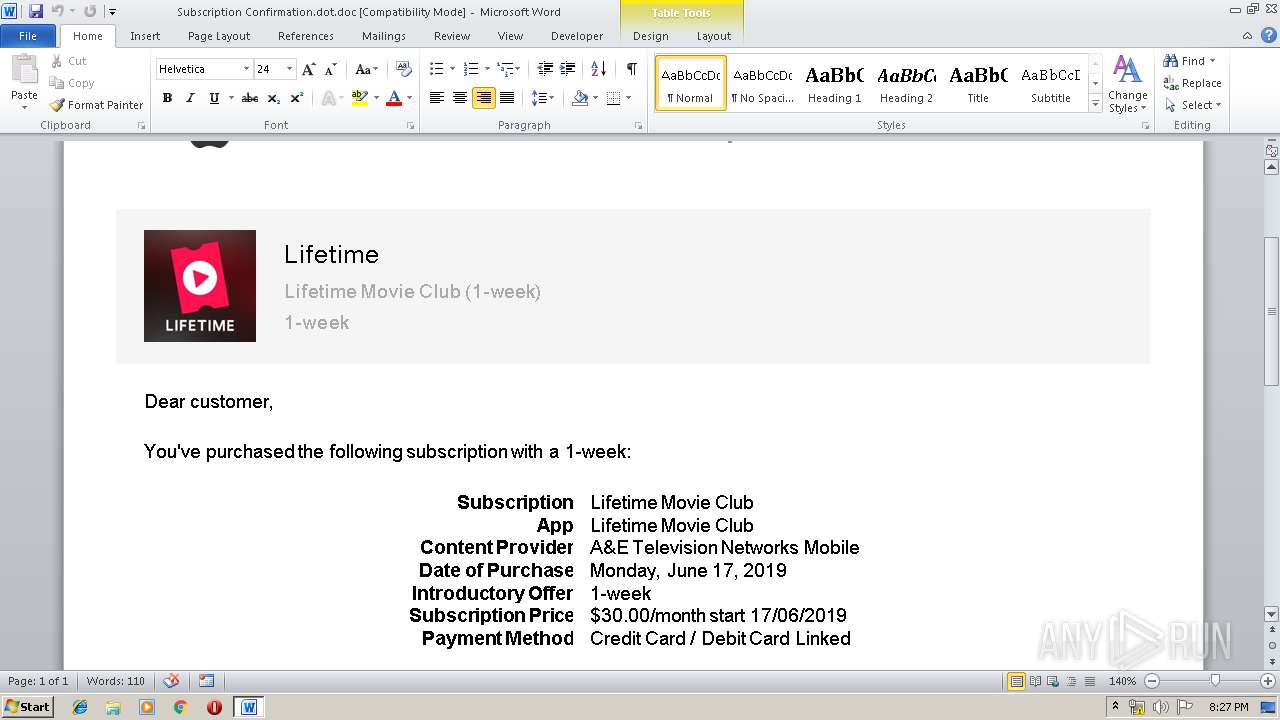
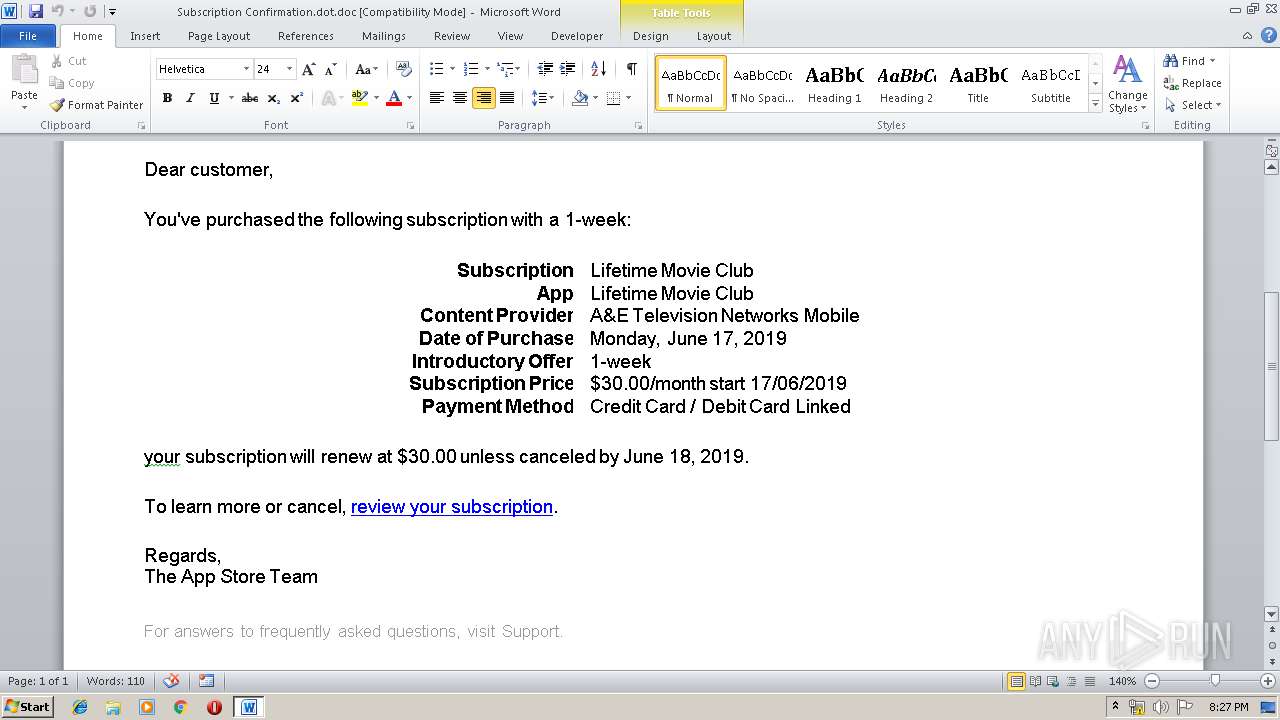
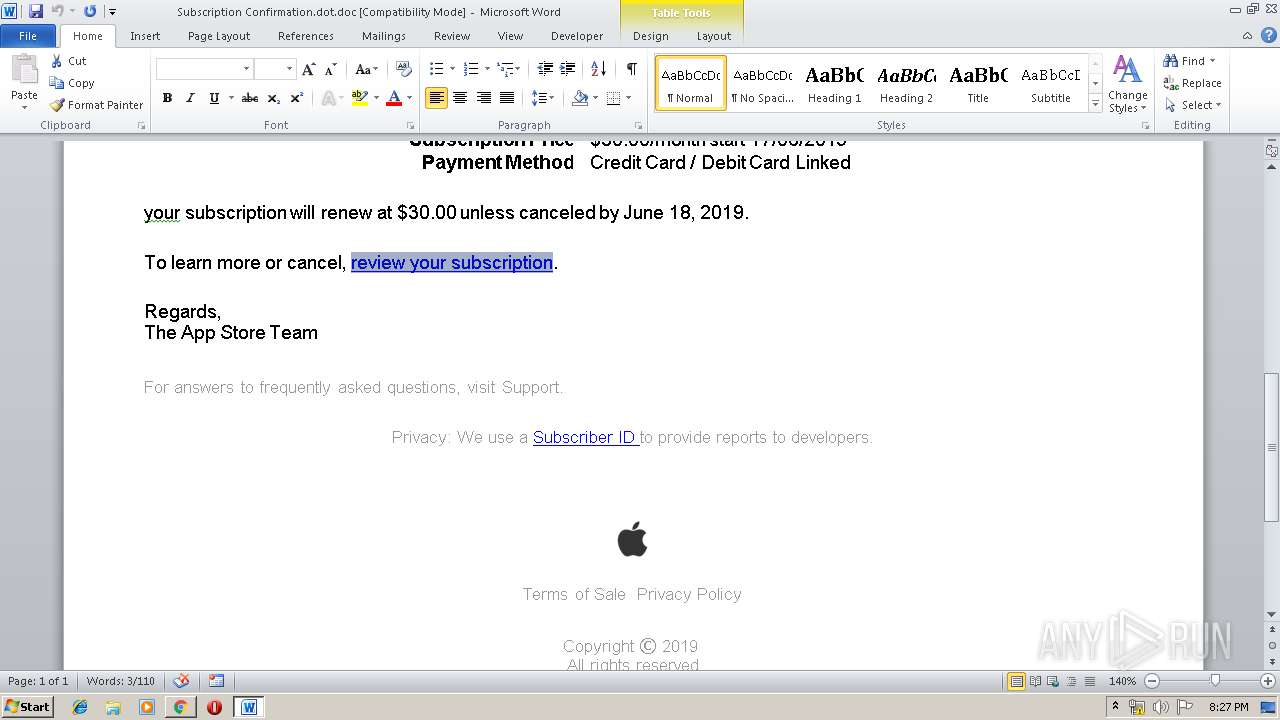
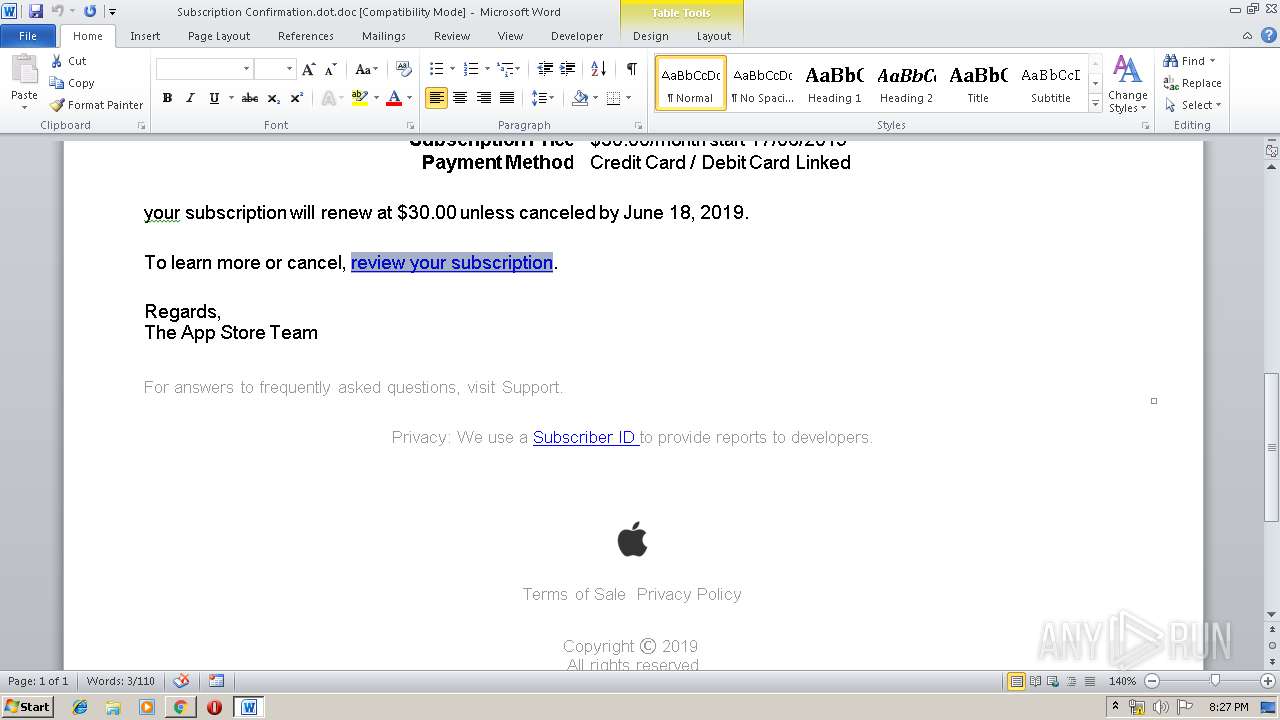
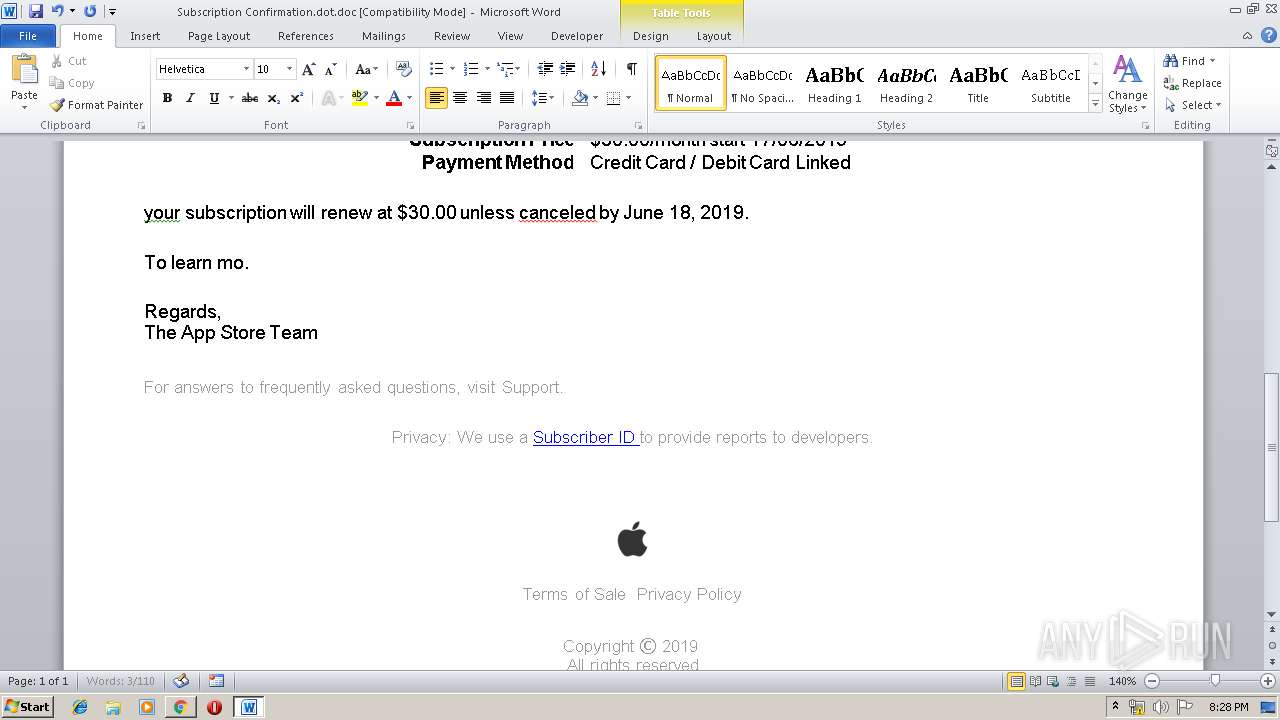
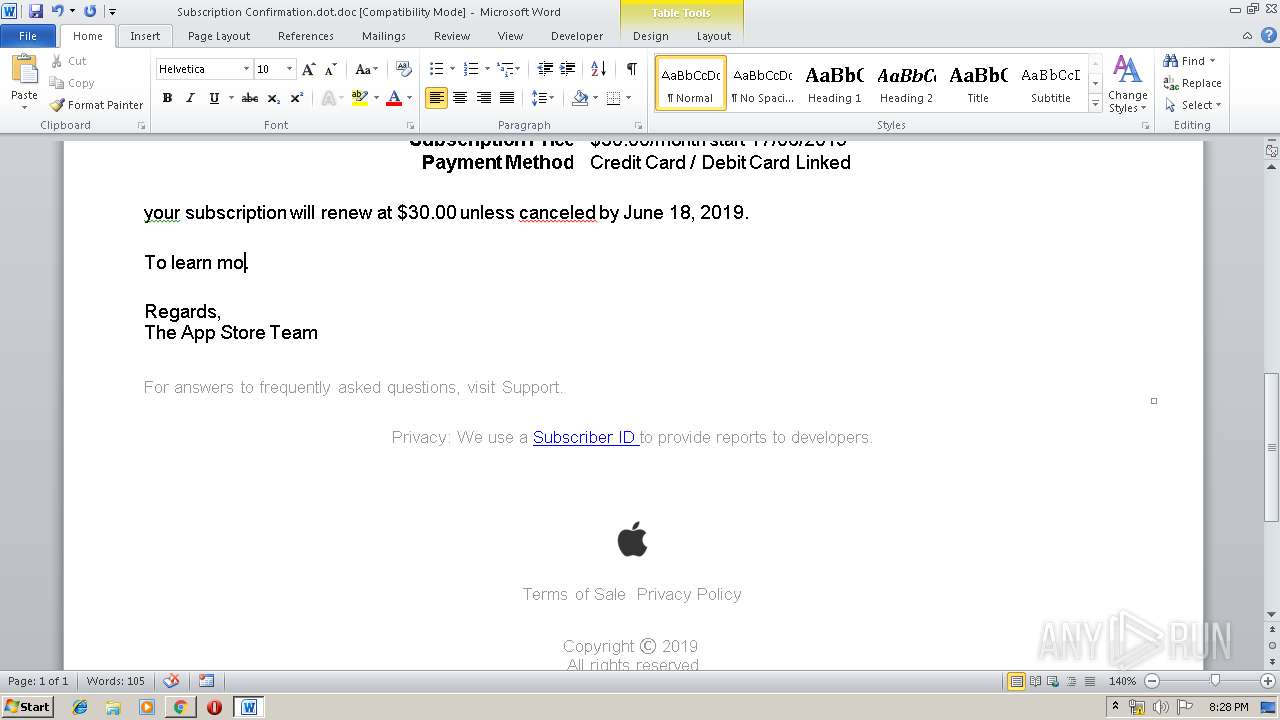
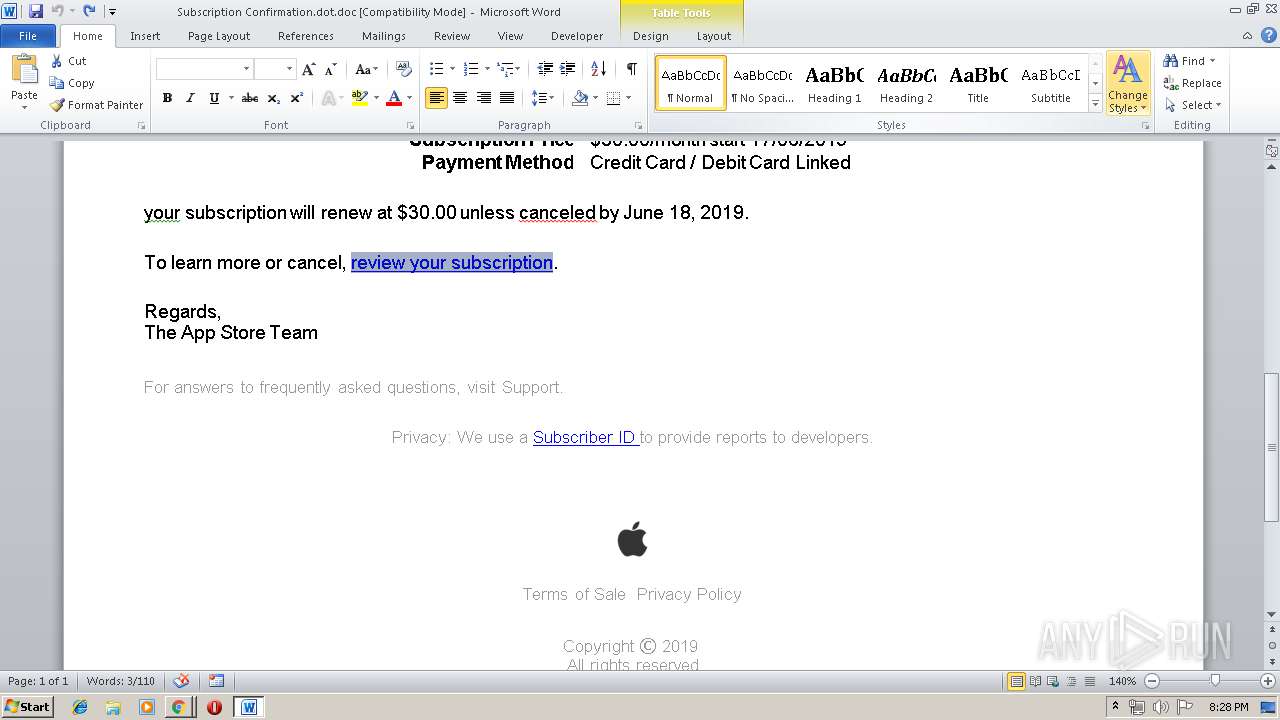
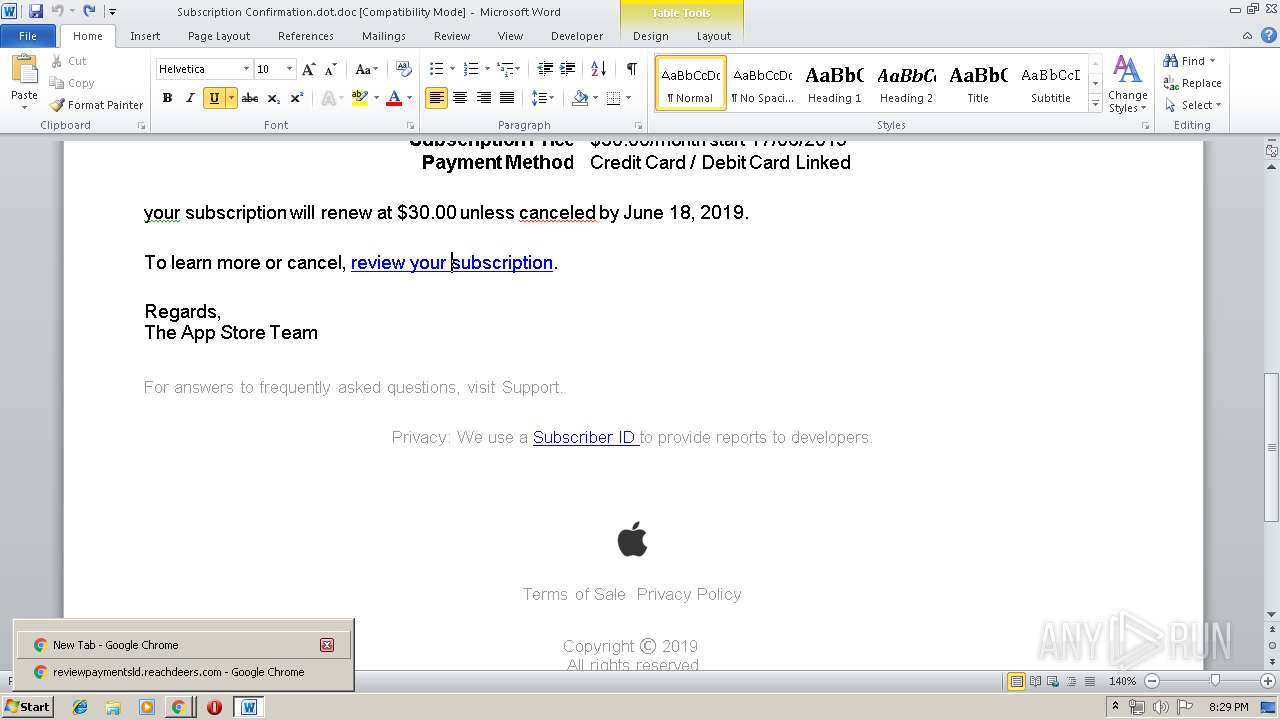
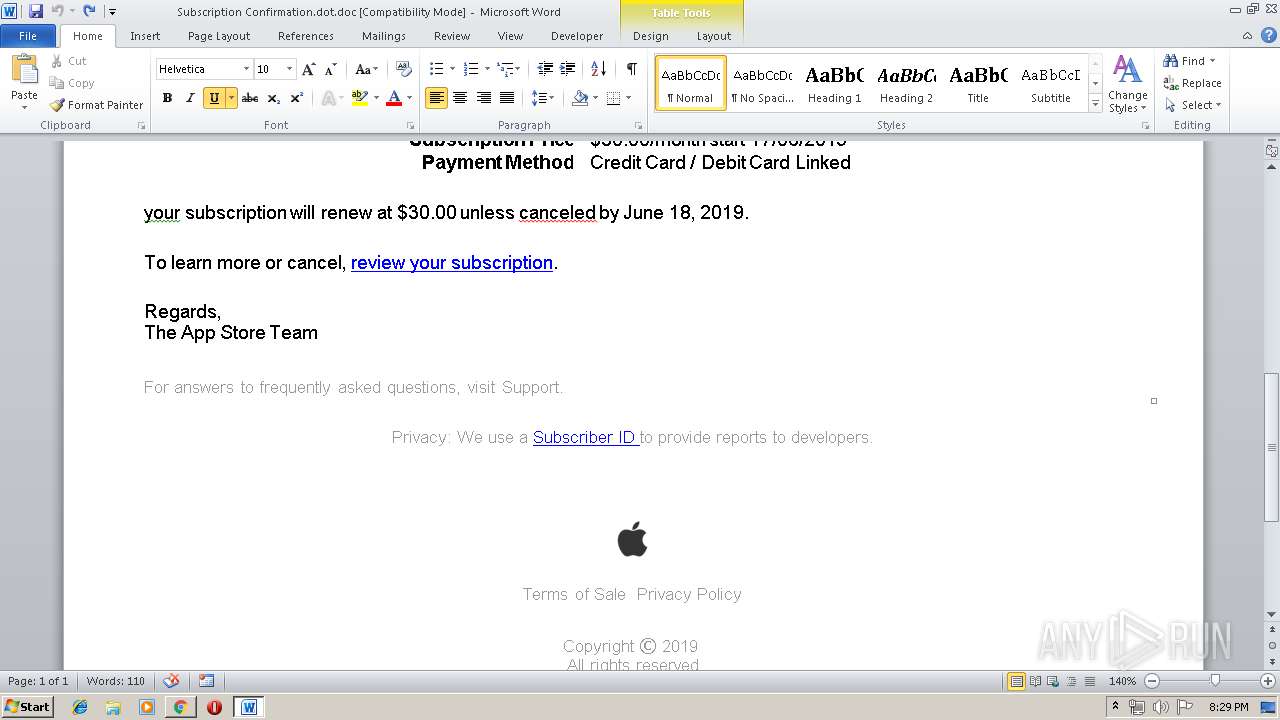
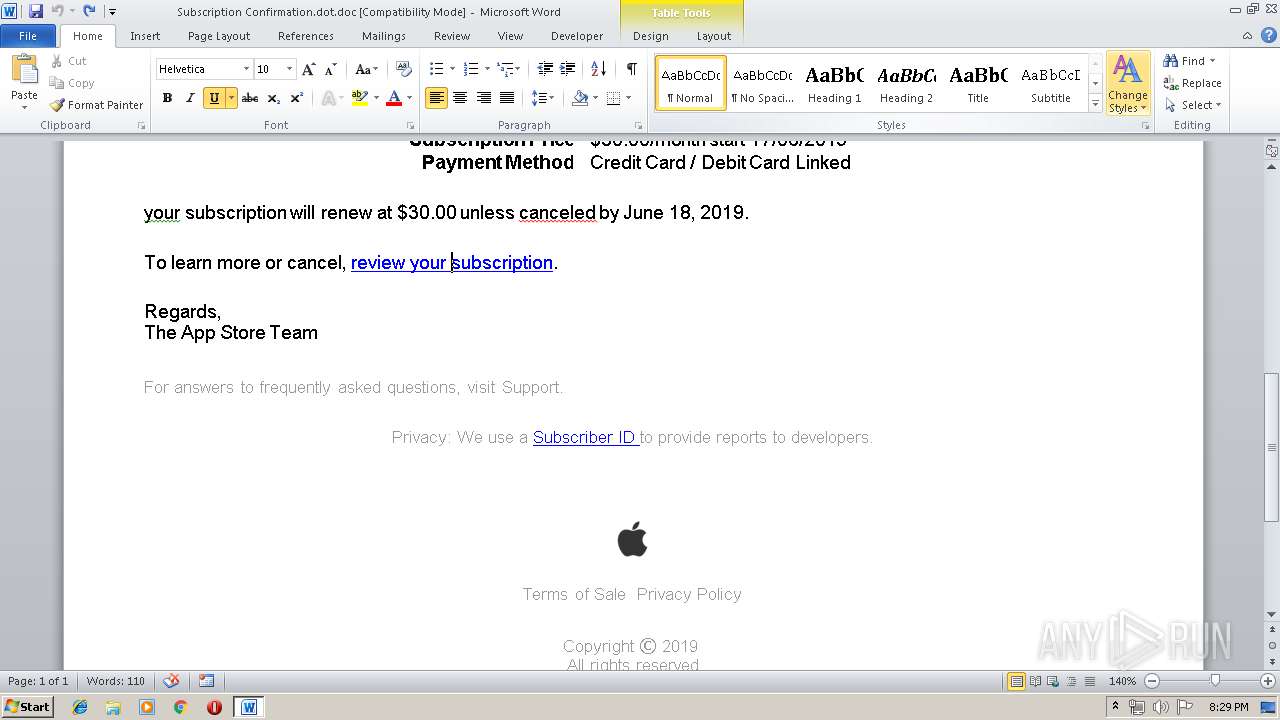
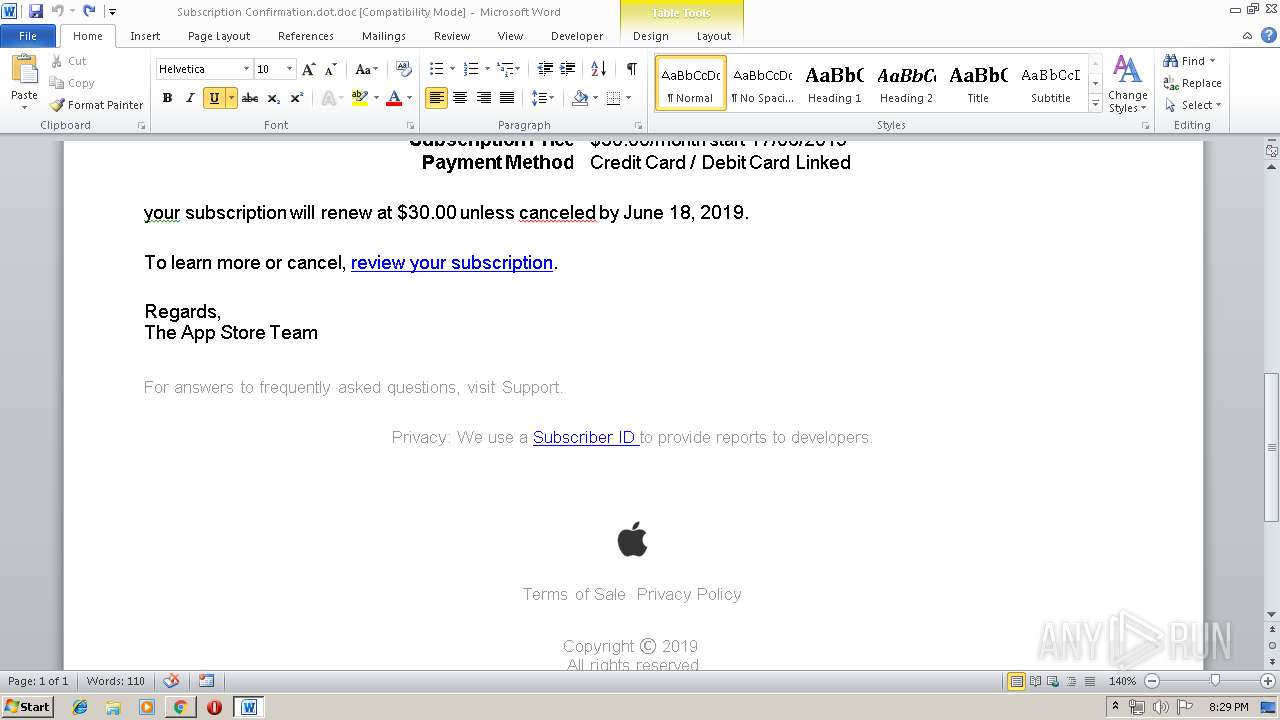
| File name: | Subscription Confirmation.dot |
| Full analysis: | https://app.any.run/tasks/84c22fe8-d419-4e49-be91-66a28a26dd3e |
| Verdict: | Malicious activity |
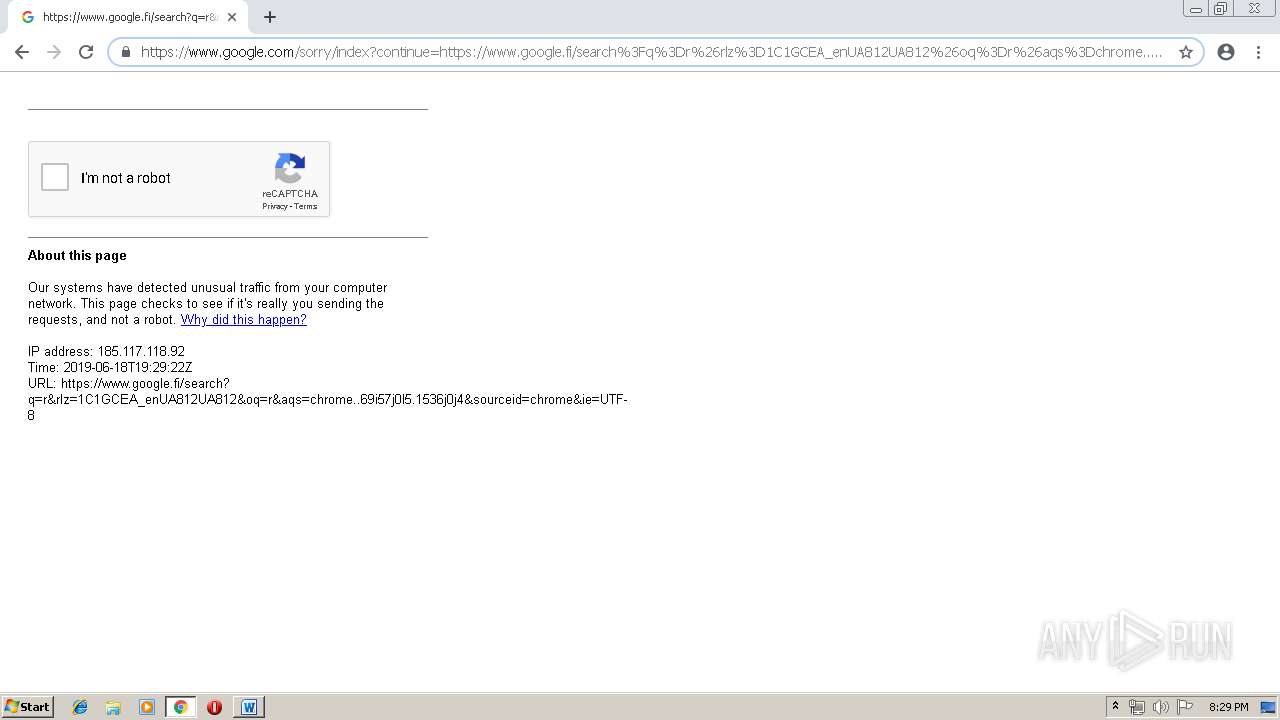
| Analysis date: | June 18, 2019, 19:25:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Author: User, Template: Subscription Confirmation, Last Saved By: User, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Total Editing Time: 01:00, Create Time/Date: Sun Jun 16 21:15:00 2019, Last Saved Time/Date: Sun Jun 16 21:16:00 2019, Number of Pages: 1, Number of Words: 155, Number of Characters: 887, Security: 0 |
| MD5: | 68529A182EBC2A6682C4D4F408178ABF |
| SHA1: | B997923BC6338840E887BC3DBD1D3D07F5EFD47F |
| SHA256: | 74F0C302F8CD0CA79792CE7A97647841B49269AE52FE4F5EAD5704AA3B138E38 |
| SSDEEP: | 384:pQ9tKFXWZcQFO2kTImX9ZlqiwW0+RgkeBPN/9NG95i9QeU90Wgq9933U9r5I9iRW:pQ9tKFyNXiOjeTVI9s066DKxz99 |
MALICIOUS
Starts Visual C# compiler
- sdiagnhost.exe (PID: 1940)
SUSPICIOUS
Executable content was dropped or overwritten
- msdt.exe (PID: 1252)
Reads Internet Cache Settings
- WINWORD.EXE (PID: 3316)
Uses IPCONFIG.EXE to discover IP address
- sdiagnhost.exe (PID: 1940)
Executed via COM
- helppane.exe (PID: 3812)
- sdiagnhost.exe (PID: 1940)
Reads internet explorer settings
- helppane.exe (PID: 3812)
- CLVIEW.EXE (PID: 3824)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3272)
Starts Microsoft Office Application
- WINWORD.EXE (PID: 3316)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3316)
- CLVIEW.EXE (PID: 3824)
Creates files in the user directory
- WINWORD.EXE (PID: 3316)
Manual execution by user
- msdt.exe (PID: 1252)
- rundll32.exe (PID: 3032)
- chrome.exe (PID: 3272)
- chrome.exe (PID: 1096)
- chrome.exe (PID: 3968)
Reads settings of System Certificates
- chrome.exe (PID: 3272)
Application launched itself
- chrome.exe (PID: 3272)
- chrome.exe (PID: 3968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Author: | User |
|---|---|
| Template: | Subscription Confirmation |
| LastModifiedBy: | User |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | 1.0 minutes |
| LastPrinted: | - |
| CreateDate: | 2019:06:16 20:15:00 |
| ModifyDate: | 2019:06:16 20:16:00 |
| Pages: | 1 |
| Words: | 155 |
| Characters: | 887 |
| Security: | None |
| Company: | - |
| Lines: | 7 |
| Paragraphs: | 2 |
| CharCountWithSpaces: | 1040 |
| AppVersion: | 14 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CodePage: | Windows Latin 1 (Western European) |
| Hyperlinks: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
111
Monitored processes
76
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 288 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=952,479871228900050027,15173844472507762491,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=10662975834861410651 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10662975834861410651 --renderer-client-id=11 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2972 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 332 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,4105469506385273615,9452525855187438008,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=8391268294135190379 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8391268294135190379 --renderer-client-id=34 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4272 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 772 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,4105469506385273615,9452525855187438008,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=1804637574937020277 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1804637574937020277 --renderer-client-id=32 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1012 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 928 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=952,479871228900050027,15173844472507762491,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=5345223212735764618 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5345223212735764618 --renderer-client-id=12 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2224 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 936 | "C:\Windows\system32\ipconfig.exe" /all | C:\Windows\system32\ipconfig.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 988 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,4105469506385273615,9452525855187438008,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=5822824100374427959 --mojo-platform-channel-handle=4364 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1016 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=960,4105469506385273615,9452525855187438008,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAACAAwAAAQAAAAAAAAAAAGAAAAAAAAEAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=9298114761621959383 --mojo-platform-channel-handle=4880 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,4105469506385273615,9452525855187438008,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=3098570646325810427 --mojo-platform-channel-handle=4768 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1096 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | — | explorer.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1180 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,4105469506385273615,9452525855187438008,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=5288155758895167116 --mojo-platform-channel-handle=2752 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
Total events
2 694
Read events
2 104
Write events
569
Delete events
21
Modification events
| (PID) Process: | (3316) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | z9? |
Value: 7A393F00F40C0000010000000000000000000000 | |||
| (PID) Process: | (3316) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3316) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3316) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1322385438 | |||
| (PID) Process: | (3316) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1322385552 | |||
| (PID) Process: | (3316) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1322385553 | |||
| (PID) Process: | (3316) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: F40C00001227049C0B26D50100000000 | |||
| (PID) Process: | (3316) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | ;? |
Value: 203B3F00F40C000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3316) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | ;? |
Value: 203B3F00F40C000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3316) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
2
Suspicious files
116
Text files
431
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3316 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRED6A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3316 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\Subscription Confirmation.dot.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 3812 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC6951.tmp | — | |
MD5:— | SHA256:— | |||
| 3812 | csc.exe | C:\Users\admin\AppData\Local\Temp\bhc-9tsp.pdb | — | |
MD5:— | SHA256:— | |||
| 2708 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES6952.tmp | — | |
MD5:— | SHA256:— | |||
| 3812 | csc.exe | C:\Users\admin\AppData\Local\Temp\bhc-9tsp.dll | — | |
MD5:— | SHA256:— | |||
| 3812 | csc.exe | C:\Users\admin\AppData\Local\Temp\bhc-9tsp.out | — | |
MD5:— | SHA256:— | |||
| 1940 | sdiagnhost.exe | C:\Users\admin\AppData\Local\Temp\D85833DB-F721-4C8D-991F-5CF9A11B5DE8.Diagnose.0.etl | — | |
MD5:— | SHA256:— | |||
| 3316 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 3316 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
37
DNS requests
43
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3272 | chrome.exe | GET | 200 | 87.245.198.16:80 | http://r5---sn-gxuog0-axqe.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=185.117.118.92&mm=28&mn=sn-gxuog0-axqe&ms=nvh&mt=1560885776&mv=u&pl=24&shardbypass=yes | RU | crx | 842 Kb | whitelisted |
3272 | chrome.exe | GET | 302 | 172.217.16.174:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 511 b | whitelisted |
972 | svchost.exe | GET | 200 | 92.122.253.175:80 | http://www.microsoft.com/ | unknown | html | 1020 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
972 | svchost.exe | 92.122.253.175:80 | www.microsoft.com | GTT Communications Inc. | — | suspicious |
3272 | chrome.exe | 8.8.8.8:53 | — | Google Inc. | US | malicious |
3272 | chrome.exe | 216.58.207.46:443 | clients1.google.com | Google Inc. | US | whitelisted |
3272 | chrome.exe | 172.217.18.3:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3272 | chrome.exe | 172.217.22.78:443 | apis.google.com | Google Inc. | US | whitelisted |
3272 | chrome.exe | 172.217.16.132:443 | www.google.com | Google Inc. | US | whitelisted |
3272 | chrome.exe | 172.217.16.138:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3272 | chrome.exe | 216.58.208.46:443 | ogs.google.com | Google Inc. | US | whitelisted |
3272 | chrome.exe | 172.217.18.174:443 | clients2.google.com | Google Inc. | US | whitelisted |
3272 | chrome.exe | 216.58.207.33:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
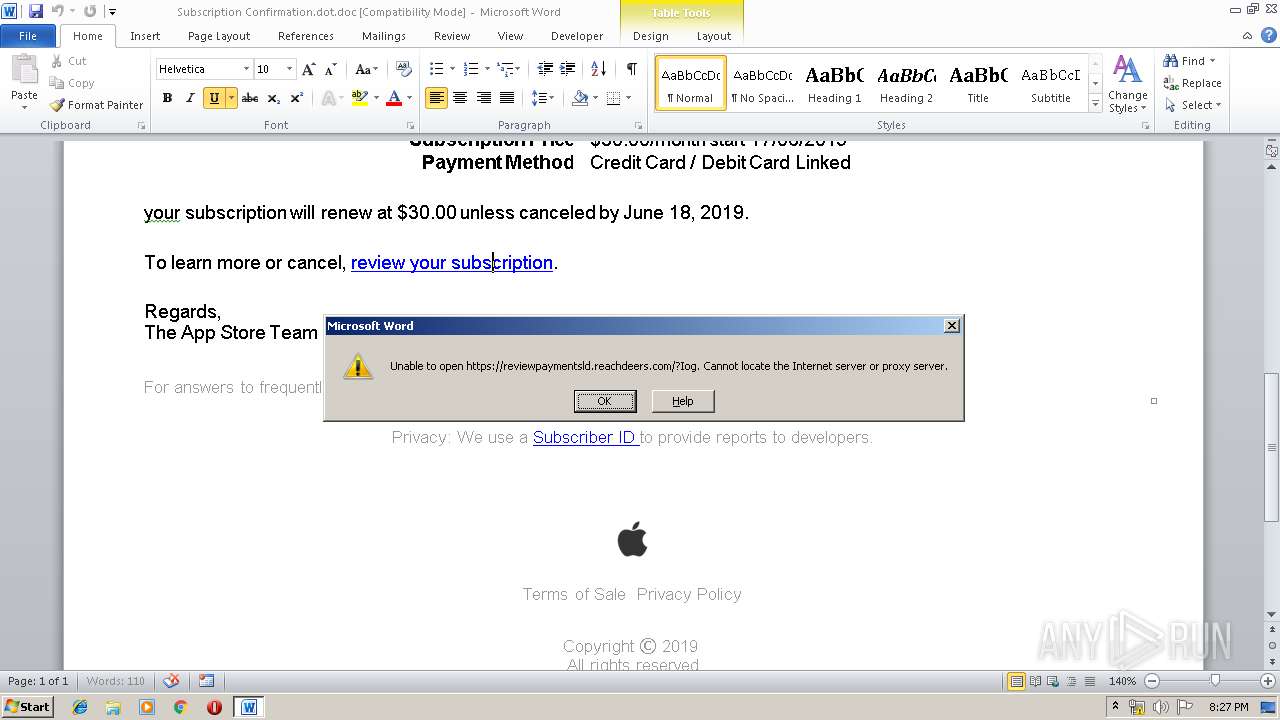
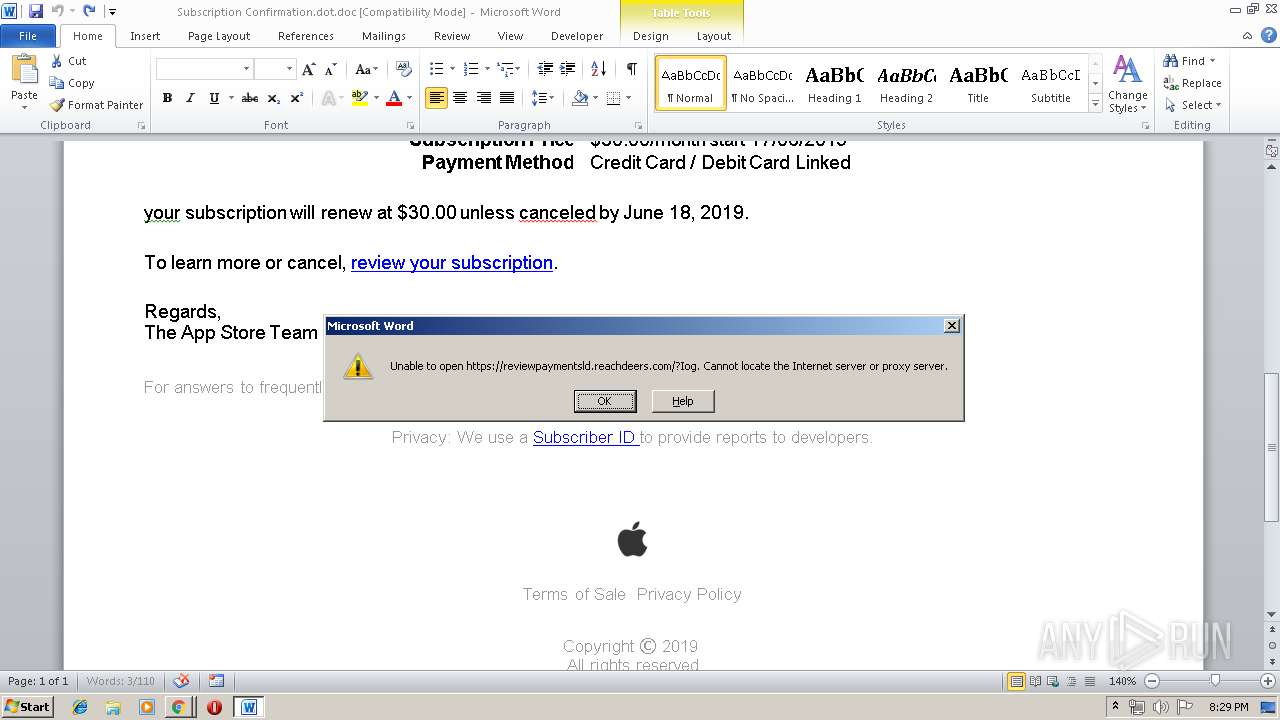
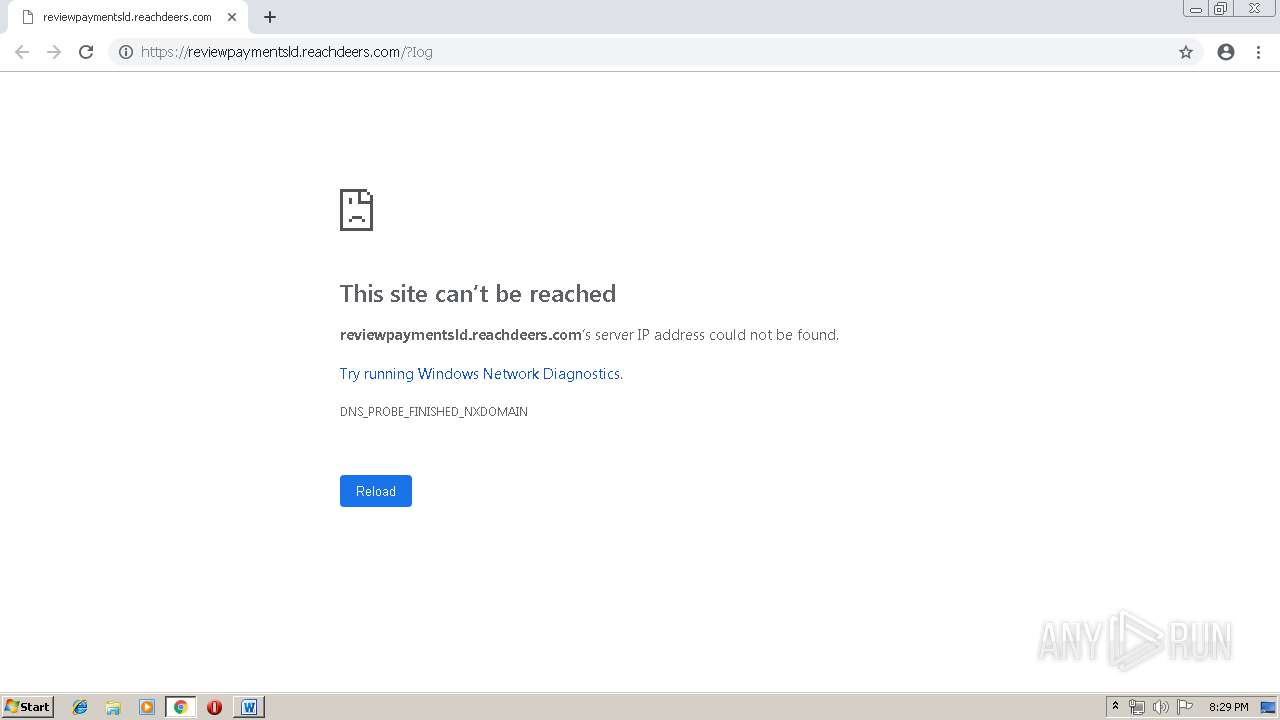
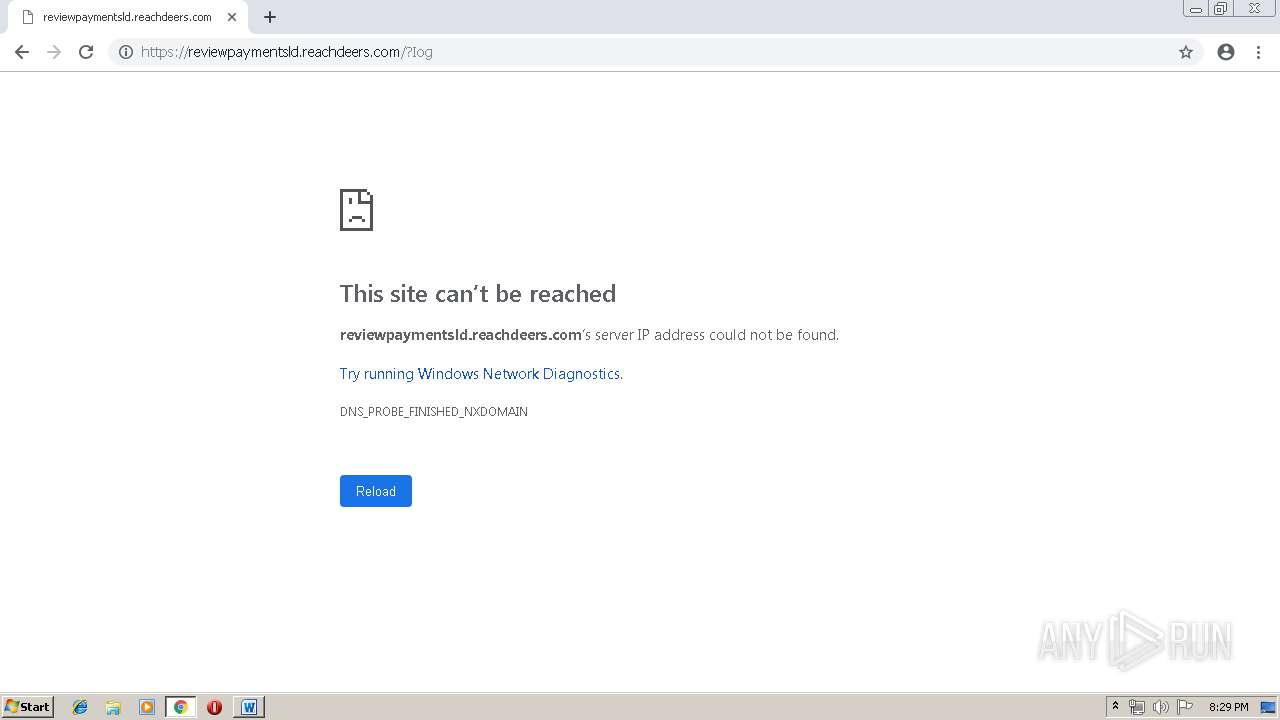
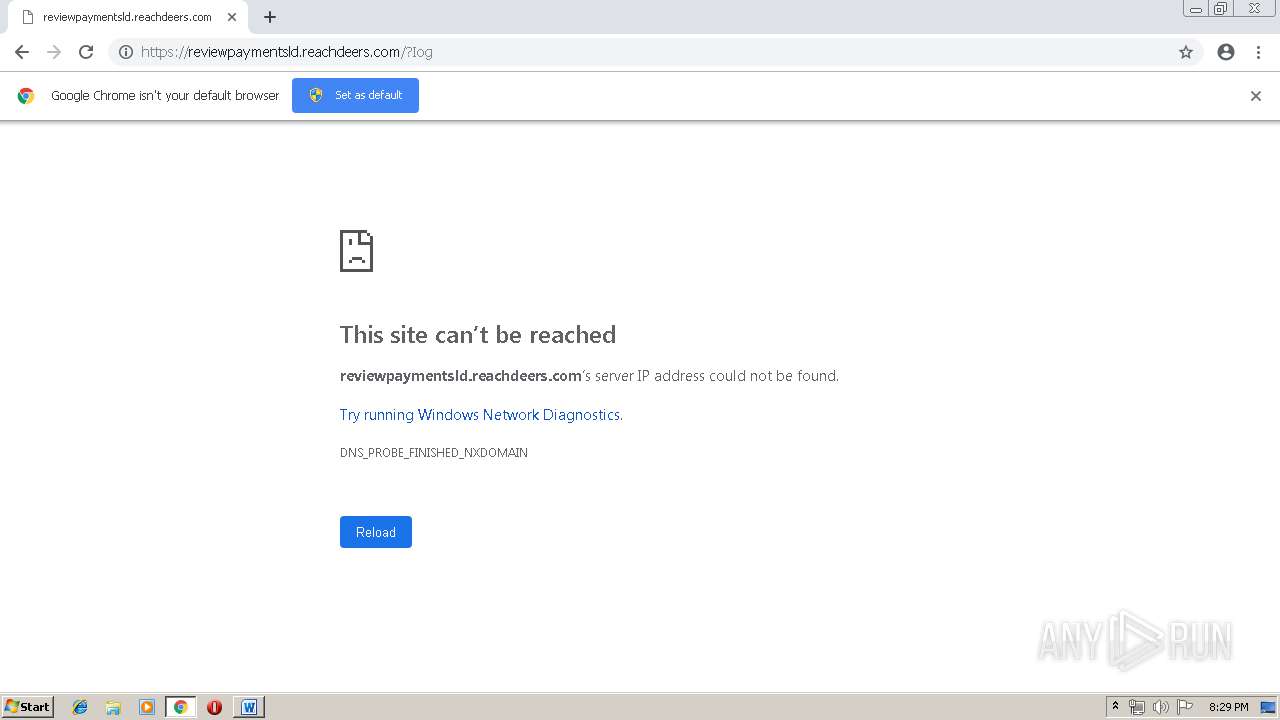
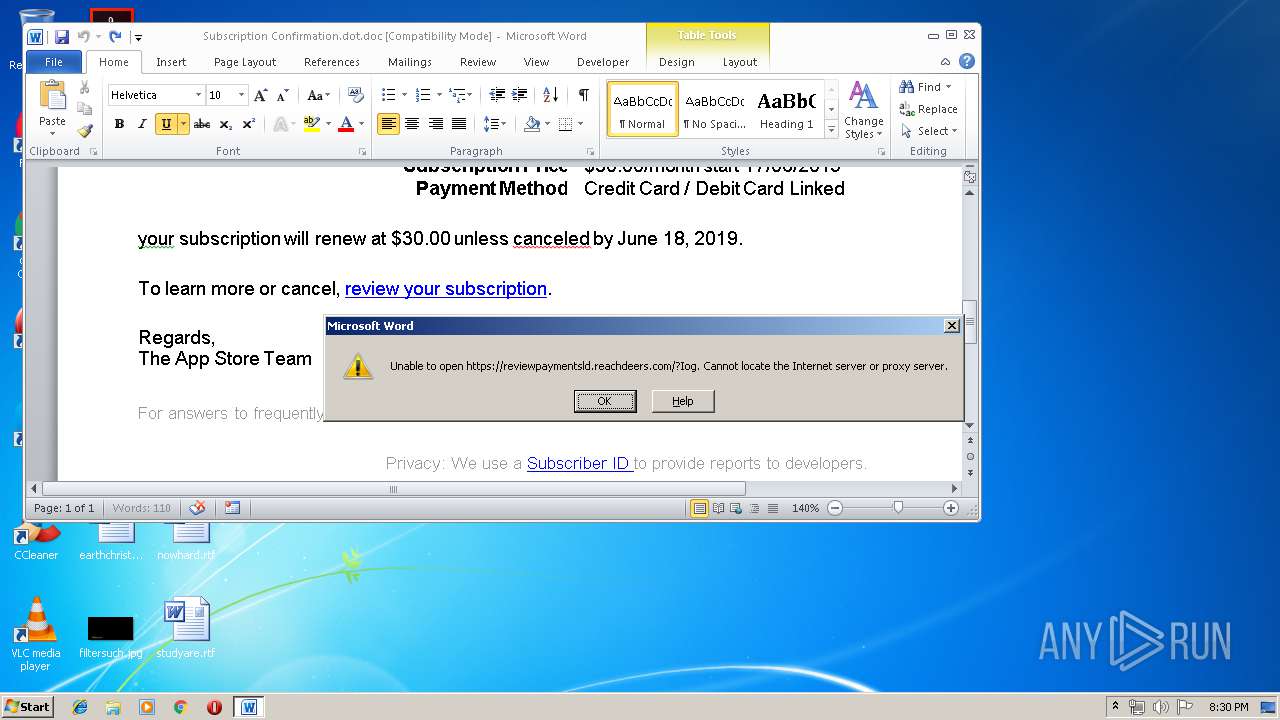
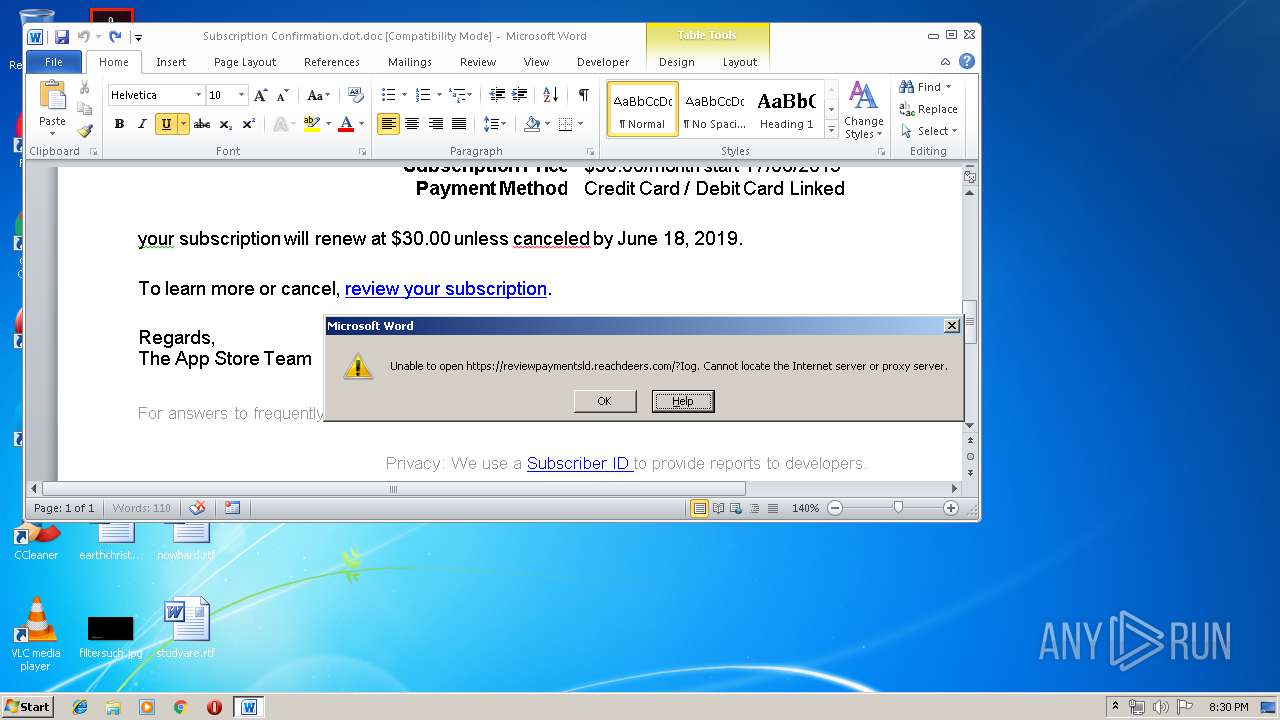
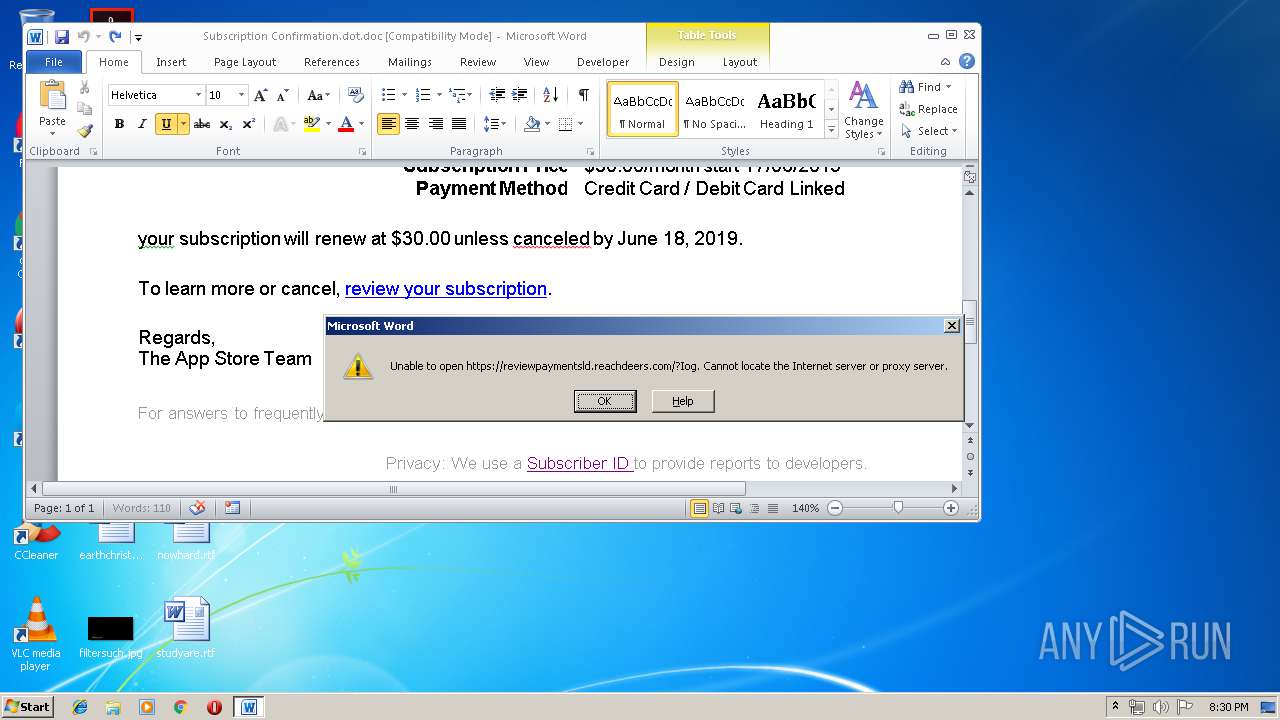
reviewpaymentsld.reachdeers.com |
| unknown |
www.google.com.ua |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
clients1.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
972 | svchost.exe | A Network Trojan was detected | ET POLICY Microsoft user-agent automated process response to automated request |
Process | Message |
|---|---|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|