| File name: | 2025-05-20_c33526339473283bd90ddc9520e68968_amadey_darkgate_elex_floxif_mafia_smoke-loader |
| Full analysis: | https://app.any.run/tasks/0a29f954-5bc0-460c-9564-c0d07f68ec72 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2025, 01:03:46 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 6 sections |
| MD5: | C33526339473283BD90DDC9520E68968 |
| SHA1: | 4F385F0332544D6D61E7FED6B17047A08047BC76 |
| SHA256: | 74A90695CF19730984C1E3EAD6D0BE24D4C87FB32B4B3898185C0F4DE08114FB |
| SSDEEP: | 98304:gxVy/zrm7vqCyKJa9/f3kzEKtCYB3/7I4ery5DX:x8T |
MALICIOUS
Executing a file with an untrusted certificate
- 2025-05-20_c33526339473283bd90ddc9520e68968_amadey_darkgate_elex_floxif_mafia_smoke-loader.exe (PID: 6240)
- 2025-05-20_c33526339473283bd90ddc9520e68968_amadey_darkgate_elex_floxif_mafia_smoke-loader.exe (PID: 2600)
Connects to the CnC server
- FileCoAuth.exe (PID: 1616)
SUSPICIOUS
Executable content was dropped or overwritten
- 2025-05-20_c33526339473283bd90ddc9520e68968_amadey_darkgate_elex_floxif_mafia_smoke-loader.exe (PID: 2600)
Process drops legitimate windows executable
- 2025-05-20_c33526339473283bd90ddc9520e68968_amadey_darkgate_elex_floxif_mafia_smoke-loader.exe (PID: 2600)
- FileCoAuth.exe (PID: 1616)
Reads security settings of Internet Explorer
- FileCoAuth.exe (PID: 1616)
Contacting a server suspected of hosting an CnC
- FileCoAuth.exe (PID: 1616)
INFO
The sample compiled with english language support
- 2025-05-20_c33526339473283bd90ddc9520e68968_amadey_darkgate_elex_floxif_mafia_smoke-loader.exe (PID: 2600)
- FileCoAuth.exe (PID: 1616)
Creates files in the program directory
- 2025-05-20_c33526339473283bd90ddc9520e68968_amadey_darkgate_elex_floxif_mafia_smoke-loader.exe (PID: 2600)
Reads the computer name
- 2025-05-20_c33526339473283bd90ddc9520e68968_amadey_darkgate_elex_floxif_mafia_smoke-loader.exe (PID: 2600)
Checks supported languages
- 2025-05-20_c33526339473283bd90ddc9520e68968_amadey_darkgate_elex_floxif_mafia_smoke-loader.exe (PID: 2600)
Checks proxy server information
- FileCoAuth.exe (PID: 1616)
- slui.exe (PID: 664)
Reads the software policy settings
- slui.exe (PID: 664)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:06:21 22:14:38+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 1742336 |
| InitializedDataSize: | 907264 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xfdaf1 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 11.16.0.0 |
| ProductVersionNumber: | 11.16.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Flexera |
| FileDescription: | Activation Licensing Service |
| FileVersion: | 11.16.0.0 build 234449 |
| InternalName: | FNPLicensingService.exe |
| LegalCopyright: | Copyright (c) 2006-2018, Flexera. All Rights Reserved. |
| OriginalFileName: | FNPLicensingService.exe |
| ProductName: | FlexNet Publisher (32 bit) |
| ProductVersion: | 11.16.0.0 build 234449 |
Total processes
127
Monitored processes
6
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe -Embedding | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneDriveFile Co-Authoring Executable Exit code: 0 Version: 19.043.0304.0013 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
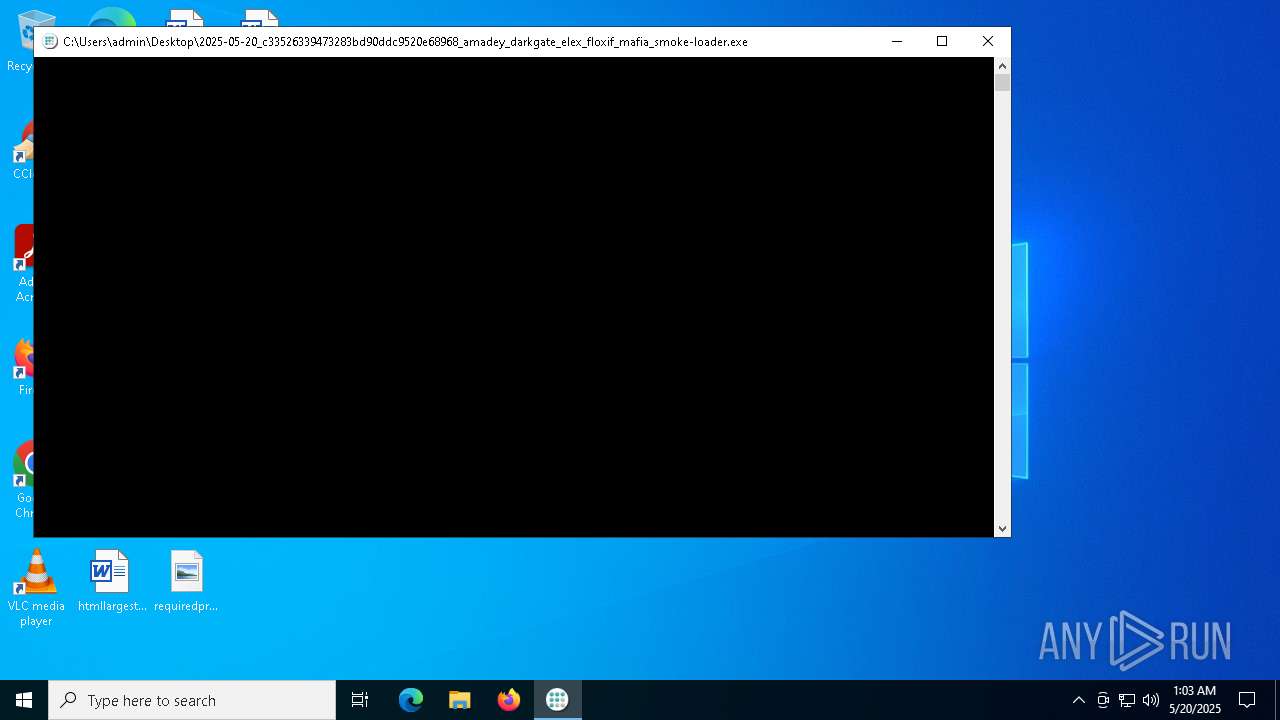
| 2600 | "C:\Users\admin\Desktop\2025-05-20_c33526339473283bd90ddc9520e68968_amadey_darkgate_elex_floxif_mafia_smoke-loader.exe" | C:\Users\admin\Desktop\2025-05-20_c33526339473283bd90ddc9520e68968_amadey_darkgate_elex_floxif_mafia_smoke-loader.exe | explorer.exe | ||||||||||||
User: admin Company: Flexera Integrity Level: HIGH Description: Activation Licensing Service Exit code: 0 Version: 11.16.0.0 build 234449 Modules
| |||||||||||||||
| 3020 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 2025-05-20_c33526339473283bd90ddc9520e68968_amadey_darkgate_elex_floxif_mafia_smoke-loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6240 | "C:\Users\admin\Desktop\2025-05-20_c33526339473283bd90ddc9520e68968_amadey_darkgate_elex_floxif_mafia_smoke-loader.exe" | C:\Users\admin\Desktop\2025-05-20_c33526339473283bd90ddc9520e68968_amadey_darkgate_elex_floxif_mafia_smoke-loader.exe | — | explorer.exe | |||||||||||
User: admin Company: Flexera Integrity Level: MEDIUM Description: Activation Licensing Service Exit code: 3221226540 Version: 11.16.0.0 build 234449 Modules
| |||||||||||||||
Total events
3 877
Read events
3 874
Write events
3
Delete events
0
Modification events
| (PID) Process: | (1616) FileCoAuth.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1616) FileCoAuth.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1616) FileCoAuth.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
9
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1616 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\LoggingPlatform.DLL.tmp | executable | |
MD5:EECA70D305FC18ECB0114F6897CDC3CB | SHA256:8A786AD4F0104F29964284A70EACB0C876A2CCF015B7795E93510C29995C13BA | |||
| 1616 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Common\FileCoAuth-2025-05-20.0104.1616.1.aodl | binary | |
MD5:28DCA2FF4B34B5A52A2E59DF202A6ED3 | SHA256:33BACCB7296F1ED1F995FC77A23049F261CF391AC0388F9E8DD161F8C17B7F94 | |||
| 1616 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\UpdateRingSettings.dll.tmp | executable | |
MD5:720A52C4C0FA7065459852A6CA868ADC | SHA256:C392DB36EEB6801B14853DD27DB1E723783A3537BF8EA31E0C5DB5FA840DD888 | |||
| 1616 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Common\FileCoAuth-2025-05-20.0104.1616.1.odl | binary | |
MD5:A7A5A8101EFDB5A26B276299E23510A9 | SHA256:C1E59CBFB5A495F741CD6BEB168846F669D33871762A8CD2C46F5716529AAE62 | |||
| 1616 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\Telemetry.dll.tmp | executable | |
MD5:31FF258A9F5A03499537EE05DD1BC948 | SHA256:725251881AF81D7064ECC8E4EE944CC8F733B6E0BB87DBB12D1C2E4CD7AACDE9 | |||
| 1616 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\MSVCP140.dll.tmp | executable | |
MD5:655A12EE613C4725EC7409E92148A1F0 | SHA256:15B316C553F394A493EC2F9F51FC277FB2D62A85CF442AF1AE8271E9DCEE5E05 | |||
| 1616 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\VCRUNTIME140.dll.tmp | executable | |
MD5:30B78A11820532EAA608A80A84E67624 | SHA256:C8972C39E70F39DE45B0B719DFEF7817D3FBD818483F47C5D3FD6F93CB5F6335 | |||
| 2600 | 2025-05-20_c33526339473283bd90ddc9520e68968_amadey_darkgate_elex_floxif_mafia_smoke-loader.exe | C:\Program Files\Common Files\System\symsrv.dll | executable | |
MD5:7574CF2C64F35161AB1292E2F532AABF | SHA256:DE055A89DE246E629A8694BDE18AF2B1605E4B9B493C7E4AEF669DD67ACF5085 | |||
| 1616 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuthLib.dll.tmp | executable | |
MD5:EC666C8BA5E15D18F1E493D18486488E | SHA256:ED775EADC480FA535B71DD99C18588D1BA34FF32C90669096F2706A9E5A21469 | |||
| 1616 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe.tmp | executable | |
MD5:96395F265A7026693EAC00B1C1D1AA23 | SHA256:DEDD6F3D98CF9F3CF465924AAA518BF2717A62633C2A56A582ED9DE0C119B8EA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
39
DNS requests
14
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1616 | FileCoAuth.exe | GET | 403 | 96.126.123.244:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
5960 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
5960 | SIHClient.exe | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5960 | SIHClient.exe | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
5960 | SIHClient.exe | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
5960 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5960 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
5960 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
5960 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5960 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1616 | FileCoAuth.exe | 96.126.123.244:80 | www.aieov.com | Linode, LLC | US | malicious |
5960 | SIHClient.exe | 23.32.238.107:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5960 | SIHClient.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5960 | SIHClient.exe | 40.69.42.241:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6964 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
5isohu.com |
| whitelisted |
www.aieov.com |
| malicious |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1616 | FileCoAuth.exe | Malware Command and Control Activity Detected | MALWARE [ANY.RUN] Possible Floxif CnC Communication |