| File name: | monoxideoriginaldangerousx86.exe |
| Full analysis: | https://app.any.run/tasks/8b0f7aa1-cb3d-44ec-8993-89709e5f2975 |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2025, 08:28:30 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | C73B178C9A88ACA764AFC4DA022FB3F0 |
| SHA1: | C5EE12C49D47C8A4D669814FEF42DA9635271FBE |
| SHA256: | 74950125B98FD53A2A2A1184D77875B6CA95ECDE4A12BA91ED281F387F0982E1 |
| SSDEEP: | 6144:qTBG4+Q4ywKhGHoJXkkkw/VEVVVVVVVVVKVVVVVVVVV3:q9YQLGHE9/CVVVVVVVVVKVVVVVVVVV |
MALICIOUS
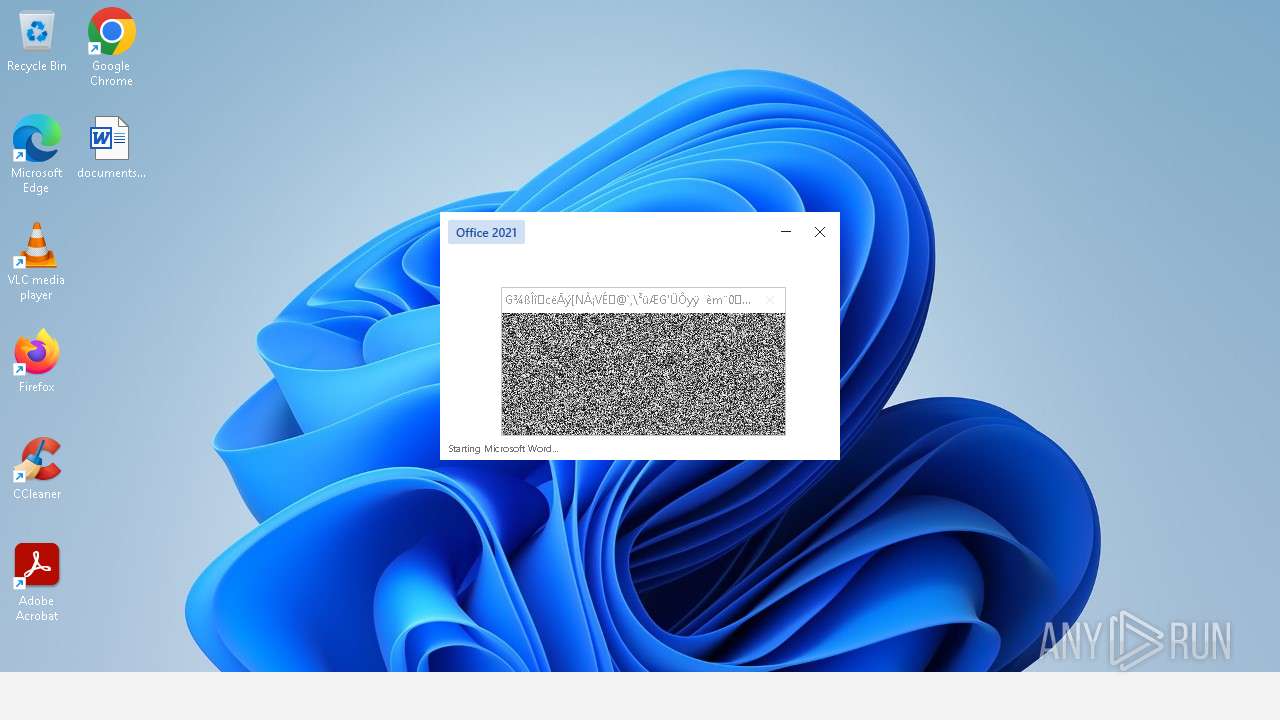
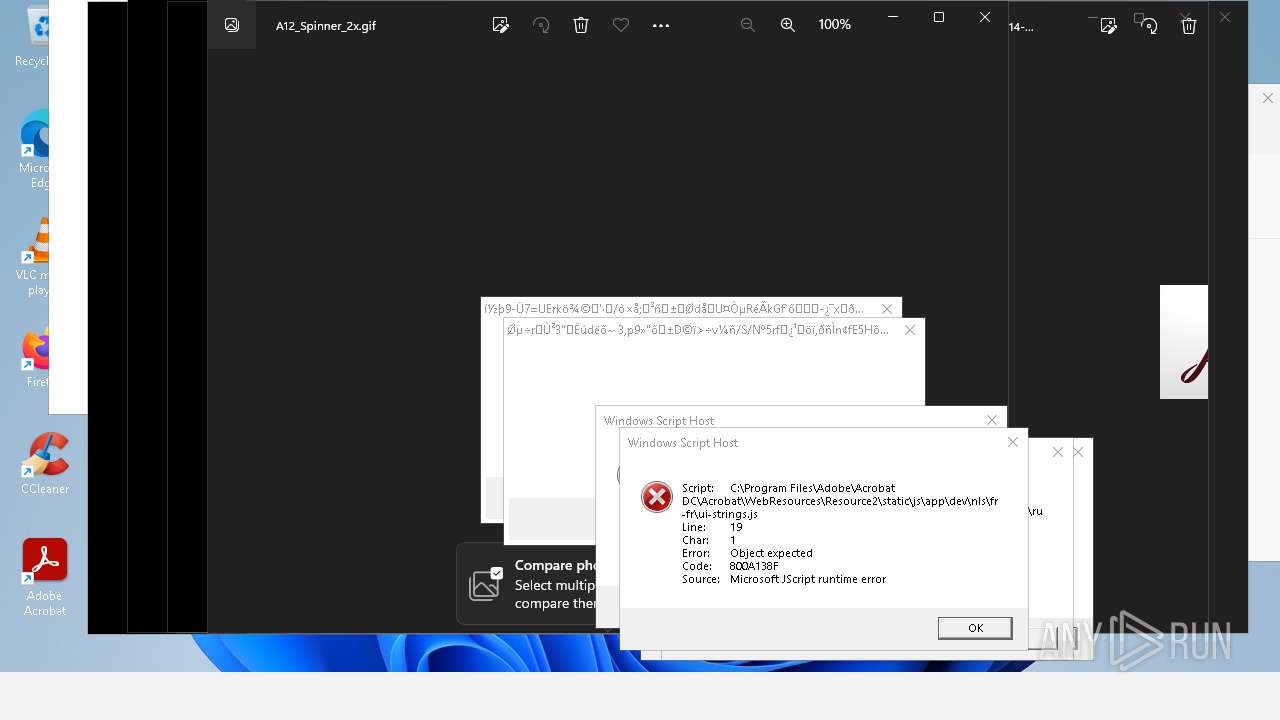
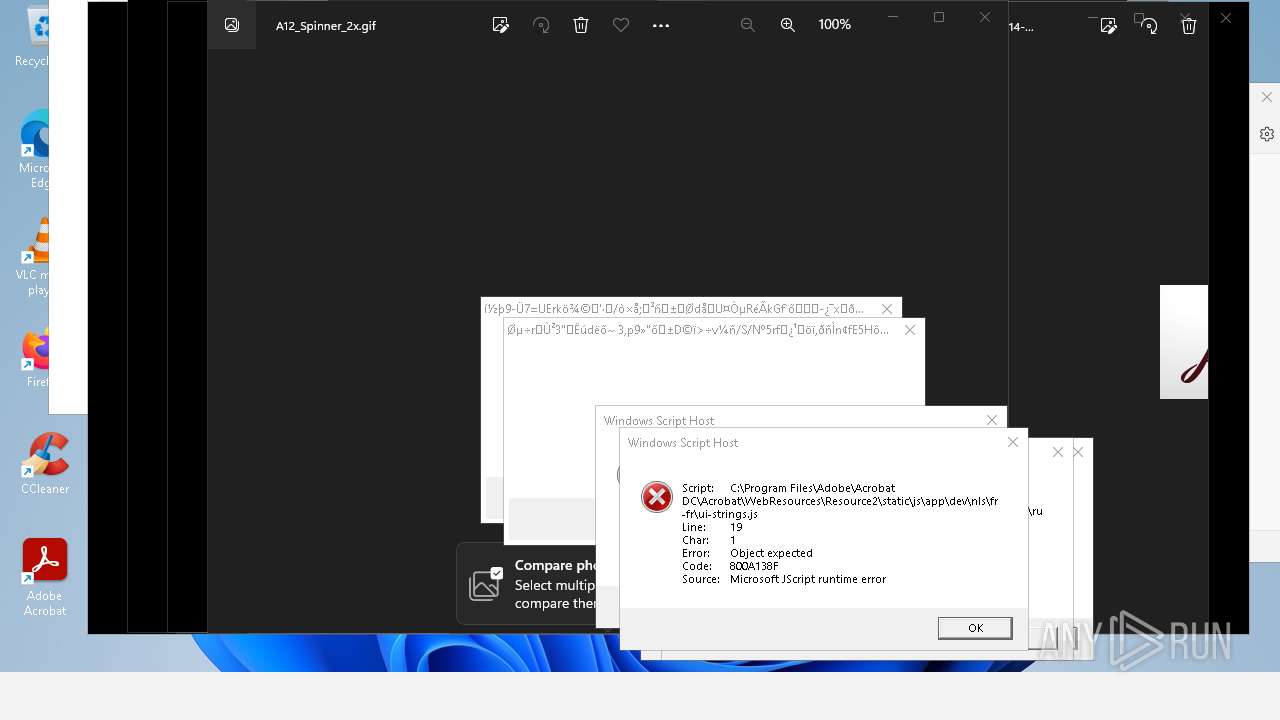
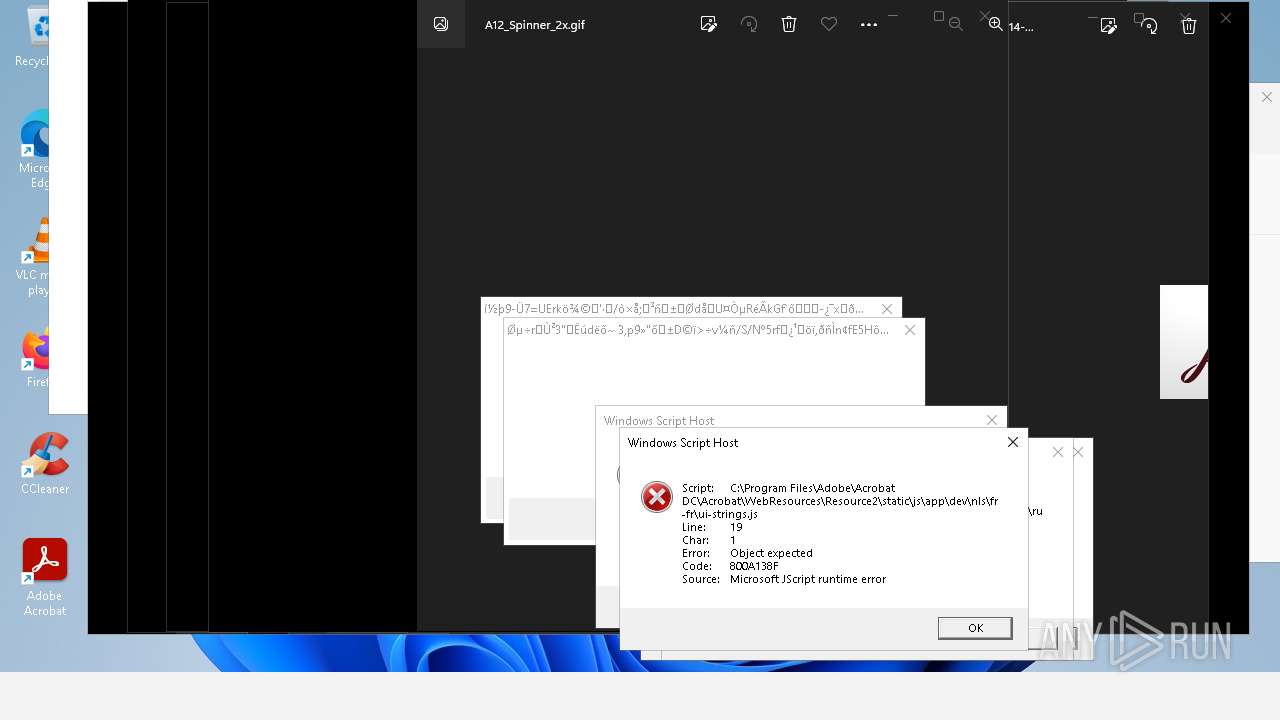
Monoxide mutex has been found
- 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe (PID: 2588)
Unusual execution from MS Office
- WINWORD.EXE (PID: 720)
SUSPICIOUS
Executable content was dropped or overwritten
- monoxideoriginaldangerousx86.exe (PID: 2276)
Creates file in the systems drive root
- 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe (PID: 2588)
Reads the Internet Settings
- 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe (PID: 2588)
- Notepad.exe (PID: 6108)
Reads security settings of Internet Explorer
- 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe (PID: 2588)
- Notepad.exe (PID: 6108)
Starts itself from another location
- monoxideoriginaldangerousx86.exe (PID: 2276)
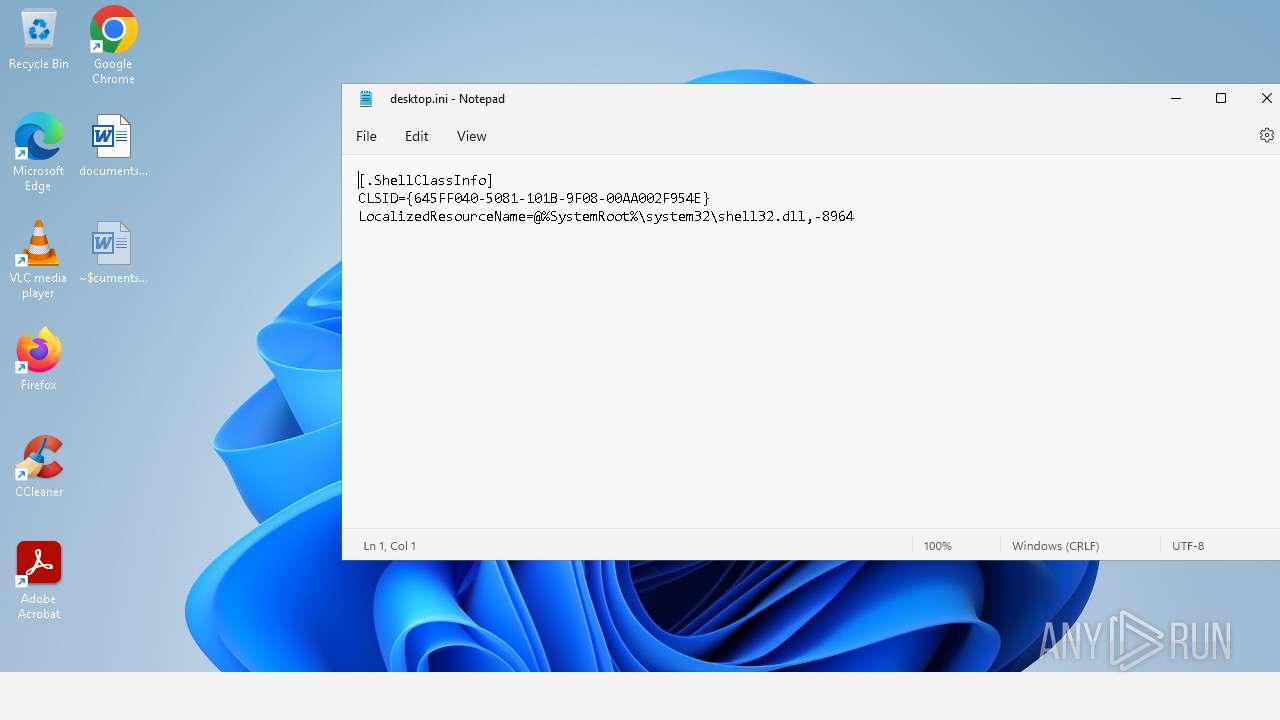
Write to the desktop.ini file (may be used to cloak folders)
- Notepad.exe (PID: 6108)
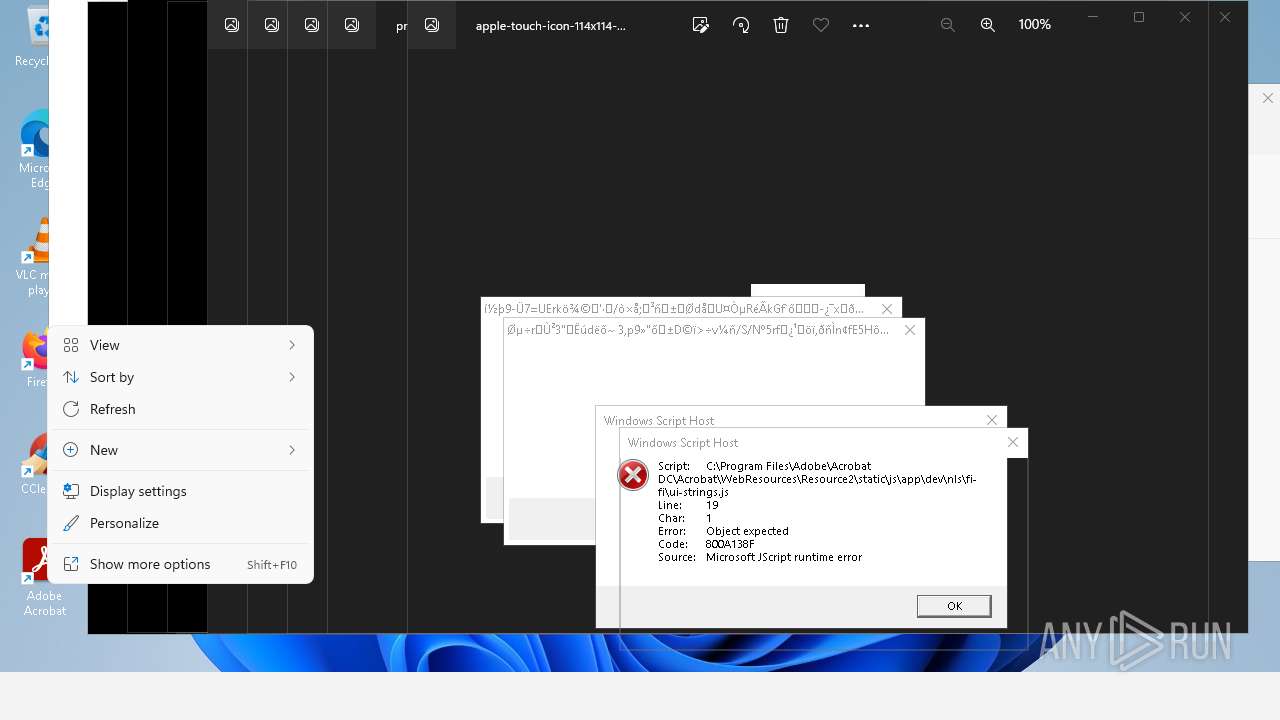
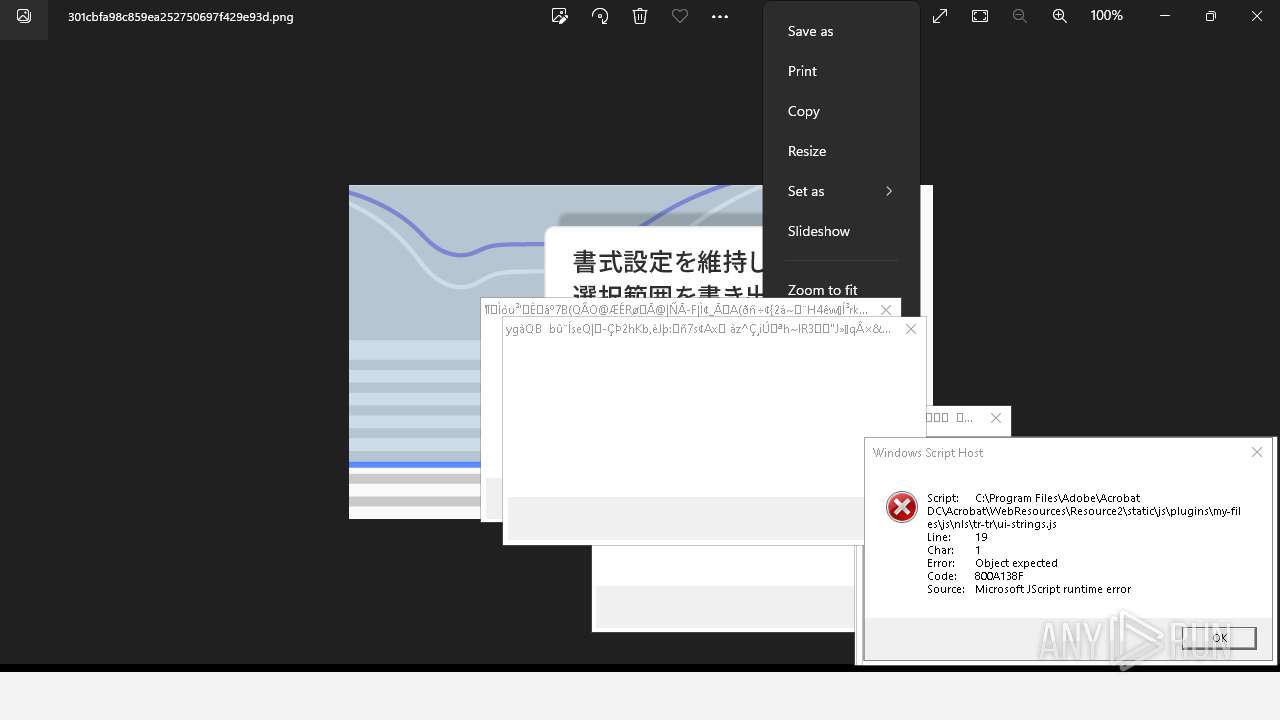
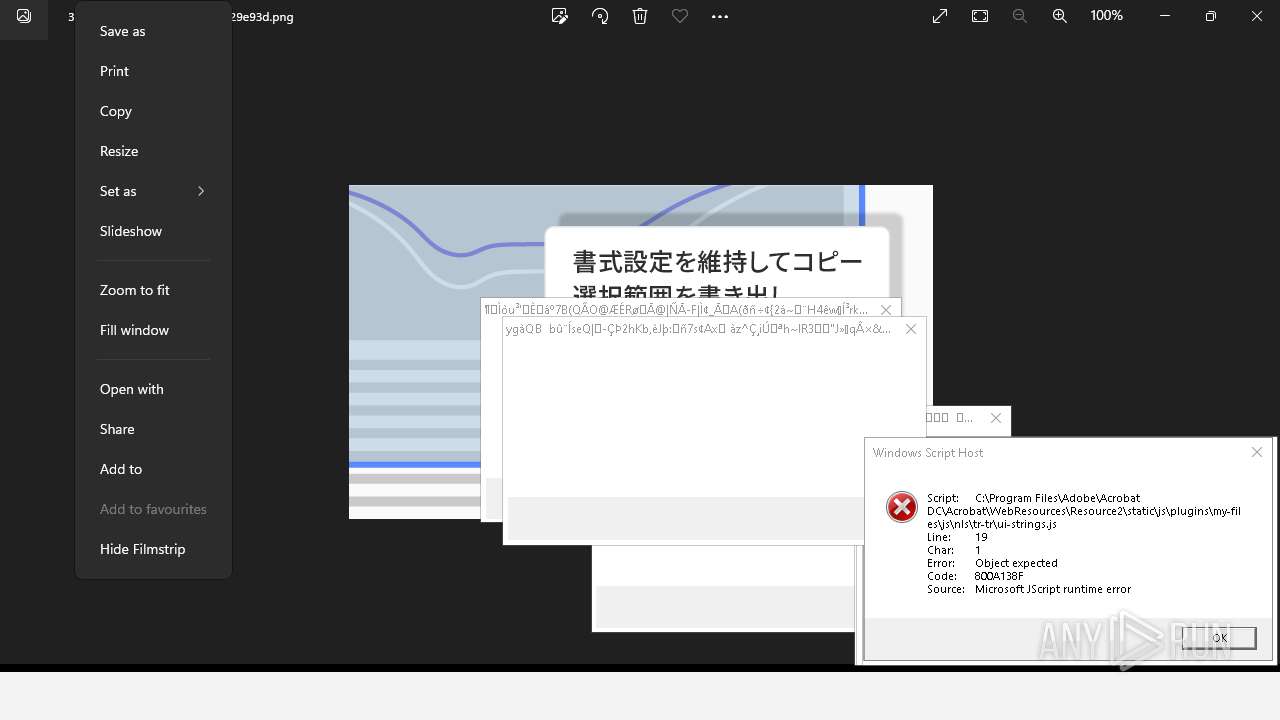
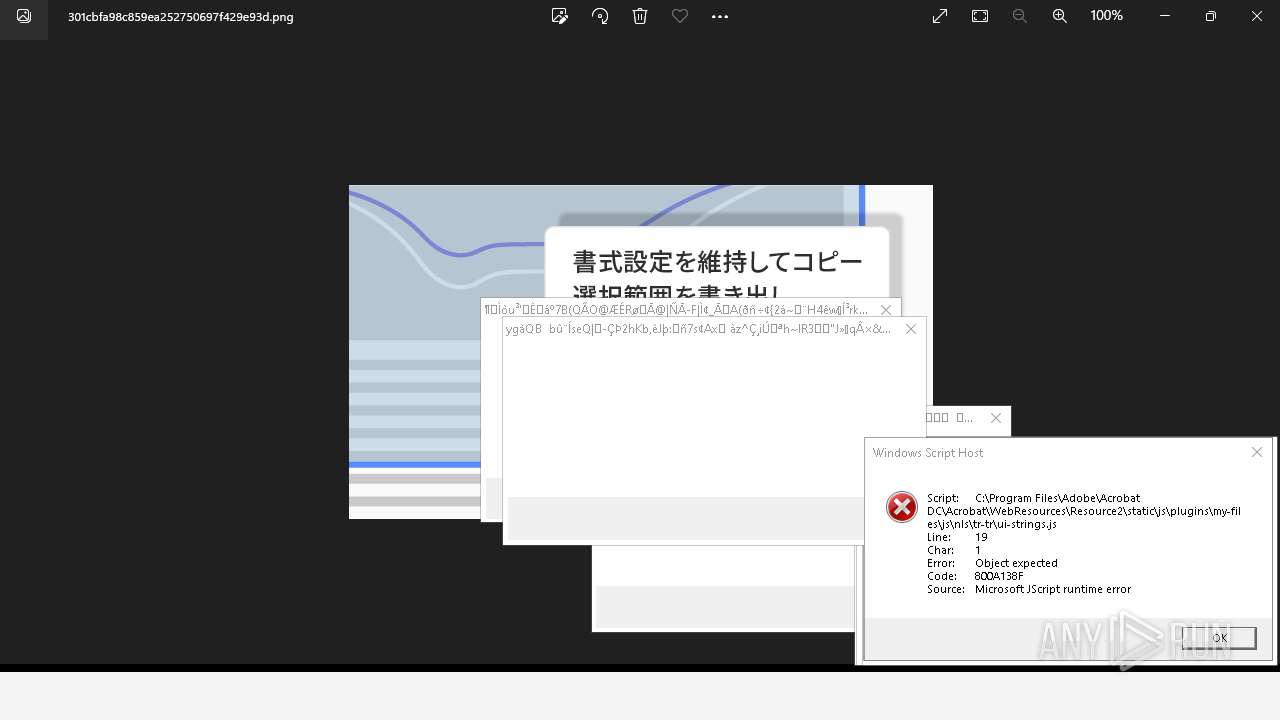
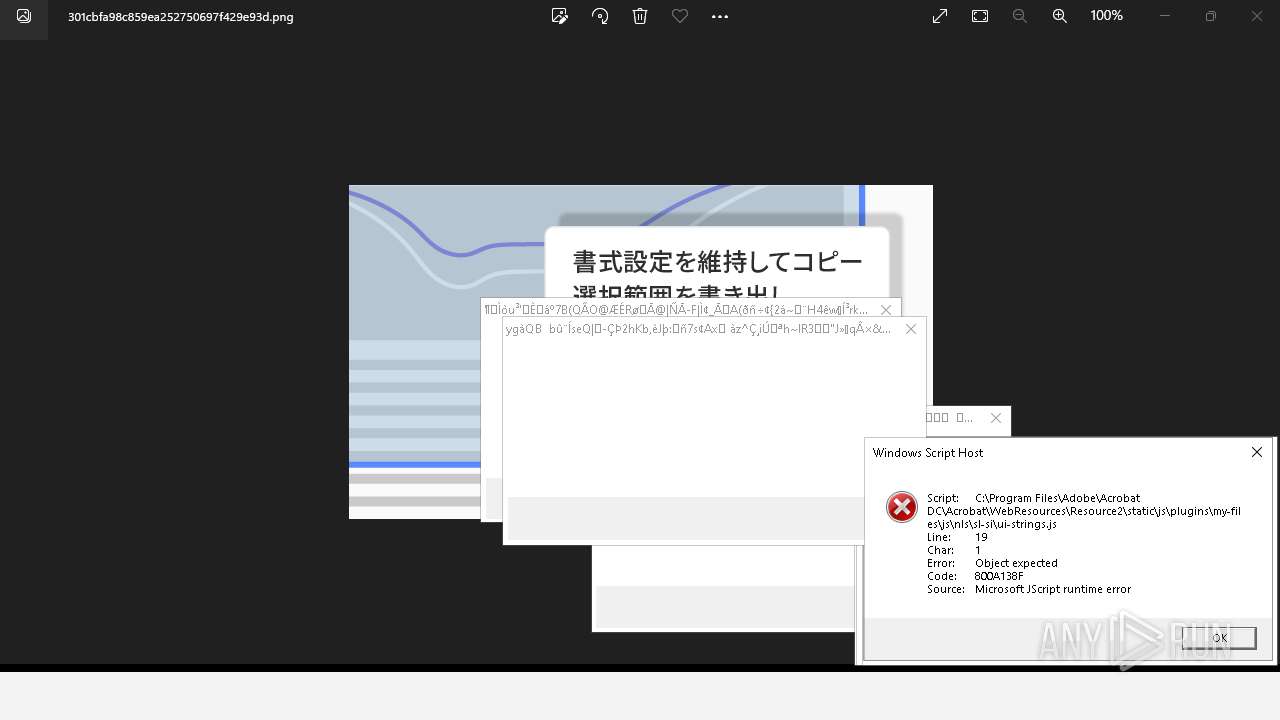
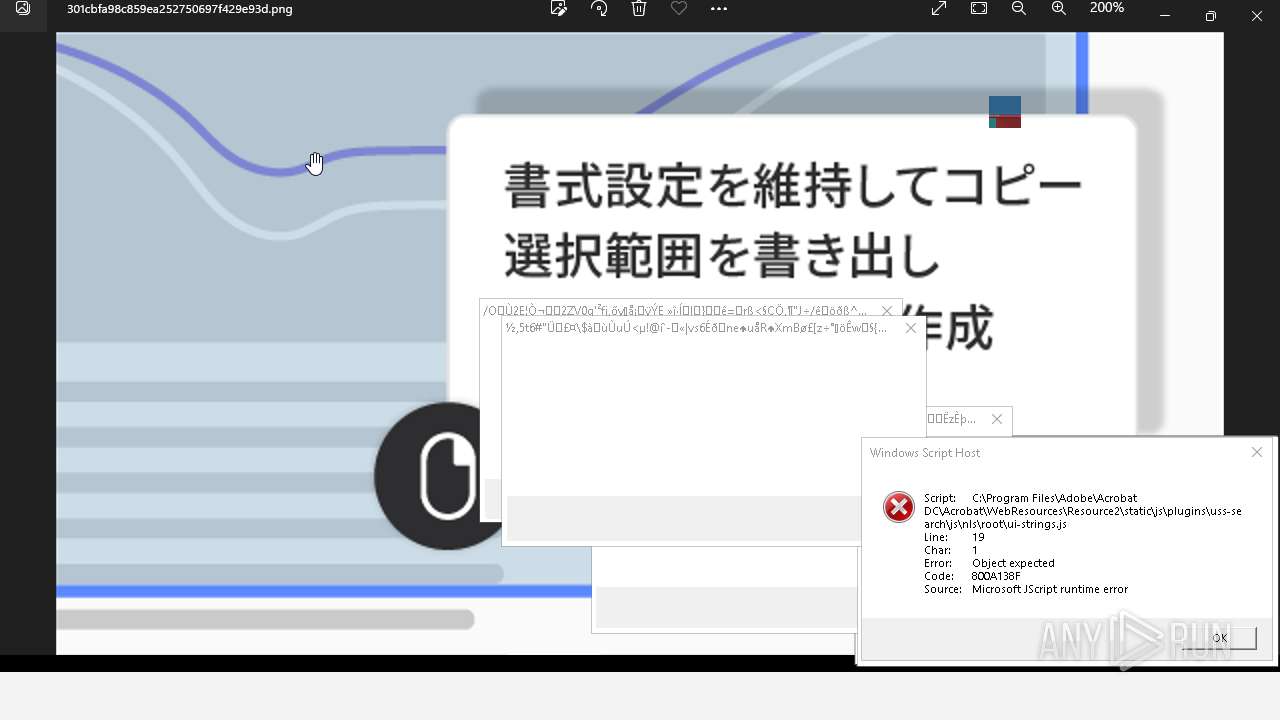
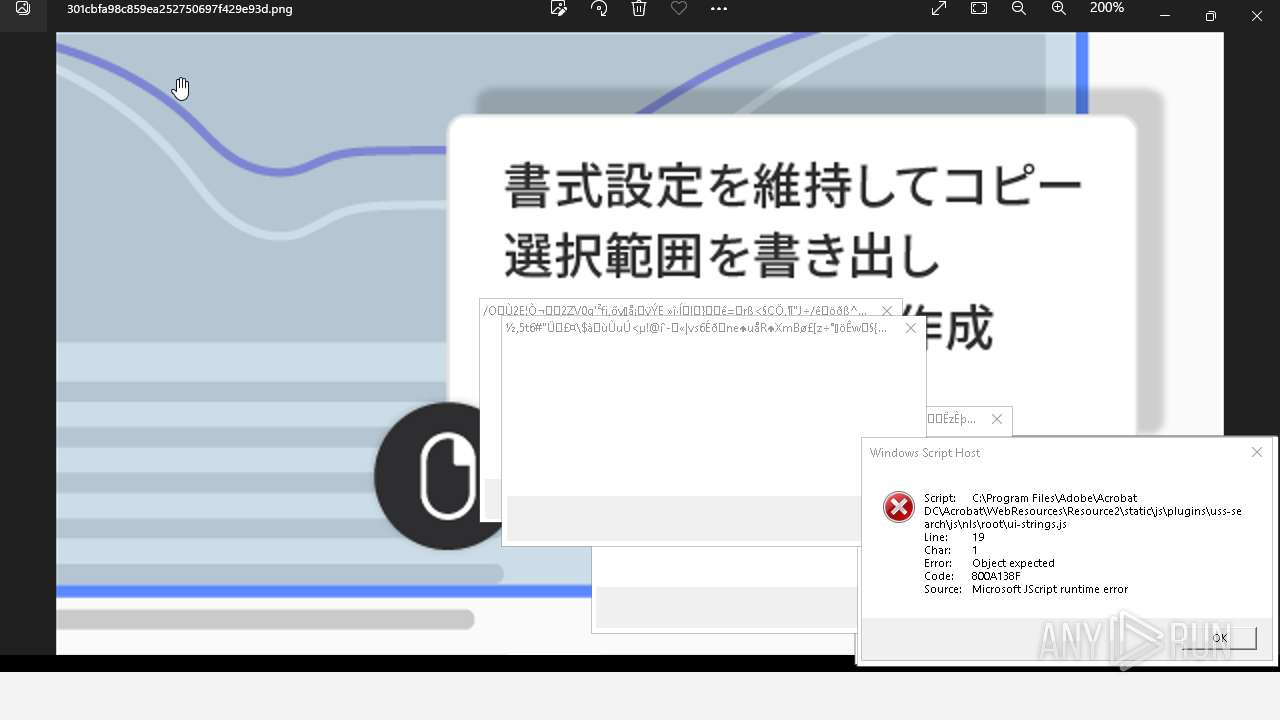
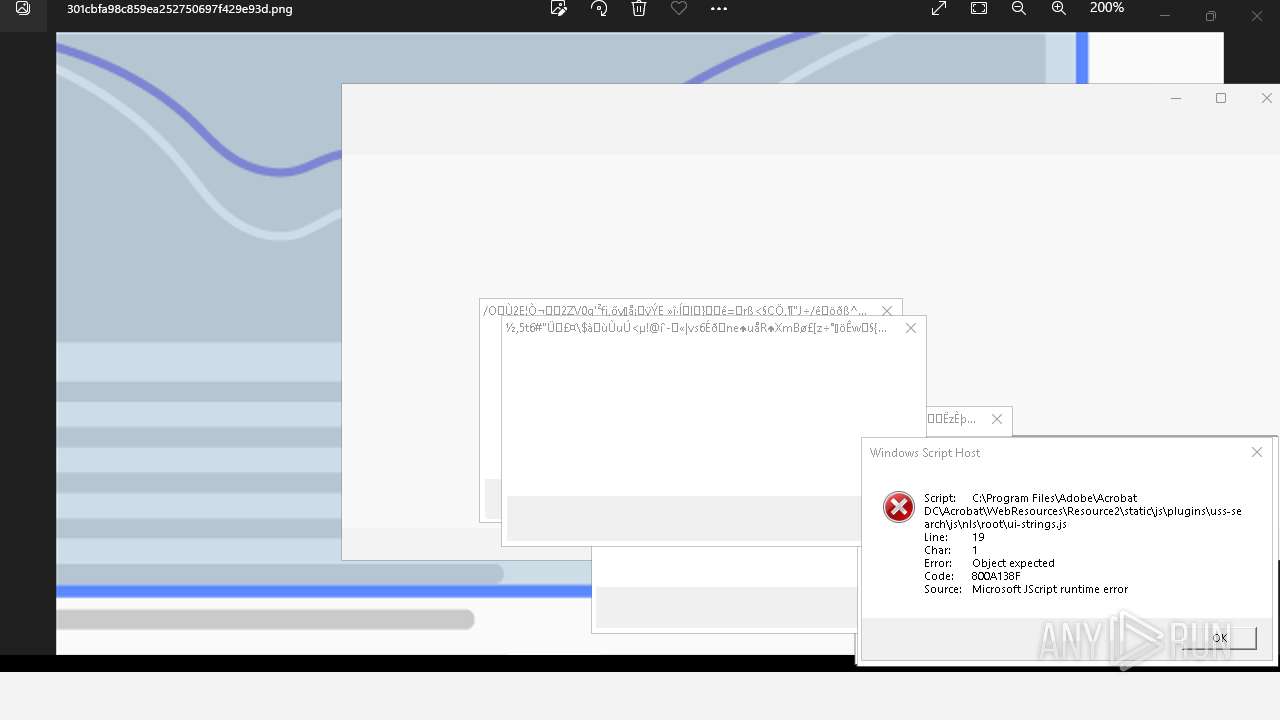
Executes application which crashes
- AcroCEF.exe (PID: 6500)
The process executes JS scripts
- 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe (PID: 2588)
There is functionality for taking screenshot (YARA)
- 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe (PID: 2588)
INFO
Checks supported languages
- monoxideoriginaldangerousx86.exe (PID: 2276)
- 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe (PID: 2588)
- Notepad.exe (PID: 6108)
Create files in a temporary directory
- monoxideoriginaldangerousx86.exe (PID: 2276)
Reads the computer name
- 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe (PID: 2588)
- Notepad.exe (PID: 6108)
Application launched itself
- msedge.exe (PID: 8972)
- msedge.exe (PID: 8376)
- msedge.exe (PID: 11012)
- msedge.exe (PID: 1088)
UPX packer has been detected
- 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe (PID: 2588)
Manual execution by a user
- msedge.exe (PID: 9956)
- msedge.exe (PID: 8732)
- msedge.exe (PID: 9400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (76) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.6) |
| .exe | | | Generic Win/DOS Executable (5.6) |
| .exe | | | DOS Executable Generic (5.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:02 04:28:57+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 73728 |
| InitializedDataSize: | 147456 |
| UninitializedDataSize: | 258048 |
| EntryPoint: | 0x519e0 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
258
Monitored processes
141
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 156 | C:\Windows\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Pick an app Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 388 | C:\Windows\system32\ApplicationFrameHost.exe -Embedding | C:\Windows\System32\ApplicationFrameHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Application Frame Host Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 624 | "C:\Program Files\WindowsApps\Microsoft.WindowsNotepad_11.2205.11.0_x64__8wekyb3d8bbwe\Notepad\Notepad.exe" "C:\Program Files\Common Files\Adobe\Acrobat\DC\Linguistics\LanguageNames2\DisplayLanguageNames.nn_NO.txt" | C:\Program Files\WindowsApps\Microsoft.WindowsNotepad_11.2205.11.0_x64__8wekyb3d8bbwe\Notepad\Notepad.exe | — | 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 720 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\documentstay.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Word Exit code: 0 Version: 16.0.16626.20134 Modules
| |||||||||||||||
| 784 | "C:\Windows\System32\WScript.exe" "C:\Program Files\Adobe\Acrobat DC\Acrobat\WebResources\Resource2\static\js\plugins\unified-share\js\nls\ca-es\ui-strings.js" | C:\Windows\SysWOW64\wscript.exe | — | 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 820 | C:\Windows\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Pick an app Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1088 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument C:\Program Files\Adobe\Acrobat DC\Acrobat\WebResources\Resource2\static\js\plugins\on-boarding\images\sca_thanksforsubscribing.svg | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 1 Version: 122.0.2365.92 Modules
| |||||||||||||||
| 1160 | "C:\Users\admin\Desktop\monoxideoriginaldangerousx86.exe" | C:\Users\admin\Desktop\monoxideoriginaldangerousx86.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1220 | "C:\Windows\system32\DllHost.exe" /Processid:{9F156763-7844-4DC4-B2B1-901F640F5155} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1336 | "C:\Program Files\WindowsApps\Microsoft.WindowsNotepad_11.2205.11.0_x64__8wekyb3d8bbwe\Notepad\Notepad.exe" "C:\Program Files\Adobe\Acrobat DC\Resource\TypeSupport\Unicode\Mappings\Mac\CENTEURO.TXT" | C:\Program Files\WindowsApps\Microsoft.WindowsNotepad_11.2205.11.0_x64__8wekyb3d8bbwe\Notepad\Notepad.exe | — | 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
416 515
Read events
413 730
Write events
2 597
Delete events
188
Modification events
| (PID) Process: | (2588) 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rtf\OpenWithProgids |
| Operation: | write | Name: | Word.RTF.8 |
Value: | |||
| (PID) Process: | (2588) 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D28010000BD0E0C47735D584D9CEDE91E22E23282290100006078A409B011A54DAFA526D86198A7801302000060B81DB4E464D2119906E49FADC173CAD40100000114020000000000C000000000000046BF020000 | |||
| (PID) Process: | (2588) 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2588) 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2588) 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2588) 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2588) 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\ApplicationAssociationToasts |
| Operation: | write | Name: | Word.RTF.8_.rtf |
Value: 0 | |||
| (PID) Process: | (2588) 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {B41DB860-8EE4-11D2-9906-E49FADC173CA} {000214E4-0000-0000-C000-000000000046} 0xFFFF |
Value: 0100000000000000D016A05E2ACADB01 | |||
| (PID) Process: | (2588) 樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D67010000BD0E0C47735D584D9CEDE91E22E23282290100006078A409B011A54DAFA526D86198A7801302000060B81DB4E464D2119906E49FADC173CAD40100000114020000000000C000000000000046BF020000 | |||
| (PID) Process: | (720) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 016411000000001000A64EF24006000000000000000D00000000000000 | |||
Executable files
3
Suspicious files
49
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 720 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json.tmp | binary | |
MD5:9BA9537A3636CD94D17CD5A630591115 | SHA256:124DB28DAF9EC407EB6A5F6AC2AE68057123A00D1138B05FEF362F12AE40FE6C | |||
| 720 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:2DC7BFBBB7ABAFE7A97E93327EB103C4 | SHA256:343C2E7521345D41C70A7E42881C4CE85FF88E1007FF83C2C7B77B609B651FAB | |||
| 2276 | monoxideoriginaldangerousx86.exe | C:\Users\admin\AppData\Local\Temp\樫鶾炮仏評箜喬麄掗絫煇鶱鵥陓尜舮.exe | executable | |
MD5:C73B178C9A88ACA764AFC4DA022FB3F0 | SHA256:74950125B98FD53A2A2A1184D77875B6CA95ECDE4A12BA91ED281F387F0982E1 | |||
| 720 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\documentstay.rtf.LNK | binary | |
MD5:5DCFF2AE951989373869EFBF0E7037FC | SHA256:EDA9B96FBAA3528F4C1181AE82264FE200C1B6701927C14A2EE2174BA5962415 | |||
| 6920 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_AcroCEF.exe_49203e4672f6b822dc7c232e70f0d98e6114b5c6_3ea955e1_caed0d50-3ffc-4e78-94b5-f31e06125b8f\Report.wer | — | |
MD5:— | SHA256:— | |||
| 720 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\Word\ASkwMDAwMDAwMC0wMDAwLTAwMDAtMDAwMC0wMDAwMDAwMDAwMDBfTnVsbAA.S | binary | |
MD5:9763E46BF902148F9BA7681520E57399 | SHA256:4BC3C765A8359336E2440B353B92511440CE2A8CE00E7C203781DEFF8A8AE8E2 | |||
| 720 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\DE75ADE.tmp | binary | |
MD5:D0EC02C77933E3F2435E5814F1D46797 | SHA256:07FE8E728A5B006B5B558DE9E1C17EFBDC54AD01884907E162C51CB7578BB154 | |||
| 720 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:D1CD20814DC3225A550222648F80358D | SHA256:982A5443C85FA6D8F08660F55F2DCDAB487F1E0538E161BC8466E32E1FA6444B | |||
| 720 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json | binary | |
MD5:9BA9537A3636CD94D17CD5A630591115 | SHA256:124DB28DAF9EC407EB6A5F6AC2AE68057123A00D1138B05FEF362F12AE40FE6C | |||
| 720 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\E0013C01-818F-410B-A090-53D07F69411A | xml | |
MD5:CBBF11D551BB99D9A5D38C0EEDCAA3B1 | SHA256:149023AAD5DB67AC7C9C826C2AB192B48E5E67F63B220F15E8FBCF23CF5C7AFF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
34
DNS requests
24
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.42:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
3560 | MoUsoCoreWorker.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0585211cc3e81e62 | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 23.50.131.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?74f19306e9a7f92f | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 23.50.131.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?e8295883656f7dad | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 23.50.131.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?3e4d47703098faed | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 23.50.131.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?06f66c290ee0a154 | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 23.50.131.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?8385a777ac1fd533 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 2.16.164.42:80 | — | Akamai International B.V. | NL | unknown |
3560 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3560 | MoUsoCoreWorker.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
3640 | svchost.exe | 40.126.31.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2744 | smartscreen.exe | 98.64.238.3:443 | checkappexec.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
720 | WINWORD.EXE | 52.109.89.18:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
720 | WINWORD.EXE | 23.48.23.45:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
720 | WINWORD.EXE | 52.123.131.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
login.live.com |
| whitelisted |
checkappexec.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
odc.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Microsoft Connection Test |
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |
Process | Message |
|---|---|
FullTrustNotifier.exe | FullTrustNotifier |
FullTrustNotifier.exe | |
FullTrustNotifier.exe | FN NewNotifcationHasArrived from UWP |
FullTrustNotifier.exe | |
FullTrustNotifier.exe | FN ConnectToAppService create the async task |
FullTrustNotifier.exe | |
FullTrustNotifier.exe |
ConnectToAppServiceAsync AppNotInstalled |
FullTrustNotifier.exe | |
FullTrustNotifier.exe | FN ConnectToAppServiceAsync |
FullTrustNotifier.exe | |