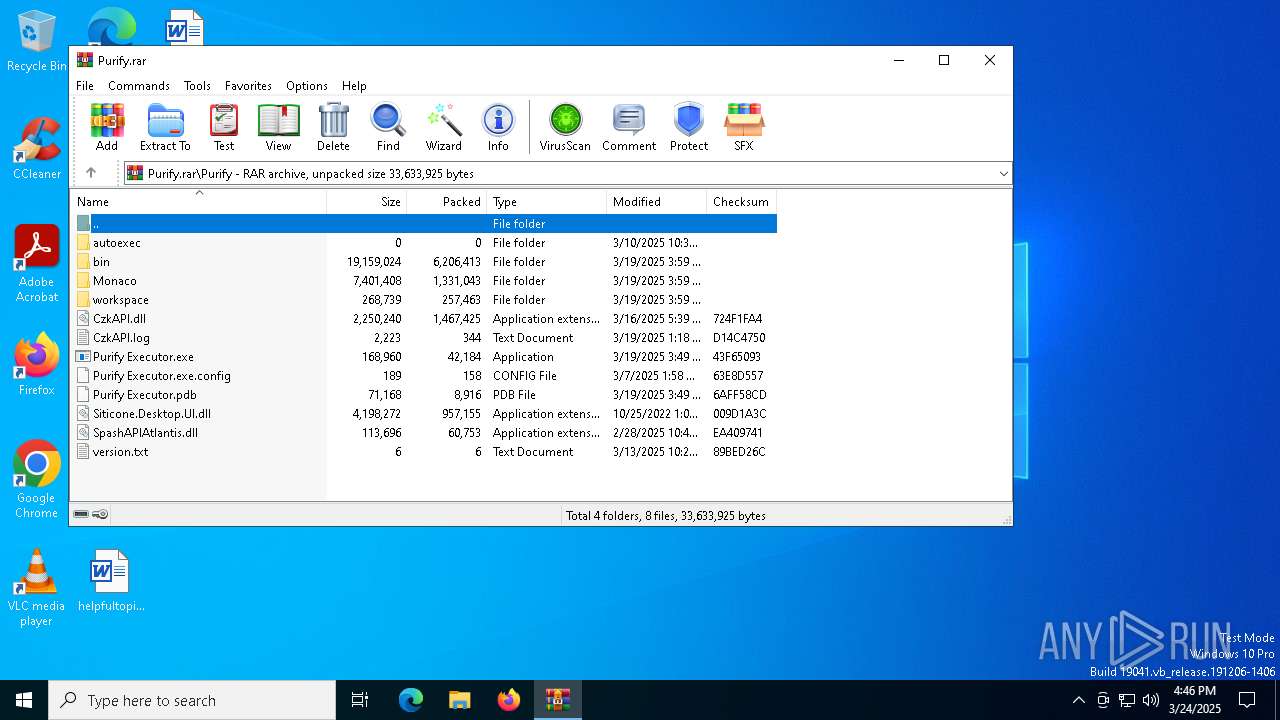
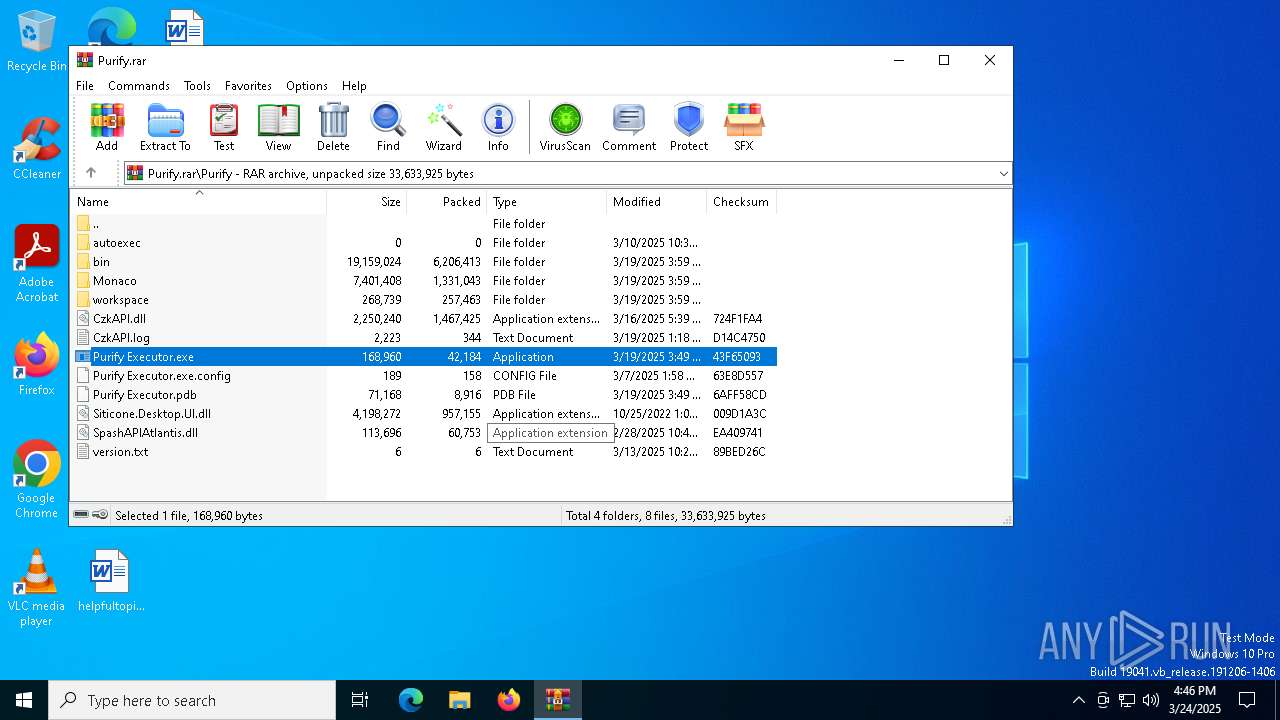
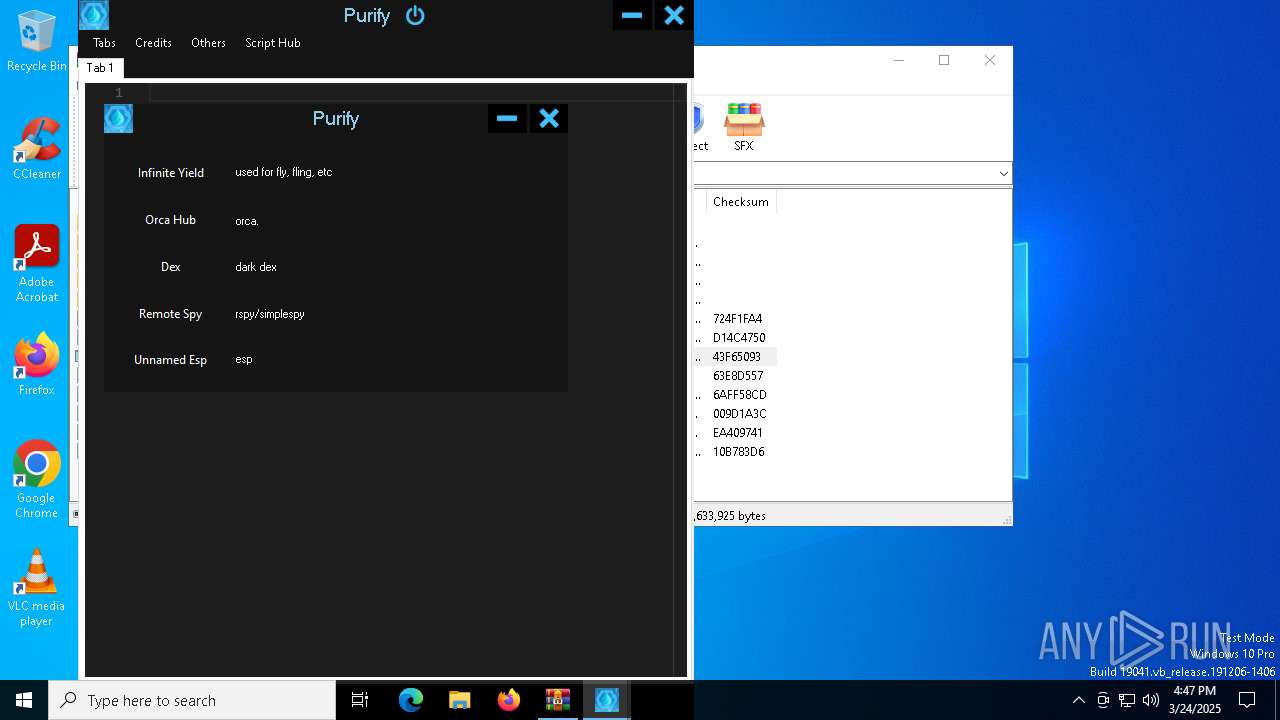
| File name: | Purify.rar |
| Full analysis: | https://app.any.run/tasks/360c1cd5-1afa-4d9d-ad47-4c8ecc52be07 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 16:46:28 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 2F8755449123F29101A2E3A021668670 |
| SHA1: | 25448AFA0B1287BB5507E03380DA553A8E6BCE8C |
| SHA256: | 748FFDE74ECBF83293002F5904258259FEBBEE5A81C546FED7CB439D3F905C87 |
| SSDEEP: | 98304:iAaY2pAueQ4oTd2ip407nQsjWrQ+oAp4wRZQmHEjq/RJBdslrg9FSEx+8BZlToiB:zW48nE5+yZdx2cufshqgvz |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 3884)
GENERIC has been found (auto)
- WinRAR.exe (PID: 3884)
SUSPICIOUS
Reads Microsoft Outlook installation path
- Purify Executor.exe (PID: 4932)
Reads Internet Explorer settings
- Purify Executor.exe (PID: 4932)
Reads security settings of Internet Explorer
- Purify Executor.exe (PID: 4932)
- Purify Executor.exe (PID: 5508)
Executable content was dropped or overwritten
- Purify Executor.exe (PID: 4932)
Executes application which crashes
- Purify Executor.exe (PID: 4932)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 3884)
Disables trace logs
- Purify Executor.exe (PID: 4932)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3884)
Reads Environment values
- Purify Executor.exe (PID: 4932)
Checks proxy server information
- Purify Executor.exe (PID: 4932)
Create files in a temporary directory
- Purify Executor.exe (PID: 4932)
Creates files or folders in the user directory
- WerFault.exe (PID: 3896)
Reads security settings of Internet Explorer
- WerFault.exe (PID: 3896)
Reads the software policy settings
- Purify Executor.exe (PID: 4932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 3521367 |
| UncompressedSize: | 10089440 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | Purify/bin/AtlantisV3.dll |
Total processes
135
Monitored processes
4
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3884 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Purify.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3896 | C:\WINDOWS\system32\WerFault.exe -u -p 4932 -s 3128 | C:\Windows\System32\WerFault.exe | — | Purify Executor.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4932 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3884.12393\Purify\Purify Executor.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3884.12393\Purify\Purify Executor.exe | WinRAR.exe | ||||||||||||
User: admin Company: https://dsc.gg/kernelos Integrity Level: MEDIUM Description: Purifytest Exit code: 3221225477 Version: 1.0.0.0 Modules
| |||||||||||||||
| 5508 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3884.15117\Purify\Purify Executor.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3884.15117\Purify\Purify Executor.exe | — | WinRAR.exe | |||||||||||
User: admin Company: https://dsc.gg/kernelos Integrity Level: MEDIUM Description: Purifytest Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
6 767
Read events
6 710
Write events
44
Delete events
13
Modification events
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Purify.rar | |||
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
34
Suspicious files
166
Text files
92
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Purify\Purify\bin\AtlantisV3.dll | executable | |
MD5:AE4BF9D9A9735A89CA4AECD34EE4CADE | SHA256:F5578DAAA27CE51CC7E30E2399CD15EFA765443F068A17D07801098D554F262B | |||
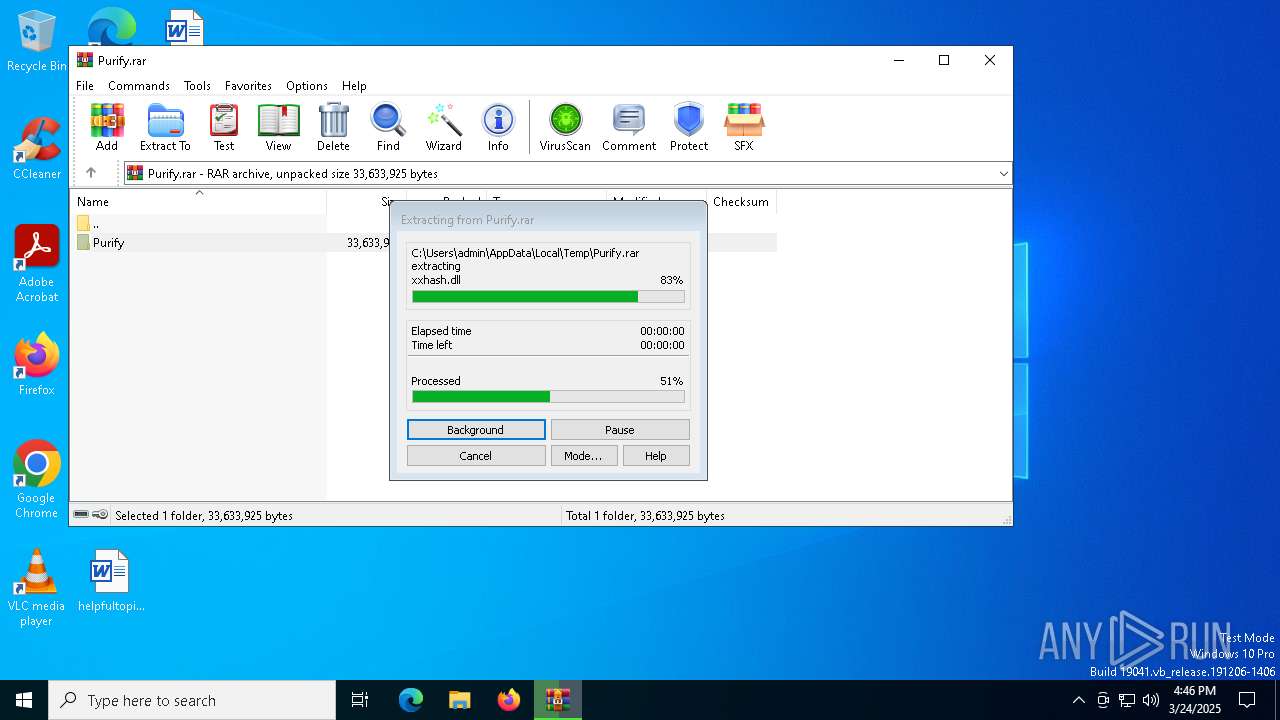
| 3884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Purify\Purify\bin\xxhash.dll | executable | |
MD5:0E9FECEA29B2B3D5EF064E112436E9D1 | SHA256:73C84884A2CCDE1D10BEC0820A6661920E70E4B53FA99AD510ACF5ED1B36AF97 | |||
| 3884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Purify\Purify\Monaco\vs\base\worker\workerMain.js | binary | |
MD5:27EAD90C7702154755785E0E53398755 | SHA256:BDF9433692A08851E13DD58504EEF19F51BD2EC7241923A68EDF5772E0E53AF5 | |||
| 3884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Purify\Purify\bin\libssl-3-x64.dll | executable | |
MD5:D66ACB55A9F095A24865C9D883F96FD1 | SHA256:7AE563B23164EC5994DBC24BCE536B33DF80C40DE5CA97D64FE84A5DAC34788E | |||
| 3884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Purify\Purify\bin\libcrypto-3-x64.dll | executable | |
MD5:54CA3E6AFCB3C57C7914C0856D779F2A | SHA256:7AED0BC00D2F0CA0DE95EAA6461327BD2E4543723A6CA443A7E899738B353B5A | |||
| 3884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Purify\Purify\bin\Nezur.dll | executable | |
MD5:0007185DE8F69F04F672362C9300D587 | SHA256:B3D0B7C9CCDC02A644CA9FF32376C065C80133283FEF3C424C1C2C2ED8E3A885 | |||
| 3884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Purify\Purify\bin\Injector.exe | executable | |
MD5:EF258D36F890691C053432241B1E52F9 | SHA256:06168B056A407D95D8F433A4EB847EB5C62F0AB14BCA2BF26C59A4C02EFEC550 | |||
| 3884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Purify\Purify\bin\zstd.dll | executable | |
MD5:567198A0119E3E2EC94208F1CDA7AA28 | SHA256:6C63D08182DEDE465C95E48A235894E598A61CC24E0BA4556637CC9C1A1E0951 | |||
| 3884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Purify\Purify\CzkAPI.log | text | |
MD5:EB706DE7B457853B859F06C2D6ED1C9D | SHA256:AF8DEBF4DB1DB7423E4640461FAA98CD58623E5B1F2516A505A8708B795CDDC3 | |||
| 3884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Purify\Purify\Monaco\index.html | html | |
MD5:B867A373E2082F0D800D1561EEA8DB21 | SHA256:10B8551148FEF60A1FA1C65F9EF38E4E8275ECF592B0EC6C873A41BBF37544CE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
22
DNS requests
12
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4244 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4244 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 20.198.162.76:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
6544 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5064 | backgroundTaskHost.exe | 20.31.169.57:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | backgroundTaskHost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4244 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
github.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |