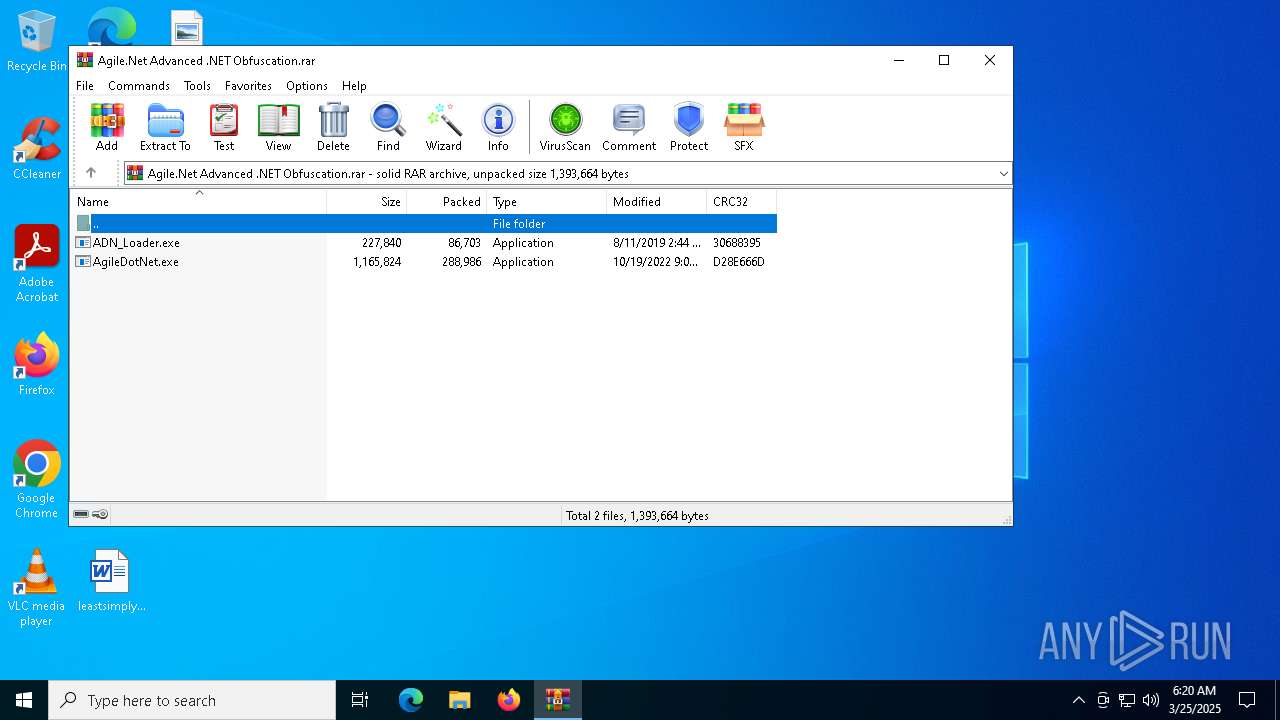
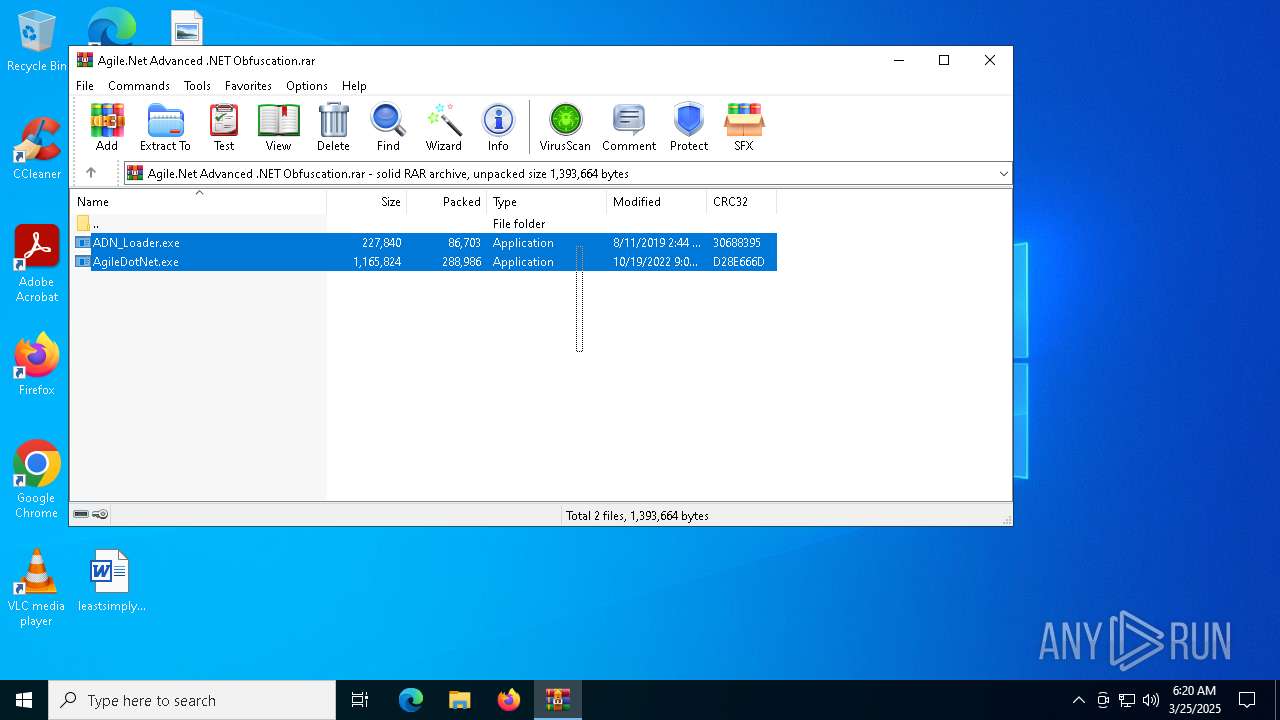
| File name: | Agile.Net Advanced .NET Obfuscation.rar |
| Full analysis: | https://app.any.run/tasks/c7830e9f-623d-4e36-a2a6-bcfb632d3511 |
| Verdict: | Malicious activity |
| Analysis date: | March 25, 2025, 06:20:18 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 5ADA21E85816EA14D61972F519EB29CC |
| SHA1: | 7C10FAA09842F9C4D8497A892642E6BDA530DE3A |
| SHA256: | 747C77C46C59F90A151A59D06B5BAECCF8ADB4BC38C4587D4B73E97143B9C1C8 |
| SSDEEP: | 6144:L72p+Q/y4H4o8zkvxESvX/ns8j29LRe/N+/99AwCoMoBlFuawWijnDNNZ44KVd4Q:/2u4ukvD3nIdRek1x/MmsawWif/hKIwD |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7296)
SUSPICIOUS
Executable content was dropped or overwritten
- ADN_Loader.exe (PID: 7884)
- x64.exe (PID: 8032)
Starts CMD.EXE for commands execution
- ADN_Loader.exe (PID: 7884)
Executing commands from a ".bat" file
- ADN_Loader.exe (PID: 7884)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7952)
Executes application which crashes
- AgileDotNet.exe (PID: 8052)
INFO
Create files in a temporary directory
- ADN_Loader.exe (PID: 7884)
- x64.exe (PID: 8032)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7296)
Manual execution by a user
- ADN_Loader.exe (PID: 7776)
- ADN_Loader.exe (PID: 7884)
Checks supported languages
- ADN_Loader.exe (PID: 7884)
- x64.exe (PID: 8032)
- AgileDotNet.exe (PID: 8052)
Reads the computer name
- AgileDotNet.exe (PID: 8052)
Creates files or folders in the user directory
- WerFault.exe (PID: 2656)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 86703 |
| UncompressedSize: | 227840 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | ADN_Loader.exe |
Total processes
146
Monitored processes
13
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2656 | C:\WINDOWS\system32\WerFault.exe -u -p 8052 -s 792 | C:\Windows\System32\WerFault.exe | — | AgileDotNet.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7296 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Agile.Net Advanced .NET Obfuscation.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7552 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7596 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7776 | "C:\Users\admin\Desktop\ADN_Loader.exe" | C:\Users\admin\Desktop\ADN_Loader.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 7884 | "C:\Users\admin\Desktop\ADN_Loader.exe" | C:\Users\admin\Desktop\ADN_Loader.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 7896 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ADN_Loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7952 | "C:\WINDOWS\system32\cmd" /c "C:\Users\admin\AppData\Local\Temp\C69D.tmp\C6AE.bat C:\Users\admin\Desktop\ADN_Loader.exe" | C:\Windows\System32\cmd.exe | — | ADN_Loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7984 | reg query HKEY_LOCAL_MACHINE\Software\imotech | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8008 | reg query HKEY_CURRENT_USER\Software\imotech | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 392
Read events
3 349
Write events
40
Delete events
3
Modification events
| (PID) Process: | (7296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Agile.Net Advanced .NET Obfuscation.rar | |||
| (PID) Process: | (7296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (7296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
5
Suspicious files
2
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2656 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_AgileDotNet.exe_5c881e1c547b36d8b882a886ec9144542927c8c_b4bcee58_66d1bb1b-47c5-49dd-8c32-c52c94e8e3ac\Report.wer | — | |
MD5:— | SHA256:— | |||
| 2656 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\AgileDotNet.exe.8052.dmp | — | |
MD5:— | SHA256:— | |||
| 7296 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7296.43471\ADN_Loader.exe | executable | |
MD5:A43BE7AC8AC3F4FC3C47D8328FB6B11F | SHA256:6E06F86D6BF4AE15090E9C074C8E7E87764D05B995A644D1A35F48D998E101D4 | |||
| 7884 | ADN_Loader.exe | C:\Users\admin\Desktop\x64.exe | executable | |
MD5:B05AC25A3943C03A93748B945D4E5769 | SHA256:B30CB11EF8C7BC78CFACFA1F257A147114450074C2BBC00AA67B9781A73FEB14 | |||
| 2656 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERCE2F.tmp.dmp | binary | |
MD5:CA8461FB8995A32594EF79275E74942A | SHA256:3D3FA8496E0A6C534A314240AF31475DB4A2DA9E8F88596731E50716A7227E38 | |||
| 7296 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7296.43471\AgileDotNet.exe | executable | |
MD5:5B0F00F24483A99ADAA455FD8166C863 | SHA256:2F4BCFAC54C540736B43235FC1CF60AD916308698C718093423B2D05229C3E75 | |||
| 8032 | x64.exe | C:\Users\admin\AppData\Local\Temp\dateinj01.dll | executable | |
MD5:4A170DACAB334791B0FB3C58CE89A698 | SHA256:55FAD45BD65CAF10722B5083F3E363871DC7351A7D0BF7D9FDBD47C371A57810 | |||
| 7884 | ADN_Loader.exe | C:\Users\admin\AppData\Local\Temp\C69D.tmp\C6AE.bat | text | |
MD5:07828F5CF65C79388F1C97543BD7D386 | SHA256:163556CE238E1634EC7F73FA71F498D3C71C71D269170625FAC1051BD8DDF268 | |||
| 2656 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERD073.tmp.xml | xml | |
MD5:EFD6EE1ABF65E6AEB8A52691676C43E2 | SHA256:4FE5376C6652EC719481FFDC1B4B4B05819E36E6CA75D1BD2475AB686E8D10BE | |||
| 7884 | ADN_Loader.exe | C:\Users\admin\Desktop\x86.exe | executable | |
MD5:63D605F8F25F0F588565FE8AB6BA2576 | SHA256:600F34375052FF602837D8D419AE82BD2EE3AB8088BDB7979103E2143F8E0D4D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
11
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.18.121.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.18.121.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5024 | RUXIMICS.exe | GET | 200 | 2.18.121.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5024 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.18.121.147:80 | crl.microsoft.com | AKAMAI-AS | FR | whitelisted |
2104 | svchost.exe | 2.18.121.147:80 | crl.microsoft.com | AKAMAI-AS | FR | whitelisted |
5024 | RUXIMICS.exe | 2.18.121.147:80 | crl.microsoft.com | AKAMAI-AS | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |