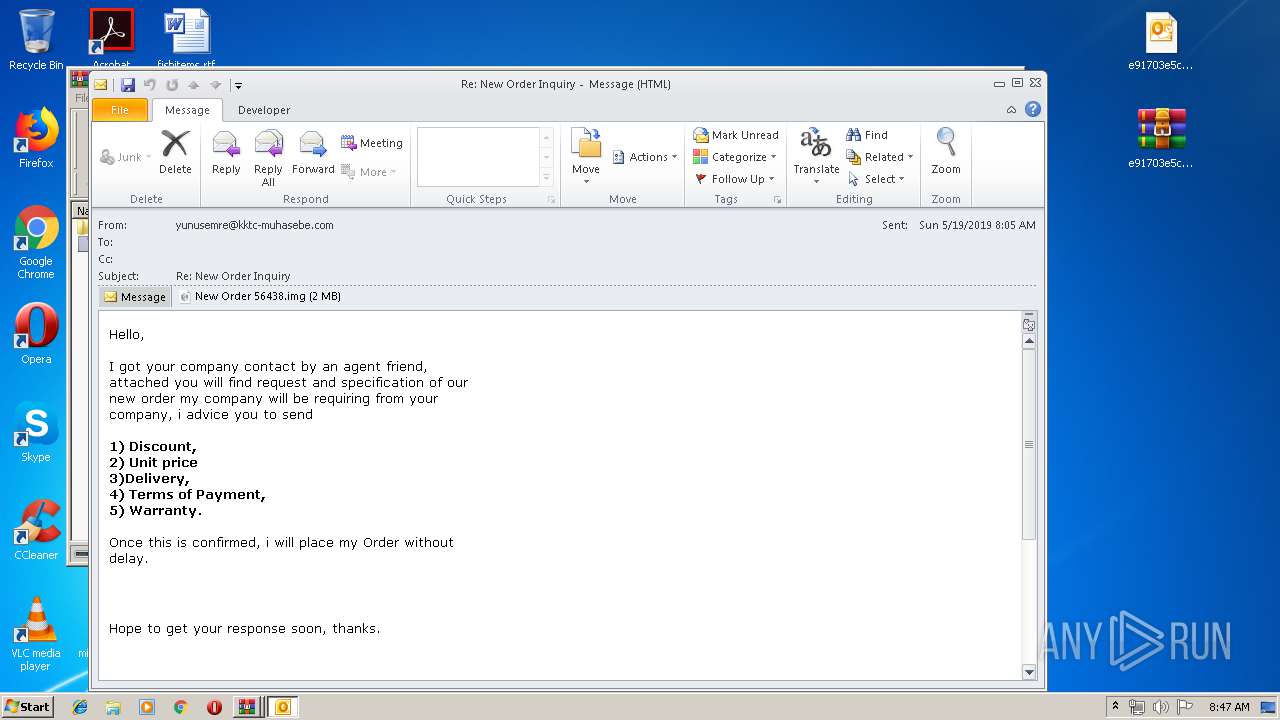
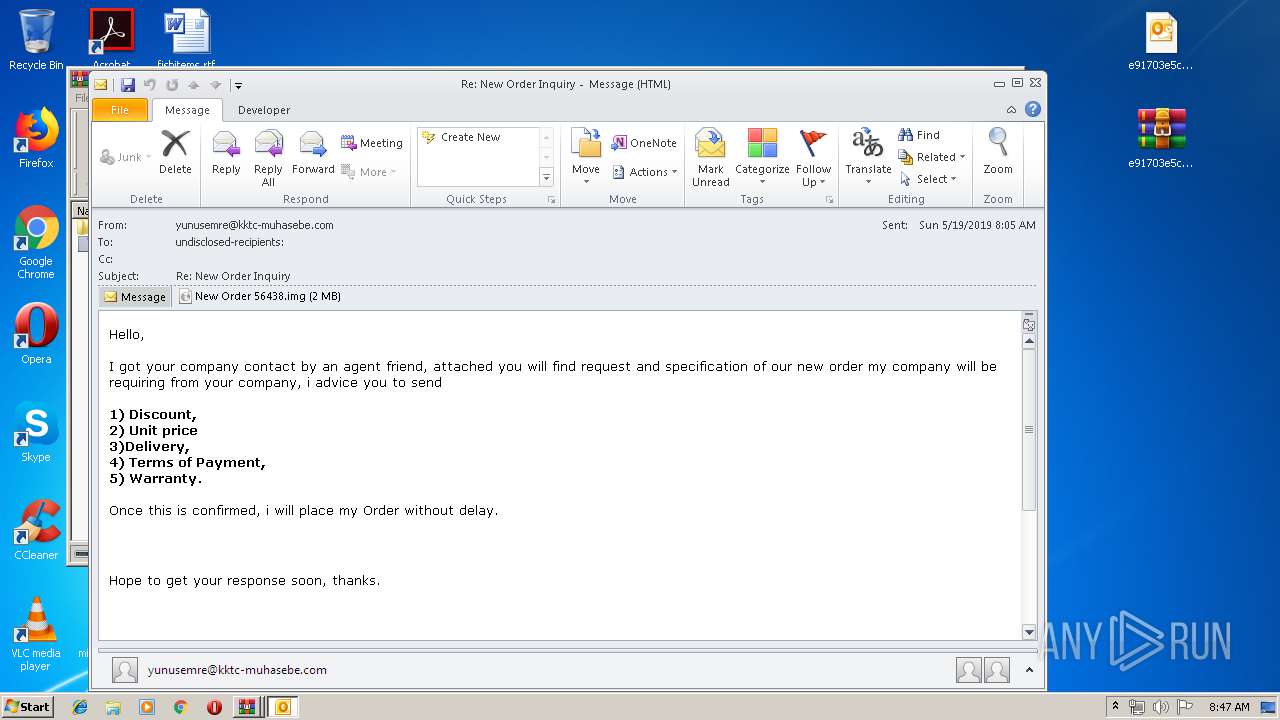
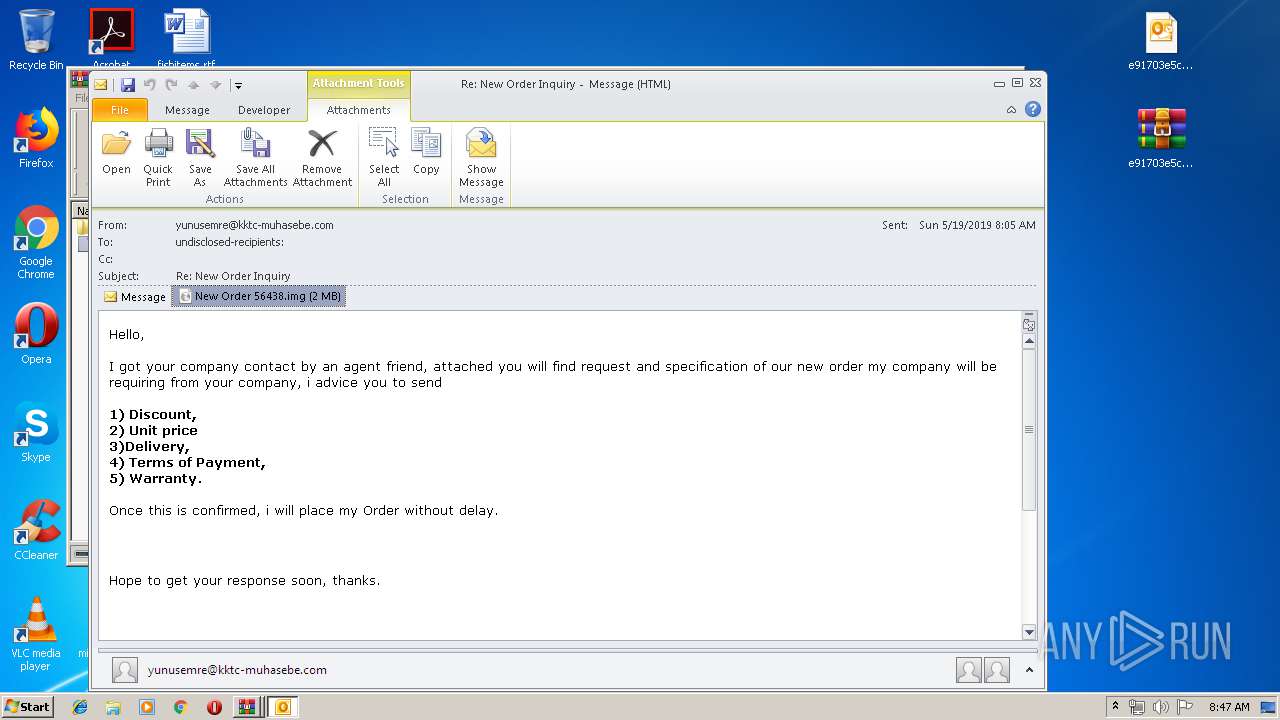
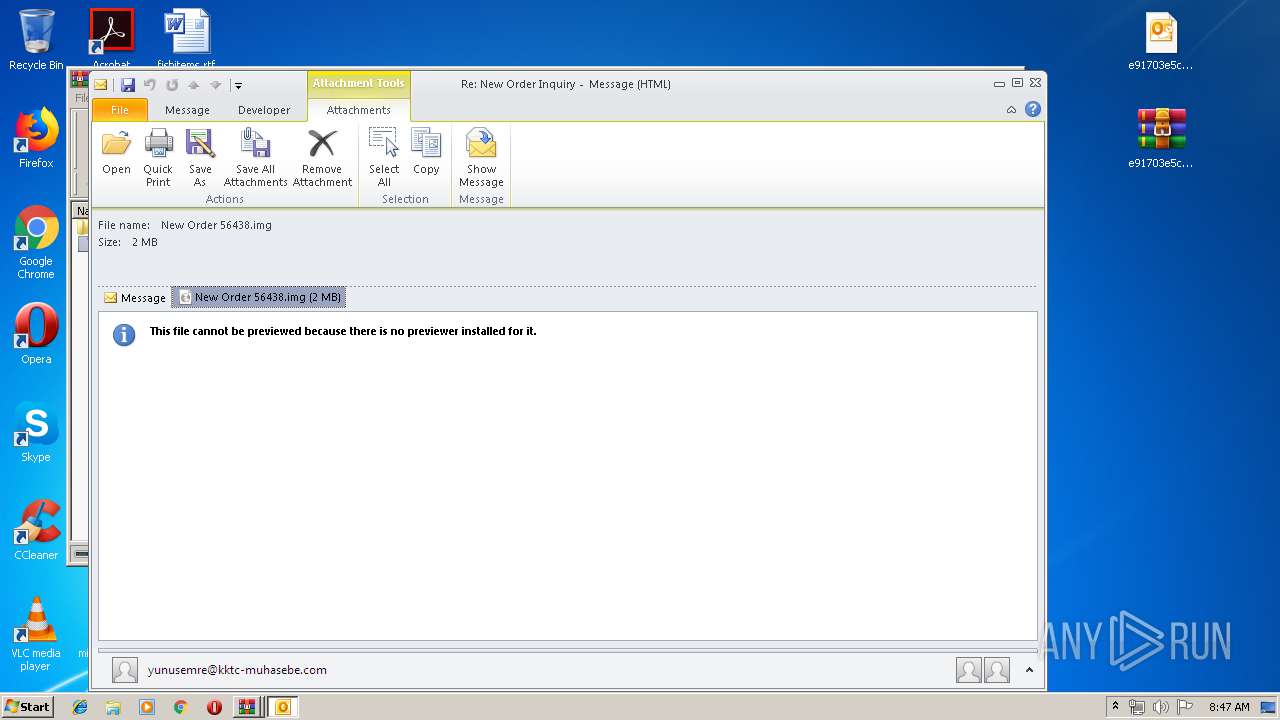
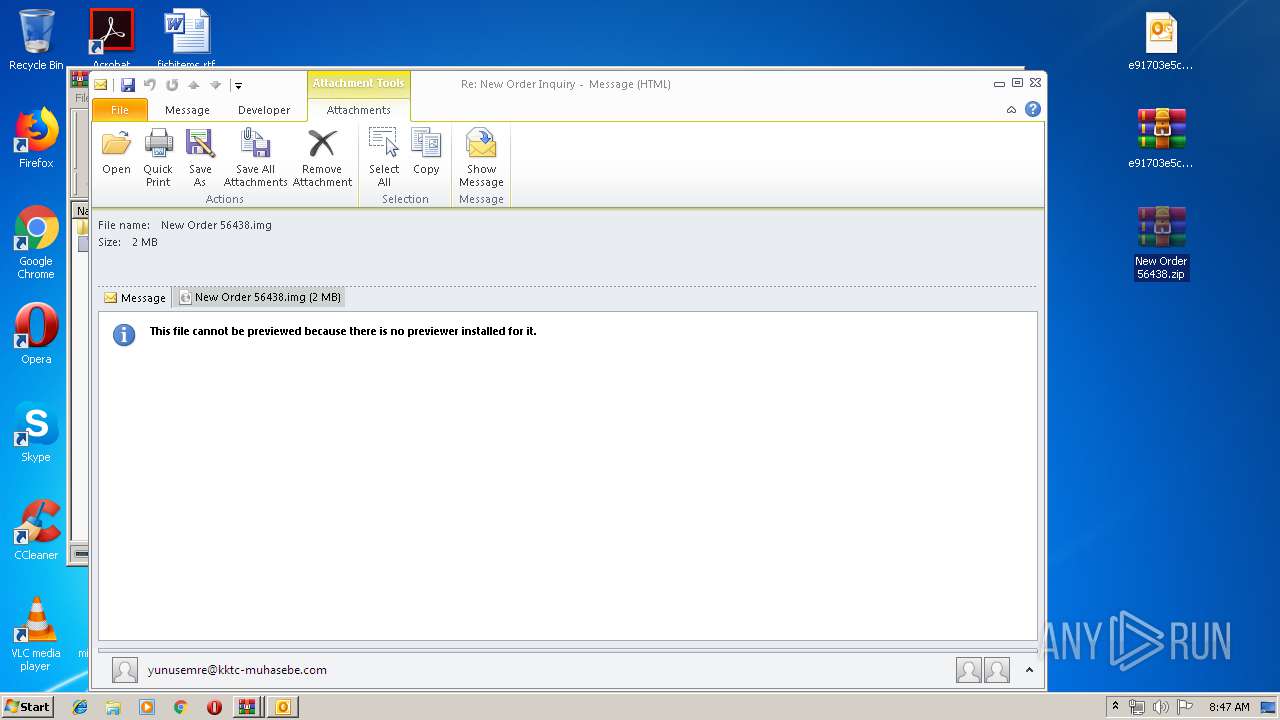
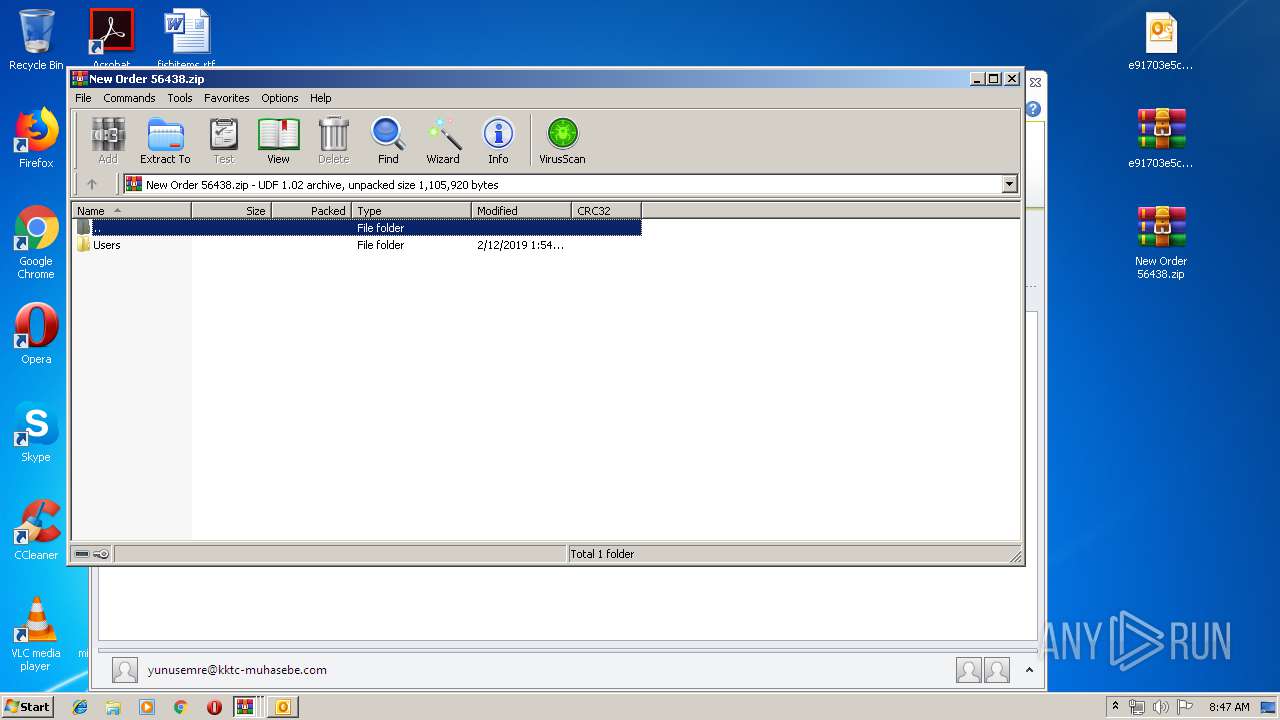
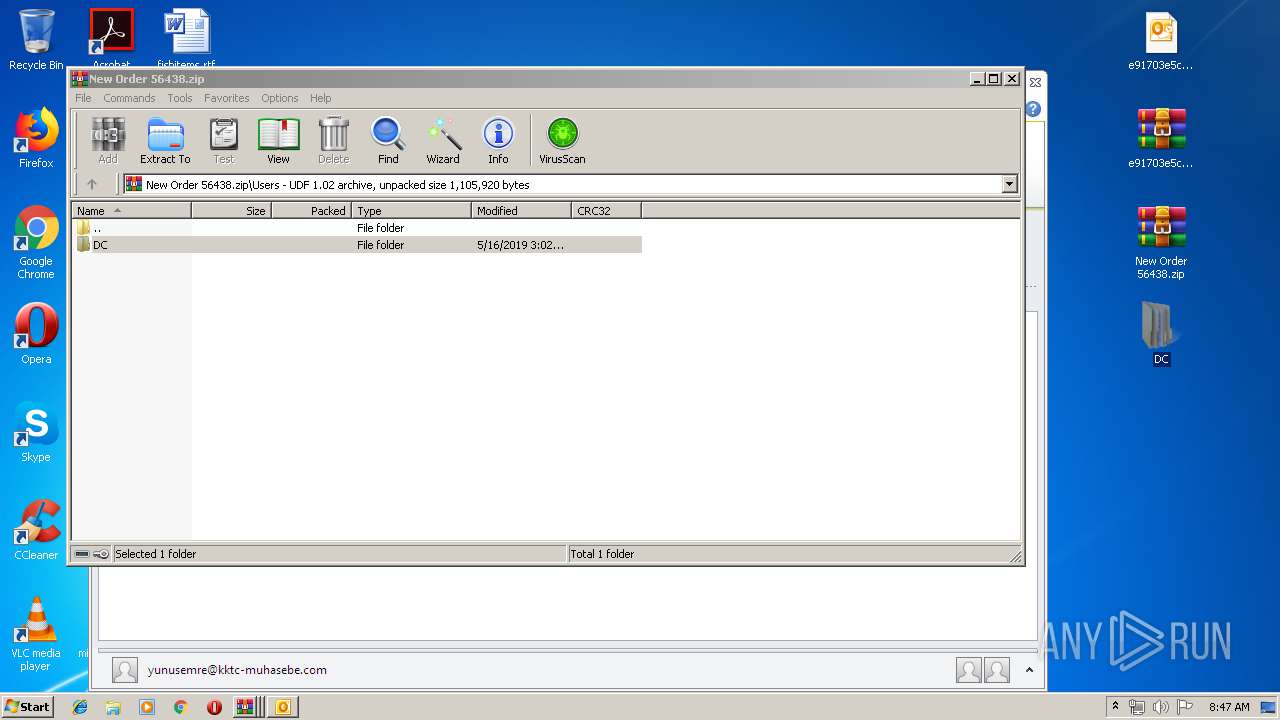
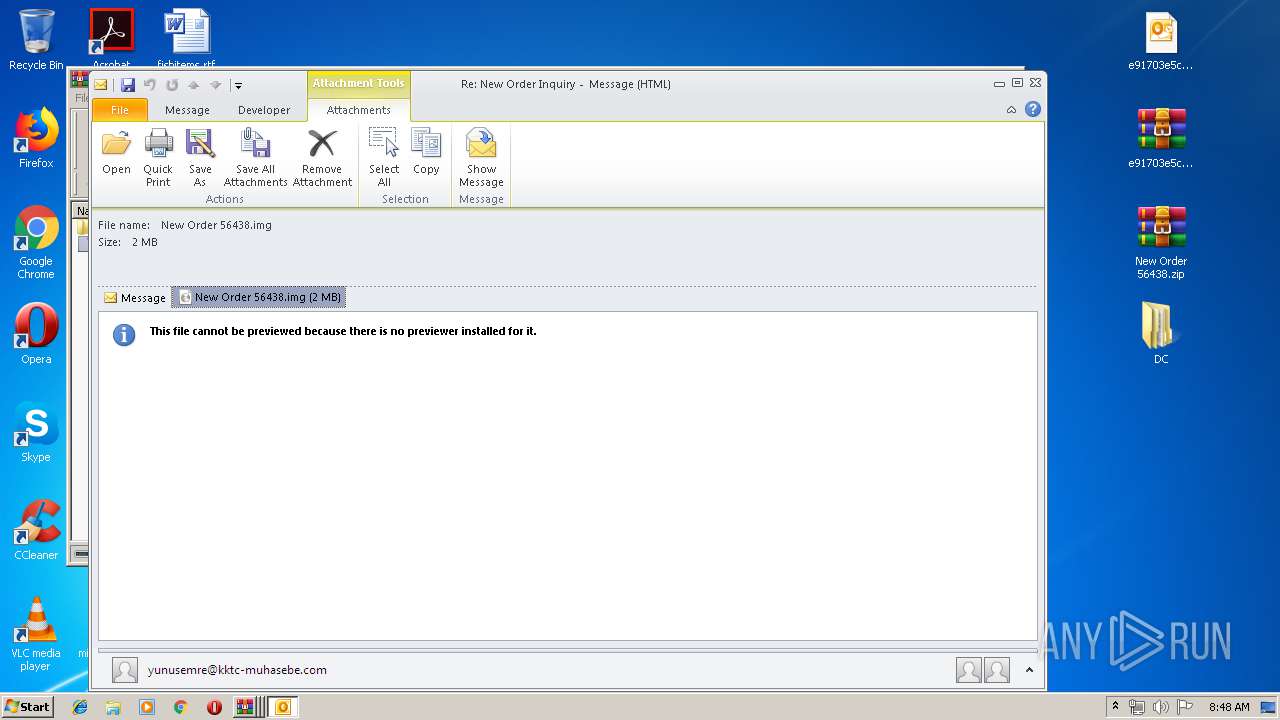
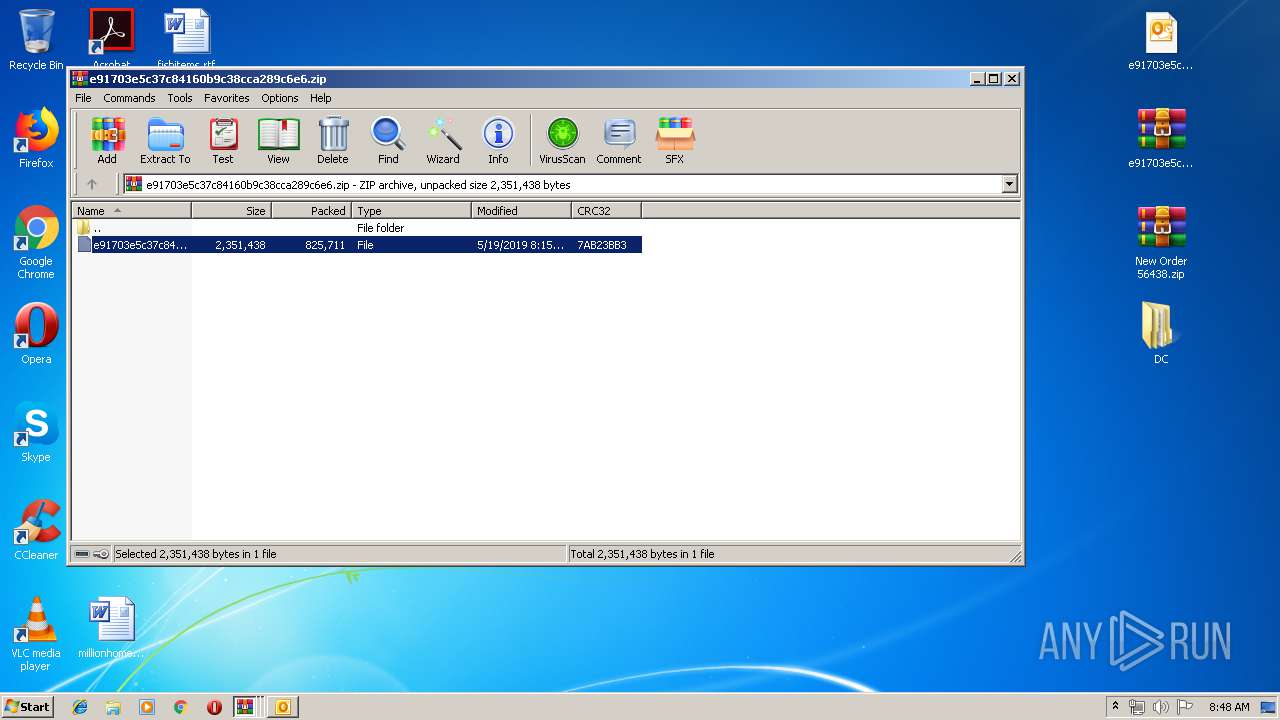
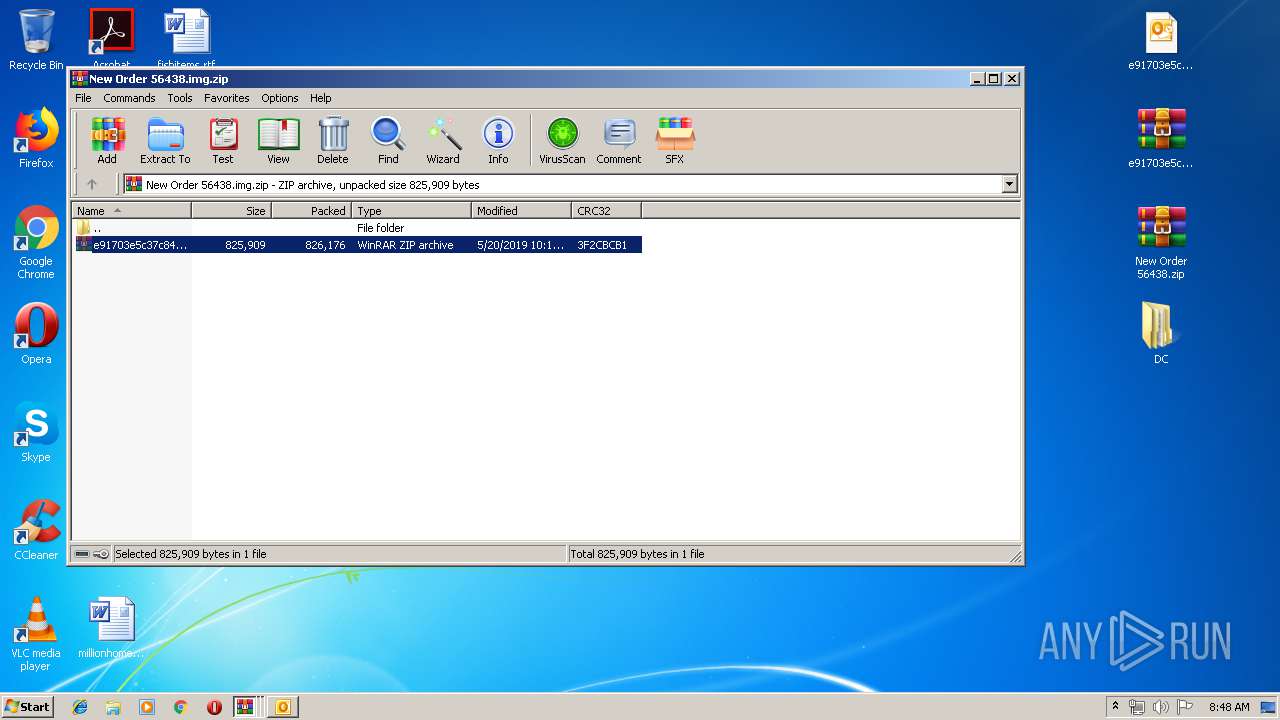
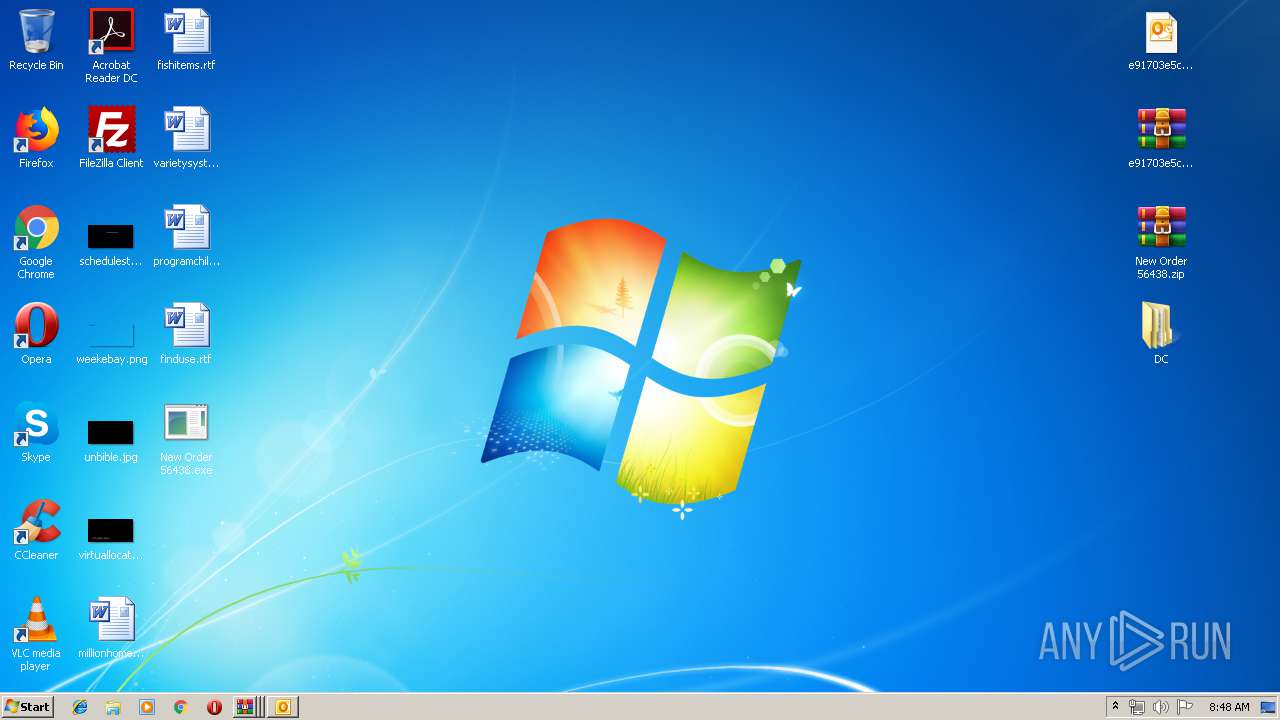
| File name: | New Order 56438.img.zip |
| Full analysis: | https://app.any.run/tasks/ed17e606-46c7-4f16-ac41-865b909e0680 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2019, 07:45:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | F04C1E0F58067022B5FC6D70DF121A33 |
| SHA1: | 898855C780497DA45FF5F7788D6496FBA7009367 |
| SHA256: | 747AFC81586CC0482CC95BC8D9DD4C9B21321FDC884F65FD8031B339E59CCD16 |
| SSDEEP: | 24576:OSqBh4jRnSZE0E4HA9B75u8e36AWqKWSOFkbKBFWR3w:Rqv4j1SZE0g3lTAWpOCbK6g |
MALICIOUS
Application was dropped or rewritten from another process
- New Order 56438.exe (PID: 2000)
- New Order 56438.exe (PID: 1344)
- New Order 56438.exe (PID: 932)
- New Order 56438.exe (PID: 1464)
- New Order 56438.exe (PID: 2468)
- New Order 56438.exe (PID: 3476)
- New Order 56438.exe (PID: 3656)
- New Order 56438.exe (PID: 2864)
- New Order 56438.exe (PID: 3908)
- New Order 56438.exe (PID: 1500)
- New Order 56438.exe (PID: 1152)
- New Order 56438.exe (PID: 1348)
- New Order 56438.exe (PID: 2932)
- New Order 56438.exe (PID: 2816)
SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 3132)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3132)
Application launched itself
- New Order 56438.exe (PID: 1344)
- New Order 56438.exe (PID: 2864)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2860)
INFO
Manual execution by user
- OUTLOOK.EXE (PID: 3132)
- WinRAR.exe (PID: 2844)
- WinRAR.exe (PID: 2860)
- New Order 56438.exe (PID: 1344)
- New Order 56438.exe (PID: 2864)
- WinRAR.exe (PID: 1020)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3132)
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 2844)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:05:20 10:16:19 |
| ZipCRC: | 0x3f2cbcb1 |
| ZipCompressedSize: | 826176 |
| ZipUncompressedSize: | 825909 |
| ZipFileName: | e91703e5c37c84160b9c38cca289c6e6.zip |
Total processes
62
Monitored processes
19
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 932 | "C:\Users\admin\Desktop\New Order 56438.exe" | C:\Users\admin\Desktop\New Order 56438.exe | — | New Order 56438.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1020 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\New Order 56438.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1152 | "C:\Users\admin\Desktop\New Order 56438.exe" | C:\Users\admin\Desktop\New Order 56438.exe | — | New Order 56438.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1344 | "C:\Users\admin\Desktop\New Order 56438.exe" | C:\Users\admin\Desktop\New Order 56438.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1348 | "C:\Users\admin\Desktop\New Order 56438.exe" | C:\Users\admin\Desktop\New Order 56438.exe | — | New Order 56438.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1464 | "C:\Users\admin\Desktop\New Order 56438.exe" | C:\Users\admin\Desktop\New Order 56438.exe | — | New Order 56438.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1500 | "C:\Users\admin\Desktop\New Order 56438.exe" | C:\Users\admin\Desktop\New Order 56438.exe | — | New Order 56438.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2000 | "C:\Users\admin\Desktop\New Order 56438.exe" | C:\Users\admin\Desktop\New Order 56438.exe | — | New Order 56438.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2468 | "C:\Users\admin\Desktop\New Order 56438.exe" | C:\Users\admin\Desktop\New Order 56438.exe | — | New Order 56438.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2816 | "C:\Users\admin\Desktop\New Order 56438.exe" | C:\Users\admin\Desktop\New Order 56438.exe | — | New Order 56438.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
2 604
Read events
2 154
Write events
431
Delete events
19
Modification events
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\New Order 56438.img.zip | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
Executable files
1
Suspicious files
2
Text files
24
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2956.37450\e91703e5c37c84160b9c38cca289c6e6.zip | — | |
MD5:— | SHA256:— | |||
| 3132 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR245.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3132 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp44A.tmp | — | |
MD5:— | SHA256:— | |||
| 3132 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\VDC3F7YO\New Order 56438 (2).img\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2860 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2860.45331\Users\DC\Desktop\New Order 56438.exe | — | |
MD5:— | SHA256:— | |||
| 2844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2844.38972\e91703e5c37c84160b9c38cca289c6e6 | eml | |
MD5:— | SHA256:— | |||
| 3132 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3132 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\VDC3F7YO\New Order 56438 (2).img | compressed | |
MD5:— | SHA256:— | |||
| 3132 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:48DD6CAE43CE26B992C35799FCD76898 | SHA256:7BFE1F3691E2B4FB4D61FBF5E9F7782FBE49DA1342DBD32201C2CC8E540DBD1A | |||
| 3132 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\VDC3F7YO\New Order 56438.img | compressed | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3132 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |