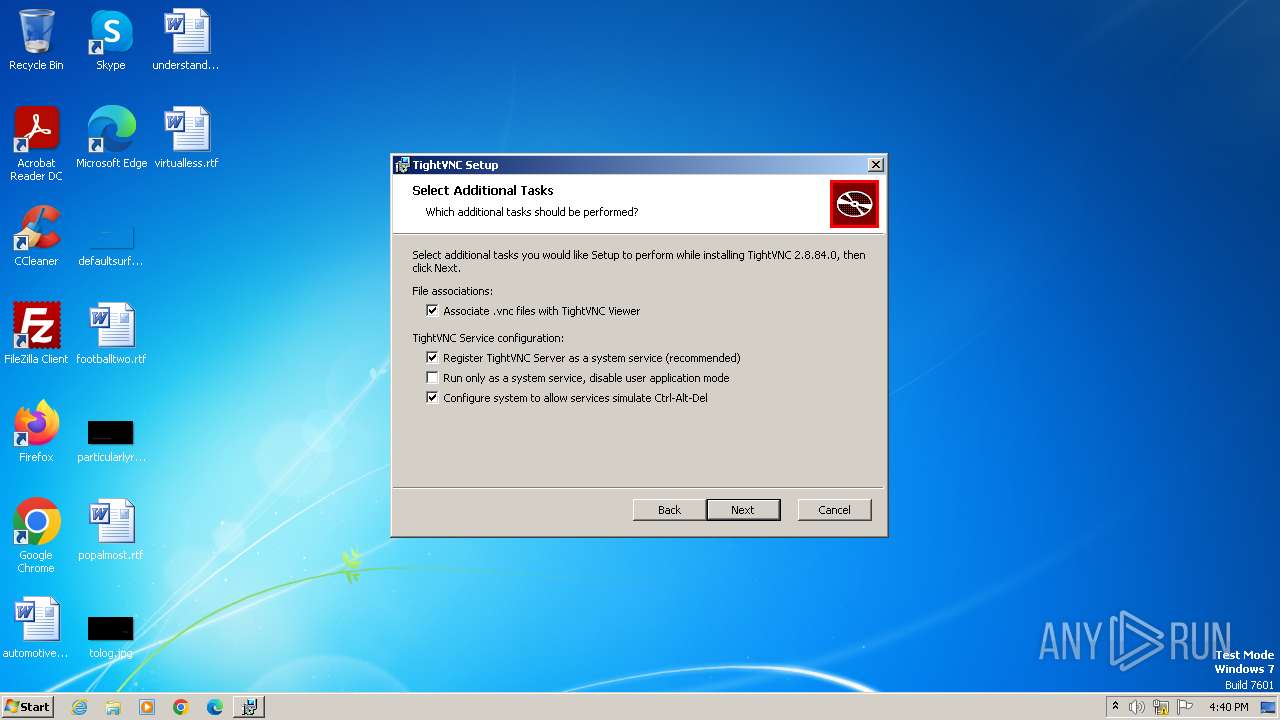
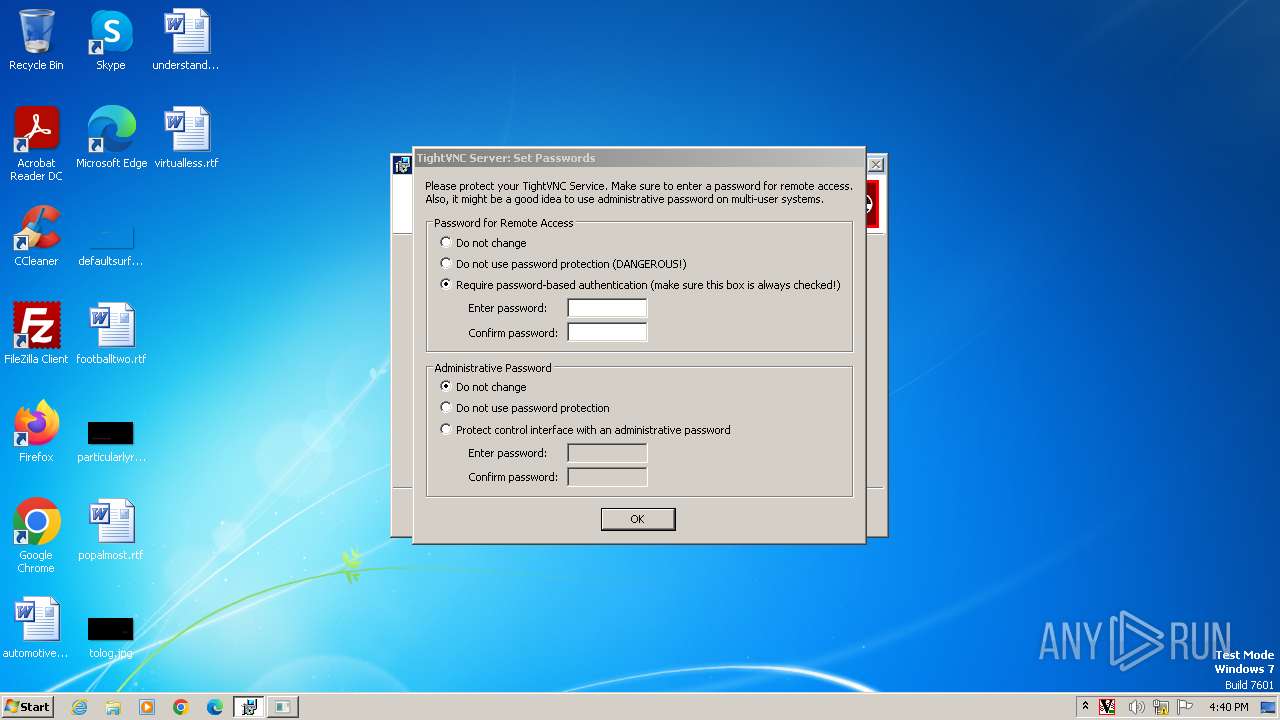
| File name: | tightvnc-2.8.84-gpl-setup-32bit.msi |
| Full analysis: | https://app.any.run/tasks/6be2f140-c190-4df6-95ad-7999ab8274ba |
| Verdict: | Malicious activity |
| Analysis date: | May 28, 2024, 15:39:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: TightVNC, Author: GlavSoft LLC., Keywords: Installer, Comments: This installer database contains the logic and data required to install TightVNC., Template: Intel;1033, Revision Number: {E3F7046B-43B7-475F-A50D-785A7AD35191}, Create Time/Date: Wed May 8 07:06:12 2024, Last Saved Time/Date: Wed May 8 07:06:12 2024, Number of Pages: 200, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.11.2.4516), Security: 2 |
| MD5: | 1D061EA0A0413669C4320040B308CB4C |
| SHA1: | DDAC4E4CC6A510F5B48E168293961F71A4318DE2 |
| SHA256: | 74777A93BA424EE70B3020AF8BA03E7A6A618C74AB447F83291AAD5211F1A3EA |
| SSDEEP: | 98304:29FMEM2zLOPN5uuBq9L4/c5TI98y5BcOBvn73wAMEoI4Ty0M33/0fnraa5ybtY:yR |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 3972)
- msiexec.exe (PID: 4020)
Changes the autorun value in the registry
- tvnserver.exe (PID: 2256)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 1200)
- tvnserver.exe (PID: 1804)
Process drops legitimate windows executable
- msiexec.exe (PID: 4020)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 4020)
Application launched itself
- tvnserver.exe (PID: 824)
- tvnserver.exe (PID: 444)
Checks Windows Trust Settings
- msiexec.exe (PID: 4020)
INFO
Reads security settings of Internet Explorer
- msiexec.exe (PID: 3972)
Reads the software policy settings
- msiexec.exe (PID: 3972)
- msiexec.exe (PID: 4020)
Reads the machine GUID from the registry
- msiexec.exe (PID: 4020)
- msiexec.exe (PID: 4060)
- msiexec.exe (PID: 1132)
- msiexec.exe (PID: 1552)
Application launched itself
- msiexec.exe (PID: 4020)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4020)
- msiexec.exe (PID: 3972)
Reads the computer name
- msiexec.exe (PID: 4020)
- msiexec.exe (PID: 1132)
- msiexec.exe (PID: 1552)
- tvnserver.exe (PID: 2256)
- tvnserver.exe (PID: 824)
- tvnserver.exe (PID: 1804)
- msiexec.exe (PID: 4060)
Checks supported languages
- msiexec.exe (PID: 4060)
- msiexec.exe (PID: 4020)
- tvnserver.exe (PID: 2256)
- tvnserver.exe (PID: 824)
- msiexec.exe (PID: 1552)
- tvnserver.exe (PID: 1804)
- tvnserver.exe (PID: 2464)
- tvnserver.exe (PID: 2476)
- tvnserver.exe (PID: 444)
- tvnviewer.exe (PID: 2656)
- msiexec.exe (PID: 1132)
Create files in a temporary directory
- msiexec.exe (PID: 4020)
Creates a software uninstall entry
- msiexec.exe (PID: 4020)
Manual execution by a user
- tvnviewer.exe (PID: 2656)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | TightVNC |
| Author: | GlavSoft LLC. |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install TightVNC. |
| Template: | Intel;1033 |
| RevisionNumber: | {E3F7046B-43B7-475F-A50D-785A7AD35191} |
| CreateDate: | 2024:05:08 07:06:12 |
| ModifyDate: | 2024:05:08 07:06:12 |
| Pages: | 200 |
| Words: | 2 |
| Software: | Windows Installer XML Toolset (3.11.2.4516) |
| Security: | Read-only recommended |
Total processes
46
Monitored processes
13
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 444 | "C:\Program Files\TightVNC\tvnserver.exe" -checkservicepasswords | C:\Program Files\TightVNC\tvnserver.exe | — | msiexec.exe | |||||||||||
User: admin Company: GlavSoft LLC. Integrity Level: MEDIUM Description: TightVNC Server Exit code: 0 Version: 2, 8, 84, 0 Modules
| |||||||||||||||
| 824 | "C:\Program Files\TightVNC\tvnserver.exe" -start | C:\Program Files\TightVNC\tvnserver.exe | — | msiexec.exe | |||||||||||
User: admin Company: GlavSoft LLC. Integrity Level: MEDIUM Description: TightVNC Server Exit code: 0 Version: 2, 8, 84, 0 Modules
| |||||||||||||||
| 1132 | C:\Windows\system32\MsiExec.exe -Embedding 4359C2A185FCDFA5C95ECE89A7170BF8 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1200 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1552 | C:\Windows\system32\MsiExec.exe -Embedding E547009CDBB2C079299F71A45E85DEF5 E Global\MSI0000 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1804 | "C:\Program Files\TightVNC\tvnserver.exe" -service | C:\Program Files\TightVNC\tvnserver.exe | — | services.exe | |||||||||||
User: SYSTEM Company: GlavSoft LLC. Integrity Level: SYSTEM Description: TightVNC Server Version: 2, 8, 84, 0 Modules
| |||||||||||||||
| 2256 | "C:\Program Files\TightVNC\tvnserver.exe" -reinstall -silent | C:\Program Files\TightVNC\tvnserver.exe | msiexec.exe | ||||||||||||
User: admin Company: GlavSoft LLC. Integrity Level: MEDIUM Description: TightVNC Server Exit code: 0 Version: 2, 8, 84, 0 Modules
| |||||||||||||||
| 2464 | "C:\Program Files\TightVNC\tvnserver.exe" -controlservice -slave | C:\Program Files\TightVNC\tvnserver.exe | tvnserver.exe | ||||||||||||
User: SYSTEM Company: GlavSoft LLC. Integrity Level: SYSTEM Description: TightVNC Server Version: 2, 8, 84, 0 Modules
| |||||||||||||||
| 2476 | "C:\Program Files\TightVNC\tvnserver.exe" -controlservice -reload | C:\Program Files\TightVNC\tvnserver.exe | tvnserver.exe | ||||||||||||
User: SYSTEM Company: GlavSoft LLC. Integrity Level: SYSTEM Description: TightVNC Server Exit code: 0 Version: 2, 8, 84, 0 Modules
| |||||||||||||||
| 2656 | "C:\Program Files\TightVNC\tvnviewer.exe" | C:\Program Files\TightVNC\tvnviewer.exe | — | explorer.exe | |||||||||||
User: admin Company: GlavSoft LLC. Integrity Level: MEDIUM Description: TightVNC Viewer Exit code: 0 Version: 2, 8, 84, 0 Modules
| |||||||||||||||
Total events
14 158
Read events
13 719
Write events
423
Delete events
16
Modification events
| (PID) Process: | (3972) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4020) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 400000000000000086F4515915B1DA01B40F000000040000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4020) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 400000000000000086F4515915B1DA01B40F000000040000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4020) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 75 | |||
| (PID) Process: | (4020) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000005A75155A15B1DA01B40F000000040000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4020) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000B4D7175A15B1DA01B40F0000EC070000E80300000100000000000000000000007533668F9B99C64DB66399535A48C6B30000000000000000 | |||
| (PID) Process: | (1200) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000084EA2A5A15B1DA01B004000048010000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1200) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000084EA2A5A15B1DA01B0040000A0030000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1200) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000084EA2A5A15B1DA01B004000038080000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1200) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000084EA2A5A15B1DA01B0040000A0040000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
13
Suspicious files
16
Text files
3
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4020 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 4020 | msiexec.exe | C:\Windows\Installer\MSIE332.tmp | executable | |
MD5:A3AE5D86ECF38DB9427359EA37A5F646 | SHA256:C8D190D5BE1EFD2D52F72A72AE9DFA3940AB3FACEB626405959349654FE18B74 | |||
| 4020 | msiexec.exe | C:\Windows\Installer\MSIE2B2.tmp | executable | |
MD5:A3AE5D86ECF38DB9427359EA37A5F646 | SHA256:C8D190D5BE1EFD2D52F72A72AE9DFA3940AB3FACEB626405959349654FE18B74 | |||
| 4020 | msiexec.exe | C:\Program Files\TightVNC\TightVNC Web Site.url | url | |
MD5:398AD5309240BAD56D399DF9517BB12C | SHA256:0B9A87C6A3E5EA6448CC4CECABD780457966B60AC38BEC75E3B47C1085D4DD14 | |||
| 4020 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:8391AF5E7D968C1734199F1C528FAA62 | SHA256:CFDDC68799F5DDF0A51FB0F49F67F6687E9C5D98ABD3BE73C7AB6D7F0B1A4FF4 | |||
| 4020 | msiexec.exe | C:\Windows\Installer\MSIE301.tmp | executable | |
MD5:93394D2866590FB66759F5F0263453F2 | SHA256:5C29B8255ACE0CD94C066C528C8AD04F0F45EBA12FCF94DA7B9CA1B64AD4288B | |||
| 4020 | msiexec.exe | C:\Windows\Installer\MSIE312.tmp | executable | |
MD5:93394D2866590FB66759F5F0263453F2 | SHA256:5C29B8255ACE0CD94C066C528C8AD04F0F45EBA12FCF94DA7B9CA1B64AD4288B | |||
| 4020 | msiexec.exe | C:\Windows\Installer\MSIE282.tmp | binary | |
MD5:C982193AA71387041B08163132DEC292 | SHA256:BA0C49DE0FC34CB98D5AEDADA92BBBA7421AEFD3EA5F7EDF9BDB61A6B6FAE4B7 | |||
| 4020 | msiexec.exe | C:\Program Files\TightVNC\screenhooks32.dll | executable | |
MD5:EEFA2026B9FCC1476A5917E9D5743A6E | SHA256:A9880C8D67203E516FCDA0DE8D0E65A17BC665F201EC9C61F1E5A00DF9901A38 | |||
| 4020 | msiexec.exe | C:\Program Files\TightVNC\tvnviewer.exe | executable | |
MD5:AFC76796248AEBB026ED8A070A62D1BA | SHA256:DE6558F9F6F83CA7B1336D3D558537F697F68E3FDF41997D114567C293495180 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |