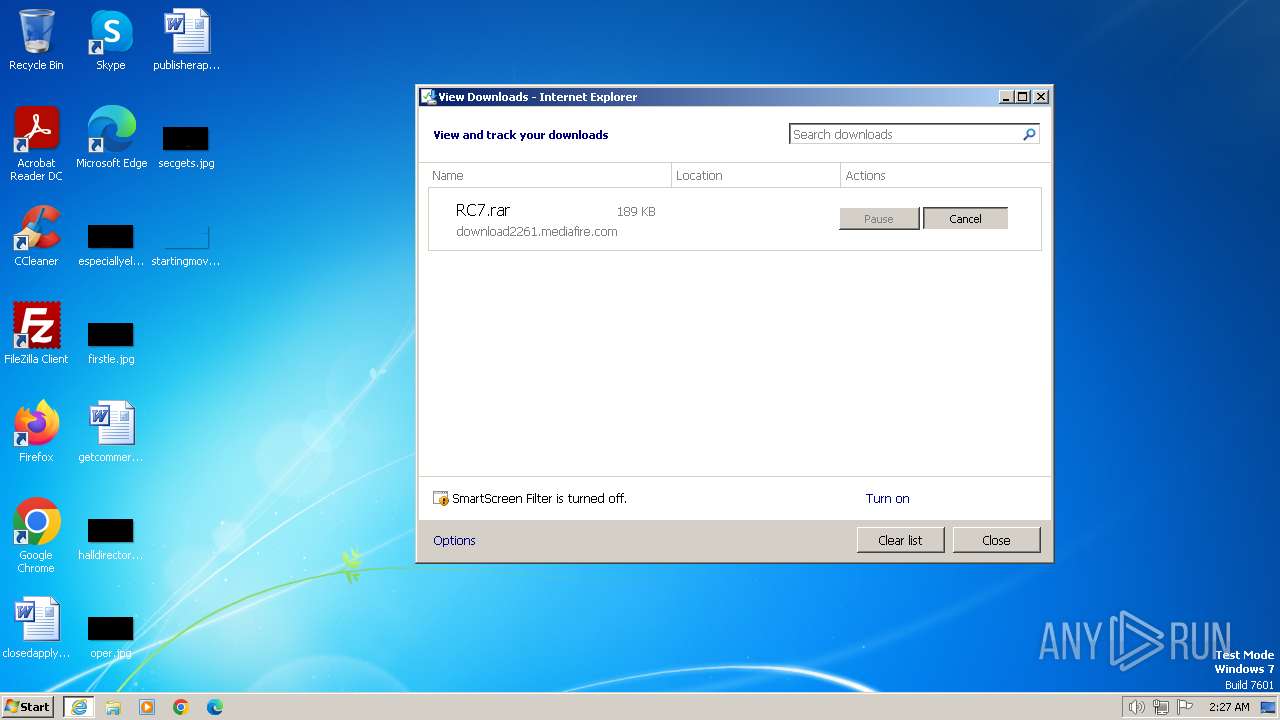
| URL: | https://download2261.mediafire.com/hoqfnel9n7iggbSU0m6HRV3vNMlnwSjyCn81_p00HLwpkw2X75JR5z52o4x98GtMQkXpPY0Mx3N8q_qNHja-x_4clTIUgsb4k7rsBomuZONkR1VTKmCxxiNc41z3Z4pzull1K4MN9HBGwFG0kh2ZecO5dtHKJiLIk490ZYi3QrvslFU/nzfujcxwop05pzg/RC7.rar |
| Full analysis: | https://app.any.run/tasks/fa6233c7-ba76-4e42-a6a8-b7e69befd2c5 |
| Verdict: | Malicious activity |
| Analysis date: | February 12, 2024, 02:26:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | D40388437BBE5613DDD06AFD7F046E5A |
| SHA1: | EBB0B5F2C731876F9EA02427947185291B93929B |
| SHA256: | 746DF70A5C0423E631AB75D5C89DFB2CC484A93D71C6CB88BDF57FA793794AEF |
| SSDEEP: | 3:N8SE52xQeGaKQVHroFFPb9vSX9jzXIAWSbJxs3vnOTUdbAzfclEyvsvoGOL/hQIP:2SW2xQeGB3rvSXl6Stq32TU5AYPd |
MALICIOUS
Adds path to the Windows Defender exclusion list
- rc7.exe (PID: 3388)
Create files in the Startup directory
- rc7.exe (PID: 3388)
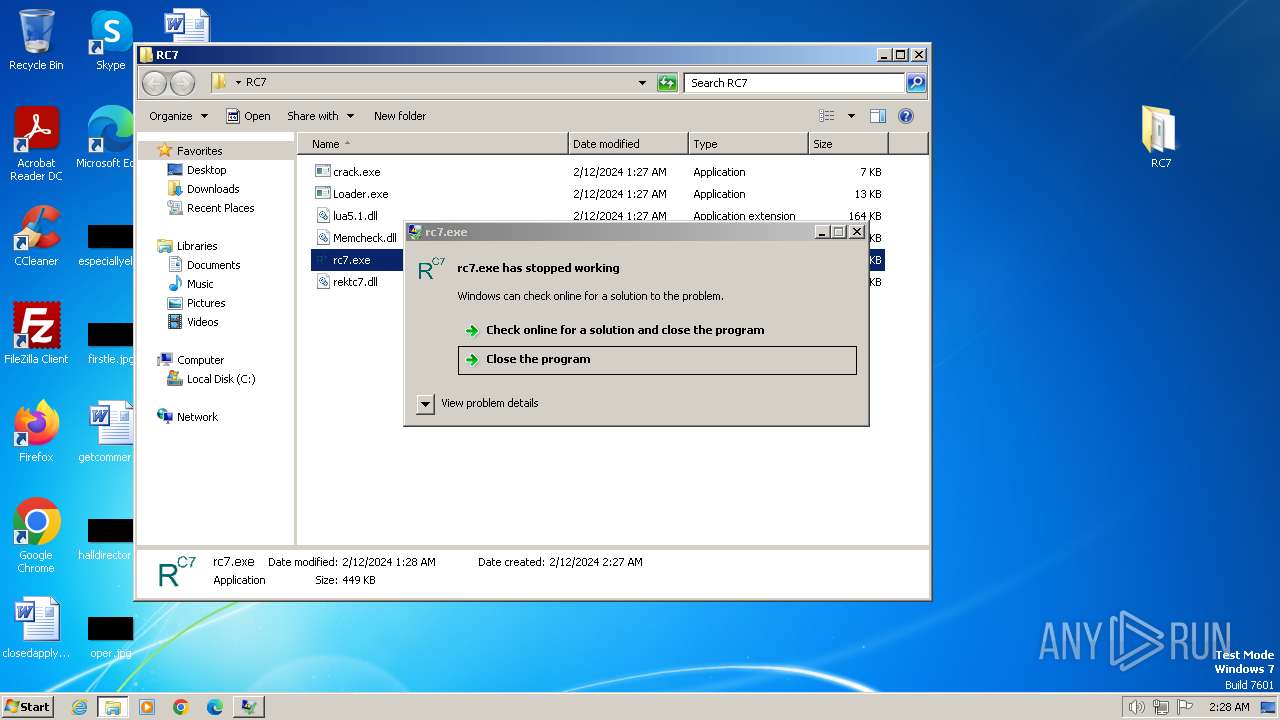
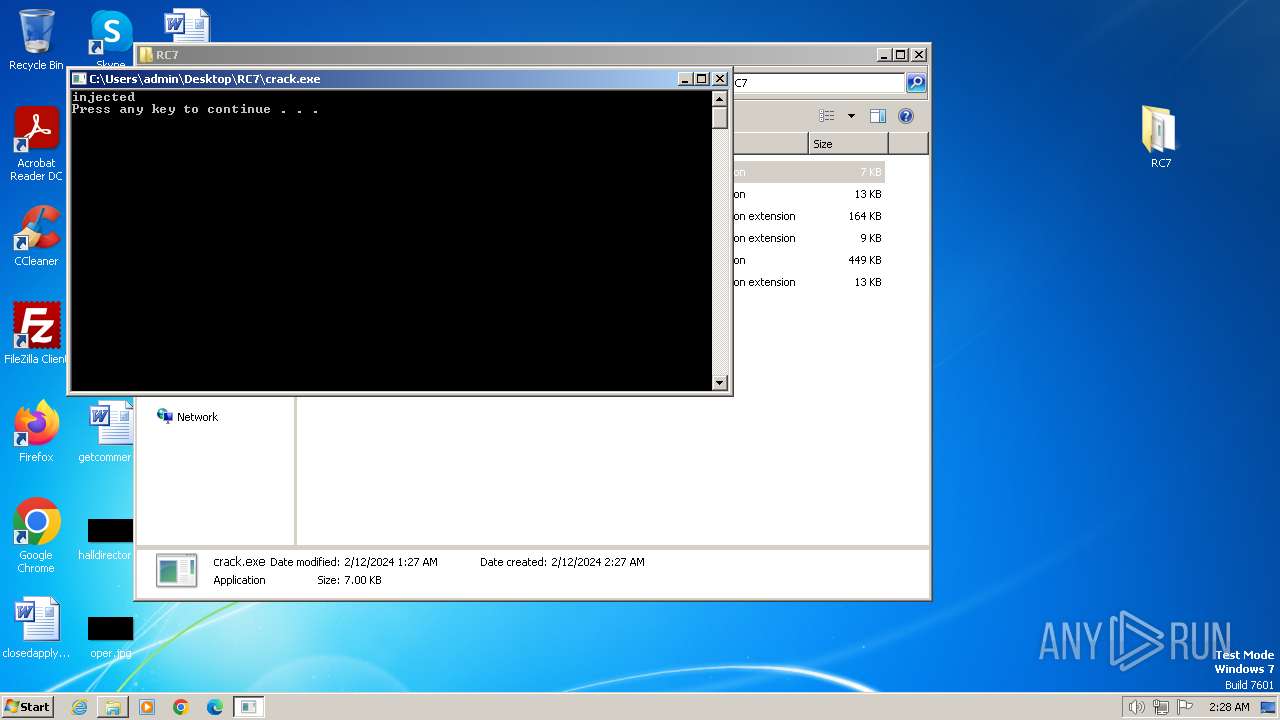
Runs injected code in another process
- crack.exe (PID: 1548)
Modifies hosts file to block updates
- rc7.exe (PID: 3388)
Application was injected by another process
- conhost.exe (PID: 2776)
Windows Defender preferences modified via 'Set-MpPreference'
- rc7.exe (PID: 3388)
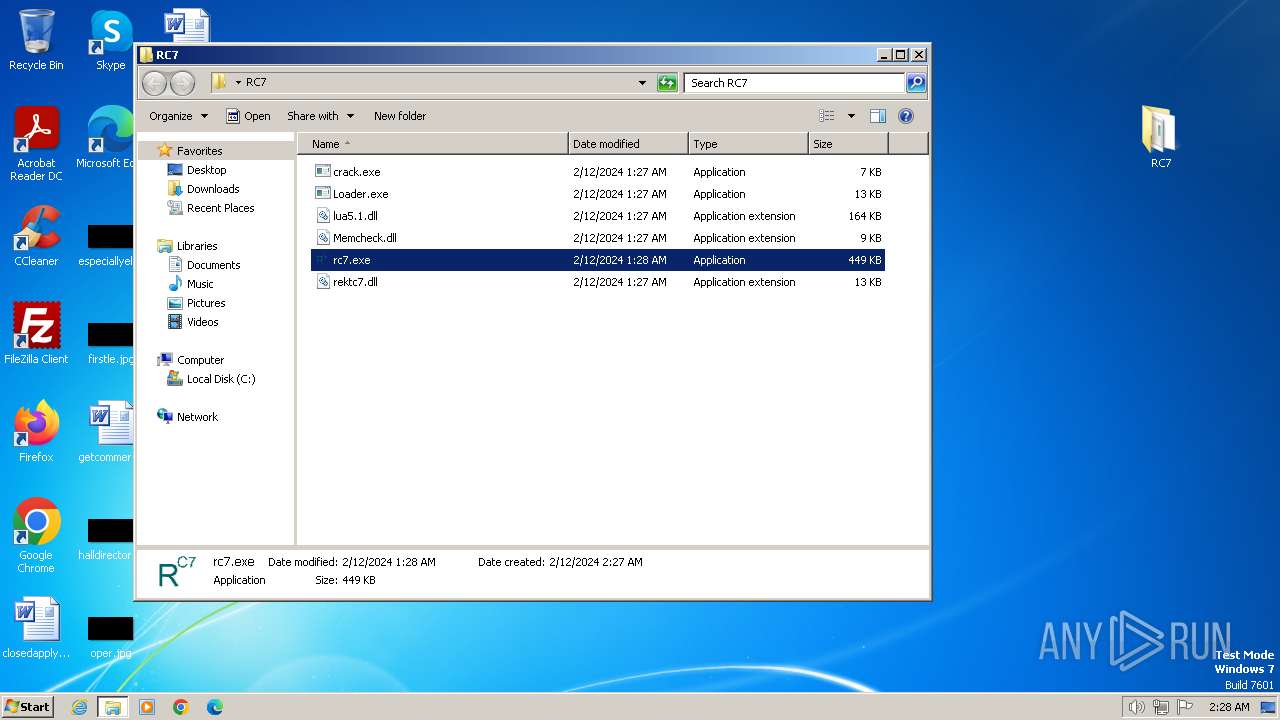
Drops the executable file immediately after the start
- rc7.exe (PID: 3388)
Actions looks like stealing of personal data
- rc7.exe (PID: 3388)
SUSPICIOUS
Reads the Internet Settings
- rc7.exe (PID: 2348)
- WMIC.exe (PID: 664)
- rc7.exe (PID: 3388)
- WMIC.exe (PID: 2764)
- powershell.exe (PID: 3276)
Uses WMIC.EXE to obtain Windows Installer data
- rc7.exe (PID: 2348)
- rc7.exe (PID: 3388)
Reads settings of System Certificates
- rc7.exe (PID: 2348)
- rc7.exe (PID: 3388)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 664)
- WMIC.exe (PID: 2764)
Reads security settings of Internet Explorer
- rc7.exe (PID: 2348)
Starts POWERSHELL.EXE for commands execution
- rc7.exe (PID: 3388)
Uses ATTRIB.EXE to modify file attributes
- rc7.exe (PID: 3388)
Script adds exclusion path to Windows Defender
- rc7.exe (PID: 3388)
Checks for external IP
- rc7.exe (PID: 2348)
- rc7.exe (PID: 3388)
Application launched itself
- rc7.exe (PID: 2348)
Executable content was dropped or overwritten
- rc7.exe (PID: 3388)
Starts CMD.EXE for commands execution
- crack.exe (PID: 1548)
Script disables Windows Defender's IPS
- rc7.exe (PID: 3388)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 3276)
Script disables Windows Defender's real-time protection
- rc7.exe (PID: 3388)
INFO
Modifies the phishing filter of IE
- iexplore.exe (PID: 1384)
Application launched itself
- iexplore.exe (PID: 1384)
- msedge.exe (PID: 3960)
Checks supported languages
- rc7.exe (PID: 2348)
- rc7.exe (PID: 3388)
- crack.exe (PID: 1548)
- Loader.exe (PID: 3468)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2176)
The process uses the downloaded file
- WinRAR.exe (PID: 2176)
- msedge.exe (PID: 3956)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2176)
Manual execution by a user
- msedge.exe (PID: 3960)
- rc7.exe (PID: 2348)
- crack.exe (PID: 1548)
- Loader.exe (PID: 3468)
Reads the computer name
- rc7.exe (PID: 2348)
- rc7.exe (PID: 3388)
Reads Environment values
- rc7.exe (PID: 2348)
- rc7.exe (PID: 3388)
Reads the machine GUID from the registry
- rc7.exe (PID: 2348)
- rc7.exe (PID: 3388)
Reads the software policy settings
- rc7.exe (PID: 2348)
- rc7.exe (PID: 3388)
Creates files in the program directory
- rc7.exe (PID: 3388)
Create files in a temporary directory
- rc7.exe (PID: 3388)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
99
Monitored processes
44
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 448 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3976 --field-trial-handle=1376,i,12586254343239488640,14237698979926813960,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 532 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=17 --mojo-platform-channel-handle=3368 --field-trial-handle=1376,i,12586254343239488640,14237698979926813960,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 584 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --mojo-platform-channel-handle=4420 --field-trial-handle=1376,i,12586254343239488640,14237698979926813960,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 664 | "wmic.exe" csproduct get uuid | C:\Windows\System32\wbem\WMIC.exe | — | rc7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 908 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4716 --field-trial-handle=1376,i,12586254343239488640,14237698979926813960,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 908 | "attrib.exe" +h +s "C:\Users\admin\Desktop\RC7\rc7.exe" | C:\Windows\System32\attrib.exe | — | rc7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 952 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4204 --field-trial-handle=1376,i,12586254343239488640,14237698979926813960,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1216 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3580 --field-trial-handle=1376,i,12586254343239488640,14237698979926813960,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2192 --field-trial-handle=1376,i,12586254343239488640,14237698979926813960,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1384 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://download2261.mediafire.com/hoqfnel9n7iggbSU0m6HRV3vNMlnwSjyCn81_p00HLwpkw2X75JR5z52o4x98GtMQkXpPY0Mx3N8q_qNHja-x_4clTIUgsb4k7rsBomuZONkR1VTKmCxxiNc41z3Z4pzull1K4MN9HBGwFG0kh2ZecO5dtHKJiLIk490ZYi3QrvslFU/nzfujcxwop05pzg/RC7.rar" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
46 045
Read events
45 760
Write events
234
Delete events
51
Modification events
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31087962 | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31087962 | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
15
Suspicious files
249
Text files
116
Unknown types
248
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_BACC6CD2B29F18349081C9FD2343833B | binary | |
MD5:5F5B341BA3D4F0B1888ADC2E31D8A18B | SHA256:FBF21B4892CAFDB26C5299B644BDA99192C39A5540CD0A7CD5D7B79DB60D808C | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\72BA427A91F50409B9EAC87F2B59B951_8FD6BB79A5EEF06F3F8595CB48A9AB04 | binary | |
MD5:F94839429BCED2BBC9113268CCD1A47C | SHA256:FF31CA80A12455C9AB6BB6802E467964971FBE4459C364117D19C0AD18BC708D | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:FFCB6CF80096A2774243CECF7828E6E9 | SHA256:7EAD04183ACA8FD068034F72F0D2C3E4D9837ECF327C72F7F778818FE9AB28D5 | |||
| 1384 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFB46707B08CBA5AE8.TMP | binary | |
MD5:7C8F5964669AB8D23A3EDB3D5574A8A7 | SHA256:2DE56F586C6E7E6A33954117C30F21097344F3186288C06E3DA58AFAE34B8B9D | |||
| 1384 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{16F3FD6B-C94E-11EE-AE0A-12A9866C77DE}.dat | binary | |
MD5:C35EE407E81F5ECF9B34FF2B82786691 | SHA256:3C447F3AA5BB655BBEAB8FFD51E7D023C0D5C905809F9B9EAB2BD9FF0C63B4ED | |||
| 3960 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF18c128.TMP | — | |
MD5:— | SHA256:— | |||
| 3960 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_BACC6CD2B29F18349081C9FD2343833B | binary | |
MD5:BDF77FD047CB0869153F790DA9445A20 | SHA256:AA1AA726E3EAE19BF56F8207AC71E885284928950F0308B1B9F8D8541FC0689F | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\72BA427A91F50409B9EAC87F2B59B951_8FD6BB79A5EEF06F3F8595CB48A9AB04 | binary | |
MD5:8E200DC9D9B773FFB6E6F6CFDD7CAF27 | SHA256:C150AA2B6479AF6EA3B8904E8F9944B8FD58E961986109EA53DA37E2DC2751B1 | |||
| 1384 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:C46F74CCDF3CD21ED3DAC5E0C403AF23 | SHA256:424A60C6EDDC3619D9B087581A428C78D5D9271DCFD64421D5231119A26F258C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
151
DNS requests
196
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3916 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?545e1839169dd0e6 | unknown | — | — | unknown |
3916 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a08f35fbea17b647 | unknown | — | — | unknown |
3916 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEBN9U5yqfDGppDNwGWiEeo0%3D | unknown | binary | 2.18 Kb | unknown |
3916 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQh80WaEMqmyEvaHjlisSfVM4p8SAQUF9nWJSdn%2BTHCSUPZMDZEjGypT%2BsCED%2B0KeRQ8NP60VP53TIby3A%3D | unknown | binary | 471 b | unknown |
1384 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?76ad697231f9b13b | unknown | — | — | unknown |
1384 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4ad9b1827f1f75f1 | unknown | — | — | unknown |
1384 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b23edf5cfbe16fd7 | unknown | — | — | unknown |
2184 | msedge.exe | GET | 302 | 104.19.215.37:80 | http://otnolatrnup.com/hideref.engine?d=https%3A%2F%2Fworeppercomming.com%2F90c1a7c4-9526-4fe6-befc-18062e96619e%3Fcampaignname%3D2_OperaGX%26placementname%3D2_OperaGX_DE_Win_WL%26bid%3D11.5%26totalcpv%3D0.0115%26channel%3DFile%2BHosting%2B%2526%2BSharing%26subchannel%3DFile%2BHosting%2B%2526%2BSharing%26medianame%3D2_OperaGX_WW_5.22%26keywords%3Donline+storage%2Cfree+storage%2Ccloud+storage%2Ccollaboration%2Cbackup+file+sharing%2Cshare+files%2Cphoto+backup%2Cphoto+sharing%2Cftp+replacement%2Ccross+platform%2Cremote+access%2Cmobile+access%2Csend+large+files%2Crecover+files%2Cfile+versioning%2Cundelete%2Cwindows%2Cpc%2Cmac%2Cos+x%2Clinux%2Ciphone%2Conline+storage%2Cfree+storage%2Ccloud+storage%2Ccollaboration%2Cbackup+file+sharing%2Cshare+files%2Cphoto+backup%2Cphoto+sharing%2Cftp+replacement%2Ccross+platform%2Cremote+access%2Cmobile+access%2Csend+large+files%2Crecover+files%2Cfile+versioning%2Cundelete%2Cwindows%2Cpc%2Cmac%2Cos+x%2Clinux%2Ciphone%26sourceid%3D101%26domainid%3D1%26cpv%3D0.0115%26s2sParam%3D75a9479f-ac6f-4cba-80a2-84127f97ba16 | unknown | — | — | unknown |
1080 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?1b8fee253118cbef | unknown | compressed | 65.2 Kb | unknown |
1384 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3916 | iexplore.exe | 199.91.155.2:443 | download2261.mediafire.com | MEDIAFIRE | US | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3916 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3916 | iexplore.exe | 104.18.38.233:80 | ocsp.usertrust.com | CLOUDFLARENET | — | shared |
1384 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
1384 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1384 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1080 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download2261.mediafire.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ntp.msn.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
2184 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
2184 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
2184 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
2184 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
2348 | rc7.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2348 | rc7.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
2348 | rc7.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
3388 | rc7.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
3388 | rc7.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |