| download: | index.html |
| Full analysis: | https://app.any.run/tasks/9fca1662-ce73-48ce-92cb-51fec2b6a8c9 |
| Verdict: | Malicious activity |
| Analysis date: | November 15, 2018, 01:35:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines, with CRLF, CR, LF line terminators |
| MD5: | B0B736B53314453386BC2D774ADE85FF |
| SHA1: | 3B933131B3F1BAC11B0FC97EA363F87F5BCAC543 |
| SHA256: | 7452DE928402E79F9DD5B2036EB4EBF27FCA74C06749E3277405D2CF3EDB2AF9 |
| SSDEEP: | 3072:Vv5AIPFjkJS8eXemg5e3d7VNaW7wJz+6OyhUYlty7kUT09dcAkF3:VhAI+JXm4yQEAz+6OyhUYlty7kl4 |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Reads internet explorer settings
- iexplore.exe (PID: 896)
- iexplore.exe (PID: 2548)
Creates files in the user directory
- iexplore.exe (PID: 2548)
- iexplore.exe (PID: 896)
Application launched itself
- iexplore.exe (PID: 3848)
Changes internet zones settings
- iexplore.exe (PID: 3848)
Reads Internet Cache Settings
- iexplore.exe (PID: 896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .htm/html | | | HyperText Markup Language with DOCTYPE (80.6) |
|---|---|---|
| .html | | | HyperText Markup Language (19.3) |
EXIF
HTML
| ContentType: | text/html; charset=utf-8 |
|---|---|
| ContentStyleType: | text/css |
| ContentScriptType: | text/javascript |
| Description: | 日本最大級のポータルサイト。検索、オークション、ニュース、天気、スポーツ、メール、ショッピングなど多数のサービスを展開。あなたの生活をより豊かにする「課題解決エンジン」を目指していきます。 |
| Robots: | noodp |
| googleSiteVerification: | fsLMOiigp5fIpCDMEVodQnQC7jIY1K3UXW5QkQcBmVs |
| msapplicationNavbuttonColor: | #5780cc |
| Title: | Yahoo! JAPAN |
Total processes
34
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 896 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3848 CREDAT:203009 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2548 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3848 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
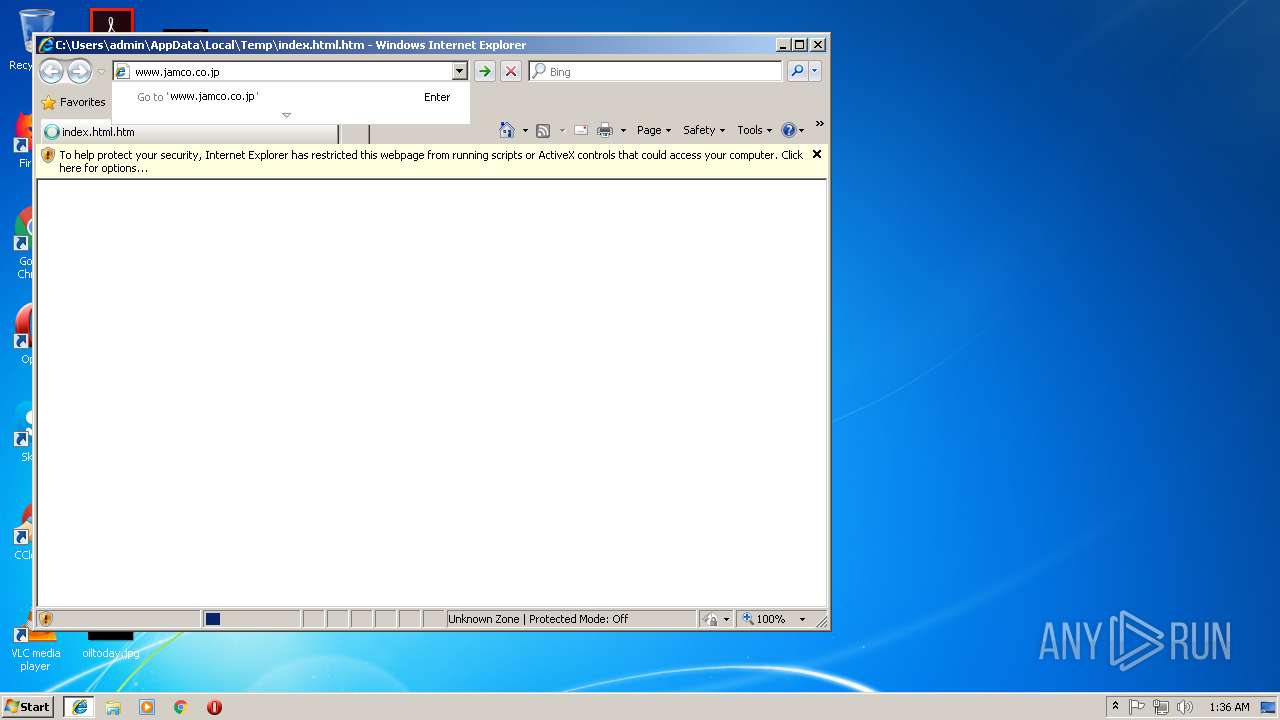
| 3848 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\index.html.htm | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
583
Read events
478
Write events
102
Delete events
3
Modification events
| (PID) Process: | (3848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {D7FDBFDD-E876-11E8-A505-5254004AAD11} |
Value: 0 | |||
| (PID) Process: | (3848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (3848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E2070B0004000F00010024001100FA02 | |||
Executable files
0
Suspicious files
1
Text files
12
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3848 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFCD19F6EE0446C373.TMP | — | |
MD5:— | SHA256:— | |||
| 896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\dnserror[1] | html | |
MD5:68E03ED57EC741A4AFBBCD11FAB1BDBE | SHA256:1FF3334C3EB27033F8F37029FD72F648EDD4551FCE85FC1F5159FEAEA1439630 | |||
| 2548 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\JavaDeployReg.log | text | |
MD5:— | SHA256:— | |||
| 896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\d1di2lzuh97fh2_cloudfront_net[1].xml | xml | |
MD5:— | SHA256:— | |||
| 3848 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\StructuredQuery.log | text | |
MD5:— | SHA256:— | |||
| 3848 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{D7FDBFDE-E876-11E8-A505-5254004AAD11}.dat | binary | |
MD5:— | SHA256:— | |||
| 3848 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012018111520181116\index.dat | dat | |
MD5:— | SHA256:— | |||
| 896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\MSHist012018111520181116\index.dat | dat | |
MD5:— | SHA256:— | |||
| 896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PP6KS563\errorPageStrings[1] | text | |
MD5:1A0563F7FB85A678771450B131ED66FD | SHA256:EB5678DE9D8F29CA6893D4E6CA79BD5AB4F312813820FE4997B009A2B1A1654C | |||
| 896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\BWPPCY0O\httpErrorPagesScripts[1] | text | |
MD5:E7CA76A3C9EE0564471671D500E3F0F3 | SHA256:58268CA71A28973B756A48BBD7C9DC2F6B87B62AE343E582CE067C725275B63C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
14
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
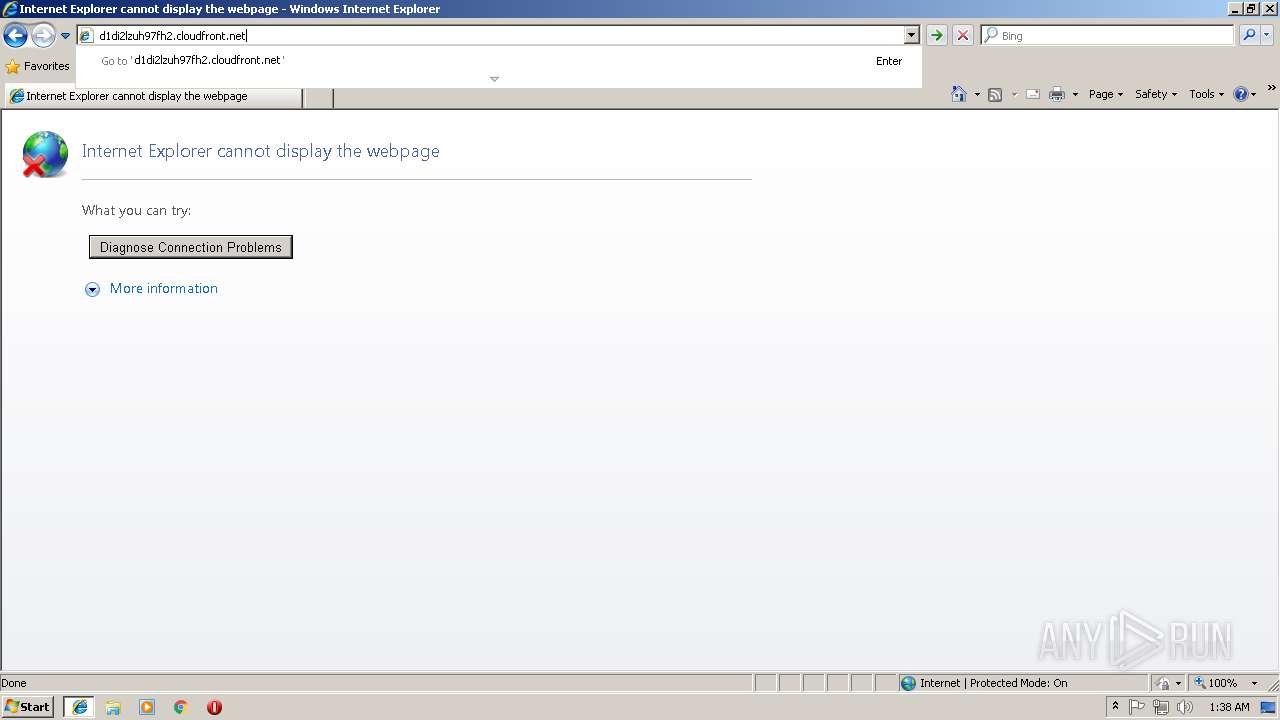
3848 | iexplore.exe | GET | 404 | 52.85.182.70:80 | http://d1di2lzuh97fh2.cloudfront.net/favicon.ico | US | xml | 282 b | whitelisted |
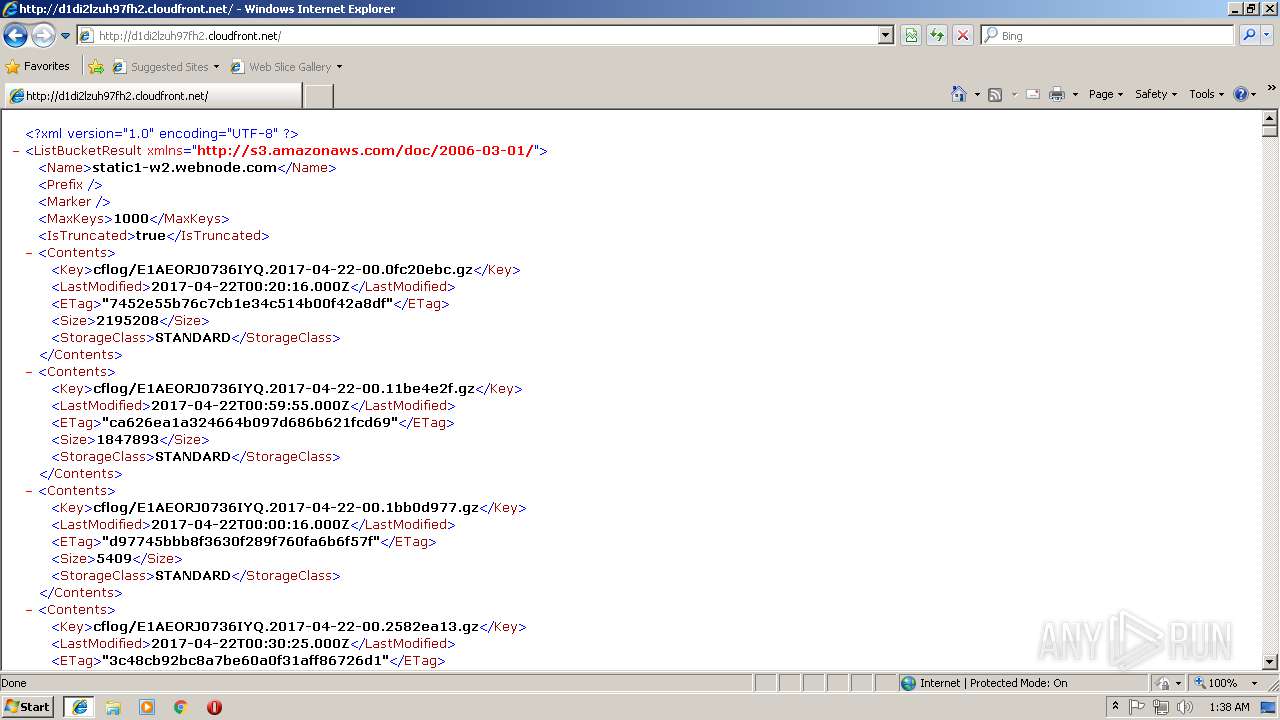
896 | iexplore.exe | GET | 200 | 52.85.182.70:80 | http://d1di2lzuh97fh2.cloudfront.net/ | US | xml | 239 Kb | whitelisted |
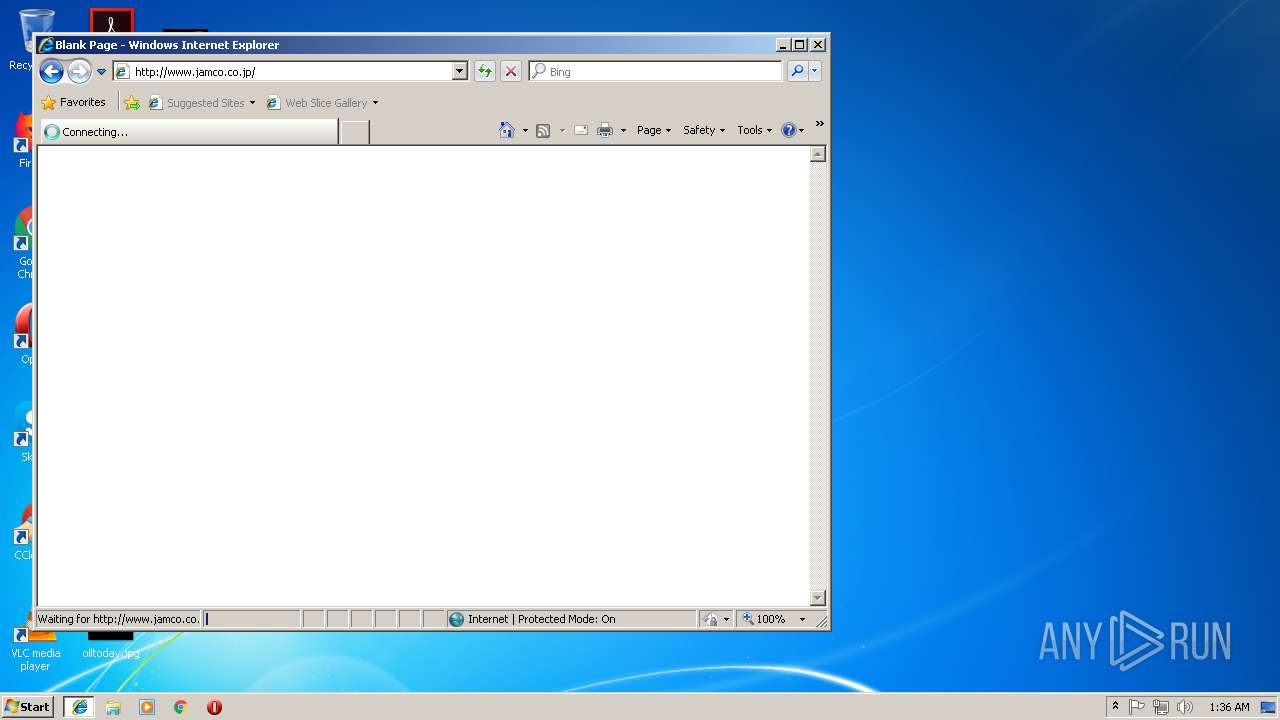
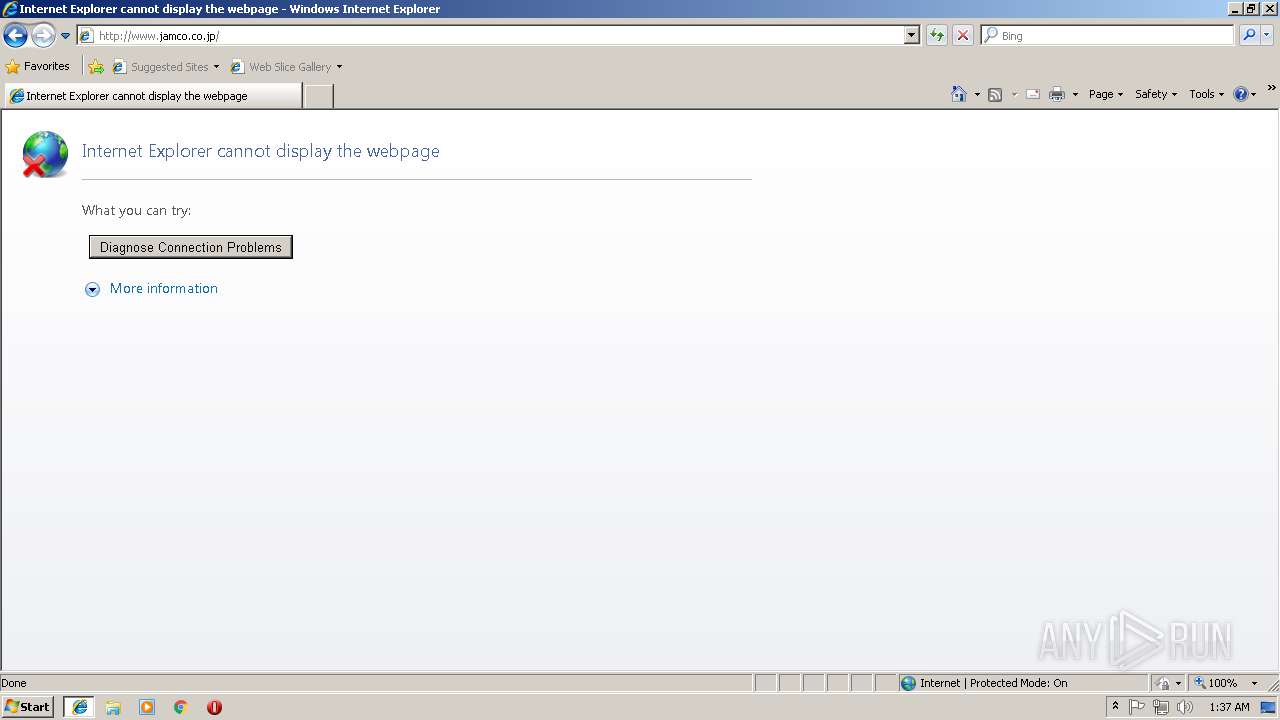
896 | iexplore.exe | GET | 301 | 54.230.202.197:80 | http://www.jamco.co.jp/ | US | html | 183 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 183.79.249.124:445 | s.yimg.jp | Yahoo Japan | JP | unknown |
3848 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
— | — | 183.79.249.124:137 | s.yimg.jp | Yahoo Japan | JP | unknown |
896 | iexplore.exe | 54.230.202.199:80 | www.jamco.co.jp | Amazon.com, Inc. | US | unknown |
3848 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
896 | iexplore.exe | 54.230.202.230:80 | www.jamco.co.jp | Amazon.com, Inc. | US | unknown |
896 | iexplore.exe | 54.230.202.197:80 | www.jamco.co.jp | Amazon.com, Inc. | US | unknown |
896 | iexplore.exe | 54.230.202.30:80 | www.jamco.co.jp | Amazon.com, Inc. | US | suspicious |
896 | iexplore.exe | 54.230.202.197:443 | www.jamco.co.jp | Amazon.com, Inc. | US | unknown |
3848 | iexplore.exe | 52.85.182.70:80 | d1di2lzuh97fh2.cloudfront.net | Amazon.com, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
s.yimg.jp |
| whitelisted |
www.bing.com |
| whitelisted |
www.jamco.co.jp |
| suspicious |
dns.msftncsi.com |
| shared |
d1di2lzuh97fh2.cloudfront.net |
| whitelisted |