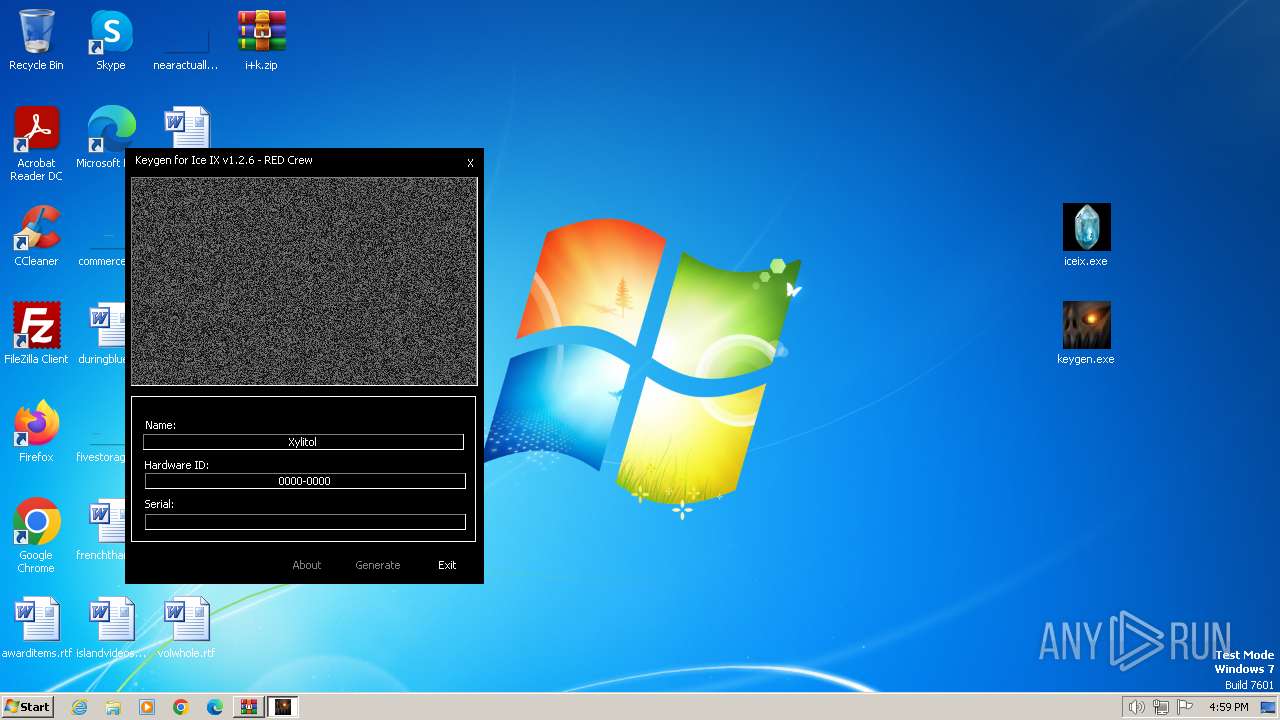
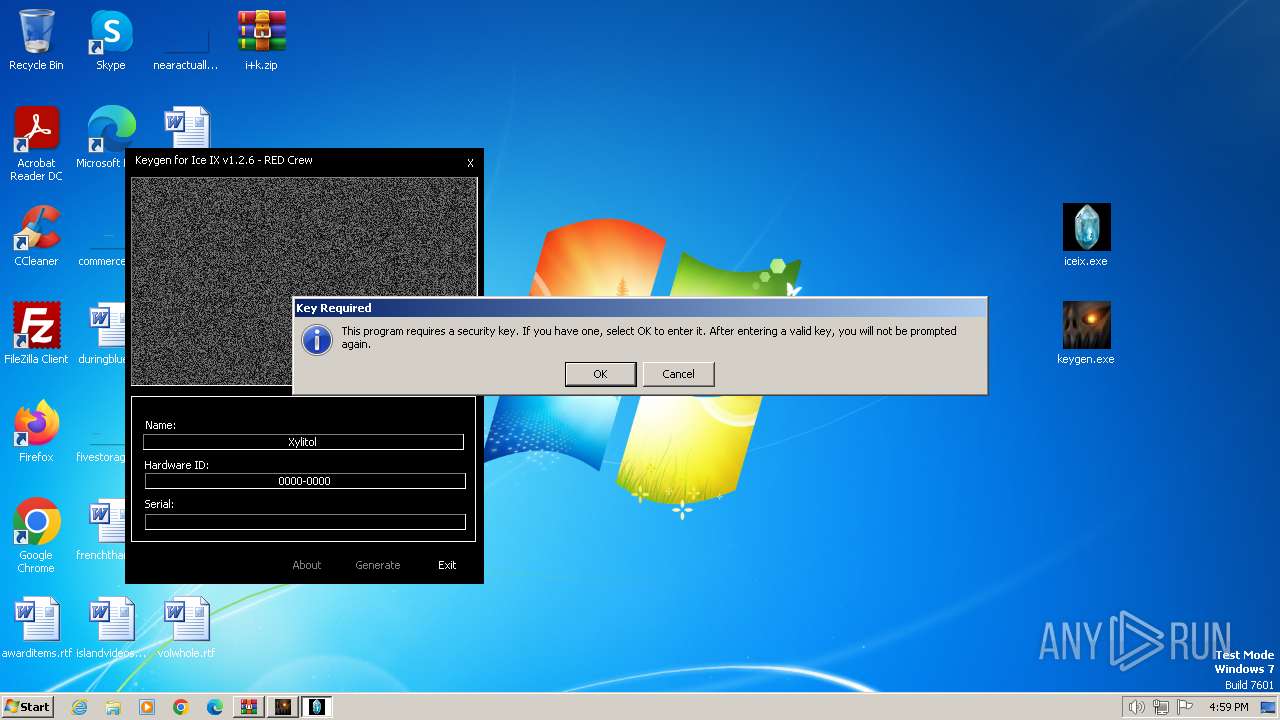
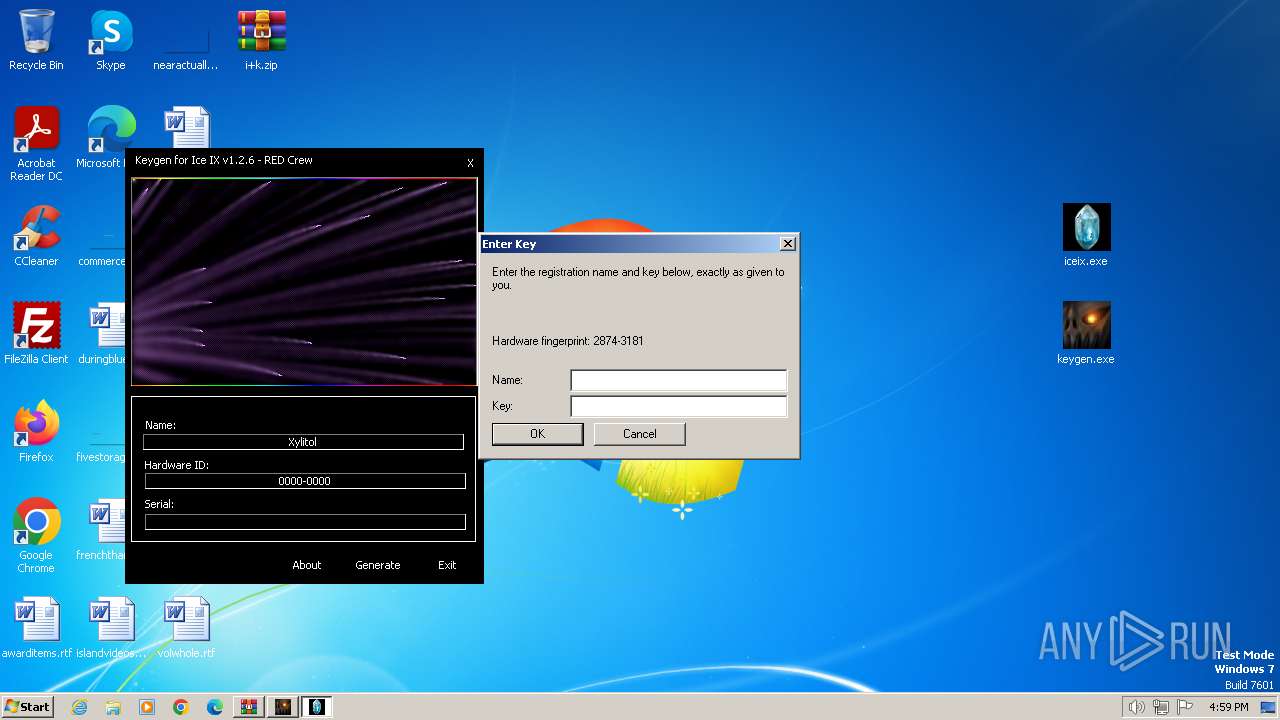
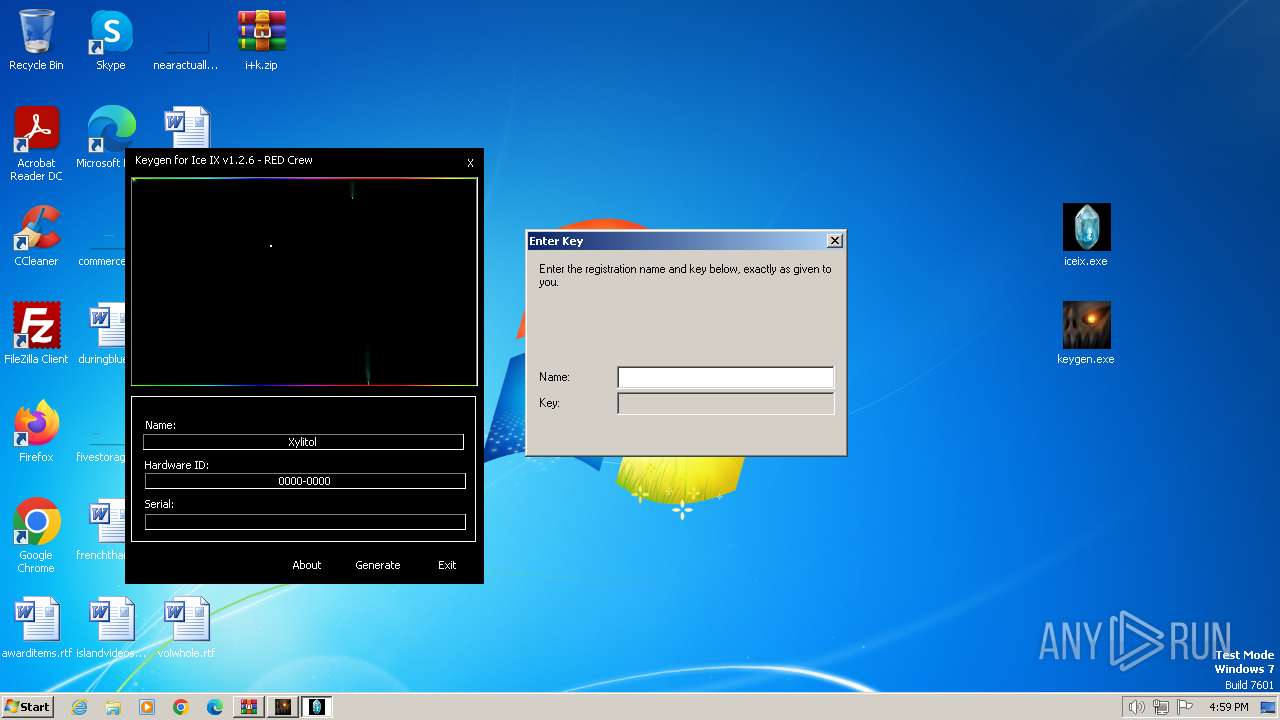
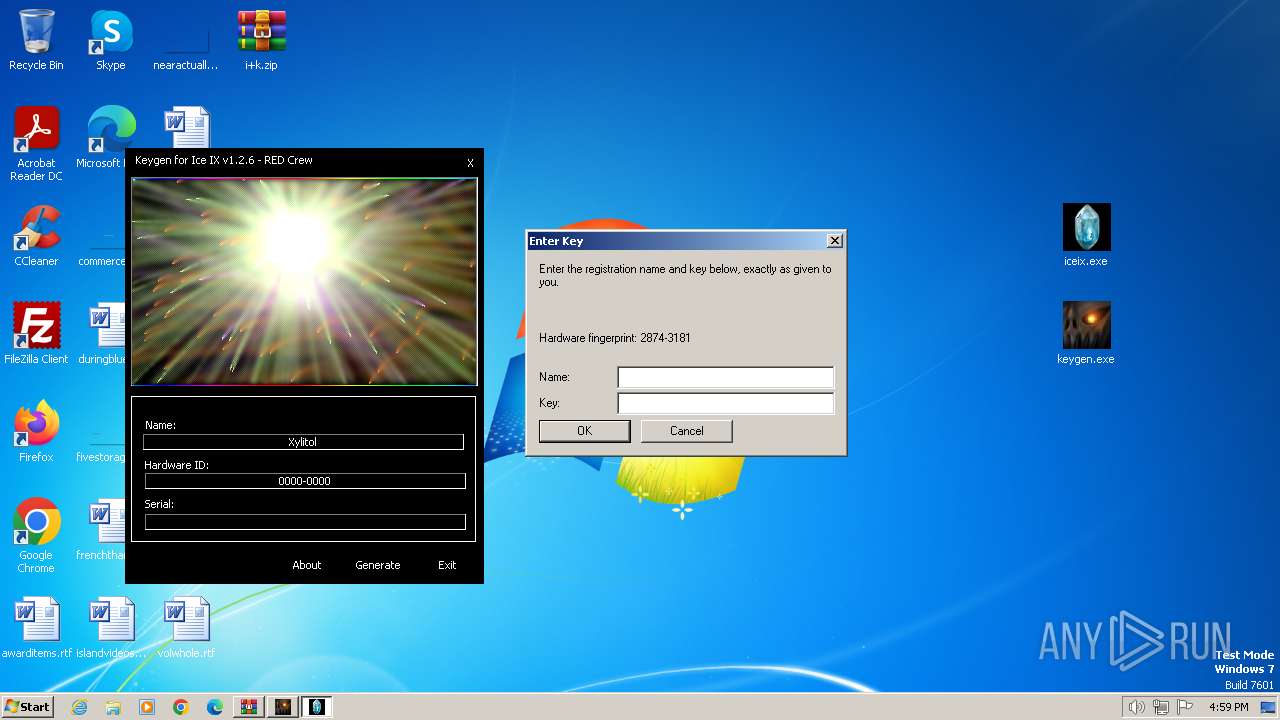
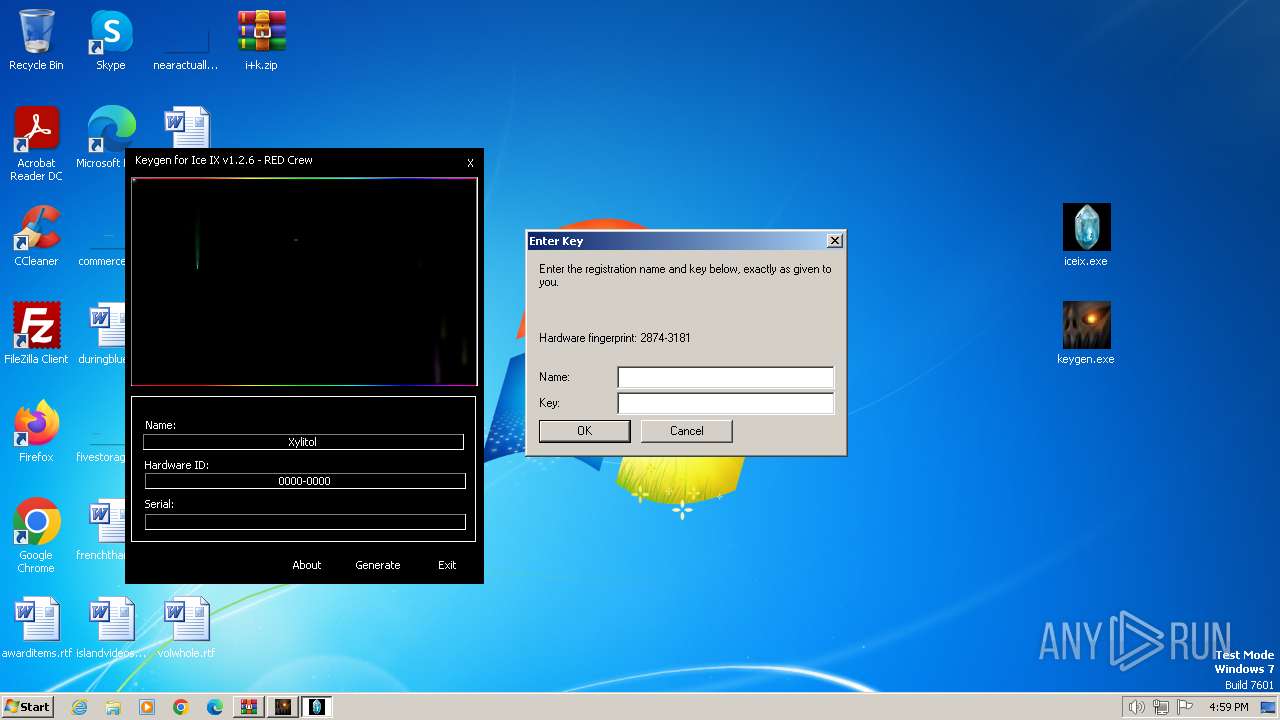
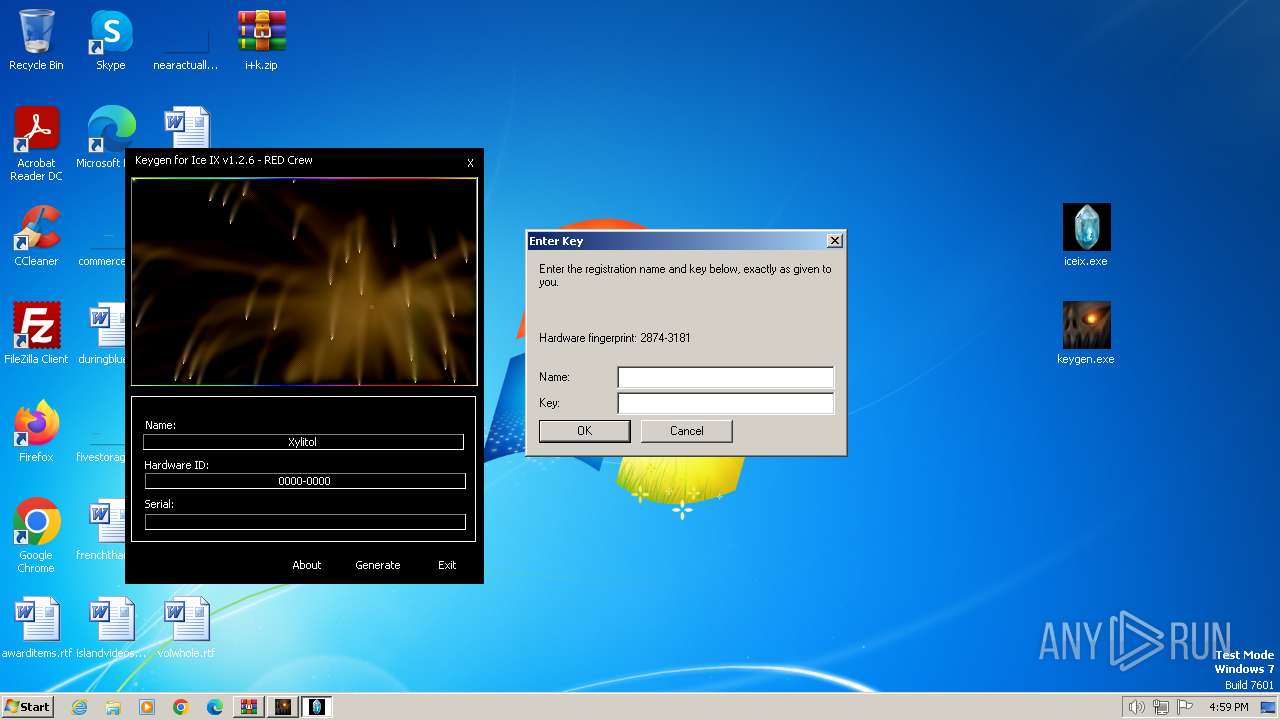
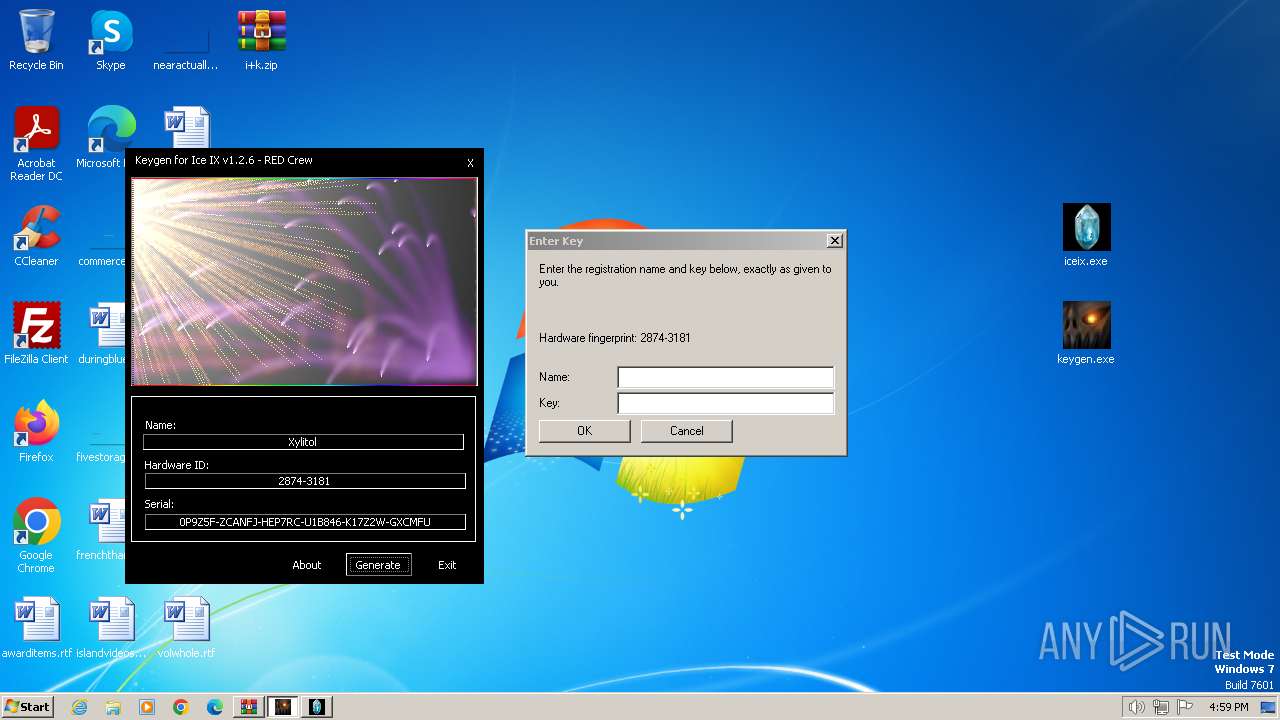
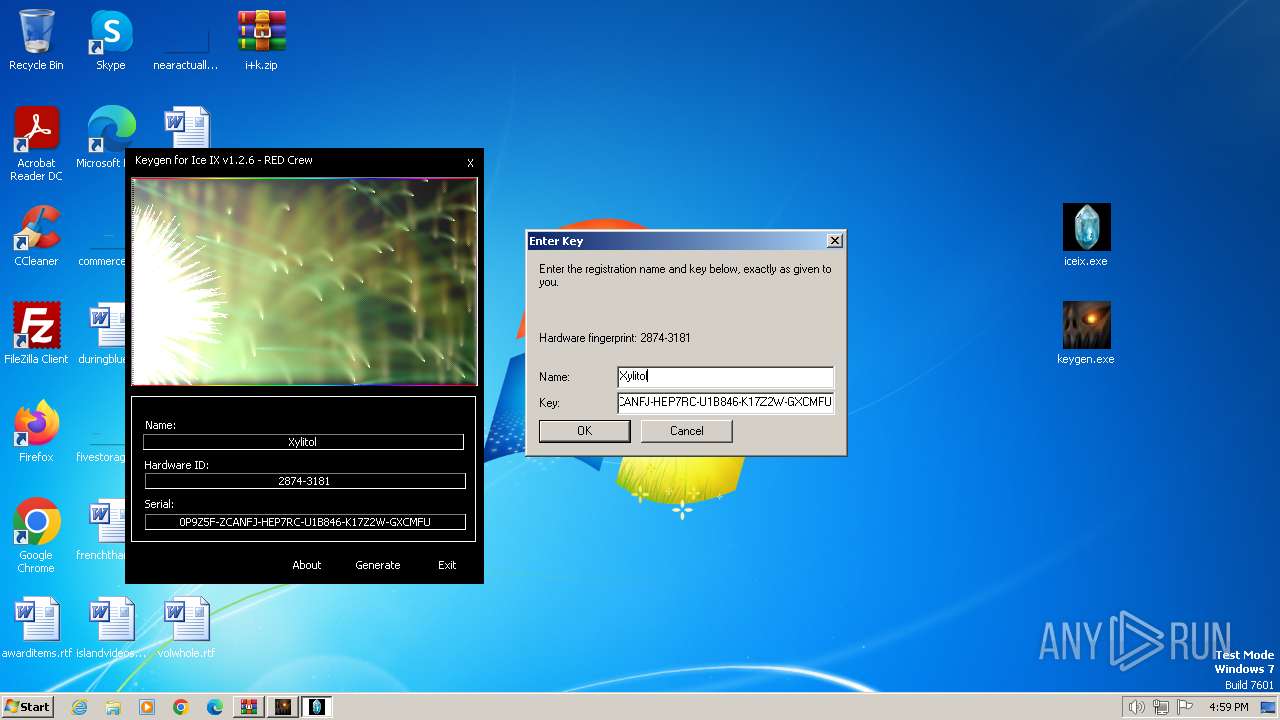
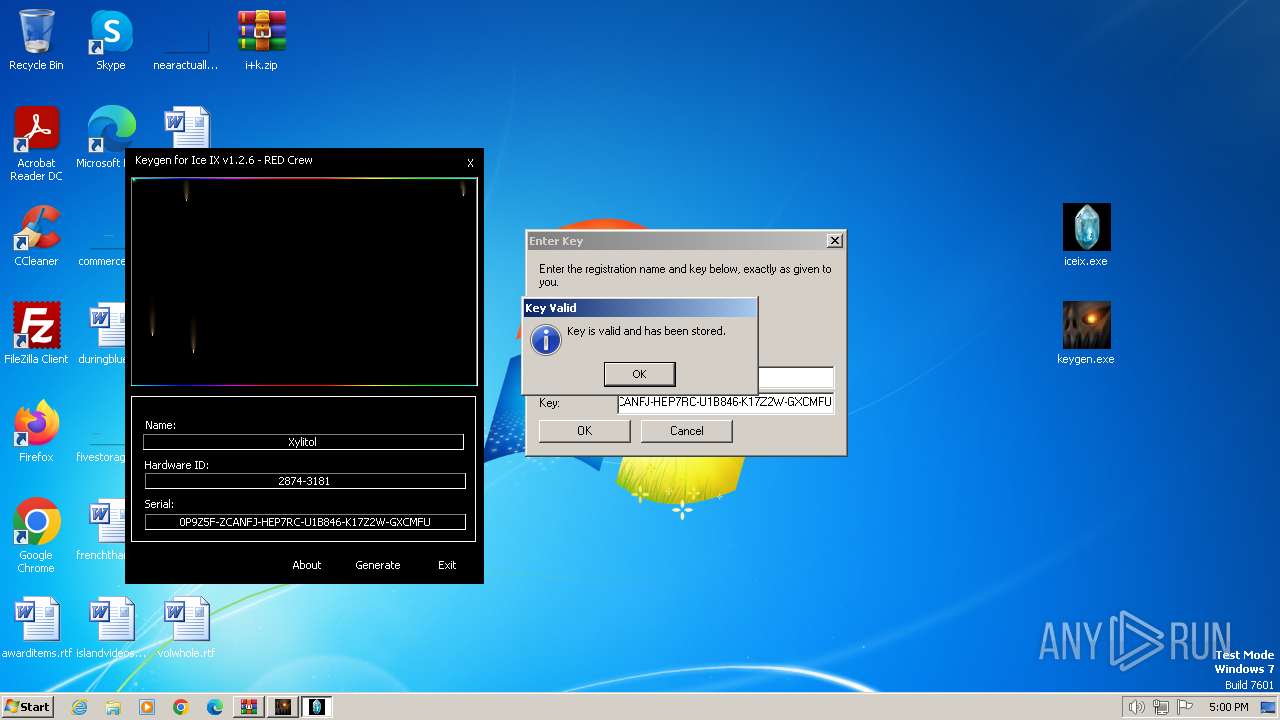
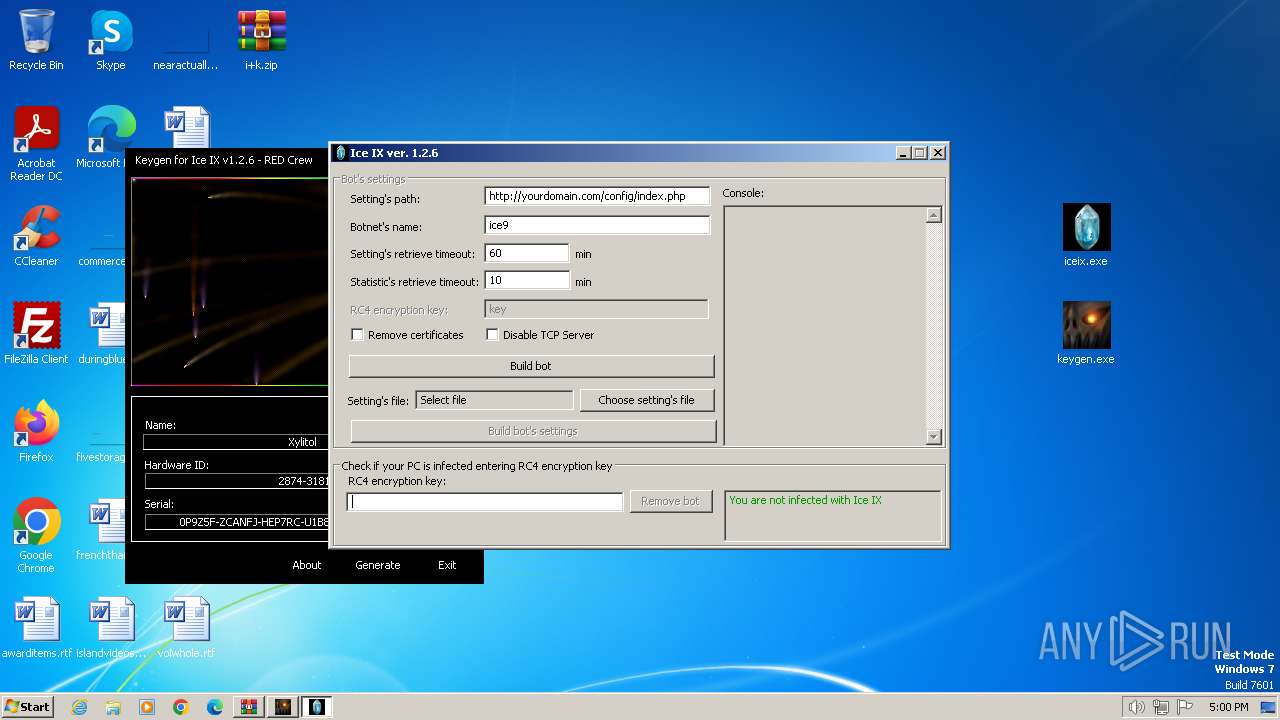
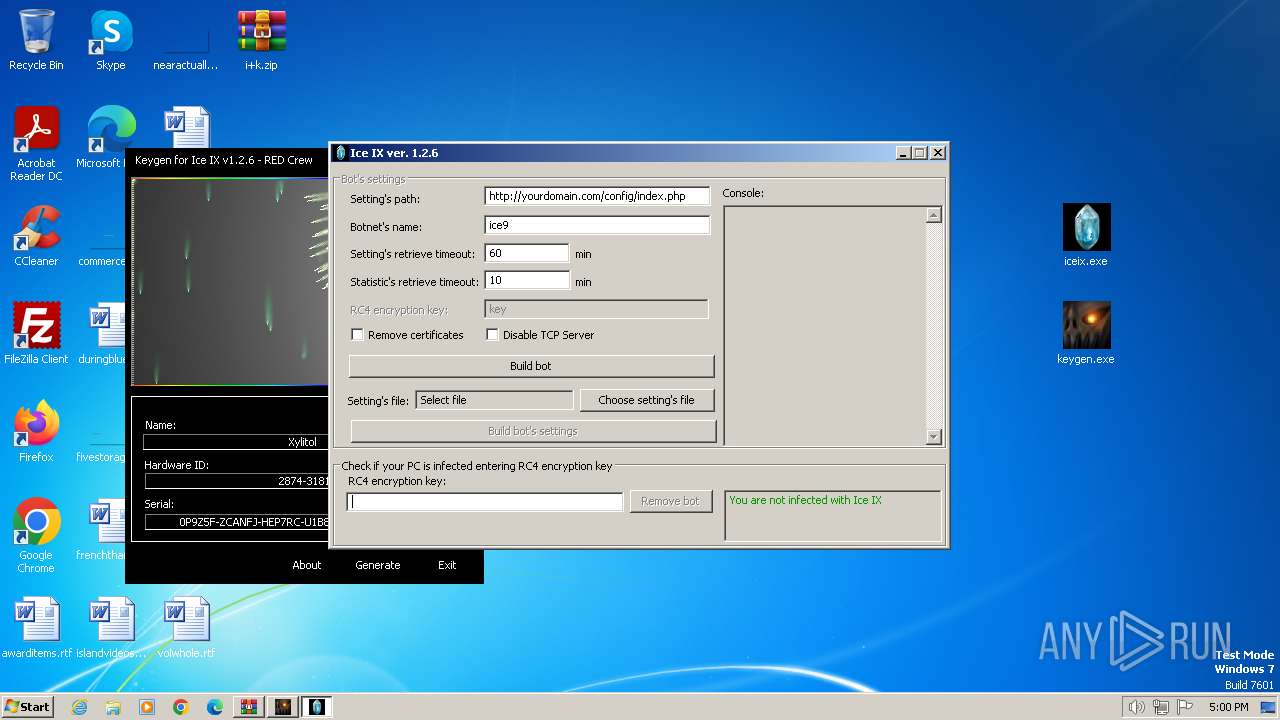
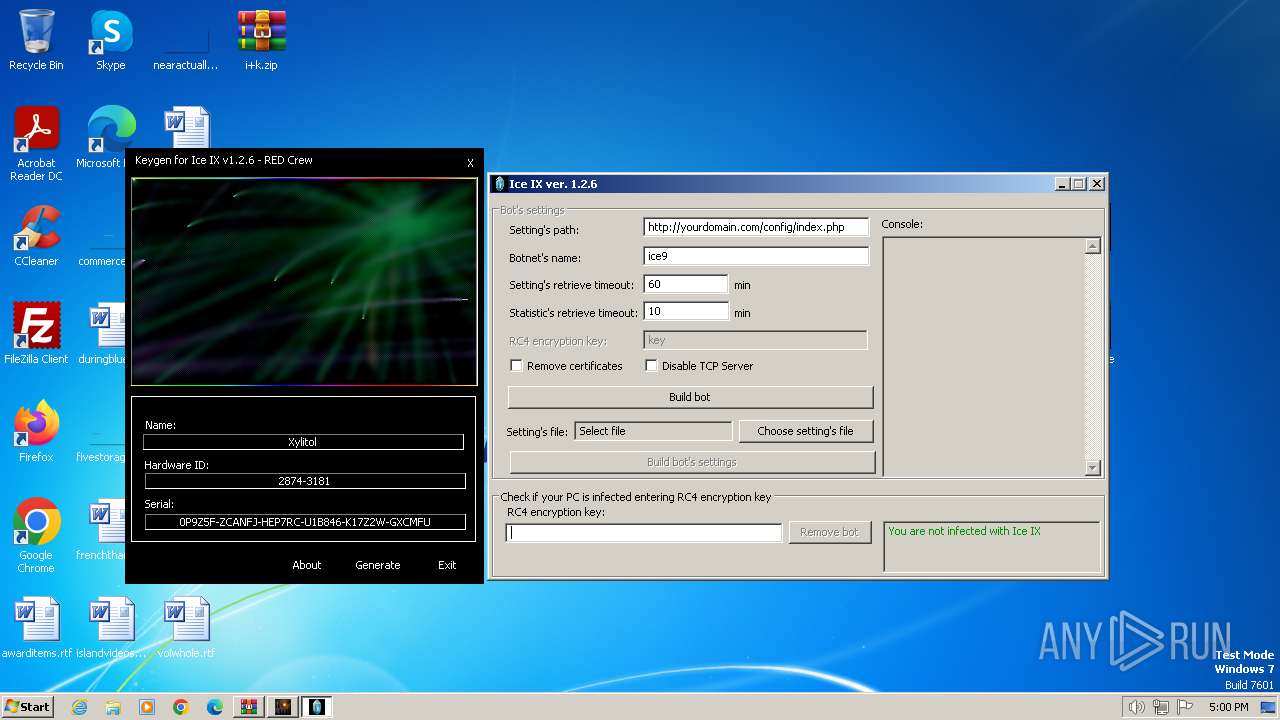
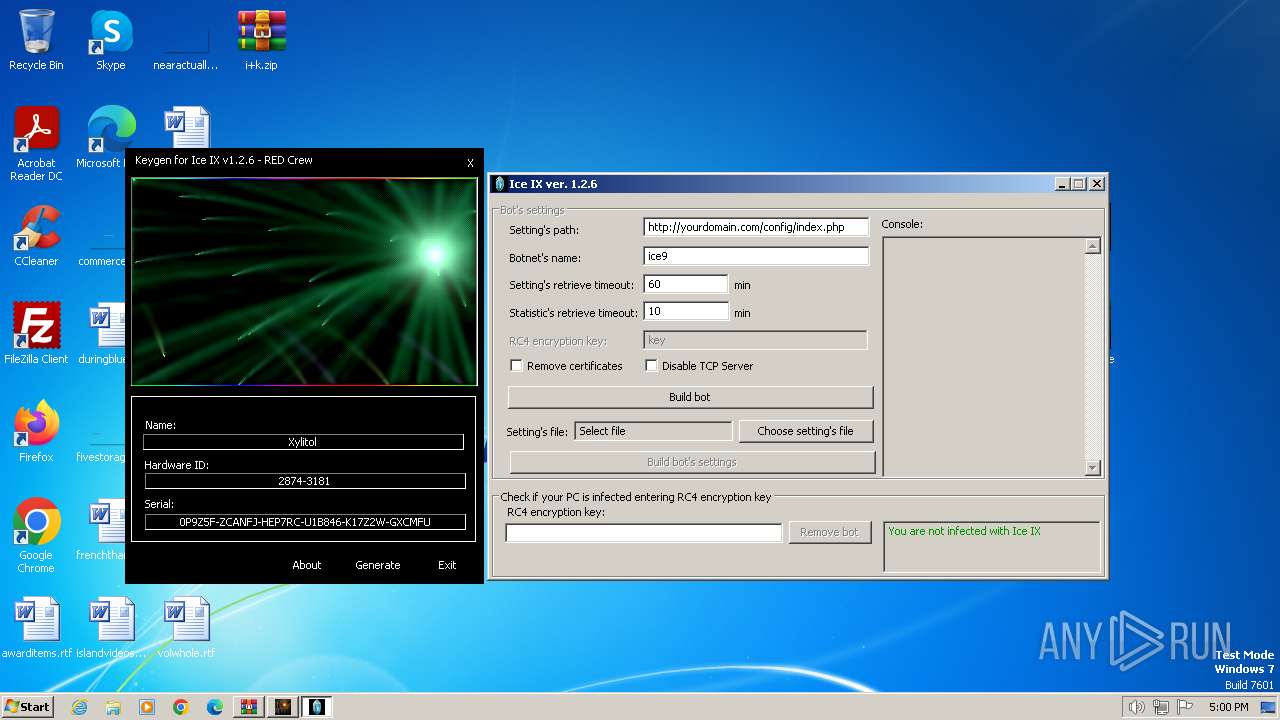
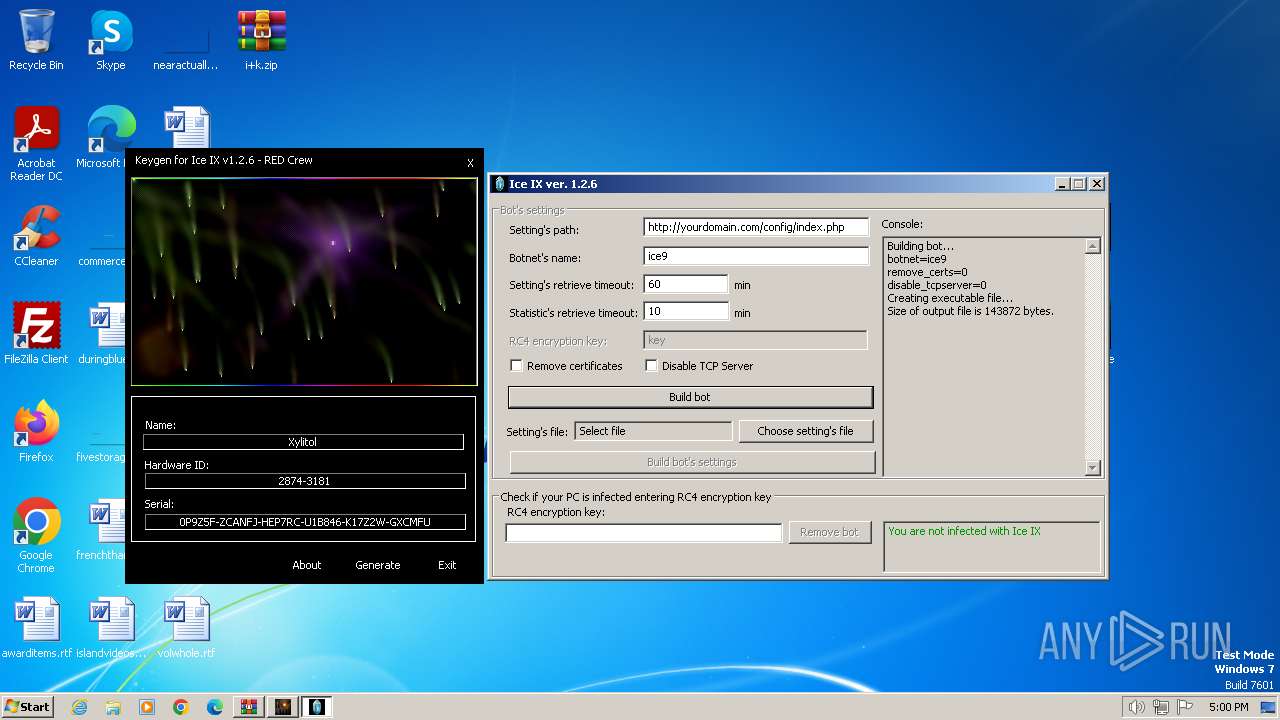
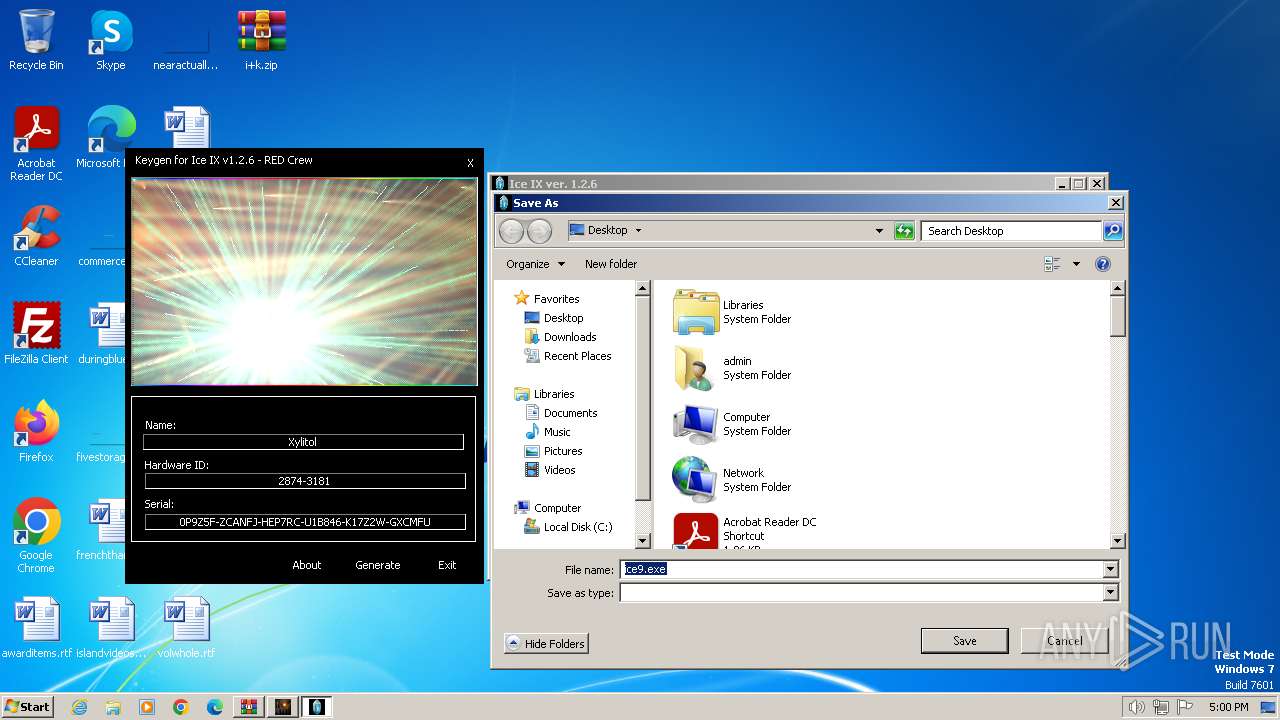
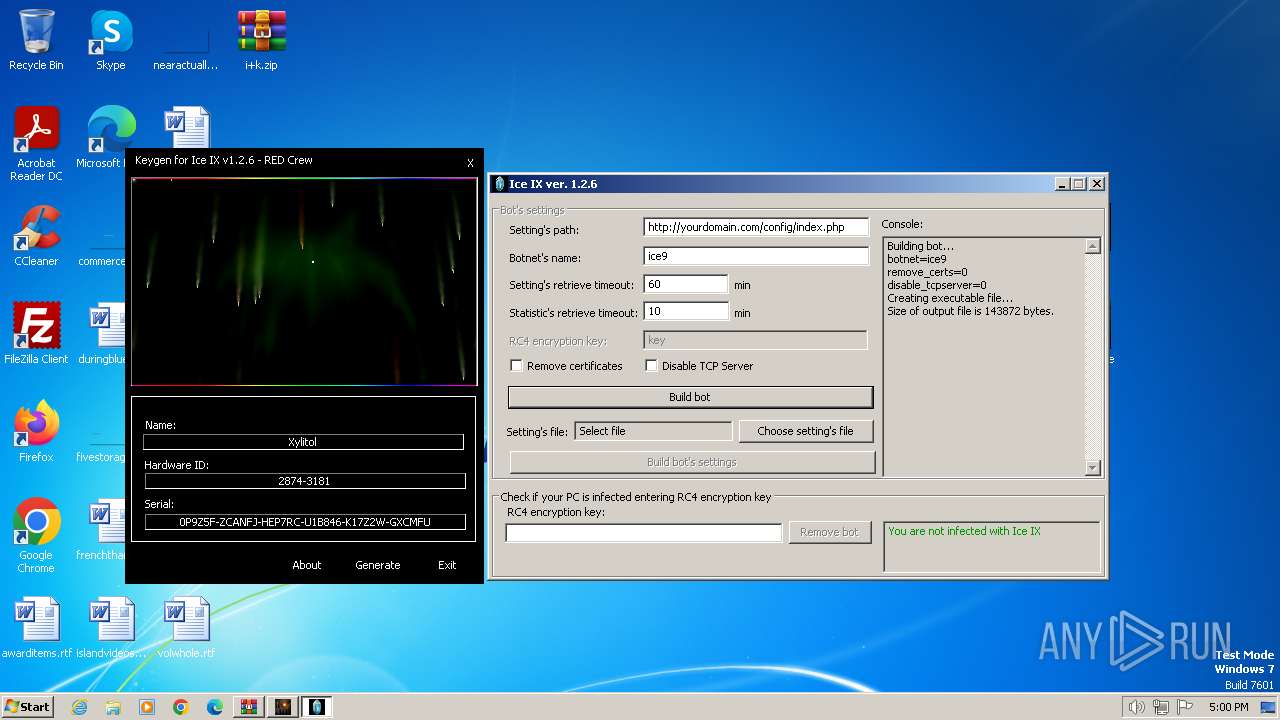
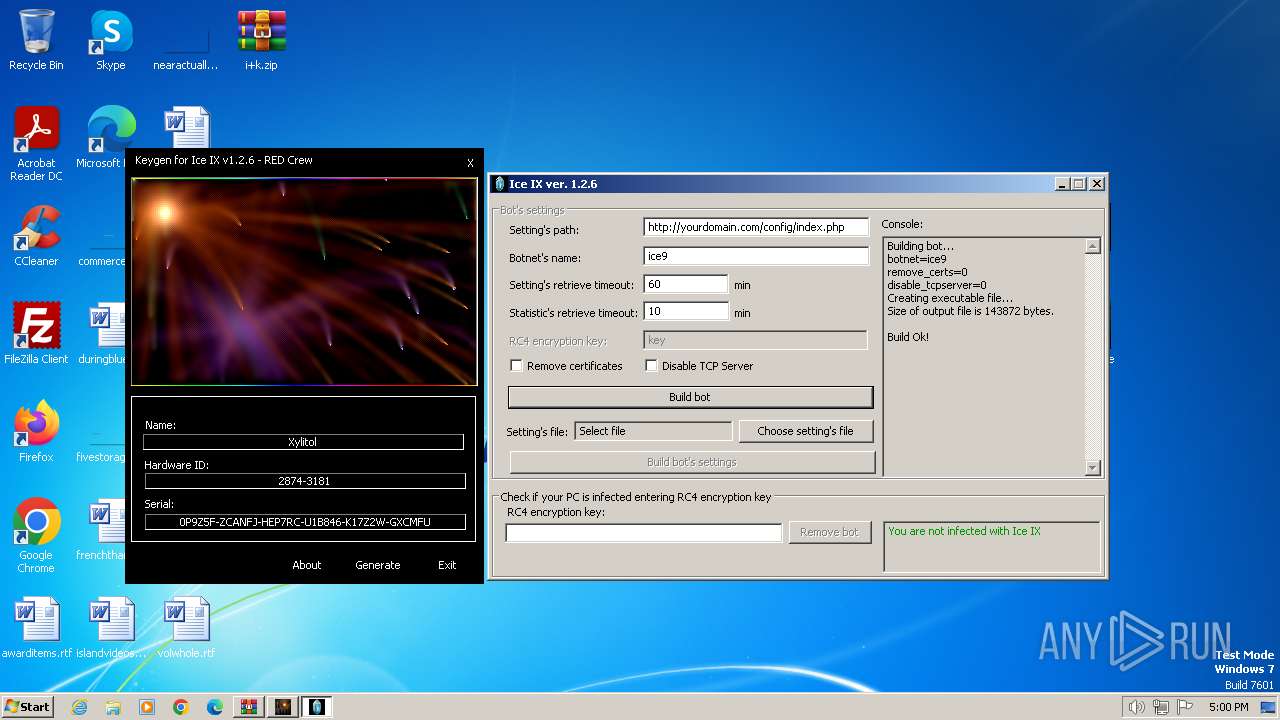
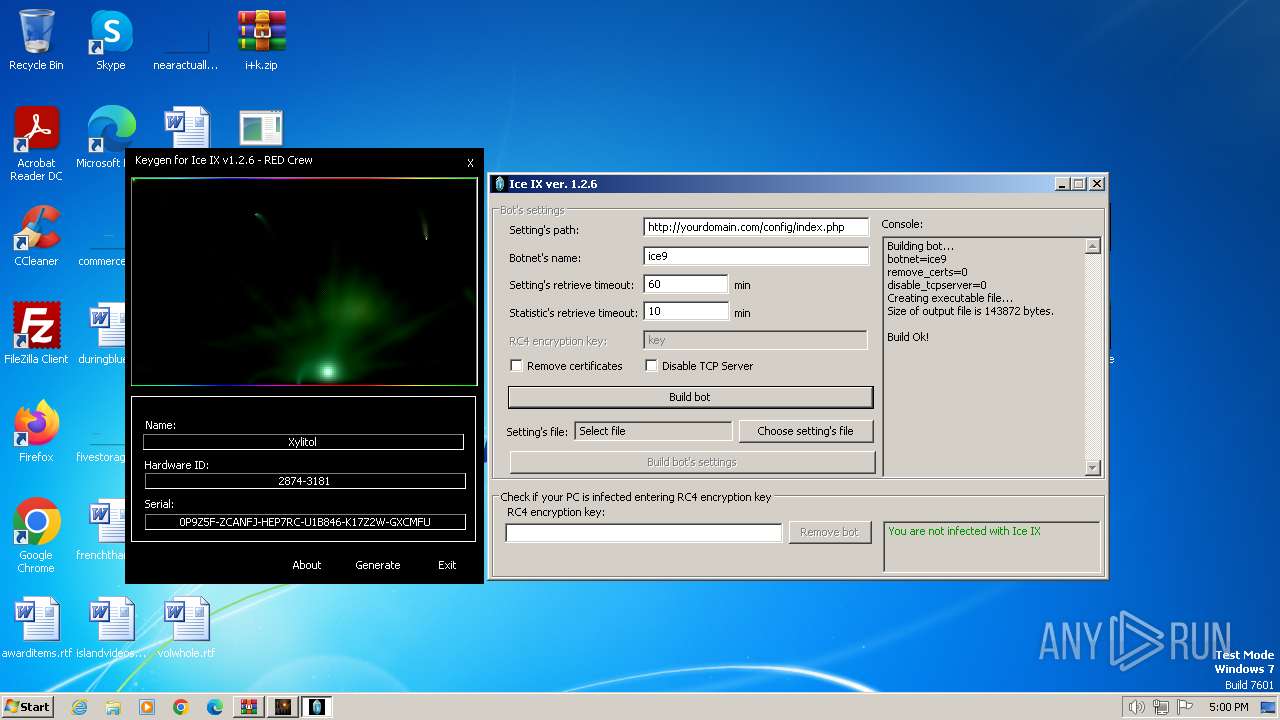
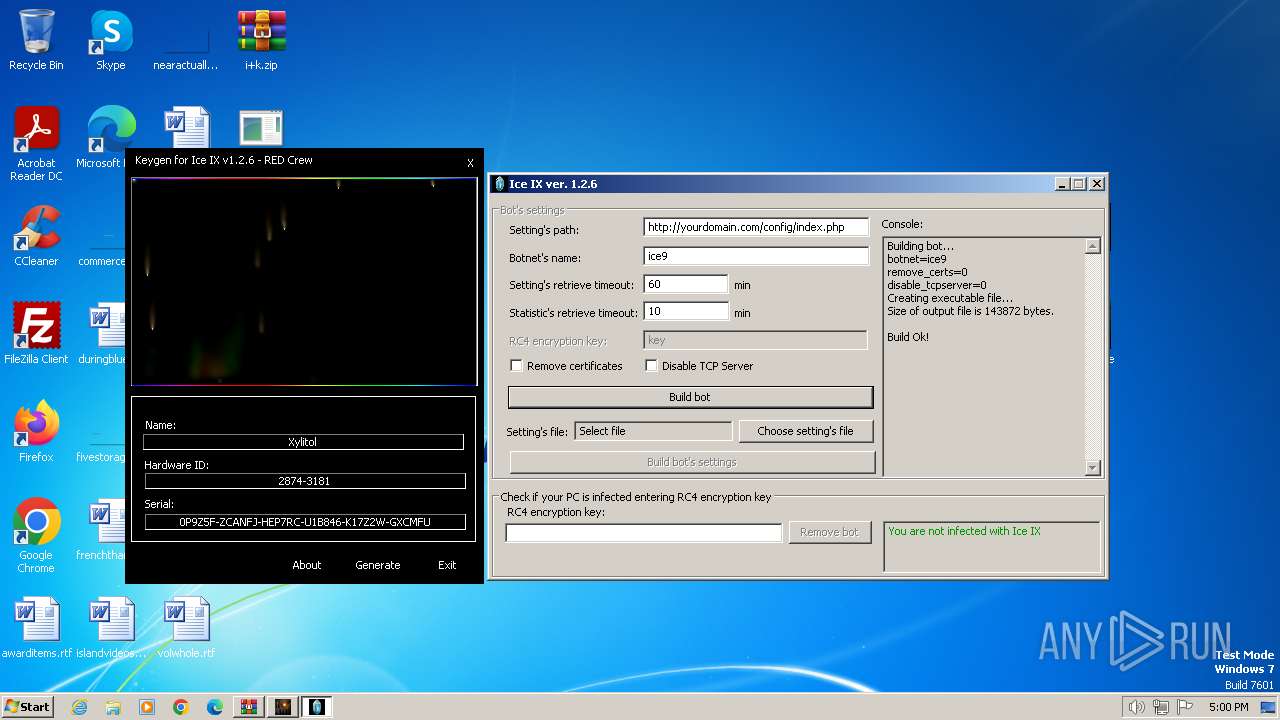
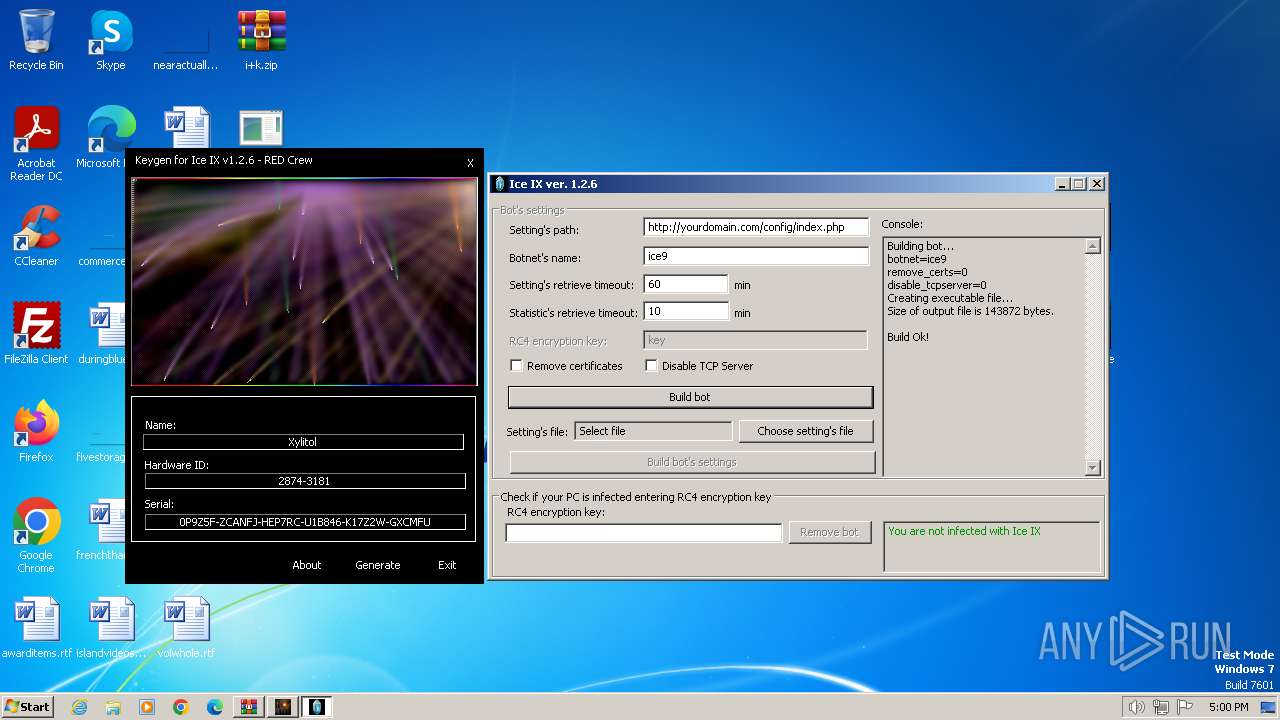
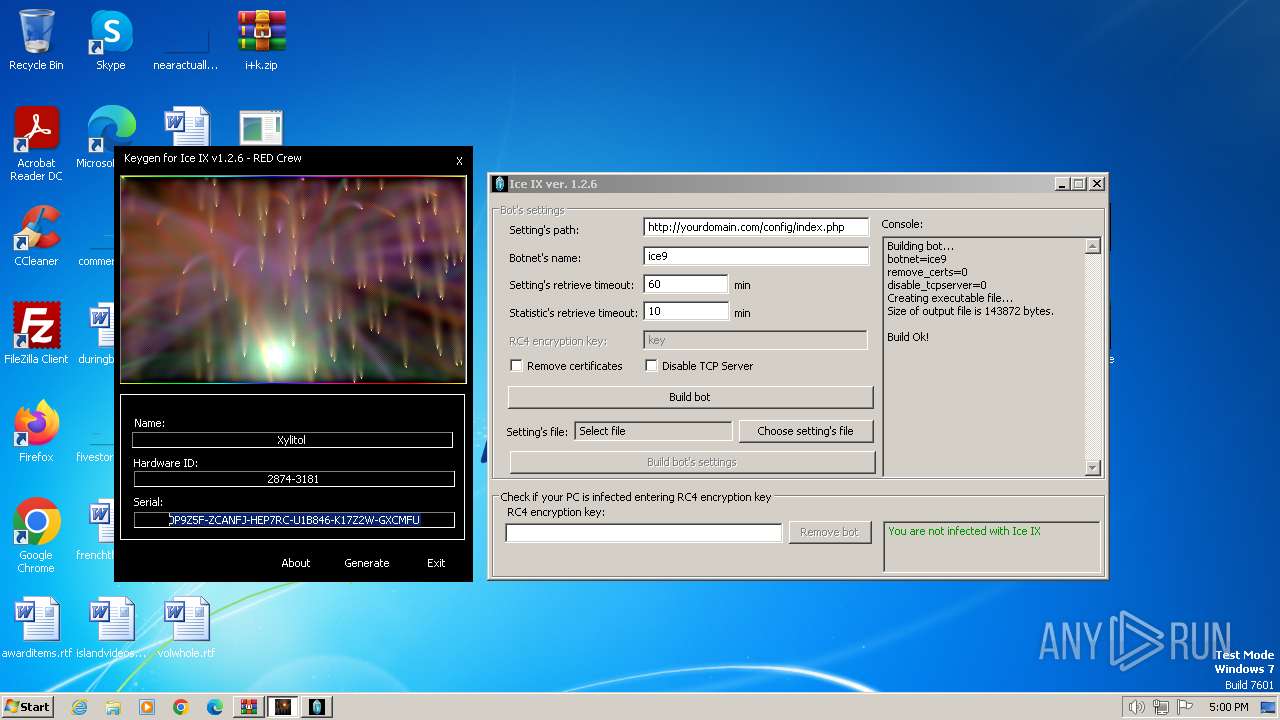
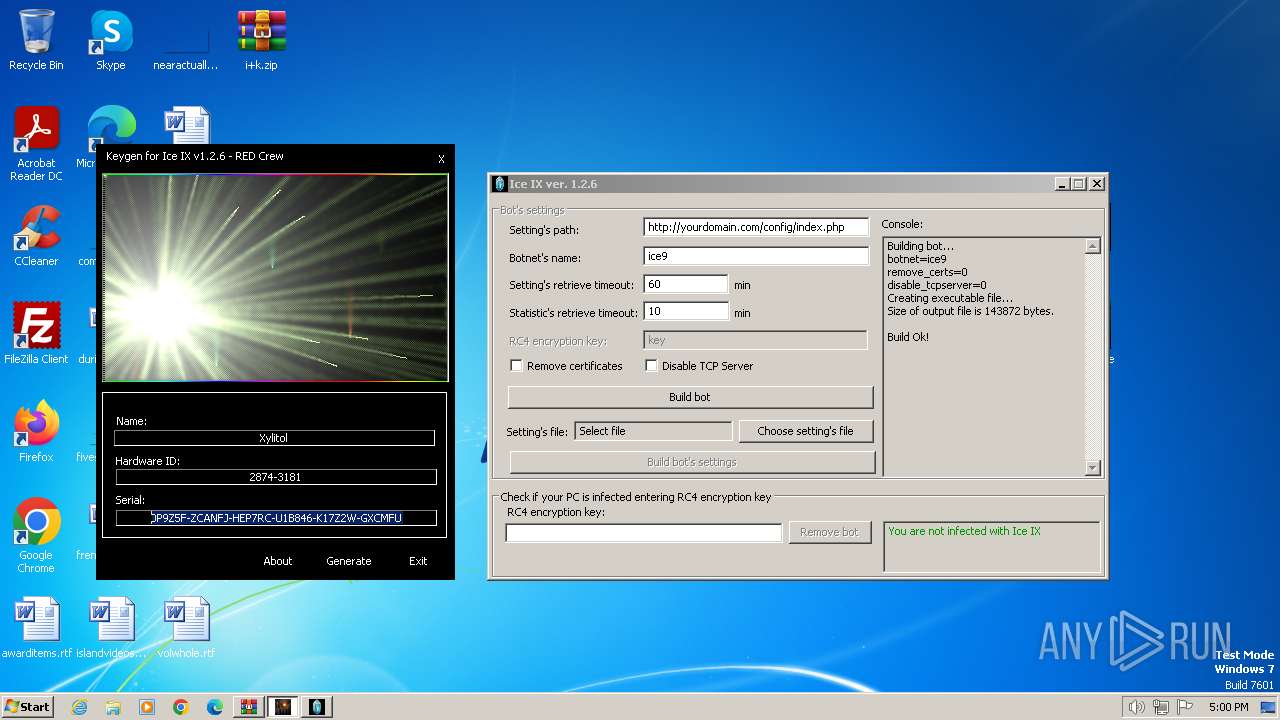
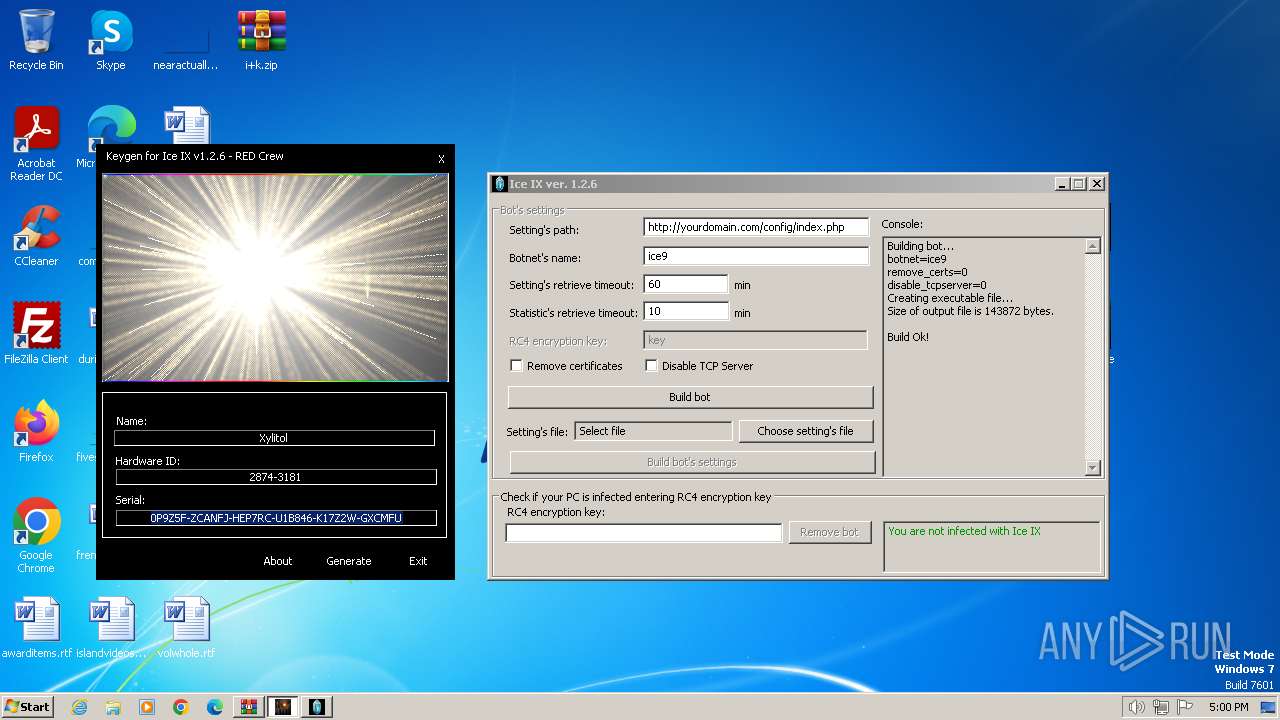
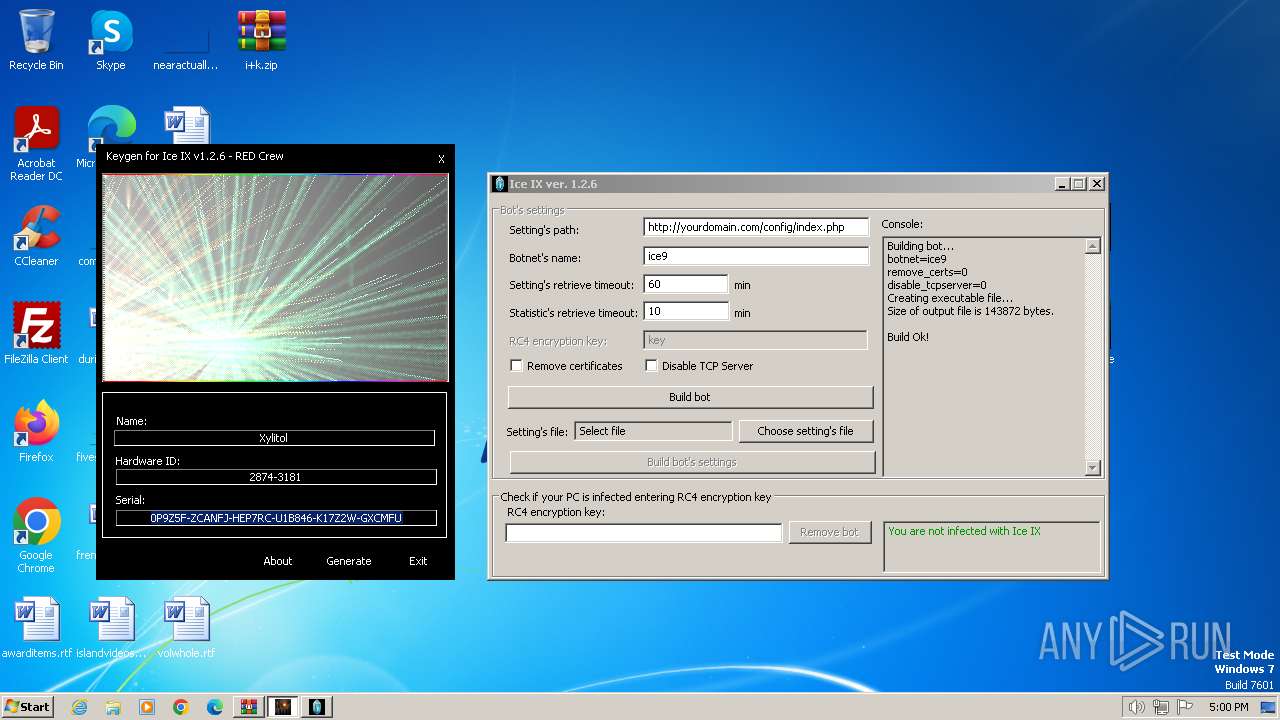
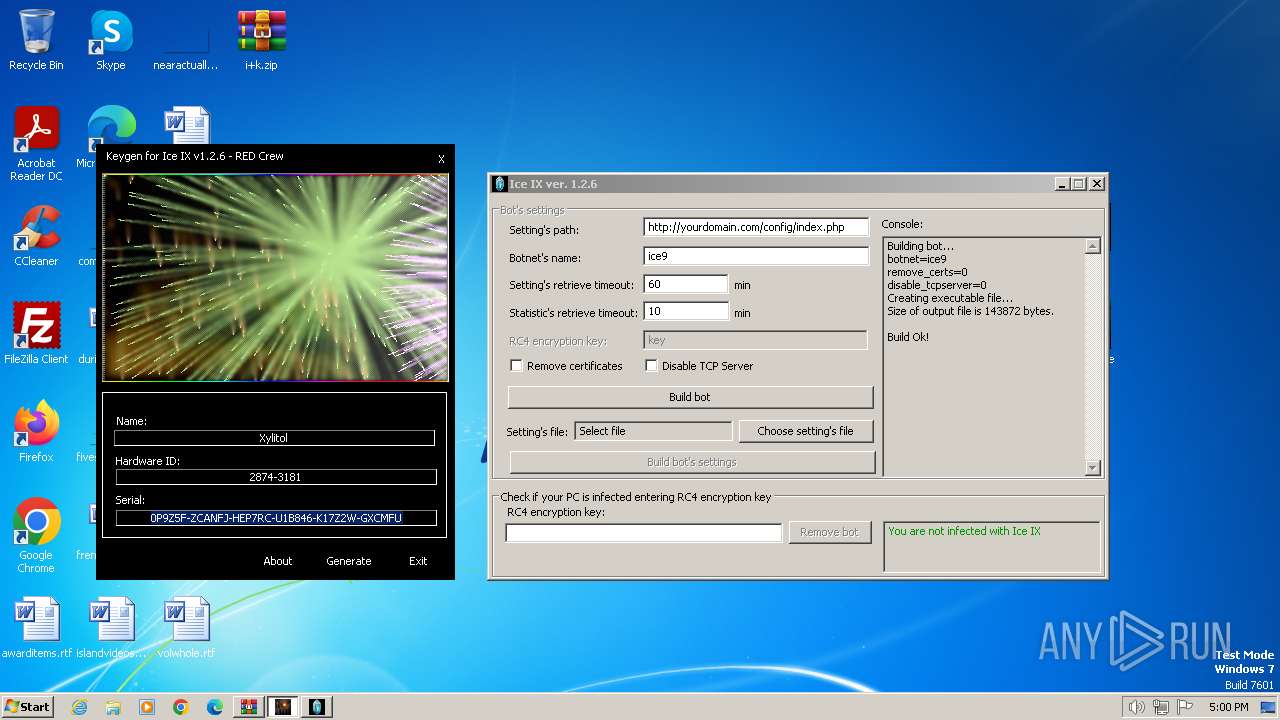
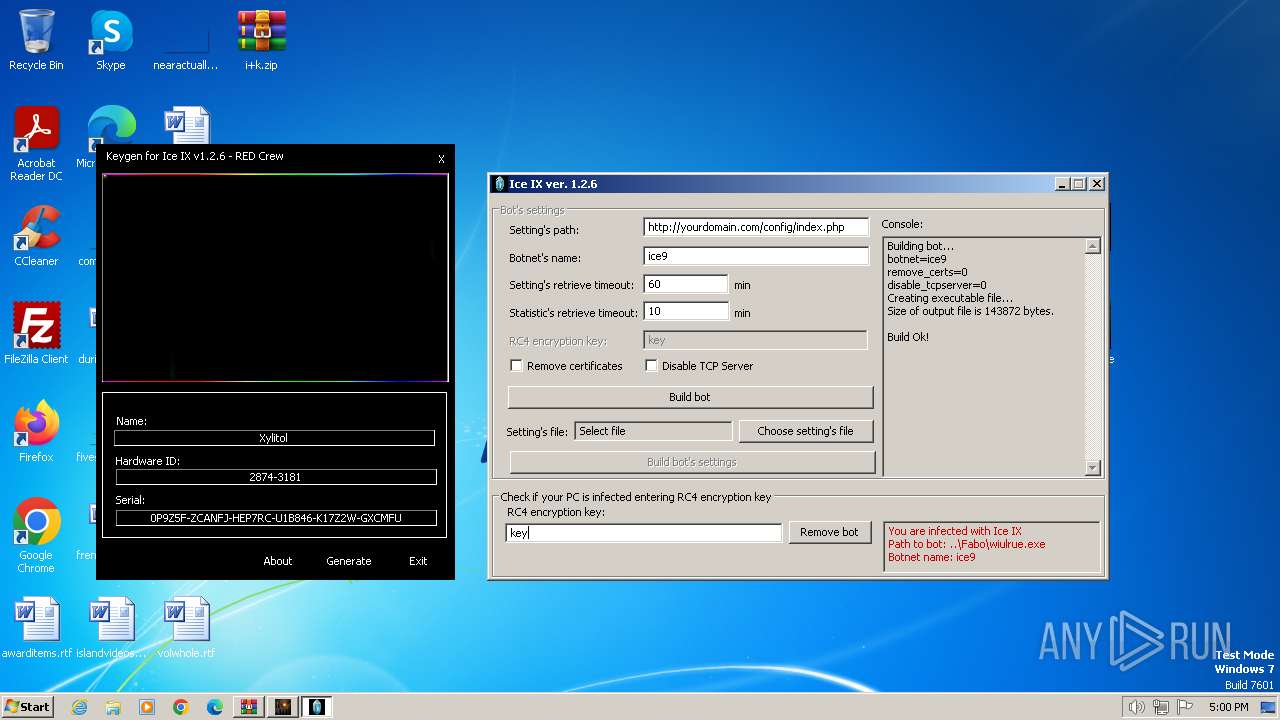
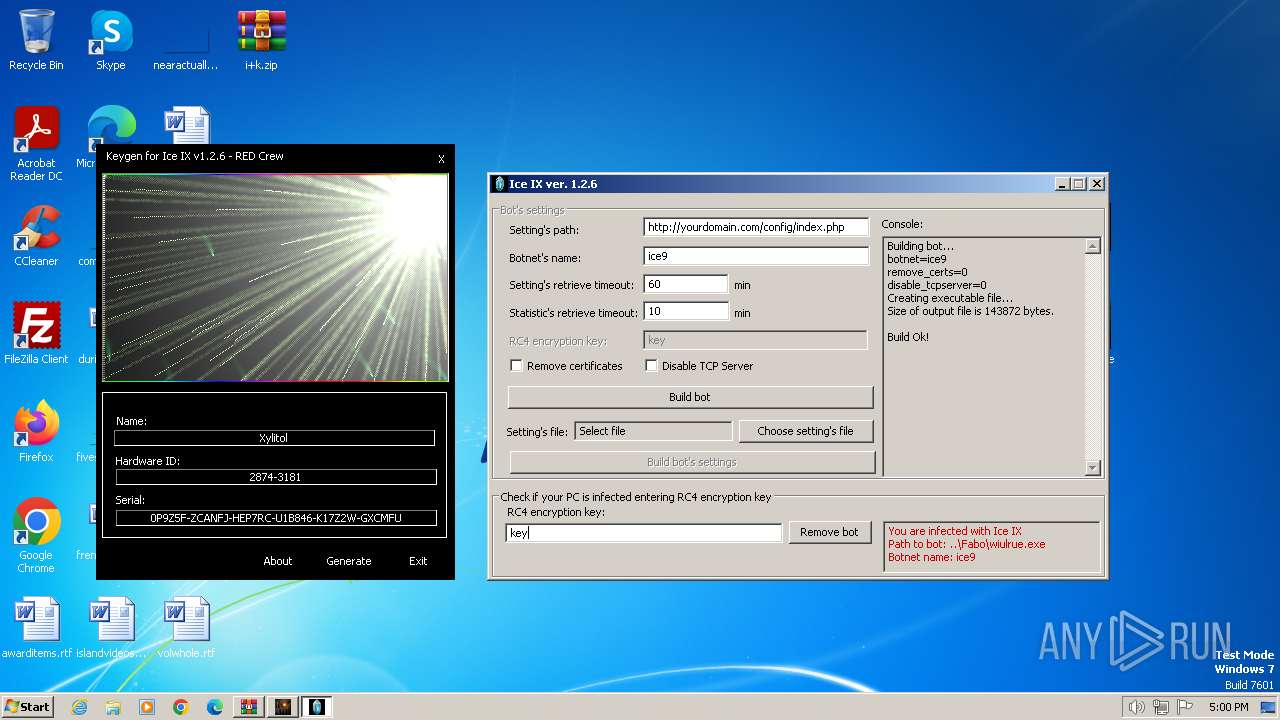
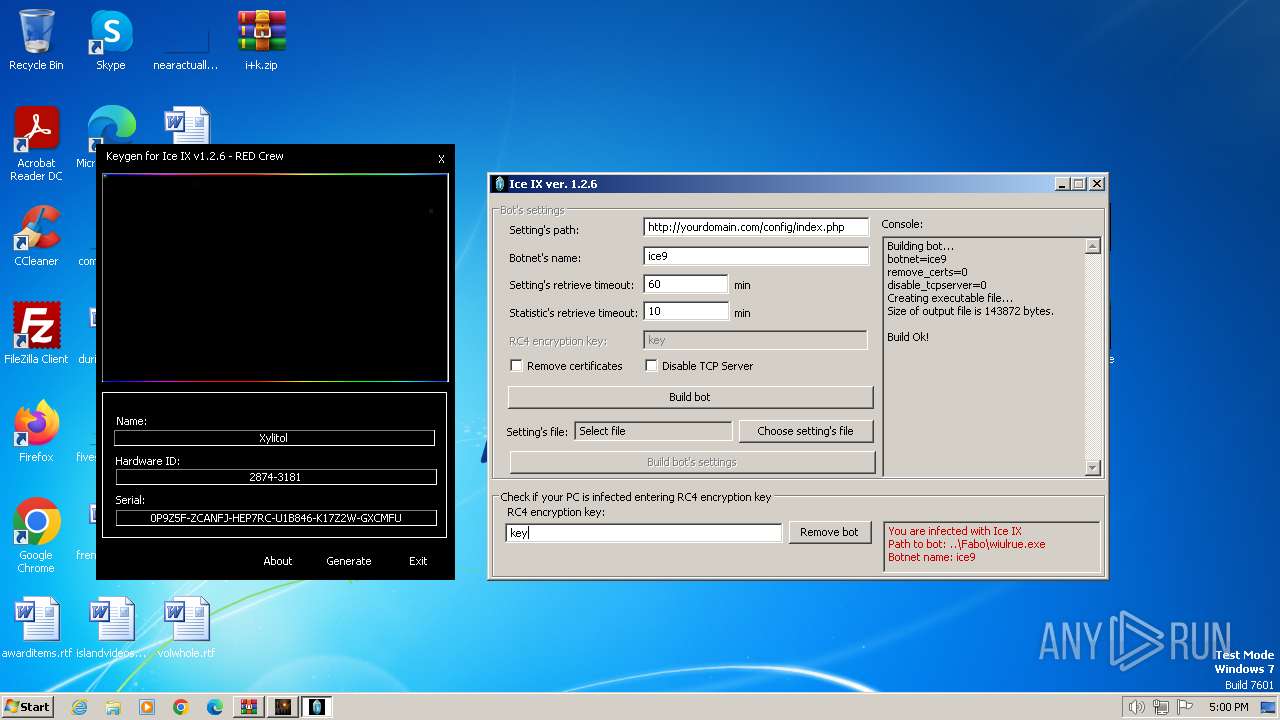
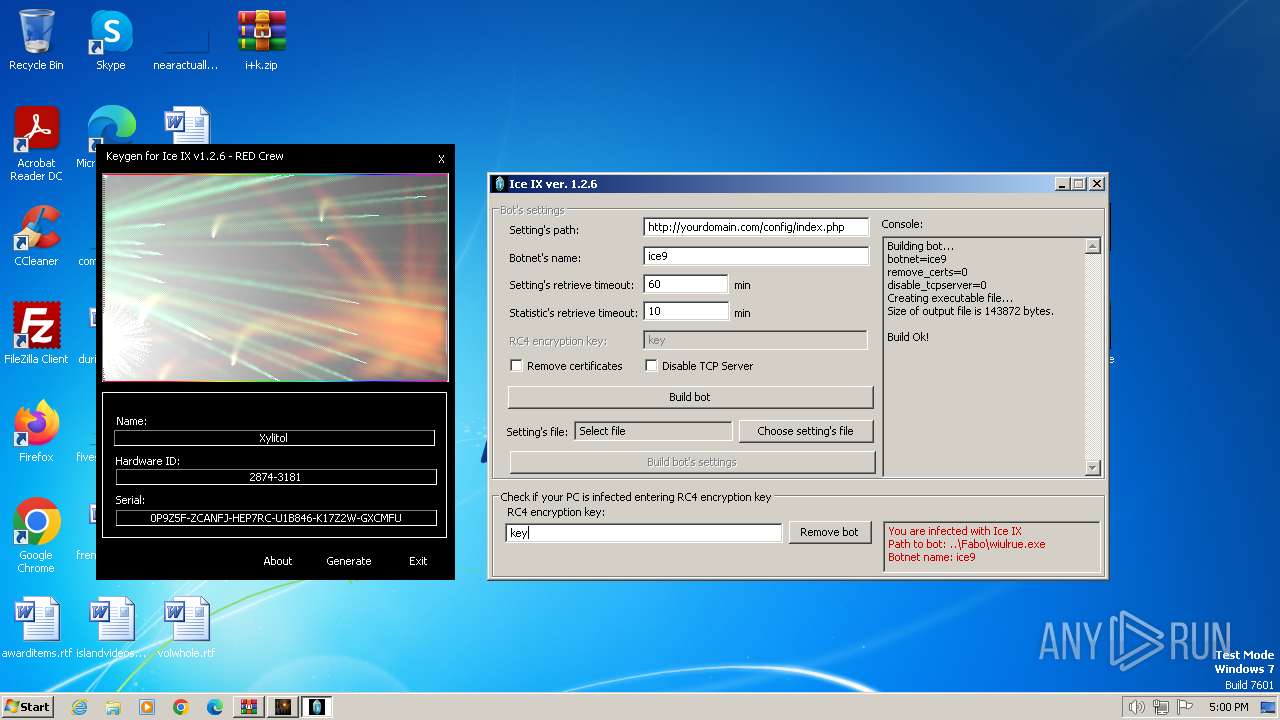
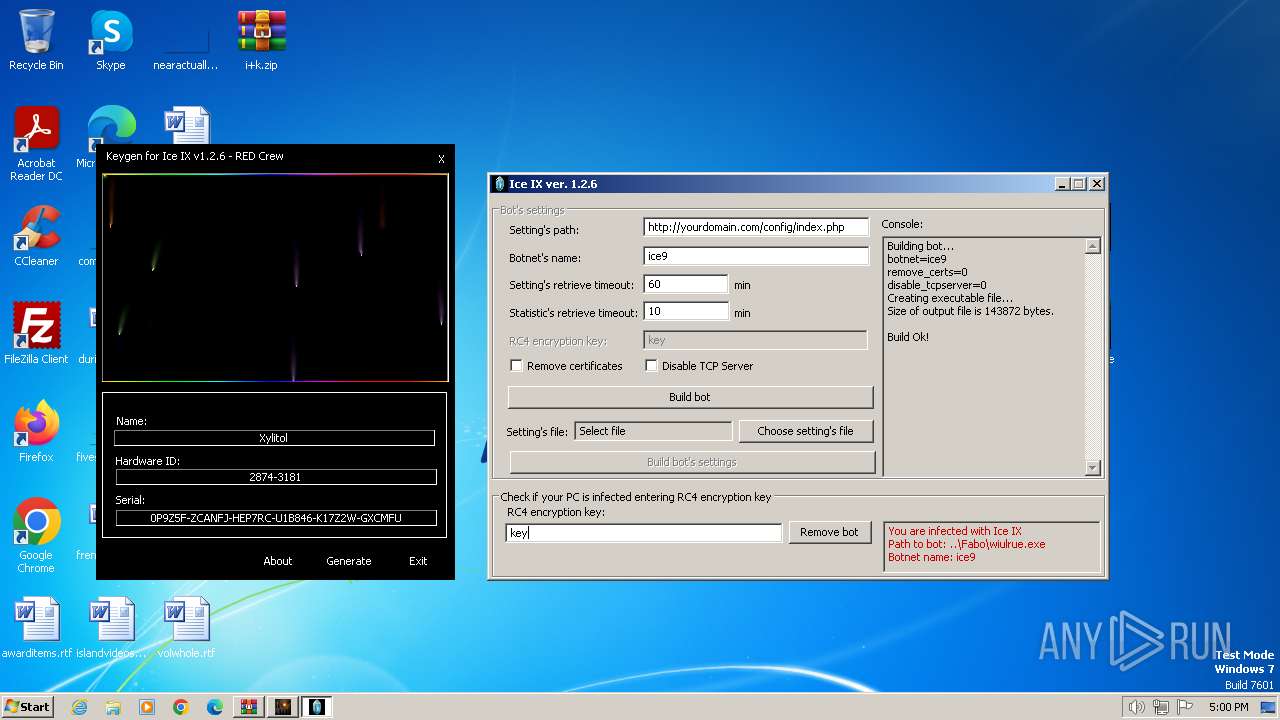
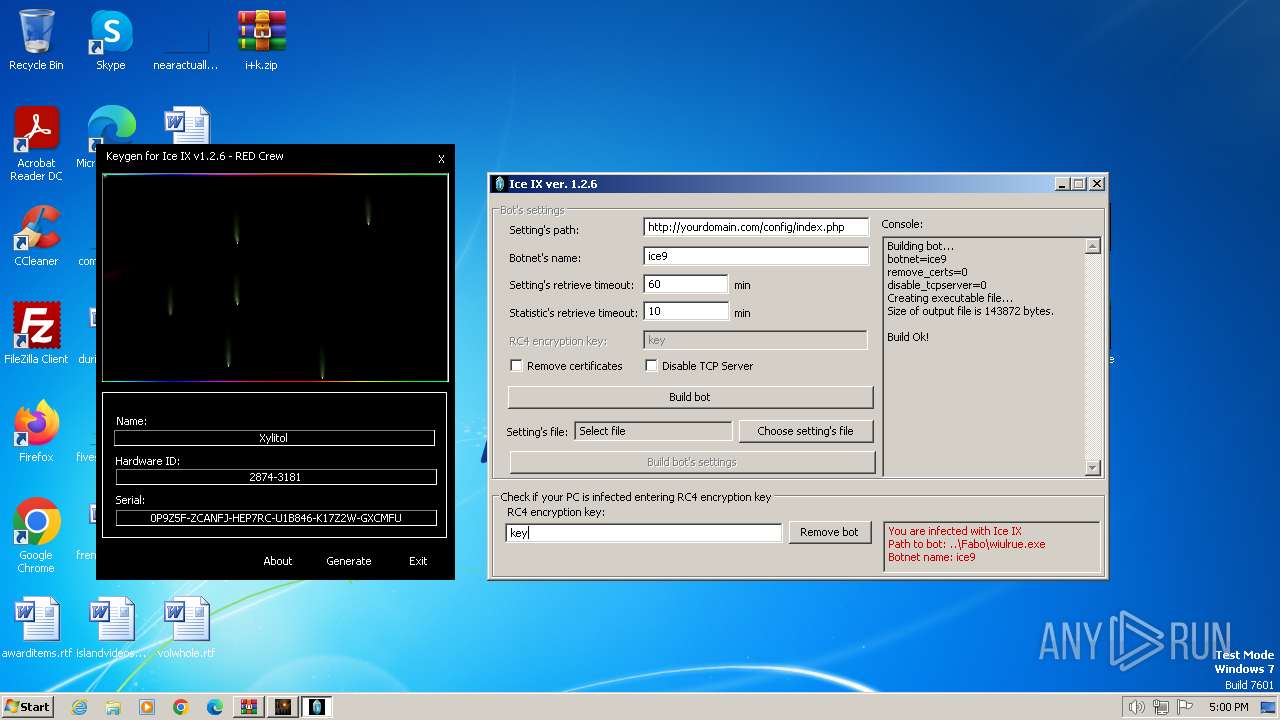
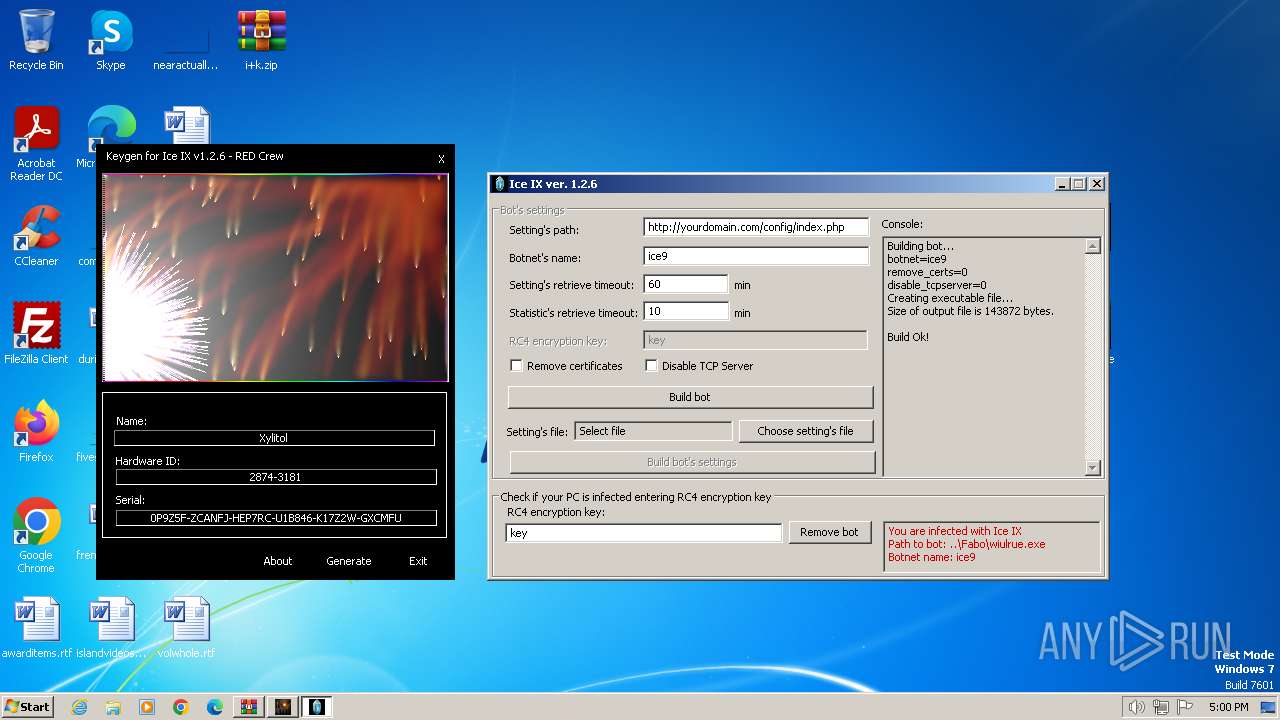
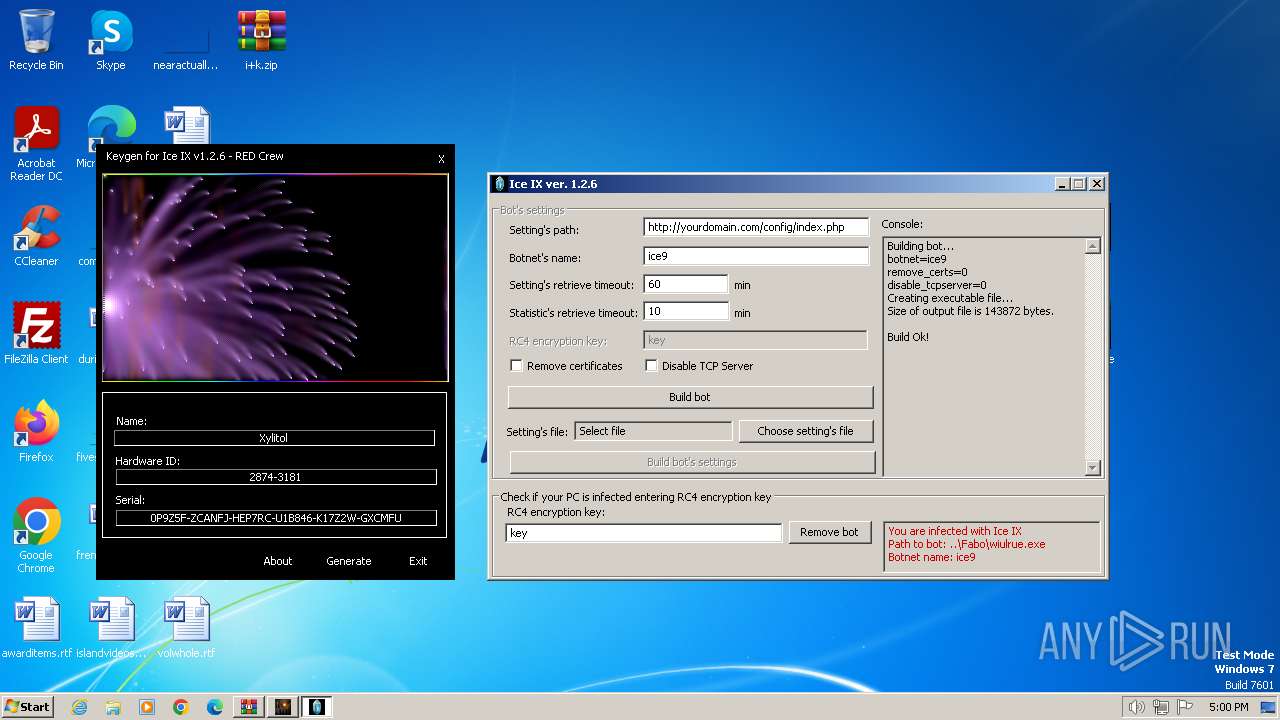
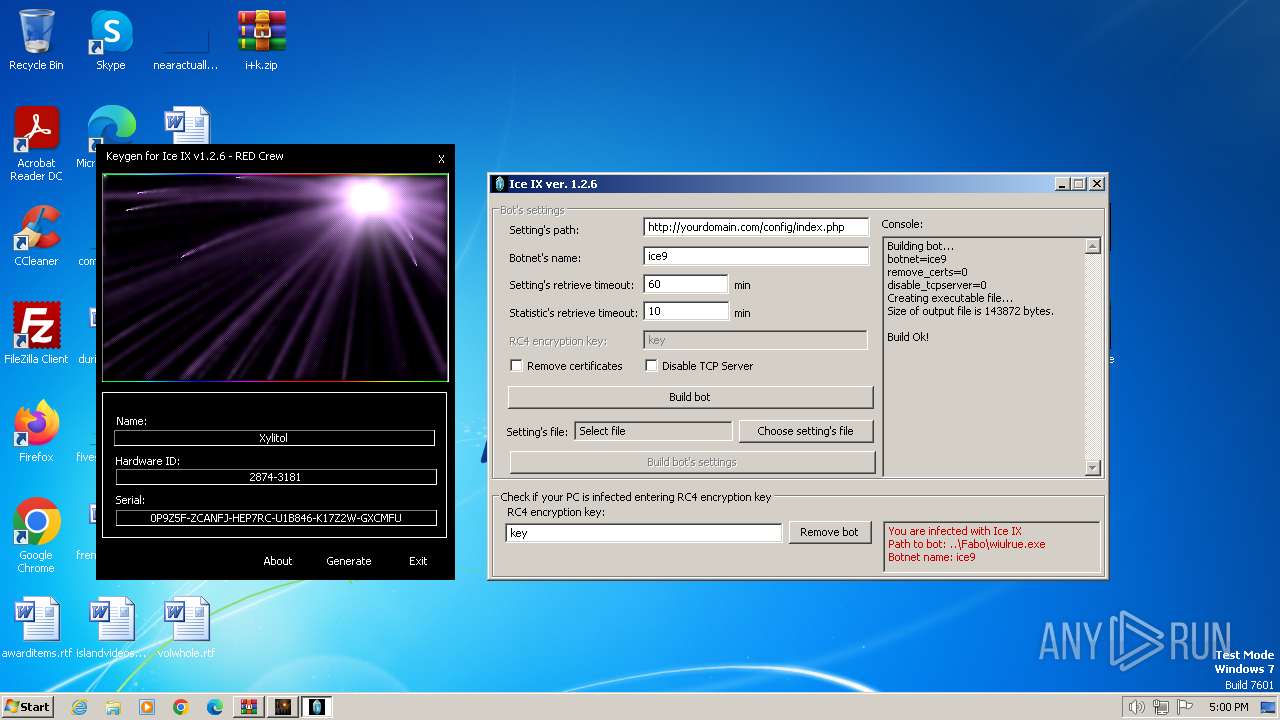
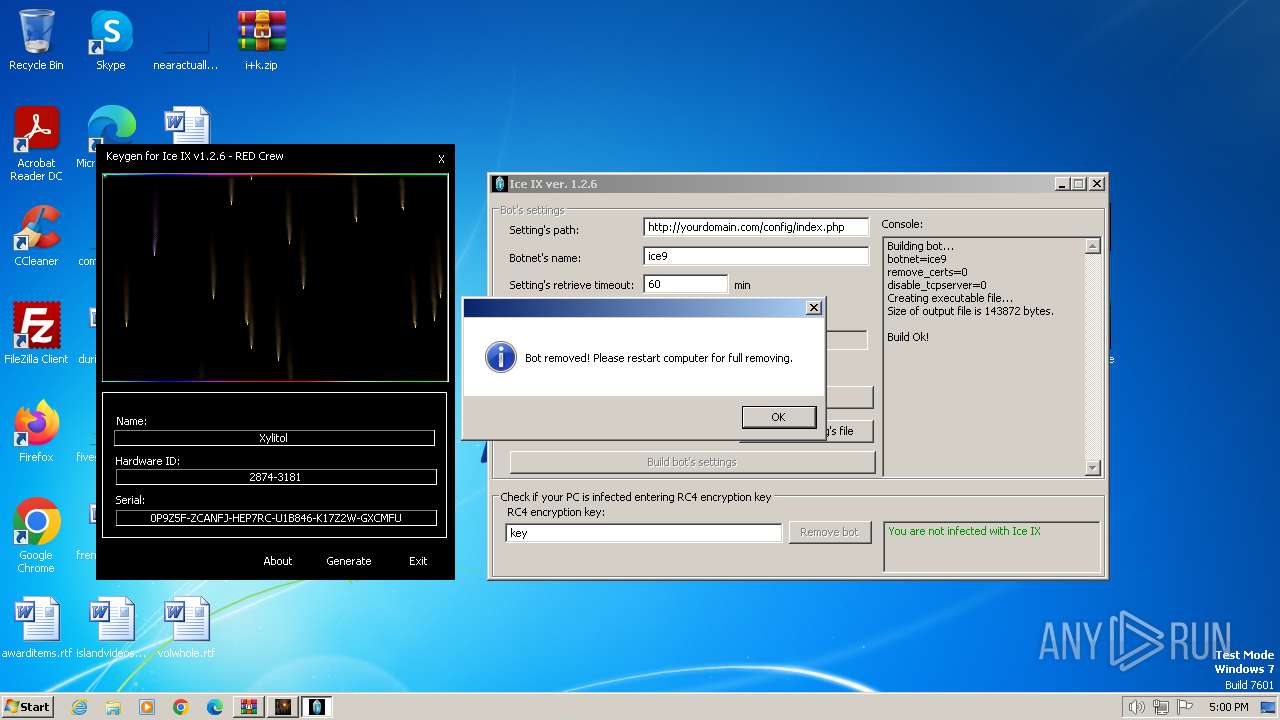
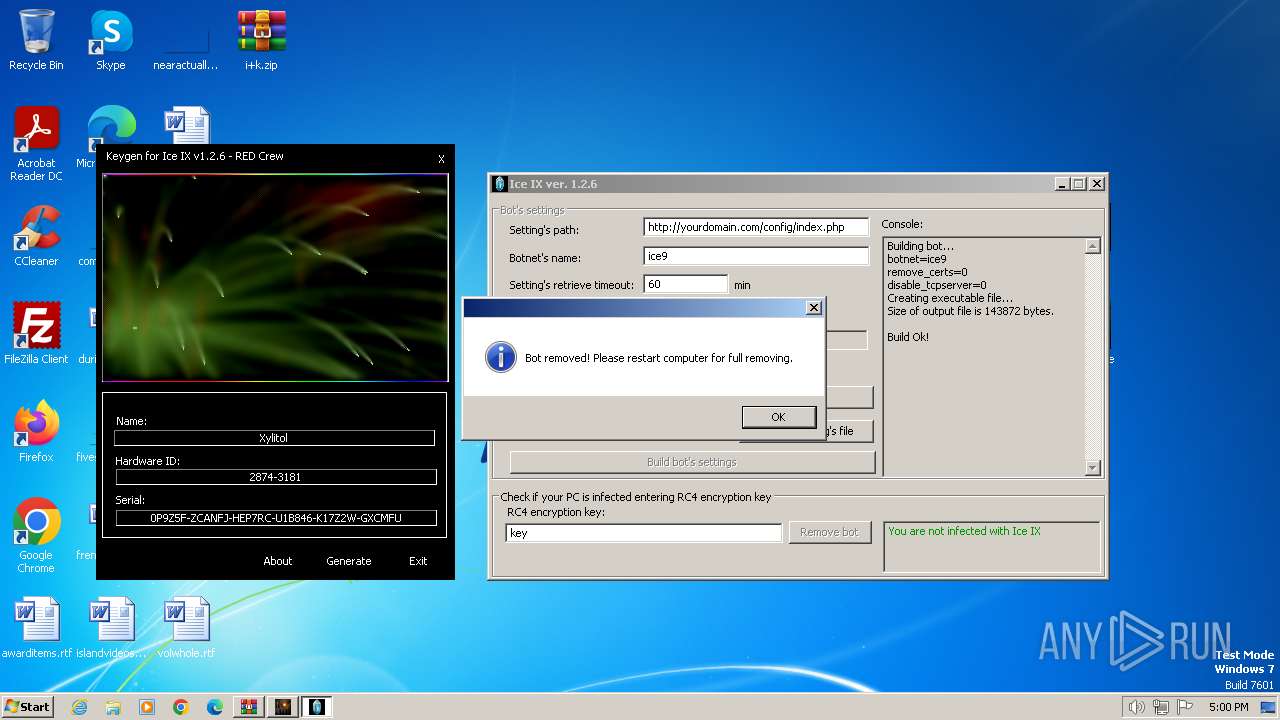
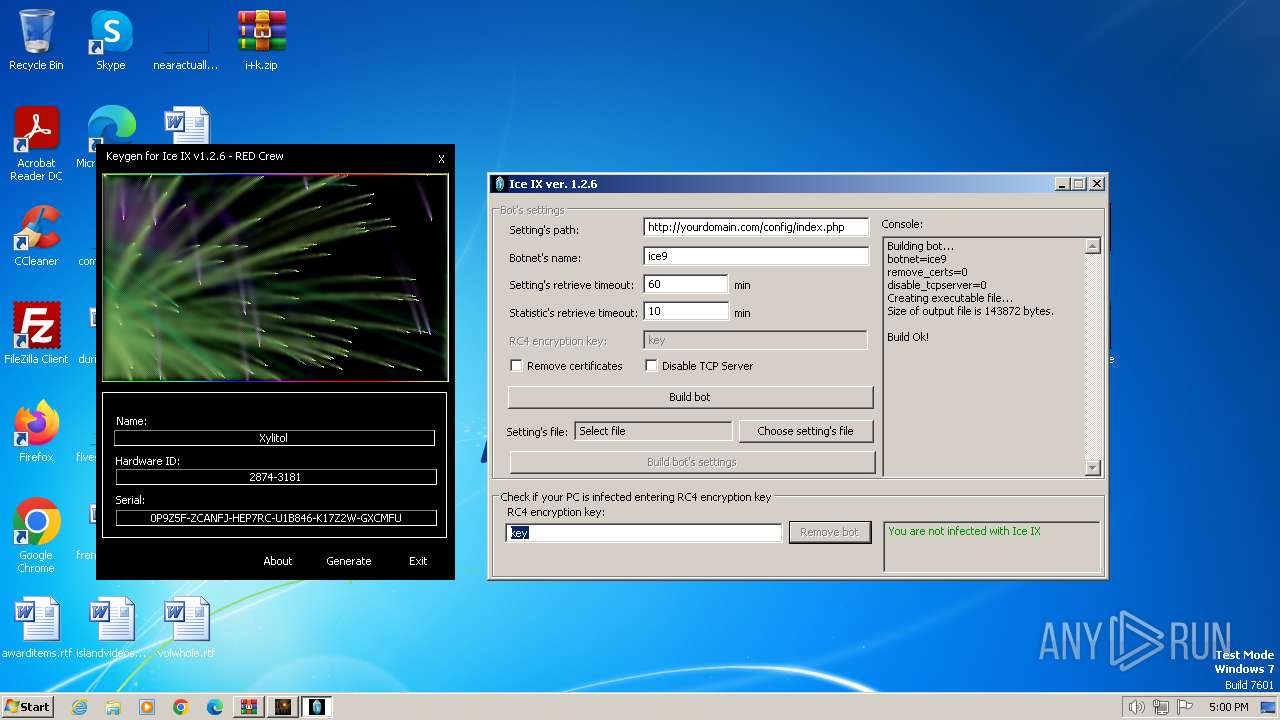
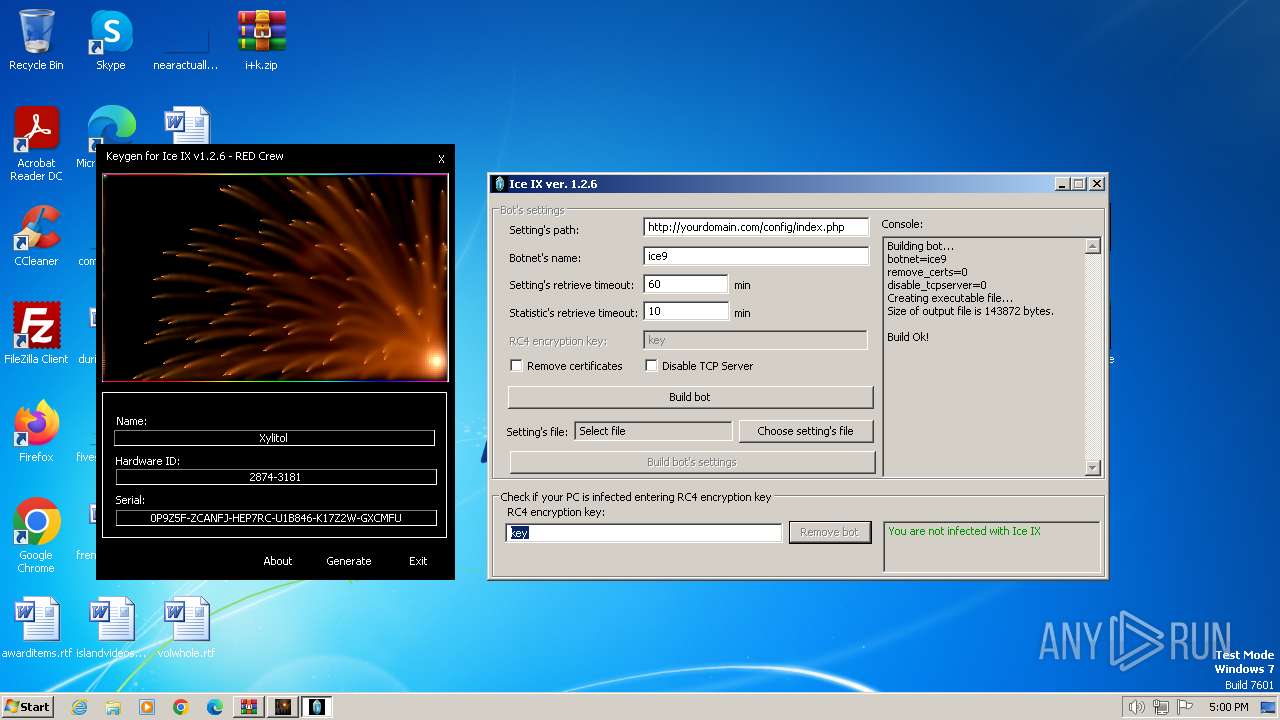
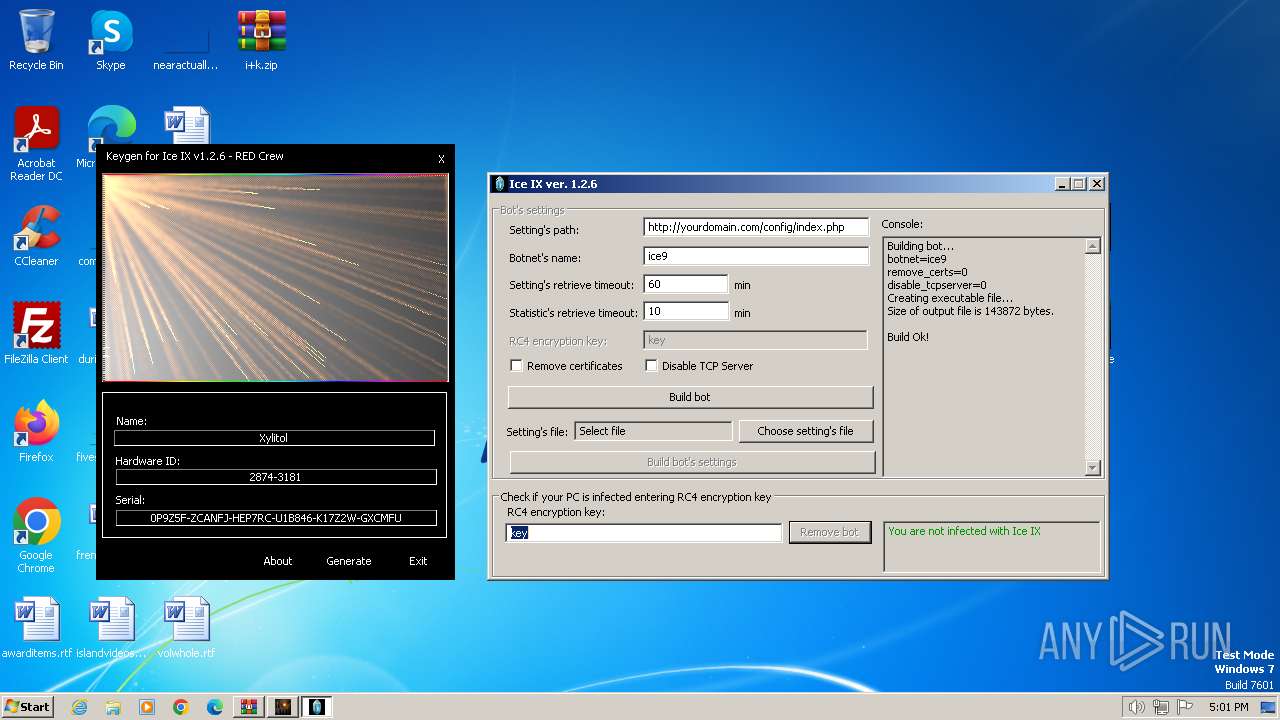
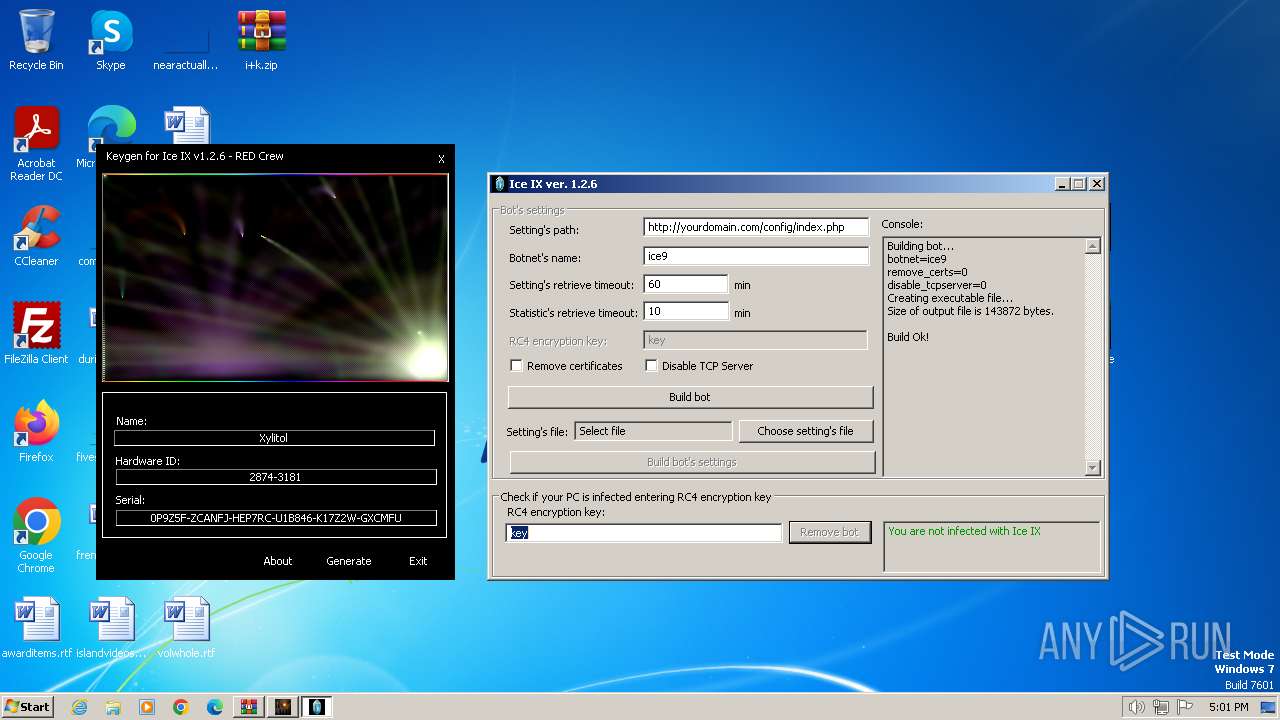
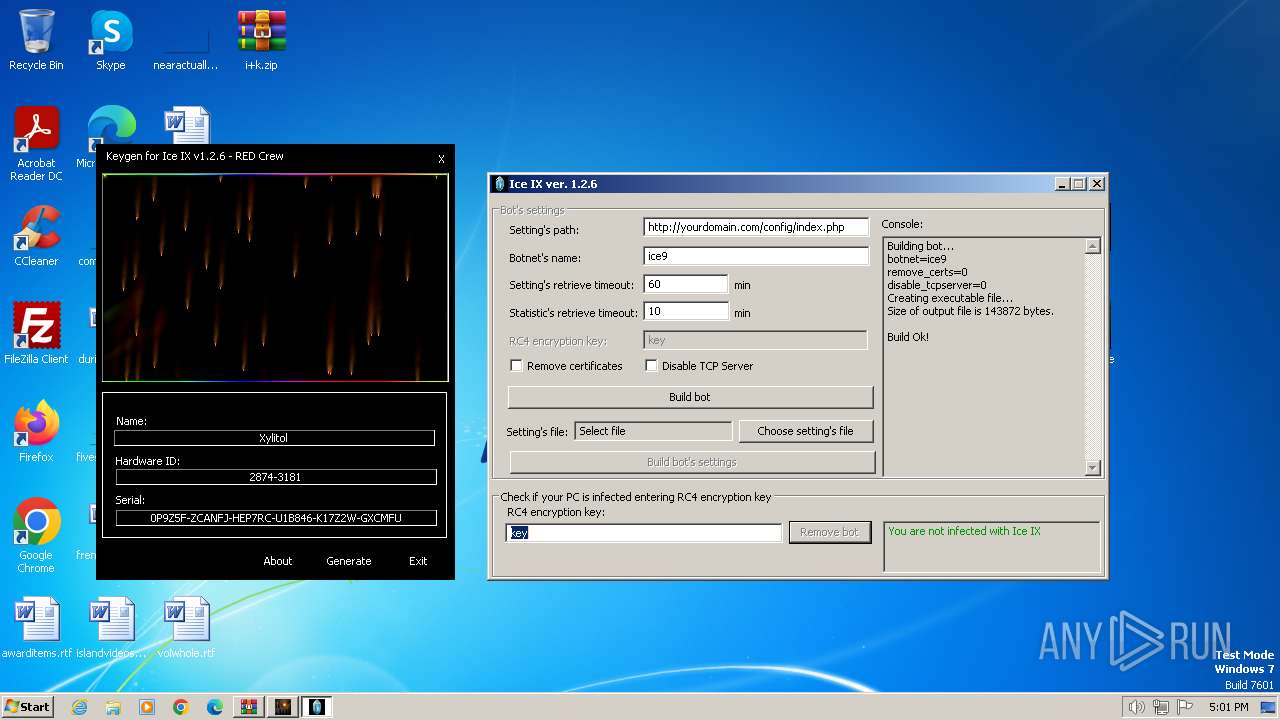
| File name: | i+k.zip |
| Full analysis: | https://app.any.run/tasks/48412c56-4ad5-43ae-b5dd-170b9f42716f |
| Verdict: | Malicious activity |
| Analysis date: | December 18, 2023, 16:59:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 9EF55BA622F3B264B525AC6086834378 |
| SHA1: | 5B2D0DE764D7B65B46D4384C79A13553A47F6C3C |
| SHA256: | 7414BD4CCB06D8FA8BCF1A2DE66D1A359963A2434960E8D17009355CC2465B4C |
| SSDEEP: | 49152:MGoroVmtUkkwAtiMzgc2GI5b53eYZv/wH93LGTfFXqSyuS6YcEtkb0VmNaIlCMtv:MGorpSkvAMc2Z5dOsAd6TfFSuS6YcXbD |
MALICIOUS
Drops the executable file immediately after the start
- iceix.exe (PID: 1496)
- WinMail.exe (PID: 1976)
- ice9.exe (PID: 3752)
Scans artifacts that could help determine the target
- WinMail.exe (PID: 1976)
Runs injected code in another process
- wiulrue.exe (PID: 3732)
Application was injected by another process
- dwm.exe (PID: 612)
SUSPICIOUS
Application launched itself
- iceix.exe (PID: 1236)
Reads the BIOS version
- iceix.exe (PID: 1496)
Detected use of alternative data streams (AltDS)
- iceix.exe (PID: 1496)
- WinMail.exe (PID: 1976)
Reads the Internet Settings
- iceix.exe (PID: 1496)
- WinMail.exe (PID: 1976)
- keygen.exe (PID: 2268)
- dwm.exe (PID: 612)
- ice9.exe (PID: 3752)
- cmd.exe (PID: 1748)
- iceix.exe (PID: 1236)
Drops a self-deleting batch file
- ice9.exe (PID: 3752)
- iceix.exe (PID: 1496)
Executing commands from a ".bat" file
- ice9.exe (PID: 3752)
- iceix.exe (PID: 1496)
Starts itself from another location
- ice9.exe (PID: 3752)
Starts CMD.EXE for commands execution
- ice9.exe (PID: 3752)
- iceix.exe (PID: 1496)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 3848)
Reads Microsoft Outlook installation path
- WinMail.exe (PID: 1976)
Reads Internet Explorer settings
- WinMail.exe (PID: 1976)
Checks Windows Trust Settings
- WinMail.exe (PID: 1976)
Reads security settings of Internet Explorer
- WinMail.exe (PID: 1976)
Reads settings of System Certificates
- WinMail.exe (PID: 1976)
INFO
Checks supported languages
- keygen.exe (PID: 2268)
- iceix.exe (PID: 1236)
- iceix.exe (PID: 1496)
- ice9.exe (PID: 3752)
- wiulrue.exe (PID: 3732)
- WinMail.exe (PID: 1976)
Manual execution by a user
- keygen.exe (PID: 2268)
- iceix.exe (PID: 1236)
- ice9.exe (PID: 3752)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 128)
Reads the computer name
- keygen.exe (PID: 2268)
- iceix.exe (PID: 1496)
- wiulrue.exe (PID: 3732)
- WinMail.exe (PID: 1976)
- iceix.exe (PID: 1236)
- ice9.exe (PID: 3752)
Reads the machine GUID from the registry
- iceix.exe (PID: 1496)
- WinMail.exe (PID: 1976)
Creates files in the program directory
- iceix.exe (PID: 1496)
Create files in a temporary directory
- ice9.exe (PID: 3752)
- WinMail.exe (PID: 1976)
- iceix.exe (PID: 1496)
Creates files or folders in the user directory
- WinMail.exe (PID: 1976)
- ice9.exe (PID: 3752)
Checks proxy server information
- WinMail.exe (PID: 1976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:12:18 16:58:38 |
| ZipCRC: | 0x238e7af5 |
| ZipCompressedSize: | 971631 |
| ZipUncompressedSize: | 1159168 |
| ZipFileName: | iceix.exe |
Total processes
56
Monitored processes
12
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\i+k.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 612 | "C:\Windows\system32\Dwm.exe" | C:\Windows\System32\dwm.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Desktop Window Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1236 | "C:\Users\admin\Desktop\iceix.exe" | C:\Users\admin\Desktop\iceix.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1496 | "C:\Users\admin\Desktop\iceix.exe" | C:\Users\admin\Desktop\iceix.exe | — | iceix.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1748 | "C:\Windows\system32\cmd.exe" /c "C:\Users\admin\AppData\Local\Temp\tmp63c71a8b.bat" | C:\Windows\System32\cmd.exe | — | ice9.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1976 | "C:\Program Files\Windows Mail\WinMail.exe" -Embedding | C:\Program Files\Windows Mail\WinMail.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Mail Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2228 | netsh advfirewall firewall add rule name="explore" dir=in action=allow program="C:\Users\admin\AppData\Roaming\Fabo\wiulrue.exe" | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2268 | "C:\Users\admin\Desktop\keygen.exe" | C:\Users\admin\Desktop\keygen.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2636 | "C:\Windows\system32\cmd.exe" /c "C:\Users\admin\AppData\Local\Temp\tmp41069ff0.bat" | C:\Windows\System32\cmd.exe | — | iceix.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3732 | "C:\Users\admin\AppData\Roaming\Fabo\wiulrue.exe" | C:\Users\admin\AppData\Roaming\Fabo\wiulrue.exe | — | ice9.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
9 932
Read events
9 800
Write events
122
Delete events
10
Modification events
| (PID) Process: | (128) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1496) iceix.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
Executable files
5
Suspicious files
19
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa128.23715\keygen.exe | executable | |
MD5:218CE56C9E126939A950DAAA3DD27953 | SHA256:639344D3D99225E59765E78354A2553EE20A6794D97AD3A43BD0155E6E0FD391 | |||
| 128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa128.23715\iceix.exe | executable | |
MD5:CC474EE65CFB0A498ADD7863E9DF799B | SHA256:C8D4B53A2EB65A01875257E654B6C186801217AC678E778B00AC243411887B21 | |||
| 1976 | WinMail.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Mail\edb.log | binary | |
MD5:09F9EC30C43F61C1B4E3CF574CEF1740 | SHA256:3A2C8485989DE3437B107D5459308E6984CC2D0F029B25CA74DFA0BC4B754054 | |||
| 1496 | iceix.exe | C:\Users\admin\Desktop\ice9.exe | executable | |
MD5:A577DA8635D8B8EF440E533D9A2248C6 | SHA256:73EA2A99E475DDC500495EA0C1E0F6E31DA9726FD02E33A84549E521F3DEB5C6 | |||
| 3752 | ice9.exe | C:\Users\admin\AppData\Roaming\Fabo\wiulrue.exe | executable | |
MD5:DD7F1DB15C2FD49CCAA0EBEC69995A48 | SHA256:D1B5E888FFA2D4F9C19E2957282896DAF82D09194E7667CE0A50FC0273EA50FC | |||
| 1976 | WinMail.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Mail\Backup\temp\WindowsMail.MSMessageStore | binary | |
MD5:04980F3B678CF90FAF46B01259F34C33 | SHA256:8952C3BF8B91AF49A8FAD3A44B4B59F93E946186C5EC0619E841FB5636D43547 | |||
| 3752 | ice9.exe | C:\Users\admin\AppData\Local\Temp\tmp175d3e7f.bat | text | |
MD5:4FDED8A65E0FA7FADF3EF1B8223C4962 | SHA256:64B60A67CE13DB500449090535EADE86DF09754E651539AF3827BE91F2DAEED3 | |||
| 1976 | WinMail.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Mail\WindowsMail.MSMessageStore | binary | |
MD5:DF2859480707B12827D98668AD70D049 | SHA256:8A3A25A03F7EFA8998E4C1C4CB99BF9E1161F4A6F32C744E744CD57BC4D64E4A | |||
| 1976 | WinMail.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Mail\Backup\temp\WindowsMail.pat | binary | |
MD5:EFA9461A8FC8B0503987D28FC31F5A63 | SHA256:9497046E0083E6610B7300FDF3FFB949A93218520908C298E3420D230B6F6D97 | |||
| 1976 | WinMail.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Mail\edbtmp.log | binary | |
MD5:FECA2A0EB68C40A8663874993ECF0404 | SHA256:0836419C4E8C85F5D34805277E722920C3C2A9CD8161993EA944A0D948E6C458 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
15
DNS requests
1
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
276 | taskhost.exe | POST | 405 | 64.190.63.222:80 | http://yourdomain.com/config/index.php | unknown | html | 556 b | unknown |
276 | taskhost.exe | POST | 405 | 64.190.63.222:80 | http://yourdomain.com/config/index.php | unknown | html | 556 b | unknown |
276 | taskhost.exe | POST | 405 | 64.190.63.222:80 | http://yourdomain.com/config/index.php | unknown | html | 556 b | unknown |
276 | taskhost.exe | POST | 405 | 64.190.63.222:80 | http://yourdomain.com/config/index.php | unknown | html | 556 b | unknown |
276 | taskhost.exe | POST | 405 | 64.190.63.222:80 | http://yourdomain.com/config/index.php | unknown | html | 556 b | unknown |
276 | taskhost.exe | POST | 405 | 64.190.63.222:80 | http://yourdomain.com/config/index.php | unknown | html | 556 b | unknown |
276 | taskhost.exe | POST | 405 | 64.190.63.222:80 | http://yourdomain.com/config/index.php | unknown | html | 556 b | unknown |
276 | taskhost.exe | POST | 405 | 64.190.63.222:80 | http://yourdomain.com/config/index.php | unknown | html | 556 b | unknown |
276 | taskhost.exe | POST | 405 | 64.190.63.222:80 | http://yourdomain.com/config/index.php | unknown | html | 556 b | unknown |
276 | taskhost.exe | POST | 405 | 64.190.63.222:80 | http://yourdomain.com/config/index.php | unknown | html | 556 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
276 | taskhost.exe | 64.190.63.222:80 | yourdomain.com | SEDO GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
yourdomain.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
276 | taskhost.exe | A Network Trojan was detected | ET MALWARE Generic - POST To .php w/Extended ASCII Characters |
276 | taskhost.exe | A Network Trojan was detected | ET MALWARE Generic - POST To .php w/Extended ASCII Characters |
276 | taskhost.exe | A Network Trojan was detected | ET MALWARE Generic - POST To .php w/Extended ASCII Characters |
276 | taskhost.exe | A Network Trojan was detected | ET MALWARE Generic - POST To .php w/Extended ASCII Characters |
276 | taskhost.exe | A Network Trojan was detected | ET MALWARE Generic - POST To .php w/Extended ASCII Characters |
276 | taskhost.exe | A Network Trojan was detected | ET MALWARE Generic - POST To .php w/Extended ASCII Characters |
276 | taskhost.exe | A Network Trojan was detected | ET MALWARE Generic - POST To .php w/Extended ASCII Characters |
276 | taskhost.exe | A Network Trojan was detected | ET MALWARE Generic - POST To .php w/Extended ASCII Characters |
276 | taskhost.exe | A Network Trojan was detected | ET MALWARE Generic - POST To .php w/Extended ASCII Characters |
276 | taskhost.exe | A Network Trojan was detected | ET MALWARE Generic - POST To .php w/Extended ASCII Characters |
Process | Message |
|---|---|
iceix.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
iceix.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |