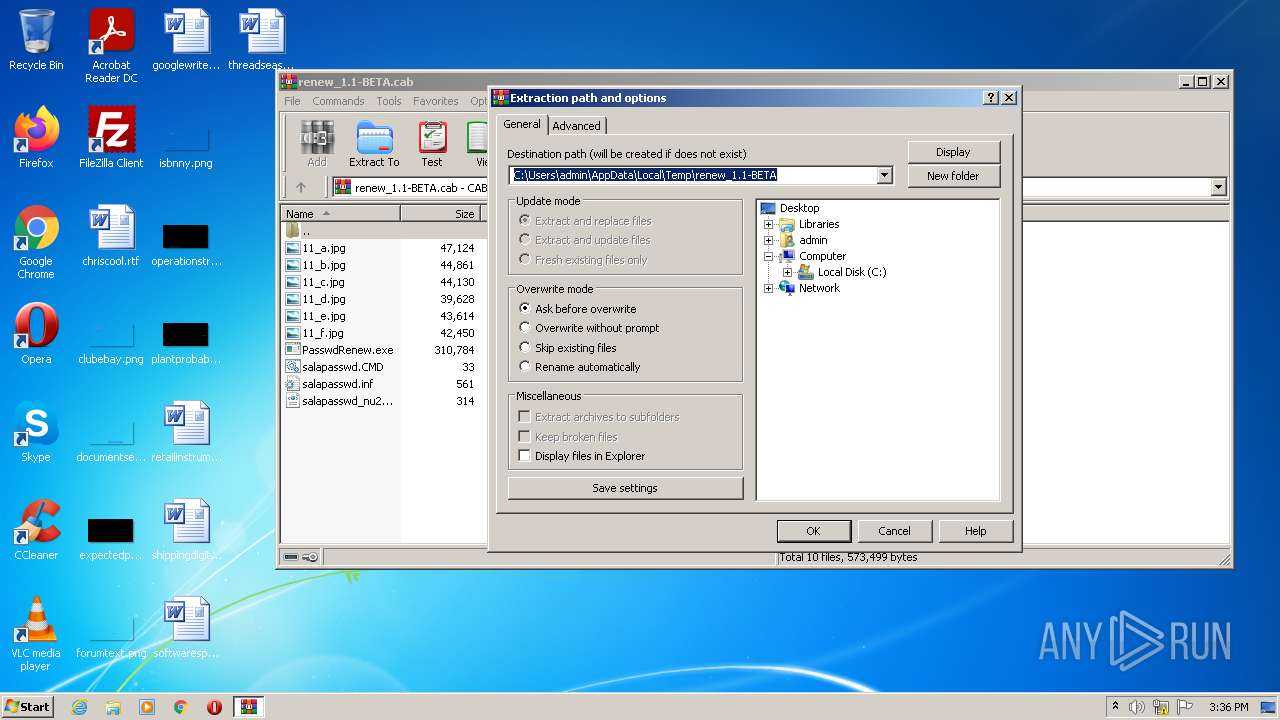
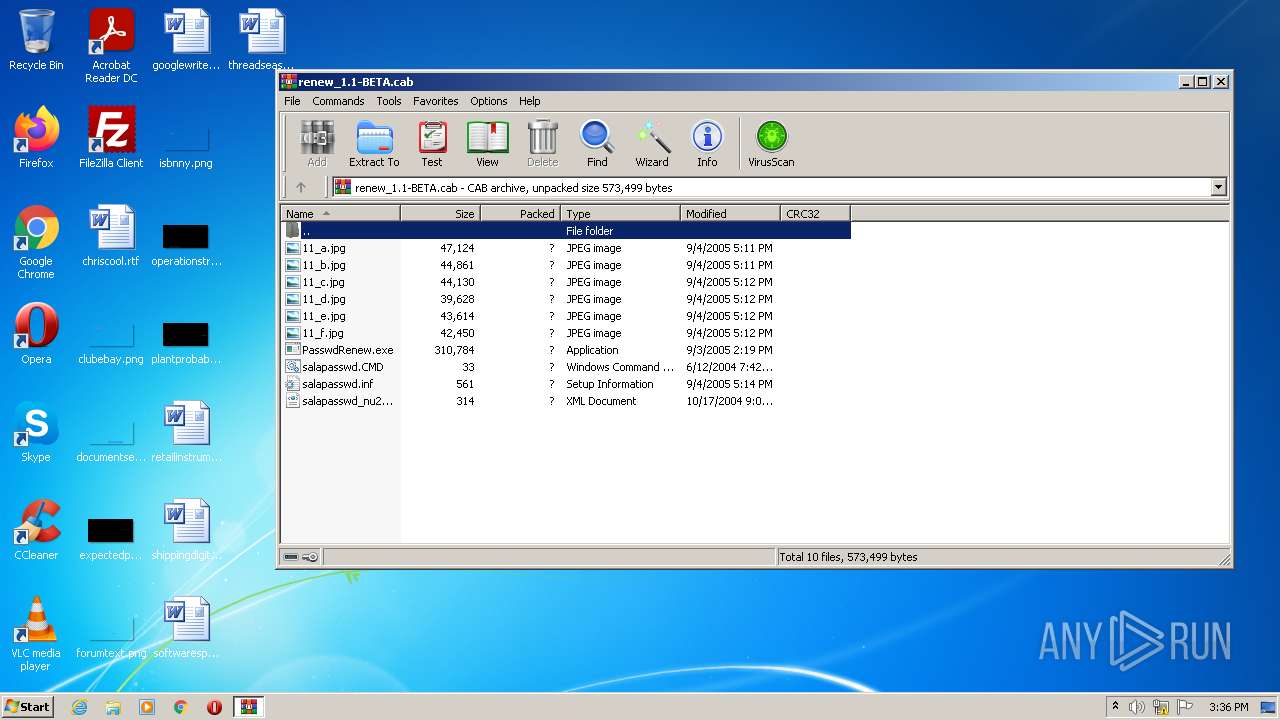
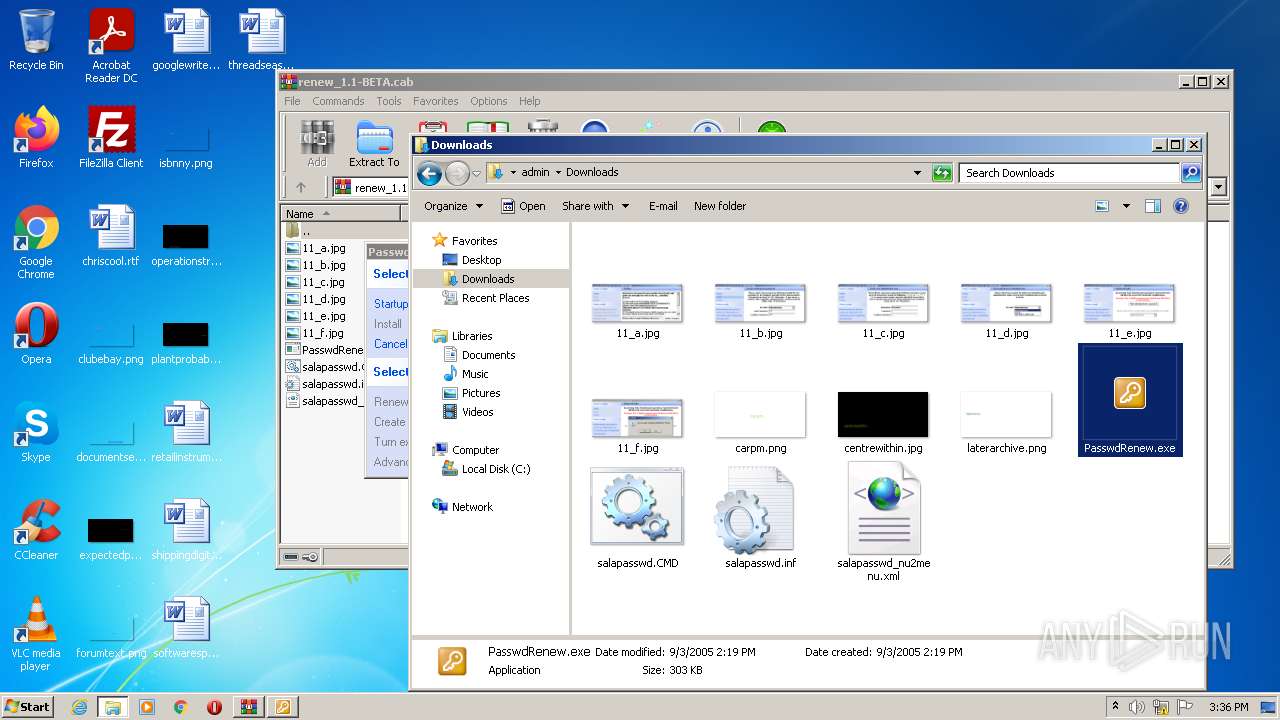
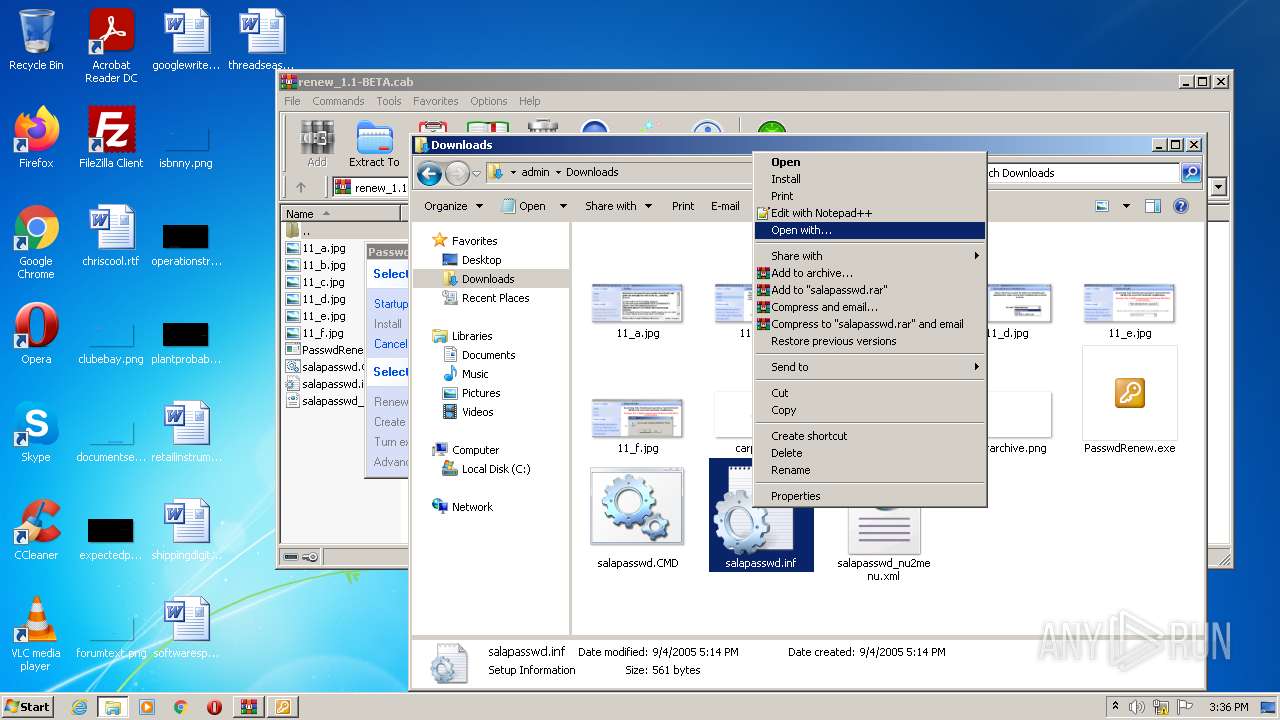
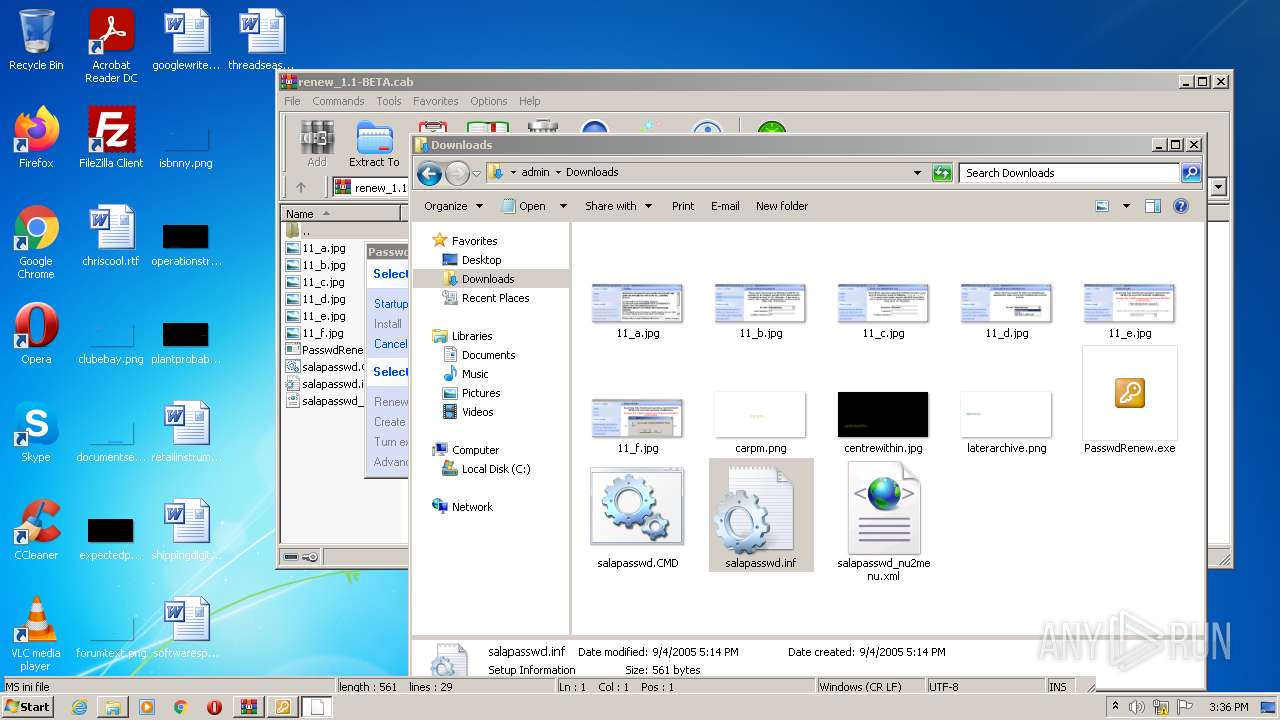
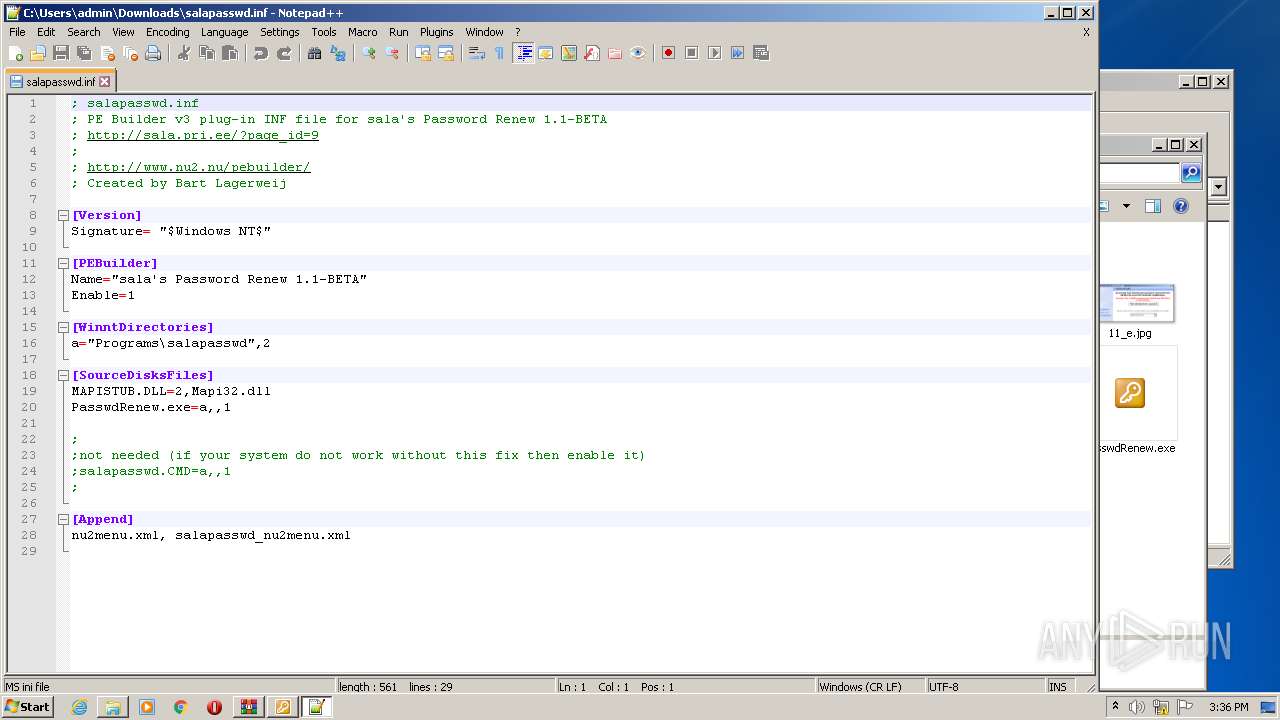
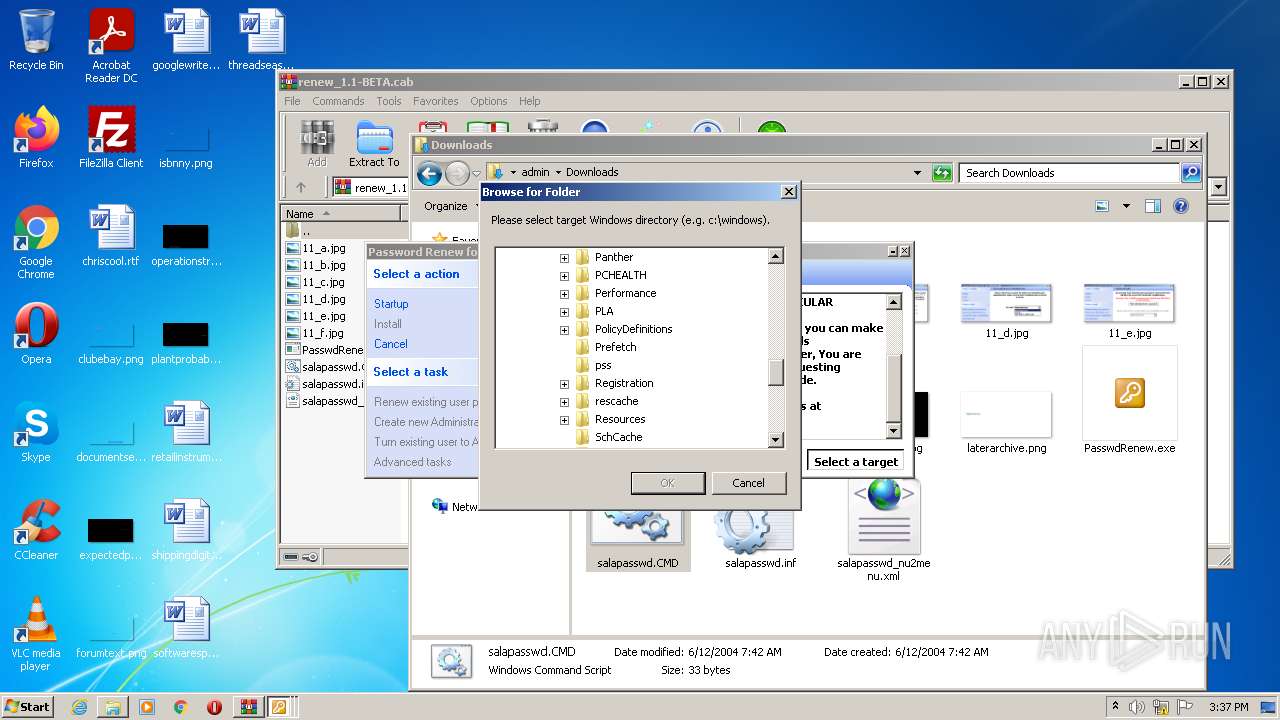
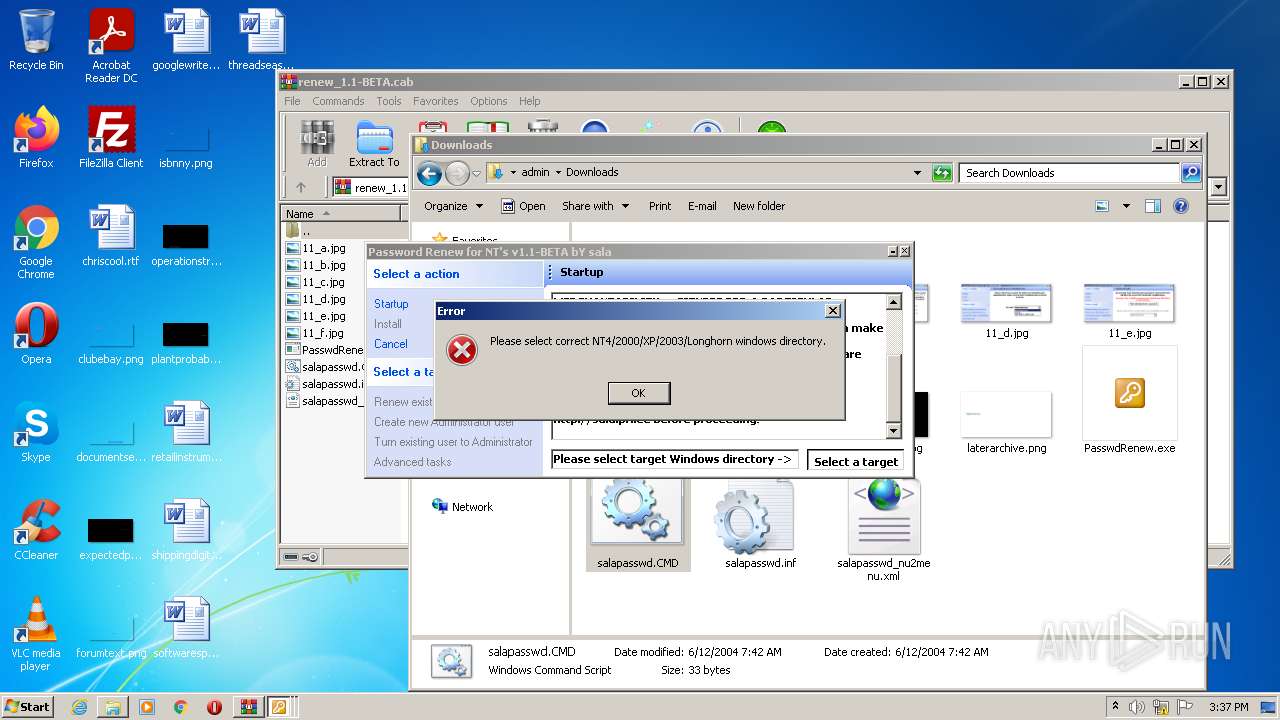
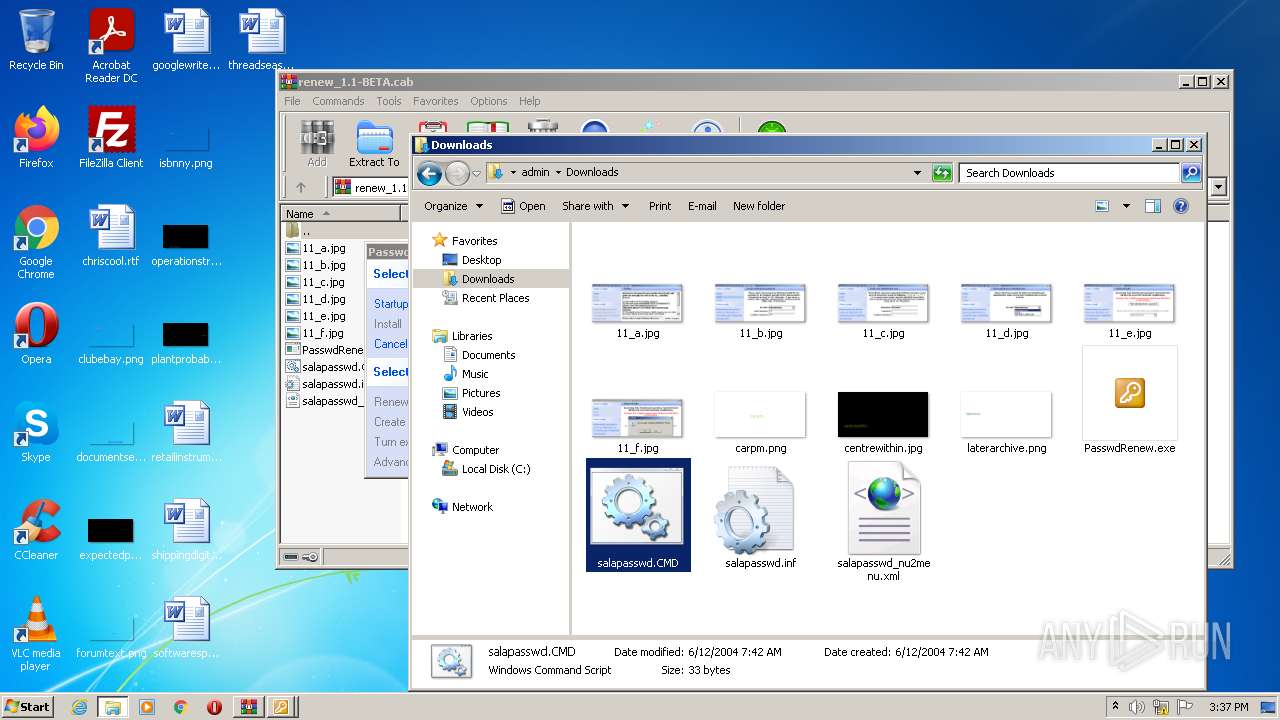
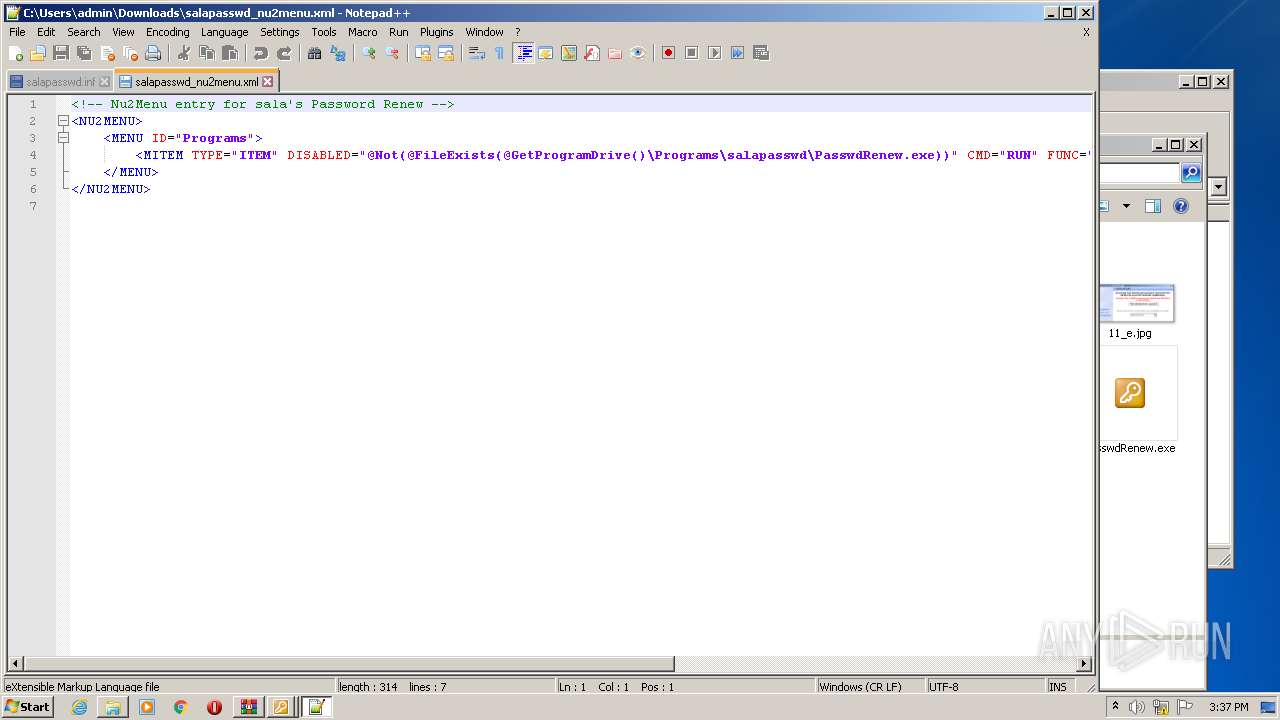
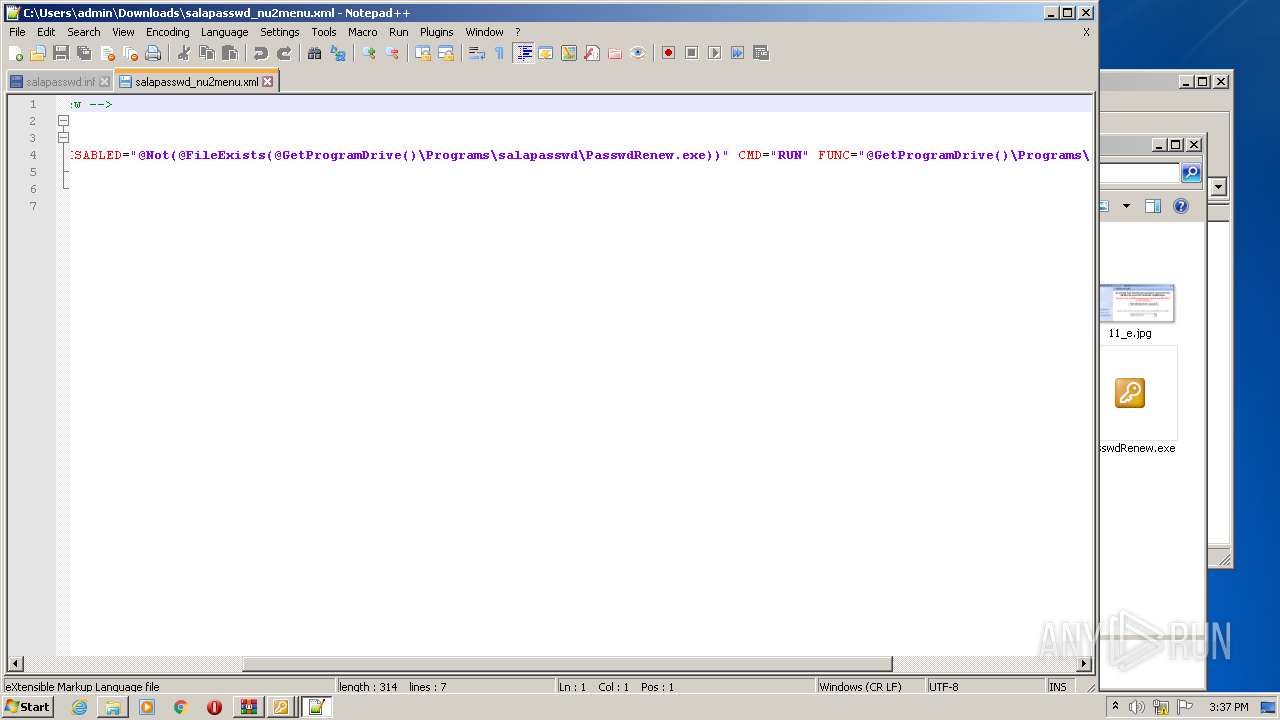
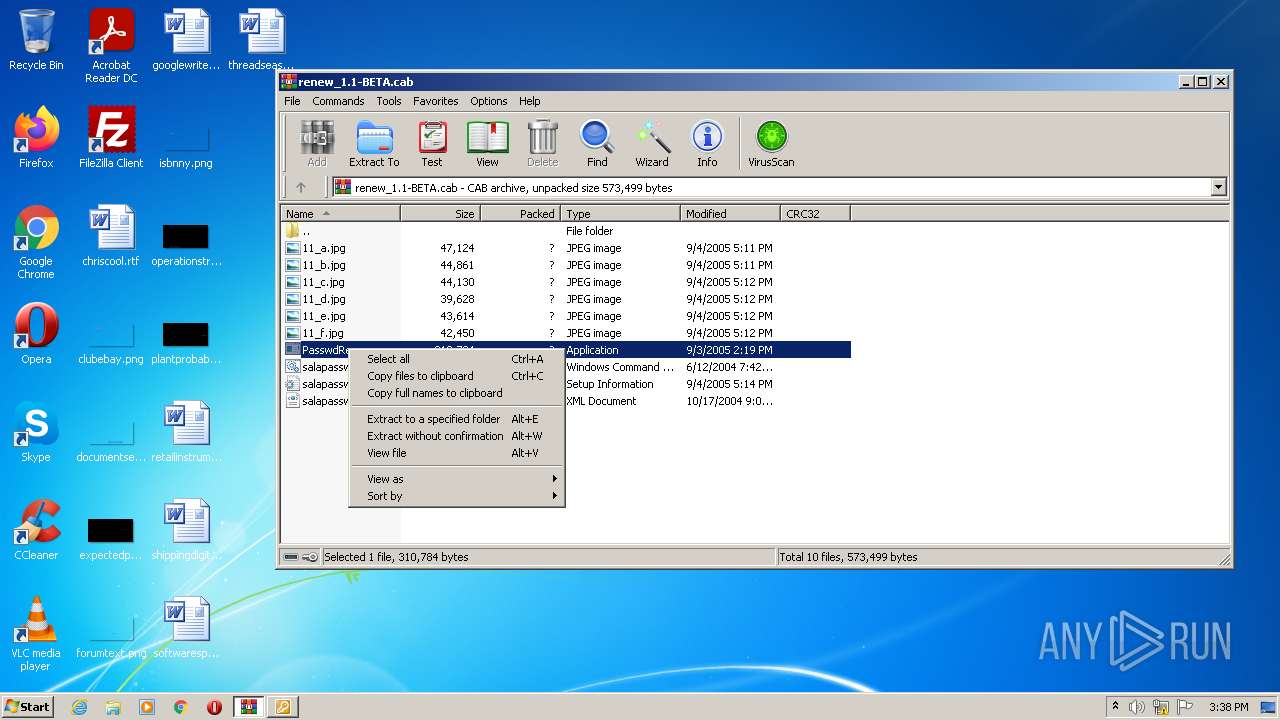
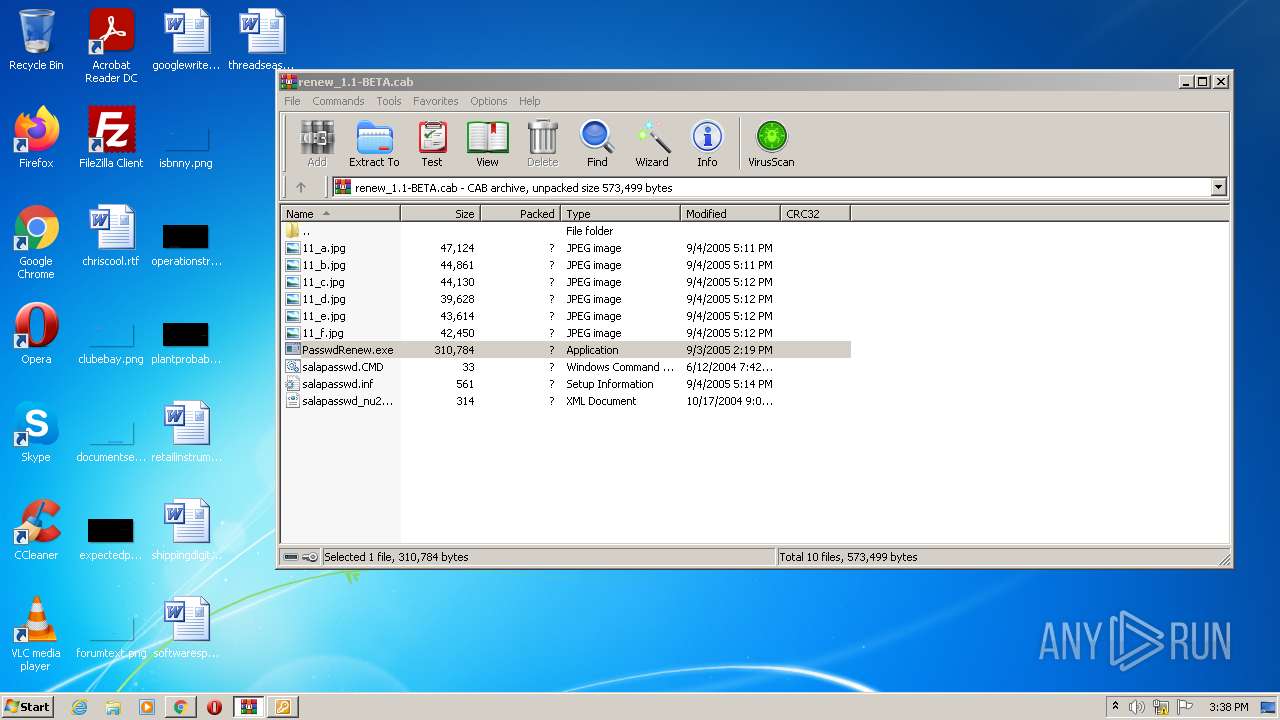
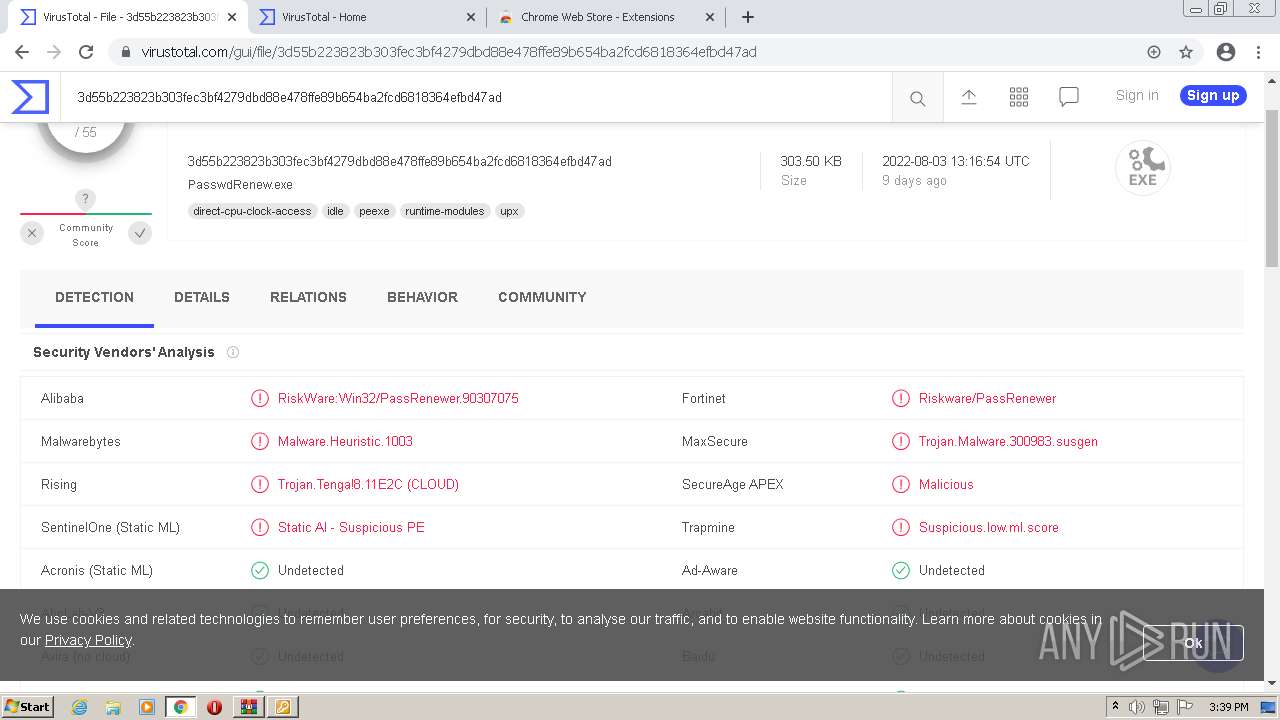
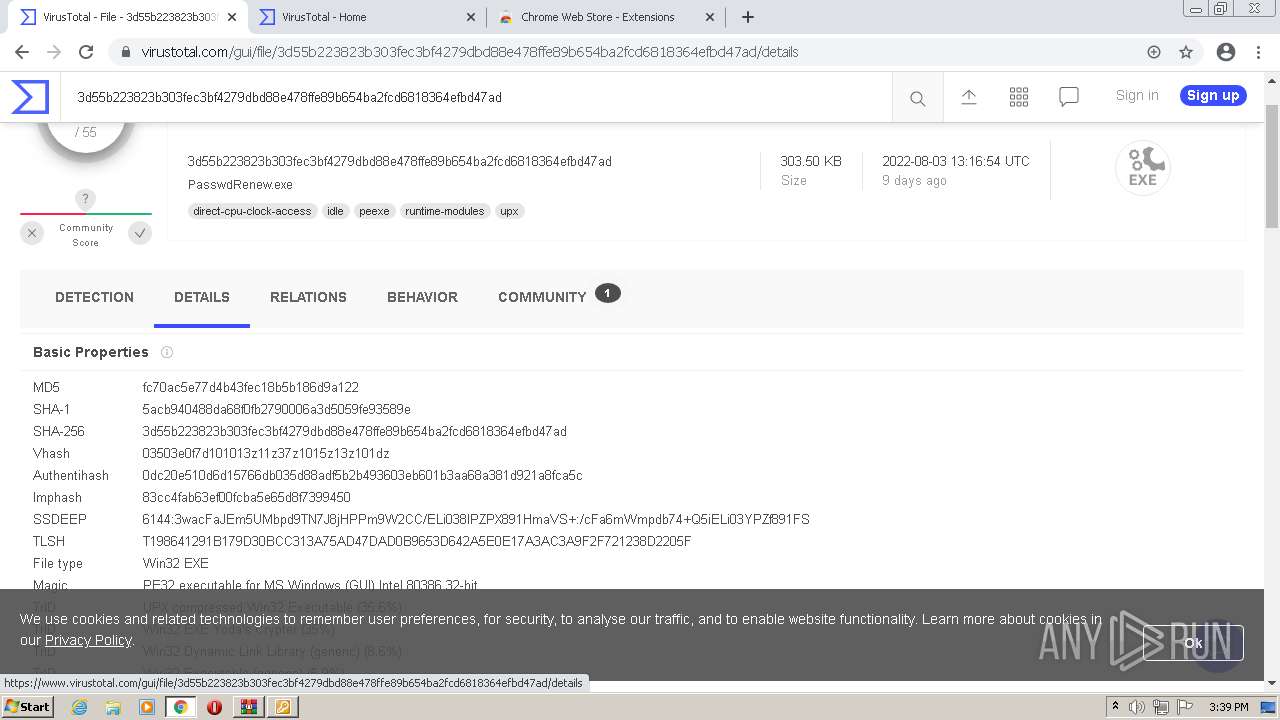
| File name: | renew_1.1-BETA.cab |
| Full analysis: | https://app.any.run/tasks/a7bbcefb-75e4-444f-9e72-148a780e6fbc |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2022, 14:35:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-cab-compressed |
| File info: | Microsoft Cabinet archive data, 506781 bytes, 10 files |
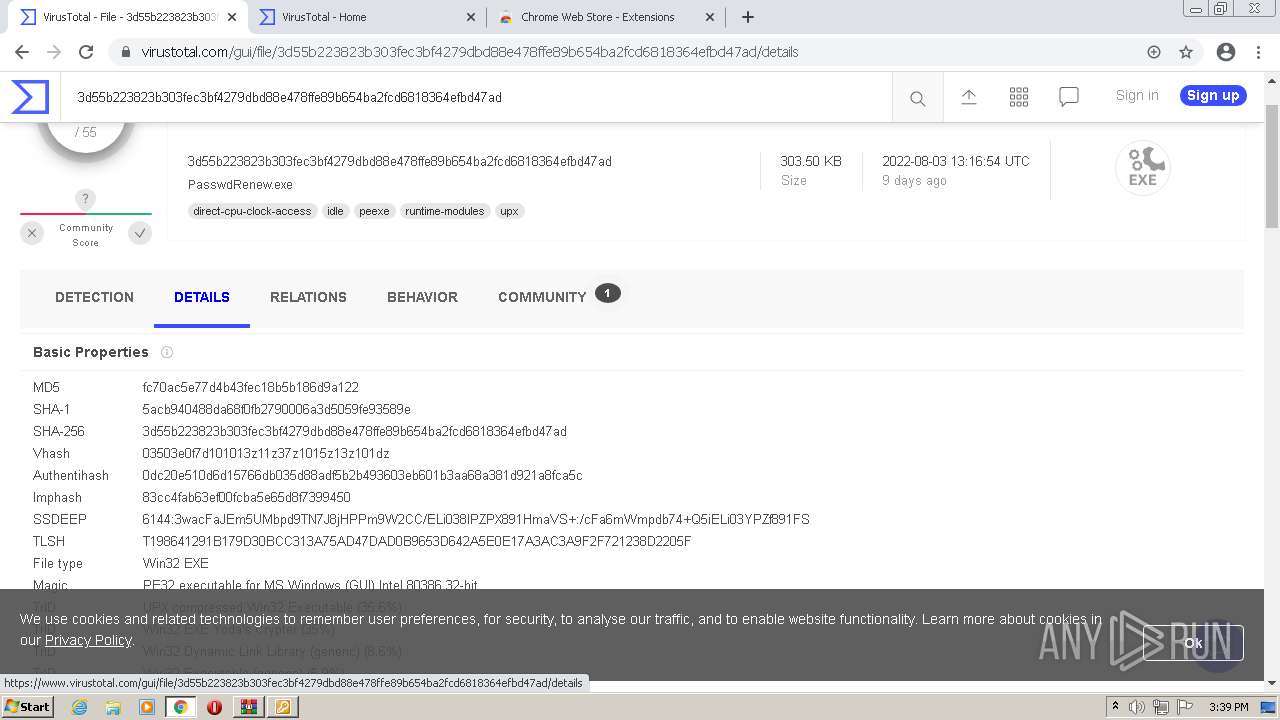
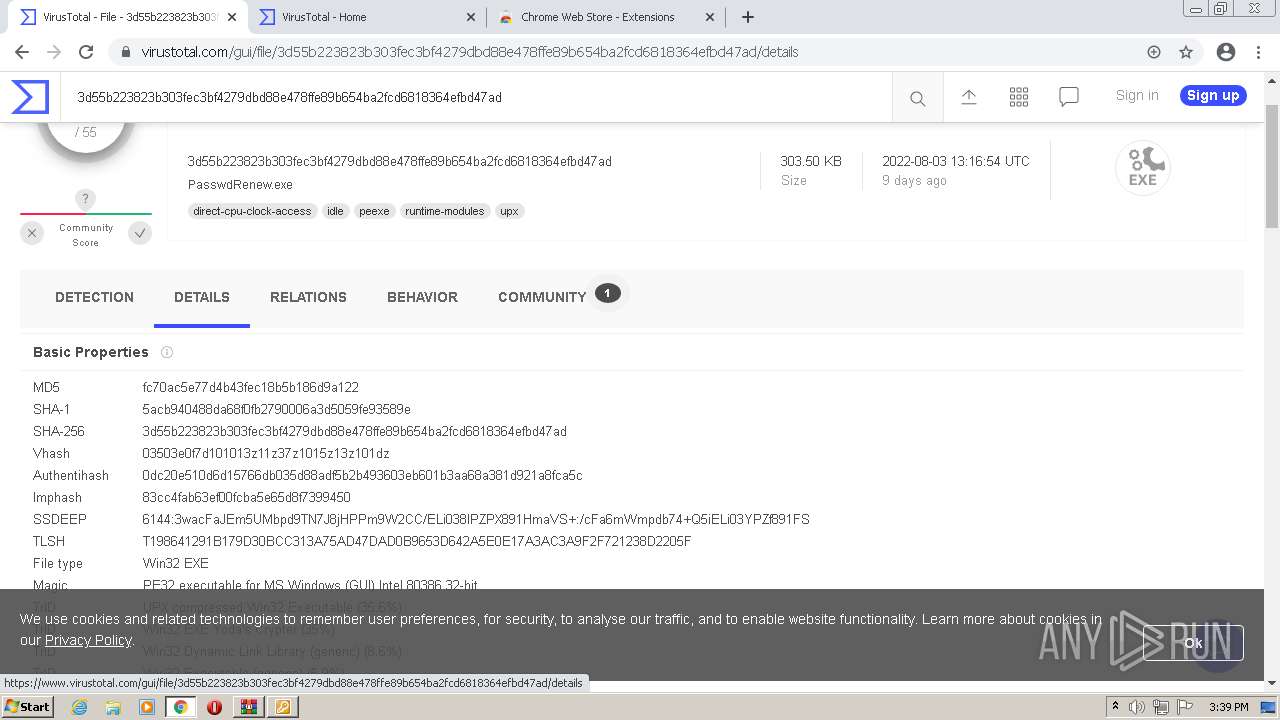
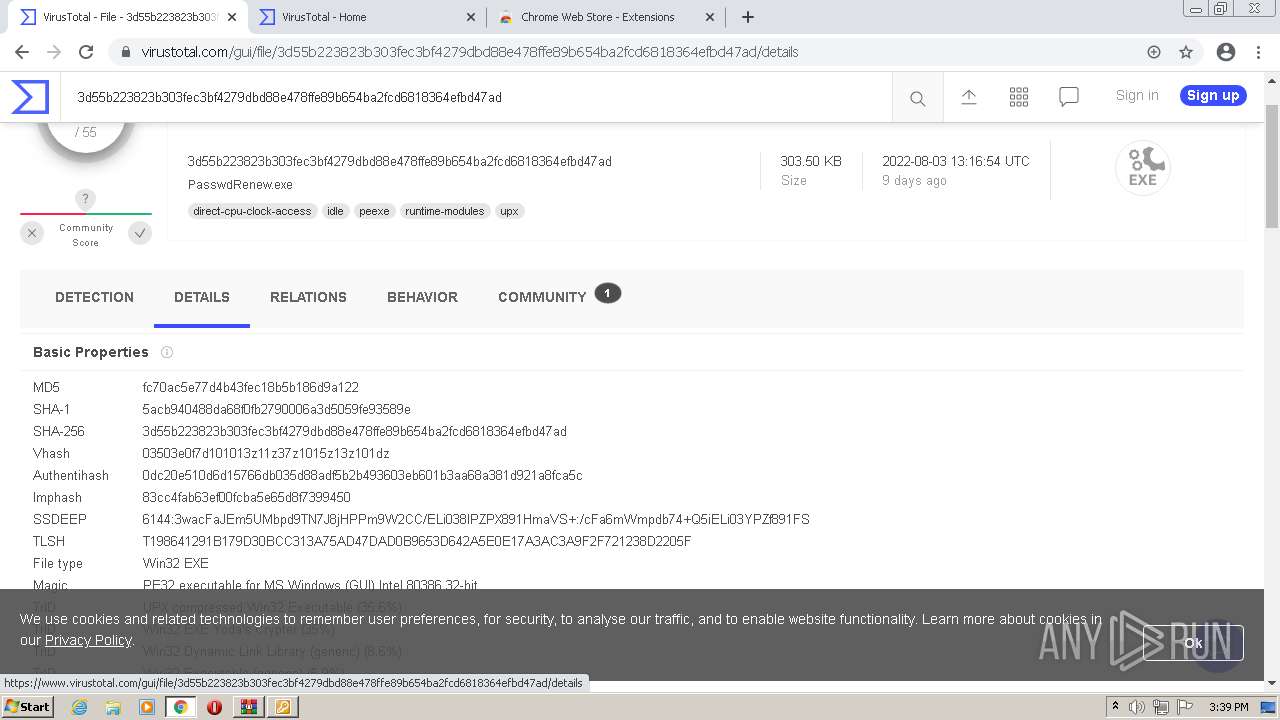
| MD5: | AE6D5B1371515116AE985F26DAC1779B |
| SHA1: | 1A8D88609FD09439768D1F112F7D069721821CF2 |
| SHA256: | 73F25BAE88DE3247B8068EA86286A5E88F48FC86267AA56C37847A4E81814157 |
| SSDEEP: | 12288:Z2hdWUDsvNDN/JjO29oHOcwaMt9A0VjDLn6I7IkFYR4:ZGdWLvNZ/Jjf6HVwaMX5DLZPJ |
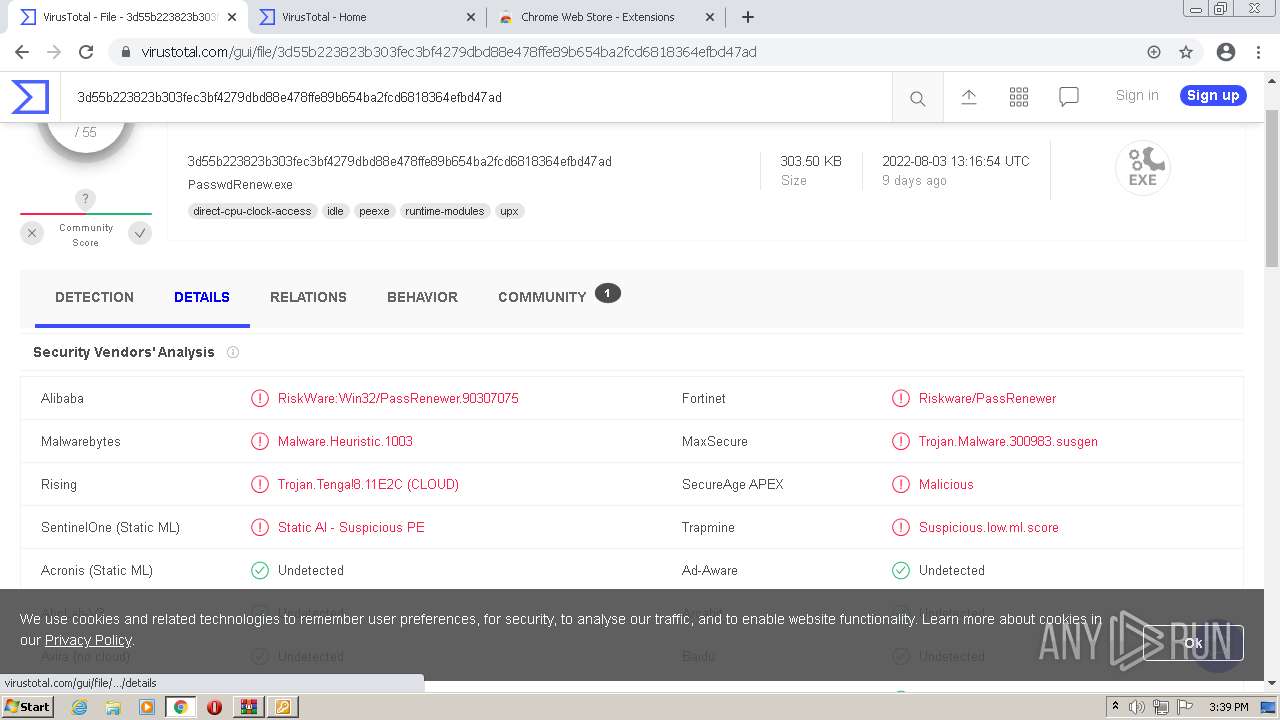
MALICIOUS
Drops executable file immediately after starts
- WinRAR.exe (PID: 3428)
Application was dropped or rewritten from another process
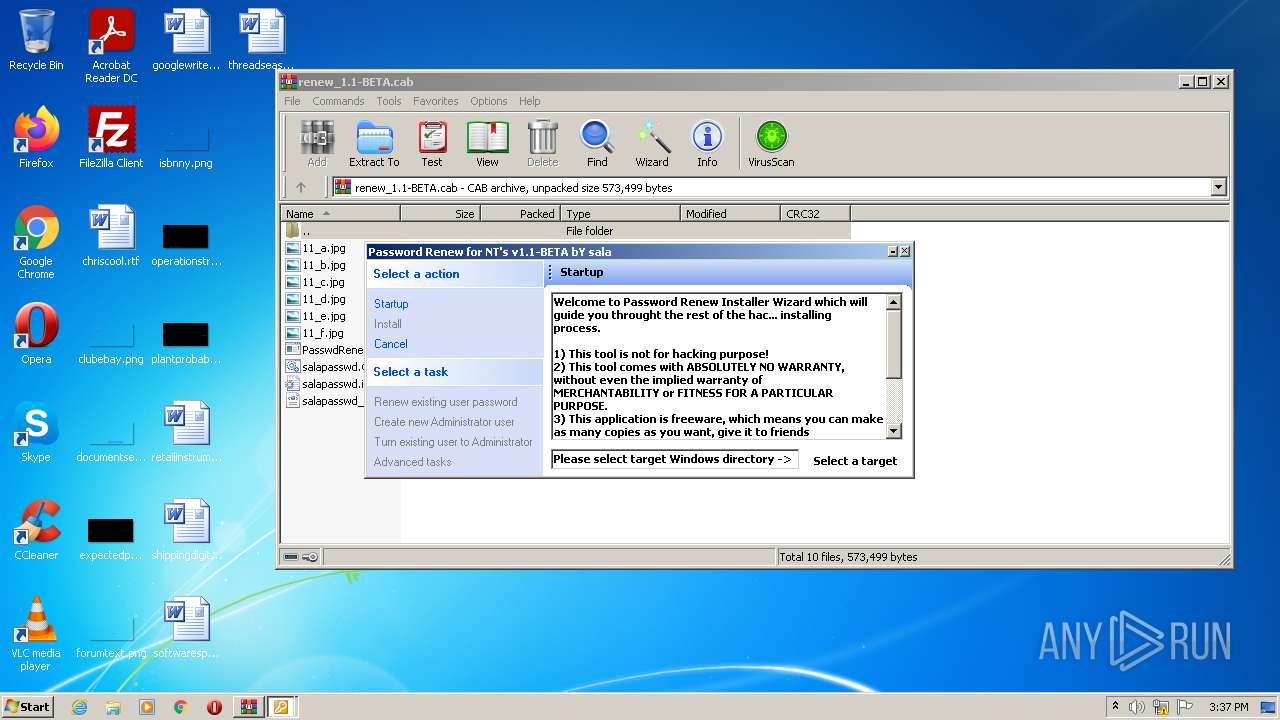
- PasswdRenew.exe (PID: 2180)
- PasswdRenew.exe (PID: 2312)
- PasswdRenew.exe (PID: 3828)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3428)
- PasswdRenew.exe (PID: 2180)
- notepad++.exe (PID: 3100)
- cmd.exe (PID: 3944)
- cmd.exe (PID: 3380)
- PasswdRenew.exe (PID: 2312)
- PasswdRenew.exe (PID: 3828)
- notepad++.exe (PID: 3284)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3428)
Reads the computer name
- WinRAR.exe (PID: 3428)
- PasswdRenew.exe (PID: 3828)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3428)
Reads default file associations for system extensions
- PasswdRenew.exe (PID: 3828)
- chrome.exe (PID: 2584)
- chrome.exe (PID: 3108)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2108)
INFO
Manual execution by user
- explorer.exe (PID: 2904)
- PasswdRenew.exe (PID: 2180)
- notepad++.exe (PID: 3100)
- cmd.exe (PID: 3380)
- cmd.exe (PID: 3944)
- notepad++.exe (PID: 3284)
- chrome.exe (PID: 2108)
Reads the computer name
- explorer.exe (PID: 2904)
- chrome.exe (PID: 2108)
- chrome.exe (PID: 3632)
- chrome.exe (PID: 3096)
- chrome.exe (PID: 2900)
- chrome.exe (PID: 476)
- chrome.exe (PID: 2584)
- chrome.exe (PID: 3108)
- chrome.exe (PID: 2152)
- chrome.exe (PID: 2496)
- chrome.exe (PID: 3892)
- chrome.exe (PID: 3108)
Checks supported languages
- explorer.exe (PID: 2904)
- chrome.exe (PID: 2108)
- chrome.exe (PID: 3500)
- chrome.exe (PID: 336)
- chrome.exe (PID: 3632)
- chrome.exe (PID: 3096)
- chrome.exe (PID: 3512)
- chrome.exe (PID: 1952)
- chrome.exe (PID: 2900)
- chrome.exe (PID: 3732)
- chrome.exe (PID: 3800)
- chrome.exe (PID: 2928)
- chrome.exe (PID: 728)
- chrome.exe (PID: 2916)
- chrome.exe (PID: 3160)
- chrome.exe (PID: 476)
- chrome.exe (PID: 3096)
- chrome.exe (PID: 3928)
- chrome.exe (PID: 3140)
- chrome.exe (PID: 3696)
- chrome.exe (PID: 752)
- chrome.exe (PID: 3808)
- chrome.exe (PID: 2480)
- chrome.exe (PID: 2584)
- chrome.exe (PID: 2152)
- chrome.exe (PID: 3108)
- chrome.exe (PID: 2496)
- chrome.exe (PID: 2844)
- chrome.exe (PID: 2920)
- chrome.exe (PID: 3480)
- chrome.exe (PID: 3508)
- chrome.exe (PID: 3624)
- chrome.exe (PID: 3892)
- chrome.exe (PID: 3704)
- chrome.exe (PID: 3828)
- chrome.exe (PID: 2384)
- chrome.exe (PID: 1204)
- chrome.exe (PID: 304)
- chrome.exe (PID: 1604)
- chrome.exe (PID: 3132)
- chrome.exe (PID: 3108)
- chrome.exe (PID: 4000)
- chrome.exe (PID: 2456)
- chrome.exe (PID: 2556)
- chrome.exe (PID: 3216)
- chrome.exe (PID: 3476)
Application launched itself
- chrome.exe (PID: 2108)
Reads settings of System Certificates
- chrome.exe (PID: 3632)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 2108)
Reads the date of Windows installation
- chrome.exe (PID: 3108)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .cab | | | Microsoft Cabinet Archive (100) |
|---|
Total processes
94
Monitored processes
54
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1048,3844619393583317086,16483525406813858199,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1664 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 336 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6dfbd988,0x6dfbd998,0x6dfbd9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 476 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1048,3844619393583317086,16483525406813858199,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3272 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 728 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1048,3844619393583317086,16483525406813858199,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3568 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 752 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1048,3844619393583317086,16483525406813858199,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2368 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1204 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1048,3844619393583317086,16483525406813858199,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2764 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1604 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1048,3844619393583317086,16483525406813858199,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2700 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,3844619393583317086,16483525406813858199,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2184 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2108 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | Explorer.EXE | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2152 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1048,3844619393583317086,16483525406813858199,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1720 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
21 921
Read events
21 538
Write events
371
Delete events
12
Modification events
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\renew_1.1-BETA.cab | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
2
Suspicious files
240
Text files
182
Unknown types
10
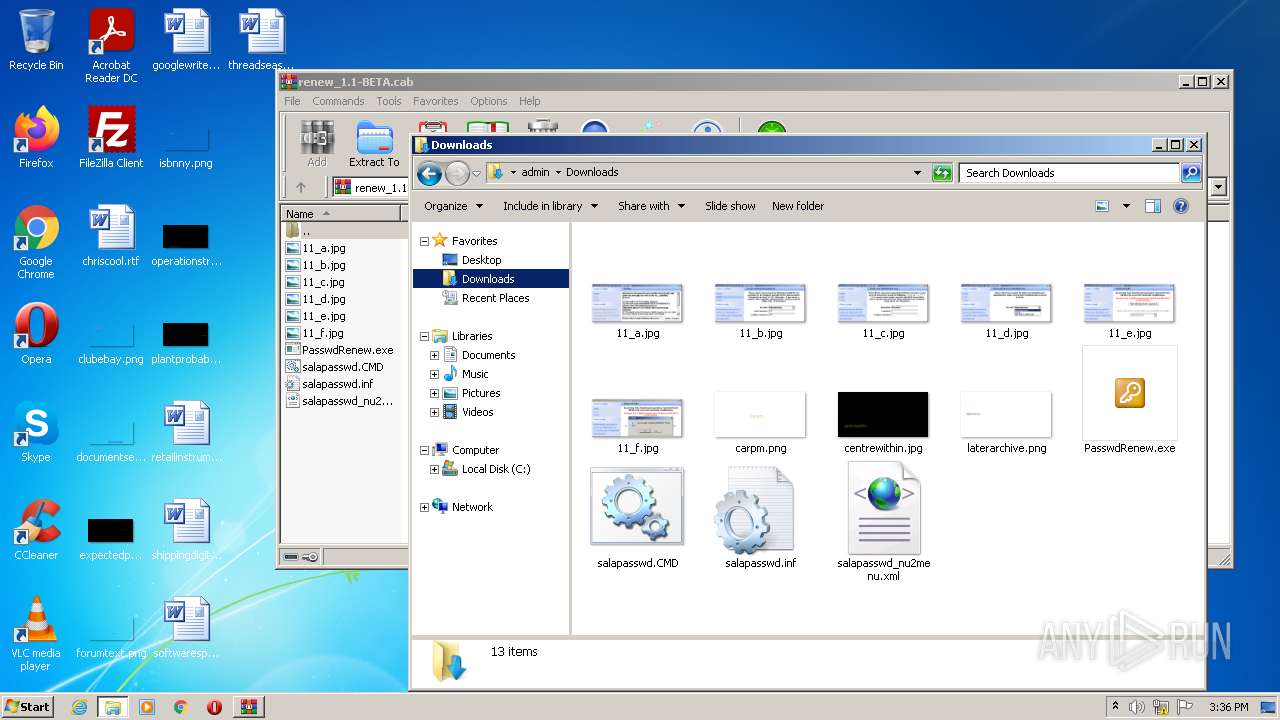
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\renew_1.1-BETA\11_c.jpg | image | |
MD5:D2E9ED8D2FC3556DD92BDDF2A241651A | SHA256:59027852D303454D35D30568B6FEBD4D24E341BA081899C5E268AE3D2B06508A | |||
| 3428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\renew_1.1-BETA\11_a.jpg | image | |
MD5:AA7C09B05C7E36F31EA0CBA9129440E4 | SHA256:46D1B34BC7A9A453A798E452B8D3F0CDDAED7931595138D68B1A445643B2246C | |||
| 3428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\renew_1.1-BETA\11_e.jpg | image | |
MD5:FB7B544307BBF5E757165D0E0421B48E | SHA256:D6F493E4435092735AB47E1F3A57A1AE554BF53EF37FF4A88D63934D5CEAE24C | |||
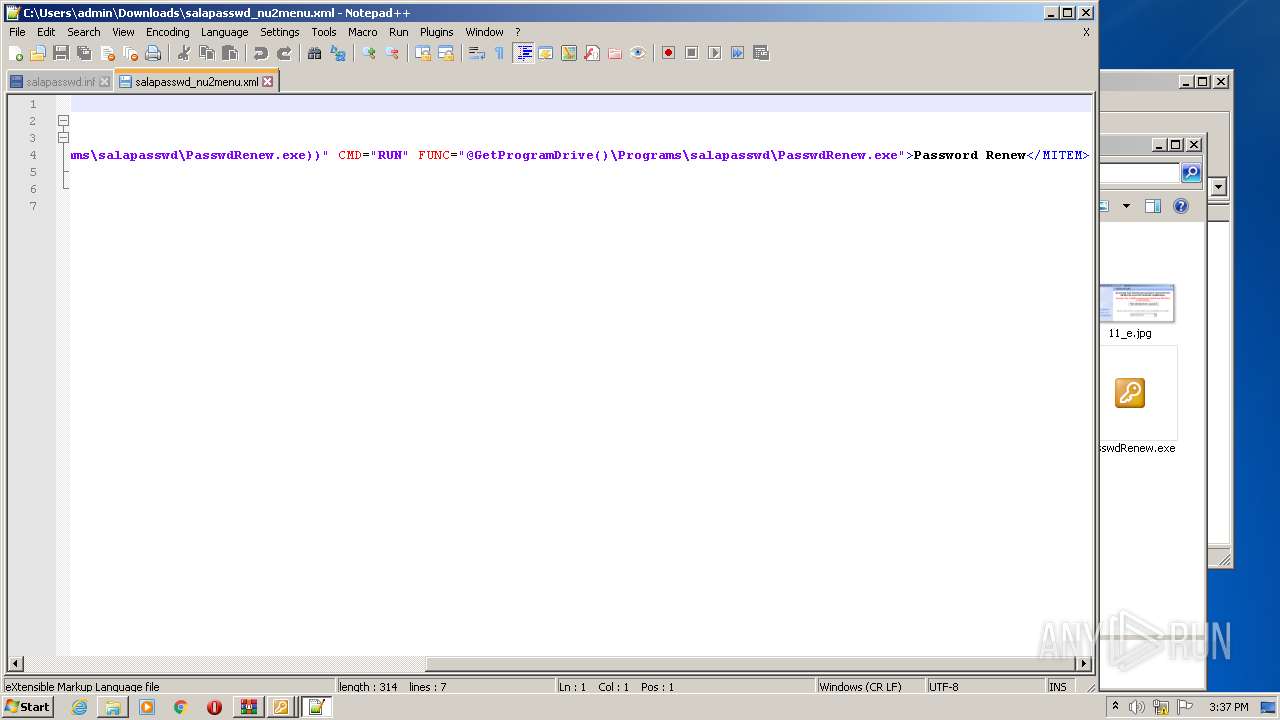
| 3428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\renew_1.1-BETA\salapasswd_nu2menu.xml | text | |
MD5:34E3454B41BF9D76D195F91C203C028B | SHA256:41B0A13A3D39274F39E278407CC44CBD85D903CF52B0B96DA1ECFFEEC7F6B1CF | |||
| 3428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\renew_1.1-BETA\11_b.jpg | image | |
MD5:426DB948952F9782B2DC4A7CB966A568 | SHA256:97ADA288C486C724915430BFEA8D8EB073D75373D90F4789F43A27622B6D0DC6 | |||
| 2108 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-62F665DA-83C.pma | — | |
MD5:— | SHA256:— | |||
| 3428 | WinRAR.exe | C:\Users\admin\Downloads\11_a.jpg | image | |
MD5:AA7C09B05C7E36F31EA0CBA9129440E4 | SHA256:46D1B34BC7A9A453A798E452B8D3F0CDDAED7931595138D68B1A445643B2246C | |||
| 3428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\renew_1.1-BETA\11_f.jpg | image | |
MD5:C0EC602B7E586DB5527807DDD45474D2 | SHA256:1B2FAF6C1A59D1EB44C295D97FFE18BA920F0B45AD7DEE842AF5CF71DC565511 | |||
| 3428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\renew_1.1-BETA\11_d.jpg | image | |
MD5:2C34EB75CA43A724BCC373147A713760 | SHA256:4A3A4D2C64AA5C1C55465A8956729B43432D950C91FB6C1683B0EC9D342CB12B | |||
| 3428 | WinRAR.exe | C:\Users\admin\Downloads\11_d.jpg | image | |
MD5:2C34EB75CA43A724BCC373147A713760 | SHA256:4A3A4D2C64AA5C1C55465A8956729B43432D950C91FB6C1683B0EC9D342CB12B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
39
TCP/UDP connections
48
DNS requests
34
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3632 | chrome.exe | GET | 302 | 216.239.32.21:80 | http://virustotal.com/ | US | — | — | whitelisted |
928 | svchost.exe | HEAD | 302 | 142.250.181.238:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | — | — | whitelisted |
928 | svchost.exe | HEAD | 200 | 84.15.64.140:80 | http://r1---sn-cpux-8ov6.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3?cms_redirect=yes&mh=VX&mip=85.206.166.82&mm=28&mn=sn-cpux-8ov6&ms=nvh&mt=1660314744&mv=m&mvi=1&pl=22&shardbypass=sd | LT | — | — | whitelisted |
3632 | chrome.exe | GET | 302 | 142.250.181.238:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 612 b | whitelisted |
928 | svchost.exe | GET | 302 | 142.250.181.238:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | html | 539 b | whitelisted |
928 | svchost.exe | GET | 302 | 142.250.181.238:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | html | 539 b | whitelisted |
928 | svchost.exe | GET | 302 | 142.250.181.238:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | html | 539 b | whitelisted |
928 | svchost.exe | GET | 206 | 84.15.64.140:80 | http://r1---sn-cpux-8ov6.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3?cms_redirect=yes&mh=VX&mip=85.206.166.82&mm=28&mn=sn-cpux-8ov6&ms=nvh&mt=1660314744&mv=m&mvi=1&pl=22&shardbypass=sd | LT | binary | 9.54 Kb | whitelisted |
928 | svchost.exe | GET | 206 | 84.15.64.140:80 | http://r1---sn-cpux-8ov6.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3?cms_redirect=yes&mh=VX&mip=85.206.166.82&mm=28&mn=sn-cpux-8ov6&ms=nvh&mt=1660314744&mv=m&mvi=1&pl=22&shardbypass=sd | LT | binary | 12.0 Kb | whitelisted |
928 | svchost.exe | GET | 302 | 142.250.181.238:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | html | 539 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3632 | chrome.exe | 142.250.185.142:443 | clients2.google.com | Google Inc. | US | whitelisted |
3632 | chrome.exe | 142.250.181.225:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
3632 | chrome.exe | 142.250.186.164:443 | www.google.com | Google Inc. | US | whitelisted |
3632 | chrome.exe | 142.250.185.67:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3632 | chrome.exe | 142.251.36.10:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3632 | chrome.exe | 172.217.18.3:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3632 | chrome.exe | 172.217.16.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3632 | chrome.exe | 142.250.185.174:443 | encrypted-tbn0.gstatic.com | Google Inc. | US | whitelisted |
3632 | chrome.exe | 172.217.16.195:443 | update.googleapis.com | Google Inc. | US | whitelisted |
3632 | chrome.exe | 142.250.181.238:80 | redirector.gvt1.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clients2.google.com |
| whitelisted |
accounts.google.com |
| shared |
clients2.googleusercontent.com |
| whitelisted |
www.google.com |
| malicious |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
apis.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|