| File name: | Setup.exe |
| Full analysis: | https://app.any.run/tasks/df2cc205-e523-4891-b06f-76b49997da3a |
| Verdict: | Malicious activity |
| Analysis date: | July 26, 2025, 08:43:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | 72C434AE868156CAD89A3C0446DD1C26 |
| SHA1: | 8D05118776719E1ABF5DE865EC4696E852F68DAB |
| SHA256: | 73E75B9542520645FC474CB678297744A064ADC91DBAD2E18146C2CA63951846 |
| SSDEEP: | 98304:fC3CpAgJebngUnAGFJ+90pB1/B91QEZkdeHnUxn8MJlIMhpBIMoFqetcFNtImIT2:iKNFzm6aqBy2EabxUyVLkgGS55A/P |
MALICIOUS
Create files in the Startup directory
- AnyDesk.exe (PID: 5712)
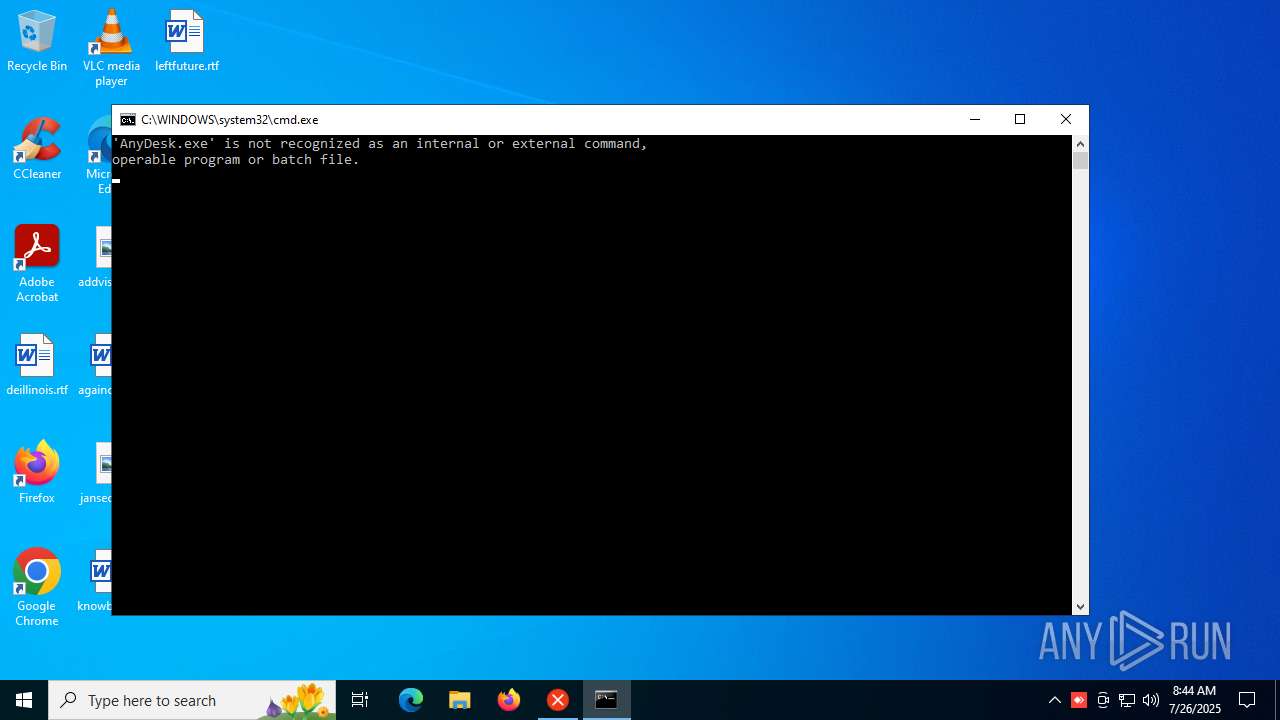
Bypass execution policy to execute commands
- powershell.exe (PID: 1056)
SUSPICIOUS
The process drops C-runtime libraries
- Setup.exe (PID: 3860)
- Setup.exe (PID: 5780)
Process drops python dynamic module
- Setup.exe (PID: 3860)
- Setup.exe (PID: 5780)
Process drops legitimate windows executable
- Setup.exe (PID: 3860)
- Setup.exe (PID: 5780)
Reads the date of Windows installation
- Setup.exe (PID: 768)
Application launched itself
- Setup.exe (PID: 768)
- Setup.exe (PID: 5780)
- AnyDesk.exe (PID: 5712)
- Setup.exe (PID: 3860)
- cmd.exe (PID: 3840)
- cmd.exe (PID: 6732)
Executable content was dropped or overwritten
- Setup.exe (PID: 5780)
- Setup.exe (PID: 3556)
- AnyDesk.exe (PID: 5712)
- Setup.exe (PID: 3860)
The executable file from the user directory is run by the CMD process
- AnyDesk.exe (PID: 5712)
Starts CMD.EXE for commands execution
- Setup.exe (PID: 3556)
- cmd.exe (PID: 3840)
- cmd.exe (PID: 6732)
ANYDESK has been found
- cmd.exe (PID: 3840)
- AnyDesk.exe (PID: 5712)
- AnyDesk.exe (PID: 7104)
- AnyDesk.exe (PID: 5712)
- AnyDesk.exe (PID: 6780)
- cmd.exe (PID: 4540)
- AnyDesk.exe (PID: 4044)
- AnyDesk.exe (PID: 3100)
- cmd.exe (PID: 6732)
- AnyDesk.exe (PID: 6760)
Executing commands from a ".bat" file
- Setup.exe (PID: 3556)
ANYDESK mutex has been found
- AnyDesk.exe (PID: 5712)
- AnyDesk.exe (PID: 6452)
- AnyDesk.exe (PID: 1324)
- AnyDesk.exe (PID: 7104)
- AnyDesk.exe (PID: 4044)
- AnyDesk.exe (PID: 6780)
- AnyDesk.exe (PID: 2632)
- AnyDesk.exe (PID: 3100)
- AnyDesk.exe (PID: 6760)
Creates file in the systems drive root
- AnyDesk.exe (PID: 5712)
Executes as Windows Service
- AnyDesk.exe (PID: 7104)
Reads security settings of Internet Explorer
- Setup.exe (PID: 768)
Creates a software uninstall entry
- AnyDesk.exe (PID: 7104)
- AnyDesk.exe (PID: 5712)
Searches for installed software
- AnyDesk.exe (PID: 7104)
- AnyDesk.exe (PID: 4044)
- AnyDesk.exe (PID: 6780)
- AnyDesk.exe (PID: 3100)
- AnyDesk.exe (PID: 6760)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 3840)
There is functionality for taking screenshot (YARA)
- Setup.exe (PID: 5780)
- Setup.exe (PID: 3556)
INFO
Create files in a temporary directory
- Setup.exe (PID: 3860)
- Setup.exe (PID: 5780)
- Setup.exe (PID: 3556)
Reads the computer name
- Setup.exe (PID: 3860)
- Setup.exe (PID: 5780)
- Setup.exe (PID: 3556)
- AnyDesk.exe (PID: 5712)
- AnyDesk.exe (PID: 6452)
- AnyDesk.exe (PID: 1324)
- AnyDesk.exe (PID: 7104)
- Setup.exe (PID: 768)
- AnyDesk.exe (PID: 6780)
- AnyDesk.exe (PID: 4044)
- AnyDesk.exe (PID: 2632)
- AnyDesk.exe (PID: 3100)
- AnyDesk.exe (PID: 6760)
Checks supported languages
- Setup.exe (PID: 3860)
- Setup.exe (PID: 5780)
- Setup.exe (PID: 3556)
- AnyDesk.exe (PID: 5712)
- AnyDesk.exe (PID: 1324)
- AnyDesk.exe (PID: 6452)
- Setup.exe (PID: 768)
- AnyDesk.exe (PID: 7104)
- AnyDesk.exe (PID: 6780)
- AnyDesk.exe (PID: 4044)
- AnyDesk.exe (PID: 2632)
- AnyDesk.exe (PID: 3100)
- AnyDesk.exe (PID: 6760)
Process checks computer location settings
- Setup.exe (PID: 768)
The sample compiled with english language support
- Setup.exe (PID: 5780)
- Setup.exe (PID: 3556)
- AnyDesk.exe (PID: 5712)
- Setup.exe (PID: 3860)
Creates files or folders in the user directory
- AnyDesk.exe (PID: 5712)
Reads the machine GUID from the registry
- AnyDesk.exe (PID: 1324)
- AnyDesk.exe (PID: 7104)
- AnyDesk.exe (PID: 4044)
Checks proxy server information
- AnyDesk.exe (PID: 6452)
- AnyDesk.exe (PID: 6780)
- Setup.exe (PID: 3556)
- slui.exe (PID: 3396)
Creates files in the program directory
- AnyDesk.exe (PID: 7104)
- AnyDesk.exe (PID: 5712)
Launching a file from the Startup directory
- AnyDesk.exe (PID: 5712)
Manual execution by a user
- AnyDesk.exe (PID: 6780)
- cmd.exe (PID: 6732)
- AnyDesk.exe (PID: 6760)
- powershell.exe (PID: 1056)
PyInstaller has been detected (YARA)
- Setup.exe (PID: 5780)
- Setup.exe (PID: 3556)
Reads CPU info
- AnyDesk.exe (PID: 6760)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1056)
UPX packer has been detected
- Setup.exe (PID: 3556)
Reads the software policy settings
- slui.exe (PID: 3396)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:07:26 08:40:12+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 174592 |
| InitializedDataSize: | 157184 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xd0d0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
156
Monitored processes
24
Malicious processes
8
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | timeout /t 1 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 768 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | — | Setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1056 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\Desktop\set.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | "C:\Users\admin\AppData\Local\Temp\tmpei8alrtt\AnyDesk.exe" --local-service | C:\Users\admin\AppData\Local\Temp\tmpei8alrtt\AnyDesk.exe | AnyDesk.exe | ||||||||||||
User: admin Company: AnyDesk Software GmbH Integrity Level: HIGH Description: AnyDesk Exit code: 9099 Version: 8.0.8 Modules
| |||||||||||||||
| 2120 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo LOCREMOTEPC " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
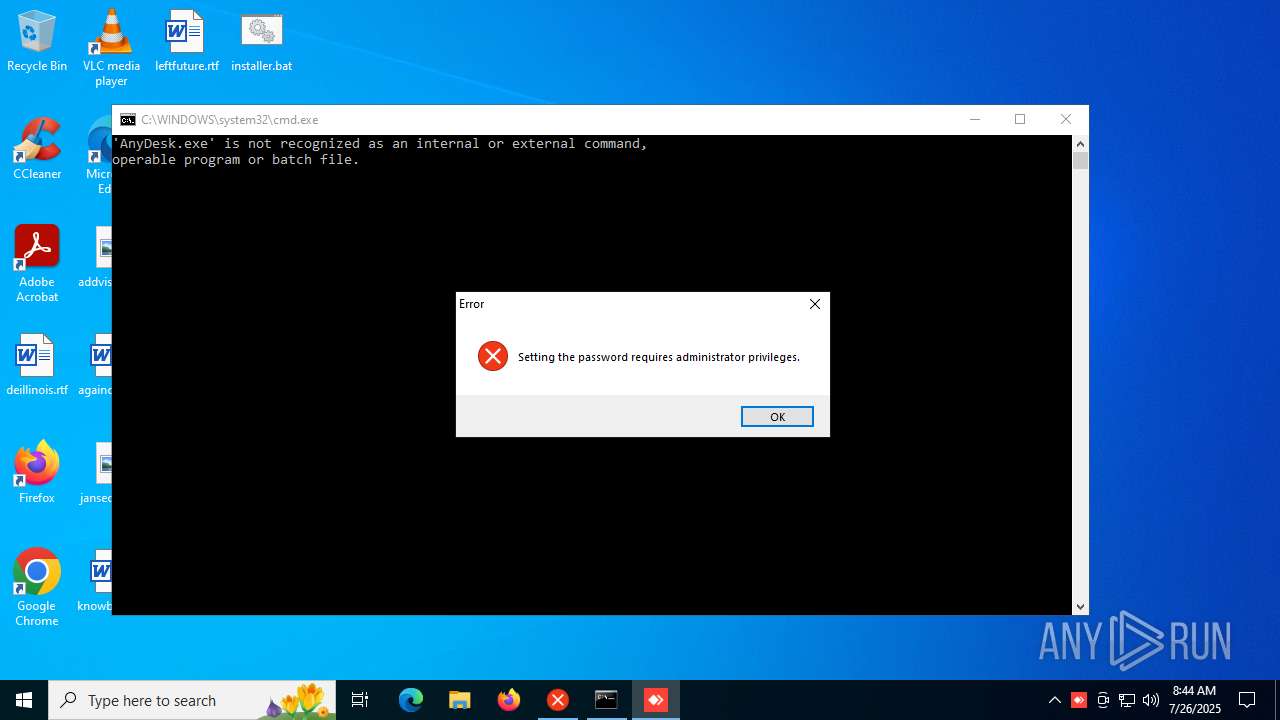
| 2632 | "C:\Program Files (x86)\AnyDesk\AnyDesk.exe" --set-password | C:\Program Files (x86)\AnyDesk\AnyDesk.exe | — | cmd.exe | |||||||||||
User: admin Company: AnyDesk Software GmbH Integrity Level: MEDIUM Description: AnyDesk Version: 8.0.8 Modules
| |||||||||||||||
| 3028 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3100 | "C:\Program Files (x86)\AnyDesk\AnyDesk.exe" --get-id | C:\Program Files (x86)\AnyDesk\AnyDesk.exe | — | cmd.exe | |||||||||||
User: admin Company: AnyDesk Software GmbH Integrity Level: HIGH Description: AnyDesk Exit code: 0 Version: 8.0.8 Modules
| |||||||||||||||
| 3396 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3556 | "C:\Users\admin\Desktop\Setup.exe" "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | Setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
10 238
Read events
10 215
Write events
23
Delete events
0
Modification events
| (PID) Process: | (5712) AnyDesk.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AnyDesk |
| Operation: | write | Name: | DisplayIcon |
Value: "C:\Program Files (x86)\AnyDesk\AnyDesk.exe" | |||
| (PID) Process: | (5712) AnyDesk.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AnyDesk |
| Operation: | write | Name: | DisplayName |
Value: AnyDesk | |||
| (PID) Process: | (5712) AnyDesk.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AnyDesk |
| Operation: | write | Name: | DisplayVersion |
Value: ad 8.0.8 | |||
| (PID) Process: | (5712) AnyDesk.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AnyDesk |
| Operation: | write | Name: | EstimatedSize |
Value: 2048 | |||
| (PID) Process: | (5712) AnyDesk.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AnyDesk |
| Operation: | write | Name: | HelpLink |
Value: https://help.anydesk.com/ | |||
| (PID) Process: | (5712) AnyDesk.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AnyDesk |
| Operation: | write | Name: | InstallLocation |
Value: "C:\Program Files (x86)\AnyDesk" | |||
| (PID) Process: | (5712) AnyDesk.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AnyDesk |
| Operation: | write | Name: | Publisher |
Value: AnyDesk Software GmbH | |||
| (PID) Process: | (5712) AnyDesk.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AnyDesk |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files (x86)\AnyDesk\AnyDesk.exe" --uninstall | |||
| (PID) Process: | (5712) AnyDesk.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AnyDesk |
| Operation: | write | Name: | VersionMajor |
Value: 8 | |||
| (PID) Process: | (5712) AnyDesk.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AnyDesk |
| Operation: | write | Name: | VersionMinor |
Value: 0 | |||
Executable files
44
Suspicious files
11
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3860 | Setup.exe | C:\Users\admin\AppData\Local\Temp\_MEI38602\_asyncio.pyd | executable | |
MD5:407A5F96128B79261AC282BCA6A73E2D | SHA256:A16FB3D1389840C273B7D1738E81A67E3D67B2D76E83CDDADFC9BC88BA045E80 | |||
| 3860 | Setup.exe | C:\Users\admin\AppData\Local\Temp\_MEI38602\VCRUNTIME140.dll | executable | |
MD5:32DA96115C9D783A0769312C0482A62D | SHA256:8B10C53241726B0ACC9F513157E67FCB01C166FEC69E5E38CA6AADA8F9A3619F | |||
| 3860 | Setup.exe | C:\Users\admin\AppData\Local\Temp\_MEI38602\_lzma.pyd | executable | |
MD5:5A67E09FDDAC7F870FC85D0D1425FAC2 | SHA256:D6B43F206910D421BFFCF2FBA39ACB6D1EBE1A66B1E286B0B54345A886ABFCD1 | |||
| 3860 | Setup.exe | C:\Users\admin\AppData\Local\Temp\_MEI38602\_multiprocessing.pyd | executable | |
MD5:181CBC250909CBC7CBB9A36DDE570F69 | SHA256:B51F8808C182CC21DD1C7DCB74B9F31D9602EDAC096BC8C79A99BA412D89D045 | |||
| 3860 | Setup.exe | C:\Users\admin\AppData\Local\Temp\_MEI38602\_queue.pyd | executable | |
MD5:FC7764652C24B8B0FE4ED51C0A7DDBF1 | SHA256:237DFC86E5644EE176B63501099E7FB4DB3C6FEA058BFF0D405EA761A9031787 | |||
| 3860 | Setup.exe | C:\Users\admin\AppData\Local\Temp\_MEI38602\_ctypes.pyd | executable | |
MD5:DE0B4AA088EE89BB15F8EB5C9DD20987 | SHA256:E0B6B4CFCC59BBB8F84F31F337C74774C895EAC4CF47AD36474022A0C6D2B049 | |||
| 3860 | Setup.exe | C:\Users\admin\AppData\Local\Temp\_MEI38602\_decimal.pyd | executable | |
MD5:A572AA95D2CE1E31F4CBFCAB8660327B | SHA256:A9C91599D96743A8D80BFFD8D6E50AE0FE9B3B29CD285BDEA8618FAFD4D5241B | |||
| 3860 | Setup.exe | C:\Users\admin\AppData\Local\Temp\_MEI38602\_ssl.pyd | executable | |
MD5:689368FE253E7BD465D35C8B4016AD75 | SHA256:7104EBB48FA102E25484AA914BE09853940A50FFC025013C2803163741F38C0B | |||
| 3860 | Setup.exe | C:\Users\admin\AppData\Local\Temp\_MEI38602\_overlapped.pyd | executable | |
MD5:55D570234A19D5A3E7F4D9D845A4223E | SHA256:E35B160BC6EF019593CFB7383D04E10D6F5FE1B9D464E32D46E760BEE0943308 | |||
| 3860 | Setup.exe | C:\Users\admin\AppData\Local\Temp\_MEI38602\_hashlib.pyd | executable | |
MD5:9D7B716E121A35E71997CBED4BD7117B | SHA256:E75E98D9F927C33E58C9ED6E7DCBFD92272A673861E62F5F65A5B3DB399437AA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
84
DNS requests
21
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.55.110.193:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.55.110.193:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.55.110.193:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.3.109.244:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.3.109.244:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.3.109.244:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.31.2:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.131:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | GET | 304 | 52.149.20.212:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | POST | 200 | 20.190.159.23:443 | https://login.live.com/RST2.srf | unknown | xml | 10.3 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.55.110.193:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.55.110.193:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.55.110.193:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.3.109.244:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 23.3.109.244:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.3.109.244:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
boot.net.anydesk.com |
| whitelisted |
relay-1461944f.net.anydesk.com |
| whitelisted |
data-center-9b03f-default-rtdb.asia-southeast1.firebasedatabase.app |
| unknown |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Misc activity | ET REMOTE_ACCESS Anydesk Relay Domain (net .anydesk .com) in DNS Lookup |
2200 | svchost.exe | Misc activity | ET REMOTE_ACCESS Anydesk Domain (boot .net .anydesk .com) in DNS Lookup |
2200 | svchost.exe | Misc activity | ET REMOTE_ACCESS Anydesk Relay Domain (net .anydesk .com) in DNS Lookup |